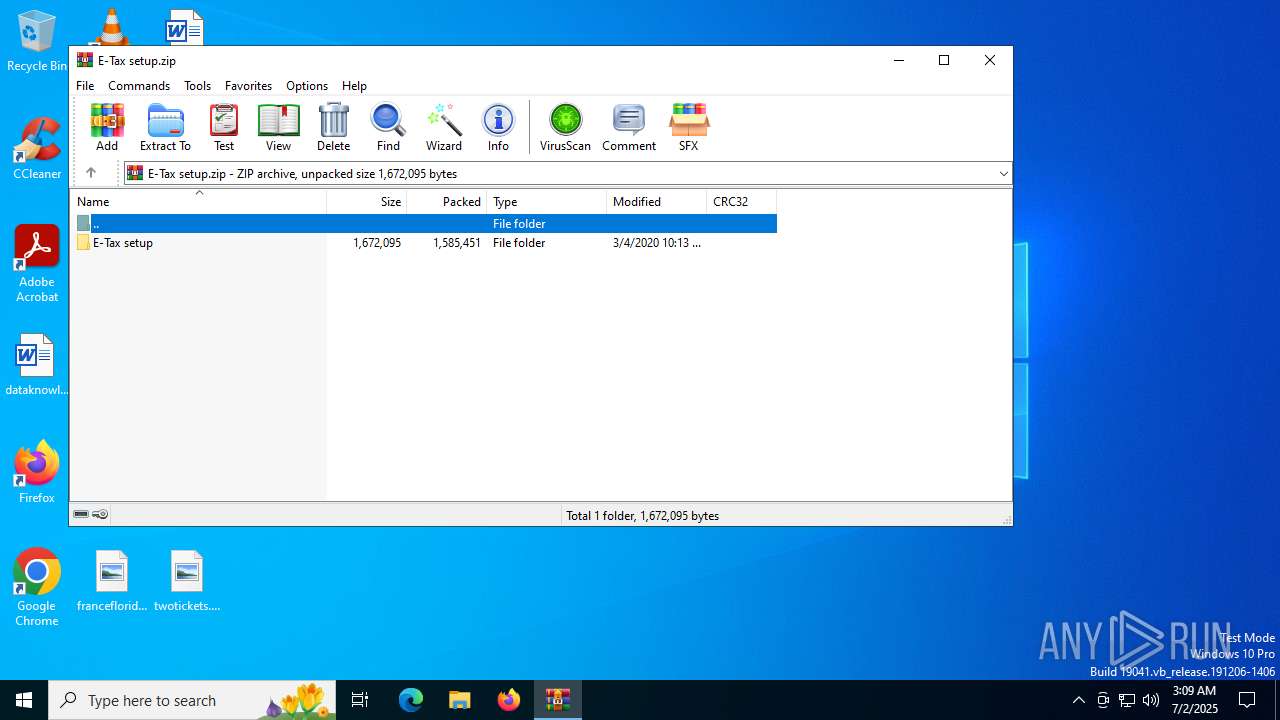
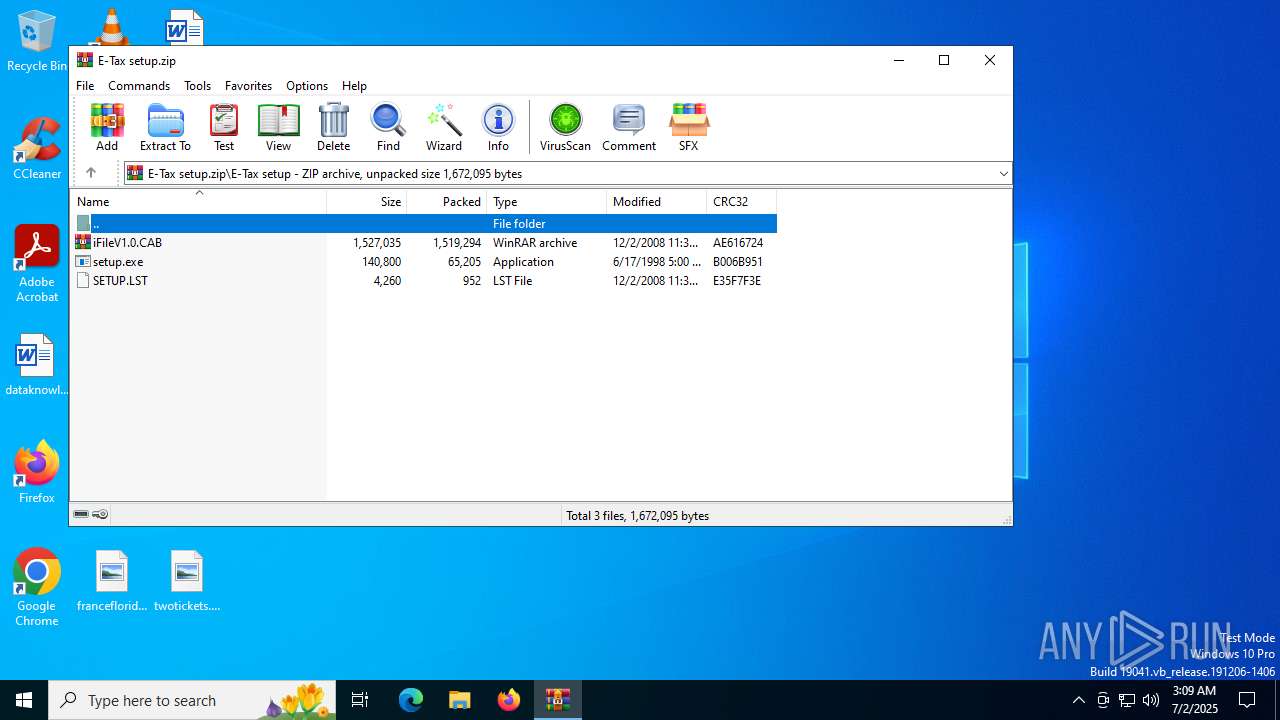
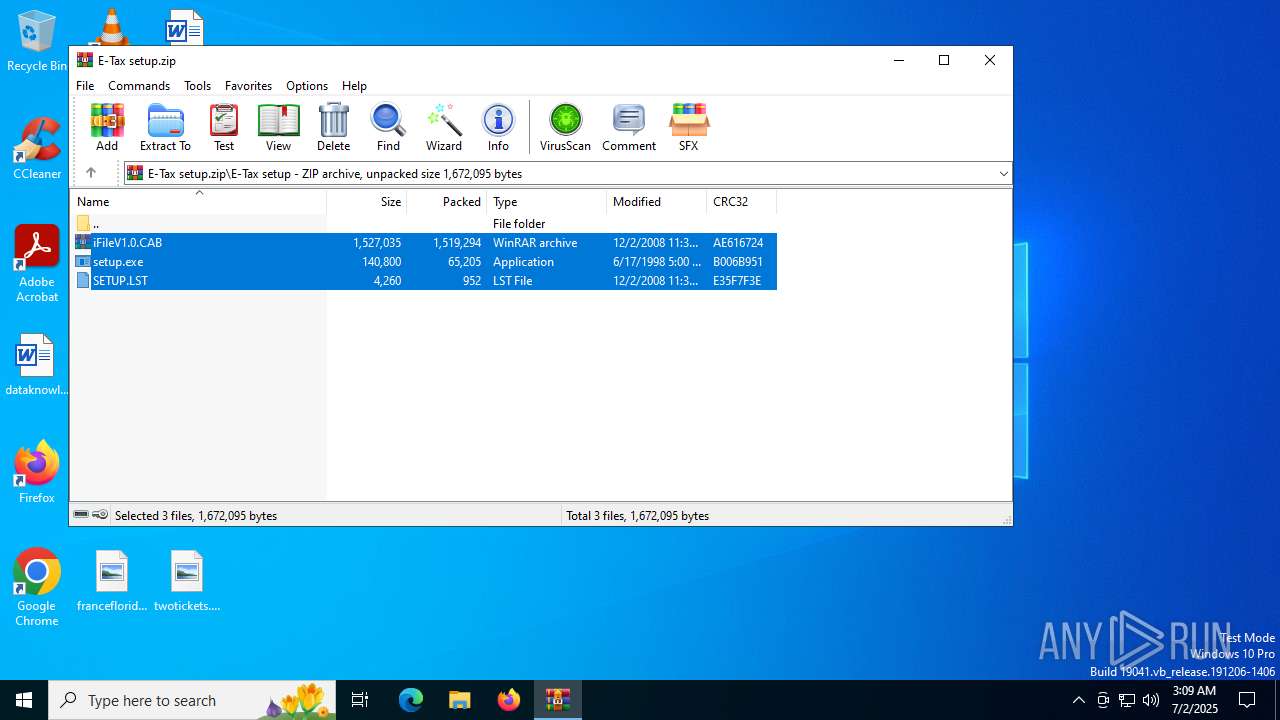
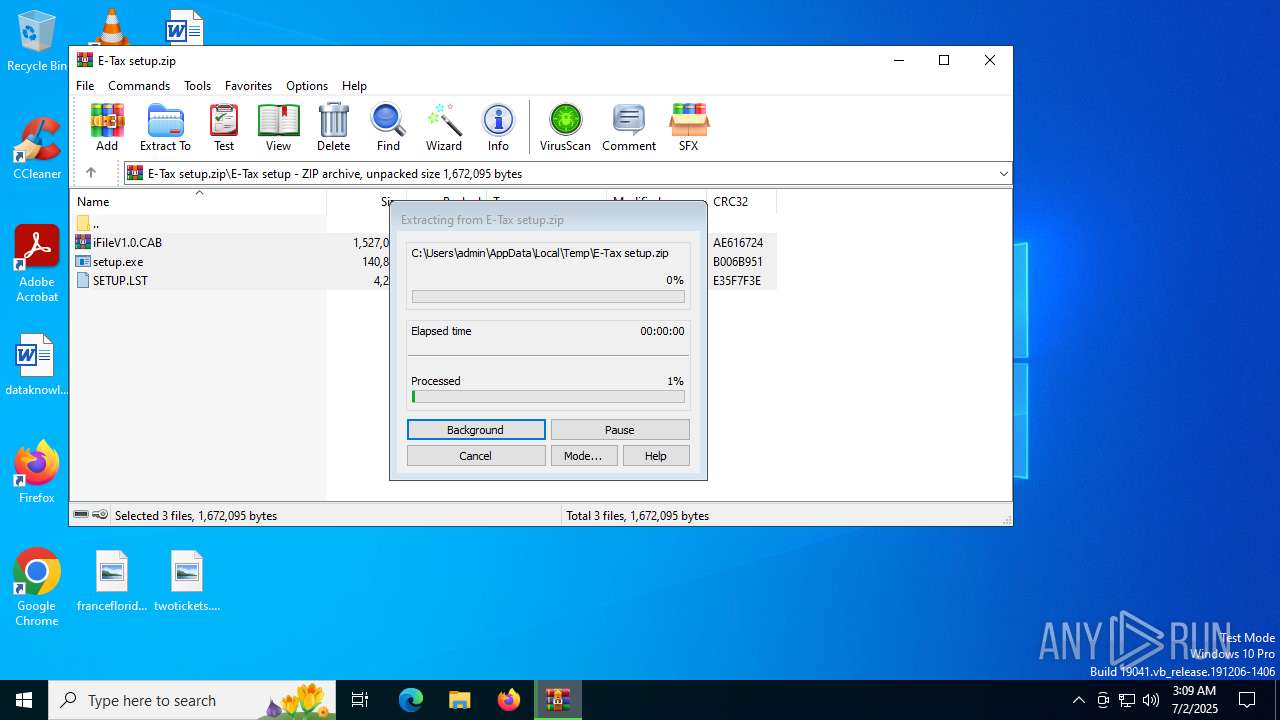
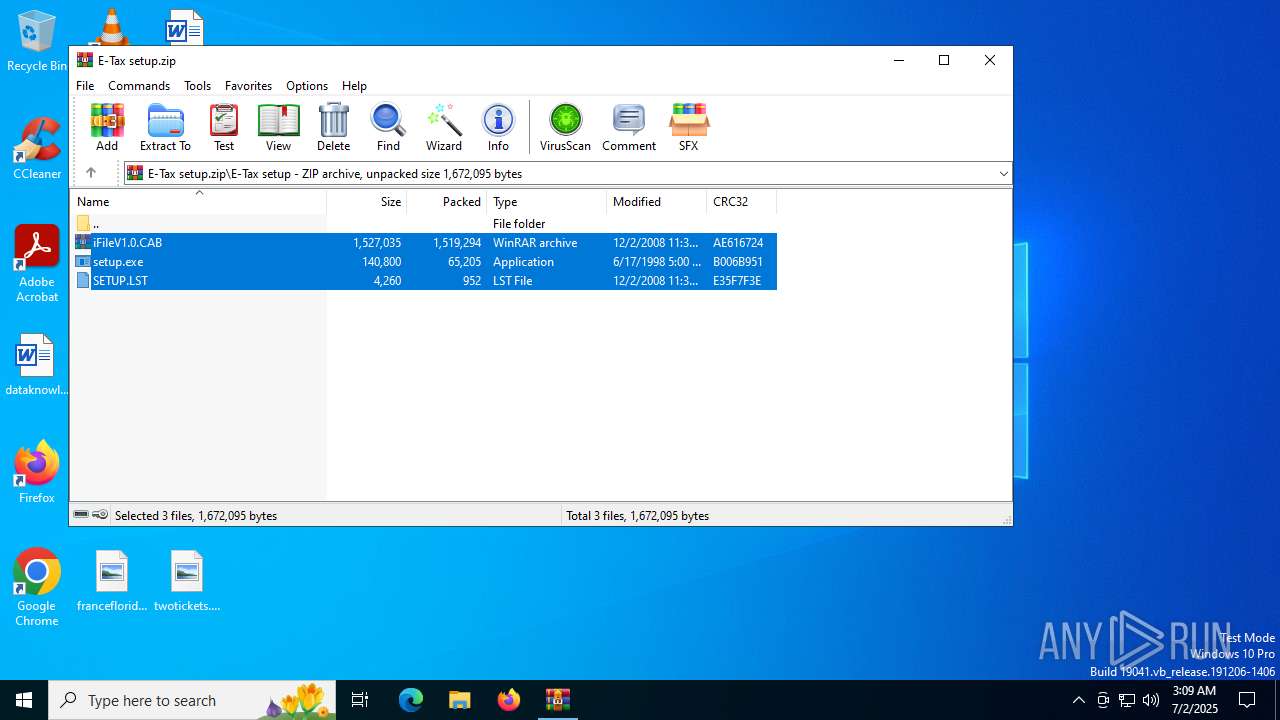
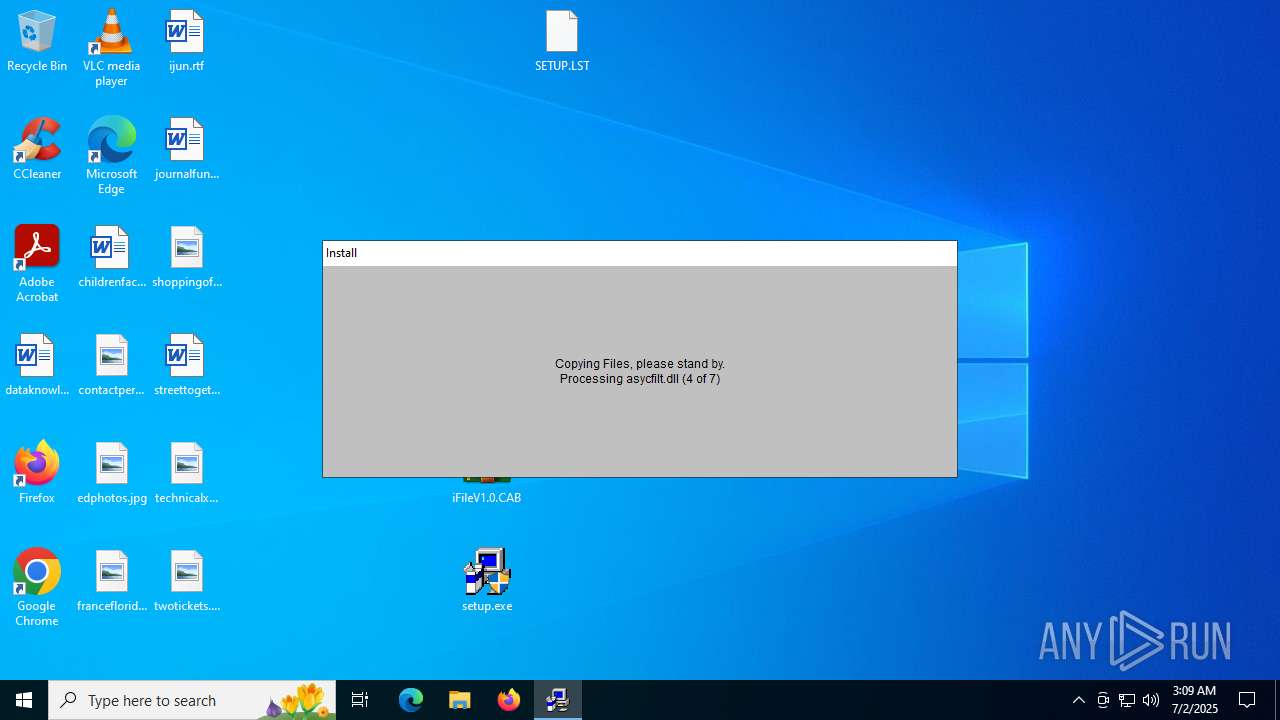
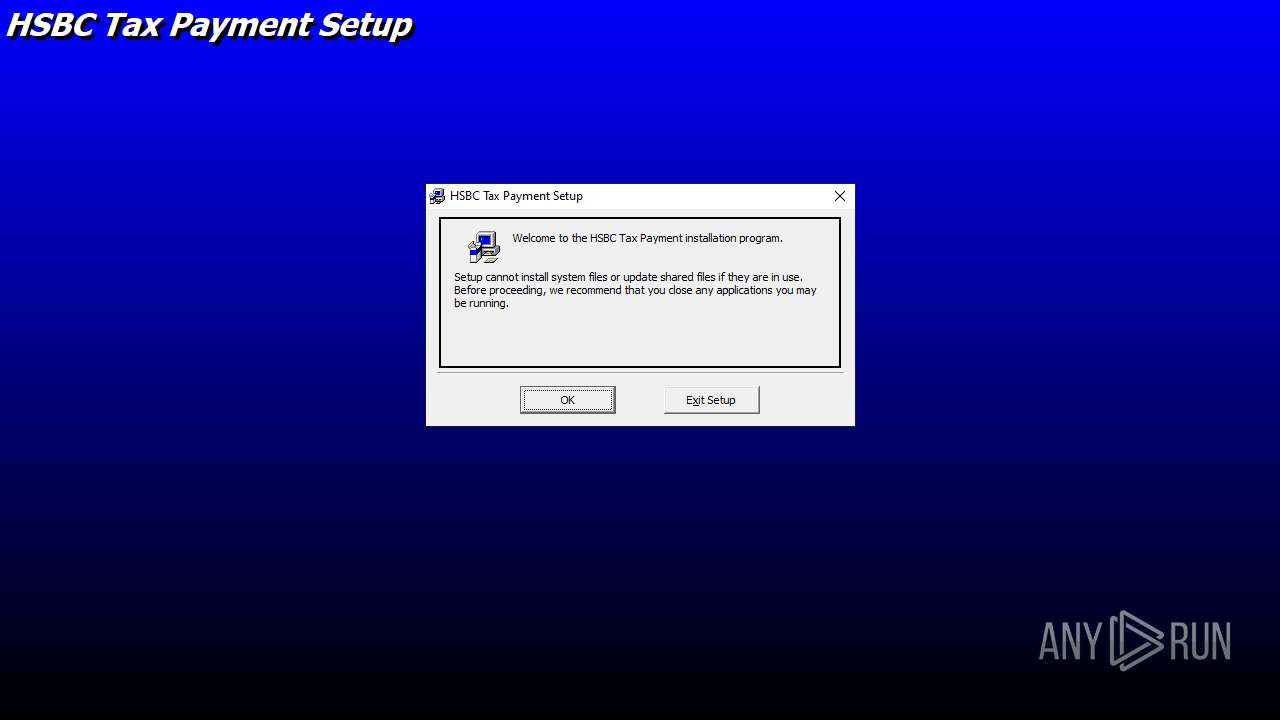
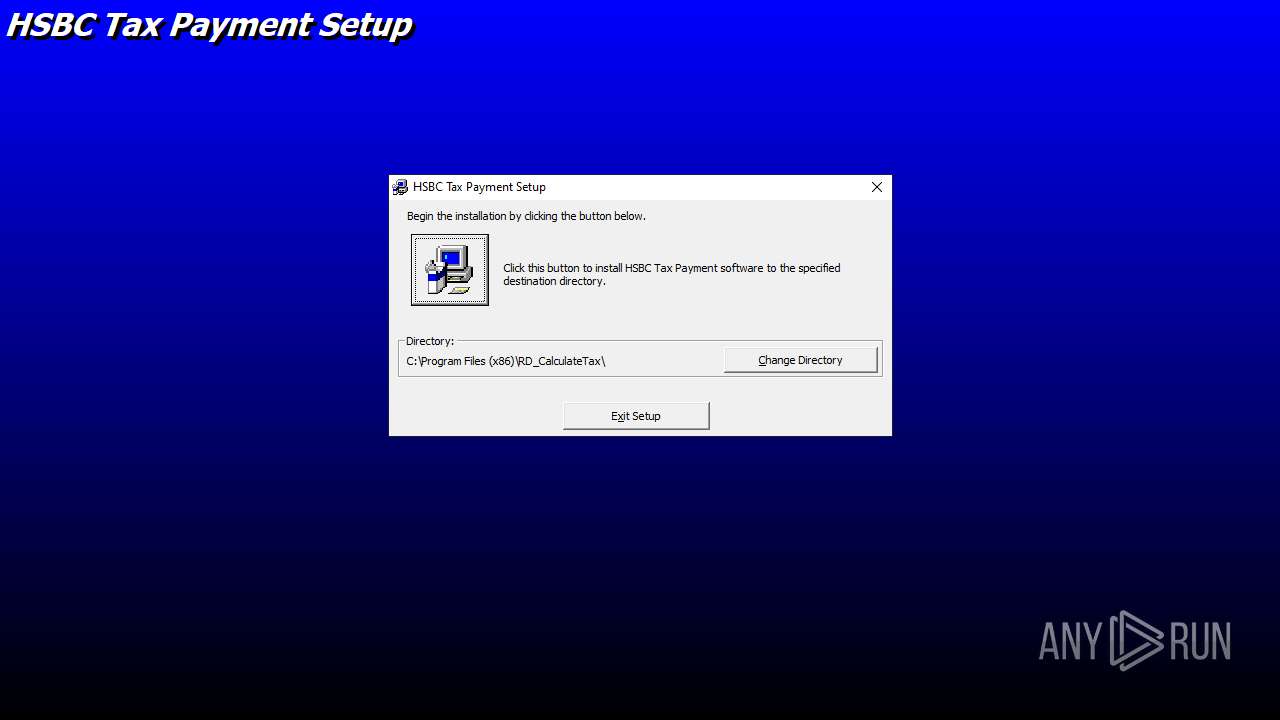
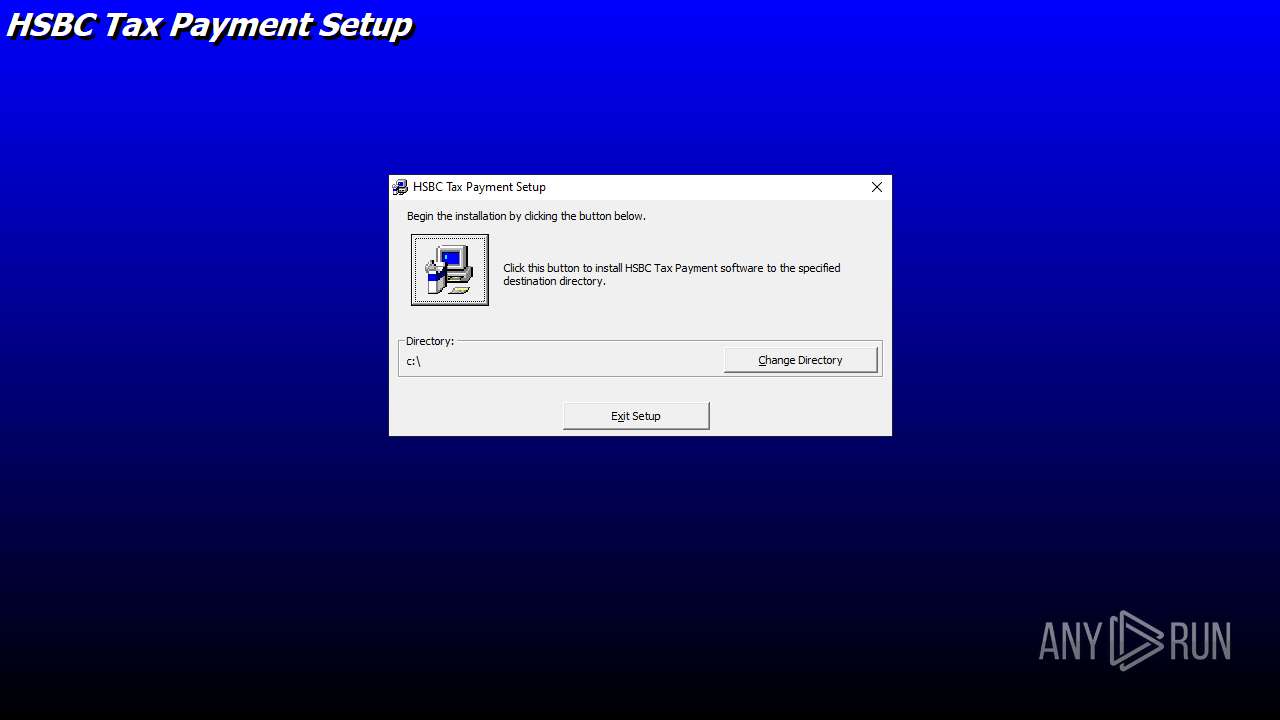
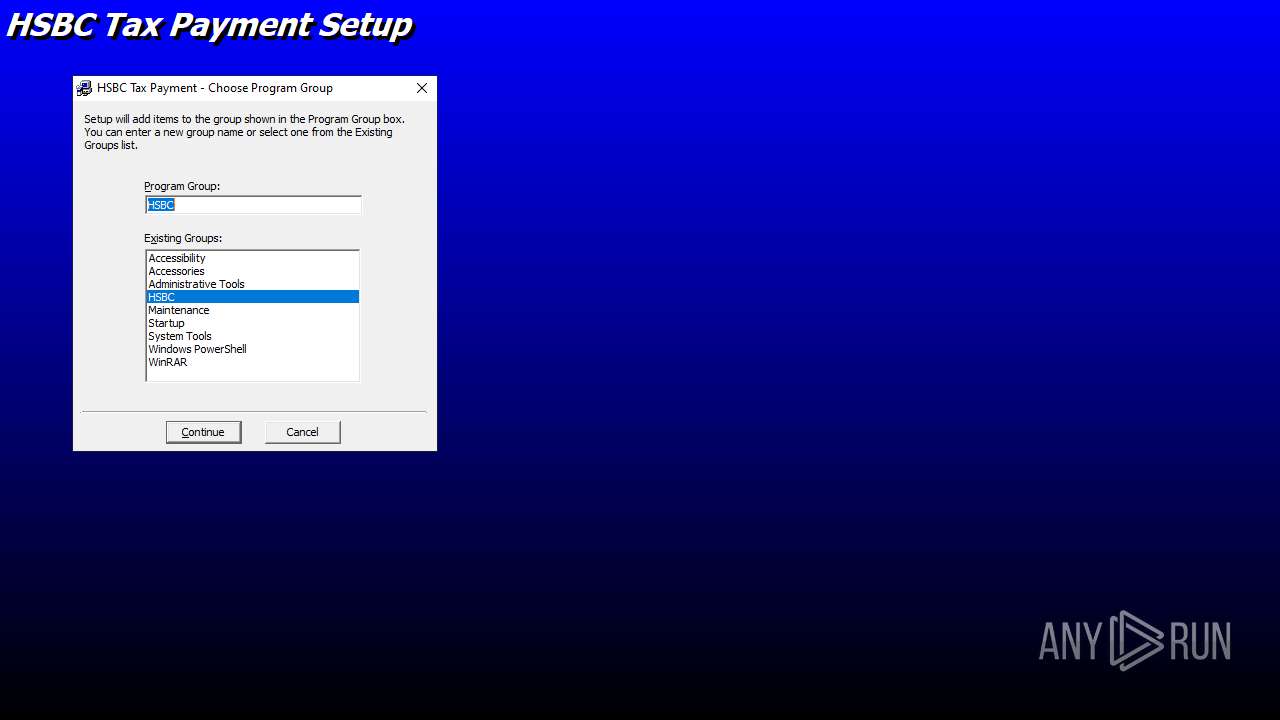
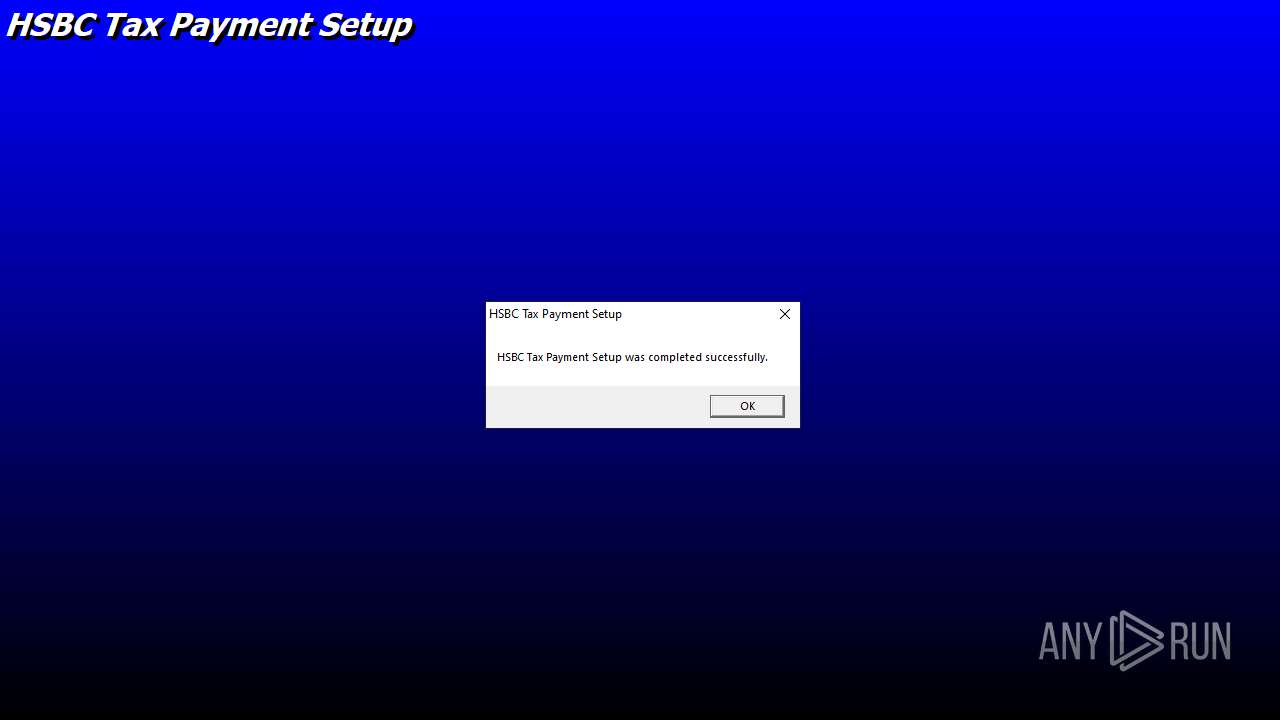
| File name: | E-Tax setup.zip |
| Full analysis: | https://app.any.run/tasks/80c0b20b-fecc-4ec2-8b73-6b2bbc0cd52a |
| Verdict: | Malicious activity |
| Analysis date: | July 02, 2025, 03:09:18 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 72C5FEF7C5F073869A7D6BEBE6C36C71 |
| SHA1: | 38B3E057DD2EA03631614D06F9B13F45DE6773F9 |
| SHA256: | 5D0C05A6CB533345F490C2B0DF0D23396417EA2BA3BCE422AD7DF1794F0334EB |
| SSDEEP: | 49152:SsDLfaR3ASZlizZUZkunWTcjY05wAE/leYMJzUDMr44JaDpsobPrKZNWbcYWYoJ4:SCLfuASjitUaunaz02AE/UYM6Mr4CaDh |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4192)
Create files in the Startup directory
- setup.exe (PID: 4920)
SUSPICIOUS
Starts a Microsoft application from unusual location
- setup.exe (PID: 3944)
- setup.exe (PID: 4920)
Process drops legitimate windows executable
- WinRAR.exe (PID: 4192)
- setup.exe (PID: 4920)
- Setup1.exe (PID: 6852)
Executable content was dropped or overwritten
- setup.exe (PID: 4920)
- Setup1.exe (PID: 6852)
Creates/Modifies COM task schedule object
- setup.exe (PID: 4920)
- Setup1.exe (PID: 6852)
Creates file in the systems drive root
- Setup1.exe (PID: 6852)
Creates a software uninstall entry
- Setup1.exe (PID: 6852)
INFO
Manual execution by a user
- setup.exe (PID: 4920)
- setup.exe (PID: 3944)
The sample compiled with english language support
- WinRAR.exe (PID: 4192)
- setup.exe (PID: 4920)
- Setup1.exe (PID: 6852)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4192)
Reads the computer name
- setup.exe (PID: 4920)
- Setup1.exe (PID: 6852)
Checks supported languages
- setup.exe (PID: 4920)
- Setup1.exe (PID: 6852)
Create files in a temporary directory
- setup.exe (PID: 4920)
- Setup1.exe (PID: 6852)
Launching a file from the Startup directory
- setup.exe (PID: 4920)
Creates files or folders in the user directory
- setup.exe (PID: 4920)
- Setup1.exe (PID: 6852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:03:04 17:13:48 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | E-Tax setup/ |
Total processes
141
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3944 | "C:\Users\admin\Desktop\setup.exe" | C:\Users\admin\Desktop\setup.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Setup Bootstrap for Visual Basic Setup Toolkit Exit code: 3221226540 Version: 6.00.8169 Modules
| |||||||||||||||
| 4024 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4192 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\E-Tax setup.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4920 | "C:\Users\admin\Desktop\setup.exe" | C:\Users\admin\Desktop\setup.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Setup Bootstrap for Visual Basic Setup Toolkit Exit code: 0 Version: 6.00.8169 Modules
| |||||||||||||||
| 6852 | Setup1.exe "C:\Users\admin\Desktop\" "C:\WINDOWS\ST6UNST.000" "C:\WINDOWS\st6unst.exe" | C:\Windows\Setup1.exe | setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual Basic 6.0 Setup Toolkit Exit code: 0 Version: 6.00.8171 Modules
| |||||||||||||||
Total events
2 743
Read events
2 626
Write events
95
Delete events
22
Modification events
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\E-Tax setup.zip | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
32
Suspicious files
5
Text files
22
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4192 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4192.8073\E-Tax setup\SETUP.LST | text | |
MD5:C505F3C252046E067407FC8B0617939D | SHA256:4AF269806D34DBD13B39B19C8F9BC28BADB4C077EBDB9C0DBD48FCA31346C060 | |||
| 4920 | setup.exe | C:\Windows\SysWOW64\temp.000 | executable | |
MD5:CFF867572B44212B01B711C1FA009537 | SHA256:DF6E2F111773ADEC3B33DCB0B31E2A4D21EF7D51740706335F411E2C999C0E6B | |||
| 4920 | setup.exe | C:\Users\admin\AppData\Local\Temp\msftqws.pdw\VB6STKIT.DLL | executable | |
MD5:CFF867572B44212B01B711C1FA009537 | SHA256:DF6E2F111773ADEC3B33DCB0B31E2A4D21EF7D51740706335F411E2C999C0E6B | |||
| 4920 | setup.exe | C:\Windows\SETUP.LST | text | |
MD5:C505F3C252046E067407FC8B0617939D | SHA256:4AF269806D34DBD13B39B19C8F9BC28BADB4C077EBDB9C0DBD48FCA31346C060 | |||
| 4192 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4192.8073\E-Tax setup\setup.exe | executable | |
MD5:35561A7ACB299A7278E8706FD6E01AA0 | SHA256:978123C86B1CBC981770FBD8BDFC58EF4030F8D9B3ADF06B71B928CC0394C073 | |||
| 4920 | setup.exe | C:\Users\admin\AppData\Local\Temp\msftqws.pdw\stdole2.tlb | executable | |
MD5:0857394E30DE11CA0CD9497E310D6469 | SHA256:E2B26B1AD2D439DDED0799D195CA918A03CCF22146690577E2704F871C098426 | |||
| 4920 | setup.exe | C:\Users\admin\AppData\Local\Temp\msftqws.pdw\MSVBVM60.DLL | executable | |
MD5:F28EB5CBC3CA6D8C787F09F047D1F9C8 | SHA256:3EF32E0152CC3FA07C417E6AADF9EAD83A17B5FDEE73799044E1BD7564725D6E | |||
| 4920 | setup.exe | C:\Windows\IFILEV~1.CAB | compressed | |
MD5:01FB885A816D1FF85EECF6A19CD3FAF8 | SHA256:5B70D0F3F45C7F37D88AFD7B01708499EA784BEB748FEBC3C4A09DDCC844A065 | |||
| 4920 | setup.exe | C:\Users\admin\AppData\Local\Temp\msftqws.pdw\olepro32.dll | executable | |
MD5:B48D3193DD1474DCBCC32BF4779AC698 | SHA256:54D7EE1E4B43D2590B3B9B4A412717BFECFCCE46F9DDA68DBA4695F135FAA7B5 | |||
| 4920 | setup.exe | C:\Users\admin\AppData\Local\Temp\msftqws.pdw\st6unst.exe | executable | |
MD5:996F83E516552CA3B51445BB994A6D38 | SHA256:7E60C894A8CEAD6880FD3ED040504D02304A0B961304E40741340E31F5FA973D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
23
DNS requests
17
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.20.245.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6492 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2716 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2716 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5528 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 2.20.245.139:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
1268 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
6492 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6492 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
Process | Message |
|---|---|
setup.exe | Close
|
setup.exe | Ending BRC |
setup.exe | Ending BRC |
setup.exe | Close
|
setup.exe | Ending BRC |
setup.exe | Close
|
setup.exe | Close
|
setup.exe | Ending BRC |
setup.exe | Close
|
setup.exe | Ending BRC |