| File name: | target.ps1 |
| Full analysis: | https://app.any.run/tasks/60f0e42d-c7e8-450e-ad5a-119655da9b57 |
| Verdict: | Malicious activity |
| Analysis date: | February 20, 2025, 20:54:36 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | 754C50B318E07154F7CA1638E6944330 |
| SHA1: | 3A795BE6A0B5B69E49E7622CA5D2BC2F10C73BE4 |
| SHA256: | 5C310C49E484705D28A86155607BBB06694C52D1C7F9AAA96198B590E67BA247 |
| SSDEEP: | 3:WIuJsTE2mMVyn:WIuAmgy |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 2216)
SUSPICIOUS
Creates new GUID (POWERSHELL)
- powershell.exe (PID: 2216)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 2216)
- powershell.exe (PID: 3992)
- powershell.exe (PID: 4320)
- powershell.exe (PID: 3060)
Executing commands from ".cmd" file
- powershell.exe (PID: 2216)
- cmd.exe (PID: 2164)
- powershell.exe (PID: 4328)
- cmd.exe (PID: 5236)
- cmd.exe (PID: 4128)
- powershell.exe (PID: 5460)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 2216)
- powershell.exe (PID: 3992)
- powershell.exe (PID: 4320)
- powershell.exe (PID: 3060)
Starts SC.EXE for service management
- cmd.exe (PID: 2164)
- cmd.exe (PID: 5236)
- cmd.exe (PID: 4128)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 2216)
- cmd.exe (PID: 4764)
- cmd.exe (PID: 2164)
- powershell.exe (PID: 4328)
- cmd.exe (PID: 5872)
- cmd.exe (PID: 5236)
- cmd.exe (PID: 3848)
- cmd.exe (PID: 4128)
- powershell.exe (PID: 5460)
Windows service management via SC.EXE
- sc.exe (PID: 6016)
- sc.exe (PID: 3364)
- sc.exe (PID: 5340)
Application launched itself
- cmd.exe (PID: 2164)
- cmd.exe (PID: 4764)
- cmd.exe (PID: 5236)
- cmd.exe (PID: 5872)
- cmd.exe (PID: 3848)
- cmd.exe (PID: 4128)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2164)
- cmd.exe (PID: 5236)
- cmd.exe (PID: 4128)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 3060)
- cmd.exe (PID: 5988)
- cmd.exe (PID: 2380)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 2216)
- powershell.exe (PID: 3992)
- powershell.exe (PID: 4320)
- powershell.exe (PID: 3060)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2164)
- cmd.exe (PID: 3060)
- cmd.exe (PID: 5988)
- cmd.exe (PID: 5236)
- cmd.exe (PID: 2380)
- cmd.exe (PID: 4128)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 3060)
- cmd.exe (PID: 5988)
- cmd.exe (PID: 2380)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 2216)
INFO
Gets a random number, or selects objects randomly from a collection (POWERSHELL)
- powershell.exe (PID: 2216)
- powershell.exe (PID: 3992)
- powershell.exe (PID: 4320)
- powershell.exe (PID: 3060)
Checks proxy server information
- powershell.exe (PID: 2216)
Disables trace logs
- powershell.exe (PID: 2216)
Checks operating system version
- cmd.exe (PID: 2164)
- cmd.exe (PID: 5236)
- cmd.exe (PID: 4128)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 3992)
- powershell.exe (PID: 4320)
- powershell.exe (PID: 3060)
- powershell.exe (PID: 2216)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 3992)
- powershell.exe (PID: 4320)
- powershell.exe (PID: 3060)
- powershell.exe (PID: 2216)
Creates a byte array (POWERSHELL)
- powershell.exe (PID: 3992)
- powershell.exe (PID: 4320)
- powershell.exe (PID: 3060)
- powershell.exe (PID: 2216)
Checks supported languages
- mode.com (PID: 3612)
Starts MODE.COM to configure console settings
- mode.com (PID: 3612)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
201
Monitored processes
82
Malicious processes
6
Suspicious processes
9
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 556 | C:\WINDOWS\System32\cmd.exe /S /D /c" echo "AMD64 " " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 640 | cmd | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1144 | "C:\WINDOWS\system32\cmd.exe" /c "echo CMD is working" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1544 | find /i "FullLanguage" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1544 | reg query "HKCU\Console" /v ForceV2 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1596 | C:\WINDOWS\System32\cmd.exe /c ver | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1668 | find /i "ARM64" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1732 | C:\WINDOWS\System32\cmd.exe /S /D /c" echo "C:\Users\admin\AppData\Local\Temp\MAS_5ace38b8-c873-48de-bdc3-8cd0ca1b0e96.cmd" " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1752 | findstr /v "f7f81a39-5f63-5b42-9efd-1f13b5431005quot; "MAS_5ace38b8-c873-48de-bdc3-8cd0ca1b0e96.cmd" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1752 | find /i "True" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
35 859
Read events
35 859
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
4
Text files
17
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4320 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_vozj5dx3.zma.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2216 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_x01sp25k.o3j.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2216 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF1362e4.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 2216 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_gzbymlys.zmz.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3992 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_godwzpm0.pvd.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3992 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:B6751E5C13989128BA529AA77AE34CD2 | SHA256:FA3868A47FB4C6D9094D992E71FDE5C150FB9BF5E4905B93B7D11C8BED4D8AA5 | |||
| 2216 | powershell.exe | C:\Users\admin\AppData\Local\Temp\MAS_5ace38b8-c873-48de-bdc3-8cd0ca1b0e96.cmd | text | |
MD5:8F6CCC99C60C2BB7503399224CBDBAD3 | SHA256:0DE697EBB04746F2DF351AA5EBBEACC7626458B6F7E301EE66B132E9A38FBC59 | |||
| 3992 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_p1c3ypy1.4jd.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4328 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_idwmmtnr.jp1.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4804 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ykicdfao.y0o.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
22
DNS requests
10
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.169:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1752 | RUXIMICS.exe | GET | 200 | 23.48.23.169:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4536 | svchost.exe | GET | 200 | 23.48.23.169:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1752 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4536 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
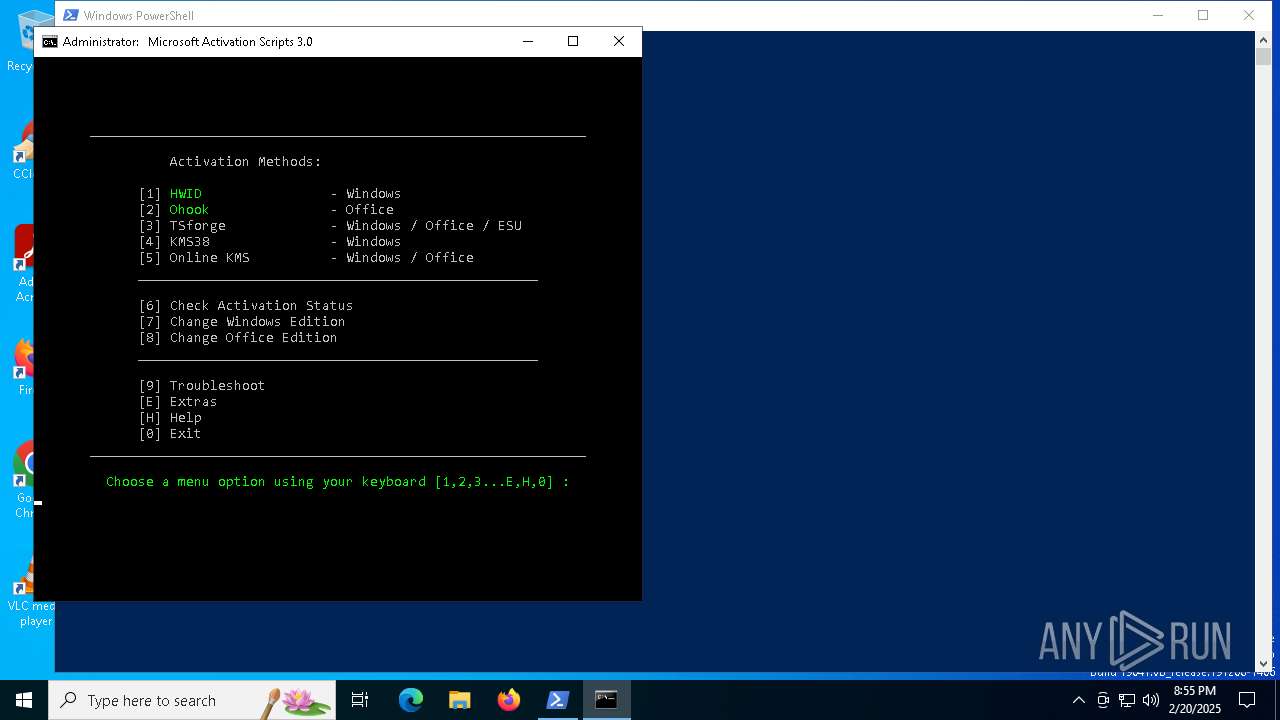
— | — | GET | 200 | 104.21.24.156:443 | https://get.activated.win/ | unknown | text | 3.98 Kb | malicious |
— | — | GET | 200 | 104.21.24.156:443 | https://git.activated.win/massgrave/Microsoft-Activation-Scripts/raw/commit/60c99742ce9ff1c675c6e381e17b0f4ccf1a57bd/MAS/All-In-One-Version-KL/MAS_AIO.cmd | unknown | text | 651 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4536 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1752 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.169:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1752 | RUXIMICS.exe | 23.48.23.169:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4536 | svchost.exe | 23.48.23.169:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1752 | RUXIMICS.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
get.activated.win |
| malicious |
git.activated.win |
| malicious |
activated.win |
| unknown |
updatecheck30.activated.win |
| unknown |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Get-WmiObject Cmdlet has been detected |
— | — | A Network Trojan was detected | ET ATTACK_RESPONSE PowerShell Internet Connectivity Check via Network GUID Inbound |
— | — | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Windows OS Version extraction by PS.Script has been detected |