| File name: | CH341SER.EXE |
| Full analysis: | https://app.any.run/tasks/62188c39-6f8b-45b6-a62b-ac9514bea3a5 |
| Verdict: | Malicious activity |
| Analysis date: | May 26, 2025, 16:50:01 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
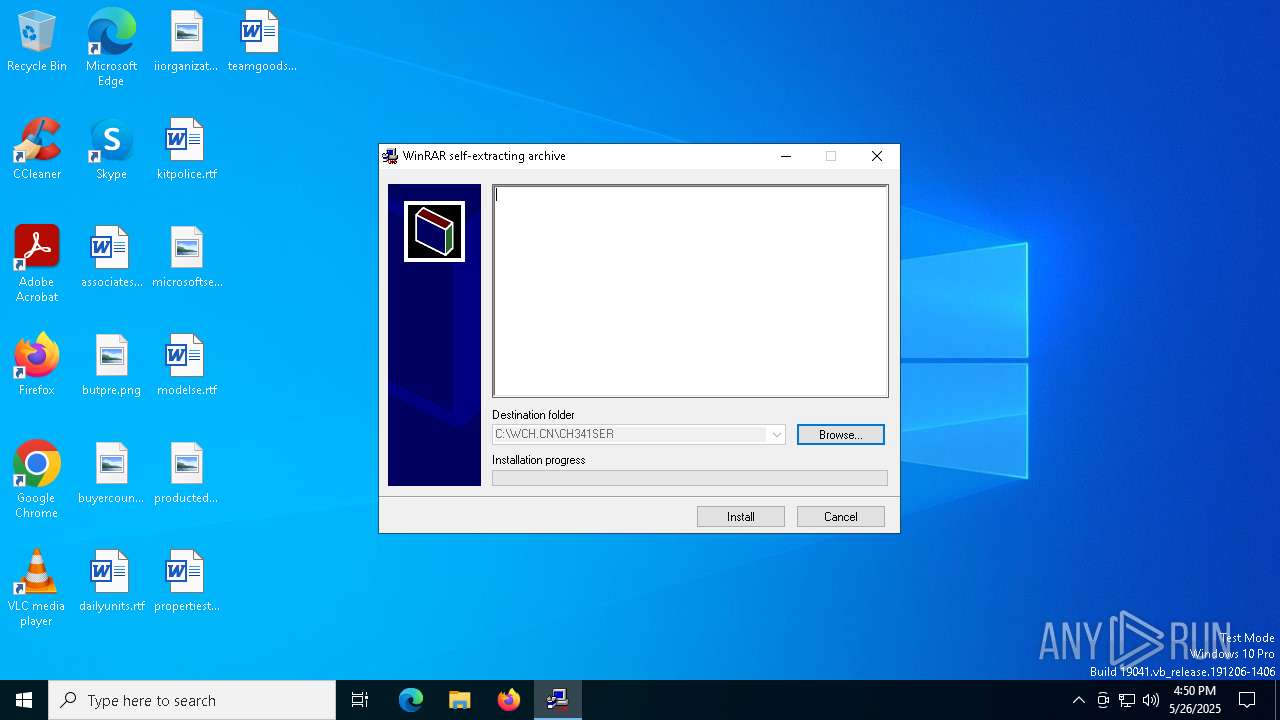
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, RAR self-extracting archive, 4 sections |
| MD5: | 1461E4F00D1F457B1EACF214FD5A2EF2 |
| SHA1: | C38D5005921D1F932EB29A57168426F06850C254 |
| SHA256: | 5C79A8C123D3FA03274FDCCC8FAD722AAF3B703DF35C39B4B42F0B5BFBB26DFD |
| SSDEEP: | 6144:h8U2qy6rRZb7jxGYXqZ9vcF/6jHLrZpEr9TI:5zy6rRxE7RrrjCJI |
MALICIOUS
Executing a file with an untrusted certificate
- SETUP.EXE (PID: 7244)
- SETUP.EXE (PID: 3192)
- DRVSETUP64.exe (PID: 7272)
SUSPICIOUS
Executable content was dropped or overwritten
- CH341SER.EXE.exe (PID: 5352)
- drvinst.exe (PID: 7592)
- DRVSETUP64.exe (PID: 7272)
Creates file in the systems drive root
- CH341SER.EXE.exe (PID: 5352)
Drops a system driver (possible attempt to evade defenses)
- drvinst.exe (PID: 7592)
- CH341SER.EXE.exe (PID: 5352)
- DRVSETUP64.exe (PID: 7272)
Creates files in the driver directory
- drvinst.exe (PID: 7592)
- DRVSETUP64.exe (PID: 7272)
Reads security settings of Internet Explorer
- CH341SER.EXE.exe (PID: 5352)
INFO
The sample compiled with english language support
- CH341SER.EXE.exe (PID: 5352)
- drvinst.exe (PID: 7592)
- DRVSETUP64.exe (PID: 7272)
Reads the computer name
- CH341SER.EXE.exe (PID: 5352)
- DRVSETUP64.exe (PID: 7272)
- drvinst.exe (PID: 7592)
Checks supported languages
- DRVSETUP64.exe (PID: 7272)
- SETUP.EXE (PID: 7244)
- drvinst.exe (PID: 7592)
- CH341SER.EXE.exe (PID: 5352)
Process checks computer location settings
- CH341SER.EXE.exe (PID: 5352)
Create files in a temporary directory
- DRVSETUP64.exe (PID: 7272)
Reads the software policy settings
- drvinst.exe (PID: 7592)
Reads the machine GUID from the registry
- drvinst.exe (PID: 7592)
The sample compiled with chinese language support
- CH341SER.EXE.exe (PID: 5352)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | WinRAR Self Extracting archive (94.3) |
|---|---|---|
| .scr | | | Windows screen saver (2.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.1) |
| .exe | | | Win32 Executable (generic) (0.8) |
| .exe | | | Win32 Executable Watcom C++ (generic) (0.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2007:05:22 04:59:14+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 5 |
| CodeSize: | 81920 |
| InitializedDataSize: | 22016 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
137
Monitored processes
8
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2096 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3192 | "C:\WCH.CN\CH341SER\SETUP.EXE" | C:\WCH.CN\CH341SER\SETUP.EXE | — | CH341SER.EXE.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: EXE For Driver Installation Exit code: 3221226540 Version: 1, 6, 0, 0 Modules
| |||||||||||||||
| 5352 | "C:\Users\admin\AppData\Local\Temp\CH341SER.EXE.exe" | C:\Users\admin\AppData\Local\Temp\CH341SER.EXE.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 7244 | "C:\WCH.CN\CH341SER\SETUP.EXE" | C:\WCH.CN\CH341SER\SETUP.EXE | CH341SER.EXE.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: EXE For Driver Installation Exit code: 0 Version: 1, 6, 0, 0 Modules
| |||||||||||||||
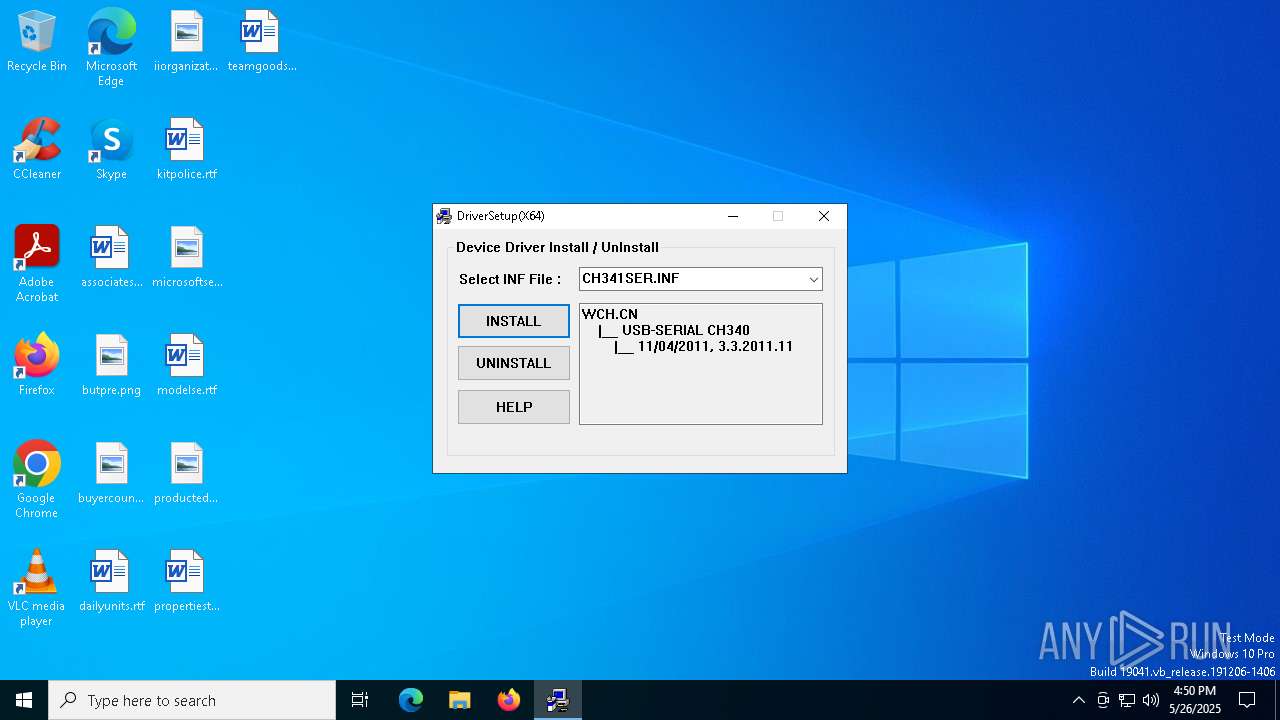
| 7272 | C:\WCH.CN\CH341SER\DRVSETUP64\DRVSETUP64.EXE | C:\WCH.CN\CH341SER\DRVSETUP64\DRVSETUP64.exe | SETUP.EXE | ||||||||||||
User: admin Integrity Level: HIGH Description: EXE For Driver Installation Exit code: 1 Version: 1, 6, 0, 0 Modules
| |||||||||||||||
| 7312 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7344 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
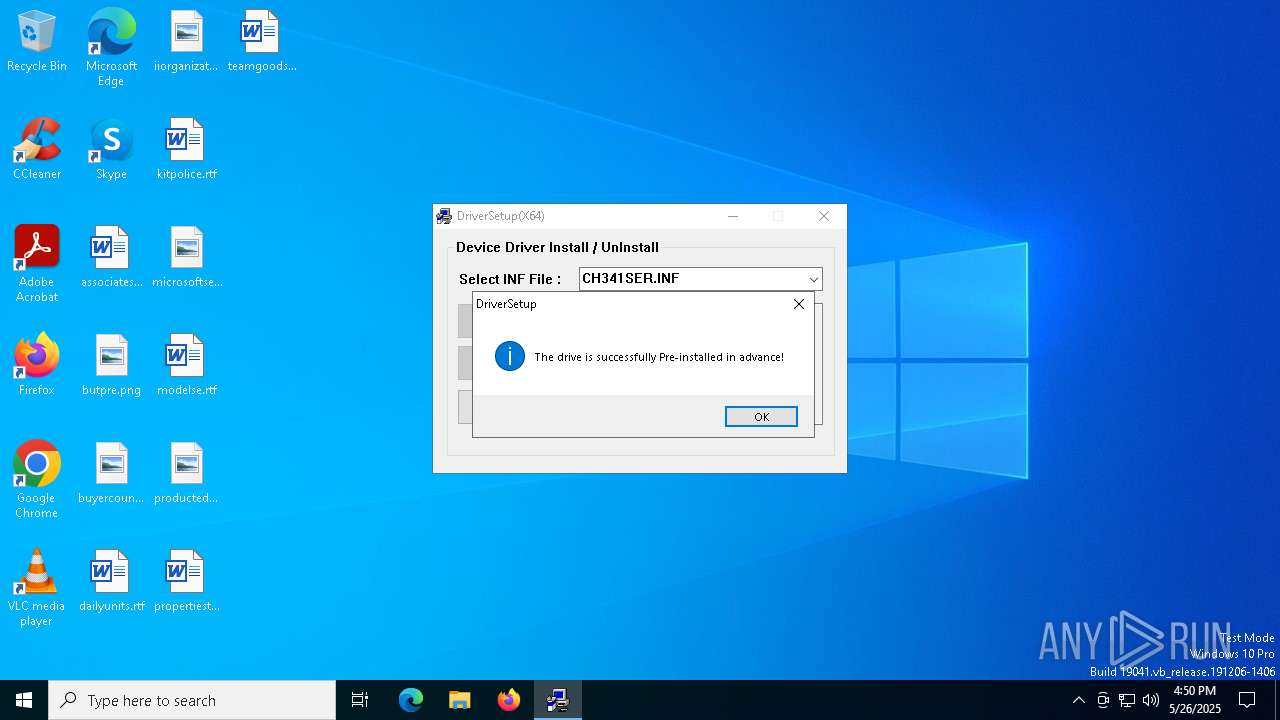
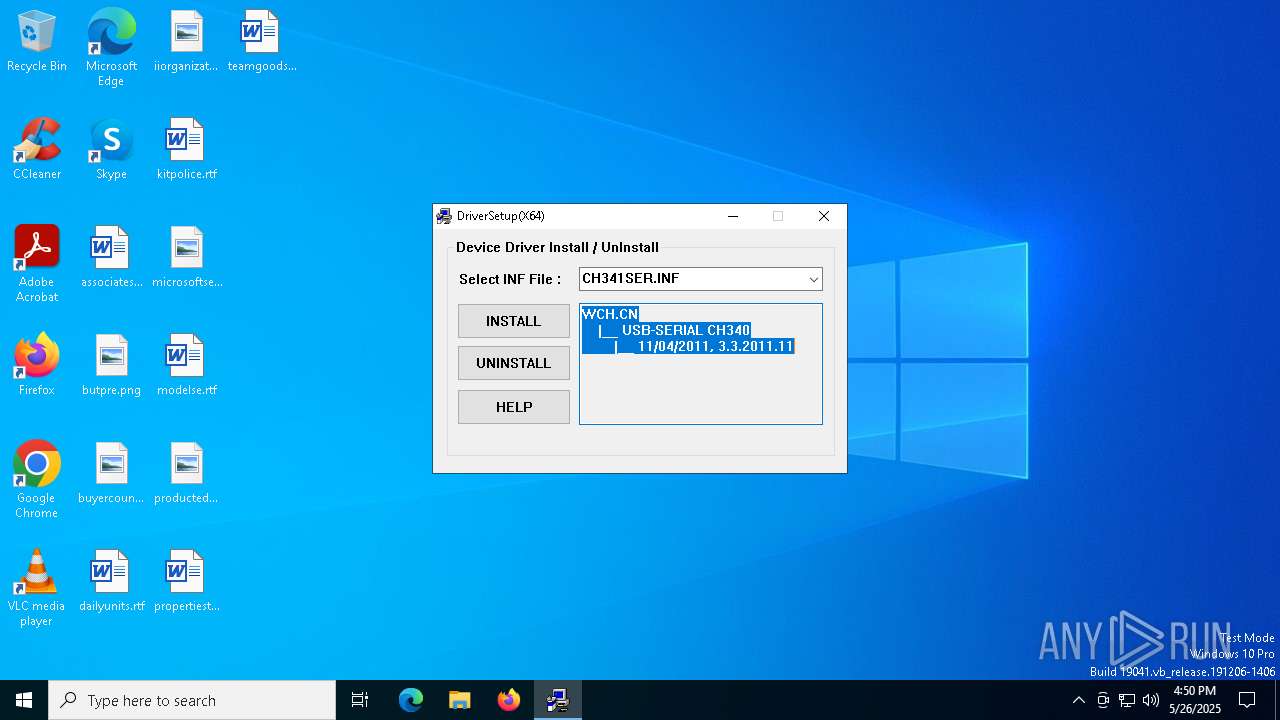
| 7592 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{de70fa13-43fd-9d42-9f78-6f27e63b4923}\CH341SER.INF" "9" "4dbd0d02f" "00000000000001D0" "WinSta0\Default" "00000000000001D8" "208" "C:\WCH.CN\CH341SER" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 557
Read events
3 555
Write events
2
Delete events
0
Modification events
| (PID) Process: | (5352) CH341SER.EXE.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR SFX |
| Operation: | write | Name: | C%%WCH.CN%CH341SER |
Value: C:\WCH.CN\CH341SER | |||
| (PID) Process: | (7272) DRVSETUP64.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\Setup\SetupapiLogStatus |
| Operation: | write | Name: | setupapi.dev.log |
Value: 4096 | |||
Executable files
41
Suspicious files
11
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5352 | CH341SER.EXE.exe | C:\WCH.CN\CH341SER\ch341SER.CAT | binary | |
MD5:1F7FE778164D85076E97B10363661CFB | SHA256:18FAB08BA0A79CC57B7A0CE8724CD17E0724B3E0A51BDBA364AE9C236D02DDDC | |||
| 5352 | CH341SER.EXE.exe | C:\WCH.CN\CH341SER\DRVSETUP64\DRVSETUP64.exe | executable | |
MD5:6DCD5BC85A93D86C24F03942541A5678 | SHA256:552E57F3100BBF78BDA39CCE9E9CF0E3016551A9197C0757A9746E7A08E71ABA | |||
| 5352 | CH341SER.EXE.exe | C:\WCH.CN\CH341SER\CH341S98.SYS | executable | |
MD5:B6F4A83911336E84BEAD8F8905285FAB | SHA256:0ECD1222627271EA31D3B64796992B6DAF5133D64CC26D43B3873CBE32FD59CB | |||
| 5352 | CH341SER.EXE.exe | C:\WCH.CN\CH341SER\CH341S64.SYS | executable | |
MD5:C58EC27035731337ADD1326880086B16 | SHA256:1A48A57D7FF5332AD380AF7884F516548DB535CFE23F3AE7D5AF291307CBC435 | |||
| 5352 | CH341SER.EXE.exe | C:\WCH.CN\CH341SER\SETUP.EXE | executable | |
MD5:B1A3B36F23C209DD6467B91DFDADD8EB | SHA256:64C4E60A7B5C3799FBA275082A05B68DD5B6AB03D63AF0CDB31C59BCA57297B5 | |||
| 7272 | DRVSETUP64.exe | C:\Users\admin\AppData\Local\Temp\{de70fa13-43fd-9d42-9f78-6f27e63b4923}\CH341SER.CAT | binary | |
MD5:1F7FE778164D85076E97B10363661CFB | SHA256:18FAB08BA0A79CC57B7A0CE8724CD17E0724B3E0A51BDBA364AE9C236D02DDDC | |||
| 5352 | CH341SER.EXE.exe | C:\WCH.CN\CH341SER\CH341PT.DLL | executable | |
MD5:69B6FEC924C30042D329AE56CA8925CC | SHA256:45494CE819C1B5C21ABB72DC47A0CA36807E0ED74CE55B631DA174C77A9B24DB | |||
| 7272 | DRVSETUP64.exe | C:\Windows\INF\setupapi.dev.log | text | |
MD5:D2461D1A9217697759115F5ECB4723A6 | SHA256:48695F870BFF7199D978239B7E7237B54E89EF41530E58B61F346F04598B2EA7 | |||
| 7272 | DRVSETUP64.exe | C:\Users\admin\AppData\Local\Temp\{de70fa13-43fd-9d42-9f78-6f27e63b4923}\SETDE6B.tmp | binary | |
MD5:1F7FE778164D85076E97B10363661CFB | SHA256:18FAB08BA0A79CC57B7A0CE8724CD17E0724B3E0A51BDBA364AE9C236D02DDDC | |||
| 7272 | DRVSETUP64.exe | C:\Users\admin\AppData\Local\Temp\{de70fa13-43fd-9d42-9f78-6f27e63b4923}\CH341PT.DLL | executable | |
MD5:69B6FEC924C30042D329AE56CA8925CC | SHA256:45494CE819C1B5C21ABB72DC47A0CA36807E0ED74CE55B631DA174C77A9B24DB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
20
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8064 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8064 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
— | — | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |