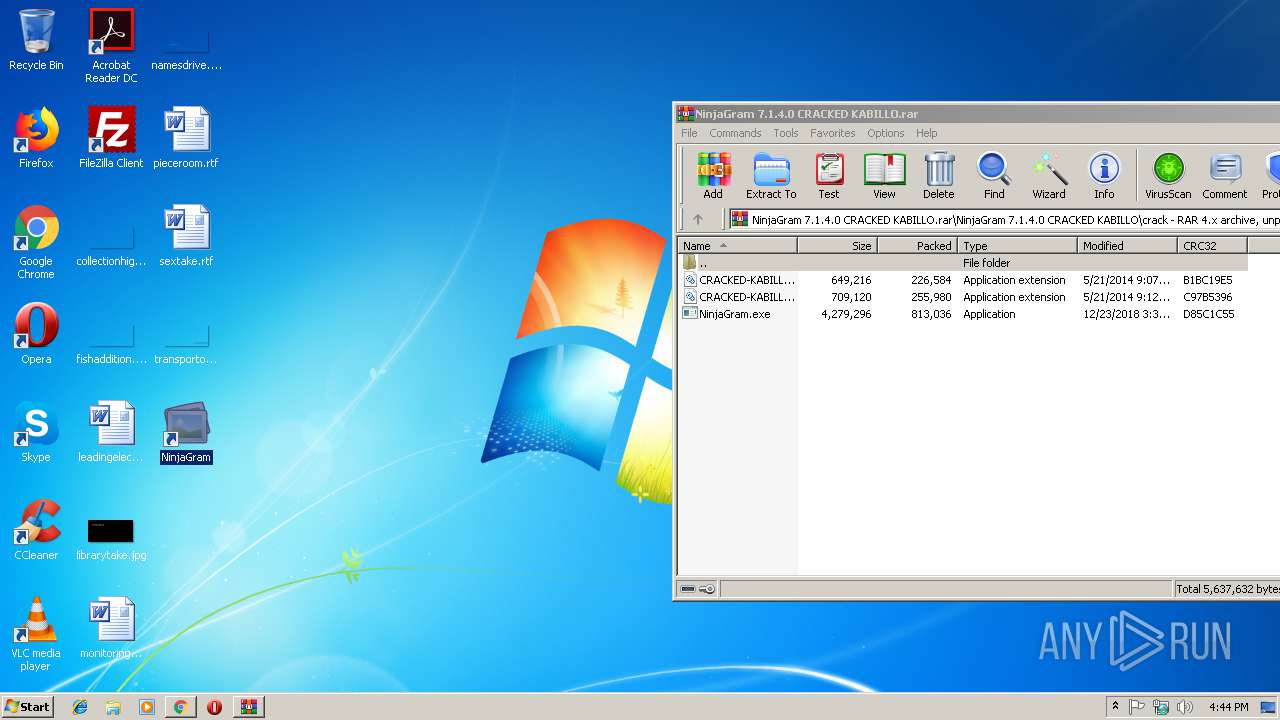
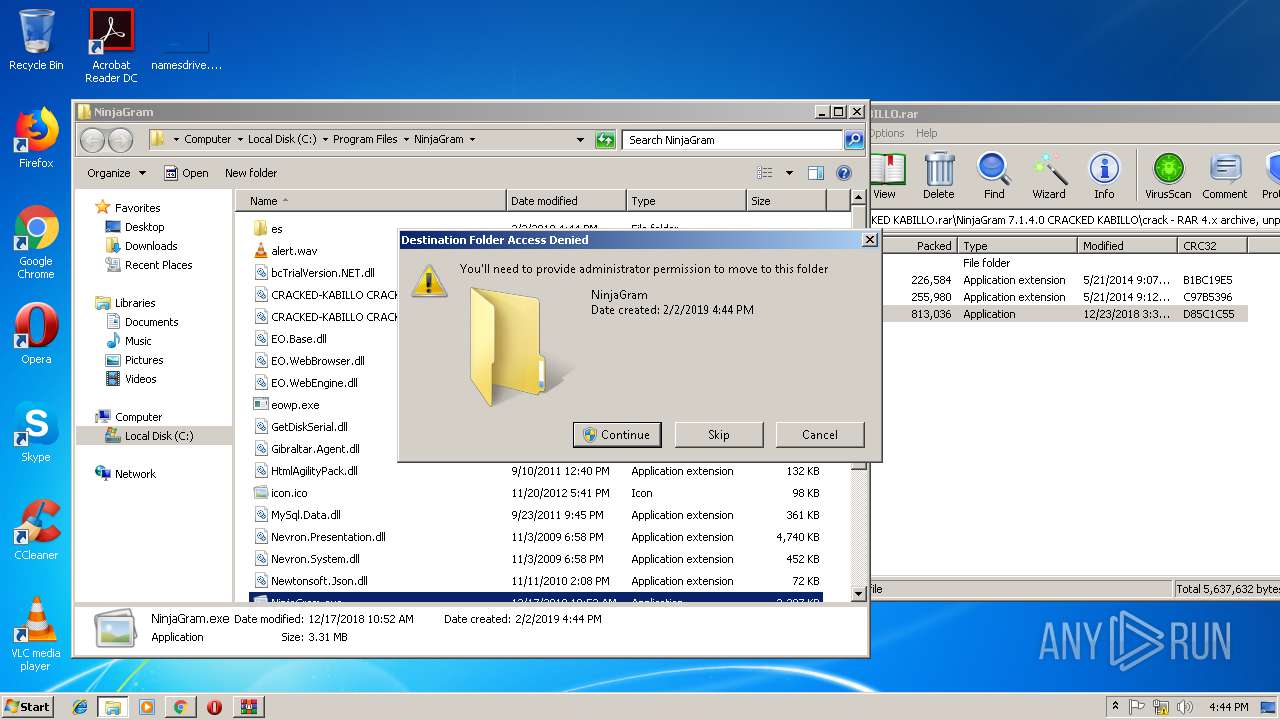
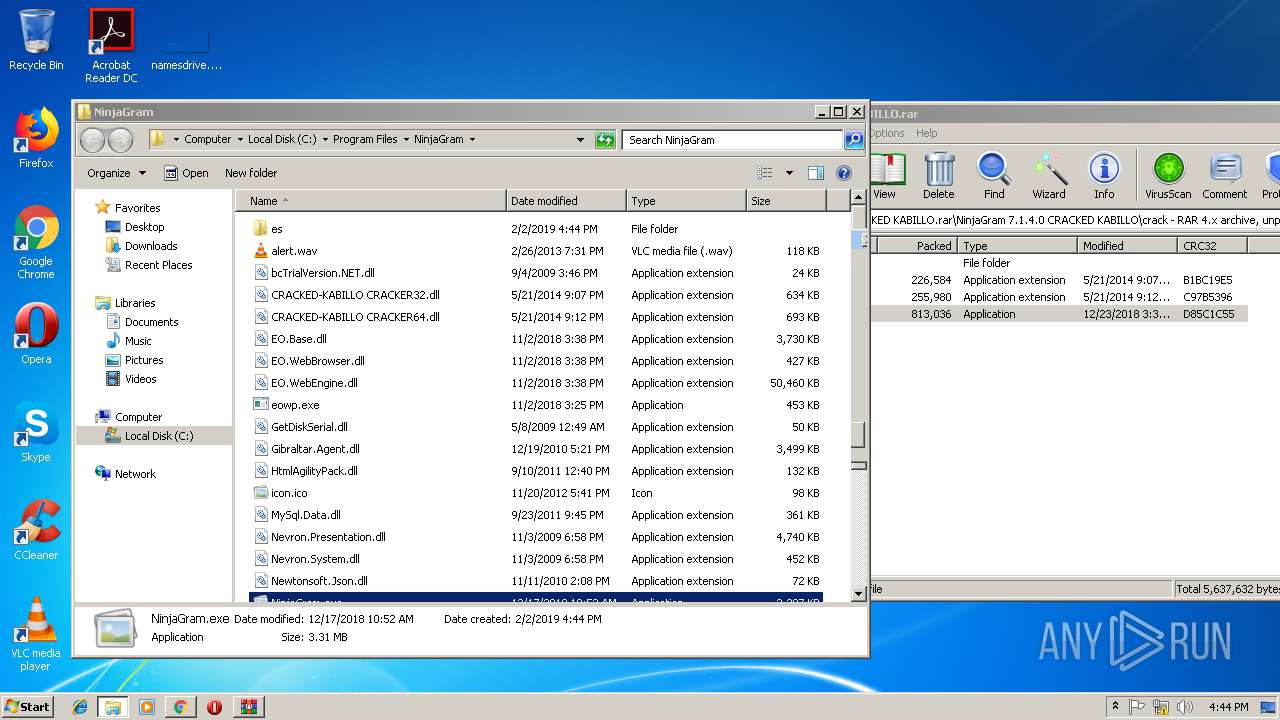
| URL: | https://mega.nz/#!ziYUlK6T!iZGaJESIMQtg4CiQglIe4XsHrxeyohJ3CHStCN-64B4 |
| Full analysis: | https://app.any.run/tasks/66d325b7-22b3-44e5-83a3-55a123949fc4 |
| Verdict: | No threats detected |
| Analysis date: | February 02, 2019, 16:43:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 557FD87BFEF6FE7A1370EAE7B7231085 |
| SHA1: | 021FEB9235DE1C3F89C537DEF92CB6FAB62AFE2B |
| SHA256: | 5C45161BD31B9752FE155DA465C4953BF552F0EAE5D20095A55D6178F2DC983E |
| SSDEEP: | 3:N8X/iGEk88uTP/iGg2sKaKwK0h:297cY2sKQLh |
MALICIOUS
No malicious indicators.SUSPICIOUS
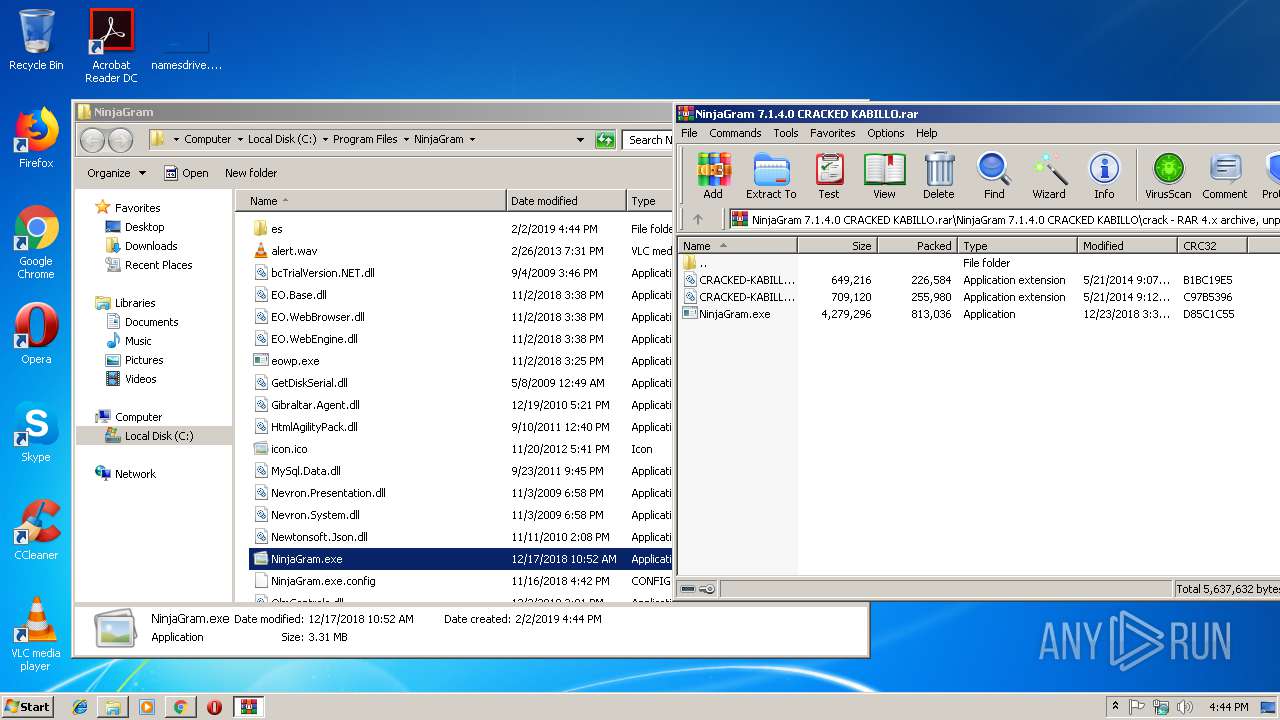
Executable content was dropped or overwritten
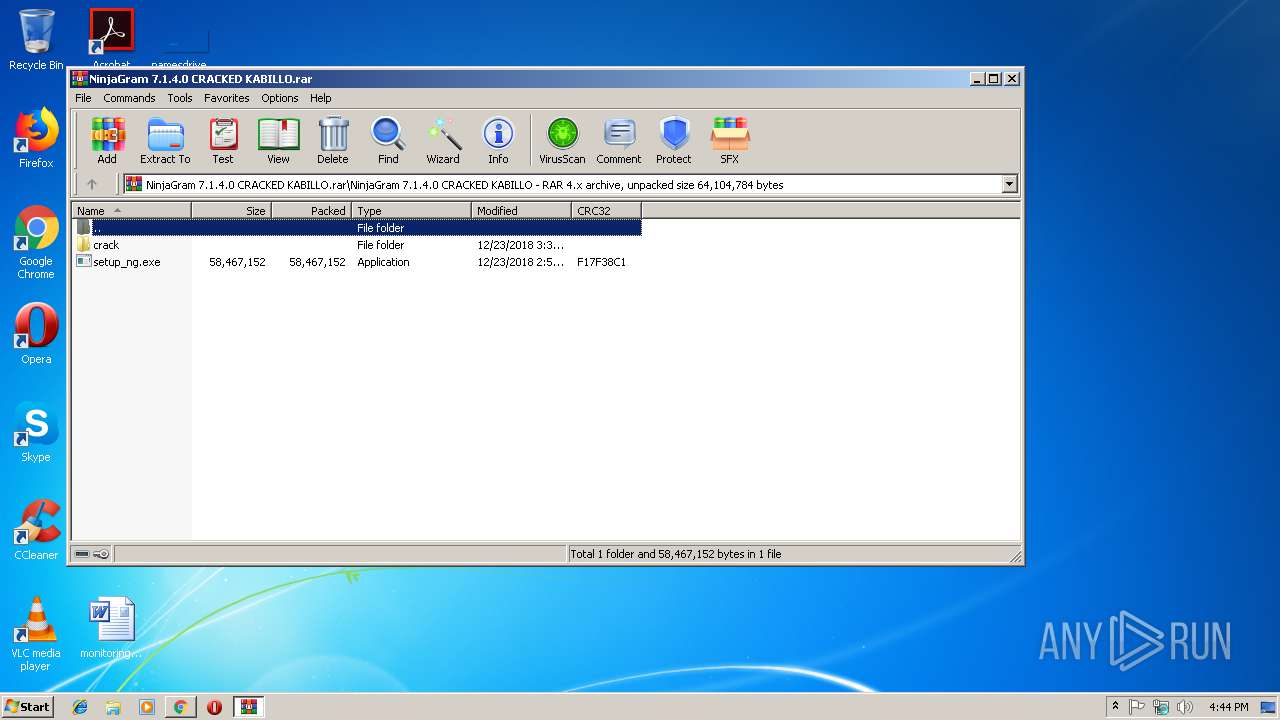
- WinRAR.exe (PID: 3020)
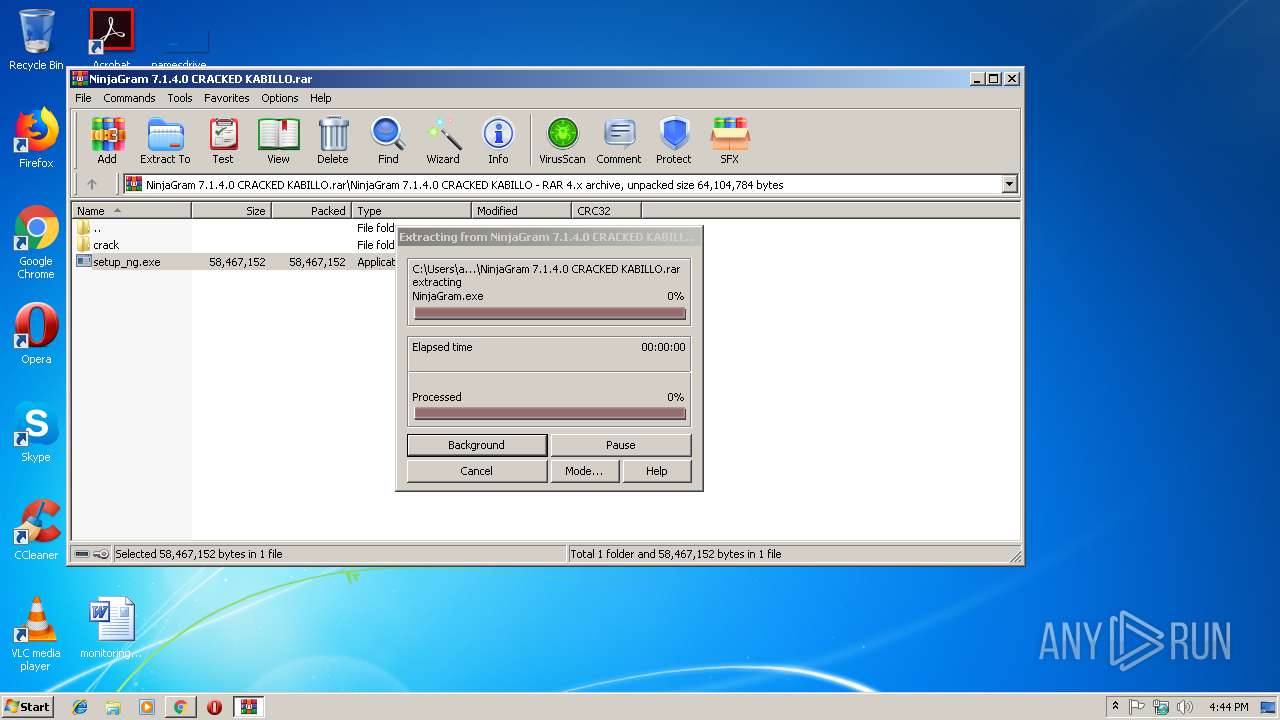
- setup_ng.tmp (PID: 3116)
- setup_ng.exe (PID: 792)
- setup_ng.exe (PID: 2312)
- DllHost.exe (PID: 3144)
INFO
Application launched itself
- chrome.exe (PID: 3012)
Creates files in the program directory
- setup_ng.tmp (PID: 3116)
Application was dropped or rewritten from another process
- setup_ng.tmp (PID: 2888)
- setup_ng.tmp (PID: 3116)
Creates a software uninstall entry
- setup_ng.tmp (PID: 3116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
52
Monitored processes
14
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
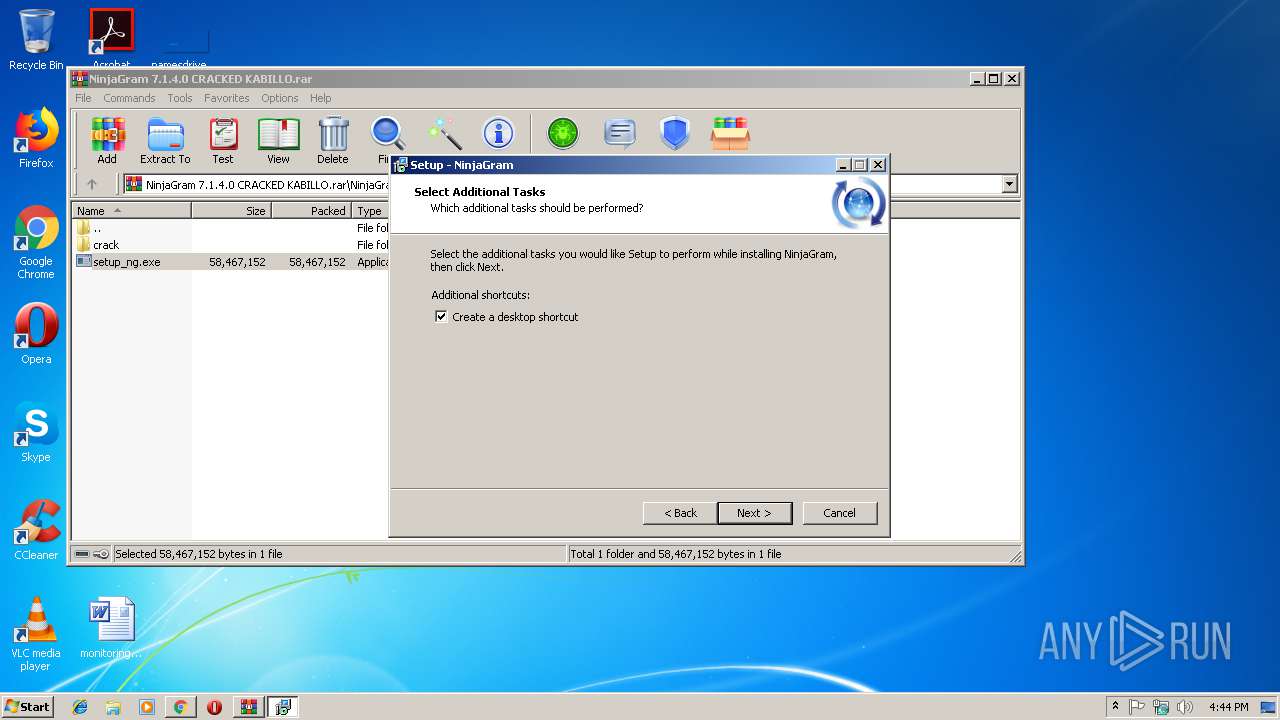
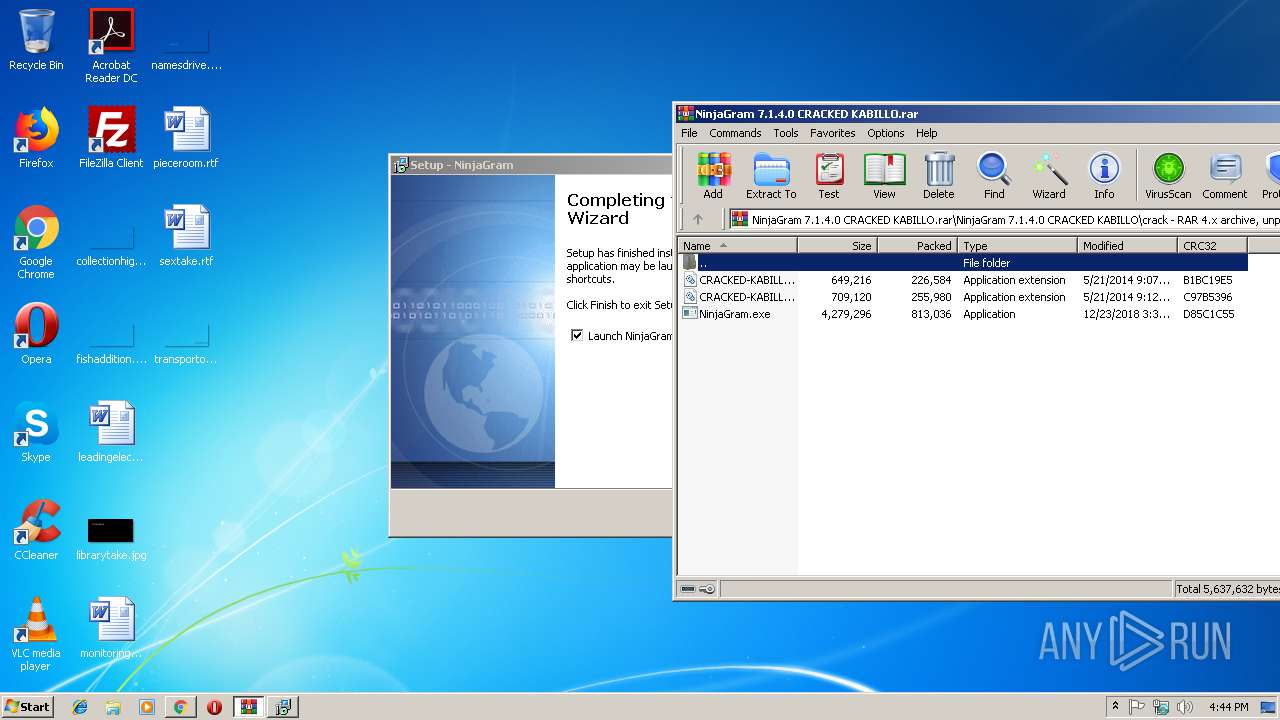
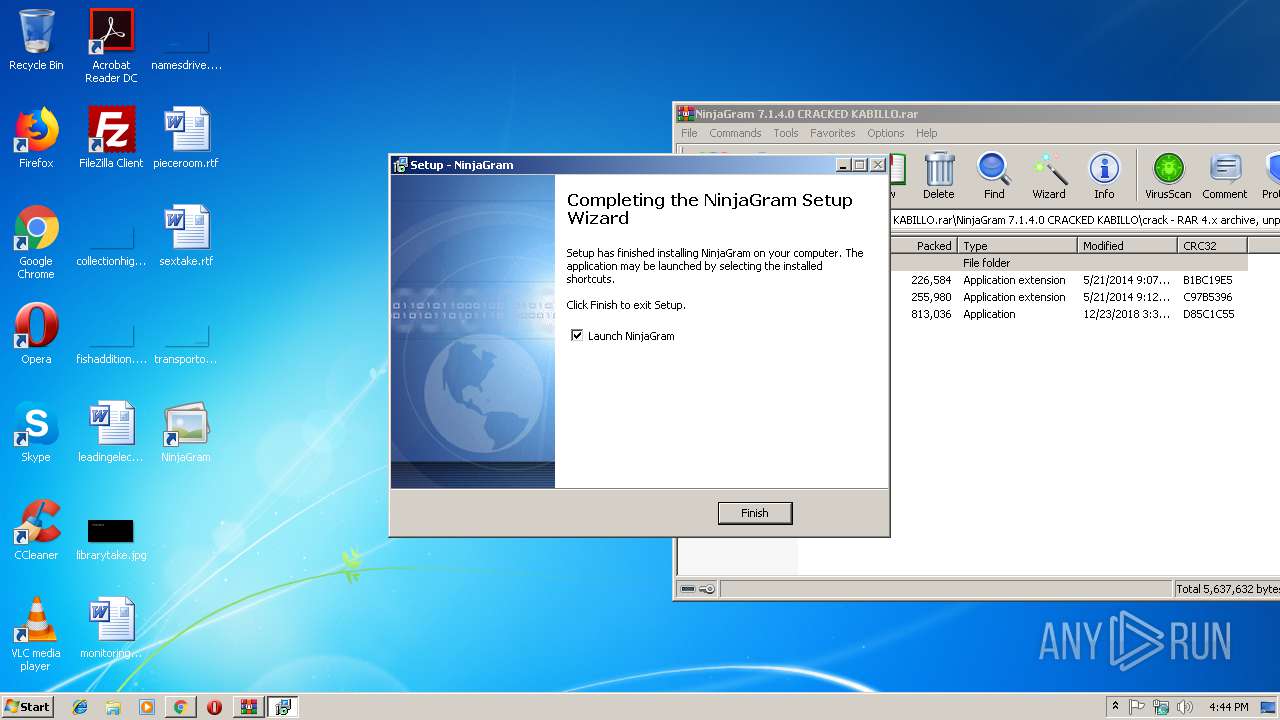
| 792 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3020.34749\NinjaGram 7.1.4.0 CRACKED KABILLO\setup_ng.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3020.34749\NinjaGram 7.1.4.0 CRACKED KABILLO\setup_ng.exe | WinRAR.exe | ||||||||||||
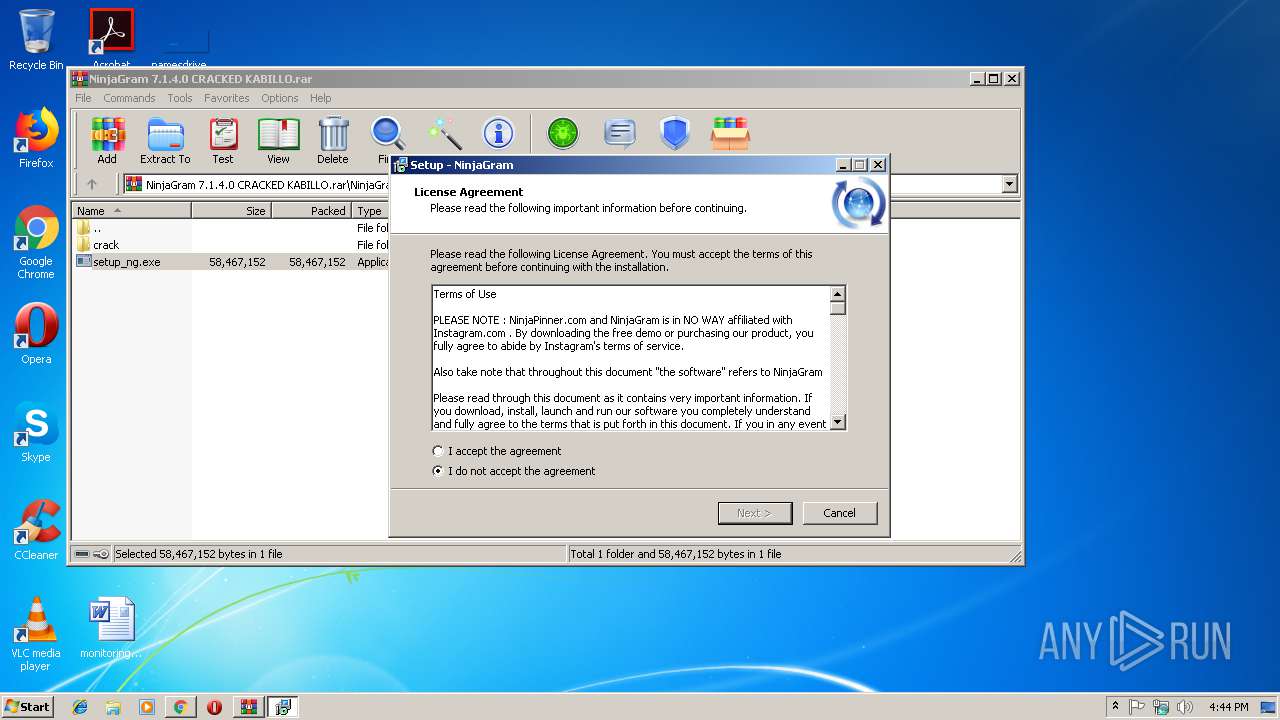
User: admin Company: ninjapinner.com Integrity Level: MEDIUM Description: NinjaGram Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 1488 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=888,3031516371800422712,2667241742975915268,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=11BFF5CE3237868FC9DA1CE0606B0AEB --mojo-platform-channel-handle=936 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2312 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3020.34749\NinjaGram 7.1.4.0 CRACKED KABILLO\setup_ng.exe" /SPAWNWND=$20196 /NOTIFYWND=$20174 | C:\Users\admin\AppData\Local\Temp\Rar$EXa3020.34749\NinjaGram 7.1.4.0 CRACKED KABILLO\setup_ng.exe | setup_ng.tmp | ||||||||||||
User: admin Company: ninjapinner.com Integrity Level: HIGH Description: NinjaGram Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 2744 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=888,3031516371800422712,2667241742975915268,131072 --enable-features=PasswordImport --service-pipe-token=98A86E6E5CC476BBB1D07F820D7A7F04 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=98A86E6E5CC476BBB1D07F820D7A7F04 --renderer-client-id=4 --mojo-platform-channel-handle=1896 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
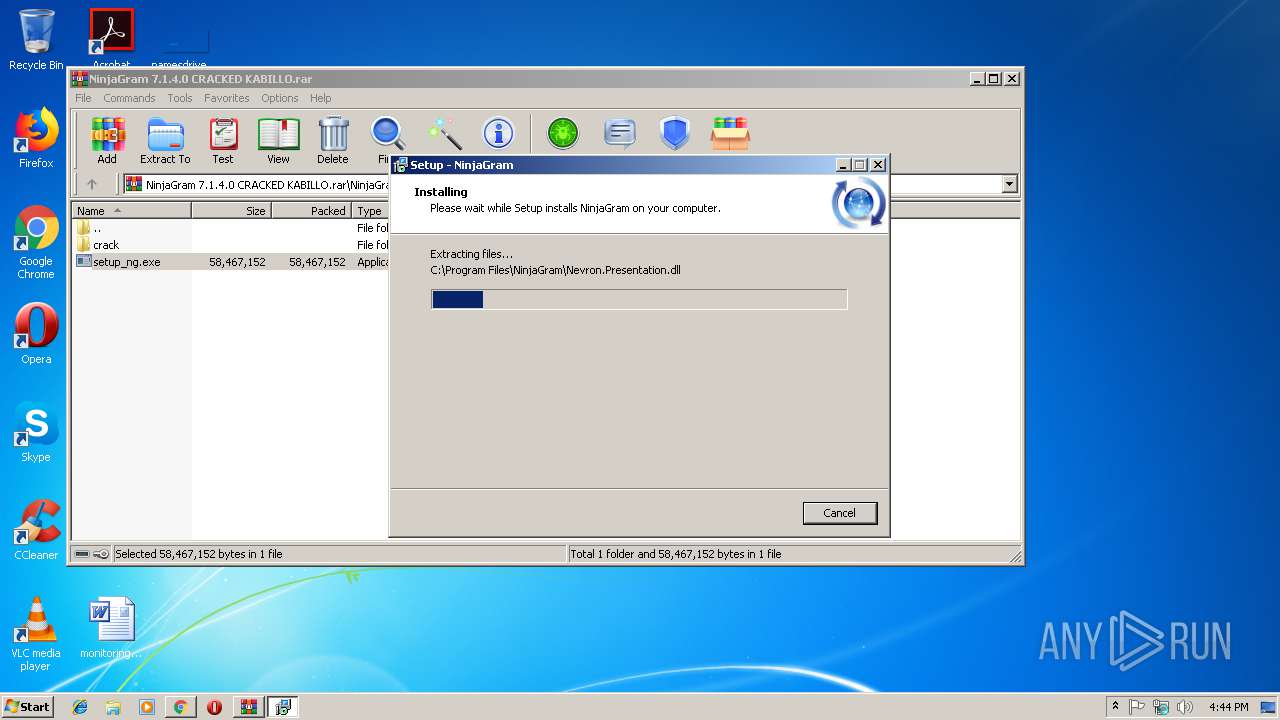
| 2888 | "C:\Users\admin\AppData\Local\Temp\is-M4J9K.tmp\setup_ng.tmp" /SL5="$20174,58177337,58368,C:\Users\admin\AppData\Local\Temp\Rar$EXa3020.34749\NinjaGram 7.1.4.0 CRACKED KABILLO\setup_ng.exe" | C:\Users\admin\AppData\Local\Temp\is-M4J9K.tmp\setup_ng.tmp | — | setup_ng.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 2968 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=3016 --on-initialized-event-handle=304 --parent-handle=308 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3012 | "C:\Program Files\Google\Chrome\Application\chrome.exe" https://mega.nz/#!ziYUlK6T!iZGaJESIMQtg4CiQglIe4XsHrxeyohJ3CHStCN-64B4 | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3020 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\NinjaGram 7.1.4.0 CRACKED KABILLO.rar" | C:\Program Files\WinRAR\WinRAR.exe | chrome.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3116 | "C:\Users\admin\AppData\Local\Temp\is-MOMA2.tmp\setup_ng.tmp" /SL5="$30194,58177337,58368,C:\Users\admin\AppData\Local\Temp\Rar$EXa3020.34749\NinjaGram 7.1.4.0 CRACKED KABILLO\setup_ng.exe" /SPAWNWND=$20196 /NOTIFYWND=$20174 | C:\Users\admin\AppData\Local\Temp\is-MOMA2.tmp\setup_ng.tmp | setup_ng.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 3144 | C:\Windows\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\system32\DllHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 898
Read events
1 808
Write events
81
Delete events
9
Modification events
| (PID) Process: | (2968) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 3012-13193599418107250 |
Value: 259 | |||
| (PID) Process: | (3012) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3012) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3012) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3012) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3012) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3012) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3516-13180984670829101 |
Value: 0 | |||
| (PID) Process: | (3012) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3012) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3012-13193599418107250 |
Value: 259 | |||
| (PID) Process: | (3012) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
28
Suspicious files
39
Text files
64
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3012 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3012 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3012 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\7b24d70b-91af-4da9-b195-dea8a7c6f700.tmp | — | |
MD5:— | SHA256:— | |||
| 3012 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3012 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3012 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\d89faacb-743d-4b13-83be-a8901bb9ae1b.tmp | — | |
MD5:— | SHA256:— | |||
| 3012 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:— | SHA256:— | |||
| 3012 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF20e851.TMP | text | |
MD5:— | SHA256:— | |||
| 3012 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3012 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old~RF20e860.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
25
DNS requests
11
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3012 | chrome.exe | 172.217.22.35:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3012 | chrome.exe | 89.44.169.135:443 | mega.nz | Datacenter Luxembourg S.A. | LU | suspicious |
3012 | chrome.exe | 172.217.21.234:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
3012 | chrome.exe | 172.217.18.163:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3012 | chrome.exe | 31.216.144.92:443 | gfs270n145.userstorage.mega.co.nz | Datacenter Luxembourg S.A. | LU | unknown |
3012 | chrome.exe | 31.216.148.11:443 | eu.static.mega.co.nz | Datacenter Luxembourg S.A. | LU | unknown |
3012 | chrome.exe | 216.58.206.14:443 | clients1.google.com | Google Inc. | US | whitelisted |
3012 | chrome.exe | 216.58.208.45:443 | accounts.google.com | Google Inc. | US | whitelisted |
3012 | chrome.exe | 172.217.22.3:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3012 | chrome.exe | 31.216.147.133:443 | g.api.mega.co.nz | Datacenter Luxembourg S.A. | LU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.gstatic.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
mega.nz |
| whitelisted |
accounts.google.com |
| shared |
safebrowsing.googleapis.com |
| whitelisted |
eu.static.mega.co.nz |
| shared |
g.api.mega.co.nz |
| shared |
clients1.google.com |
| whitelisted |
gfs270n145.userstorage.mega.co.nz |
| unknown |
ssl.gstatic.com |
| whitelisted |