| File name: | setup.exe |
| Full analysis: | https://app.any.run/tasks/33995c37-1fcd-4c00-a6f6-a06e7aa42f43 |
| Verdict: | Malicious activity |
| Analysis date: | May 14, 2019, 21:03:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 43D3FF349AD31E0AD76201755445CB1E |
| SHA1: | 7B3B15C369203CF892FB0B023201C5627E23973A |
| SHA256: | 5C402FD8244E177338A2A8F0C7B8DF055D5A06EBD7A5225EDB3D3CDAF1D1C749 |
| SSDEEP: | 24576:L20Bj512nz5ME9t+Fez6ovAJv9aGk3KgY7rmvZf5/I:L2Xzh/fvAJ4GkJECvTI |
MALICIOUS
Application was dropped or rewritten from another process
- installer.exe (PID: 2944)
Loads dropped or rewritten executable
- regsvr32.exe (PID: 2280)
- regsvr32.exe (PID: 4004)
- regsvr32.exe (PID: 2892)
- regsvr32.exe (PID: 3272)
- regsvr32.exe (PID: 2464)
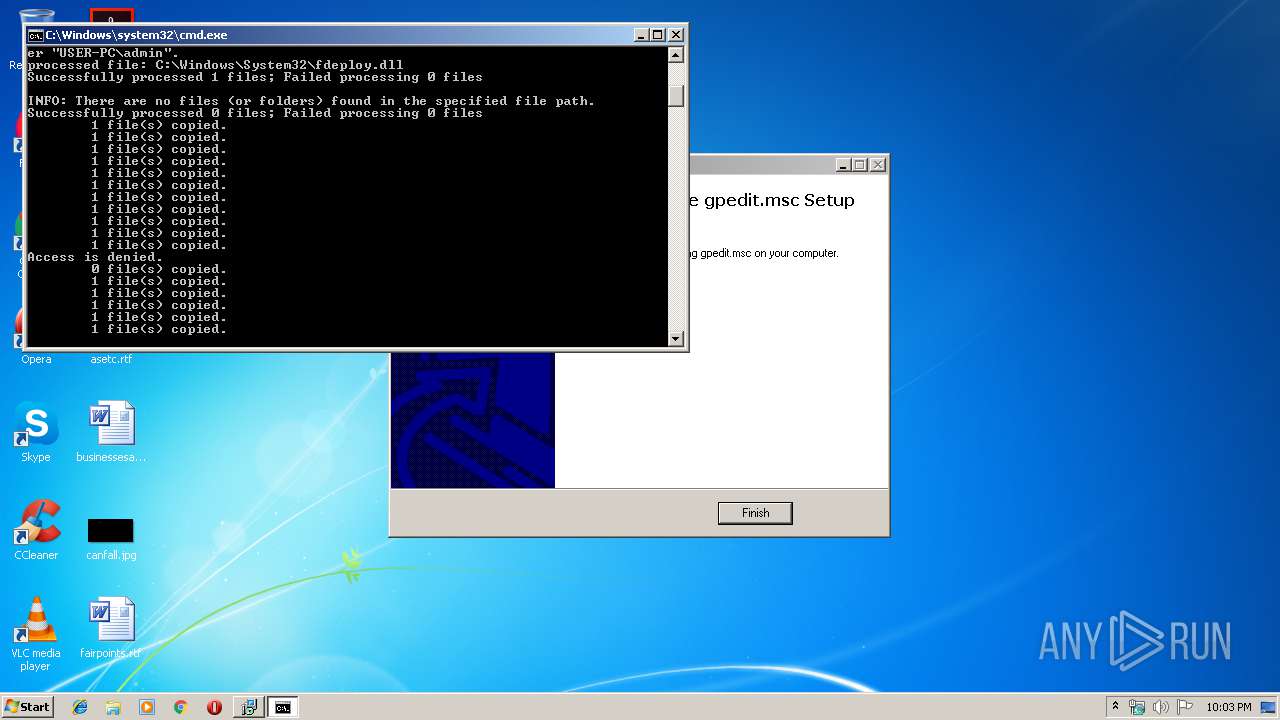
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 2348)
SUSPICIOUS
Executable content was dropped or overwritten
- setup.exe (PID: 3068)
- setup.exe (PID: 3176)
- setup.tmp (PID: 3472)
- cmd.exe (PID: 2348)
Creates files in the Windows directory
- setup.tmp (PID: 3472)
- cmd.exe (PID: 2348)
Uses ICACLS.EXE to modify access control list
- cmd.exe (PID: 2348)
Starts CMD.EXE for commands execution
- installer.exe (PID: 2944)
Creates COM task schedule object
- regsvr32.exe (PID: 2280)
- regsvr32.exe (PID: 4004)
INFO
Application was dropped or rewritten from another process
- setup.tmp (PID: 3472)
- setup.tmp (PID: 2580)
Loads dropped or rewritten executable
- setup.tmp (PID: 3472)
Dropped object may contain Bitcoin addresses
- cmd.exe (PID: 2348)
- setup.tmp (PID: 3472)
Creates a software uninstall entry
- setup.tmp (PID: 3472)
Reads settings of System Certificates
- chrome.exe (PID: 2512)
Creates files in the user directory
- opera.exe (PID: 2092)
Changes settings of System certificates
- chrome.exe (PID: 2512)
Application launched itself
- chrome.exe (PID: 2512)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (77.7) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.6) |
| .exe | | | Win32 Executable (generic) (3.1) |
| .exe | | | Win16/32 Executable Delphi generic (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 37888 |
| InitializedDataSize: | 17920 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9b24 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Richard |
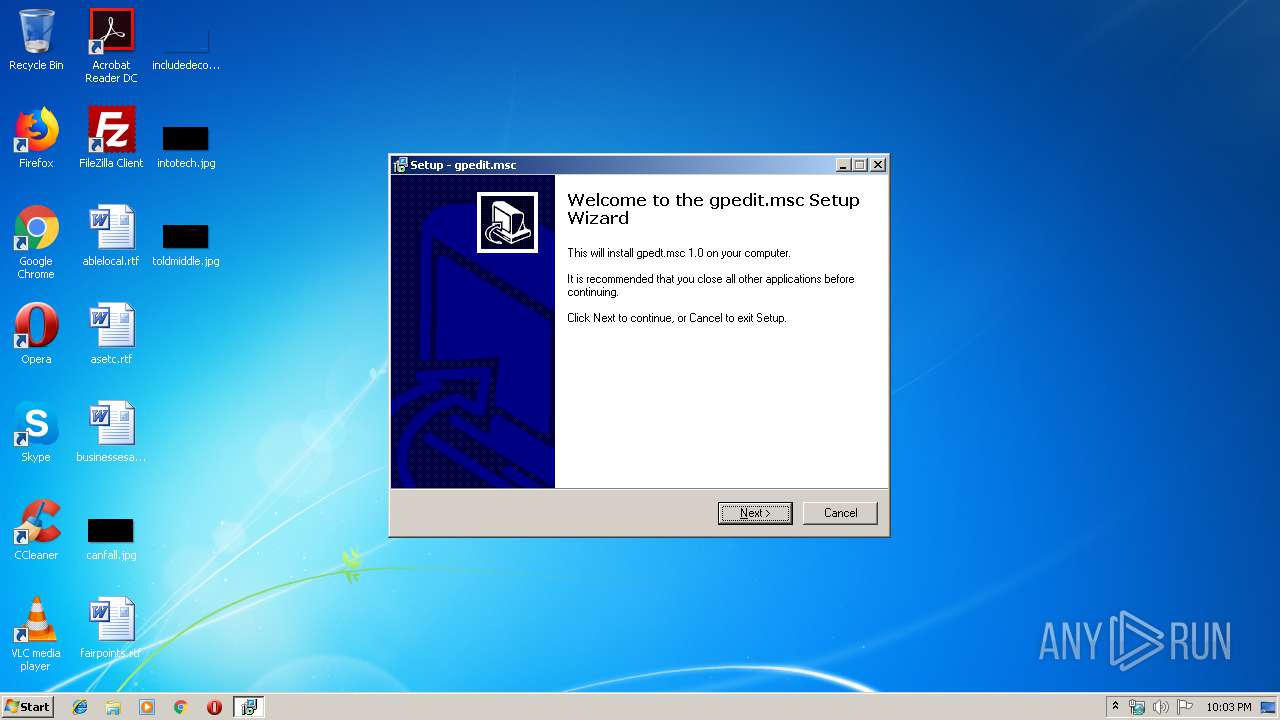
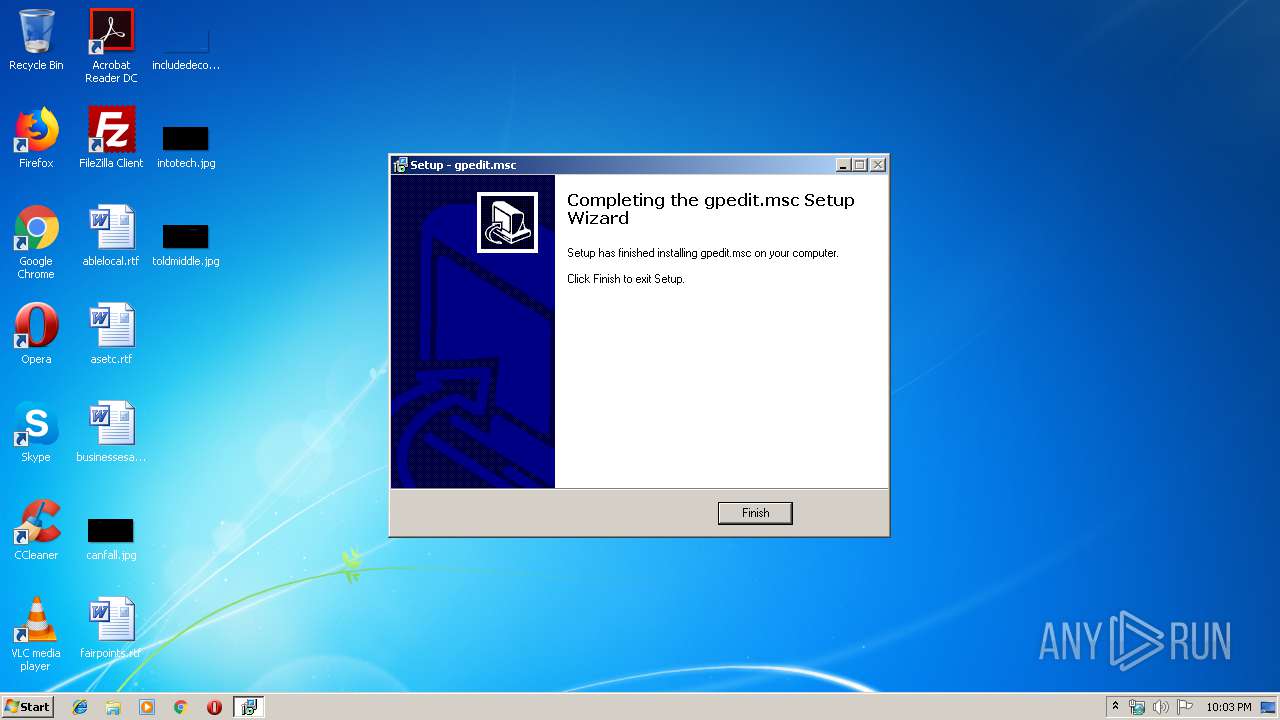
| FileDescription: | gpedit.msc Setup |
| FileVersion: | |
| LegalCopyright: | |
| ProductName: | gpedit.msc |
| ProductVersion: |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 19-Jun-1992 22:22:17 |
| Detected languages: |
|
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Richard |
| FileDescription: | gpedit.msc Setup |
| FileVersion: | - |
| LegalCopyright: | - |
| ProductName: | gpedit.msc |
| ProductVersion: | - |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 8 |
| Time date stamp: | 19-Jun-1992 22:22:17 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
CODE | 0x00001000 | 0x00009244 | 0x00009400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.53087 |
DATA | 0x0000B000 | 0x0000024C | 0x00000400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.73544 |
BSS | 0x0000C000 | 0x00000E4C | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x0000D000 | 0x00000950 | 0x00000A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.43073 |
.tls | 0x0000E000 | 0x00000008 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rdata | 0x0000F000 | 0x00000018 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 0.204488 |
.reloc | 0x00010000 | 0x000008B4 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 0 |
.rsrc | 0x00011000 | 0x00002C00 | 0x00002C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 4.45308 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.05007 | 1376 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 3.47151 | 1384 | UNKNOWN | Dutch - Netherlands | RT_ICON |
3 | 3.91708 | 744 | UNKNOWN | Dutch - Netherlands | RT_ICON |
4 | 3.91366 | 2216 | UNKNOWN | Dutch - Netherlands | RT_ICON |
4089 | 3.21823 | 754 | UNKNOWN | UNKNOWN | RT_STRING |
4090 | 3.31515 | 780 | UNKNOWN | UNKNOWN | RT_STRING |
4091 | 3.25024 | 718 | UNKNOWN | UNKNOWN | RT_STRING |
4093 | 2.86149 | 104 | UNKNOWN | UNKNOWN | RT_STRING |
4094 | 3.20731 | 180 | UNKNOWN | UNKNOWN | RT_STRING |
4095 | 3.04592 | 174 | UNKNOWN | UNKNOWN | RT_STRING |
Imports
advapi32.dll |
comctl32.dll |
kernel32.dll |
oleaut32.dll |
user32.dll |
Total processes
93
Monitored processes
56
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2092 | "C:\Program Files\Opera\opera.exe" | C:\Program Files\Opera\opera.exe | explorer.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
| 2172 | takeown /f C:\Windows\System32\appmgr.dll | C:\Windows\system32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2192 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=948,16456065172374325328,9856732038905479079,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=12902342688464797641 --mojo-platform-channel-handle=4340 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2216 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=948,16456065172374325328,9856732038905479079,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=6559222846870677538 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=6559222846870677538 --renderer-client-id=22 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5204 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
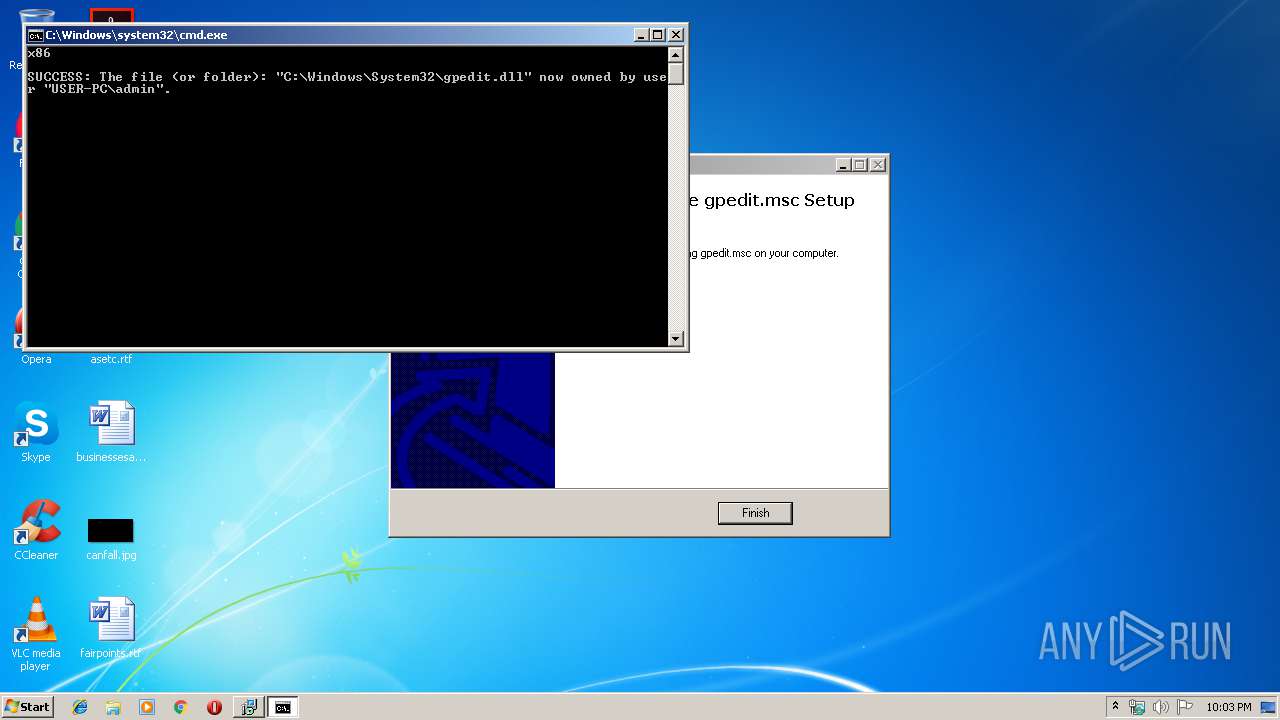
| 2280 | regsvr32 /s C:\Windows\System32\gpedit.dll | C:\Windows\system32\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2280 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=948,16456065172374325328,9856732038905479079,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=6342373503610563381 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=6342373503610563381 --renderer-client-id=29 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=7424 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2284 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=948,16456065172374325328,9856732038905479079,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=771615052167396170 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=771615052167396170 --renderer-client-id=15 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4592 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2316 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2500 --on-initialized-event-handle=308 --parent-handle=312 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2348 | cmd /c ""C:\Windows\Temp\gpedit\x86.bat" " | C:\Windows\system32\cmd.exe | installer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 3 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2352 | takeown /f C:\Windows\System32\gpedit.dll | C:\Windows\system32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 366
Read events
1 012
Write events
350
Delete events
4
Modification events
| (PID) Process: | (2944) installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2944) installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3472) setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{10B9C608-BF7C-4CCF-A658-C01D969DCA21}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 5.3.7 (a) | |||
| (PID) Process: | (3472) setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{10B9C608-BF7C-4CCF-A658-C01D969DCA21}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: | |||
| (PID) Process: | (3472) setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{10B9C608-BF7C-4CCF-A658-C01D969DCA21}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: (Default) | |||
| (PID) Process: | (3472) setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{10B9C608-BF7C-4CCF-A658-C01D969DCA21}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (3472) setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{10B9C608-BF7C-4CCF-A658-C01D969DCA21}_is1 |
| Operation: | write | Name: | DisplayName |
Value: gpedt.msc 1.0 | |||
| (PID) Process: | (3472) setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{10B9C608-BF7C-4CCF-A658-C01D969DCA21}_is1 |
| Operation: | write | Name: | UninstallString |
Value: "C:\Windows\unins000.exe" | |||
| (PID) Process: | (3472) setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{10B9C608-BF7C-4CCF-A658-C01D969DCA21}_is1 |
| Operation: | write | Name: | QuietUninstallString |
Value: "C:\Windows\unins000.exe" /SILENT | |||
| (PID) Process: | (3472) setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{10B9C608-BF7C-4CCF-A658-C01D969DCA21}_is1 |
| Operation: | write | Name: | Publisher |
Value: Richard | |||
Executable files
22
Suspicious files
169
Text files
118
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3472 | setup.tmp | C:\Windows\is-VEF2F.tmp | — | |
MD5:— | SHA256:— | |||
| 3472 | setup.tmp | C:\Windows\Temp\gpedit\is-UU7UG.tmp | — | |
MD5:— | SHA256:— | |||
| 3472 | setup.tmp | C:\Windows\Temp\gpedit\is-MV2RV.tmp | — | |
MD5:— | SHA256:— | |||
| 3472 | setup.tmp | C:\Windows\Temp\gpedit\is-NMA5F.tmp | — | |
MD5:— | SHA256:— | |||
| 3472 | setup.tmp | C:\Windows\Temp\gpedit\is-17Q48.tmp | — | |
MD5:— | SHA256:— | |||
| 3472 | setup.tmp | C:\Windows\Temp\gpedit\is-T9BAE.tmp | — | |
MD5:— | SHA256:— | |||
| 3472 | setup.tmp | C:\Windows\Temp\gpedit\is-ONG6I.tmp | — | |
MD5:— | SHA256:— | |||
| 3472 | setup.tmp | C:\Windows\Temp\gpedit\is-E3R5G.tmp | — | |
MD5:— | SHA256:— | |||
| 3472 | setup.tmp | C:\Windows\Temp\gpedit\is-UNMRC.tmp | — | |
MD5:— | SHA256:— | |||
| 3472 | setup.tmp | C:\Windows\Temp\gpedit\is-2D1H0.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
217
DNS requests
130
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2092 | opera.exe | GET | 200 | 66.225.197.197:80 | http://crl4.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 543 b | whitelisted |
2512 | chrome.exe | GET | 200 | 91.199.212.52:80 | http://crt.usertrust.com/USERTrustRSAAddTrustCA.crt | GB | der | 1.37 Kb | whitelisted |
2512 | chrome.exe | GET | 200 | 93.184.221.240:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 56.1 Kb | whitelisted |
2512 | chrome.exe | GET | 200 | 217.146.165.204:80 | http://r1---sn-oun-1gie.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=136.0.2.194&mm=28&mn=sn-oun-1gie&ms=nvh&mt=1557866853&mv=u&pl=27&shardbypass=yes | CH | crx | 842 Kb | whitelisted |
2512 | chrome.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAx5qUSwjBGVIJJhX%2BJrHYM%3D | US | der | 471 b | whitelisted |
2512 | chrome.exe | GET | 200 | 143.204.208.42:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
2512 | chrome.exe | GET | 302 | 172.217.16.174:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 502 b | whitelisted |
2512 | chrome.exe | GET | 200 | 204.13.202.71:80 | http://ssl.trustwave.com/issuers/STCA.crt | US | der | 956 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2512 | chrome.exe | 216.58.210.3:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2512 | chrome.exe | 172.217.18.13:443 | accounts.google.com | Google Inc. | US | whitelisted |
2512 | chrome.exe | 216.58.206.3:443 | www.google.ch | Google Inc. | US | whitelisted |
2512 | chrome.exe | 172.217.22.4:443 | www.google.com | Google Inc. | US | whitelisted |
2092 | opera.exe | 185.26.182.93:443 | certs.opera.com | Opera Software AS | — | whitelisted |
2092 | opera.exe | 66.225.197.197:80 | crl4.digicert.com | CacheNetworks, Inc. | US | whitelisted |
2512 | chrome.exe | 172.217.18.106:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2512 | chrome.exe | 172.217.18.97:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
2512 | chrome.exe | 172.217.16.131:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
2512 | chrome.exe | 172.217.16.174:80 | redirector.gvt1.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
www.google.com.ua |
| whitelisted |
accounts.google.com |
| shared |
clients1.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
certs.opera.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |
www.google.com |
| malicious |