| File name: | CH341SER.EXE |
| Full analysis: | https://app.any.run/tasks/adae2d3a-bcc1-4bb9-baf8-64c386ed81ad |
| Verdict: | Malicious activity |
| Analysis date: | August 17, 2024, 09:32:33 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, RAR self-extracting archive |
| MD5: | 1461E4F00D1F457B1EACF214FD5A2EF2 |
| SHA1: | C38D5005921D1F932EB29A57168426F06850C254 |
| SHA256: | 5C79A8C123D3FA03274FDCCC8FAD722AAF3B703DF35C39B4B42F0B5BFBB26DFD |
| SSDEEP: | 6144:h8U2qy6rRZb7jxGYXqZ9vcF/6jHLrZpEr9TI:5zy6rRxE7RrrjCJI |
MALICIOUS
No malicious indicators.SUSPICIOUS
Drops the executable file immediately after the start
- CH341SER.EXE.exe (PID: 6344)
Reads security settings of Internet Explorer
- CH341SER.EXE.exe (PID: 6344)
Creates file in the systems drive root
- CH341SER.EXE.exe (PID: 6344)
Reads the date of Windows installation
- CH341SER.EXE.exe (PID: 6344)
Executable content was dropped or overwritten
- CH341SER.EXE.exe (PID: 6344)
Drops a system driver (possible attempt to evade defenses)
- CH341SER.EXE.exe (PID: 6344)
INFO
Checks supported languages
- CH341SER.EXE.exe (PID: 6344)
- SETUP.EXE (PID: 6500)
- DRVSETUP64.exe (PID: 6544)
Reads the computer name
- CH341SER.EXE.exe (PID: 6344)
- DRVSETUP64.exe (PID: 6544)
Process checks computer location settings
- CH341SER.EXE.exe (PID: 6344)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | WinRAR Self Extracting archive (94.3) |
|---|---|---|
| .scr | | | Windows screen saver (2.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.1) |
| .exe | | | Win32 Executable (generic) (0.8) |
| .exe | | | Win32 Executable Watcom C++ (generic) (0.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2007:05:22 04:59:14+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 5 |
| CodeSize: | 81920 |
| InitializedDataSize: | 22016 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
136
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6344 | "C:\Users\admin\AppData\Local\Temp\CH341SER.EXE.exe" | C:\Users\admin\AppData\Local\Temp\CH341SER.EXE.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
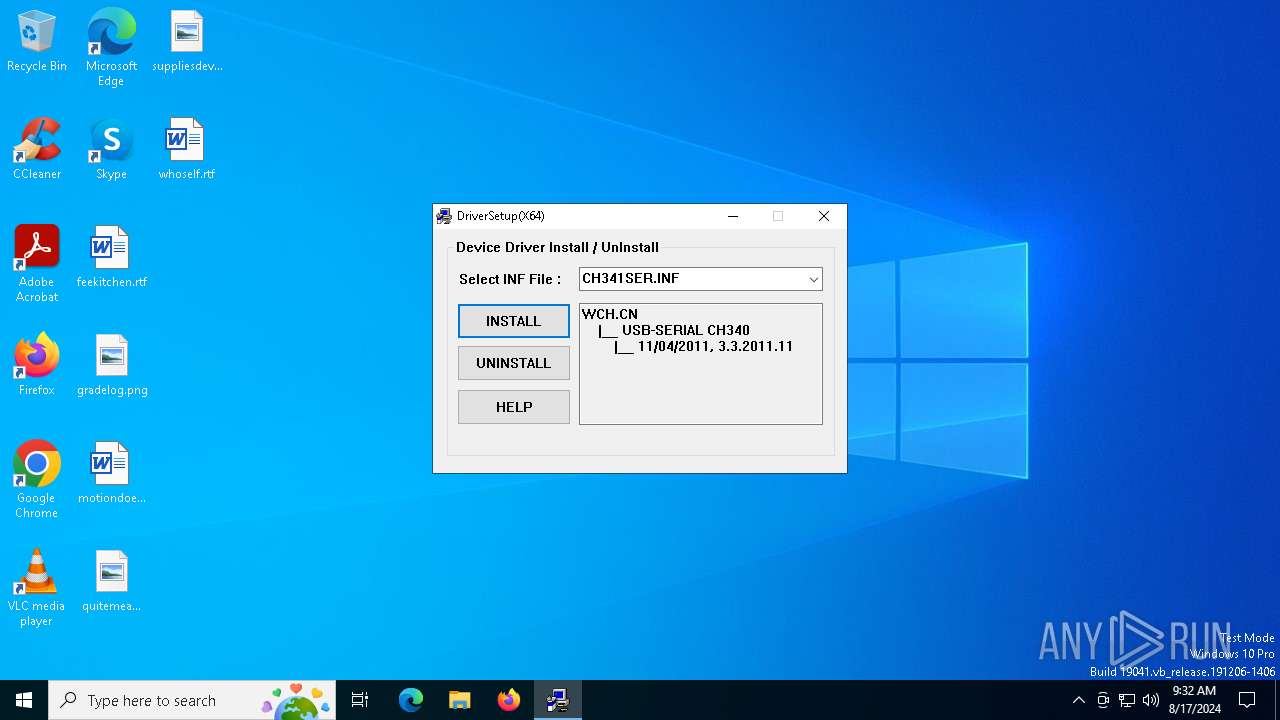
| 6432 | "C:\WCH.CN\CH341SER\SETUP.EXE" | C:\WCH.CN\CH341SER\SETUP.EXE | — | CH341SER.EXE.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: EXE For Driver Installation Exit code: 3221226540 Version: 1, 6, 0, 0 Modules
| |||||||||||||||
| 6500 | "C:\WCH.CN\CH341SER\SETUP.EXE" | C:\WCH.CN\CH341SER\SETUP.EXE | CH341SER.EXE.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: EXE For Driver Installation Exit code: 0 Version: 1, 6, 0, 0 Modules
| |||||||||||||||
| 6544 | C:\WCH.CN\CH341SER\DRVSETUP64\DRVSETUP64.EXE | C:\WCH.CN\CH341SER\DRVSETUP64\DRVSETUP64.exe | — | SETUP.EXE | |||||||||||
User: admin Integrity Level: HIGH Description: EXE For Driver Installation Version: 1, 6, 0, 0 Modules
| |||||||||||||||
Total events
1 031
Read events
1 022
Write events
9
Delete events
0
Modification events
| (PID) Process: | (6344) CH341SER.EXE.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR SFX |
| Operation: | write | Name: | C%%WCH.CN%CH341SER |
Value: C:\WCH.CN\CH341SER | |||
| (PID) Process: | (6344) CH341SER.EXE.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6344) CH341SER.EXE.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6344) CH341SER.EXE.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6344) CH341SER.EXE.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
7
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6344 | CH341SER.EXE.exe | C:\WCH.CN\CH341SER\CH341SER.INF | binary | |
MD5:B768DAEDADCC5C22F204A7F9CCD72A84 | SHA256:855213B81A595AD11E2BB8738698BAF1C7EA11BE964AEB473A3BA47F778E2C75 | |||
| 6344 | CH341SER.EXE.exe | C:\WCH.CN\CH341SER\ch341SER.CAT | cat | |
MD5:1F7FE778164D85076E97B10363661CFB | SHA256:18FAB08BA0A79CC57B7A0CE8724CD17E0724B3E0A51BDBA364AE9C236D02DDDC | |||
| 6344 | CH341SER.EXE.exe | C:\WCH.CN\CH341SER\CH341S98.SYS | executable | |
MD5:B6F4A83911336E84BEAD8F8905285FAB | SHA256:0ECD1222627271EA31D3B64796992B6DAF5133D64CC26D43B3873CBE32FD59CB | |||
| 6344 | CH341SER.EXE.exe | C:\WCH.CN\CH341SER\CH341PT.DLL | executable | |
MD5:69B6FEC924C30042D329AE56CA8925CC | SHA256:45494CE819C1B5C21ABB72DC47A0CA36807E0ED74CE55B631DA174C77A9B24DB | |||
| 6344 | CH341SER.EXE.exe | C:\WCH.CN\CH341SER\SETUP.EXE | executable | |
MD5:B1A3B36F23C209DD6467B91DFDADD8EB | SHA256:64C4E60A7B5C3799FBA275082A05B68DD5B6AB03D63AF0CDB31C59BCA57297B5 | |||
| 6344 | CH341SER.EXE.exe | C:\WCH.CN\CH341SER\CH341SER.SYS | executable | |
MD5:4798C1AD22BAF6FF25451E2194E034D1 | SHA256:1E2DD8EB6CC1095F8113448724354567AA8CEAC269391CC72B7ADCBF657CD53A | |||
| 6344 | CH341SER.EXE.exe | C:\WCH.CN\CH341SER\DRVSETUP64\DRVSETUP64.exe | executable | |
MD5:6DCD5BC85A93D86C24F03942541A5678 | SHA256:552E57F3100BBF78BDA39CCE9E9CF0E3016551A9197C0757A9746E7A08E71ABA | |||
| 6344 | CH341SER.EXE.exe | C:\WCH.CN\CH341SER\CH341S64.SYS | executable | |
MD5:C58EC27035731337ADD1326880086B16 | SHA256:1A48A57D7FF5332AD380AF7884F516548DB535CFE23F3AE7D5AF291307CBC435 | |||
| 6344 | CH341SER.EXE.exe | C:\WCH.CN\CH341SER\CH341SER.VXD | executable | |
MD5:BE7438420F1DA854917F58CAD557476D | SHA256:2A946F316EDD7E1185DEEAFDC2DE52B2D2843198BE098A724233C12F9CCD0DAE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
43
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5924 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6900 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6608 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6956 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1164 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4084 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4084 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5336 | SearchApp.exe | 2.23.209.173:443 | www.bing.com | Akamai International B.V. | GB | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5924 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5924 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |