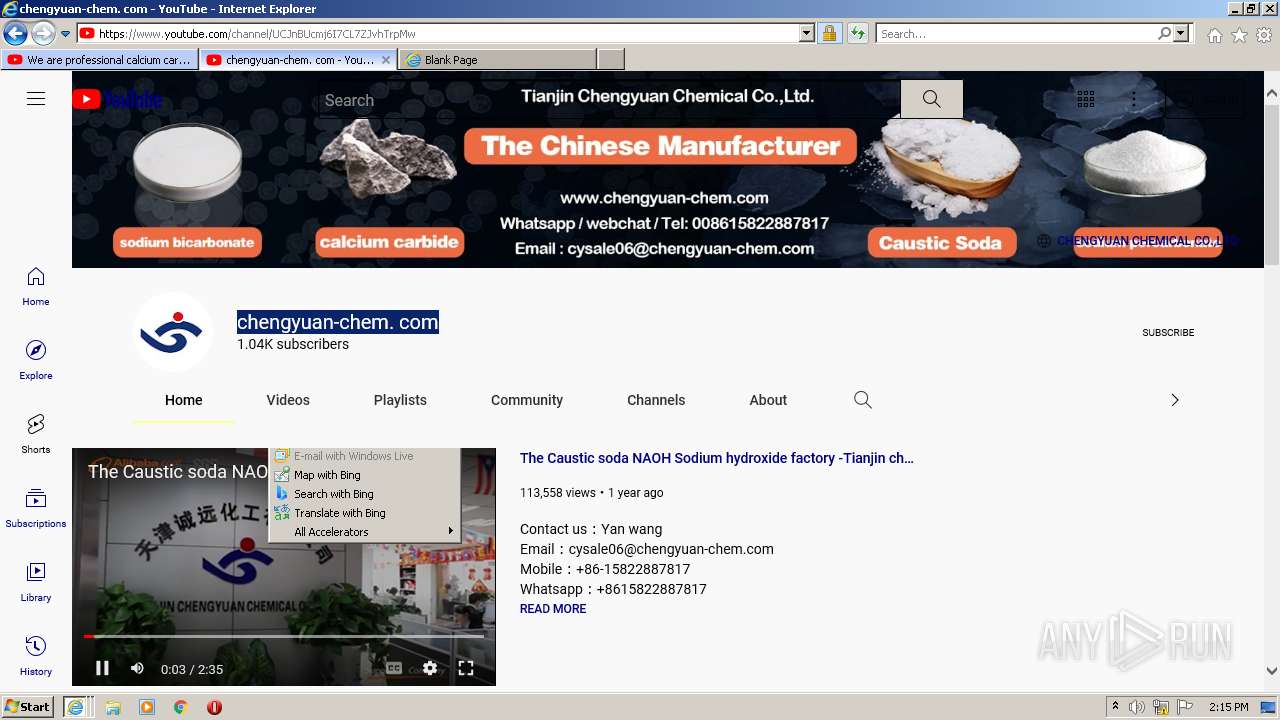
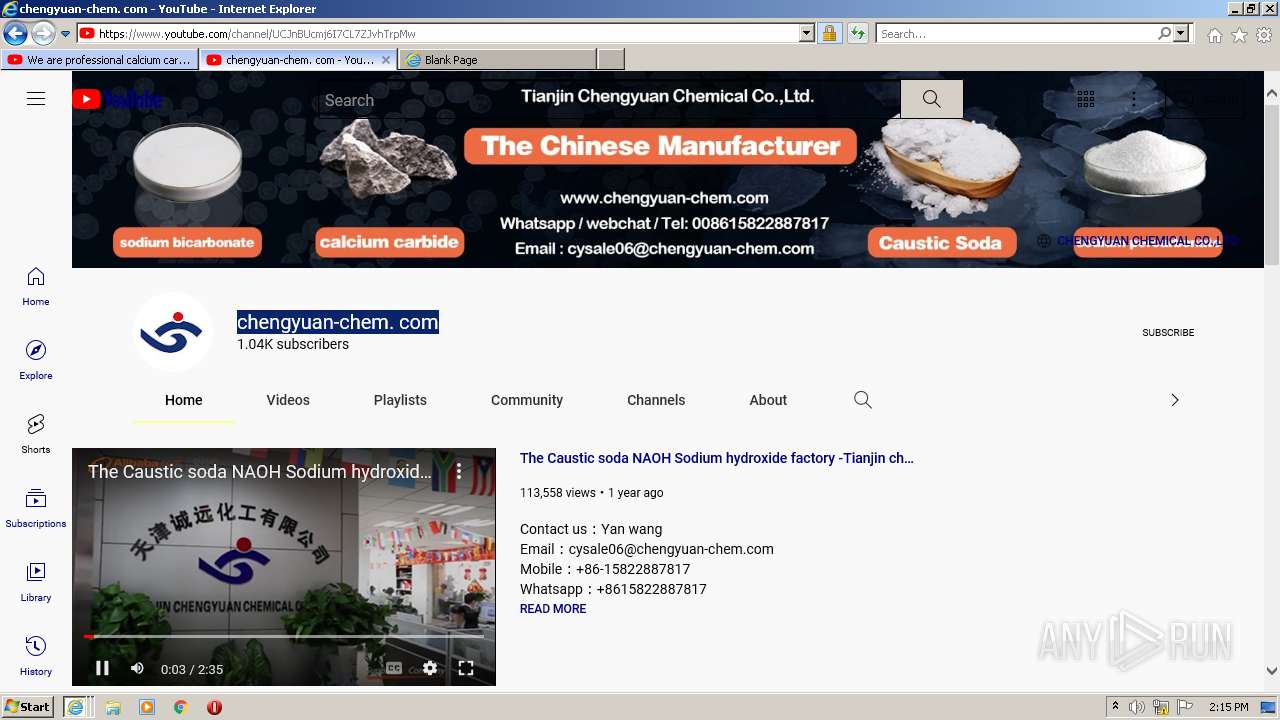
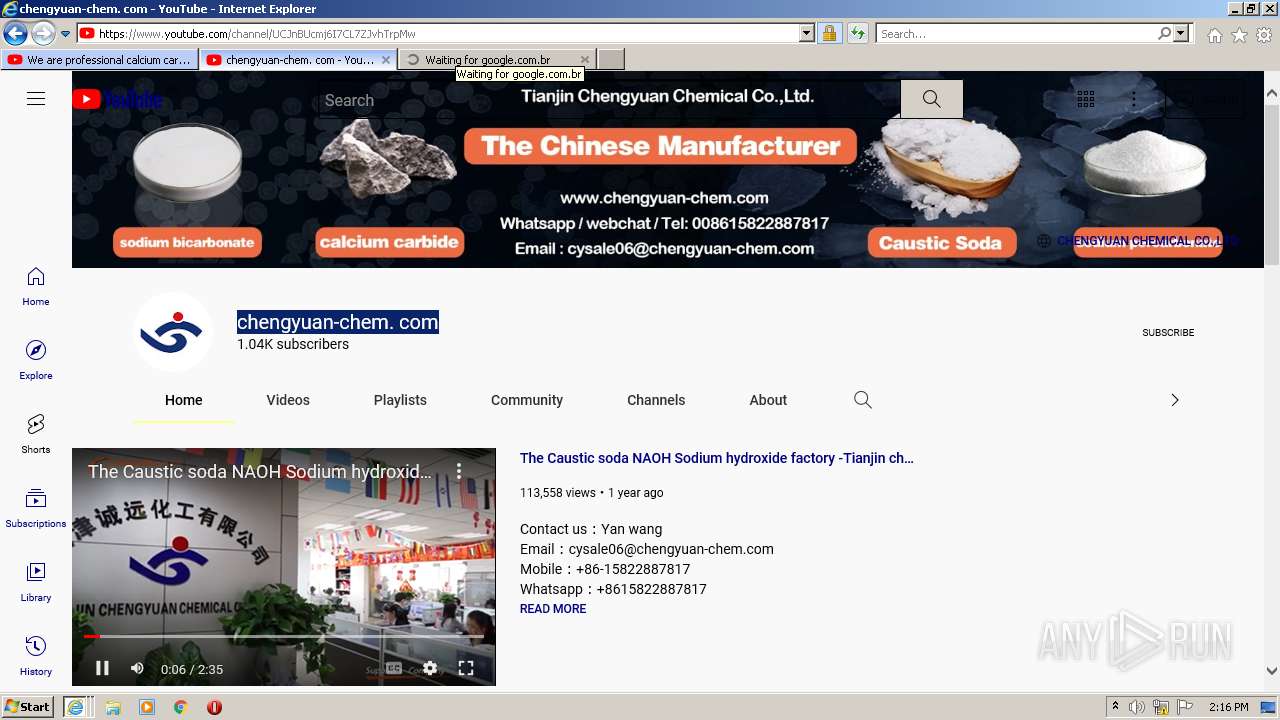
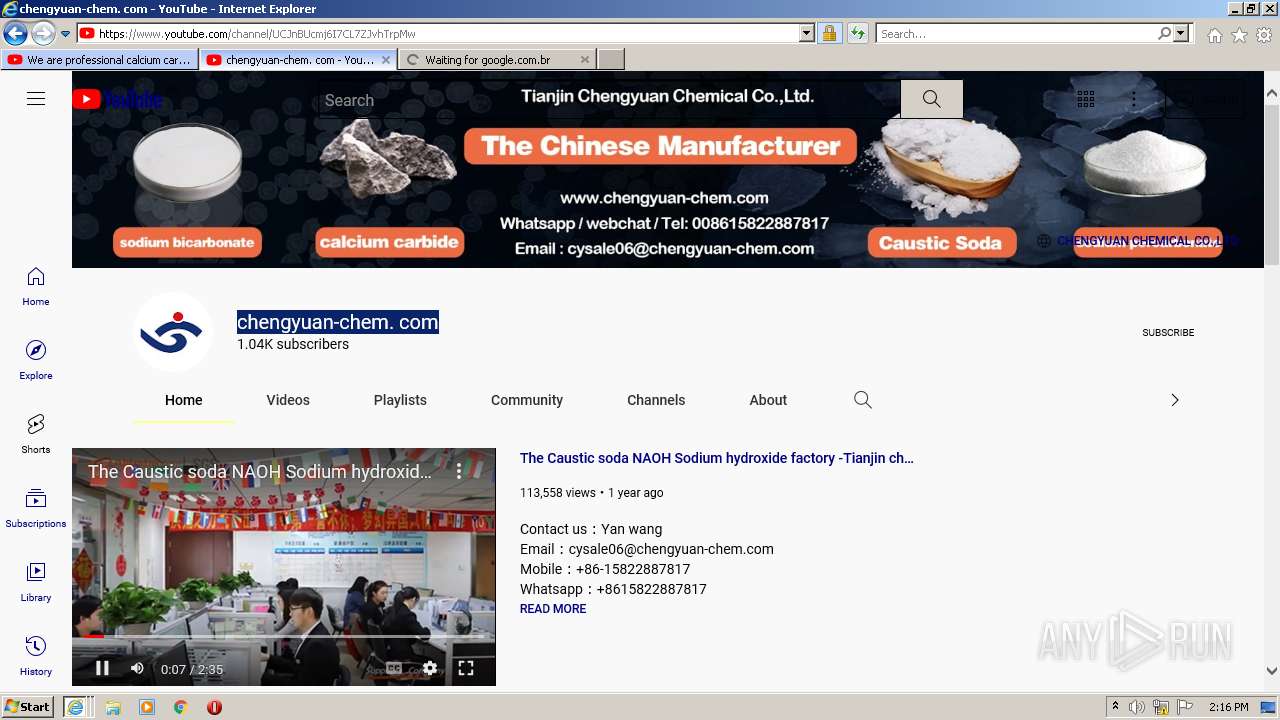
| URL: | https://www.youtube.com/embed/2A_B4Uw80AA |
| Full analysis: | https://app.any.run/tasks/b4b9b9d5-7a3a-4b26-b0b1-07625305fcfb |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 13:12:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | DC2374D0E3158C6BA552B93DA7E682B8 |
| SHA1: | CC2C27F33CFA12FE8082D03DB63B25597A6A6F7B |
| SHA256: | 5CD4A77371D2ED86B9A54E61B7278F453754FFB92F79FD9496CFA1D92159468B |
| SSDEEP: | 3:N8DSLUxGTKASlwat:2OLUxGXS5t |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2800)
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 2840)
- iexplore.exe (PID: 2740)
Executed via COM
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 1060)
Creates files in the user directory
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 1060)
Checks supported languages
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 1060)
Reads the computer name
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 1060)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2368)
INFO
Reads the computer name
- iexplore.exe (PID: 2840)
- iexplore.exe (PID: 2800)
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 2740)
- chrome.exe (PID: 2368)
- chrome.exe (PID: 3304)
- chrome.exe (PID: 2172)
- chrome.exe (PID: 2724)
- chrome.exe (PID: 3792)
- chrome.exe (PID: 3788)
Application launched itself
- iexplore.exe (PID: 2840)
- chrome.exe (PID: 2368)
Checks supported languages
- iexplore.exe (PID: 2800)
- iexplore.exe (PID: 2840)
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 2740)
- chrome.exe (PID: 2368)
- chrome.exe (PID: 2580)
- chrome.exe (PID: 3304)
- chrome.exe (PID: 1564)
- chrome.exe (PID: 2724)
- chrome.exe (PID: 3944)
- chrome.exe (PID: 2172)
- chrome.exe (PID: 2592)
- chrome.exe (PID: 2852)
- chrome.exe (PID: 2284)
- chrome.exe (PID: 4024)
- chrome.exe (PID: 3440)
- chrome.exe (PID: 2696)
- chrome.exe (PID: 3532)
- chrome.exe (PID: 3792)
- chrome.exe (PID: 1544)
- chrome.exe (PID: 2456)
- chrome.exe (PID: 2548)
- chrome.exe (PID: 4072)
- chrome.exe (PID: 3788)
Checks Windows Trust Settings
- iexplore.exe (PID: 2840)
- iexplore.exe (PID: 2800)
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 2740)
Creates files in the user directory
- iexplore.exe (PID: 2800)
- iexplore.exe (PID: 2840)
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 2740)
Changes internet zones settings
- iexplore.exe (PID: 2840)
Reads settings of System Certificates
- iexplore.exe (PID: 2840)
- iexplore.exe (PID: 2800)
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 2740)
- chrome.exe (PID: 2172)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2840)
Reads internet explorer settings
- iexplore.exe (PID: 2800)
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 2740)
Changes settings of System certificates
- iexplore.exe (PID: 2840)
Manual execution by user
- chrome.exe (PID: 2368)
Reads CPU info
- iexplore.exe (PID: 2800)
Reads the hosts file
- chrome.exe (PID: 2368)
- chrome.exe (PID: 2172)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
63
Monitored processes
25
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1060 | C:\Windows\system32\Macromed\Flash\FlashUtil32_32_0_0_453_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_32_0_0_453_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 32.0 r0 Exit code: 0 Version: 32,0,0,453 Modules
| |||||||||||||||
| 1544 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1056,5539533456698133347,3067650102148422278,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2040 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1564 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1056,5539533456698133347,3067650102148422278,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2952 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2172 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1056,5539533456698133347,3067650102148422278,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1308 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2284 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1056,5539533456698133347,3067650102148422278,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2824 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2368 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | Explorer.EXE | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2456 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1056,5539533456698133347,3067650102148422278,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3232 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2548 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1056,5539533456698133347,3067650102148422278,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2032 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2580 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=86.0.4240.198 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6aacd988,0x6aacd998,0x6aacd9a4 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2592 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1056,5539533456698133347,3067650102148422278,131072 --enable-features=PasswordImport --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2328 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
37 902
Read events
37 210
Write events
687
Delete events
5
Modification events
| (PID) Process: | (2840) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2840) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2840) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30968359 | |||
| (PID) Process: | (2840) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2840) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30968359 | |||
| (PID) Process: | (2840) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2840) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2840) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2840) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2840) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
191
Text files
329
Unknown types
50
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2840 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2840 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:— | SHA256:— | |||
| 2800 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\646C991C2A28825F3CC56E0A1D1E3FA9 | der | |
MD5:— | SHA256:— | |||
| 2800 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\265C0DEB29181DD1891051371C5F863A_C668445AACCF7A560A7B569C97BA4550 | der | |
MD5:— | SHA256:— | |||
| 2840 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 2840 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | der | |
MD5:— | SHA256:— | |||
| 2800 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | der | |
MD5:— | SHA256:— | |||
| 2800 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\646C991C2A28825F3CC56E0A1D1E3FA9 | binary | |
MD5:— | SHA256:— | |||
| 2800 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\1G2JFQWX.txt | text | |
MD5:— | SHA256:— | |||
| 2800 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\P1LBFZ1G.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
211
DNS requests
80
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2800 | iexplore.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCED8LL4LoNrATCuVyHZQ7qcY%3D | US | der | 471 b | whitelisted |
2800 | iexplore.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEG8ah82mu6j%2FCizjSGtvLoA%3D | US | der | 471 b | whitelisted |
2800 | iexplore.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCLB04PS9az5Ap1Zaaccy%2F9 | US | der | 472 b | whitelisted |
2800 | iexplore.exe | GET | 200 | 142.250.185.227:80 | http://crl.pki.goog/gsr1/gsr1.crl | US | der | 1.61 Kb | whitelisted |
2840 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
2800 | iexplore.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEFis5ZQLQXhkEp1TGjnLAGc%3D | US | der | 471 b | whitelisted |
3040 | iexplore.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDNqcm0ttxULAoGqTwy8PoU | US | der | 472 b | whitelisted |
2800 | iexplore.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEESz3%2FmlG2yGCtBzjzp1dVc%3D | US | der | 471 b | whitelisted |
2800 | iexplore.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCLB04PS9az5Ap1Zaaccy%2F9 | US | der | 472 b | whitelisted |
2800 | iexplore.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCqm%2FLZVwk%2FcRLv5CtSZANu | US | der | 472 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
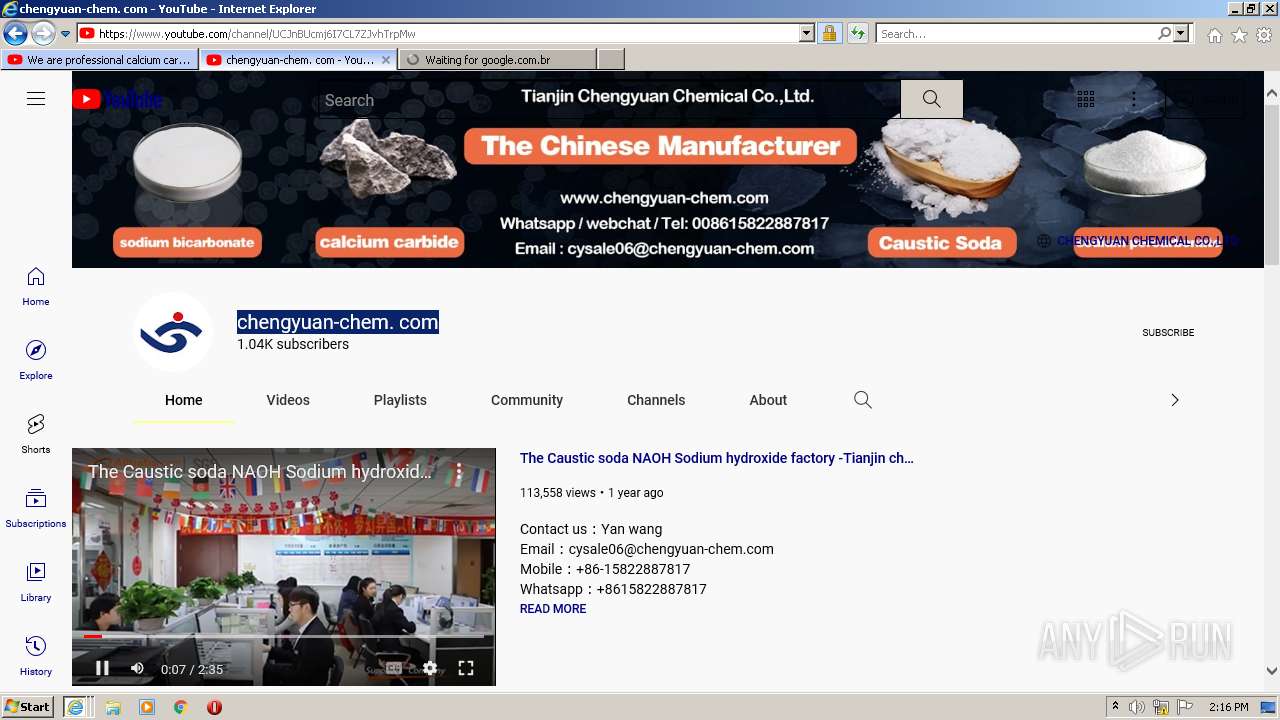
2800 | iexplore.exe | 142.250.181.238:443 | www.youtube.com | Google Inc. | US | whitelisted |
2840 | iexplore.exe | 13.107.22.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
— | — | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
2800 | iexplore.exe | 142.250.185.238:443 | www.youtube.com | Google Inc. | US | whitelisted |
2800 | iexplore.exe | 142.250.186.163:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
— | — | 142.250.185.238:443 | www.youtube.com | Google Inc. | US | whitelisted |
2800 | iexplore.exe | 172.217.18.98:443 | googleads.g.doubleclick.net | Google Inc. | US | whitelisted |
2800 | iexplore.exe | 142.250.185.99:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
2840 | iexplore.exe | 67.26.161.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
2800 | iexplore.exe | 142.250.184.202:443 | jnn-pa.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.youtube.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
crl.pki.goog |
| whitelisted |
googleads.g.doubleclick.net |
| whitelisted |