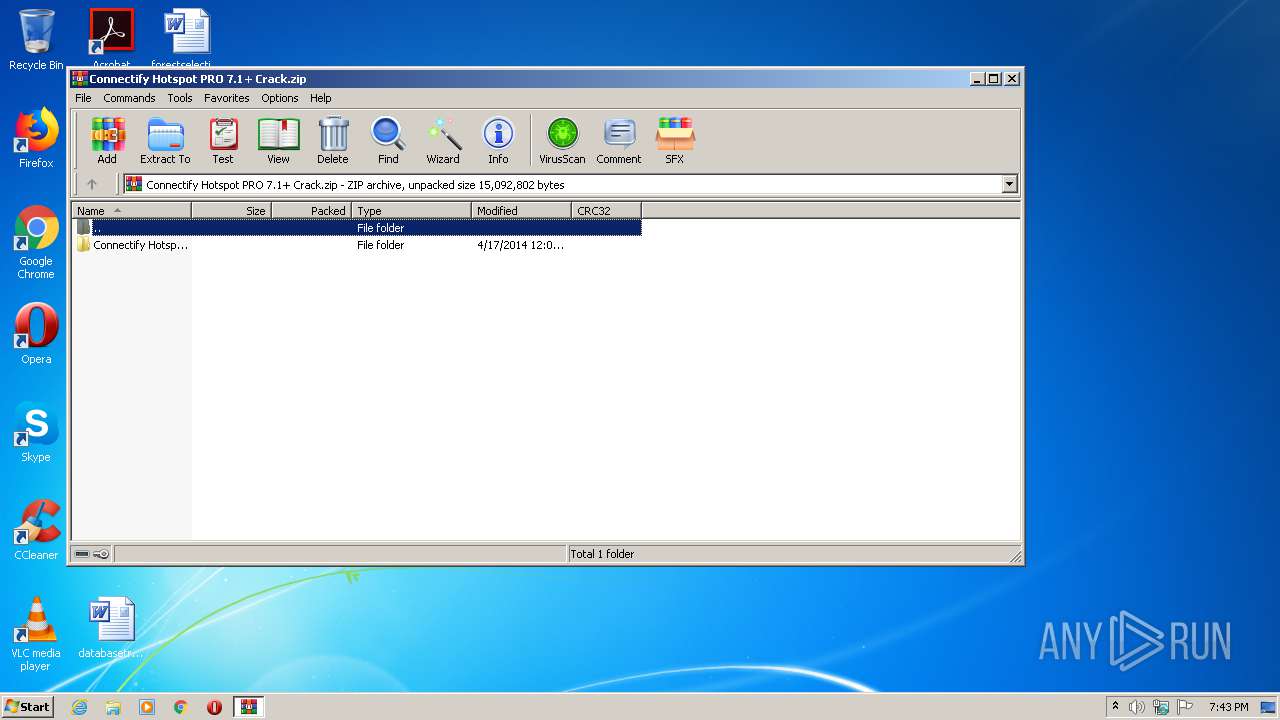
| File name: | Connectify Hotspot PRO 7.1+ Crack.zip |
| Full analysis: | https://app.any.run/tasks/f4e1fd64-c701-4014-b197-2b5405a39d74 |
| Verdict: | Malicious activity |
| Analysis date: | March 28, 2021, 18:42:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | C9FC63FB2AA61441CDAA5D0C8FAA435D |
| SHA1: | 8E19C49B48479B3FD892EE9E0A46AAE98FDFF628 |
| SHA256: | 5C05F9C595AC4DC20EBD3A4EFB0061F00491E220201DD71019C37A9912B0D4FB |
| SSDEEP: | 196608:Vj5LWEAyVvHsB1AaO8JB4+hXwMlK9NH1hv9GA2kpTDgwdmmm4AEe5:Vj56Xyl0vO8f4CwuQH1h32sTDLdNE |
MALICIOUS
Starts NET.EXE for service management
- cmd.exe (PID: 2104)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3180)
SUSPICIOUS
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2104)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3292)
Drops a file with too old compile date
- WinRAR.exe (PID: 3292)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3292)
INFO
Manual execution by user
- cmd.exe (PID: 2104)
- NOTEPAD.EXE (PID: 2920)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2014:04:17 12:07:03 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
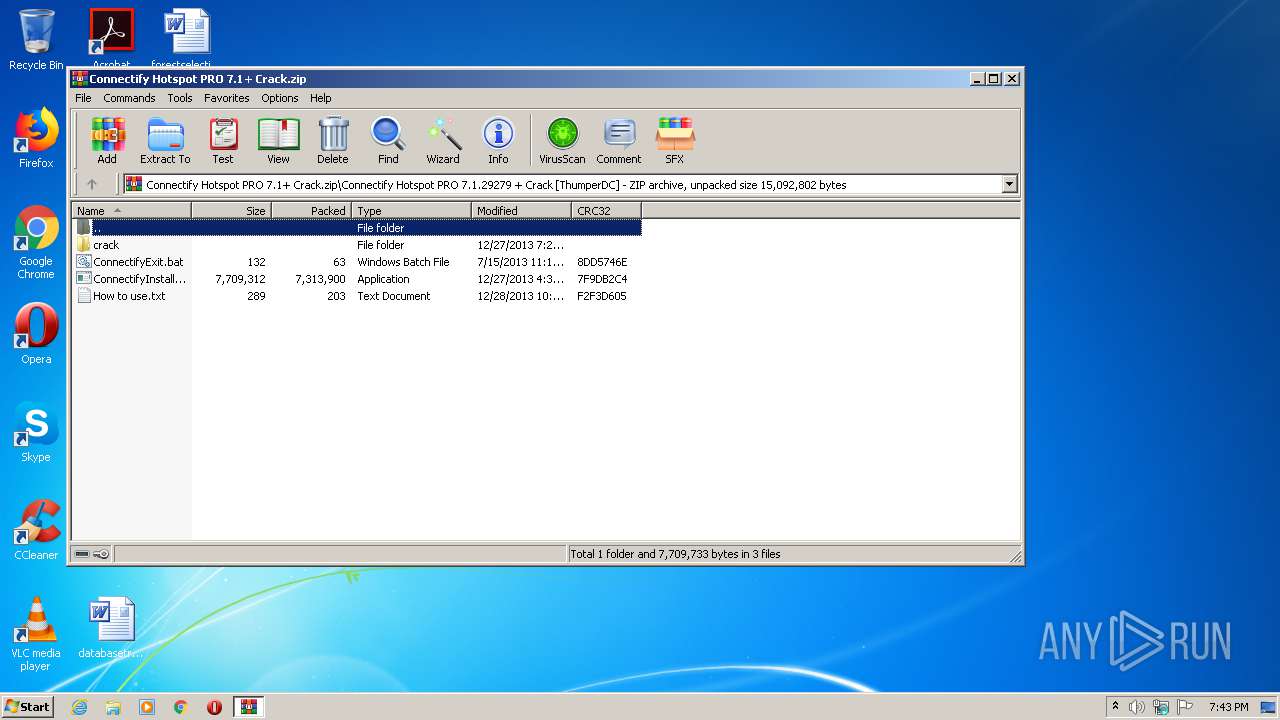
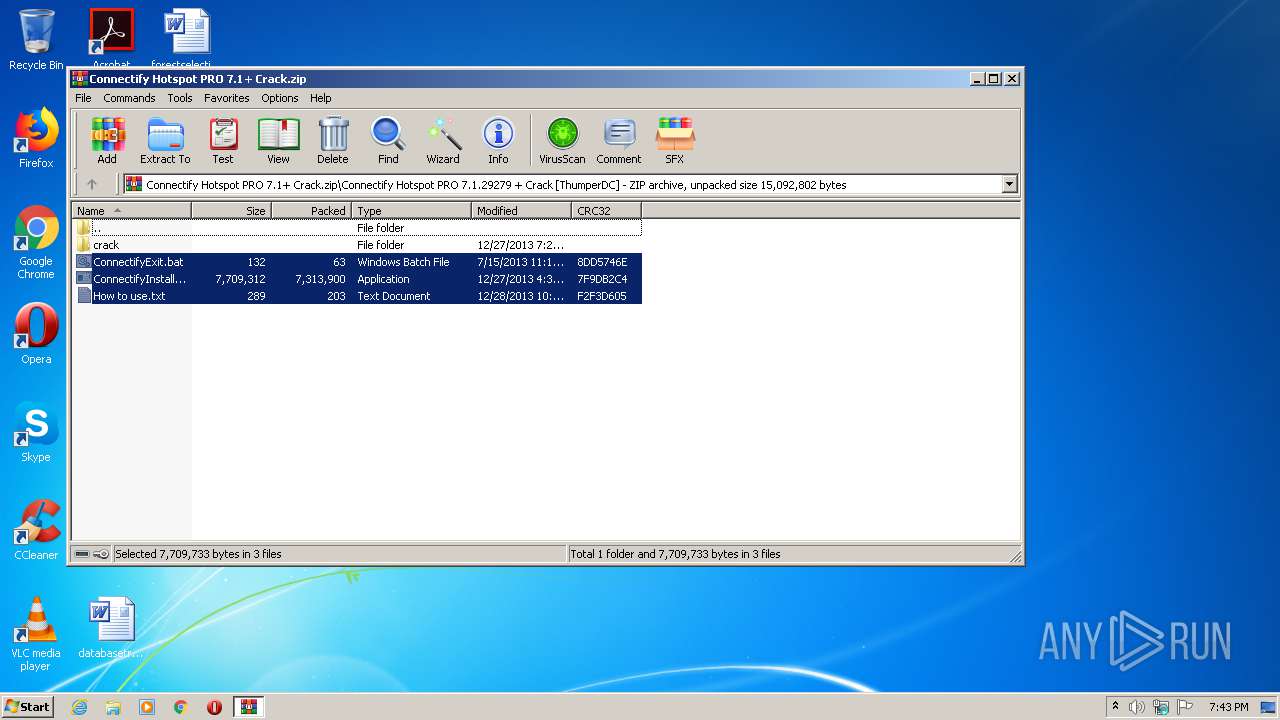
| ZipFileName: | Connectify Hotspot PRO 7.1.29279 + Crack [ThumperDC]/ |
Total processes
48
Monitored processes
9
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | taskkill /t /f /IM Connectify.exe | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
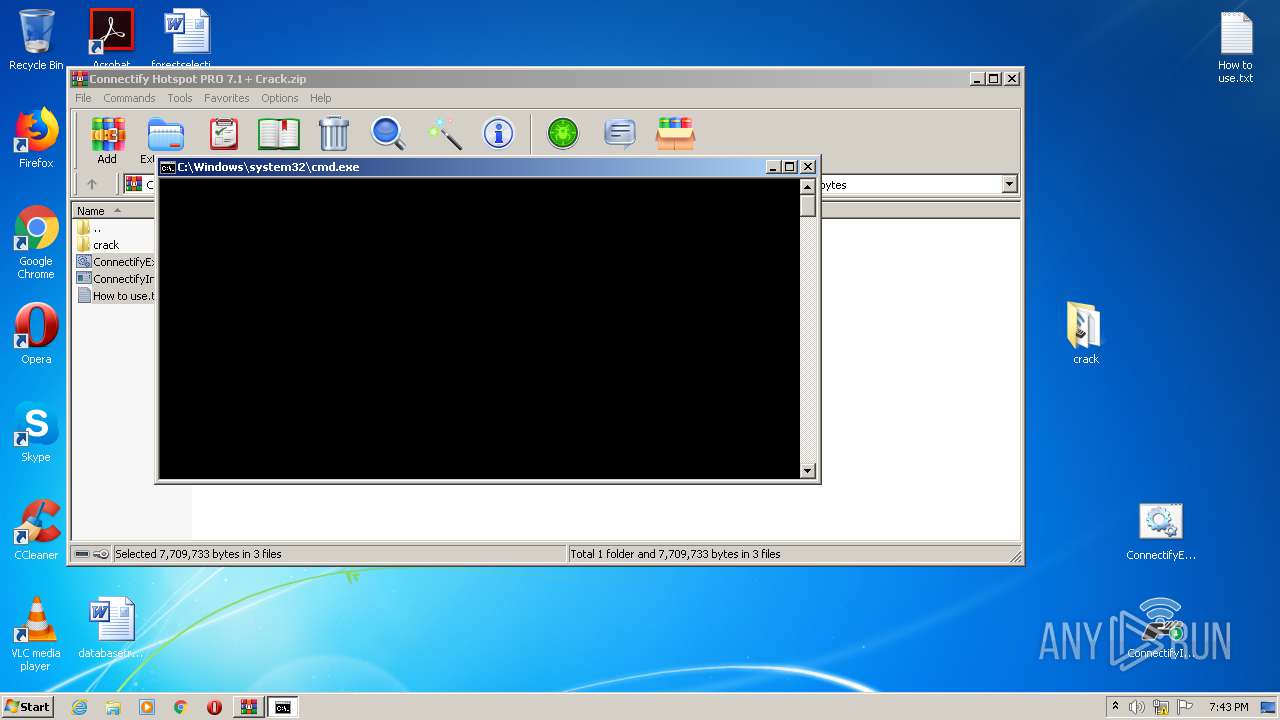
| 2104 | cmd /c ""C:\Users\admin\Desktop\ConnectifyExit.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 128 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2800 | taskkill /t /f /IM ConnectifyService.exe | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2852 | taskkill /t /f /IM Connectifyd.exe | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2880 | net stop connectify | C:\Windows\system32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
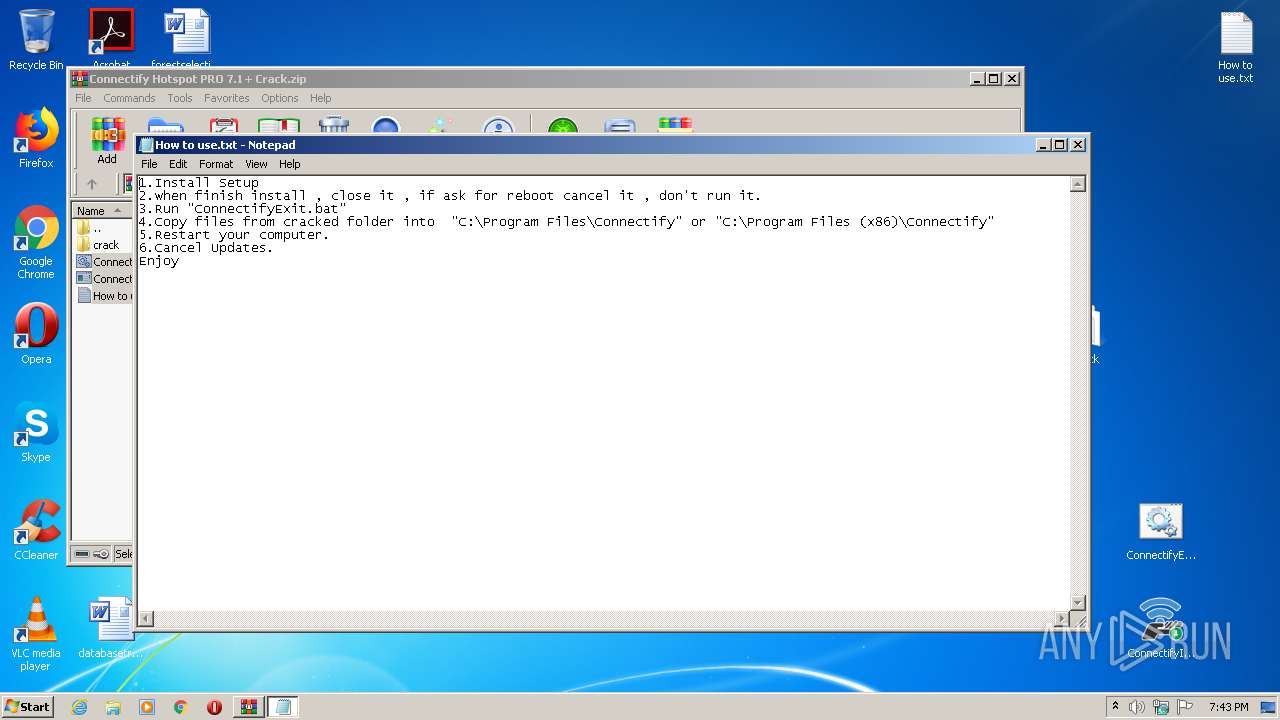
| 2920 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\How to use.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3180 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
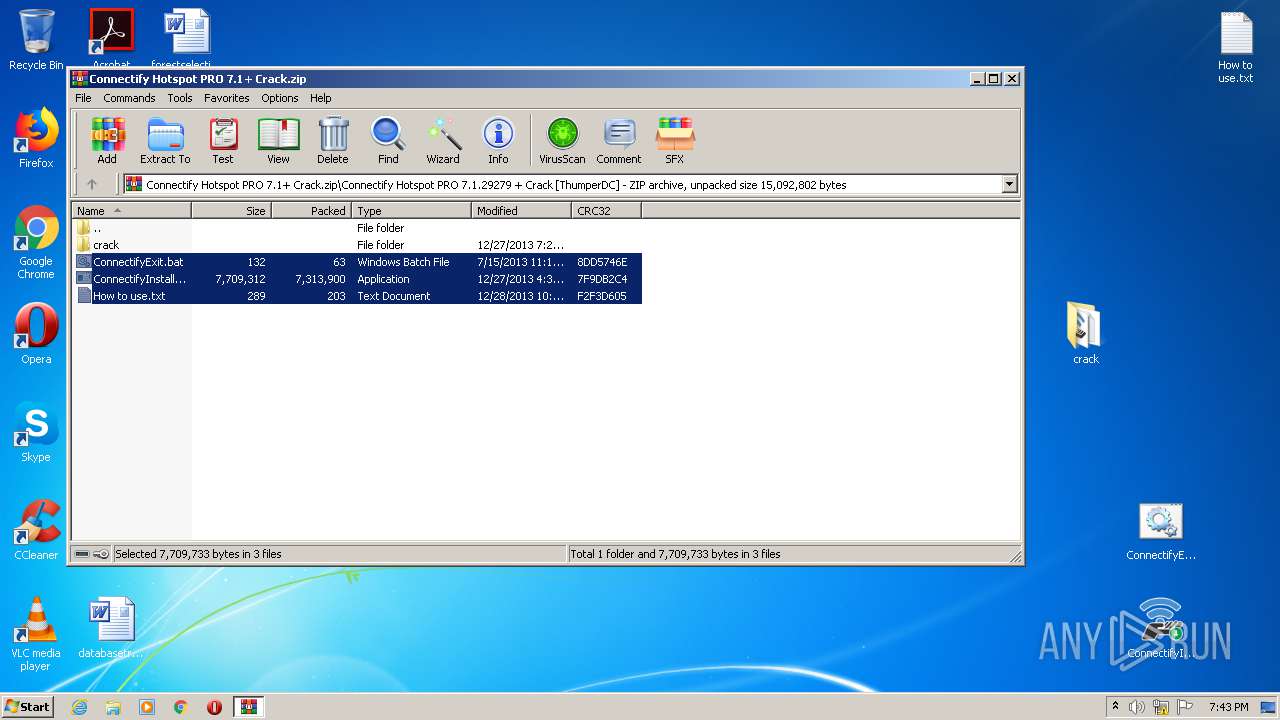
| 3292 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Connectify Hotspot PRO 7.1+ Crack.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3684 | C:\Windows\system32\net1 stop connectify | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
819
Read events
803
Write events
16
Delete events
0
Modification events
| (PID) Process: | (3292) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3292) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3292) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3292) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Connectify Hotspot PRO 7.1+ Crack.zip | |||
| (PID) Process: | (3292) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3292) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3292) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3292) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3292) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13D\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\acppage.dll,-6002 |
Value: Windows Batch File | |||
| (PID) Process: | (3292) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13D\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
Executable files
26
Suspicious files
0
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3292 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3292.32289\Connectify Hotspot PRO 7.1.29279 + Crack [ThumperDC]\crack\BuildProps.dll | executable | |
MD5:DE85EDF6548A1E2D8F114C58EE3487DC | SHA256:58B08053EE78D115DB13EB14A4B62C19180BB77E1C6557FD4EA5DB99D5B7416A | |||
| 3292 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3292.32289\Connectify Hotspot PRO 7.1.29279 + Crack [ThumperDC]\crack\DriverLib.dll | executable | |
MD5:D08F0E698F172D048782F4443D167047 | SHA256:F406126CD4D264F6E63DDA4EDD71F47CC76E0074FD1D87E90DA53E6108F19718 | |||
| 3292 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3292.32289\Connectify Hotspot PRO 7.1.29279 + Crack [ThumperDC]\crack\ErrorNumbers.dll | executable | |
MD5:35AC06455E5D40C65C080F1614312609 | SHA256:F6C90795BB659D4218AF6FE2A7024A14DFC25180332B052B4F2F36C50A30FA76 | |||
| 3292 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3292.32289\Connectify Hotspot PRO 7.1.29279 + Crack [ThumperDC]\crack\ConnectifyTheme.dll | executable | |
MD5:672B131F23694273021FEB7578AC4ABA | SHA256:BEC5CDF02E3742CAD06BFB18F55C8765FF6B35FEF407863D235162000C4A7017 | |||
| 3292 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3292.32289\Connectify Hotspot PRO 7.1.29279 + Crack [ThumperDC]\crack\Connectify.exe | executable | |
MD5:A247ECF997B98DC14C39287FE27937CC | SHA256:5E662CDCF63E2164B1D37B20DD980A235150A28DD243810BA03DC474BAE5C09A | |||
| 3292 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3292.32289\Connectify Hotspot PRO 7.1.29279 + Crack [ThumperDC]\crack\Ionic.Zip.dll | executable | |
MD5:BBAC65F85B5E35E4B1673E727D156B73 | SHA256:506AC418294228A3F57362E938A6EF23322C2C55F73002D2368AAB14F4A85B9C | |||
| 3292 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3292.32289\Connectify Hotspot PRO 7.1.29279 + Crack [ThumperDC]\crack\Interop.SHDocVw.dll | executable | |
MD5:2BF64C3D3324CFBECAD519E67EC97308 | SHA256:597A85DAE2DDAEBE12109081EC0FF58A716F0FC37A5177A5078D90D6D3E76B7F | |||
| 3292 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3292.32289\Connectify Hotspot PRO 7.1.29279 + Crack [ThumperDC]\crack\FsprgEmbeddedStore.dll | executable | |
MD5:1849323C317DDFD19AF178165DF786CA | SHA256:DE8E9016C94049BF54B67A33527482A65BE8A511C8F62C892113652FE67248B1 | |||
| 3292 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3292.32289\Connectify Hotspot PRO 7.1.29279 + Crack [ThumperDC]\crack\HttpServer.dll | executable | |
MD5:41E52D7C2E40F9CCE8F853CB2C747F10 | SHA256:93E47857CECD7BC9842788E445584E43073E2438FACB2D76E7837B6C40D87144 | |||
| 3292 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3292.32289\Connectify Hotspot PRO 7.1.29279 + Crack [ThumperDC]\crack\ndisapinet.dll | executable | |
MD5:72553EA997E637946A292C137071B10E | SHA256:CEF48B5C26937D896D9ACD062069D07B5E2ACD8ACCC26E22E7ACE93CFBF9AAB2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report