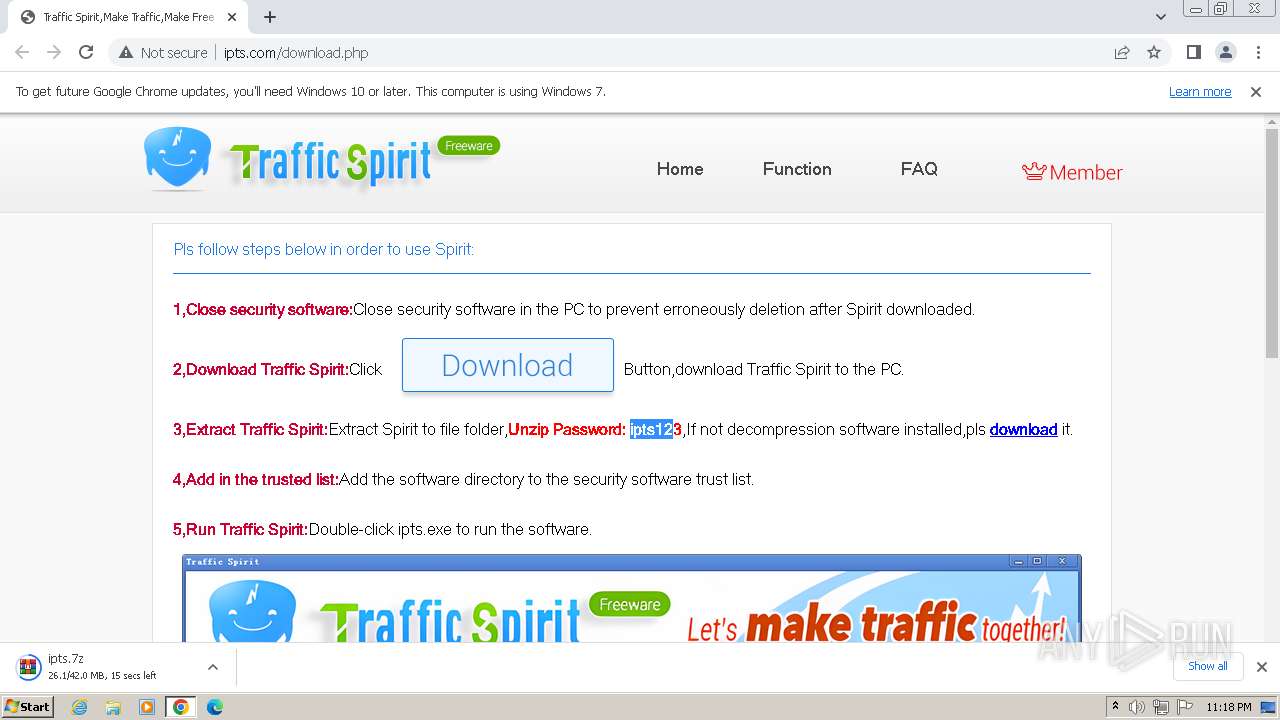
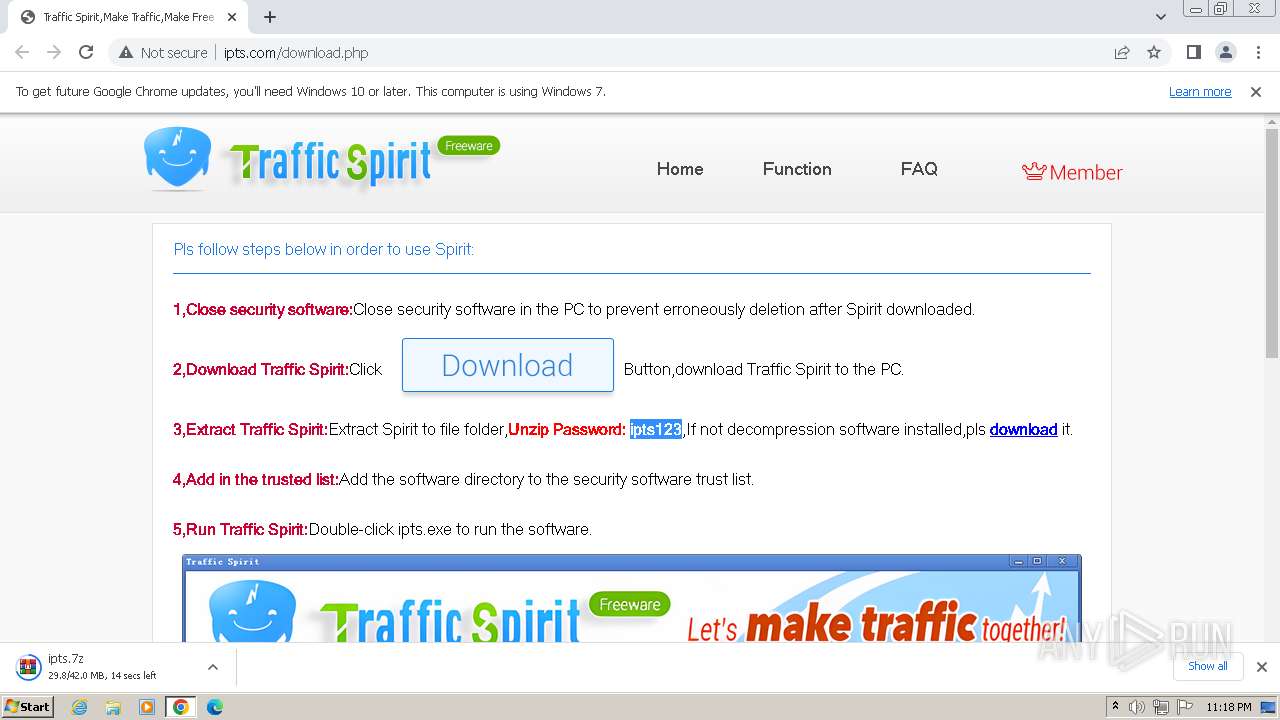
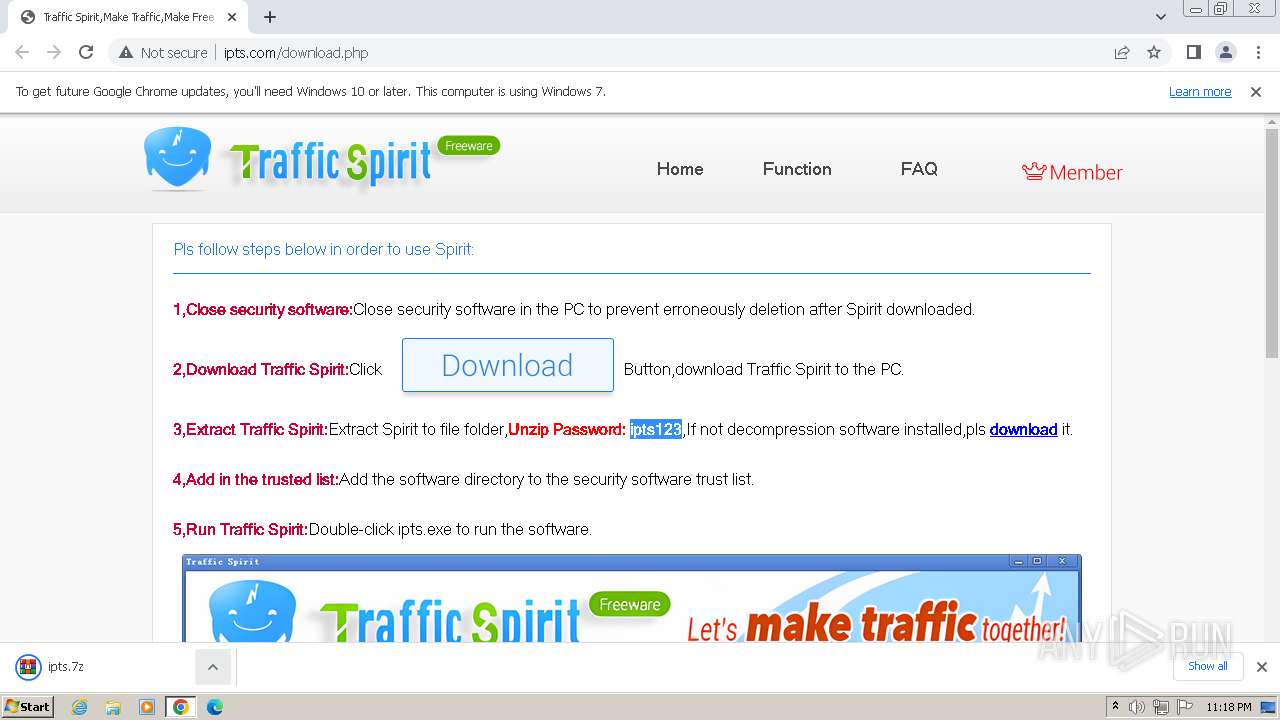
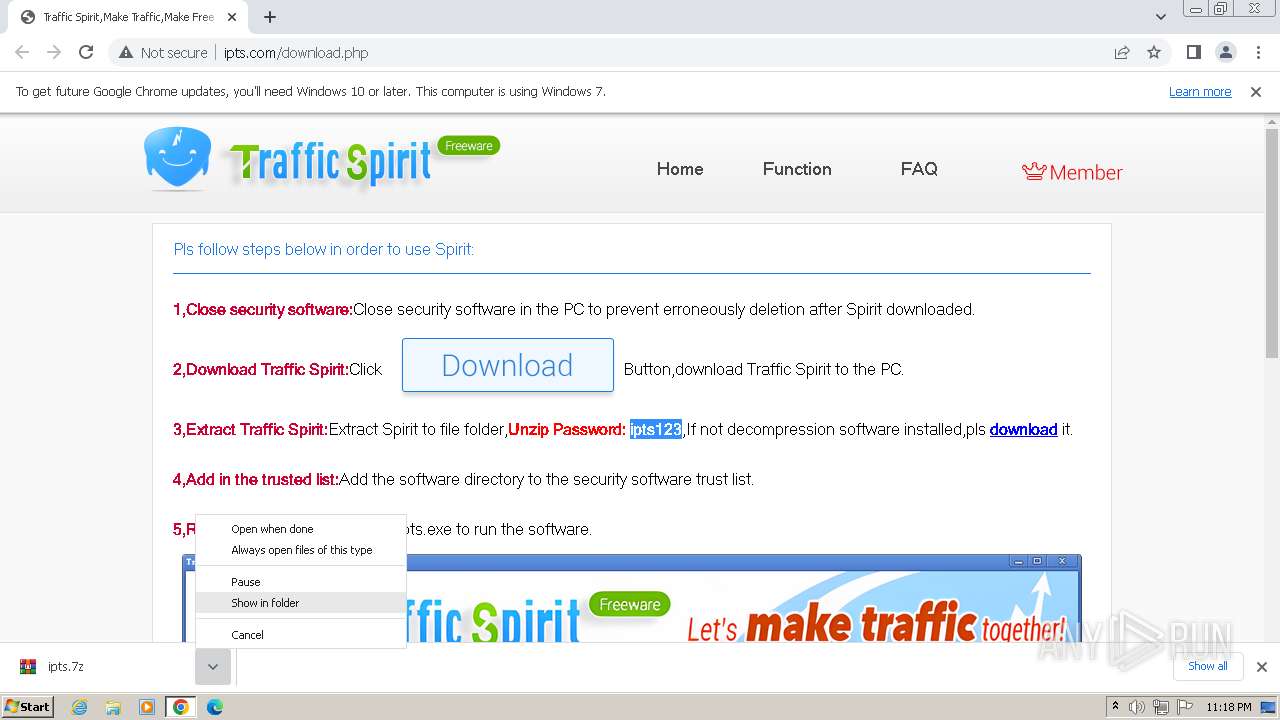
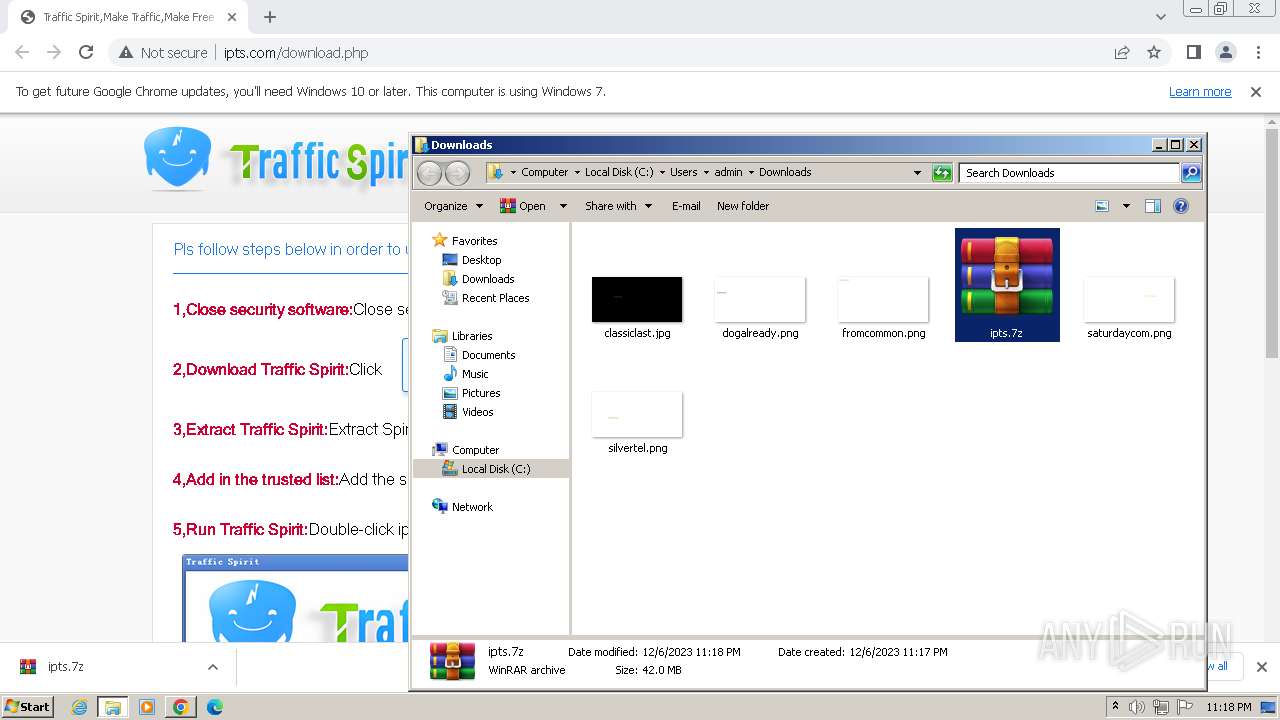
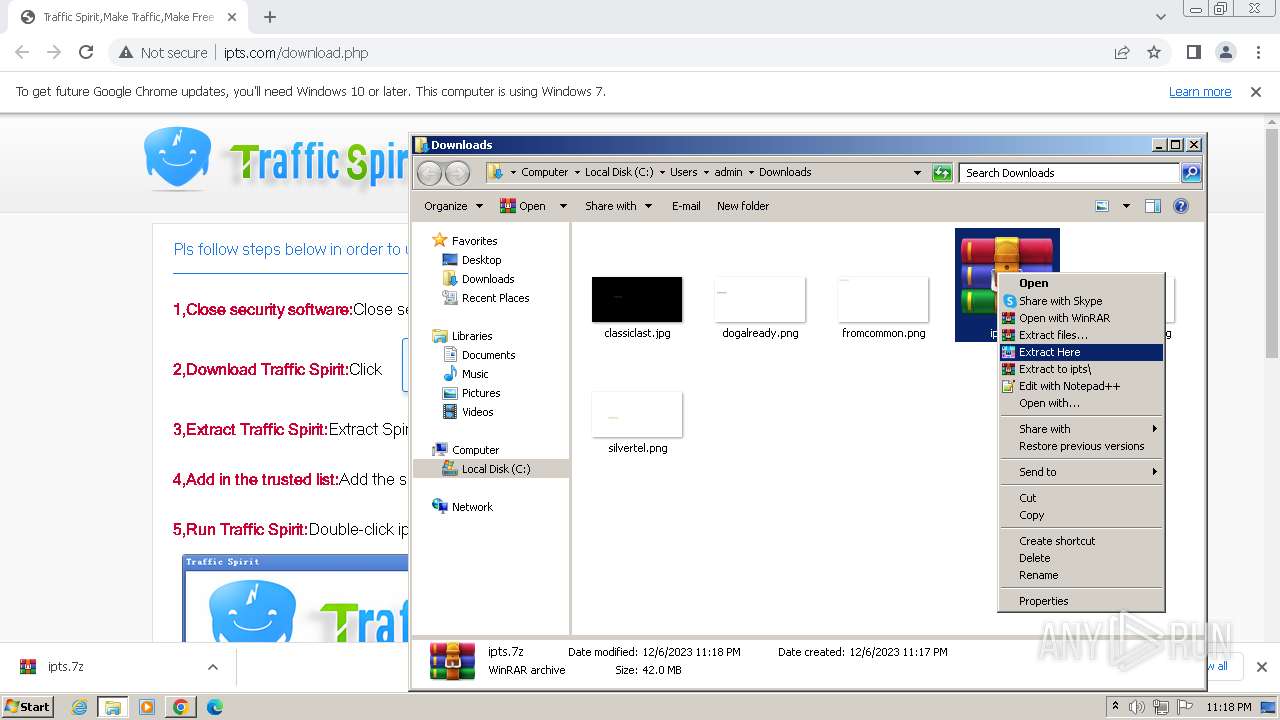
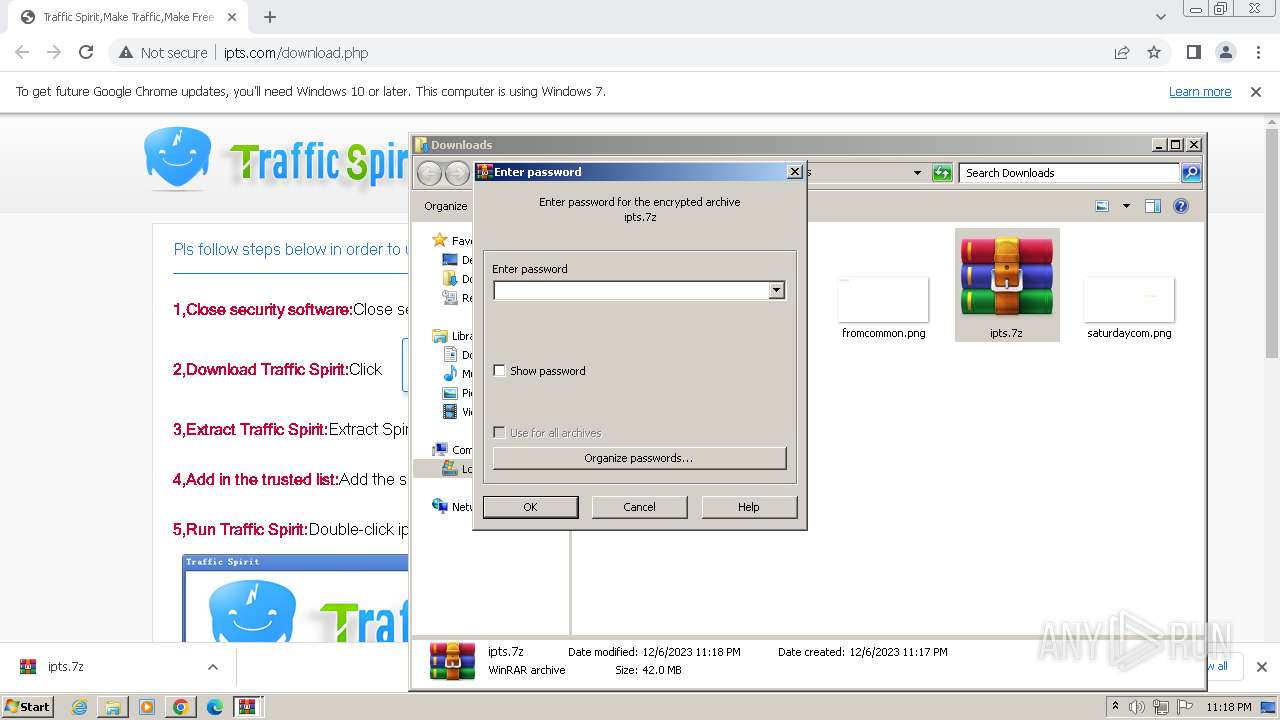
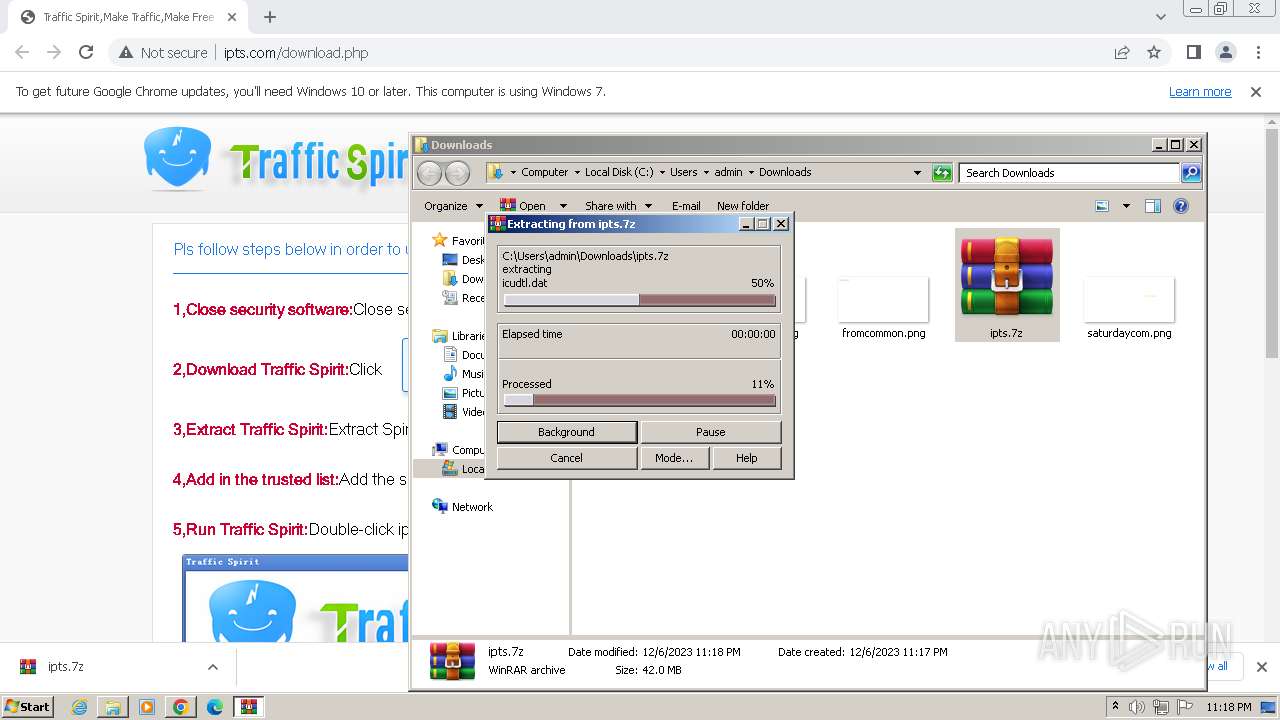
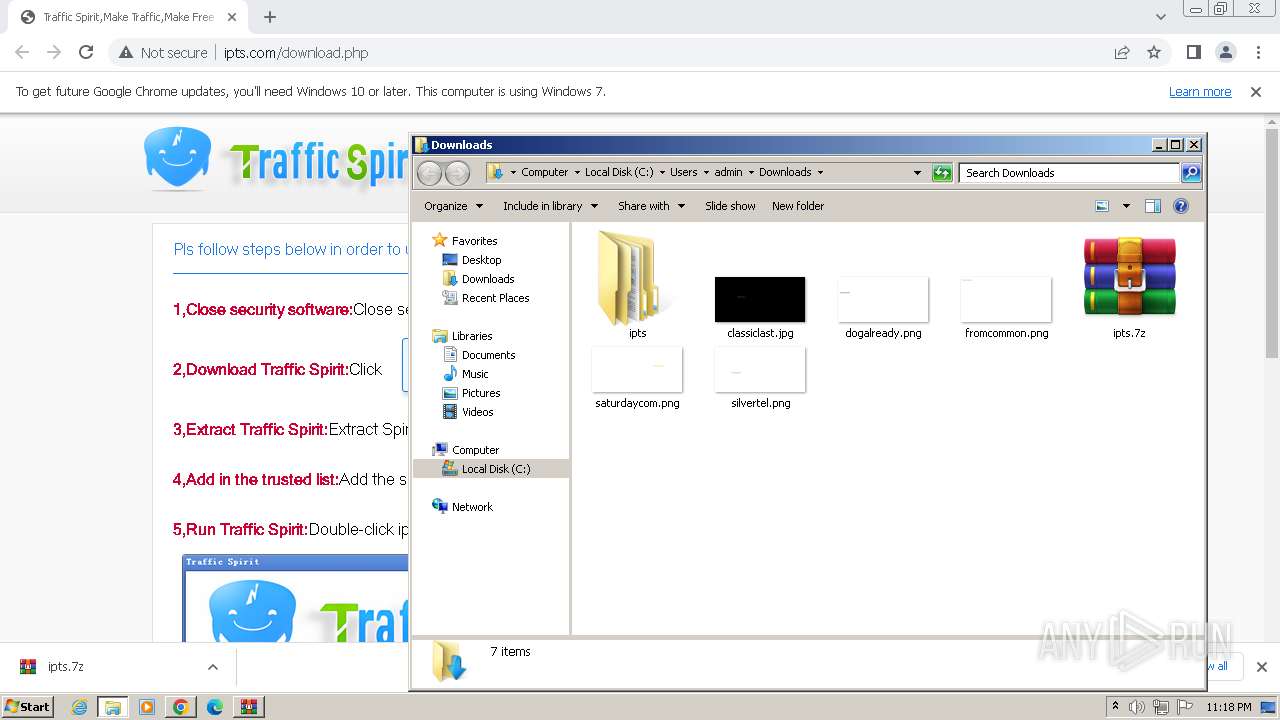
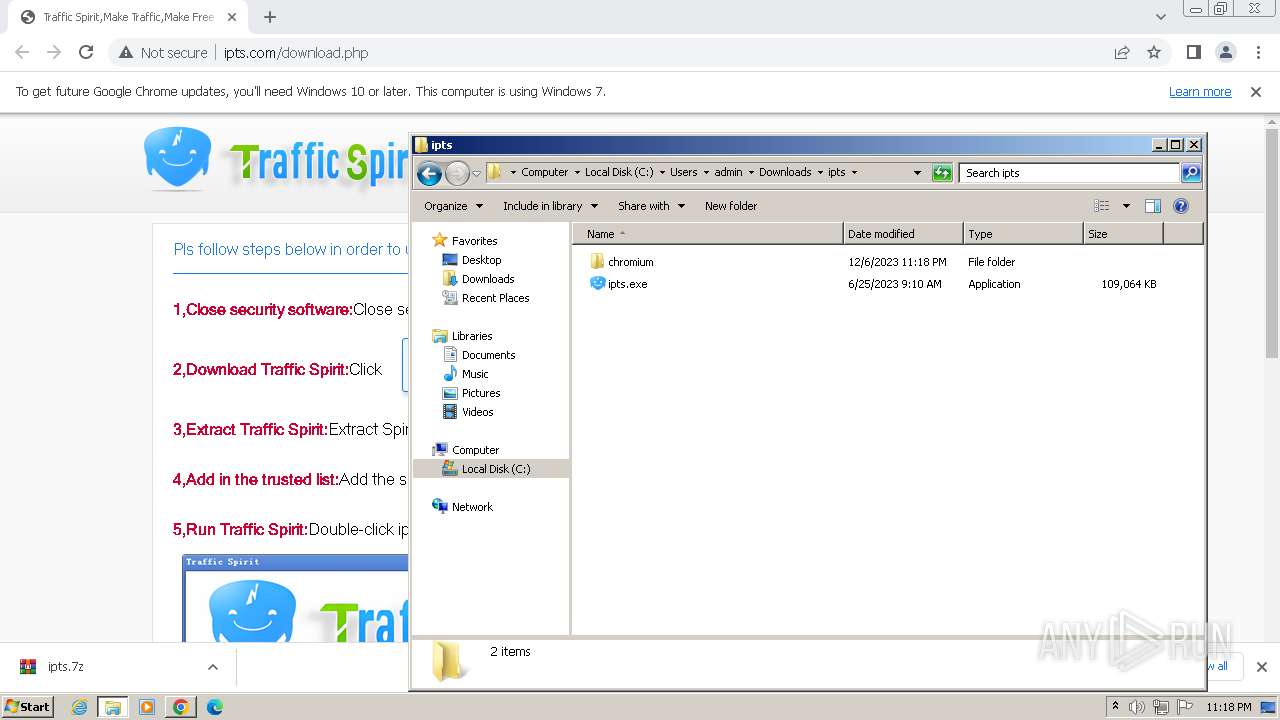
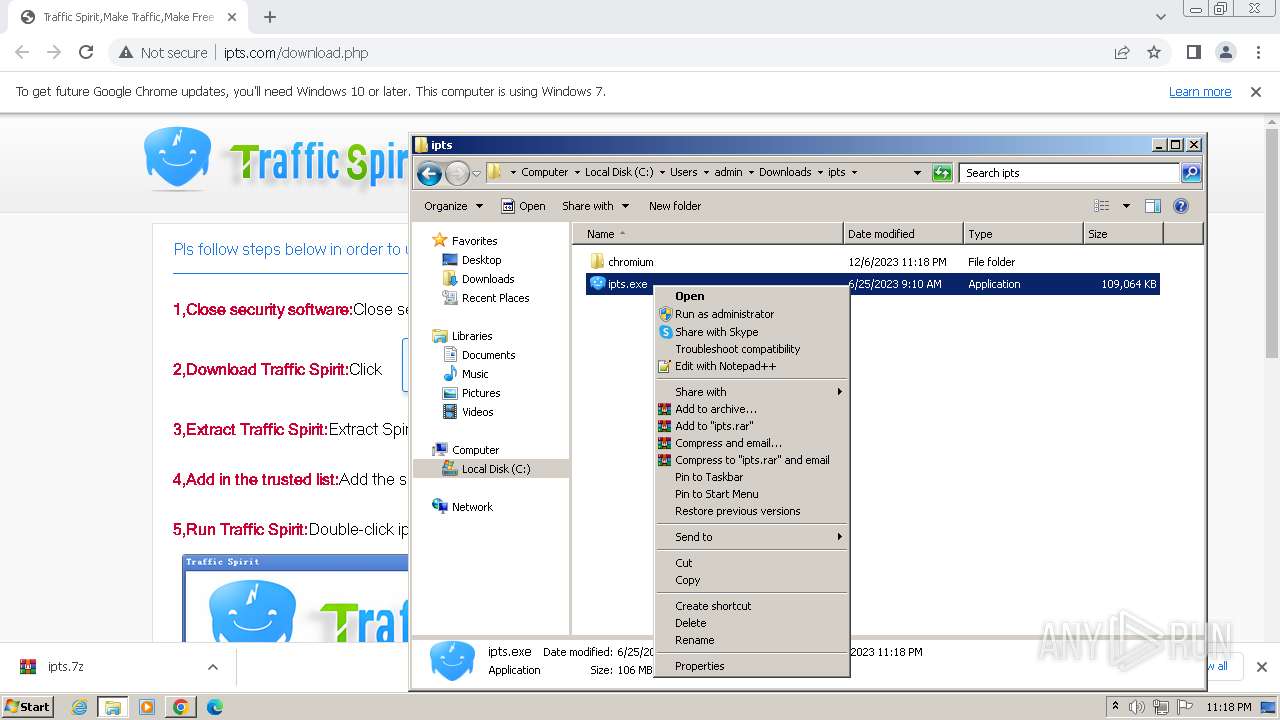
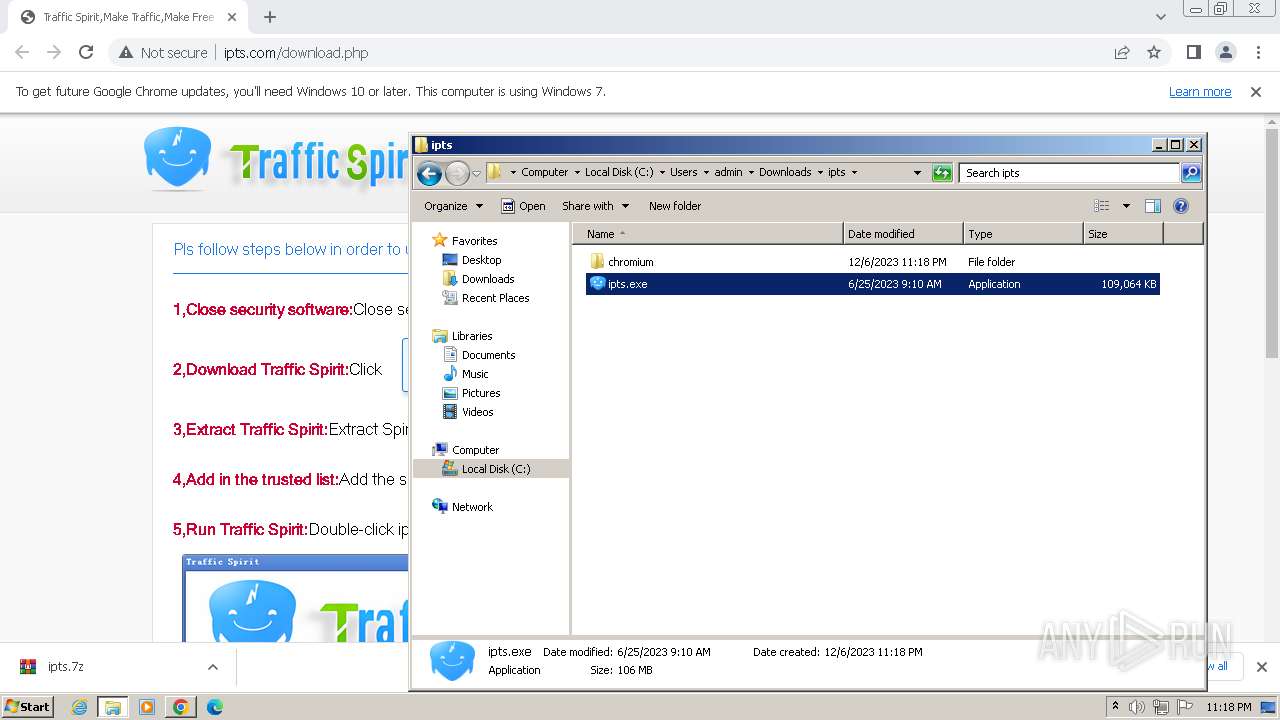
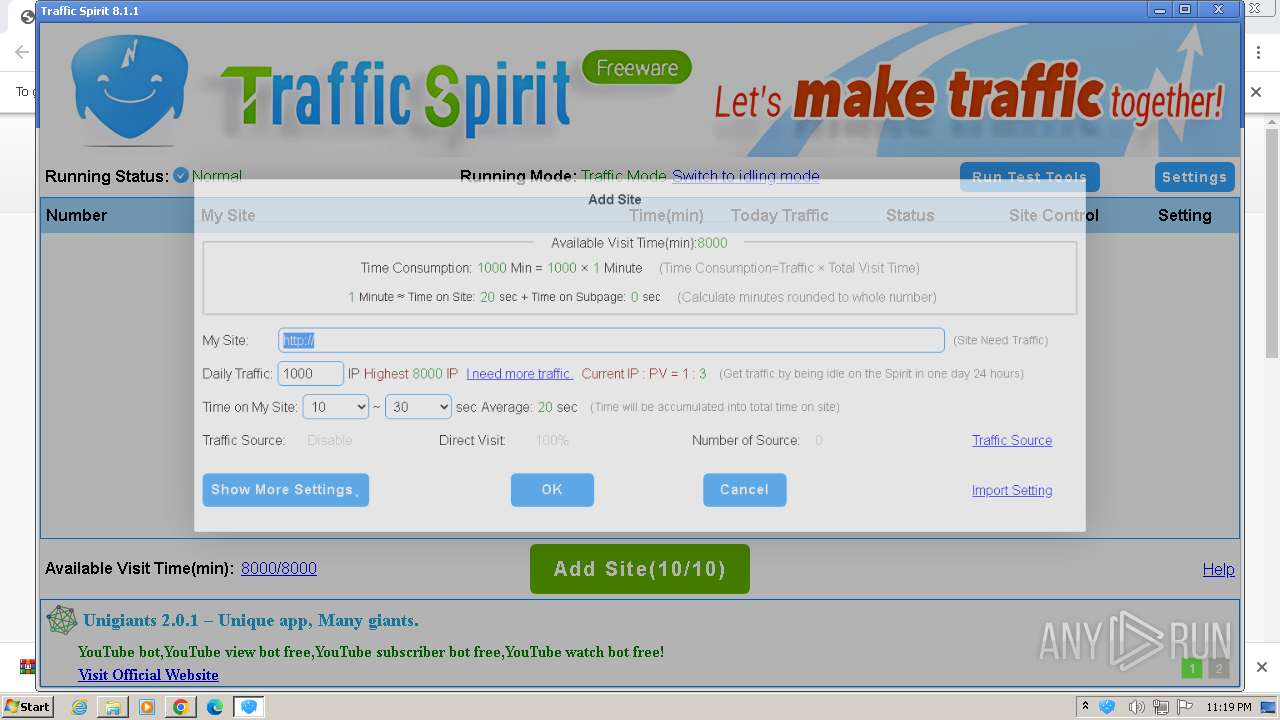
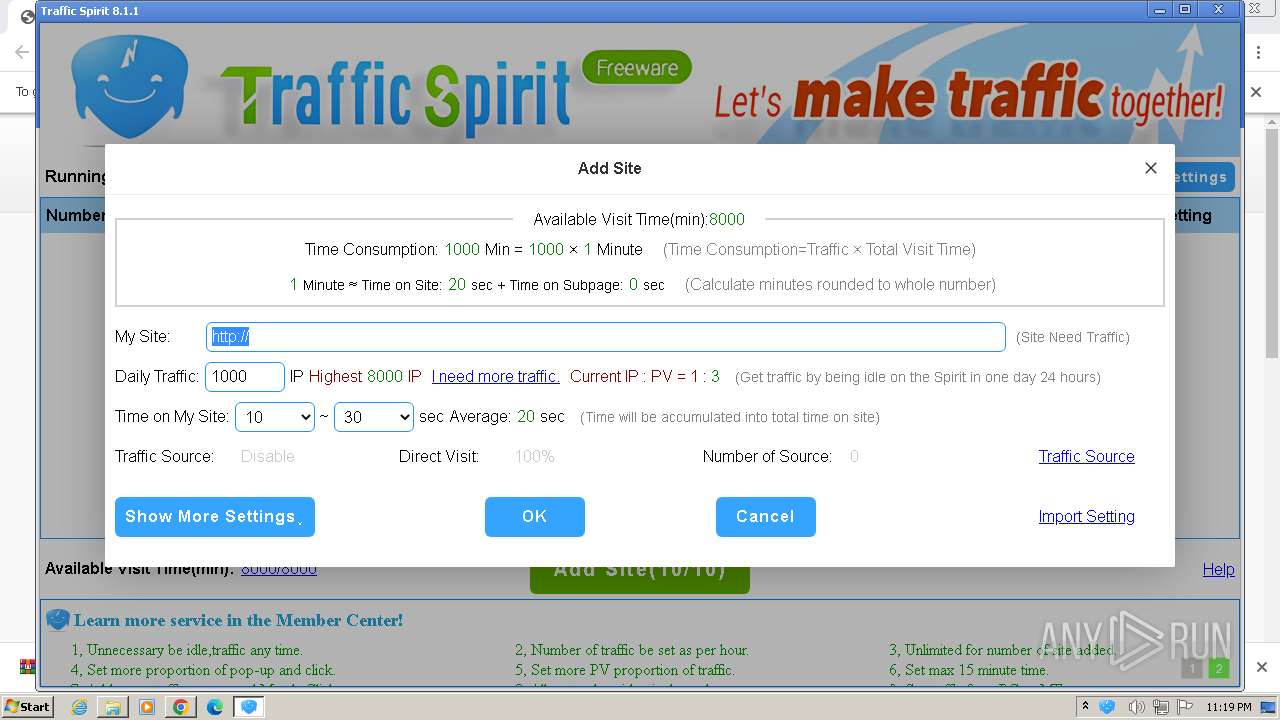
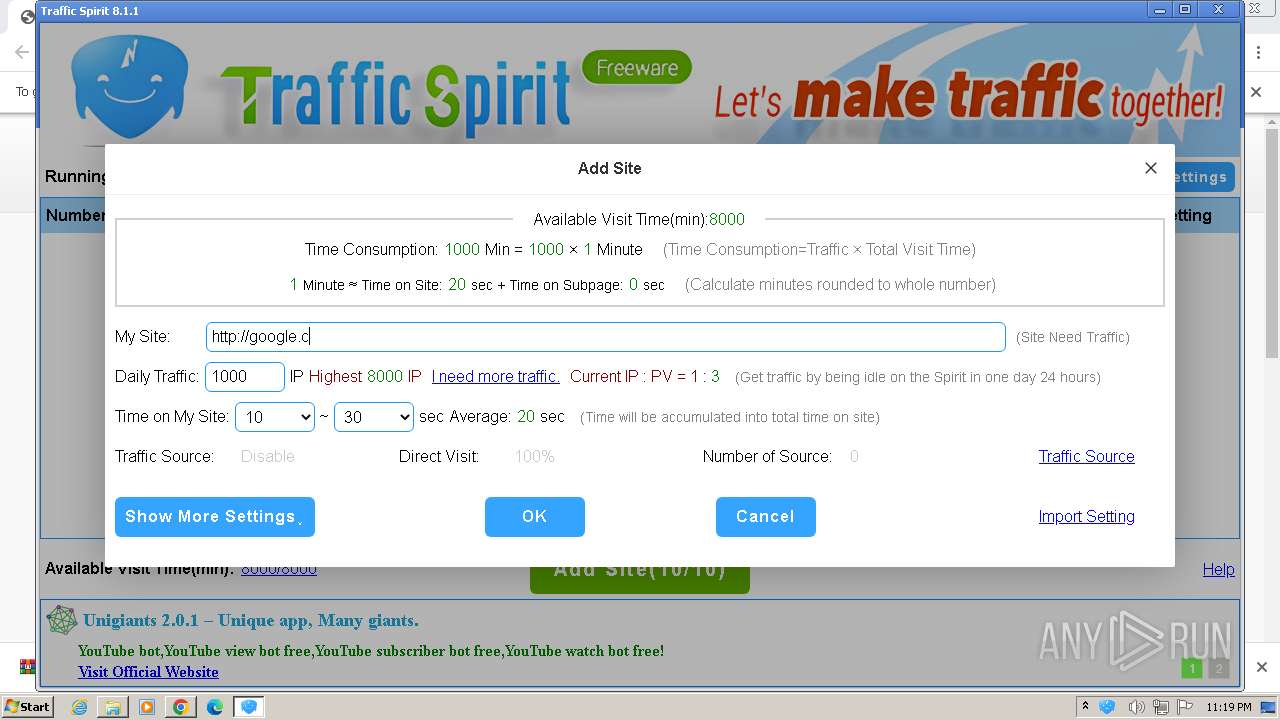
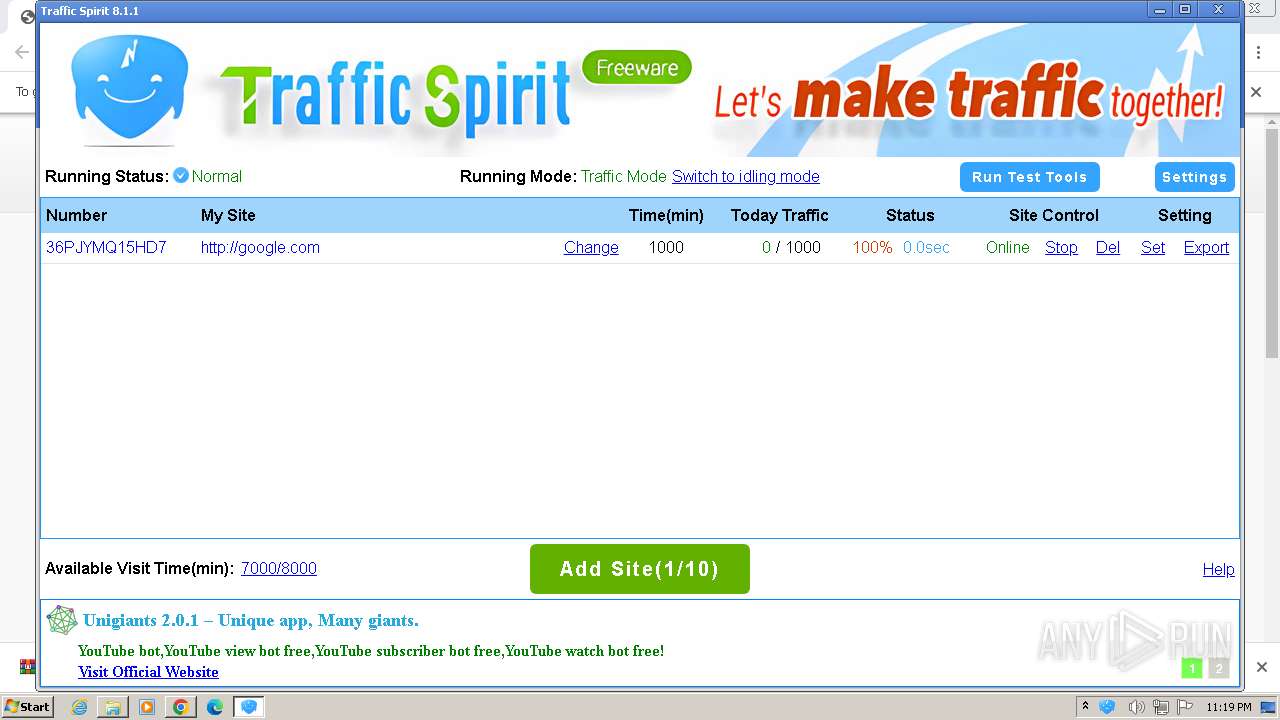
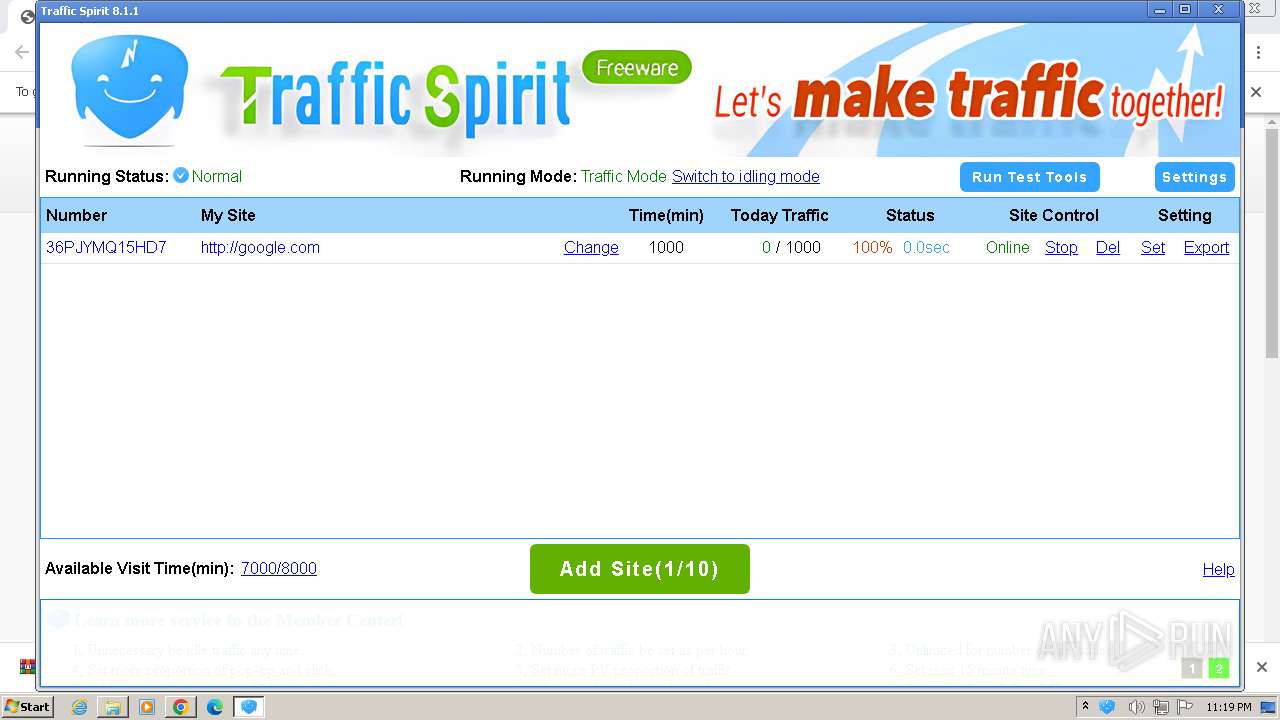
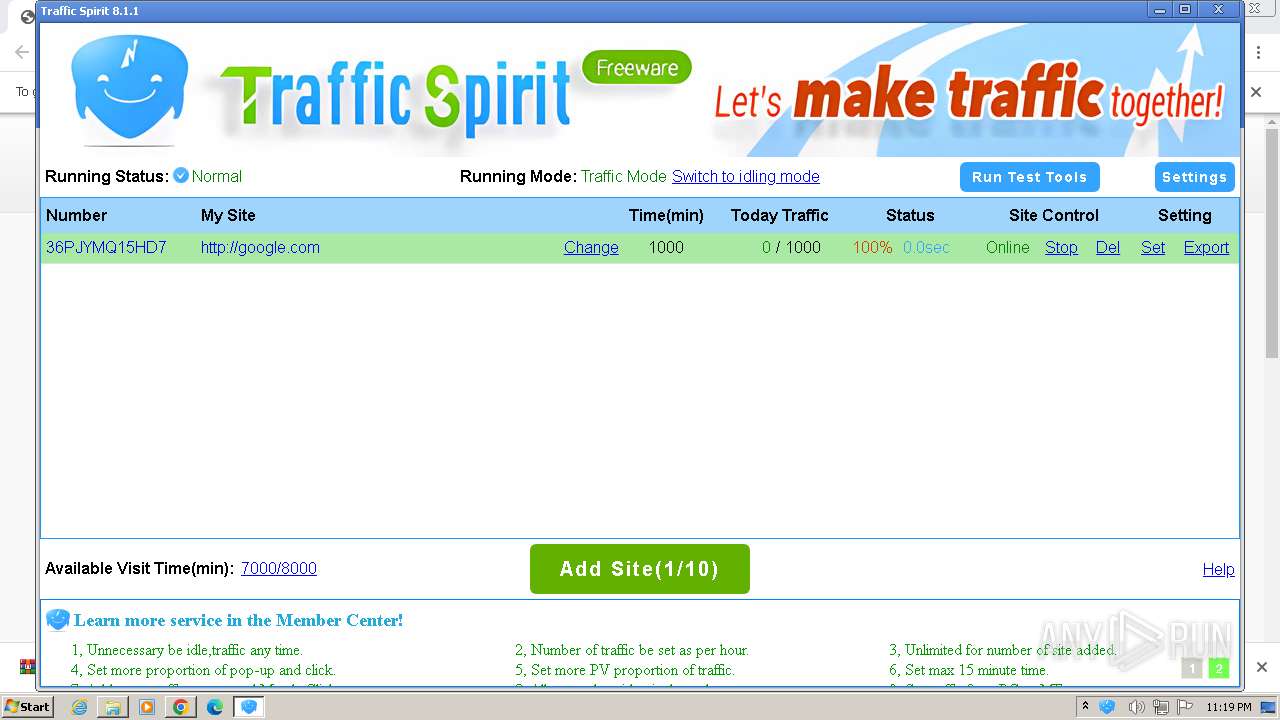
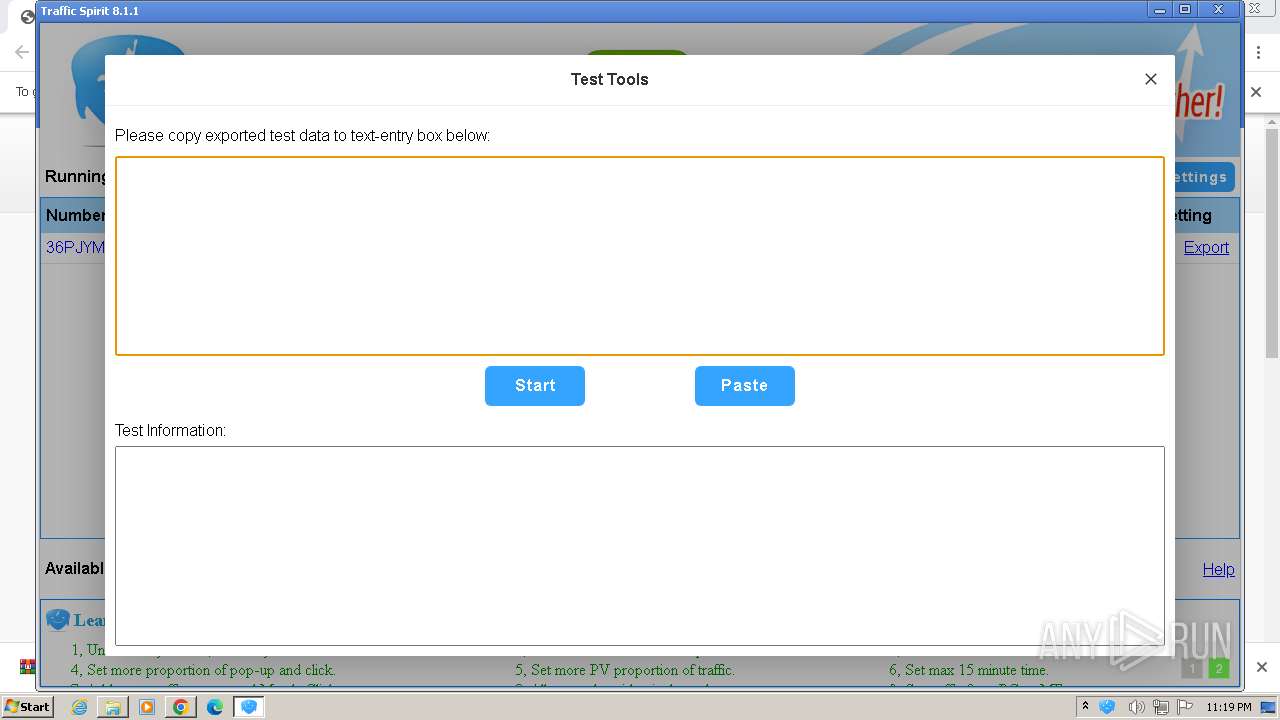
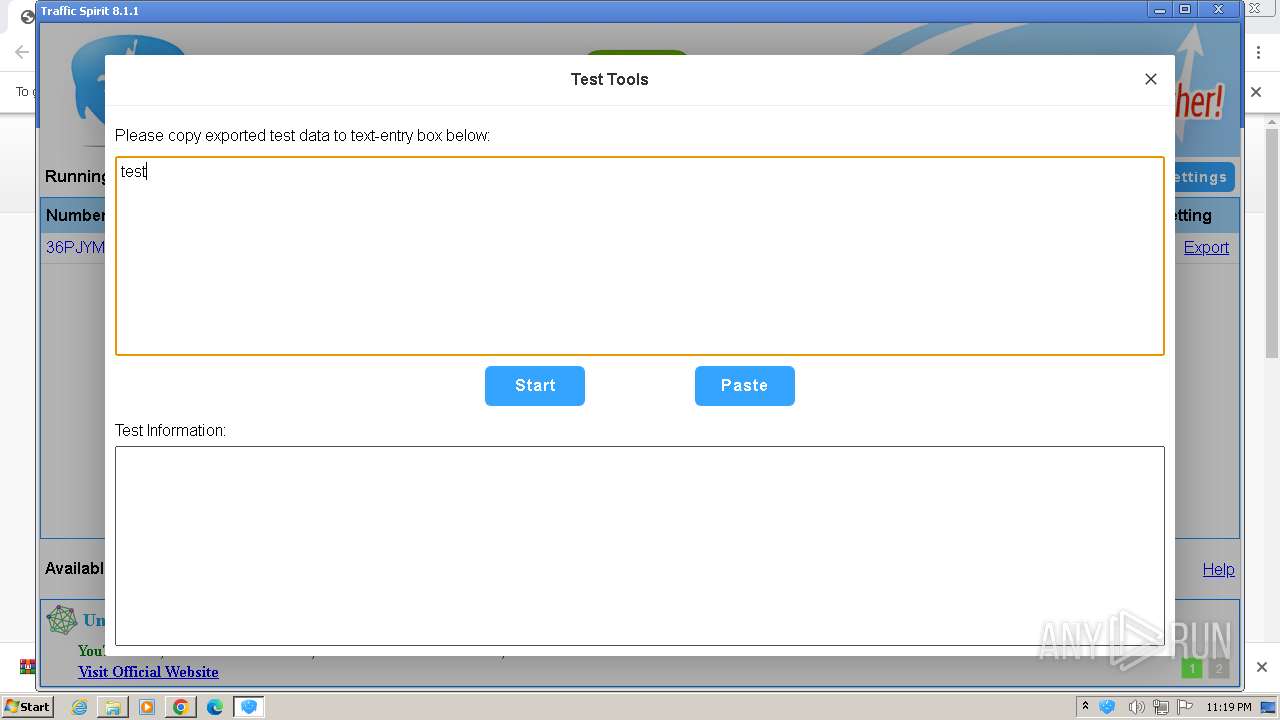
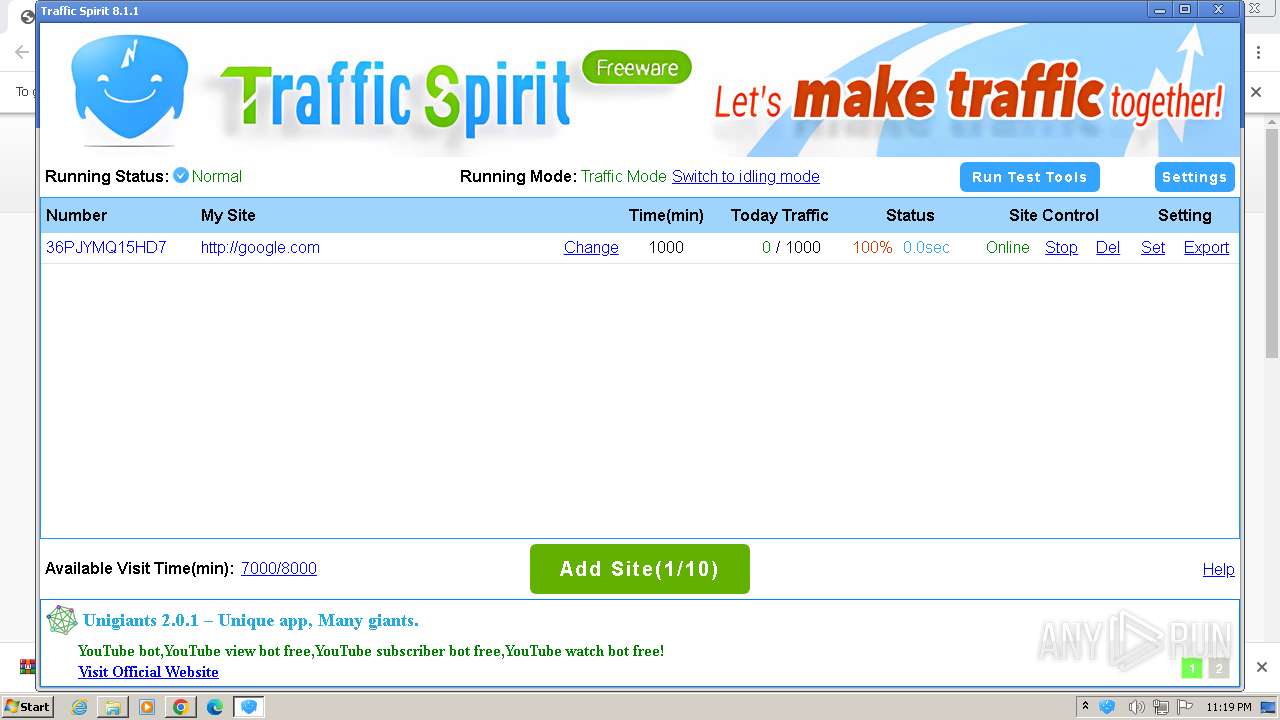
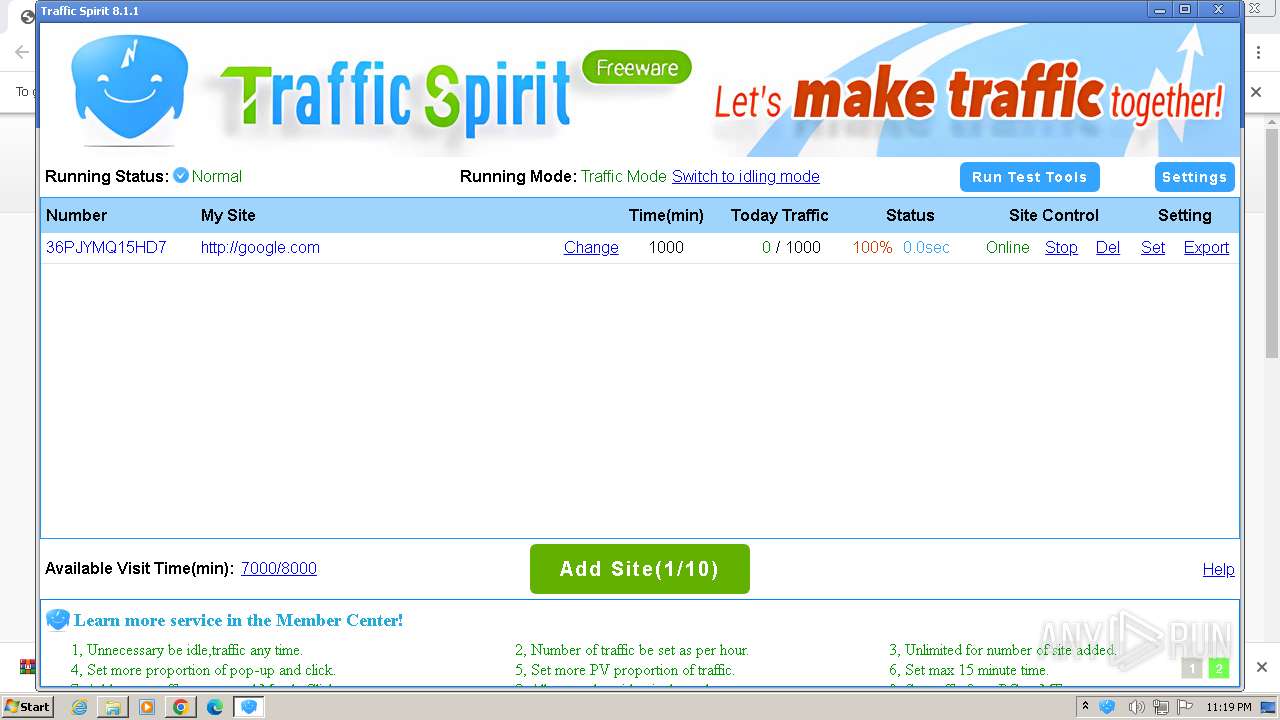
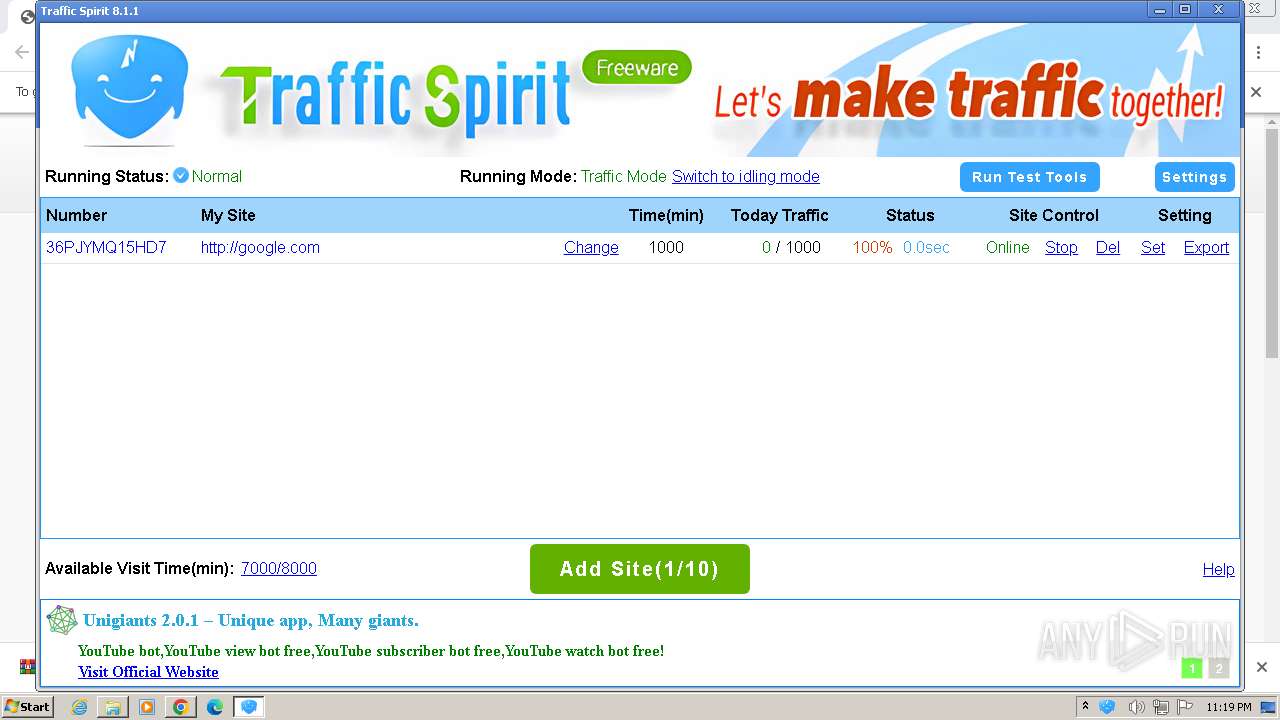
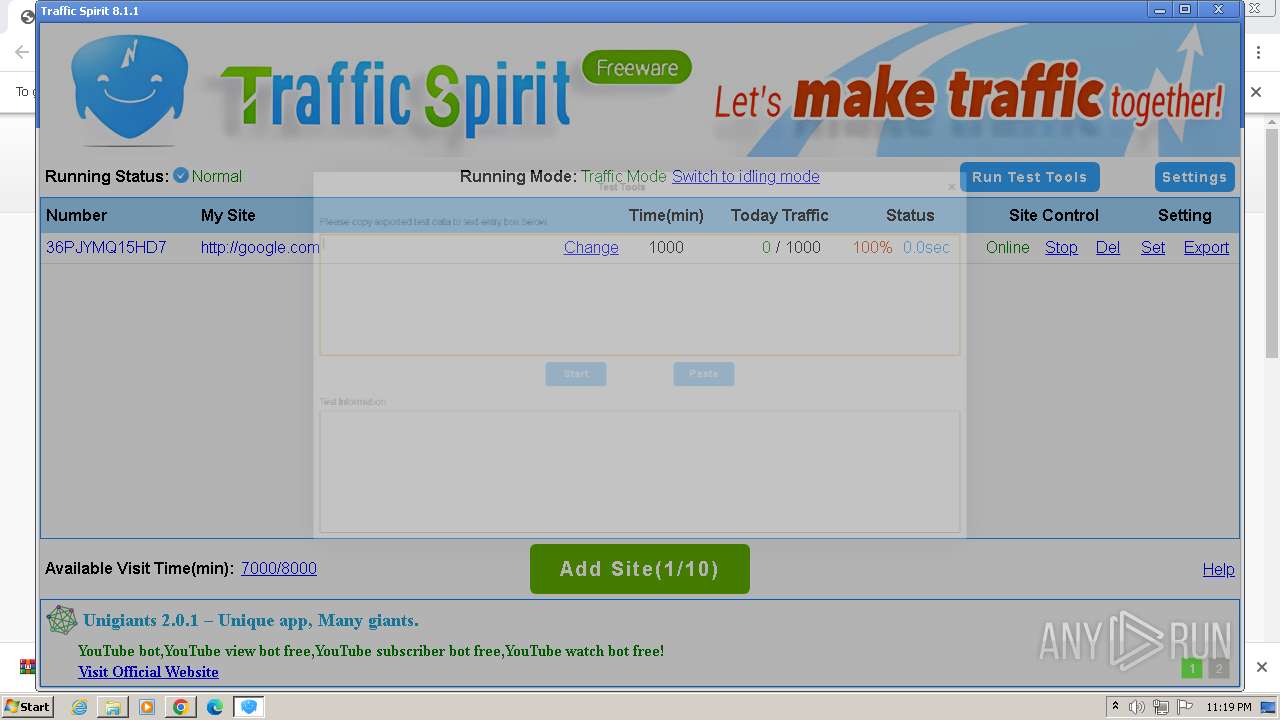
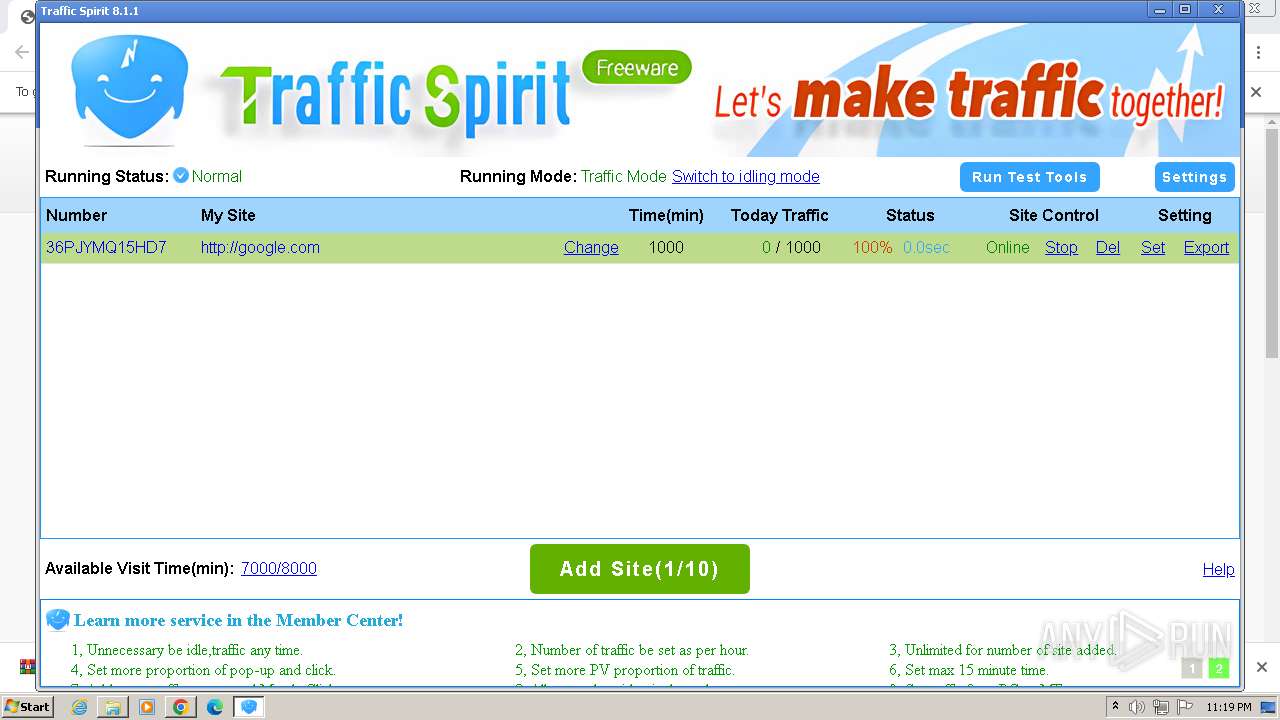
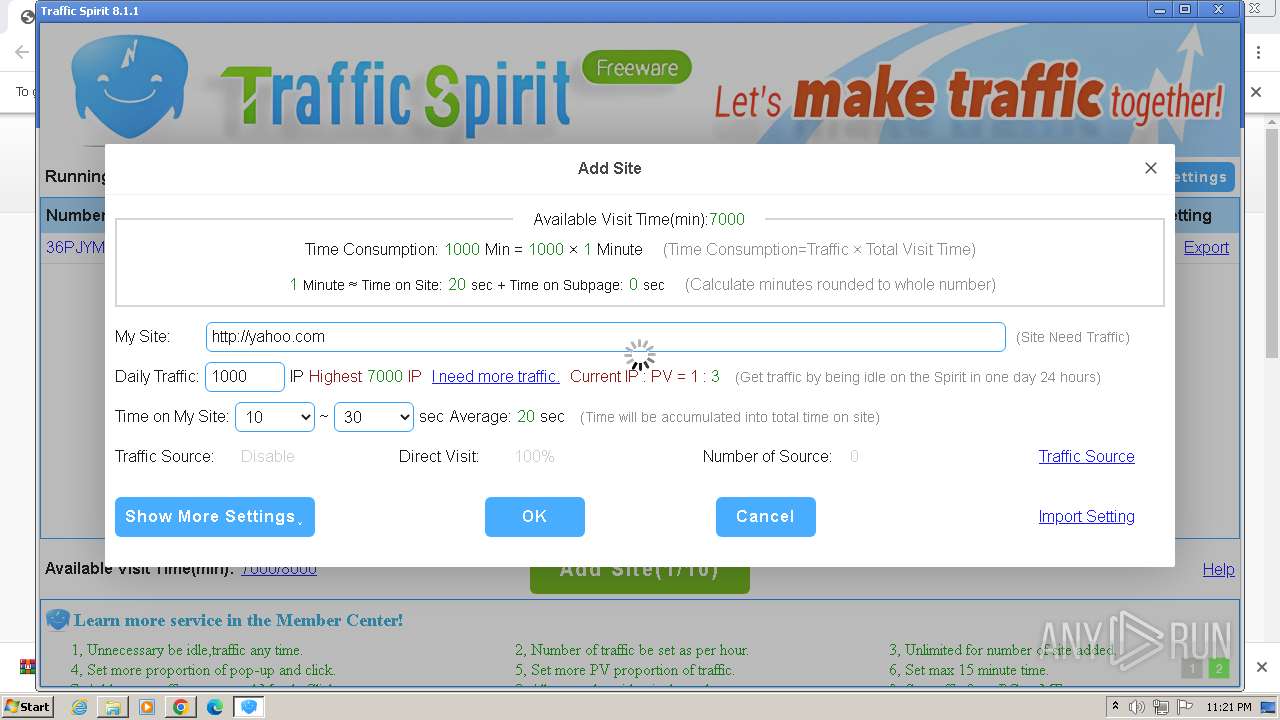
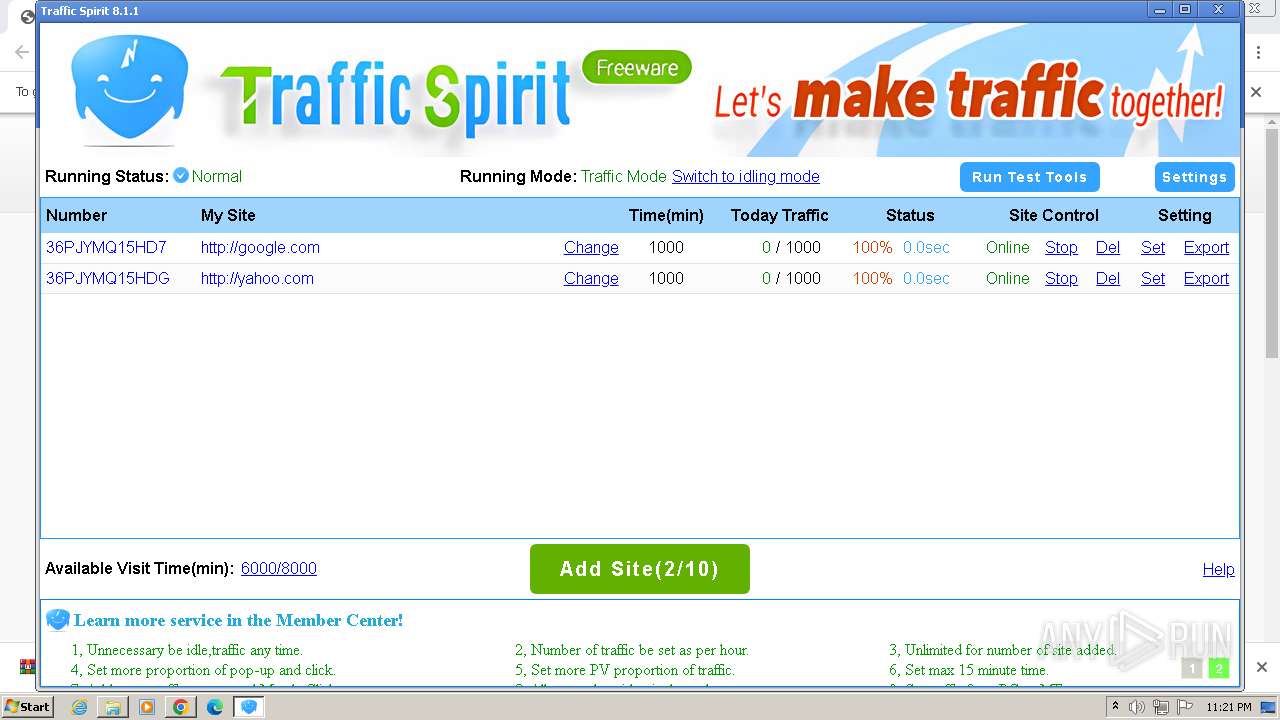
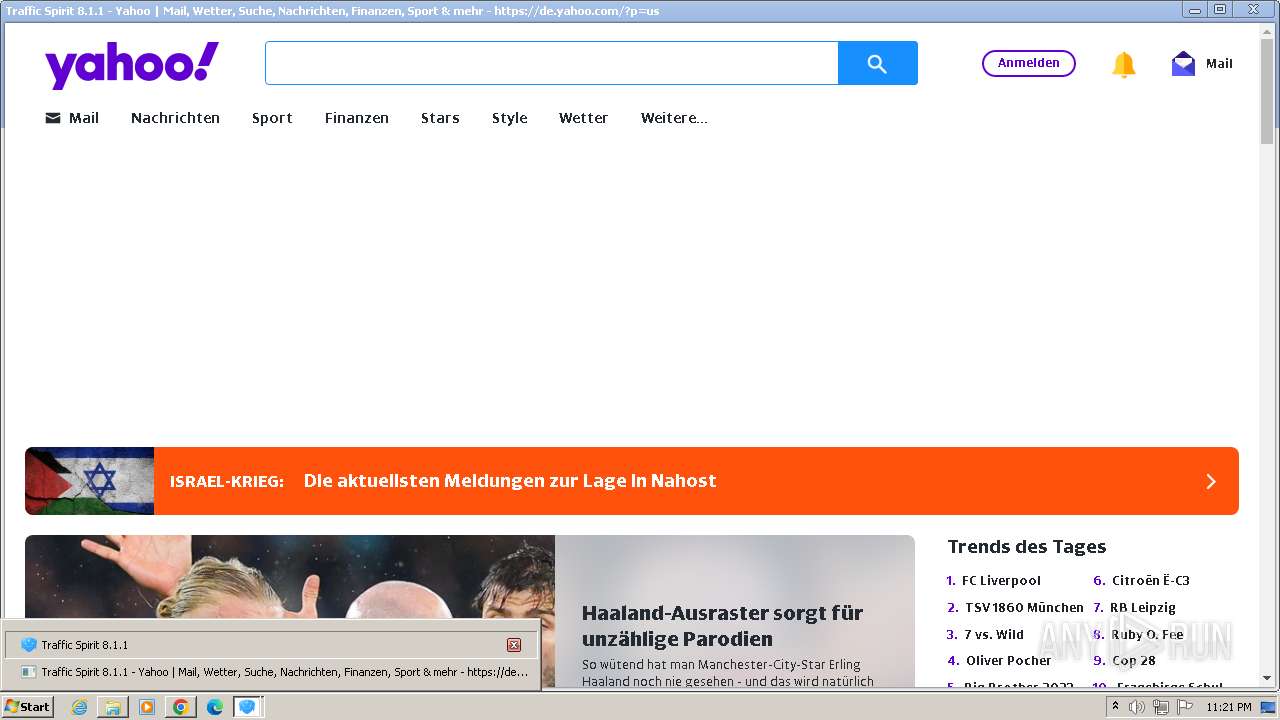
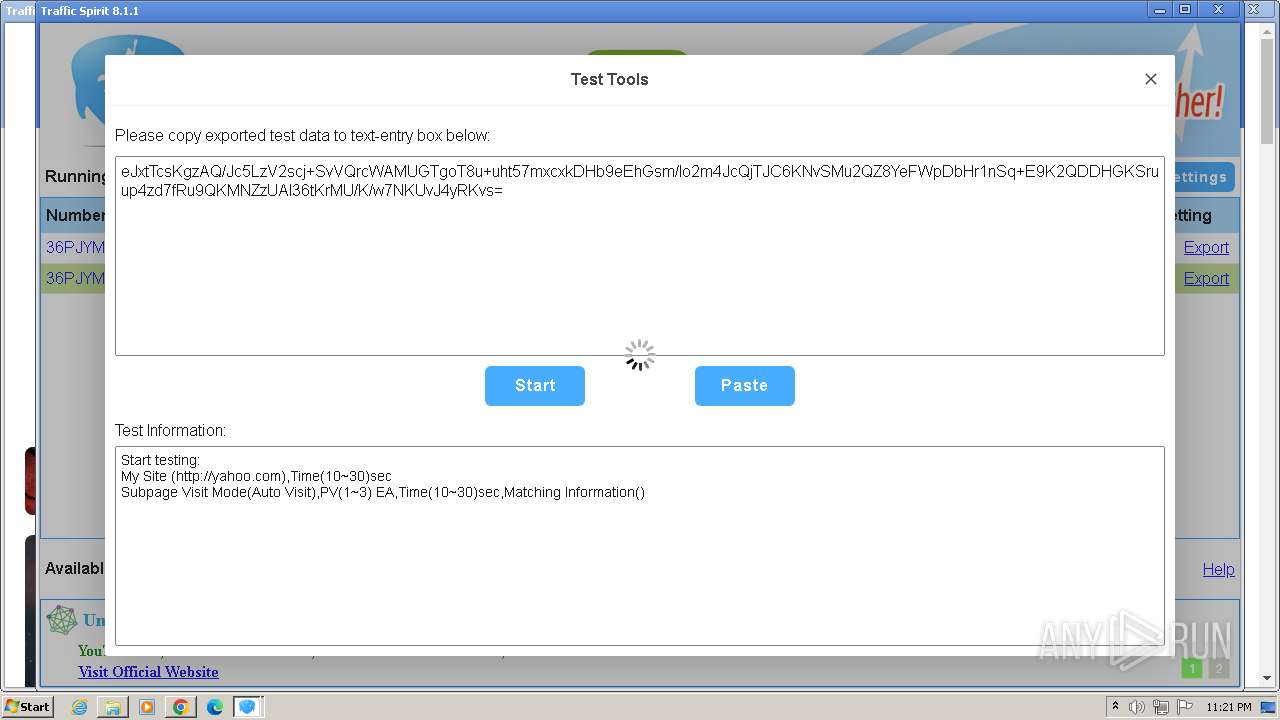
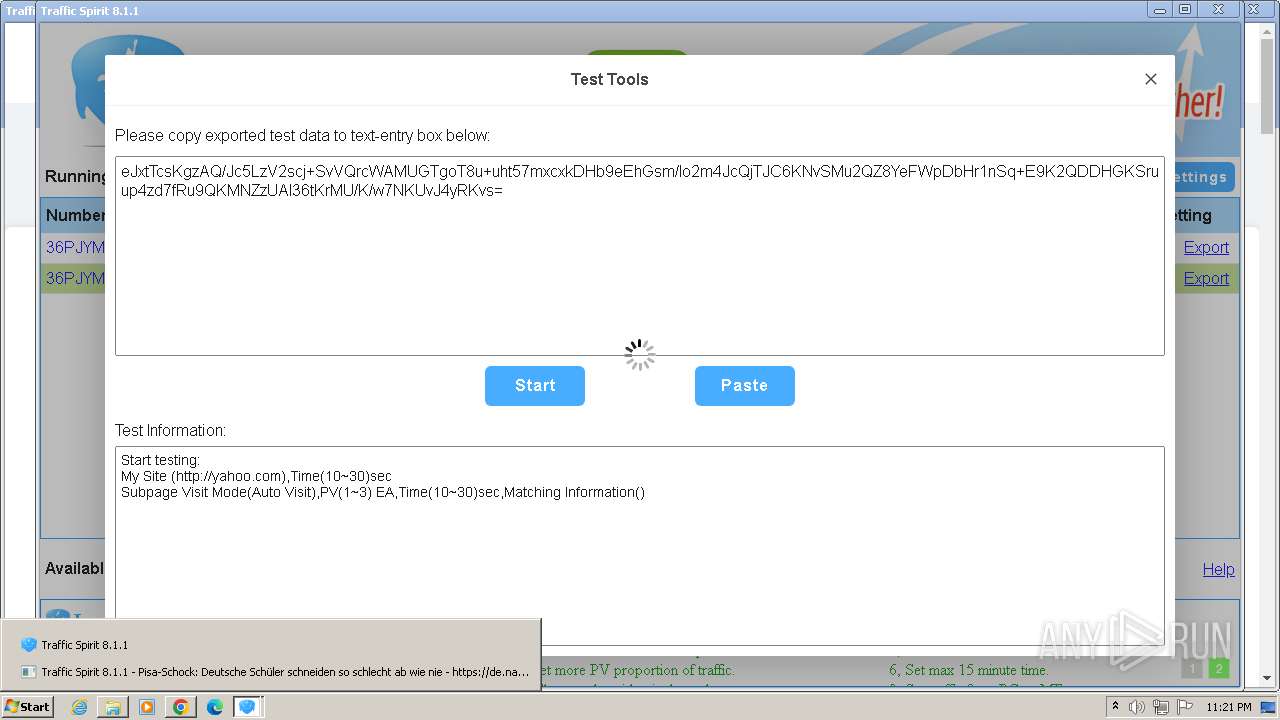
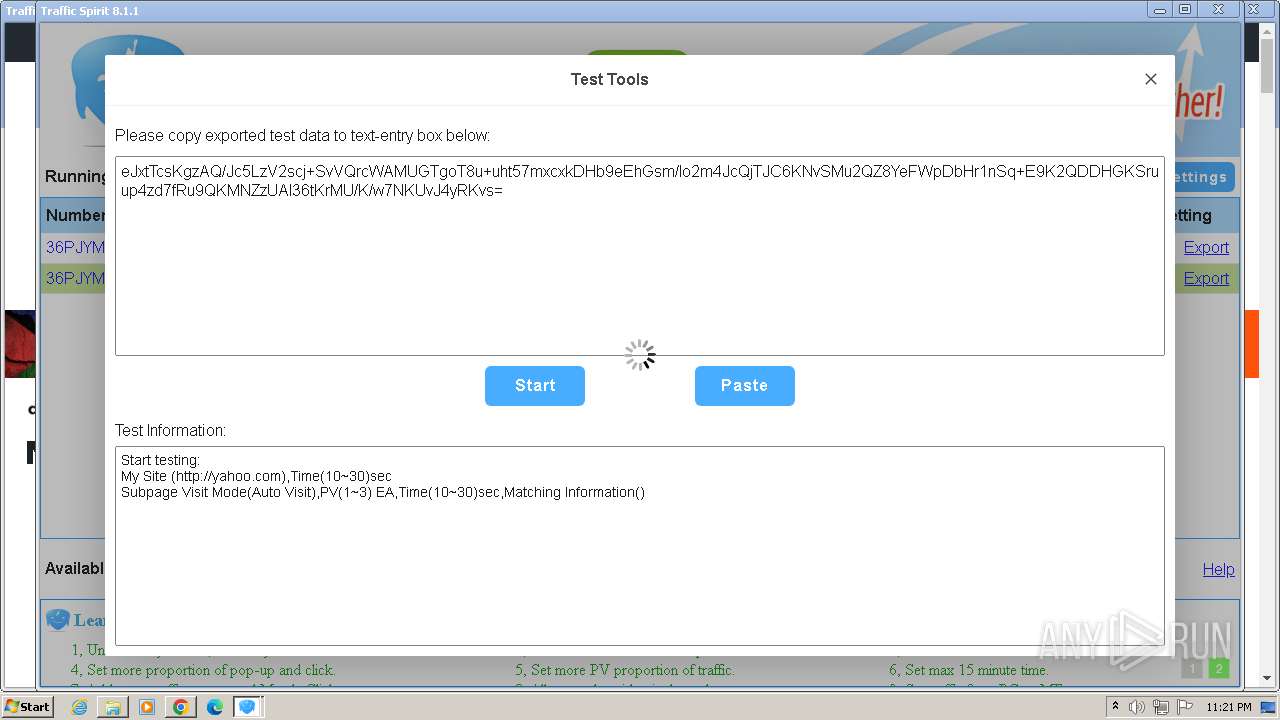
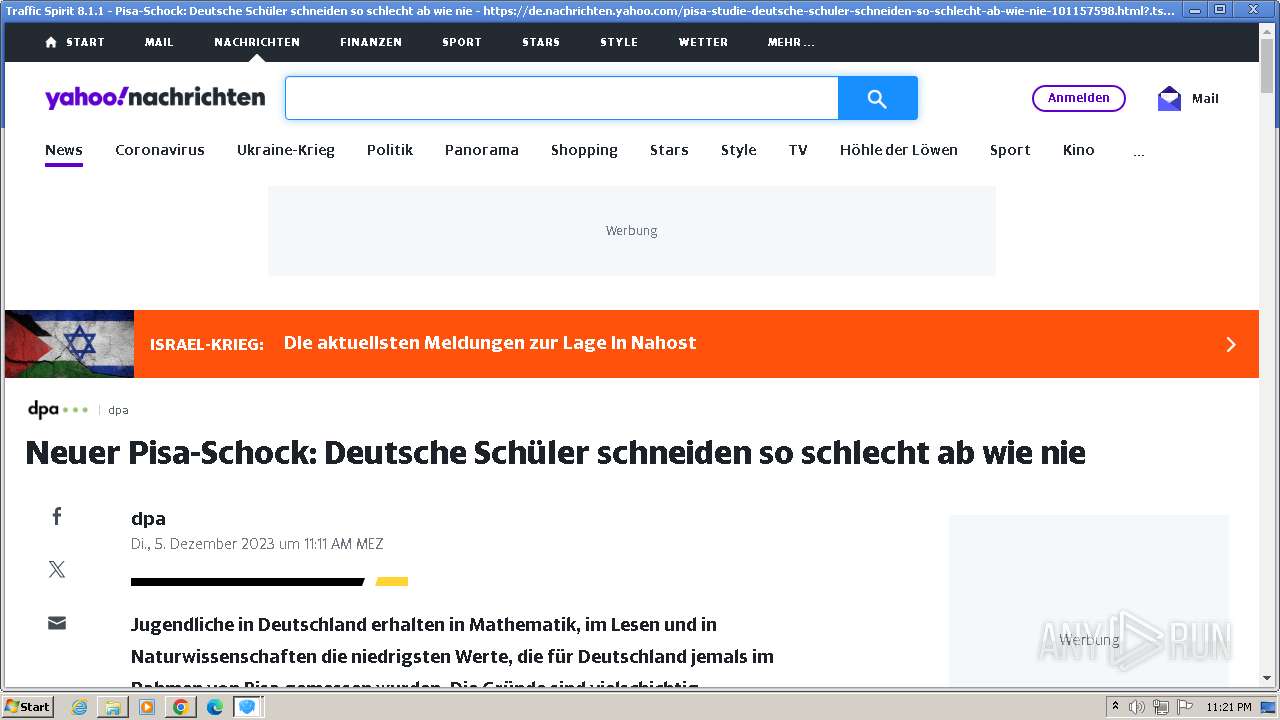
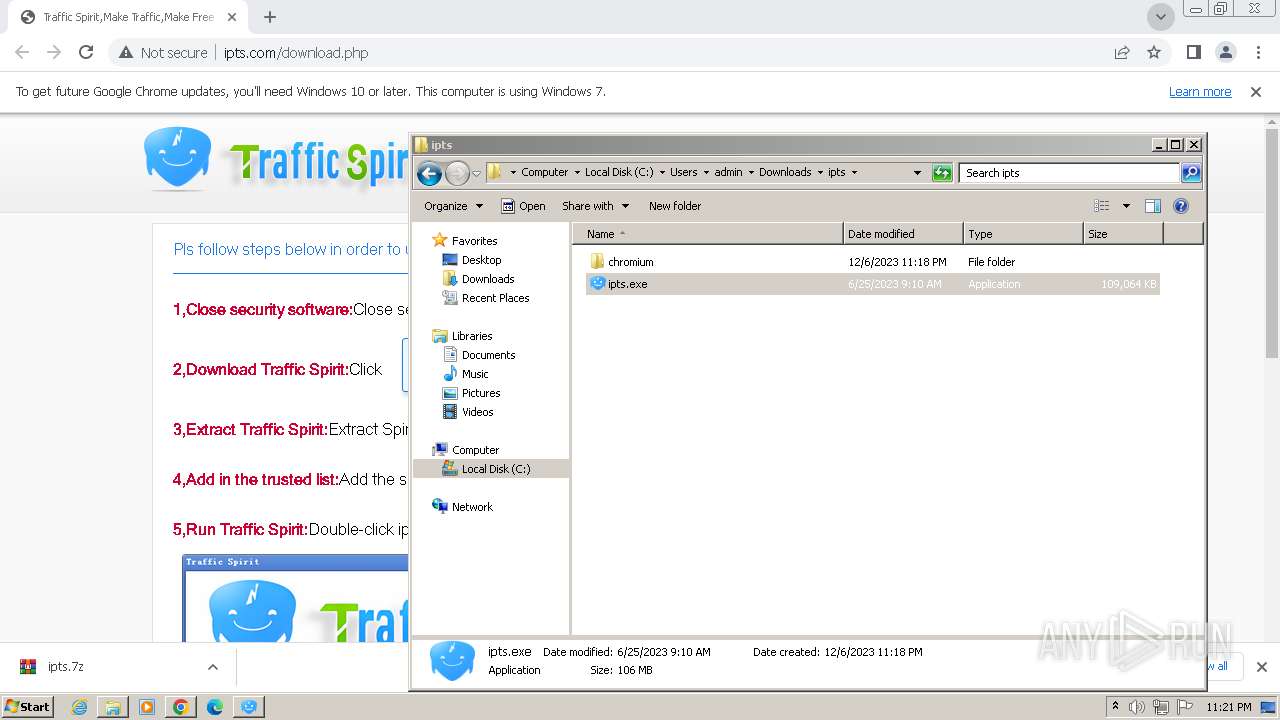
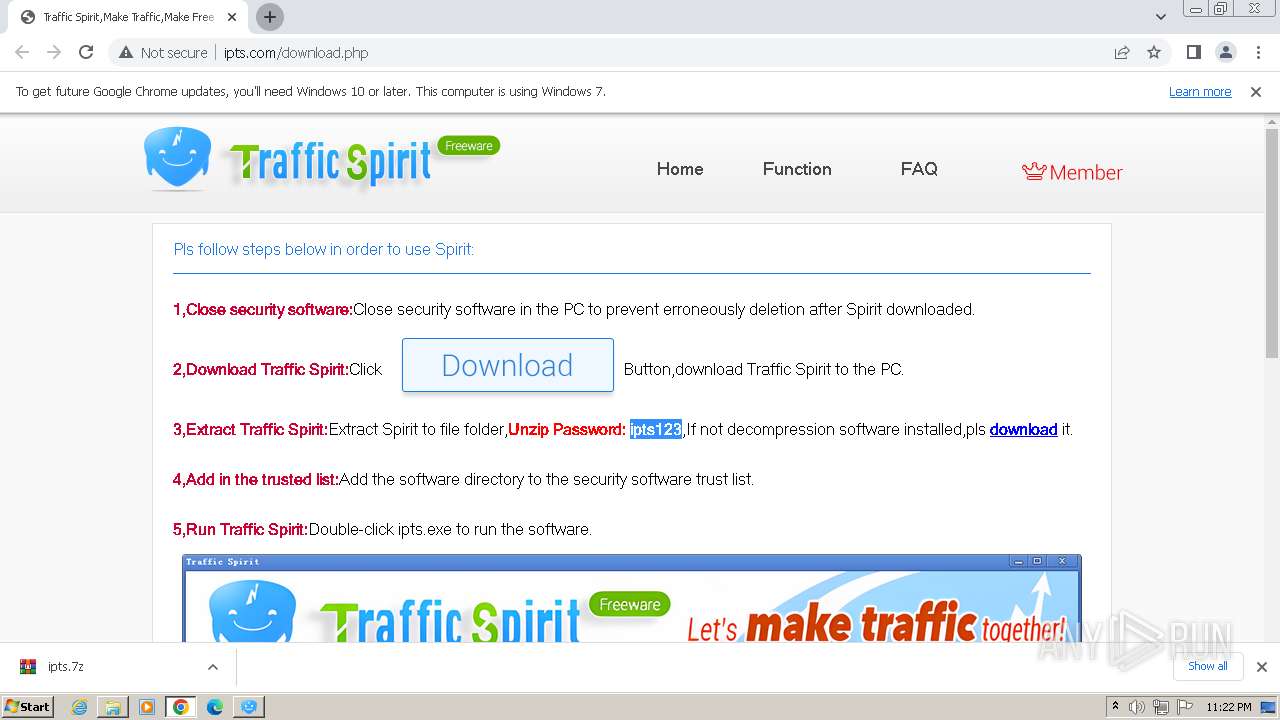
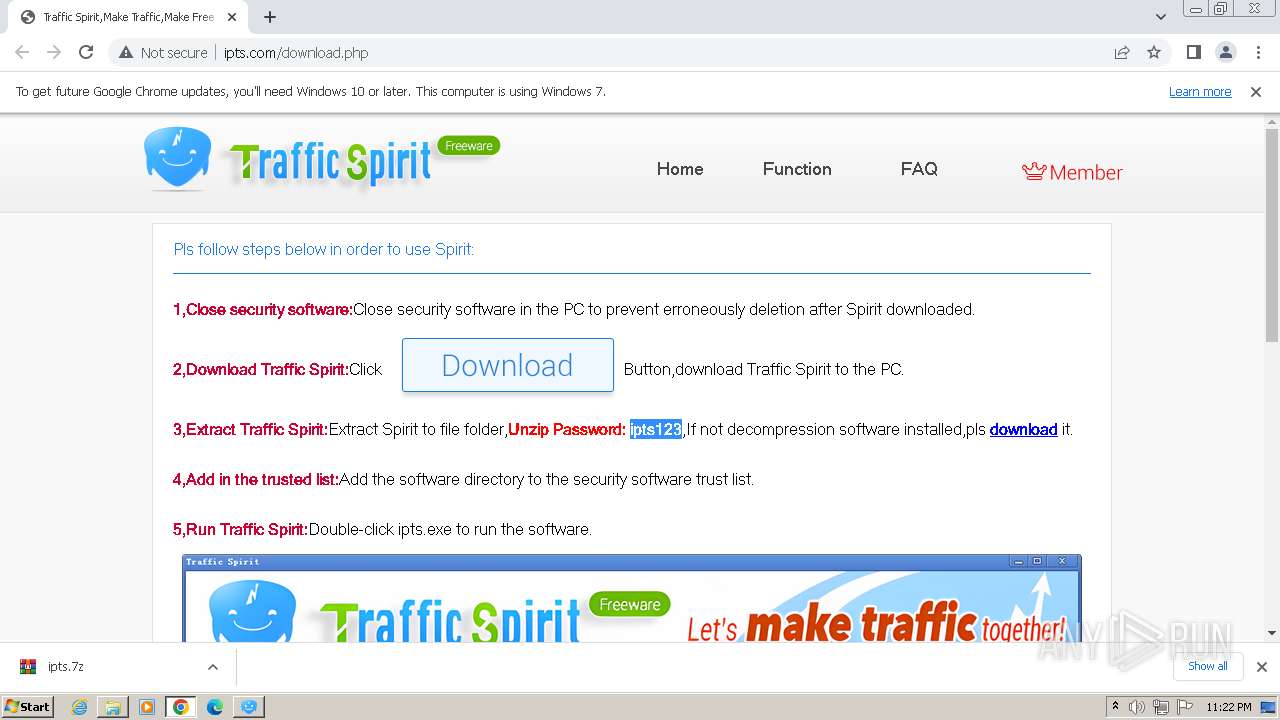
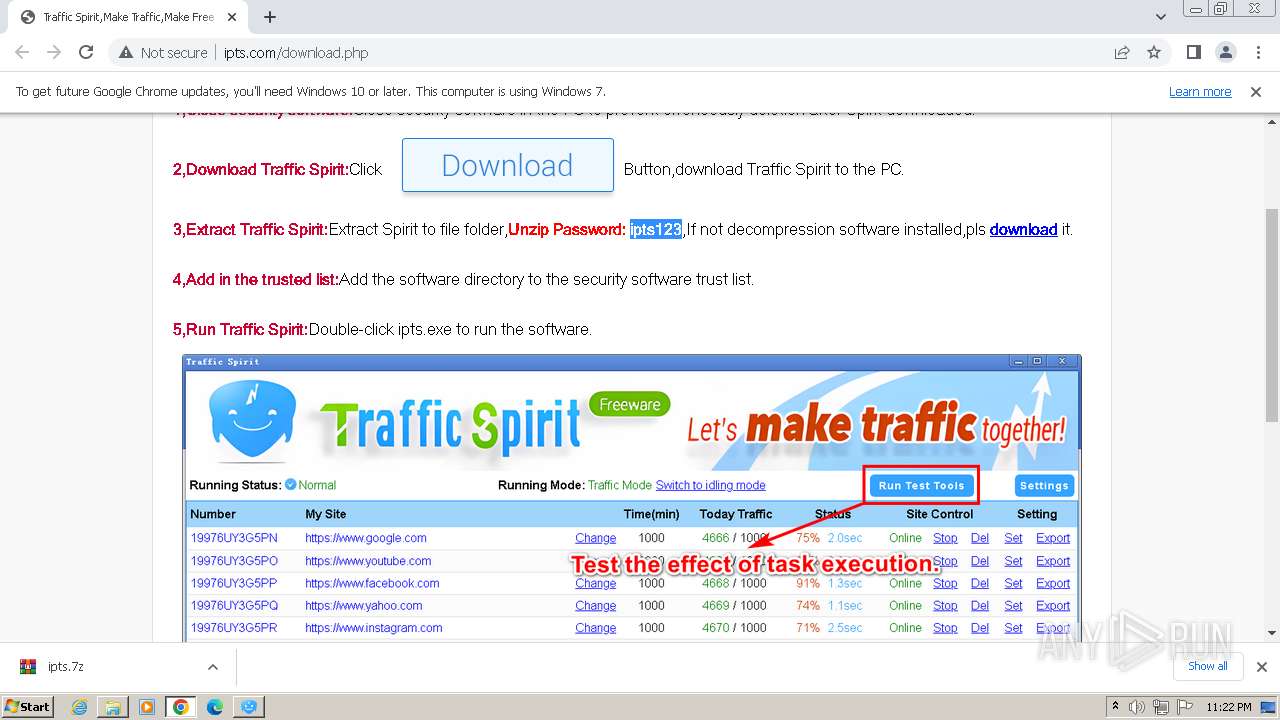
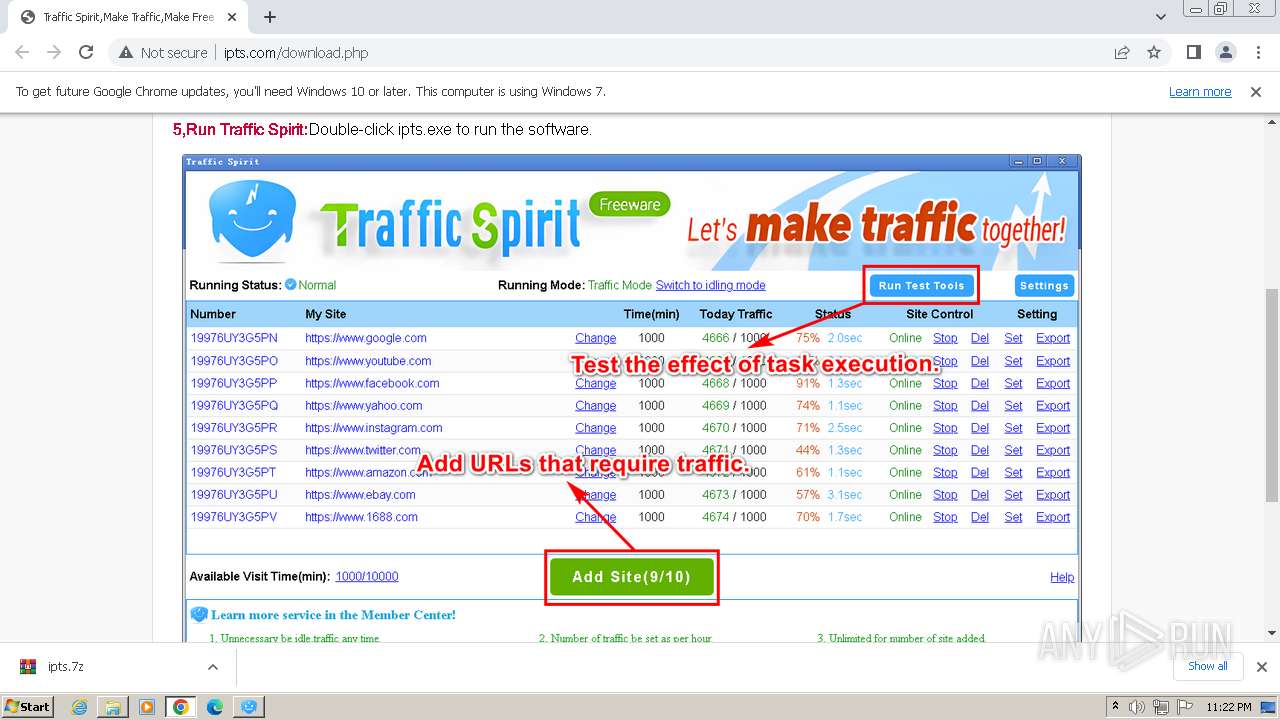
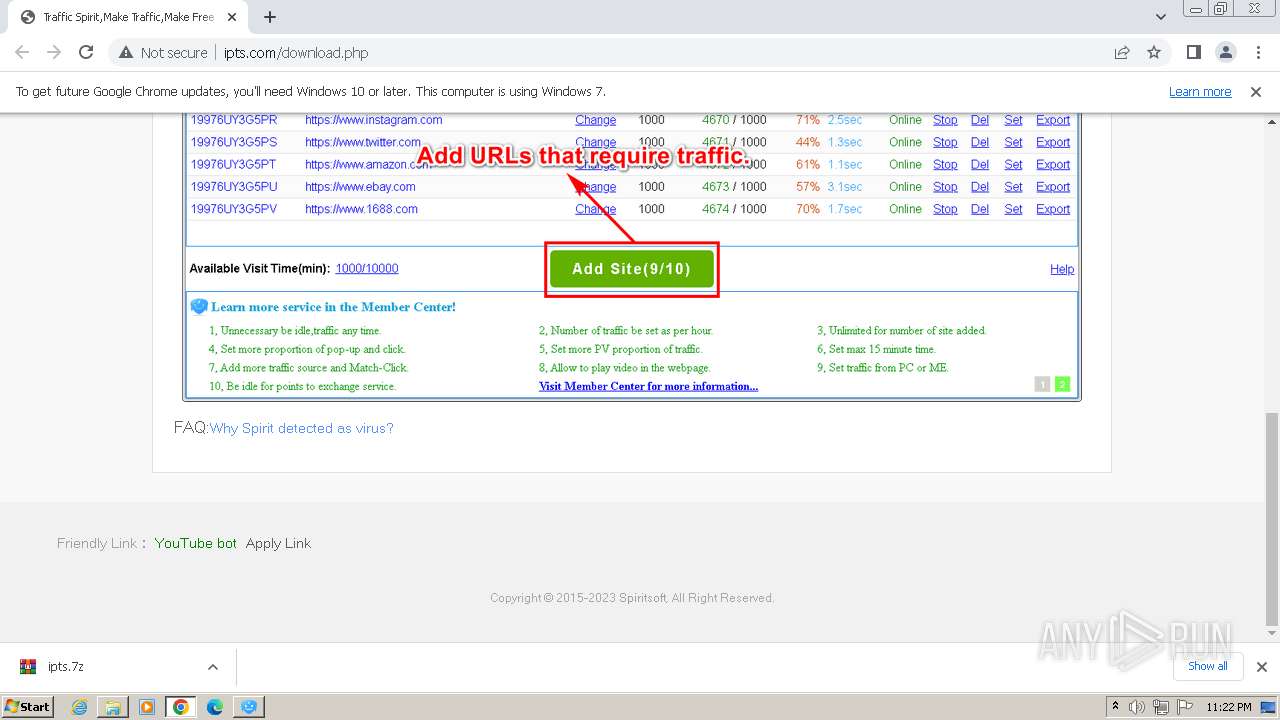
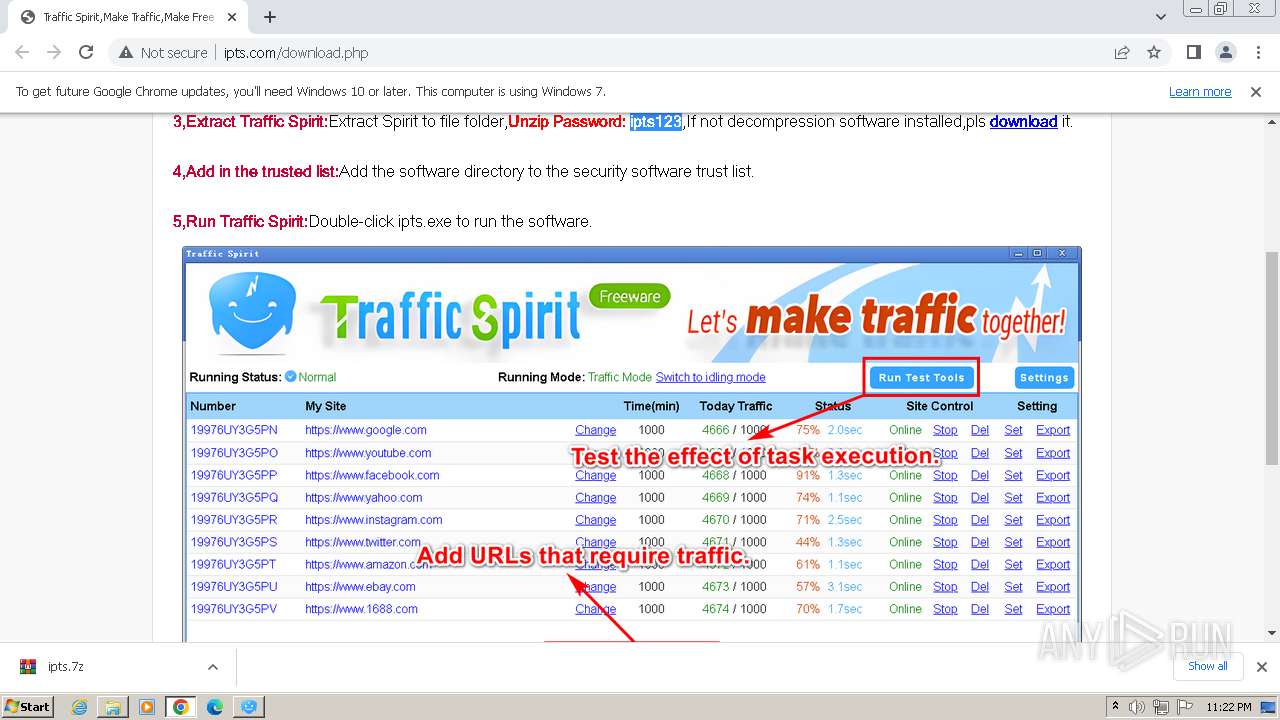
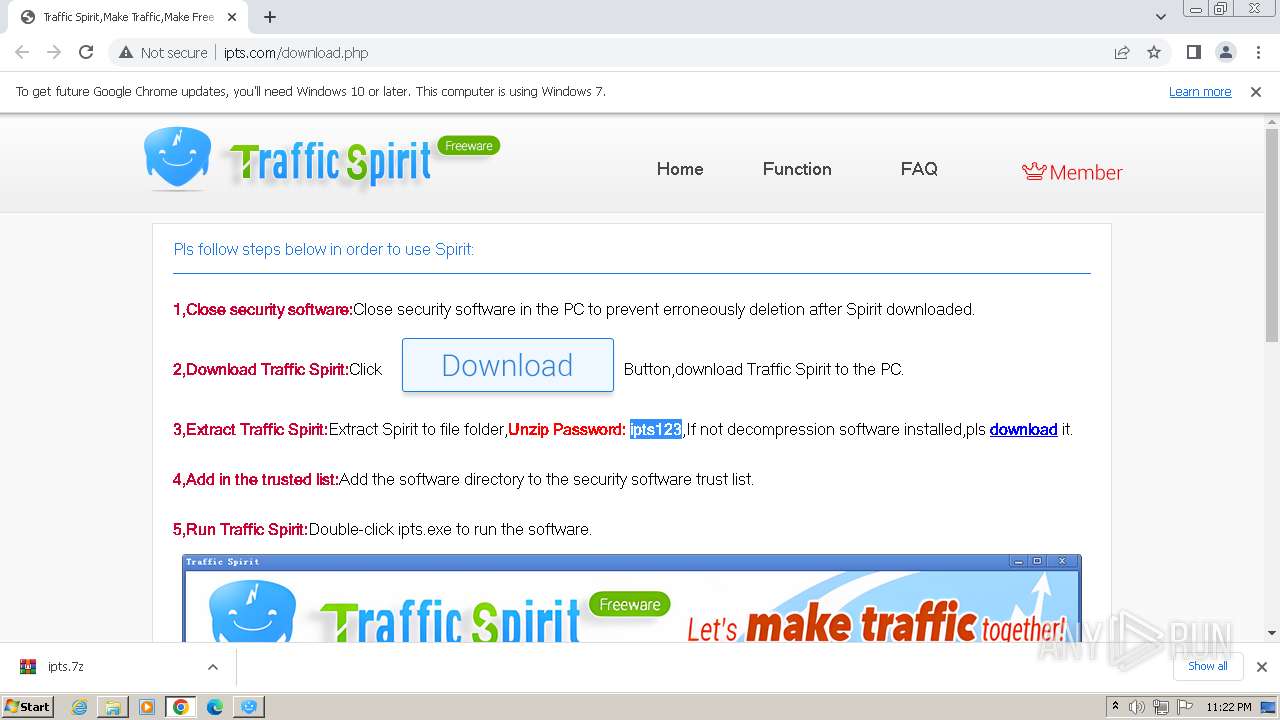
| URL: | http://www.ipts.com/download.php |
| Full analysis: | https://app.any.run/tasks/b4e32e0a-9de0-4d8f-af44-03bf74a86314 |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2023, 23:17:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 0AC36F368FE6991E15DC2CCA640C56F7 |
| SHA1: | FE2B79CF6FA2DCF3FAECF288A398BB0725D4ED74 |
| SHA256: | 5CA83E8492D7E4C381A639D133544E658061501147C98F76B44D690AD713074C |
| SSDEEP: | 3:N1KJS4rLdIKBKKV:Cc4rLdMKV |
MALICIOUS
Actions looks like stealing of personal data
- WinRAR.exe (PID: 3524)
- ipts.exe (PID: 3376)
- ipts.exe (PID: 2860)
- ipts.exe (PID: 2820)
- ipts.exe (PID: 1352)
- ipts.exe (PID: 4004)
- ipts.exe (PID: 1404)
- ipts.exe (PID: 3372)
- ipts.exe (PID: 3960)
- ipts.exe (PID: 3500)
- ipts.exe (PID: 2680)
- ipts.exe (PID: 3876)
- ipts.exe (PID: 2396)
- ipts.exe (PID: 556)
- ipts.exe (PID: 2232)
- ipts.exe (PID: 2400)
- ipts.exe (PID: 916)
- ipts.exe (PID: 372)
- ipts.exe (PID: 3228)
- ipts.exe (PID: 3988)
- ipts.exe (PID: 3096)
- ipts.exe (PID: 3860)
- ipts.exe (PID: 1376)
- ipts.exe (PID: 3844)
- ipts.exe (PID: 3652)
- ipts.exe (PID: 1788)
- ipts.exe (PID: 2088)
- ipts.exe (PID: 3012)
- ipts.exe (PID: 2328)
- ipts.exe (PID: 328)
- ipts.exe (PID: 1032)
- ipts.exe (PID: 188)
- ipts.exe (PID: 1948)
- ipts.exe (PID: 1820)
- ipts.exe (PID: 788)
- ipts.exe (PID: 2884)
- ipts.exe (PID: 2088)
- ipts.exe (PID: 3248)
- ipts.exe (PID: 1668)
- ipts.exe (PID: 1948)
- ipts.exe (PID: 3336)
- ipts.exe (PID: 2648)
- ipts.exe (PID: 3280)
- ipts.exe (PID: 2884)
- ipts.exe (PID: 3460)
- ipts.exe (PID: 1816)
- ipts.exe (PID: 1656)
- ipts.exe (PID: 2308)
- ipts.exe (PID: 2944)
- ipts.exe (PID: 4008)
- ipts.exe (PID: 2736)
- ipts.exe (PID: 3520)
- ipts.exe (PID: 1248)
- ipts.exe (PID: 3764)
- ipts.exe (PID: 2672)
- ipts.exe (PID: 3160)
- ipts.exe (PID: 372)
- ipts.exe (PID: 3808)
- ipts.exe (PID: 3460)
- ipts.exe (PID: 732)
- ipts.exe (PID: 128)
SUSPICIOUS
Process drops legitimate windows executable
- chrome.exe (PID: 3048)
- WinRAR.exe (PID: 3524)
Drops 7-zip archiver for unpacking
- WinRAR.exe (PID: 3524)
Application launched itself
- ipts.exe (PID: 3376)
- ipts.exe (PID: 2820)
- ipts.exe (PID: 3844)
- ipts.exe (PID: 2328)
- ipts.exe (PID: 2736)
Reads settings of System Certificates
- ipts.exe (PID: 3376)
- ipts.exe (PID: 2820)
- ipts.exe (PID: 3844)
- ipts.exe (PID: 2328)
- ipts.exe (PID: 2736)
Process requests binary or script from the Internet
- ipts.exe (PID: 1352)
- ipts.exe (PID: 3960)
INFO
Checks supported languages
- wmpnscfg.exe (PID: 3864)
- ipts.exe (PID: 3376)
- ipts.exe (PID: 1352)
- ipts.exe (PID: 3372)
- ipts.exe (PID: 2860)
- ipts.exe (PID: 2820)
- ipts.exe (PID: 4004)
- ipts.exe (PID: 3500)
- ipts.exe (PID: 3960)
- ipts.exe (PID: 1404)
- ipts.exe (PID: 2680)
- ipts.exe (PID: 2396)
- ipts.exe (PID: 556)
- ipts.exe (PID: 3096)
- ipts.exe (PID: 3988)
- ipts.exe (PID: 2232)
- ipts.exe (PID: 3876)
- ipts.exe (PID: 372)
- ipts.exe (PID: 3228)
- ipts.exe (PID: 2400)
- ipts.exe (PID: 1816)
- ipts.exe (PID: 1376)
- ipts.exe (PID: 3860)
- ipts.exe (PID: 3460)
- ipts.exe (PID: 3844)
- ipts.exe (PID: 3652)
- ipts.exe (PID: 1788)
- ipts.exe (PID: 2088)
- ipts.exe (PID: 128)
- ipts.exe (PID: 3012)
- ipts.exe (PID: 2328)
- ipts.exe (PID: 1948)
- ipts.exe (PID: 1032)
- ipts.exe (PID: 328)
- ipts.exe (PID: 188)
- ipts.exe (PID: 788)
- ipts.exe (PID: 1820)
- ipts.exe (PID: 3248)
- ipts.exe (PID: 2088)
- ipts.exe (PID: 3336)
- ipts.exe (PID: 916)
- ipts.exe (PID: 1668)
- ipts.exe (PID: 2884)
- ipts.exe (PID: 1948)
- ipts.exe (PID: 2648)
- ipts.exe (PID: 1656)
- ipts.exe (PID: 2736)
- ipts.exe (PID: 3280)
- ipts.exe (PID: 2308)
- ipts.exe (PID: 1248)
- ipts.exe (PID: 4008)
- ipts.exe (PID: 2884)
- ipts.exe (PID: 3520)
- ipts.exe (PID: 3808)
- ipts.exe (PID: 3460)
- ipts.exe (PID: 3764)
- ipts.exe (PID: 2672)
- ipts.exe (PID: 3160)
- ipts.exe (PID: 372)
- ipts.exe (PID: 2944)
- ipts.exe (PID: 732)
Manual execution by a user
- wmpnscfg.exe (PID: 3864)
- WinRAR.exe (PID: 3524)
- ipts.exe (PID: 3376)
Reads the computer name
- wmpnscfg.exe (PID: 3864)
- ipts.exe (PID: 3376)
- ipts.exe (PID: 1352)
- ipts.exe (PID: 2820)
- ipts.exe (PID: 4004)
- ipts.exe (PID: 3960)
- ipts.exe (PID: 2680)
- ipts.exe (PID: 1376)
- ipts.exe (PID: 3844)
- ipts.exe (PID: 3652)
- ipts.exe (PID: 2088)
- ipts.exe (PID: 2328)
- ipts.exe (PID: 1948)
- ipts.exe (PID: 1820)
- ipts.exe (PID: 1032)
- ipts.exe (PID: 2736)
- ipts.exe (PID: 3520)
- ipts.exe (PID: 1248)
- ipts.exe (PID: 2884)
- ipts.exe (PID: 3460)
The process uses the downloaded file
- chrome.exe (PID: 3172)
- chrome.exe (PID: 1784)
- chrome.exe (PID: 2448)
- WinRAR.exe (PID: 3524)
- chrome.exe (PID: 3292)
Drops the executable file immediately after the start
- chrome.exe (PID: 3048)
- WinRAR.exe (PID: 3524)
- chrome.exe (PID: 3540)
- chrome.exe (PID: 2844)
Application launched itself
- chrome.exe (PID: 3048)
Reads CPU info
- ipts.exe (PID: 3376)
Create files in a temporary directory
- ipts.exe (PID: 3376)
- ipts.exe (PID: 1352)
- ipts.exe (PID: 2820)
- ipts.exe (PID: 3844)
- ipts.exe (PID: 2328)
- ipts.exe (PID: 2736)
Process checks computer location settings
- ipts.exe (PID: 2860)
- ipts.exe (PID: 3376)
- ipts.exe (PID: 3500)
- ipts.exe (PID: 2820)
- ipts.exe (PID: 2396)
- ipts.exe (PID: 2232)
- ipts.exe (PID: 556)
- ipts.exe (PID: 3096)
- ipts.exe (PID: 3988)
- ipts.exe (PID: 3876)
- ipts.exe (PID: 2400)
- ipts.exe (PID: 372)
- ipts.exe (PID: 3228)
- ipts.exe (PID: 3460)
- ipts.exe (PID: 3860)
- ipts.exe (PID: 1816)
- ipts.exe (PID: 3844)
- ipts.exe (PID: 3012)
- ipts.exe (PID: 128)
- ipts.exe (PID: 188)
- ipts.exe (PID: 2328)
- ipts.exe (PID: 3248)
- ipts.exe (PID: 1668)
- ipts.exe (PID: 3336)
- ipts.exe (PID: 788)
- ipts.exe (PID: 916)
- ipts.exe (PID: 1948)
- ipts.exe (PID: 2884)
- ipts.exe (PID: 2648)
- ipts.exe (PID: 2088)
- ipts.exe (PID: 2308)
- ipts.exe (PID: 1656)
- ipts.exe (PID: 3280)
- ipts.exe (PID: 4008)
- ipts.exe (PID: 2736)
- ipts.exe (PID: 3808)
- ipts.exe (PID: 3764)
- ipts.exe (PID: 2672)
- ipts.exe (PID: 3160)
- ipts.exe (PID: 372)
- ipts.exe (PID: 732)
Reads the machine GUID from the registry
- ipts.exe (PID: 2820)
- ipts.exe (PID: 3376)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
128
Monitored processes
86
Malicious processes
61
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Users\admin\Downloads\ipts\ipts.exe" --type=renderer --ub-type=urltest --first-renderer-process --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=1760 --field-trial-handle=916,i,17324633026368991160,9508768518370894996,131072 /prefetch:1 | C:\Users\admin\Downloads\ipts\ipts.exe | ipts.exe | ||||||||||||
User: admin Company: Spiritsoft(www.ipts.com) Integrity Level: LOW Description: Traffic Spirit(http://www.ipts.com) Exit code: 0 Version: 2023.6.26.43 Modules
| |||||||||||||||
| 188 | "C:\Users\admin\Downloads\ipts\ipts.exe" --type=renderer --ub-type=urltest --first-renderer-process --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=1692 --field-trial-handle=932,i,17792125437286717155,290938827434532176,131072 /prefetch:1 | C:\Users\admin\Downloads\ipts\ipts.exe | ipts.exe | ||||||||||||
User: admin Company: Spiritsoft(www.ipts.com) Integrity Level: LOW Description: Traffic Spirit(http://www.ipts.com) Exit code: 0 Version: 2023.6.26.43 Modules
| |||||||||||||||
| 280 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6a7a8b38,0x6a7a8b48,0x6a7a8b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 292 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3568 --field-trial-handle=1164,i,11269331173937500977,1908815433233384982,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 328 | "C:\Users\admin\Downloads\ipts\ipts.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --ignore-certificate-errors --ignore-certificate-errors --ub-type=urltest --mojo-platform-channel-handle=1272 --field-trial-handle=932,i,17792125437286717155,290938827434532176,131072 /prefetch:8 | C:\Users\admin\Downloads\ipts\ipts.exe | ipts.exe | ||||||||||||
User: admin Company: Spiritsoft(www.ipts.com) Integrity Level: LOW Description: Traffic Spirit(http://www.ipts.com) Exit code: 0 Version: 2023.6.26.43 Modules
| |||||||||||||||
| 372 | "C:\Users\admin\Downloads\ipts\ipts.exe" --type=renderer --ub-type=urltask --image-replacement --disable-databases --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=14 --mojo-platform-channel-handle=2712 --field-trial-handle=912,i,638760438389331850,2465713818615993417,131072 /prefetch:1 | C:\Users\admin\Downloads\ipts\ipts.exe | ipts.exe | ||||||||||||
User: admin Company: Spiritsoft(www.ipts.com) Integrity Level: LOW Description: Traffic Spirit(http://www.ipts.com) Exit code: 0 Version: 2023.6.26.43 Modules
| |||||||||||||||
| 372 | "C:\Users\admin\Downloads\ipts\ipts.exe" --type=renderer --ub-type=urltask --image-replacement --disable-databases --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=36 --mojo-platform-channel-handle=2256 --field-trial-handle=912,i,638760438389331850,2465713818615993417,131072 /prefetch:1 | C:\Users\admin\Downloads\ipts\ipts.exe | ipts.exe | ||||||||||||
User: admin Company: Spiritsoft(www.ipts.com) Integrity Level: LOW Description: Traffic Spirit(http://www.ipts.com) Exit code: 0 Version: 2023.6.26.43 Modules
| |||||||||||||||
| 556 | "C:\Users\admin\Downloads\ipts\ipts.exe" --type=renderer --ub-type=urltask --image-replacement --disable-databases --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --mojo-platform-channel-handle=2088 --field-trial-handle=912,i,638760438389331850,2465713818615993417,131072 /prefetch:1 | C:\Users\admin\Downloads\ipts\ipts.exe | ipts.exe | ||||||||||||
User: admin Company: Spiritsoft(www.ipts.com) Integrity Level: LOW Description: Traffic Spirit(http://www.ipts.com) Exit code: 0 Version: 2023.6.26.43 Modules
| |||||||||||||||
| 556 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3272 --field-trial-handle=1164,i,11269331173937500977,1908815433233384982,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 732 | "C:\Users\admin\Downloads\ipts\ipts.exe" --type=renderer --ub-type=urltask --image-replacement --disable-databases --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=37 --mojo-platform-channel-handle=2428 --field-trial-handle=912,i,638760438389331850,2465713818615993417,131072 /prefetch:1 | C:\Users\admin\Downloads\ipts\ipts.exe | ipts.exe | ||||||||||||
User: admin Company: Spiritsoft(www.ipts.com) Integrity Level: LOW Description: Traffic Spirit(http://www.ipts.com) Exit code: 0 Version: 2023.6.26.43 Modules
| |||||||||||||||
Total events
9 645
Read events
9 526
Write events
118
Delete events
1
Modification events
| (PID) Process: | (3048) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3048) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3048) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3048) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3048) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3048) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 1 | |||
| (PID) Process: | (3048) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3048) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3048) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
| (PID) Process: | (3048) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_enableddate |
Value: 0 | |||
Executable files
13
Suspicious files
326
Text files
62
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3048 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF211bb5.TMP | — | |
MD5:— | SHA256:— | |||
| 3048 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3048 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\69933c6c-fb6f-44ab-9b6c-6c04d72aee65.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 3048 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF211bc4.TMP | text | |
MD5:E91E138A25FD7E5BCA5E60111F39C91A | SHA256:B1F7E3537A31A4B847F862858E5D2581993CC9372F19ABF19EA2A9185FE42A4F | |||
| 3048 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Platform Notifications\LOG.old | text | |
MD5:05387A3C4FCF1F3B992FF9FBF045AA1A | SHA256:B01E9451B8F6ABF03C9CD2E158C02D0A6BFDF771944F5D0B96DAD2DA6A7E3C8F | |||
| 3048 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old | text | |
MD5:104D1263D6BB098583985C096C03312C | SHA256:3FE38AF79B21F63EB0050149F3454A9EF953907A9D5D73ABD1FFEBB3EB3A85F8 | |||
| 3048 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF2123f2.TMP | — | |
MD5:— | SHA256:— | |||
| 3048 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3048 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:43550DBA2277BE44F5F842196E084145 | SHA256:D19055342C06316F8B80D0B029BD233A3E48AD4C591953AF7B712ADA7F68F403 | |||
| 3048 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\metadata\LOG.old~RF211ed2.TMP | text | |
MD5:8268A4D53A6A9432A8266584CBD7D624 | SHA256:F785C42945CFE320C52C763837CD41541A8CAAB3E5FD567999EED5343CF0FD7A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
252
TCP/UDP connections
819
DNS requests
485
Threats
62
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2108 | chrome.exe | GET | 200 | 203.107.86.226:80 | http://sdk.51.la/js-sdk-pro.min.js | unknown | text | 12.5 Kb | unknown |
868 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | — | — | unknown |
2108 | chrome.exe | GET | 200 | 47.88.10.215:80 | http://www.ipts.com/download.php | unknown | html | 2.69 Kb | unknown |
2108 | chrome.exe | GET | 200 | 47.88.10.215:80 | http://www.ipts.com/style/style.css | unknown | text | 521 b | unknown |
2108 | chrome.exe | GET | 200 | 47.88.10.215:80 | http://www.ipts.com/images/vipuser.png | unknown | image | 2.29 Kb | unknown |
2108 | chrome.exe | GET | 200 | 47.88.10.215:80 | http://www.ipts.com/images/xz_normal.png | unknown | image | 3.32 Kb | unknown |
2108 | chrome.exe | GET | 200 | 47.88.10.215:80 | http://www.ipts.com/images/logo.png | unknown | image | 16.2 Kb | unknown |
2108 | chrome.exe | GET | 200 | 47.88.10.215:80 | http://www.ipts.com/images/top_bg.png | unknown | image | 166 b | unknown |
2108 | chrome.exe | POST | 200 | 203.107.86.226:80 | http://collect-v6.51.la/v6/collect?dt=4 | unknown | — | — | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 43.4 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
868 | svchost.exe | 23.35.228.137:80 | — | AKAMAI-AS | DE | unknown |
2108 | chrome.exe | 108.177.15.84:443 | accounts.google.com | GOOGLE | US | unknown |
3048 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2108 | chrome.exe | 47.88.10.215:80 | www.ipts.com | Alibaba US Technology Co., Ltd. | US | unknown |
2108 | chrome.exe | 203.107.86.226:80 | sdk.51.la | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
2108 | chrome.exe | 142.250.181.232:443 | www.googletagmanager.com | GOOGLE | US | unknown |
2108 | chrome.exe | 216.239.34.36:443 | region1.google-analytics.com | GOOGLE | US | unknown |
2108 | chrome.exe | 142.250.185.196:443 | www.google.com | GOOGLE | US | whitelisted |
2108 | chrome.exe | 47.246.50.63:80 | dlc.ipts.com | Zhejiang Taobao Network Co.,Ltd | FR | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
accounts.google.com |
| shared |
www.ipts.com |
| unknown |
sdk.51.la |
| unknown |
www.googletagmanager.com |
| whitelisted |
collect-v6.51.la |
| unknown |
region1.google-analytics.com |
| whitelisted |
dlc.ipts.com |
| unknown |
vip.ipts.com |
| unknown |
www.rarlab.com |
| unknown |
www.spiritsoft.cn |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO URL Shortener Service Domain in DNS Lookup (cutt .ly) |
3960 | ipts.exe | Misc activity | ET INFO Observed URL Shortener Service Domain (cutt .ly in TLS SNI) |
1080 | svchost.exe | Misc activity | ET INFO CMS Hosting Domain in DNS Lookup (storyblok .com) |
3960 | ipts.exe | Misc activity | ET INFO CMS Hosting Domain in TLS SNI (storyblok .com) |
3960 | ipts.exe | Misc activity | ET INFO CMS Hosting Domain in TLS SNI (storyblok .com) |
3960 | ipts.exe | Misc activity | ET INFO CMS Hosting Domain in TLS SNI (storyblok .com) |
3960 | ipts.exe | Misc activity | ET INFO CMS Hosting Domain in TLS SNI (storyblok .com) |
— | — | Misc activity | ET INFO CMS Hosting Domain in TLS SNI (storyblok .com) |
— | — | Misc activity | ET INFO CMS Hosting Domain in TLS SNI (storyblok .com) |
1080 | svchost.exe | Misc activity | ET INFO CMS Hosting Domain in DNS Lookup (storyblok .com) |