| File name: | 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe |
| Full analysis: | https://app.any.run/tasks/ce1c3f2e-cd89-493b-b81f-dfc3bad90893 |
| Verdict: | Malicious activity |
| Analysis date: | March 05, 2024, 13:47:39 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | 5A1233C02E6CC4579E49D7202D847A2D |
| SHA1: | 57A710D0FDB3EF443A02382F933F591A6493EE74 |
| SHA256: | 5C53130B90F4F30685808B7B19A04751FB4EA3B922F5FAB599DF88BBE7CFC529 |
| SSDEEP: | 49152:xKEkzIzb9f9QL03ABBjBzwbZVrZFtqE+bHxXW2E+6ikhHMP/+4kUM:xKEhf9QLzvj2bXan04 |
MALICIOUS
Scans artifacts that could help determine the target
- 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe (PID: 652)
Runs injected code in another process
- powershell.exe (PID: 6600)
Application was injected by another process
- powershell.exe (PID: 2368)
Drops the executable file immediately after the start
- 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe (PID: 652)
SUSPICIOUS
Reads Microsoft Outlook installation path
- 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe (PID: 652)
Starts CMD.EXE for commands execution
- 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe (PID: 652)
The process executes Powershell scripts
- 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe (PID: 652)
Possibly malicious use of IEX has been detected
- 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe (PID: 652)
- powershell.exe (PID: 6392)
Reads security settings of Internet Explorer
- 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe (PID: 652)
Identifying current user with WHOAMI command
- 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe (PID: 652)
- powershell.exe (PID: 6392)
- powershell.exe (PID: 6600)
- powershell.exe (PID: 2368)
Starts POWERSHELL.EXE for commands execution
- 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe (PID: 652)
- powershell.exe (PID: 6392)
Reads Internet Explorer settings
- 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe (PID: 652)
The process bypasses the loading of PowerShell profile settings
- 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe (PID: 652)
- powershell.exe (PID: 6392)
Probably obfuscated PowerShell command line is found
- powershell.exe (PID: 6392)
Application launched itself
- powershell.exe (PID: 6392)
Starts SC.EXE for service management
- powershell.exe (PID: 6600)
Searches for installed software
- dllhost.exe (PID: 7052)
The Powershell connects to the Internet
- powershell.exe (PID: 6392)
Executes as Windows Service
- VSSVC.exe (PID: 6836)
Unusual connection from system programs
- powershell.exe (PID: 6392)
INFO
Checks proxy server information
- 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe (PID: 652)
- powershell.exe (PID: 6392)
- slui.exe (PID: 7124)
Reads the computer name
- 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe (PID: 652)
Process checks Internet Explorer phishing filters
- 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe (PID: 652)
Create files in a temporary directory
- powershell.exe (PID: 6600)
Reads the software policy settings
- powershell.exe (PID: 6600)
- slui.exe (PID: 7124)
Reads security settings of Internet Explorer
- powershell.exe (PID: 6600)
Checks supported languages
- 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe (PID: 652)
Creates files or folders in the user directory
- 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe (PID: 652)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2023:07:08 05:26:14+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 10 |
| CodeSize: | 910336 |
| InitializedDataSize: | 443904 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xcdb10 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.1.37.1 |
| ProductVersionNumber: | 1.1.37.1 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileDescription: | - |
| FileVersion: | 1.1.37.01 |
| InternalName: | - |
| LegalCopyright: | - |
| CompanyName: | - |
| OriginalFileName: | - |
| ProductName: | - |
| ProductVersion: | 1.1.37.01 |
Total processes
203
Monitored processes
29
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 652 | "C:\Users\admin\AppData\Local\Temp\5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe" | C:\Users\admin\AppData\Local\Temp\5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.1.37.01 Modules
| |||||||||||||||
| 816 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | takeown.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 904 | "C:\WINDOWS\system32\icacls.exe" "C:\WINDOWS\system32\themeui.dll" /grant SYSTEM:F | C:\Windows\System32\icacls.exe | — | ThemePatcher.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1296 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1380 | "C:\WINDOWS\system32\whoami.exe" /user | C:\Windows\System32\whoami.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: whoami - displays logged on user information Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1816 | "C:\WINDOWS\system32\takeown.exe" /f "C:\WINDOWS\system32\themeui.dll" | C:\Windows\System32\takeown.exe | — | ThemePatcher.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Takes ownership of a file Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
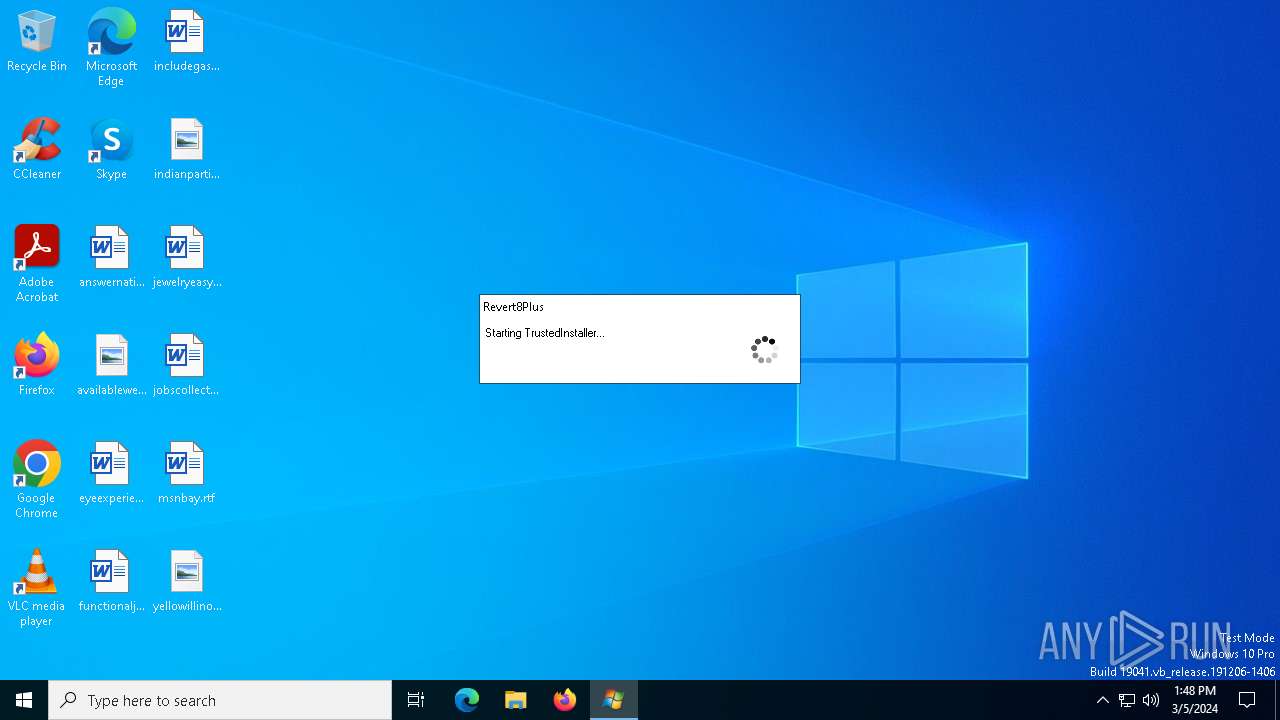
| 2368 | powershell -win 1 -nop -c iex $env:R; # RunAsTI | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | TrustedInstaller.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2940 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | takeown.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2984 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | takeown.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3040 | "C:\WINDOWS\system32\takeown.exe" /f "C:\WINDOWS\system32\themeui.dll" | C:\Windows\System32\takeown.exe | — | ThemePatcher.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Takes ownership of a file Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
20 380
Read events
20 120
Write events
237
Delete events
23
Modification events
| (PID) Process: | (652) 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (652) 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (652) 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (652) 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (652) 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (652) 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (652) 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (652) 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe | Key: | HKEY_CURRENT_USER\Volatile Environment |
| Operation: | write | Name: | R8PUSER |
Value: admin | |||
| (PID) Process: | (652) 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe | Key: | HKEY_CURRENT_USER\Volatile Environment |
| Operation: | write | Name: | R8PCMD |
Value: C:\Users\admin\AppData\Local\Temp\5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe | |||
| (PID) Process: | (652) 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\GPU |
| Operation: | write | Name: | AdapterInfo |
Value: vendorId="0x1414",deviceID="0x8c",subSysID="0x0",revision="0x0",version="10.0.19041.546"hypervisor="No Hypervisor (No SLAT)" | |||
Executable files
0
Suspicious files
2
Text files
9
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7052 | dllhost.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 6392 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_f4hfkj3u.lye.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7052 | dllhost.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{707170d6-4a41-4676-b2ee-ec74987e481b}_OnDiskSnapshotProp | binary | |
MD5:44719808A97A155864D7CB2C9D01076B | SHA256:2C7AE781CB96819AEAE9362C58B92D8F7251A2A439134C849FAF2452CD2A1D41 | |||
| 652 | 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\loader[1].gif | image | |
MD5:51051238A295D5A6AD89789CC8D2F802 | SHA256:D8AA833309B6C47B08E8C0812071C5DFFE8871BB074D118C9FCF4EE0A79336B1 | |||
| 2368 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_lhts2ree.4bd.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6600 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ohzjvfts.hgr.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6392 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\CLR_v4.0\UsageLogs\powershell.exe.log | text | |
MD5:E05D010E07FC79F5AC1F0E6D5A63BE68 | SHA256:D06594E825F0A1D736810A3AC51341D318FE1918760E676E7F42AFDC5D8A0C8E | |||
| 2368 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_oknryzqp.gud.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6392 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_0q1vf4pf.ldz.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 652 | 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\loader[1].htm | html | |
MD5:EA8CF6B77FAF31DB850FF5440B208CE7 | SHA256:0743E34940865862DD0172B09C955EEB8956DD5C5761E39DE8564BBE94D45752 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
37
DNS requests
16
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
652 | 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe | GET | 200 | 35.185.44.232:80 | http://revert8plus.gitlab.io/release/loader.html | unknown | html | 201 b | unknown |
652 | 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe | GET | 200 | 35.185.44.232:80 | http://revert8plus.gitlab.io/release/loader.gif | unknown | image | 81.9 Kb | unknown |
6392 | powershell.exe | GET | 200 | 35.185.44.232:80 | http://revert8plus.gitlab.io/release/ti.ps1 | unknown | text | 3.67 Kb | unknown |
6904 | svchost.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | binary | 1.01 Kb | unknown |
5928 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
6500 | 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe | GET | 200 | 35.185.44.232:80 | http://revert8plus.gitlab.io/release/loader.html | unknown | html | 201 b | unknown |
1268 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
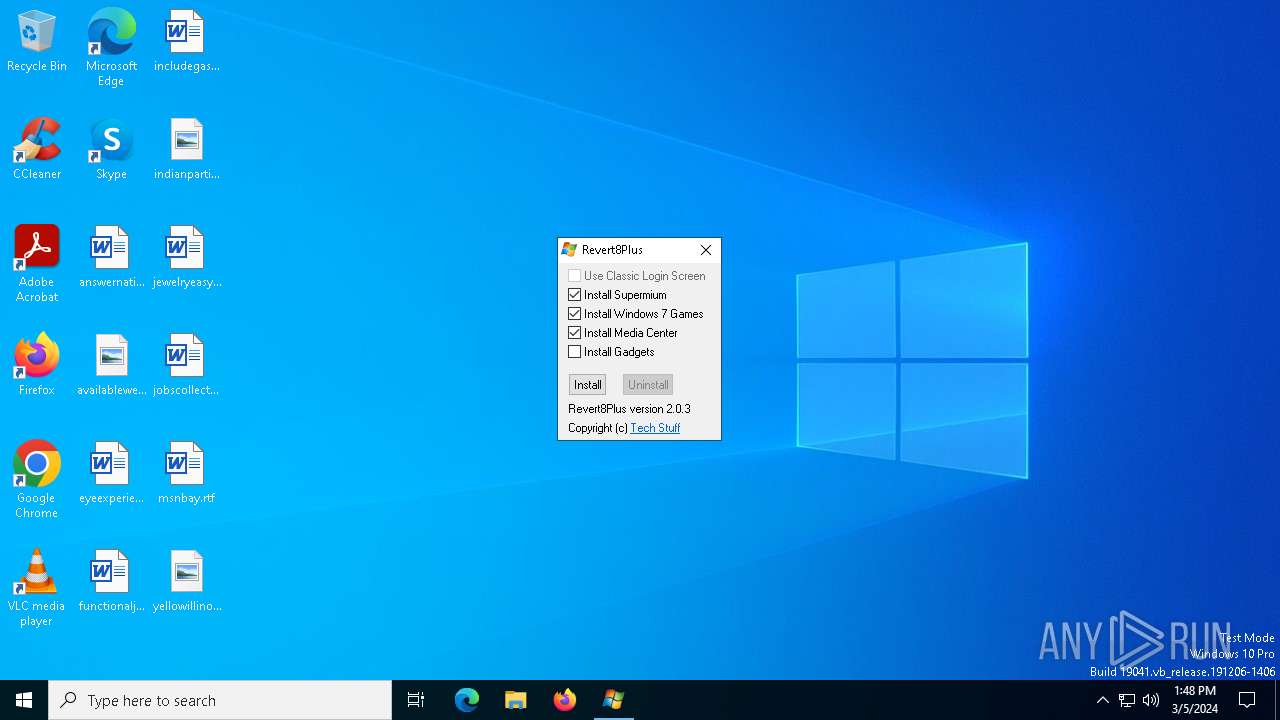
6500 | 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe | GET | 200 | 35.185.44.232:80 | http://revert8plus.gitlab.io/release/Windows.zip | unknown | compressed | 45.2 Mb | unknown |
2464 | svchost.exe | GET | 200 | 2.19.245.44:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
6500 | 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe | GET | 200 | 35.185.44.232:80 | http://revert8plus.gitlab.io/release/Themes.zip | unknown | compressed | 59.6 Mb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6904 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5928 | svchost.exe | 20.190.160.20:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3848 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
6896 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
652 | 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe | 35.185.44.232:80 | revert8plus.gitlab.io | GOOGLE-CLOUD-PLATFORM | US | unknown |
6392 | powershell.exe | 35.185.44.232:80 | revert8plus.gitlab.io | GOOGLE-CLOUD-PLATFORM | US | unknown |
5928 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6904 | svchost.exe | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
revert8plus.gitlab.io |
| unknown |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |
mhoefs.eu |
| unknown |
x1.c.lencr.org |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6392 | powershell.exe | Potentially Bad Traffic | ET INFO PS1 Powershell File Request |
6392 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
6500 | 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (AutoHotkey) |
6392 | powershell.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Windows security identifiers S-1-5-18 (NT AuthoritySystem) was detected |
6392 | powershell.exe | Potentially Bad Traffic | ET ATTACK_RESPONSE PowerShell NoProfile Command Received In Powershell Stagers |
6500 | 5c53130b90f4f30685808b7b19a04751fb4ea3b922f5fab599df88bbe7cfc529.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (AutoHotkey) |
1 ETPRO signatures available at the full report