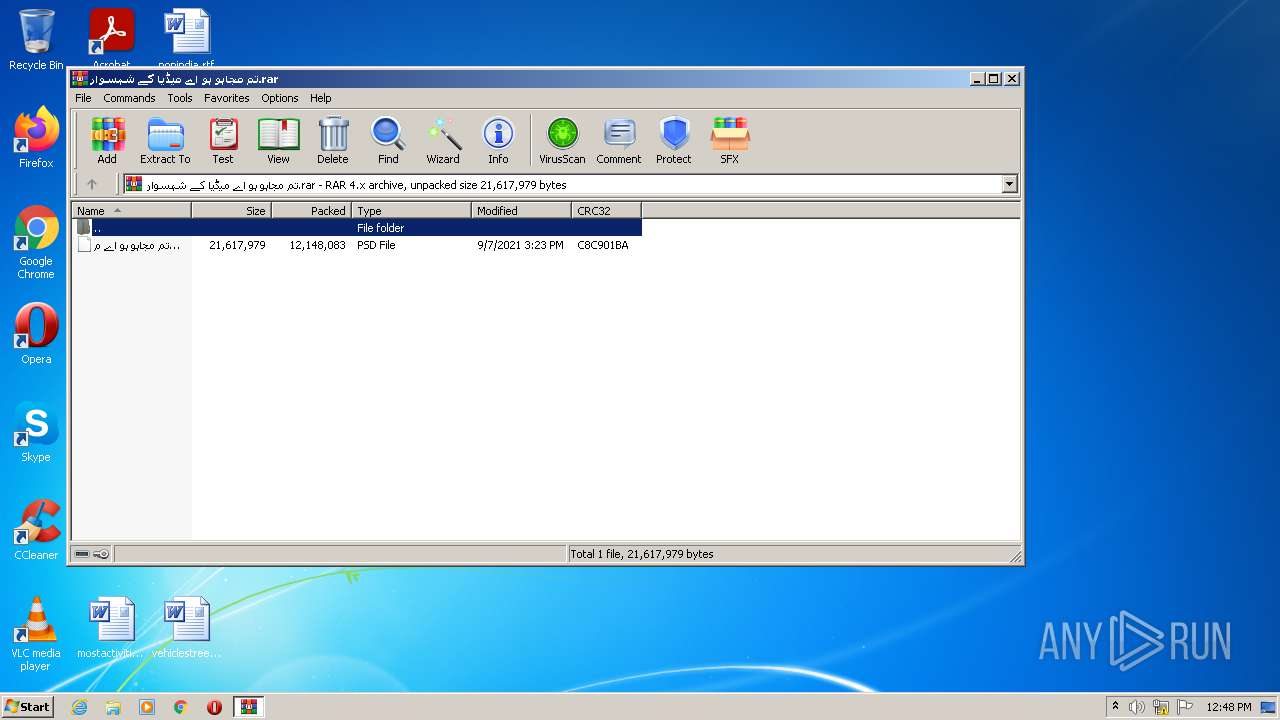
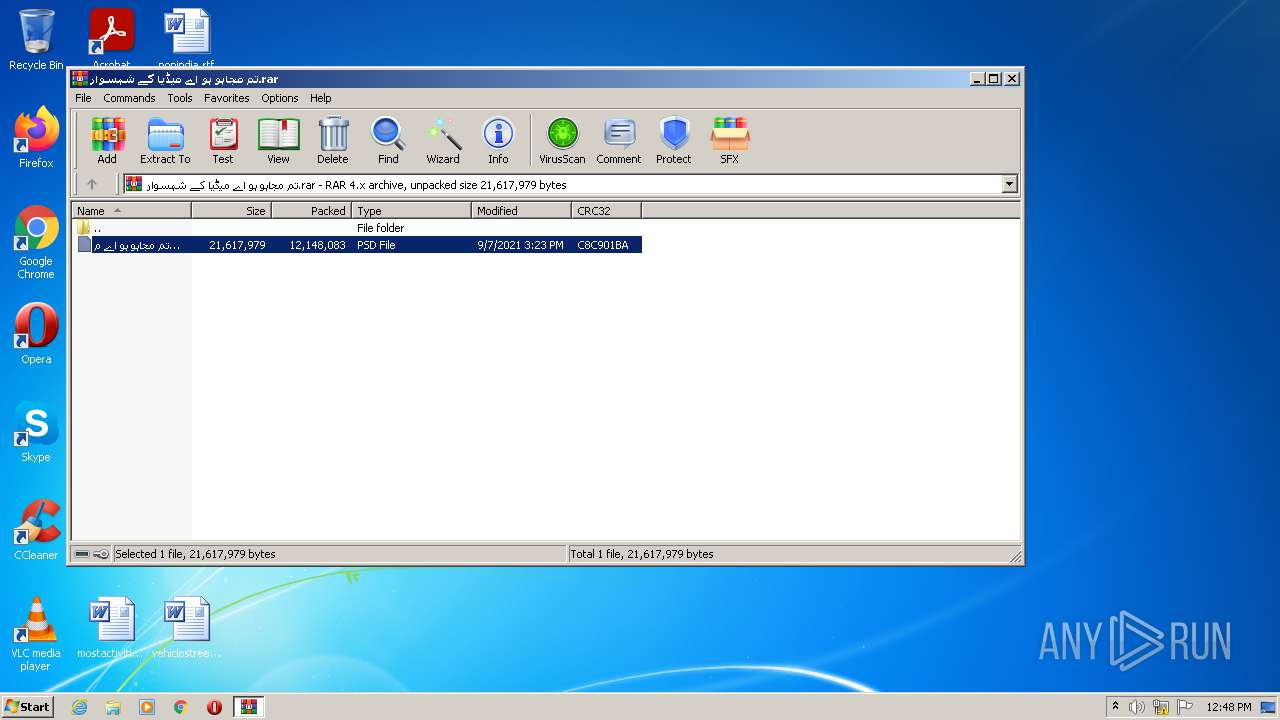
| File name: | تم مجاہو ہو اے میڈیا کے شہسوار.rar |
| Full analysis: | https://app.any.run/tasks/9e8a74c9-773e-49e8-bfd5-0dbd3b309929 |
| Verdict: | Malicious activity |
| Analysis date: | September 09, 2021, 11:48:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 9CA6B654F9B7F20F737767BB2BB8EE18 |
| SHA1: | 8BF804DA8FCBF57E0258EFC31E63BAE1809C2612 |
| SHA256: | 5C524586431210AA3A6C4537D4CBB174BC0746FAB24BA1078B079CDEAEF0F57F |
| SSDEEP: | 196608:yjS+oUznBtJrZVer6VlfVgQHRBTSewC+qmEWRLFORF9wCKiW421DhBfjFDBgOzja:WSjiBLnf3R5SrC+qXWNFOtKiWr1BjNBK |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 1072)
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 4056)
Checks supported languages
- WinRAR.exe (PID: 1072)
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 4056)
Uses RUNDLL32.EXE to load library
- WinRAR.exe (PID: 1072)
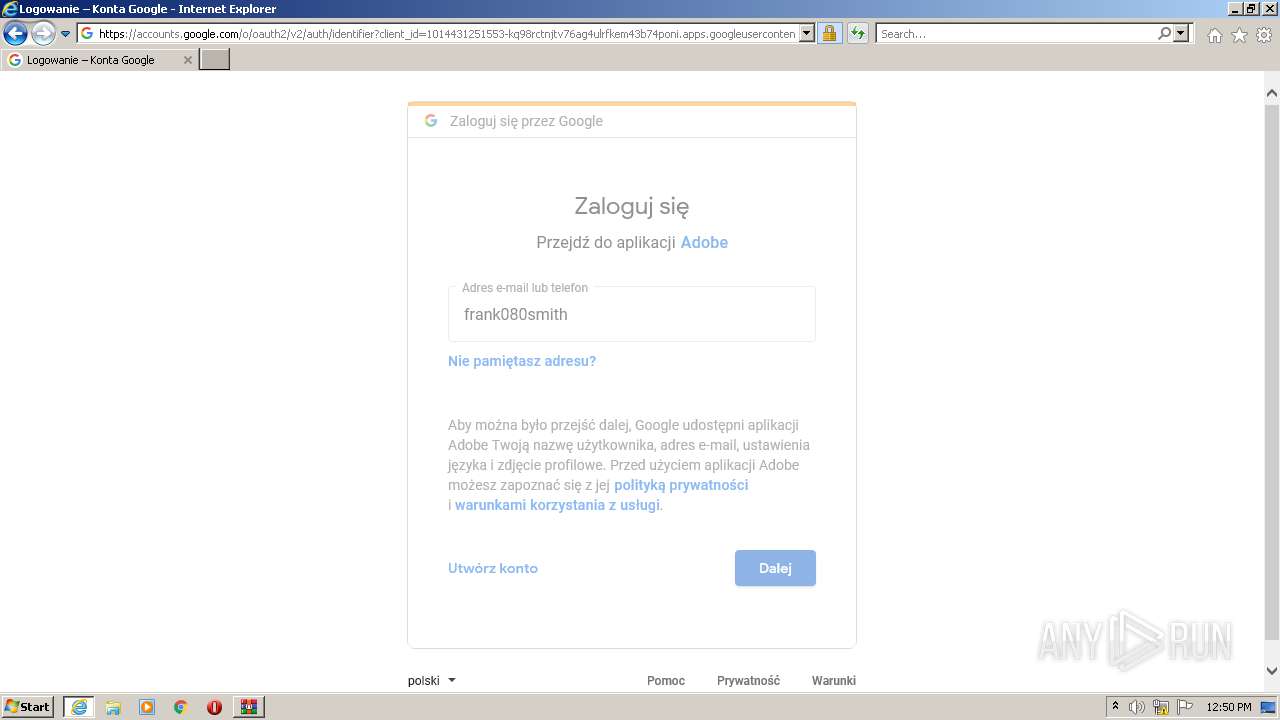
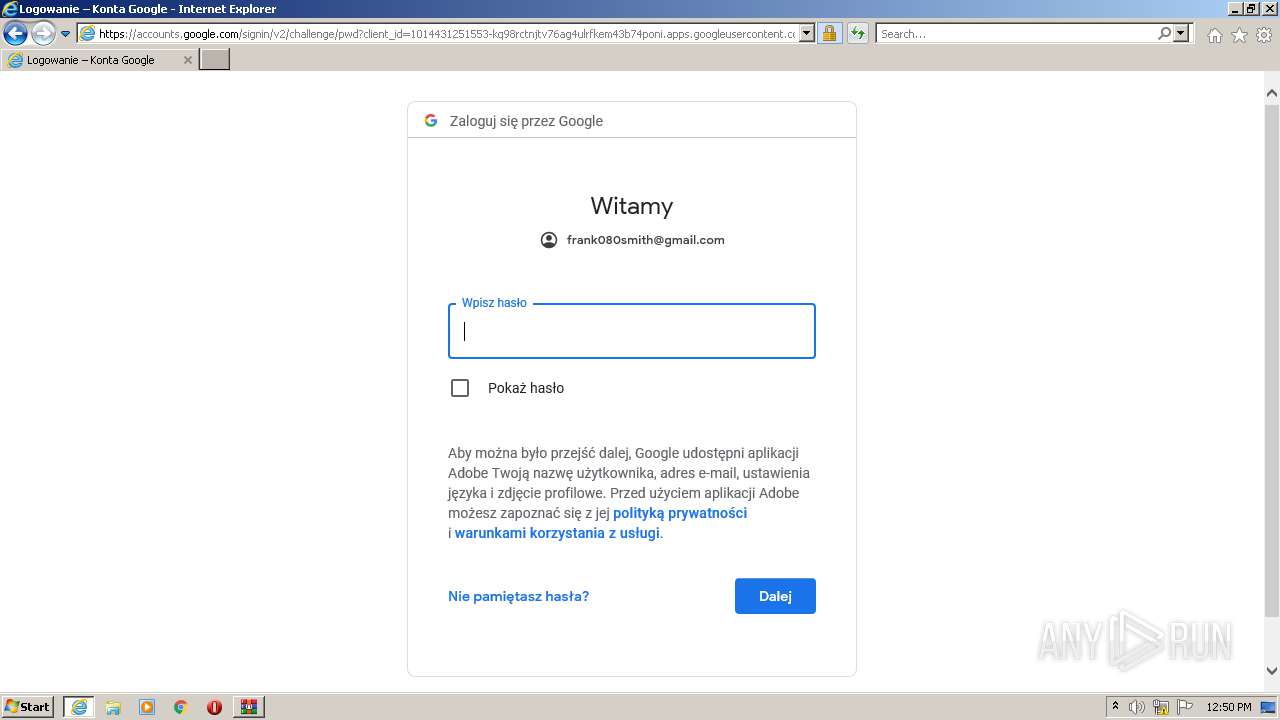
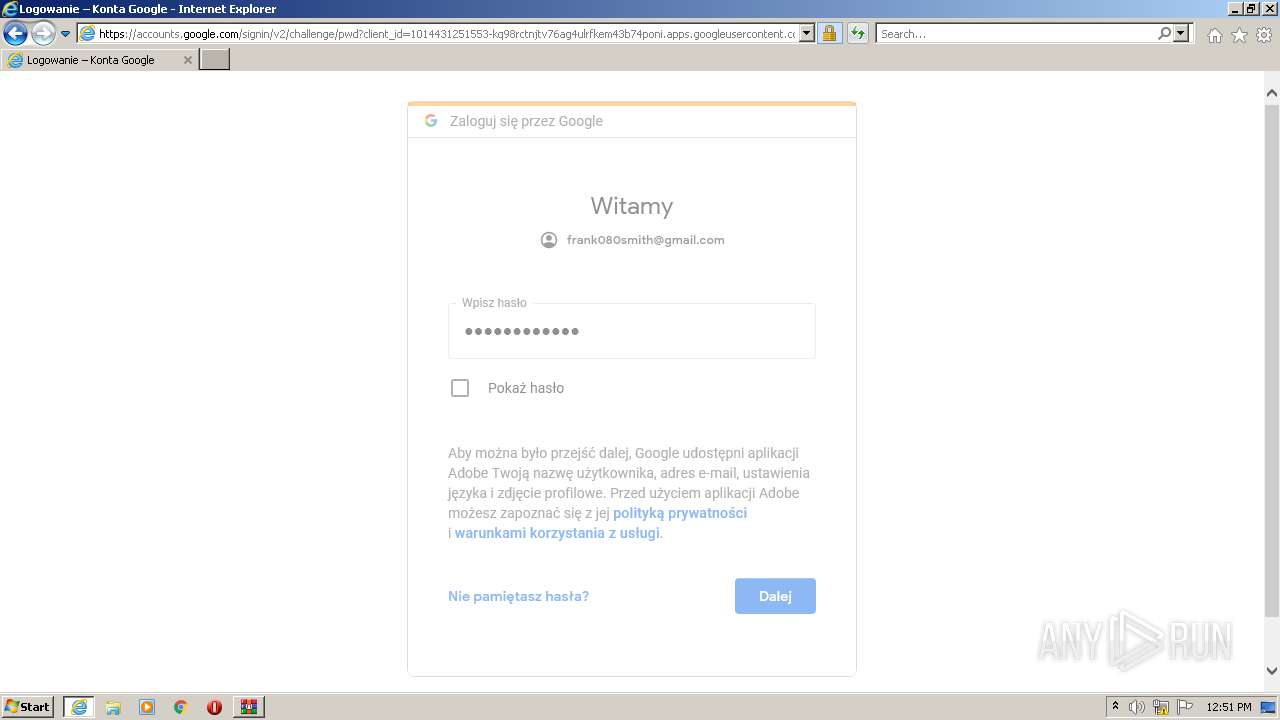
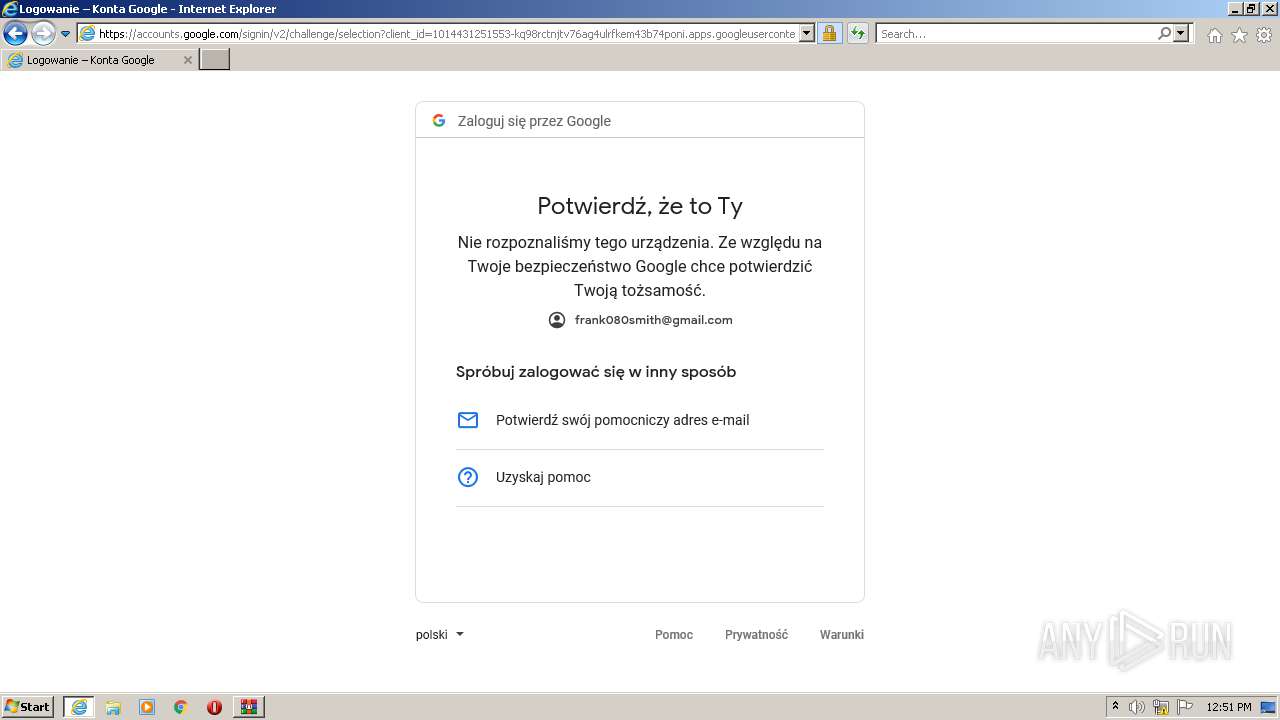
Starts Internet Explorer
- rundll32.exe (PID: 2196)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2396)
- iexplore.exe (PID: 300)
Executed via COM
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 4056)
Creates files in the user directory
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 4056)
INFO
Checks supported languages
- rundll32.exe (PID: 2196)
- iexplore.exe (PID: 2396)
- iexplore.exe (PID: 300)
Reads the computer name
- rundll32.exe (PID: 2196)
- iexplore.exe (PID: 300)
- iexplore.exe (PID: 2396)
Changes internet zones settings
- iexplore.exe (PID: 300)
Application launched itself
- iexplore.exe (PID: 300)
Reads settings of System Certificates
- iexplore.exe (PID: 2396)
- iexplore.exe (PID: 300)
Reads internet explorer settings
- iexplore.exe (PID: 2396)
Checks Windows Trust Settings
- iexplore.exe (PID: 300)
- iexplore.exe (PID: 2396)
Reads CPU info
- iexplore.exe (PID: 2396)
Creates files in the user directory
- iexplore.exe (PID: 300)
- iexplore.exe (PID: 2396)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 300)
- iexplore.exe (PID: 2396)
Changes settings of System certificates
- iexplore.exe (PID: 300)
Adds / modifies Windows certificates
- iexplore.exe (PID: 300)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| ArchivedFileName: | ?? ????? ?? ?? ????? ?? ??????.psd |
|---|---|
| PackingMethod: | Best Compression |
| ModifyDate: | 2021:09:07 15:23:03 |
| OperatingSystem: | Win32 |
| UncompressedSize: | 21617979 |
| CompressedSize: | 12148179 |
Total processes
39
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Program Files\Internet Explorer\iexplore.exe" http://go.microsoft.com/fwlink/?LinkId=57426&Ext=psd | C:\Program Files\Internet Explorer\iexplore.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1072 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\?? ????? ?? ?? ????? ?? ??????.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
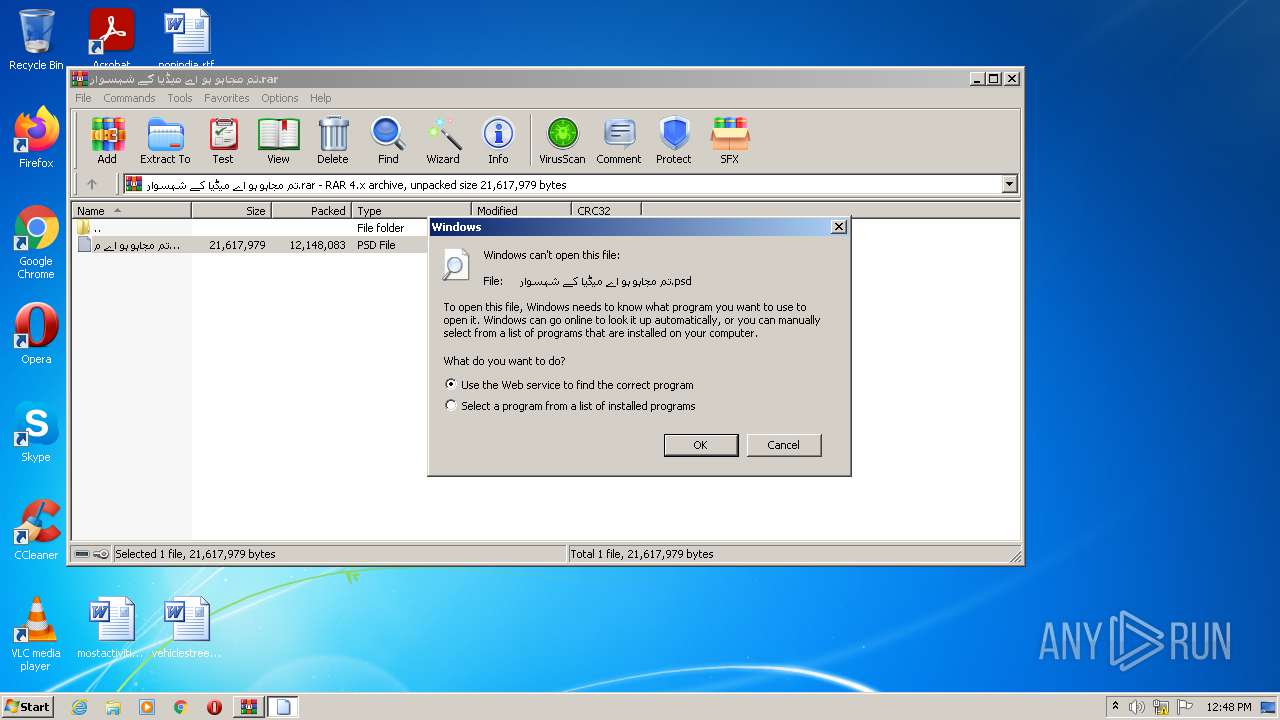
| 2196 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIa1072.27648\?? ????? ?? ?? ????? ?? ??????.psd | C:\Windows\system32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2396 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:300 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 4056 | C:\Windows\system32\Macromed\Flash\FlashUtil32_32_0_0_453_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_32_0_0_453_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Integrity Level: MEDIUM Description: Adobe� Flash� Player Installer/Uninstaller 32.0 r0 Exit code: 0 Version: 32,0,0,453 Modules
| |||||||||||||||
Total events
30 609
Read events
30 278
Write events
327
Delete events
4
Modification events
| (PID) Process: | (1072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1072) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\171\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\?? ????? ?? ?? ????? ?? ??????.rar | |||
| (PID) Process: | (1072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (300) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (300) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
Executable files
0
Suspicious files
68
Text files
648
Unknown types
100
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1072 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa1072.27648\?? ????? ?? ?? ????? ?? ??????.psd | — | |
MD5:— | SHA256:— | |||
| 2396 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 300 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_1DC6D7385EA816C957BA2B715AC5C442 | der | |
MD5:— | SHA256:— | |||
| 2396 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\82CB34DD3343FE727DF8890D352E0D8F | der | |
MD5:— | SHA256:— | |||
| 2396 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\TS439FUK.txt | text | |
MD5:— | SHA256:— | |||
| 2396 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\82CB34DD3343FE727DF8890D352E0D8F | binary | |
MD5:— | SHA256:— | |||
| 2396 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\GD8FS8J5.txt | text | |
MD5:— | SHA256:— | |||
| 2396 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 2396 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:— | SHA256:— | |||
| 300 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_1DC6D7385EA816C957BA2B715AC5C442 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
64
TCP/UDP connections
355
DNS requests
124
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2396 | iexplore.exe | GET | 301 | 2.16.186.24:80 | http://shell.windows.com/fileassoc/fileassoc.asp?Ext=psd | unknown | — | — | whitelisted |
2396 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAo1CNVcKSsBffitZcAP9%2BQ%3D | US | der | 471 b | whitelisted |
300 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
2396 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQQX6Z6gAidtSefNc6DC0OInqPHDQQUD4BhHIIxYdUvKOeNRji0LOHG2eICEAFEfh93RaX465jSR9qTD3Y%3D | US | der | 471 b | whitelisted |
2396 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/Omniroot2025.crl | US | der | 7.68 Kb | whitelisted |
2396 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTk45WiKdPUwcMf8JgMC07ACYqr2AQUt2ui6qiqhIx56rTaD5iyxZV2ufQCEA4L%2FZVyq6z%2FcS%2Bd7t0mPME%3D | US | der | 471 b | whitelisted |
2396 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTk45WiKdPUwcMf8JgMC07ACYqr2AQUt2ui6qiqhIx56rTaD5iyxZV2ufQCEAR01OSeHJor2P8HiOg6iA4%3D | US | der | 471 b | whitelisted |
2396 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEA6QE5QTl%2FQKLUlpbSkPn%2BI%3D | US | der | 471 b | whitelisted |
2396 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
2396 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2396 | iexplore.exe | 104.111.242.51:443 | go.microsoft.com | Akamai International B.V. | NL | unknown |
2396 | iexplore.exe | 23.32.238.178:80 | ctldl.windowsupdate.com | XO Communications | US | suspicious |
2396 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
300 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
300 | iexplore.exe | 23.32.238.178:80 | ctldl.windowsupdate.com | XO Communications | US | suspicious |
300 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2396 | iexplore.exe | 2.16.186.24:80 | shell.windows.com | Akamai International B.V. | — | whitelisted |
2396 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2396 | iexplore.exe | 20.190.160.132:443 | login.microsoftonline.com | Microsoft Corporation | US | suspicious |
2396 | iexplore.exe | 131.253.33.200:443 | www2.bing.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |
shell.windows.com |
| whitelisted |
login.microsoftonline.com |
| whitelisted |
login.live.com |
| whitelisted |
www2.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2396 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2396 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |