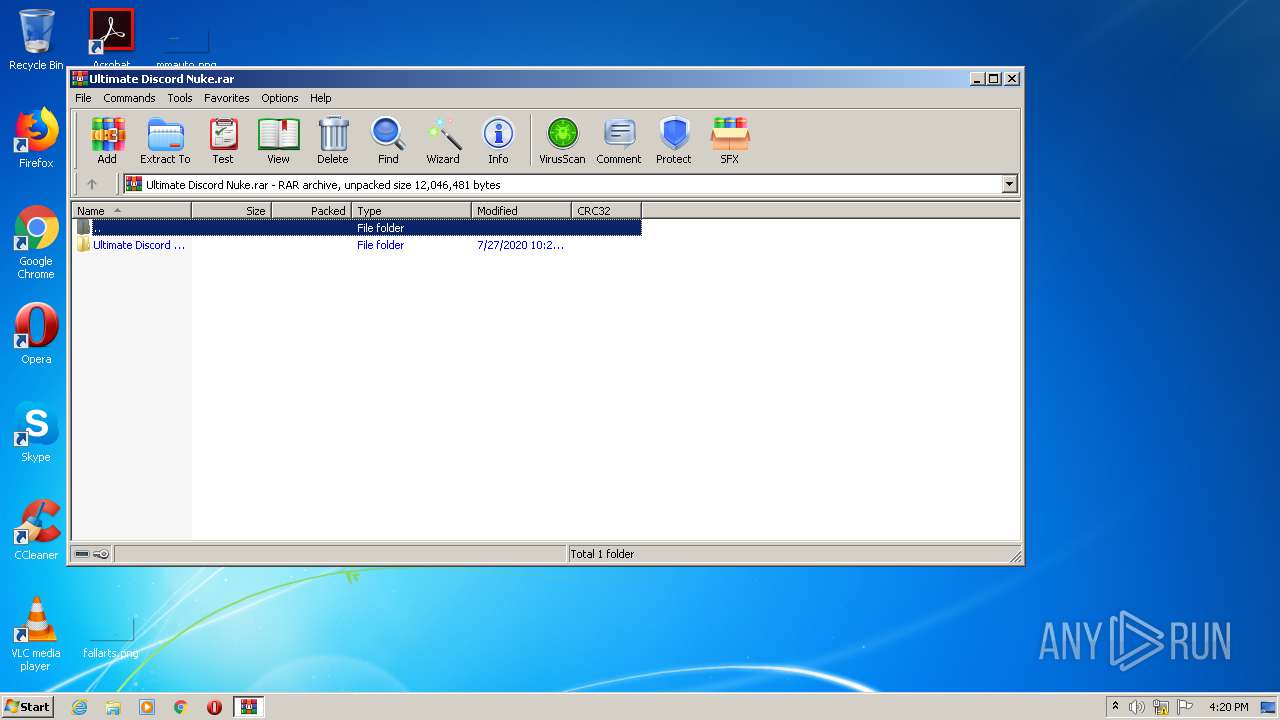
| File name: | Ultimate Discord Nuke.rar |
| Full analysis: | https://app.any.run/tasks/718954f1-77d7-4a3f-a5f9-1b2a72c8679d |
| Verdict: | Malicious activity |
| Analysis date: | August 08, 2020, 15:20:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | CBB65054ED616386F3D4A482A8940D04 |
| SHA1: | B8393CF36AF40986B3409C06CA8CAE2FB5AB8CE1 |
| SHA256: | 5C32E90BB3D4F2A77DEB7A2AAD75E515AADA16CDEB2114FE5AF9E39548B6D51A |
| SSDEEP: | 196608:Qb5VIuu6WC7eL2KUPklrqp2RU+j29J1A/qy2wtgisBEFiUeT0VOvTG6w5ED8f:QrY61iyBkwcqxnj+iUBOvCnP |
MALICIOUS
Application was dropped or rewritten from another process
- ultimate_discord_nuke.exe (PID: 3296)
- ultimate_discord_nuke.exe (PID: 3848)
Loads dropped or rewritten executable
- ultimate_discord_nuke.exe (PID: 3848)
SUSPICIOUS
Executable content was dropped or overwritten
- ultimate_discord_nuke.exe (PID: 3296)
- WinRAR.exe (PID: 3176)
Loads Python modules
- ultimate_discord_nuke.exe (PID: 3848)
Application launched itself
- ultimate_discord_nuke.exe (PID: 3296)
INFO
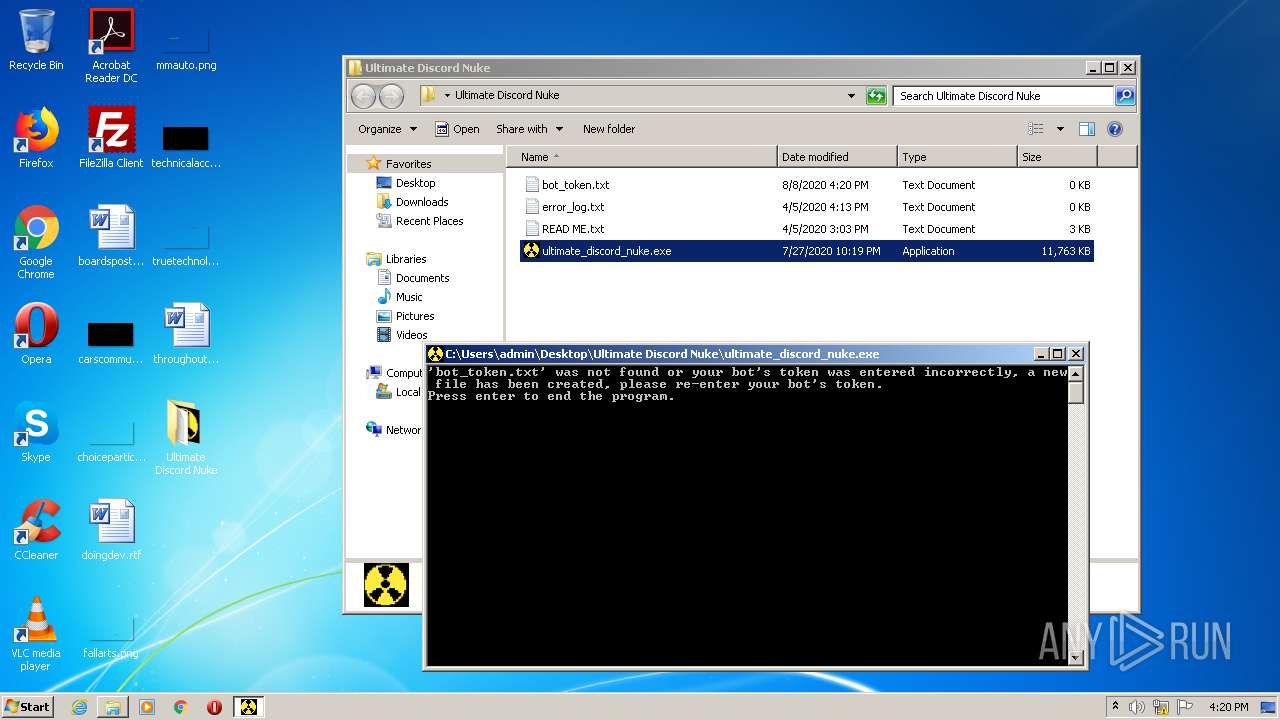
Dropped object may contain Bitcoin addresses
- ultimate_discord_nuke.exe (PID: 3296)
Manual execution by user
- iexplore.exe (PID: 1932)
- ultimate_discord_nuke.exe (PID: 3296)
Changes internet zones settings
- iexplore.exe (PID: 1932)
Reads internet explorer settings
- iexplore.exe (PID: 2252)
Reads settings of System Certificates
- ultimate_discord_nuke.exe (PID: 3848)
Reads Internet Cache Settings
- iexplore.exe (PID: 2252)
- iexplore.exe (PID: 1932)
Application launched itself
- iexplore.exe (PID: 1932)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
42
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1932 | "C:\Program Files\Internet Explorer\iexplore.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2252 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1932 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
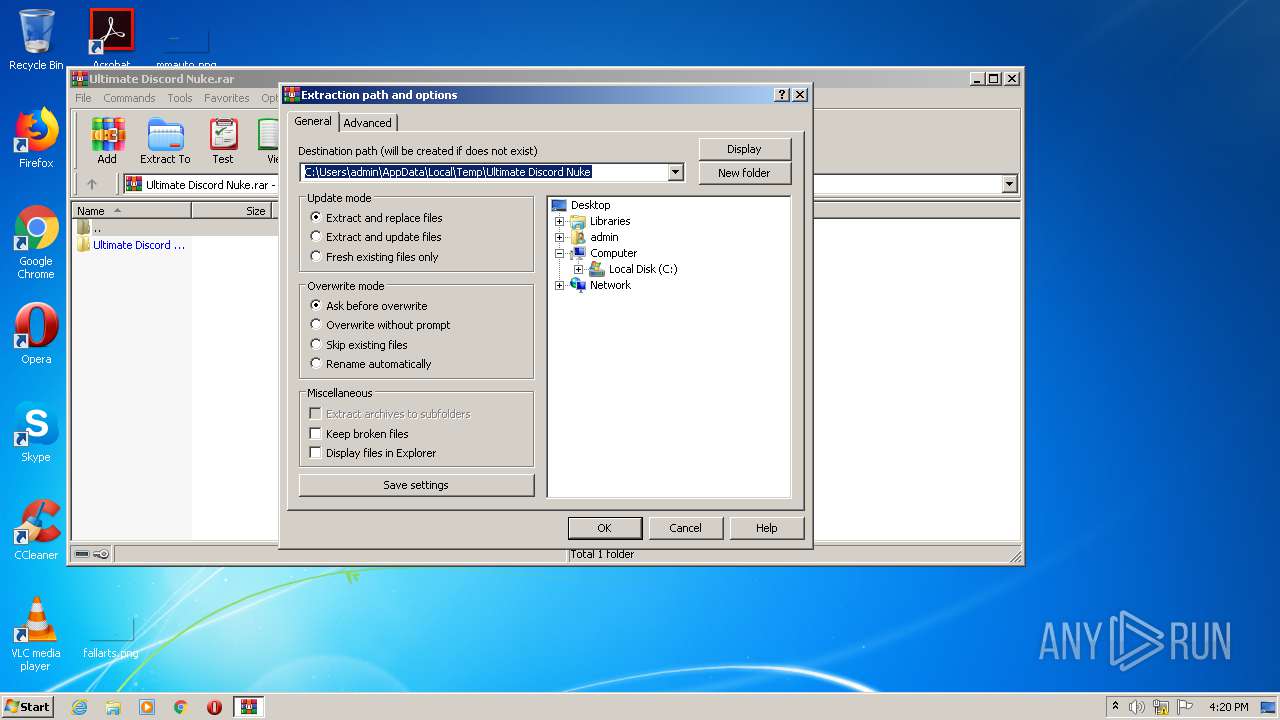
| 3176 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Ultimate Discord Nuke.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
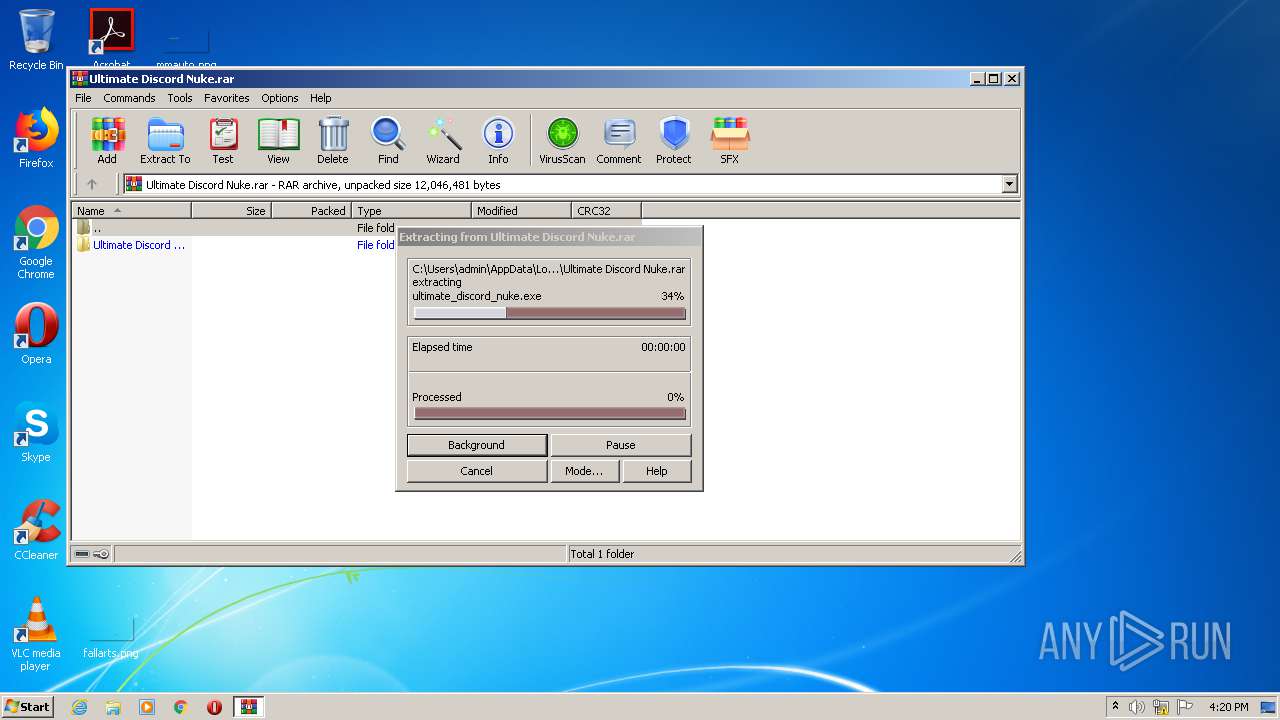
| 3296 | "C:\Users\admin\Desktop\Ultimate Discord Nuke\ultimate_discord_nuke.exe" | C:\Users\admin\Desktop\Ultimate Discord Nuke\ultimate_discord_nuke.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3848 | "C:\Users\admin\Desktop\Ultimate Discord Nuke\ultimate_discord_nuke.exe" | C:\Users\admin\Desktop\Ultimate Discord Nuke\ultimate_discord_nuke.exe | ultimate_discord_nuke.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
923
Read events
849
Write events
74
Delete events
0
Modification events
| (PID) Process: | (3176) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3176) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3176) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\137\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3176) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\137\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (3176) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Ultimate Discord Nuke.rar | |||
| (PID) Process: | (3176) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3176) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3176) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3176) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3176) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
Executable files
35
Suspicious files
3
Text files
929
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3176 | WinRAR.exe | C:\Users\admin\Desktop\Ultimate Discord Nuke\ultimate_discord_nuke.exe | executable | |
MD5:A86BC9C2F2C363E6A86AFB3078C33C68 | SHA256:A1EA0D96D6EBB8587C2E9A3AF50B9B95893229E66DC9038271C19C465E1E4432 | |||
| 3296 | ultimate_discord_nuke.exe | C:\Users\admin\AppData\Local\Temp\_MEI32962\_cffi_backend.cp38-win32.pyd | executable | |
MD5:012DB6C90D38DB71D0647659217CA286 | SHA256:4207E3276411F75A6680EAE28D7D5ED7F6CAD946B1DE7B724440F44593267414 | |||
| 3296 | ultimate_discord_nuke.exe | C:\Users\admin\AppData\Local\Temp\_MEI32962\_decimal.pyd | executable | |
MD5:8601C853146A4BE85238A57C9FD56865 | SHA256:2A57023D4F355E3857187C02577FA4641A4D1DFF195196B3C33B90322EDF9FD4 | |||
| 3176 | WinRAR.exe | C:\Users\admin\Desktop\Ultimate Discord Nuke\READ ME.txt | text | |
MD5:— | SHA256:— | |||
| 3296 | ultimate_discord_nuke.exe | C:\Users\admin\AppData\Local\Temp\_MEI32962\_ctypes.pyd | executable | |
MD5:3A2E78784B929003A6BACEEBDB0EFA4D | SHA256:F205948B01B29CB244AE09C5B57FD4B6C8F356DFCD2F8CB49E7CFD177A748CF9 | |||
| 3296 | ultimate_discord_nuke.exe | C:\Users\admin\AppData\Local\Temp\_MEI32962\_elementtree.pyd | executable | |
MD5:29928F61AAC2E9989BB097620B52A289 | SHA256:EB8DE455AE9EF9B5223DA2EAA2A74121EB2FE5371CB07E803E8E6E5C3CB5FB44 | |||
| 3296 | ultimate_discord_nuke.exe | C:\Users\admin\AppData\Local\Temp\_MEI32962\_overlapped.pyd | executable | |
MD5:AA428E44A78A280EC8152C43D8284F6F | SHA256:F8FDA2A6E3FF0069E634FEEC4854EE7A8C24134C747DE3211AC2BA26E0188C79 | |||
| 3296 | ultimate_discord_nuke.exe | C:\Users\admin\AppData\Local\Temp\_MEI32962\_asyncio.pyd | executable | |
MD5:5435CE08F40FBE43230CAE8D3DFF232C | SHA256:79FDA30CBFC95DB2BA60646FF53DFF45B5ADD57C12241C4A82FA798CB3B543DF | |||
| 3296 | ultimate_discord_nuke.exe | C:\Users\admin\AppData\Local\Temp\_MEI32962\_bz2.pyd | executable | |
MD5:0F75C236C4CCFEA1B16F132F6C139236 | SHA256:5DC26DCBF58CC7F5BFDEC0BADD5240D6724DB3E34010AAF35A31876FE4057158 | |||
| 3296 | ultimate_discord_nuke.exe | C:\Users\admin\AppData\Local\Temp\_MEI32962\VCRUNTIME140.dll | executable | |
MD5:4C360F78DE1F5BAAA5F110E65FAC94B4 | SHA256:AD1B0992B890BFE88EF52D0A830873ACC0AECC9BD6E4FC22397DBCCF4D2B4E37 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
3
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1932 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3848 | ultimate_discord_nuke.exe | 162.159.134.233:443 | discordapp.com | Cloudflare Inc | — | shared |
1932 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
discordapp.com |
| whitelisted |
www.bing.com |
| whitelisted |
api.bing.com |
| whitelisted |