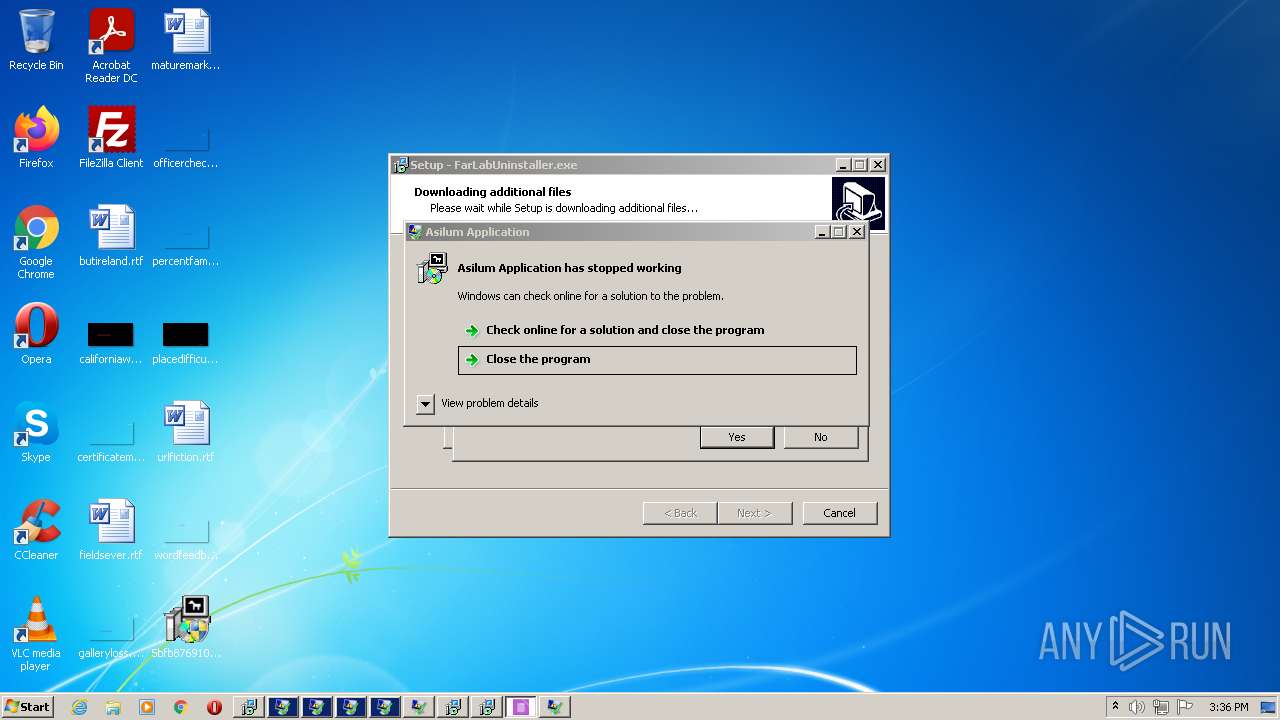
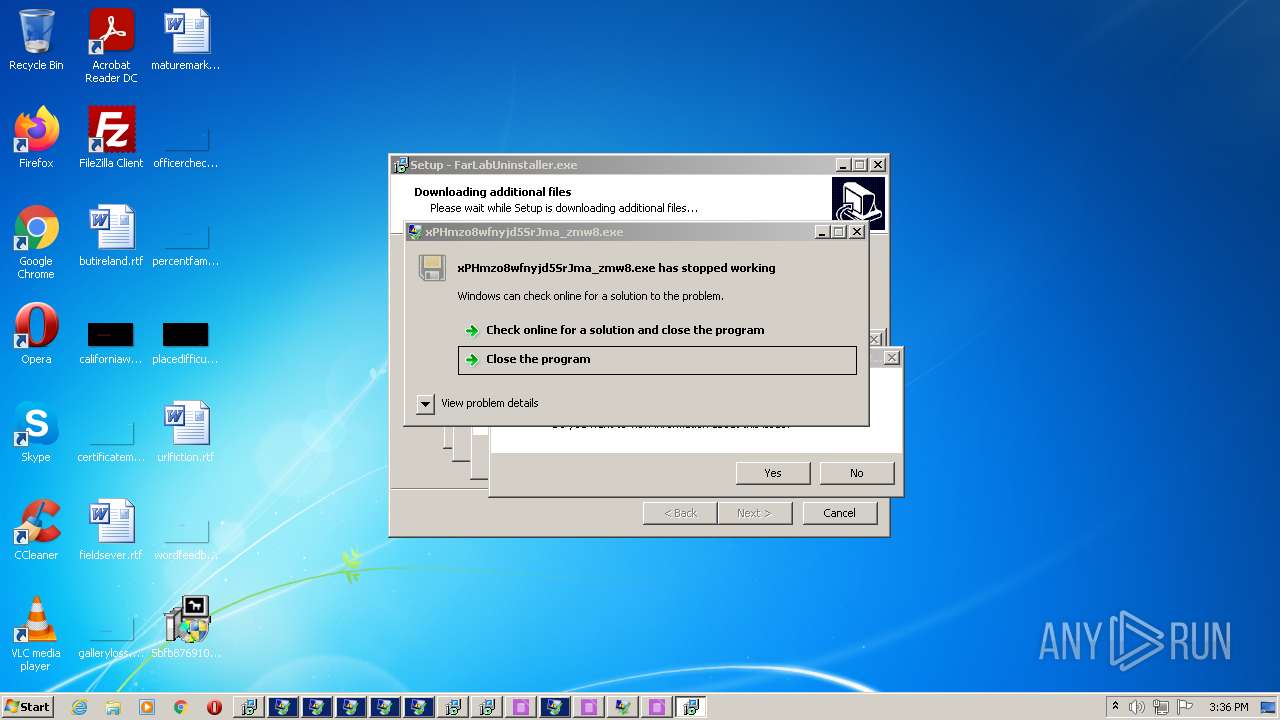
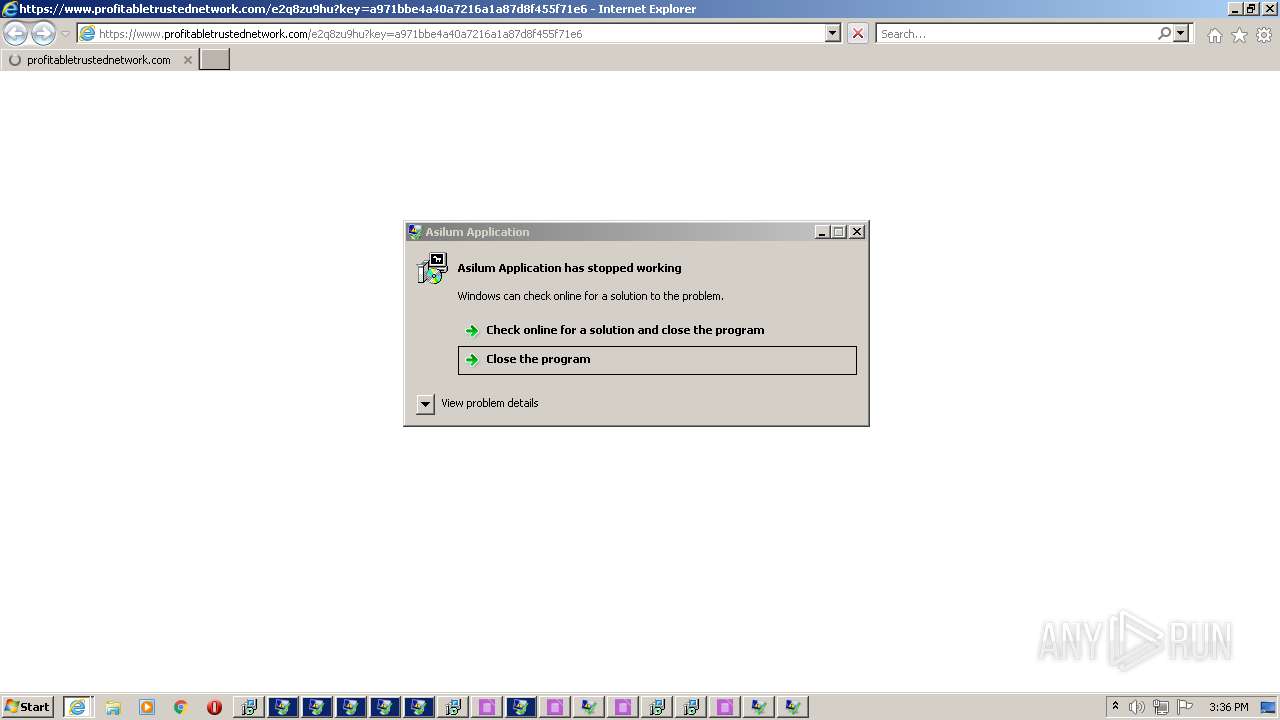
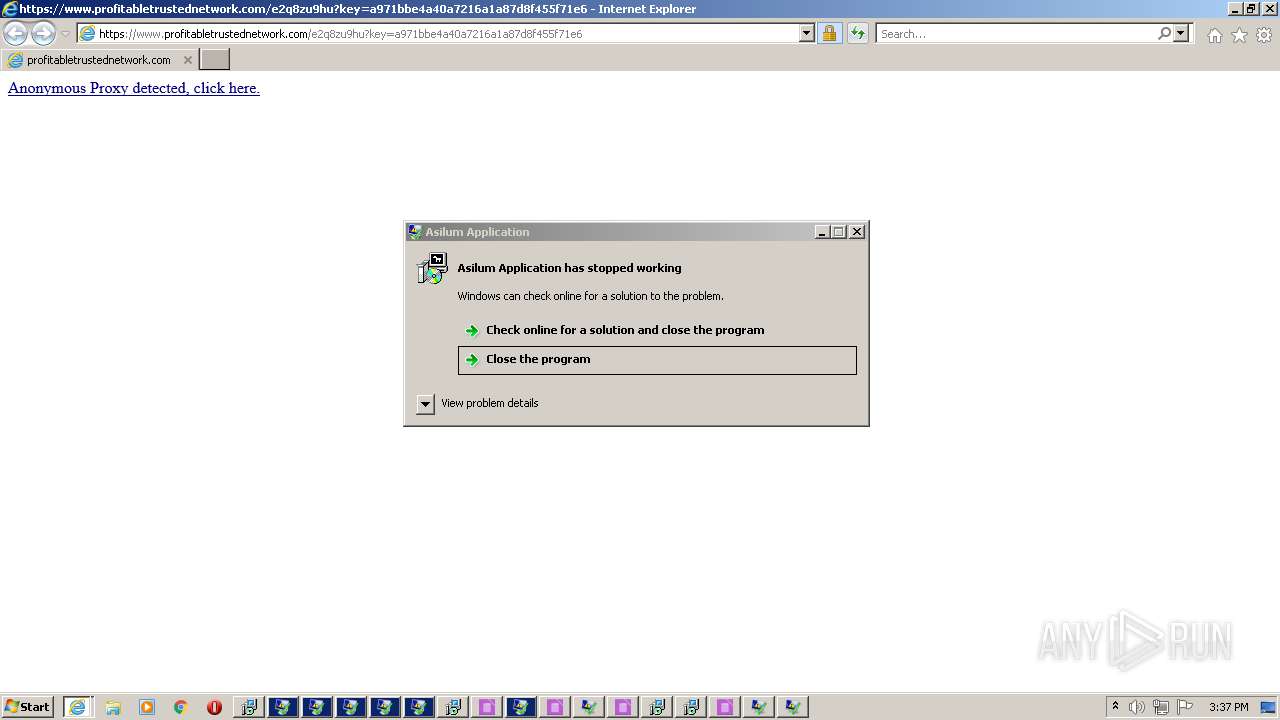
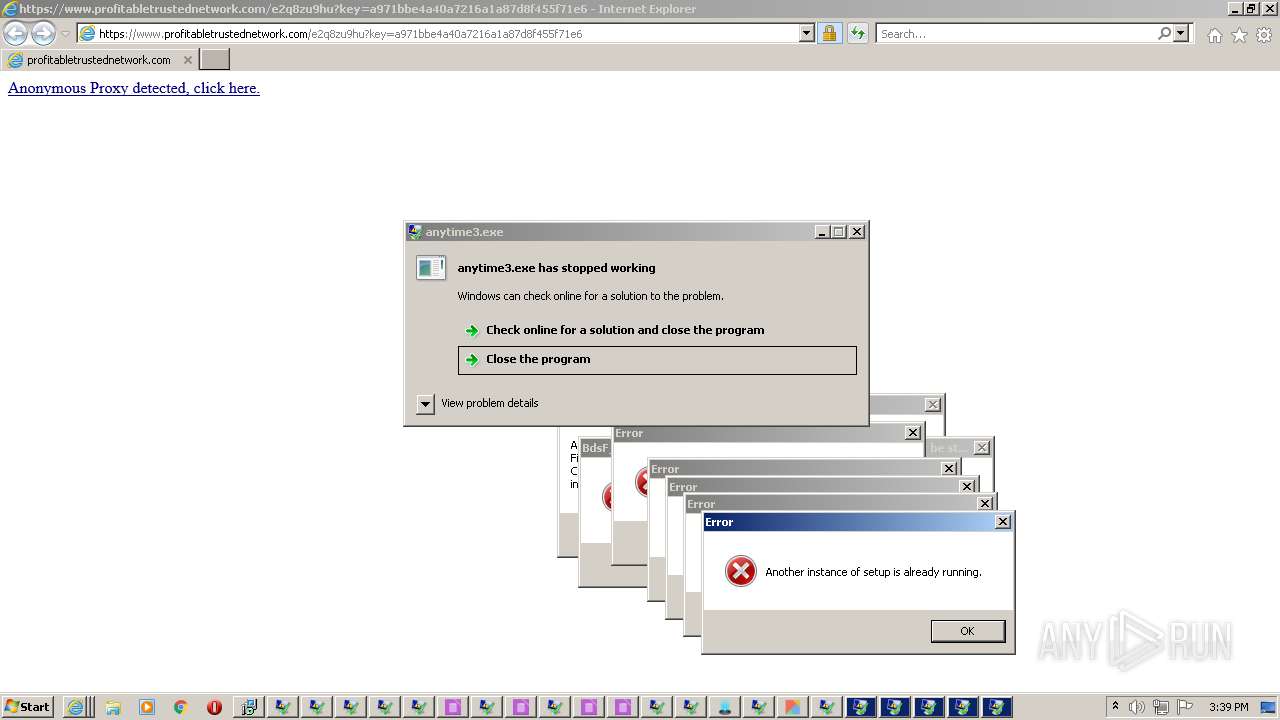
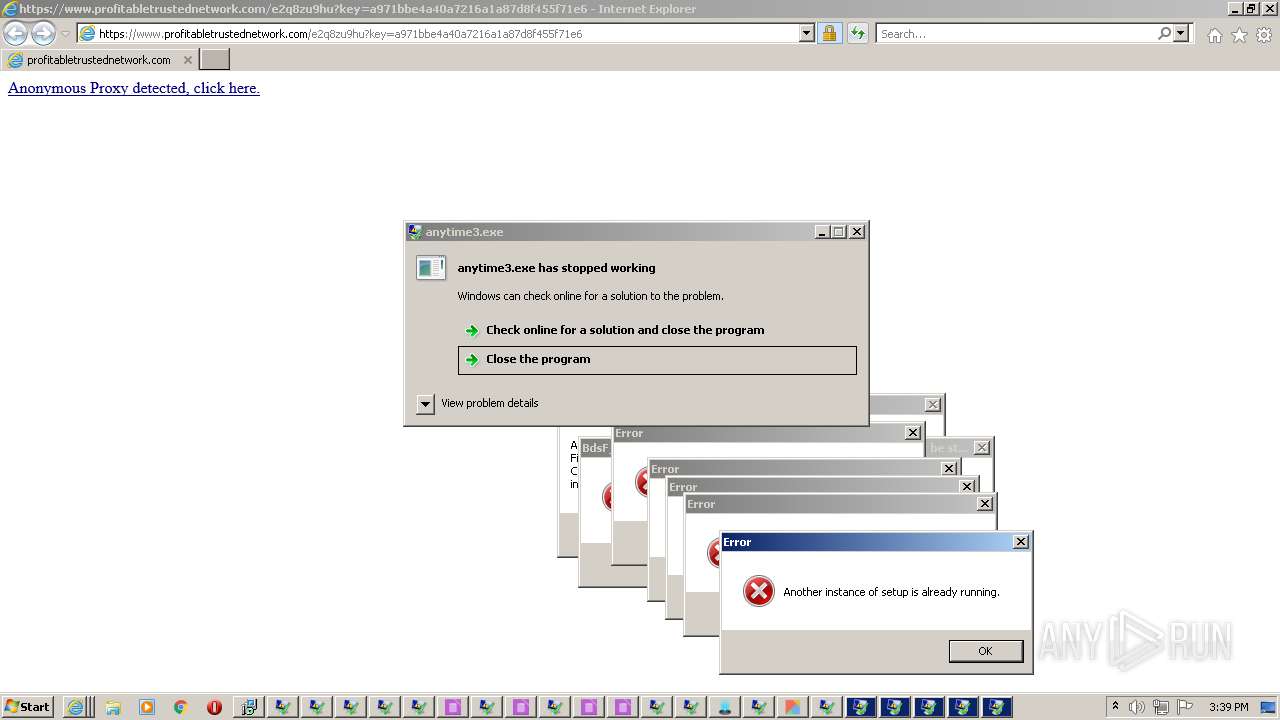
| File name: | 5bfb87691070668037df7a6bc1eac92bdb683ada3159b83c136146632835cb7f.exe |
| Full analysis: | https://app.any.run/tasks/9d9e0f9c-239c-40f4-99d9-9903614e9129 |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | January 03, 2022, 15:35:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | E4C99DCC117B45DBD02C49723DF0E5DA |
| SHA1: | 9B31D81AA541F473360574FDBDD86ACA2201033A |
| SHA256: | 5BFB87691070668037DF7A6BC1EAC92BDB683ADA3159B83C136146632835CB7F |
| SSDEEP: | 98304:Jm5tMCL1IVwr6K1JbcJSAzjznJQP2mHIb5cDXLqA9Nrq:J47X6mcLz/nJZmob5cDJvq |
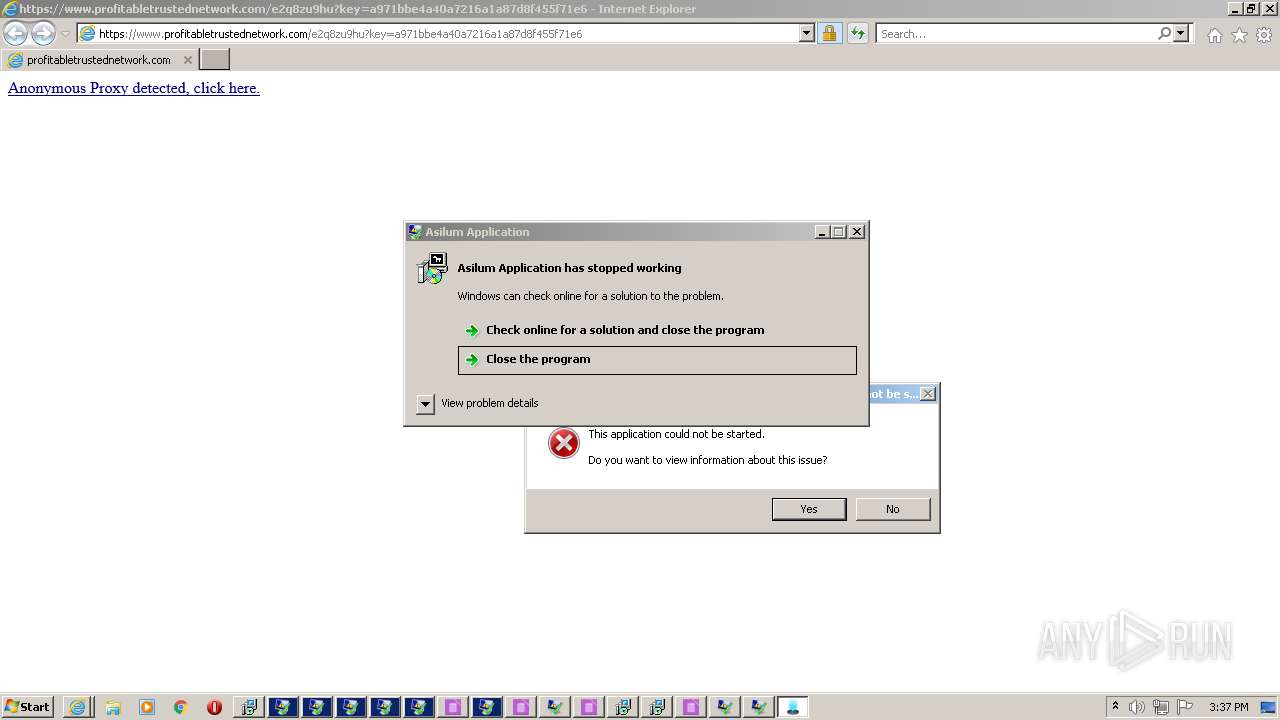
MALICIOUS
Drops executable file immediately after starts
- setup_installer.exe (PID: 2284)
- Fri05eeb2dae7b88520a.exe (PID: 3872)
- Fri05eeb2dae7b88520a.tmp (PID: 3732)
- Fri05eeb2dae7b88520a.exe (PID: 1284)
- Fri05eeb2dae7b88520a.tmp (PID: 3656)
- cmd.exe (PID: 2980)
- cmd.exe (PID: 2512)
- ag7CVdjSW97W3oRaIOR4Q3oQ.exe (PID: 2100)
- vbJgmru47WuZkTuLzaHrweCH.exe (PID: 2888)
- 8BWzAZaUY356vapXZ3r7riFu.exe (PID: 3112)
- cC95N5mvhiND9SaOJgZL_GrP.exe (PID: 3392)
- UXSvpgMlC9m9bBKQDE2JZTmm.exe (PID: 3664)
- _qPnAfbohQzsKyRjIAPGwvSD.exe (PID: 3956)
- 9ZztShvlpEcbYXbhysio6quv.exe (PID: 3288)
- _qPnAfbohQzsKyRjIAPGwvSD.tmp (PID: 768)
- 9ZztShvlpEcbYXbhysio6quv.tmp (PID: 3308)
- jhEkDR4LiF_xoKM1IRc2oolq.exe (PID: 5460)
- 76NC6H3jxnj41tBn5ReACOJx.exe (PID: 5488)
- P9Ccbs2yHGCPGAbWuC9lVqzm.exe (PID: 4372)
- whn8M8ZOzPDNHOMoUALHk6bF.exe (PID: 5872)
- whn8M8ZOzPDNHOMoUALHk6bF.tmp (PID: 4124)
- MAOJnCpxxB5VrEICaKPP1TBL.exe (PID: 13276)
- e3dwefw.exe (PID: 10540)
- jTZNXyp8ZD8XCh_p6Bwy1ozw.exe (PID: 7712)
- AW3v1Pv1azQc96UgcSRj2eON.exe (PID: 12444)
- AW3v1Pv1azQc96UgcSRj2eON.tmp (PID: 12972)
- LzmwAqmV.exe (PID: 13900)
- MyNotes Installation.exe (PID: 6928)
- chenyuying.exe (PID: 12060)
- 161.tmp (PID: 11692)
- DrvInst.exe (PID: 10552)
- 161.exe (PID: 6548)
- autosubplayer.exe (PID: 10872)
- autosubplayer.exe (PID: 13348)
- Roads License Agreement.exe (PID: 5636)
- EasyCalc License Agreement.exe (PID: 8448)
Executes PowerShell scripts
- cmd.exe (PID: 3740)
- cmd.exe (PID: 2380)
Application was dropped or rewritten from another process
- setup_installer.exe (PID: 2284)
- Fri05851d7f13.exe (PID: 2688)
- Fri0575b7d291a755f8.exe (PID: 2196)
- Fri05890d11cdb13f95e.exe (PID: 3704)
- Fri05a277b9a3d2.exe (PID: 1832)
- Fri05b5df5106928d62.exe (PID: 1472)
- Fri05f84fa77402bf.exe (PID: 3116)
- Fri05f84fa77402bf.exe (PID: 2428)
- Fri053f5694ea31c9a.exe (PID: 2492)
- Fri053f5694ea31c9a.exe (PID: 3288)
- Fri05a277b9a3d2.exe (PID: 2432)
- Fri055cc2a6e65.exe (PID: 2564)
- Fri05eeb2dae7b88520a.exe (PID: 3872)
- Fri05eeb2dae7b88520a.exe (PID: 1284)
- Fri051e1e7444.exe (PID: 2572)
- Fri0541e16ce794d258f.exe (PID: 3808)
- setup_install.exe (PID: 2148)
- Fri05cc28ce70b.exe (PID: 2216)
- EiV4.Exe (PID: 3856)
- Fri053f5694ea31c9a.exe (PID: 3008)
- ag7CVdjSW97W3oRaIOR4Q3oQ.exe (PID: 2100)
- vbJgmru47WuZkTuLzaHrweCH.exe (PID: 2888)
- 8BWzAZaUY356vapXZ3r7riFu.exe (PID: 3112)
- UXSvpgMlC9m9bBKQDE2JZTmm.exe (PID: 3664)
- cC95N5mvhiND9SaOJgZL_GrP.exe (PID: 3392)
- HSMNMHTbjtwpdzFM1XzkF8cR.exe (PID: 2732)
- IHyVJ19EQJnOQjW7pnzDJQaJ.exe (PID: 3288)
- EjrVa4svUGraKSpsvKX0OSEG.exe (PID: 2980)
- 38WaMQDe4eShkMw3z66q_F6i.exe (PID: 2300)
- mj_FCKU_1Gvo6WnWeDAwFlk1.exe (PID: 1788)
- jjMhwD8vifrmbi3EoANo0n87.exe (PID: 3816)
- UG4OUxxiIM92aDb0mIZeo27n.exe (PID: 4064)
- IHyVJ19EQJnOQjW7pnzDJQaJ.exe (PID: 3428)
- 2IDx4MjyyKCzrWVqZ7oRpu0L.exe (PID: 2568)
- CU3YoKS1pKwuxjVJDC_wI_9H.exe (PID: 2184)
- _plqVbpyQ72EAcDdXQafZHDS.exe (PID: 2204)
- _qPnAfbohQzsKyRjIAPGwvSD.exe (PID: 3956)
- gFsr_46eH9u5HTXyOeXC9r1V.exe (PID: 3756)
- 9ZztShvlpEcbYXbhysio6quv.exe (PID: 3288)
- 1A9E.tmp.exe (PID: 1028)
- m2TfQKJPCNVe5CpJOH7aekp7.exe (PID: 268)
- jhEkDR4LiF_xoKM1IRc2oolq.exe (PID: 5460)
- 76NC6H3jxnj41tBn5ReACOJx.exe (PID: 5488)
- P9Ccbs2yHGCPGAbWuC9lVqzm.exe (PID: 4372)
- xPHmzo8wfnyjd5SrJma_zmw8.exe (PID: 6140)
- PH1uwTXFZdm6S9tdW3hhxu1f.exe (PID: 4320)
- lmrRudIW6hC8f4tZCEZFScX1.exe (PID: 4768)
- 378E.tmp.exe (PID: 4192)
- AF8rGFxccUKYCIBH33I5lTUI.exe (PID: 3620)
- Vo8NvV9gwIArTRJTTs1VZ4WN.exe (PID: 2300)
- v00LWkGSaWY4x3B_h3ybD_hd.exe (PID: 5828)
- whn8M8ZOzPDNHOMoUALHk6bF.exe (PID: 5872)
- kLWXU7ly_PJqLRZqDfxkkISG.exe (PID: 5060)
- SdJonBkhYaN9iMb9EsPUKK1Q.exe (PID: 4500)
- JKe45826Dcj8CCzvf708WPoJ.exe (PID: 4416)
- 4F4A.tmp.exe (PID: 2608)
- ZHuruwiwawu.exe (PID: 5888)
- ZHuruwiwawu.exe (PID: 4272)
- 7484765222.exe (PID: 6120)
- 68FE.tmp.exe (PID: 6132)
- Nohululito.exe (PID: 4532)
- SHazhobajaezhae.exe (PID: 7596)
- 8587610666.exe (PID: 6752)
- Wizhagaevaeko.exe (PID: 4004)
- Caehyxicaqe.exe (PID: 6732)
- iwKI0DEILCOs0EA7JE_ZYkrd.exe (PID: 8428)
- KdfEj_2TX4Gp0Nu_7E2BBvGy.exe (PID: 10048)
- Funywacaefa.exe (PID: 6924)
- rSHu1NJFyRf28EYfj0aYOh9q.exe (PID: 13412)
- xeyKz1D17PVy_DXmozuhOdcw.exe (PID: 8028)
- UG4OUxxiIM92aDb0mIZeo27n.exe (PID: 13828)
- UG4OUxxiIM92aDb0mIZeo27n.exe (PID: 11156)
- UG4OUxxiIM92aDb0mIZeo27n.exe (PID: 9872)
- UG4OUxxiIM92aDb0mIZeo27n.exe (PID: 8576)
- UG4OUxxiIM92aDb0mIZeo27n.exe (PID: 9568)
- UG4OUxxiIM92aDb0mIZeo27n.exe (PID: 7372)
- UG4OUxxiIM92aDb0mIZeo27n.exe (PID: 1332)
- UG4OUxxiIM92aDb0mIZeo27n.exe (PID: 8208)
- UG4OUxxiIM92aDb0mIZeo27n.exe (PID: 10776)
- UG4OUxxiIM92aDb0mIZeo27n.exe (PID: 10556)
- AdvancedRun.exe (PID: 9072)
- AdvancedRun.exe (PID: 9964)
- MAOJnCpxxB5VrEICaKPP1TBL.exe (PID: 13276)
- 2mfRD25PYb2qCl_Lq_jTnazX.exe (PID: 13660)
- installer.exe (PID: 5028)
- installer.exe (PID: 7904)
- _dpOQFqSEbu1yisLxJYasR8i.exe (PID: 5420)
- _dpOQFqSEbu1yisLxJYasR8i.exe (PID: 12800)
- random.exe (PID: 9792)
- random.exe (PID: 3224)
- jTZNXyp8ZD8XCh_p6Bwy1ozw.exe (PID: 7712)
- AW3v1Pv1azQc96UgcSRj2eON.exe (PID: 12444)
- whw.exe (PID: 11240)
- e3dwefw.exe (PID: 10540)
- GcleanerEU.exe (PID: 7780)
- GcleanerEU.exe (PID: 5792)
- o0u1oYVCSrrEorCJhdBq8sAb.exe (PID: 12860)
- random.exe (PID: 11892)
- random.exe (PID: 8752)
- AdvancedRun.exe (PID: 11784)
- AdvancedRun.exe (PID: 2260)
- SdJonBkhYaN9iMb9EsPUKK1Q.exe (PID: 8456)
- SdJonBkhYaN9iMb9EsPUKK1Q.exe (PID: 6948)
- SdJonBkhYaN9iMb9EsPUKK1Q.exe (PID: 1328)
- SdJonBkhYaN9iMb9EsPUKK1Q.exe (PID: 14312)
- SdJonBkhYaN9iMb9EsPUKK1Q.exe (PID: 9348)
- SdJonBkhYaN9iMb9EsPUKK1Q.exe (PID: 1148)
- SdJonBkhYaN9iMb9EsPUKK1Q.exe (PID: 13272)
- SdJonBkhYaN9iMb9EsPUKK1Q.exe (PID: 8644)
- SdJonBkhYaN9iMb9EsPUKK1Q.exe (PID: 5648)
- SdJonBkhYaN9iMb9EsPUKK1Q.exe (PID: 9088)
- Install.exe (PID: 10980)
- sdfsd.exe (PID: 12528)
- 0GT0VvHyDZrSeiPVmt2rOb3t.exe (PID: 10052)
- Install.exe (PID: 10484)
- Xugovocylae.exe (PID: 8108)
- Cidaecashehu.exe (PID: 2080)
- 0zXGRheNbfb6gDNyfNaowrnY.exe (PID: 9880)
- installer.exe (PID: 10108)
- Install.exe (PID: 14176)
- askinstall42.exe (PID: 9000)
- random.exe (PID: 13228)
- Install.exe (PID: 4668)
- random.exe (PID: 9968)
- clipper.exe (PID: 8572)
- gcleaner.exe (PID: 12824)
- gcleaner.exe (PID: 14284)
- LzmwAqmV.exe (PID: 13900)
- setupww1.exe (PID: 7332)
- anytime1.exe (PID: 13460)
- anytime4.exe (PID: 3196)
- anytime2.exe (PID: 12468)
- inst.exe (PID: 13920)
- RobCleanerInstll33132.exe (PID: 11196)
- logger.exe (PID: 2392)
- anytime3.exe (PID: 3444)
- Proxyupd.exe (PID: 12164)
- askinstall25.exe (PID: 13712)
- Fixfile01.exe (PID: 14144)
- setup.exe (PID: 9800)
- jli.exe (PID: 13800)
- jli.exe (PID: 9852)
- MyNotes Installation.exe (PID: 6928)
- installer.exe (PID: 588)
- installer.exe (PID: 11544)
- e72756b9-3e61-49d0-98c2-5ba1255e38e8.exe (PID: 11072)
- chenyuying.exe (PID: 9236)
- askinstall35.exe (PID: 9528)
- chenyuying.exe (PID: 12060)
- random.exe (PID: 11652)
- random.exe (PID: 7128)
- random.exe (PID: 13072)
- random.exe (PID: 8036)
- 161.exe (PID: 6548)
- tapinstall.exe (PID: 8924)
- tapinstall.exe (PID: 12980)
- PyuJGVV.exe (PID: 4908)
- installer.exe (PID: 10404)
- mask_svc.exe (PID: 11504)
- random.exe (PID: 7000)
- random.exe (PID: 12864)
- mask_svc.exe (PID: 9984)
- mask_svc.exe (PID: 8408)
- autosubplayer.exe (PID: 9820)
- toolspab3.exe (PID: 9508)
- autosubplayer.exe (PID: 11196)
- toolspab3.exe (PID: 4176)
- hCisxSr.exe (PID: 6272)
- autosubplayer.exe (PID: 2416)
- autosubplayer.exe (PID: 8992)
- installer.exe (PID: 8492)
- autosubplayer.exe (PID: 10872)
- autosubplayer.exe (PID: 13348)
- MaskVPNUpdate.exe (PID: 13728)
- EasyCalc License Agreement.exe (PID: 8448)
Loads dropped or rewritten executable
- setup_install.exe (PID: 2148)
- rundll32.exe (PID: 3180)
- vbJgmru47WuZkTuLzaHrweCH.exe (PID: 2888)
- 8BWzAZaUY356vapXZ3r7riFu.exe (PID: 3112)
- UXSvpgMlC9m9bBKQDE2JZTmm.exe (PID: 3664)
- cC95N5mvhiND9SaOJgZL_GrP.exe (PID: 3392)
- jhEkDR4LiF_xoKM1IRc2oolq.exe (PID: 5460)
- 76NC6H3jxnj41tBn5ReACOJx.exe (PID: 5488)
- P9Ccbs2yHGCPGAbWuC9lVqzm.exe (PID: 4372)
- enJg7NoG88QfYbCNfm8CGIxY.exe (PID: 1832)
- bpQalRIkWhtCbaq_LU6Sjqxc.exe (PID: 4932)
- MAOJnCpxxB5VrEICaKPP1TBL.exe (PID: 13276)
- rundll32.exe (PID: 9884)
- installer.exe (PID: 5028)
- MsiExec.exe (PID: 10032)
- MsiExec.exe (PID: 12312)
- MsiExec.exe (PID: 2440)
- rundll32.exe (PID: 6464)
- rundll32.exe (PID: 3092)
- rundll32.exe (PID: 13316)
- MyNotes Installation.exe (PID: 6928)
- rundll32.exe (PID: 11536)
- rundll32.exe (PID: 10696)
- rundll32.exe (PID: 9180)
- rundll32.exe (PID: 10764)
- mask_svc.exe (PID: 9984)
- lighteningplayer-cache-gen.exe (PID: 11624)
- autosubplayer.exe (PID: 9820)
- autosubplayer.exe (PID: 11196)
- lighteningplayer-cache-gen.exe (PID: 7028)
- autosubplayer.exe (PID: 2416)
- lighteningplayer-cache-gen.exe (PID: 2004)
- lighteningplayer-cache-gen.exe (PID: 11744)
- lighteningplayer-cache-gen.exe (PID: 5792)
- autosubplayer.exe (PID: 8992)
- rundll32.EXE (PID: 5848)
- autosubplayer.exe (PID: 13348)
- autosubplayer.exe (PID: 10872)
- MaskVPNUpdate.exe (PID: 13728)
- Roads License Agreement.exe (PID: 5636)
- lighteningplayer-cache-gen.exe (PID: 5748)
- EasyCalc License Agreement.exe (PID: 8448)
Changes settings of System certificates
- Fri05851d7f13.exe (PID: 2688)
- Fri051e1e7444.exe (PID: 2572)
- HSMNMHTbjtwpdzFM1XzkF8cR.exe (PID: 2732)
- RegAsm.exe (PID: 448)
- tapinstall.exe (PID: 12980)
- 161.tmp (PID: 11692)
Application was injected by another process
- svchost.exe (PID: 884)
Runs injected code in another process
- rundll32.exe (PID: 3180)
- rundll32.exe (PID: 9884)
- rundll32.exe (PID: 6464)
- rundll32.exe (PID: 3092)
- rundll32.exe (PID: 13316)
- rundll32.exe (PID: 11536)
- rundll32.exe (PID: 10696)
- rundll32.exe (PID: 10764)
Disables Windows Defender
- Fri051e1e7444.exe (PID: 2572)
- Fri05b5df5106928d62.exe (PID: 1472)
- KdfEj_2TX4Gp0Nu_7E2BBvGy.exe (PID: 10048)
Connects to CnC server
- Fri051e1e7444.exe (PID: 2572)
- Fri05b5df5106928d62.exe (PID: 1472)
- 38WaMQDe4eShkMw3z66q_F6i.exe (PID: 2300)
- jjMhwD8vifrmbi3EoANo0n87.exe (PID: 3816)
- EjrVa4svUGraKSpsvKX0OSEG.exe (PID: 2980)
- RegAsm.exe (PID: 448)
- HSMNMHTbjtwpdzFM1XzkF8cR.exe (PID: 2732)
- lmrRudIW6hC8f4tZCEZFScX1.exe (PID: 4768)
- PH1uwTXFZdm6S9tdW3hhxu1f.exe (PID: 4320)
- RegAsm.exe (PID: 5984)
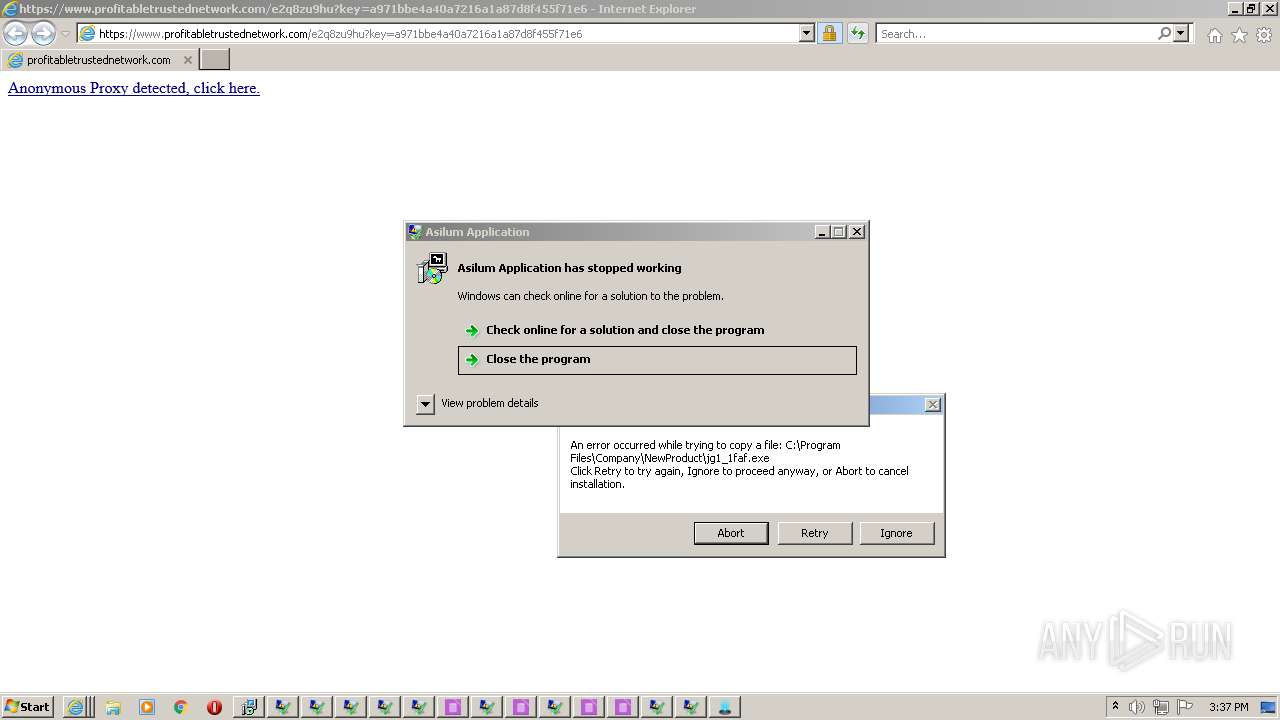
- jg1_1faf.exe (PID: 7552)
- AF8rGFxccUKYCIBH33I5lTUI.exe (PID: 3620)
- KdfEj_2TX4Gp0Nu_7E2BBvGy.exe (PID: 10048)
- whw.exe (PID: 11240)
- Proxyupd.exe (PID: 12164)
- askinstall35.exe (PID: 9528)
REDLINE was detected
- 38WaMQDe4eShkMw3z66q_F6i.exe (PID: 2300)
- jjMhwD8vifrmbi3EoANo0n87.exe (PID: 3816)
- RegAsm.exe (PID: 448)
- lmrRudIW6hC8f4tZCEZFScX1.exe (PID: 4768)
- RegAsm.exe (PID: 5984)
- whw.exe (PID: 11240)
- Proxyupd.exe (PID: 12164)
Actions looks like stealing of personal data
- jjMhwD8vifrmbi3EoANo0n87.exe (PID: 3816)
- 38WaMQDe4eShkMw3z66q_F6i.exe (PID: 2300)
- RegAsm.exe (PID: 448)
- lmrRudIW6hC8f4tZCEZFScX1.exe (PID: 4768)
- enJg7NoG88QfYbCNfm8CGIxY.exe (PID: 1832)
- RegAsm.exe (PID: 5984)
- bpQalRIkWhtCbaq_LU6Sjqxc.exe (PID: 4932)
- jg1_1faf.exe (PID: 7552)
- whw.exe (PID: 11240)
- LzmwAqmV.exe (PID: 13900)
- e72756b9-3e61-49d0-98c2-5ba1255e38e8.exe (PID: 11072)
- Proxyupd.exe (PID: 12164)
- askinstall35.exe (PID: 9528)
- Fixfile01.exe (PID: 14144)
- hCisxSr.exe (PID: 6272)
Steals credentials from Web Browsers
- jjMhwD8vifrmbi3EoANo0n87.exe (PID: 3816)
- 38WaMQDe4eShkMw3z66q_F6i.exe (PID: 2300)
- RegAsm.exe (PID: 448)
- lmrRudIW6hC8f4tZCEZFScX1.exe (PID: 4768)
- enJg7NoG88QfYbCNfm8CGIxY.exe (PID: 1832)
- RegAsm.exe (PID: 5984)
- bpQalRIkWhtCbaq_LU6Sjqxc.exe (PID: 4932)
- jg1_1faf.exe (PID: 7552)
- whw.exe (PID: 11240)
- Proxyupd.exe (PID: 12164)
- askinstall35.exe (PID: 9528)
- Fixfile01.exe (PID: 14144)
- hCisxSr.exe (PID: 6272)
VIDAR was detected
- enJg7NoG88QfYbCNfm8CGIxY.exe (PID: 1832)
- bpQalRIkWhtCbaq_LU6Sjqxc.exe (PID: 4932)
- Fixfile01.exe (PID: 14144)
Uses Task Scheduler to run other applications
- HSMNMHTbjtwpdzFM1XzkF8cR.exe (PID: 2732)
- AF8rGFxccUKYCIBH33I5lTUI.exe (PID: 3620)
- Install.exe (PID: 10484)
- Install.exe (PID: 4668)
- PyuJGVV.exe (PID: 4908)
- hCisxSr.exe (PID: 6272)
- rundll32.EXE (PID: 5848)
Uses Task Scheduler to autorun other applications
- HSMNMHTbjtwpdzFM1XzkF8cR.exe (PID: 2732)
- AF8rGFxccUKYCIBH33I5lTUI.exe (PID: 3620)
- hCisxSr.exe (PID: 6272)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 5108)
- schtasks.exe (PID: 3320)
- schtasks.exe (PID: 6504)
- schtasks.exe (PID: 6864)
- MsiExec.exe (PID: 12312)
- schtasks.exe (PID: 11360)
- schtasks.exe (PID: 9076)
- installer.exe (PID: 5028)
- schtasks.exe (PID: 2488)
- schtasks.exe (PID: 2980)
- svchost.exe (PID: 884)
- schtasks.exe (PID: 3996)
- schtasks.exe (PID: 12148)
- schtasks.exe (PID: 9144)
- schtasks.exe (PID: 4704)
- schtasks.exe (PID: 7204)
- schtasks.exe (PID: 11040)
- schtasks.exe (PID: 9944)
- schtasks.exe (PID: 736)
- schtasks.exe (PID: 7544)
- schtasks.exe (PID: 6564)
- schtasks.exe (PID: 6484)
- schtasks.exe (PID: 13992)
- schtasks.exe (PID: 2596)
- schtasks.exe (PID: 5844)
- schtasks.exe (PID: 4504)
- schtasks.exe (PID: 10104)
- schtasks.exe (PID: 10668)
Writes to a start menu file
- 378E.tmp.exe (PID: 4192)
- 68FE.tmp.exe (PID: 6132)
Changes the autorun value in the registry
- Bouderbela.exe (PID: 4824)
- Bouderbela.exe (PID: 5212)
- Bouderbela.exe (PID: 6972)
- e3dwefw.exe (PID: 10540)
- DrvInst.exe (PID: 11508)
- svchost.exe (PID: 884)
Stealing of credential data
- enJg7NoG88QfYbCNfm8CGIxY.exe (PID: 1832)
- bpQalRIkWhtCbaq_LU6Sjqxc.exe (PID: 4932)
- e72756b9-3e61-49d0-98c2-5ba1255e38e8.exe (PID: 11072)
- Fixfile01.exe (PID: 14144)
Changes the login/logoff helper path in the registry
- UG4OUxxiIM92aDb0mIZeo27n.exe (PID: 4064)
- SdJonBkhYaN9iMb9EsPUKK1Q.exe (PID: 4500)
Stops/Deletes Windows Defender service via SC.exe
- AdvancedRun.exe (PID: 9072)
- AdvancedRun.exe (PID: 11784)
Registers / Runs the DLL via REGSVR32.EXE
- Bk8YtZl4A3N6x8qYcOCqCeqX.exe (PID: 10876)
Loads the Task Scheduler DLL interface
- schtasks.exe (PID: 9112)
- schtasks.exe (PID: 12668)
- schtasks.exe (PID: 1460)
- schtasks.exe (PID: 5524)
- schtasks.exe (PID: 3188)
Modifies exclusions in Windows Defender
- reg.exe (PID: 10544)
- reg.exe (PID: 7008)
- reg.exe (PID: 332)
- reg.exe (PID: 7592)
- reg.exe (PID: 5816)
- reg.exe (PID: 13992)
- reg.exe (PID: 12680)
- reg.exe (PID: 12512)
- reg.exe (PID: 3904)
Modifies files in Chrome extension folder
- hCisxSr.exe (PID: 6272)
SUSPICIOUS
Reads the computer name
- 5bfb87691070668037df7a6bc1eac92bdb683ada3159b83c136146632835cb7f.exe (PID: 4000)
- setup_installer.exe (PID: 2284)
- powershell.exe (PID: 3032)
- powershell.exe (PID: 2940)
- Fri05cc28ce70b.exe (PID: 2216)
- setup_install.exe (PID: 2148)
- Fri053f5694ea31c9a.exe (PID: 2492)
- Fri055cc2a6e65.exe (PID: 2564)
- Fri05a277b9a3d2.exe (PID: 1832)
- Fri05f84fa77402bf.exe (PID: 2428)
- Fri05890d11cdb13f95e.exe (PID: 3704)
- Fri05b5df5106928d62.exe (PID: 1472)
- Fri051e1e7444.exe (PID: 2572)
- Fri0575b7d291a755f8.exe (PID: 2196)
- Fri05851d7f13.exe (PID: 2688)
- Fri05eeb2dae7b88520a.tmp (PID: 3732)
- mshta.exe (PID: 1144)
- Fri05eeb2dae7b88520a.tmp (PID: 3656)
- EiV4.Exe (PID: 3856)
- mshta.exe (PID: 2104)
- mshta.exe (PID: 2744)
- Fri05f84fa77402bf.exe (PID: 3116)
- Fri05a277b9a3d2.exe (PID: 2432)
- Fri053f5694ea31c9a.exe (PID: 3008)
- 8BWzAZaUY356vapXZ3r7riFu.exe (PID: 3112)
- vbJgmru47WuZkTuLzaHrweCH.exe (PID: 2888)
- cC95N5mvhiND9SaOJgZL_GrP.exe (PID: 3392)
- UXSvpgMlC9m9bBKQDE2JZTmm.exe (PID: 3664)
- HSMNMHTbjtwpdzFM1XzkF8cR.exe (PID: 2732)
- 38WaMQDe4eShkMw3z66q_F6i.exe (PID: 2300)
- EjrVa4svUGraKSpsvKX0OSEG.exe (PID: 2980)
- UG4OUxxiIM92aDb0mIZeo27n.exe (PID: 4064)
- jjMhwD8vifrmbi3EoANo0n87.exe (PID: 3816)
- 2IDx4MjyyKCzrWVqZ7oRpu0L.exe (PID: 2568)
- powershell.exe (PID: 688)
- _plqVbpyQ72EAcDdXQafZHDS.exe (PID: 2204)
- powershell.exe (PID: 2616)
- powershell.exe (PID: 2624)
- gFsr_46eH9u5HTXyOeXC9r1V.exe (PID: 3756)
- _qPnAfbohQzsKyRjIAPGwvSD.tmp (PID: 768)
- 9ZztShvlpEcbYXbhysio6quv.tmp (PID: 3308)
- RegAsm.exe (PID: 448)
- enJg7NoG88QfYbCNfm8CGIxY.exe (PID: 1832)
- rIB1BkwDhthKpnxajOOpLgh3.exe (PID: 2060)
- 1A9E.tmp.exe (PID: 1028)
- m2TfQKJPCNVe5CpJOH7aekp7.exe (PID: 268)
- ov1snh4Tg6kf928AODelm4Og.exe (PID: 4592)
- 76NC6H3jxnj41tBn5ReACOJx.exe (PID: 5488)
- jhEkDR4LiF_xoKM1IRc2oolq.exe (PID: 5460)
- P9Ccbs2yHGCPGAbWuC9lVqzm.exe (PID: 4372)
- Bouderbela.exe (PID: 4824)
- Bouderbela.exe (PID: 5212)
- dhadvB8_Quoe9xPDdD0Q5CQD.exe (PID: 5320)
- lmrRudIW6hC8f4tZCEZFScX1.exe (PID: 4768)
- PH1uwTXFZdm6S9tdW3hhxu1f.exe (PID: 4320)
- AF8rGFxccUKYCIBH33I5lTUI.exe (PID: 3620)
- Vo8NvV9gwIArTRJTTs1VZ4WN.exe (PID: 2300)
- LPHjJF5n47iOwNngscTzzVj4.exe (PID: 5044)
- SdJonBkhYaN9iMb9EsPUKK1Q.exe (PID: 4500)
- whn8M8ZOzPDNHOMoUALHk6bF.tmp (PID: 4124)
- ZHuruwiwawu.exe (PID: 5888)
- powershell.exe (PID: 5240)
- JKe45826Dcj8CCzvf708WPoJ.exe (PID: 4416)
- ZHuruwiwawu.exe (PID: 4272)
- kLWXU7ly_PJqLRZqDfxkkISG.exe (PID: 5060)
- v00LWkGSaWY4x3B_h3ybD_hd.tmp (PID: 4756)
- 4F4A.tmp.exe (PID: 2608)
- RegAsm.exe (PID: 5984)
- PQyjub4sGtiOLkeJS8qnzwIH.exe (PID: 3940)
- powershell.exe (PID: 5120)
- bpQalRIkWhtCbaq_LU6Sjqxc.exe (PID: 4932)
- powershell.exe (PID: 3772)
- Nohululito.exe (PID: 4532)
- Bouderbela.exe (PID: 6116)
- Bouderbela.exe (PID: 6972)
- 4iGZ806jNW1O_2JG8hY1OHgP.exe (PID: 876)
- SHazhobajaezhae.exe (PID: 7596)
- iwKI0DEILCOs0EA7JE_ZYkrd.exe (PID: 8428)
- ULwnBgtUX9nTwZWP9MzQIxOh.exe (PID: 10152)
- Wizhagaevaeko.exe (PID: 4004)
- Caehyxicaqe.exe (PID: 6732)
- jg1_1faf.exe (PID: 7552)
- KdfEj_2TX4Gp0Nu_7E2BBvGy.exe (PID: 10048)
- Funywacaefa.exe (PID: 6924)
- rSHu1NJFyRf28EYfj0aYOh9q.exe (PID: 13412)
- AdvancedRun.exe (PID: 9964)
- powershell.exe (PID: 9700)
- AdvancedRun.exe (PID: 9072)
- installer.exe (PID: 5028)
- MAOJnCpxxB5VrEICaKPP1TBL.exe (PID: 13276)
- _dpOQFqSEbu1yisLxJYasR8i.exe (PID: 5420)
- _dpOQFqSEbu1yisLxJYasR8i.exe (PID: 12800)
- installer.exe (PID: 7904)
- meZPURcXNeNqpioAjuoodB1K.exe (PID: 8960)
- whw.exe (PID: 11240)
- random.exe (PID: 9792)
- e3dwefw.exe (PID: 10540)
- random.exe (PID: 3224)
- jTZNXyp8ZD8XCh_p6Bwy1ozw.tmp (PID: 8020)
- AW3v1Pv1azQc96UgcSRj2eON.tmp (PID: 12972)
- o0u1oYVCSrrEorCJhdBq8sAb.exe (PID: 12860)
- BdsF_xHbWSiaAiRHpSBd66U8.exe (PID: 8808)
- GcleanerEU.exe (PID: 5792)
- Install.exe (PID: 10484)
- powershell.exe (PID: 9236)
- random.exe (PID: 11892)
- random.exe (PID: 8752)
- WMIC.exe (PID: 9164)
- powershell.exe (PID: 12476)
- powershell.exe (PID: 3716)
- WMIC.exe (PID: 6852)
- AdvancedRun.exe (PID: 11784)
- WMIC.exe (PID: 10876)
- powershell.exe (PID: 3460)
- powershell.exe (PID: 5712)
- Bouderbela.exe (PID: 13180)
- AdvancedRun.exe (PID: 2260)
- WMIC.exe (PID: 4804)
- Bouderbela.exe (PID: 7820)
- Bk8YtZl4A3N6x8qYcOCqCeqX.exe (PID: 10876)
- sdfsd.exe (PID: 12528)
- Xugovocylae.exe (PID: 8108)
- Cidaecashehu.exe (PID: 2080)
- installer.exe (PID: 10108)
- askinstall42.exe (PID: 9000)
- powershell.EXE (PID: 7668)
- AppLaunch.exe (PID: 12012)
- random.exe (PID: 9968)
- powershell.exe (PID: 8676)
- WMIC.exe (PID: 1372)
- random.exe (PID: 13228)
- Install.exe (PID: 4668)
- powershell.exe (PID: 10616)
- WMIC.exe (PID: 12540)
- powershell.exe (PID: 11120)
- WMIC.exe (PID: 11264)
- powershell.exe (PID: 8224)
- WMIC.exe (PID: 5668)
- gcleaner.exe (PID: 14284)
- powershell.EXE (PID: 3168)
- RobCleanerInstll33132.exe (PID: 11196)
- LzmwAqmV.exe (PID: 13900)
- jli.exe (PID: 9852)
- jli.exe (PID: 13800)
- anytime2.exe (PID: 12468)
- Proxyupd.exe (PID: 12164)
- askinstall25.exe (PID: 13712)
- MyNotes Installation.exe (PID: 6928)
- anytime1.exe (PID: 13460)
- anytime3.exe (PID: 3444)
- anytime4.exe (PID: 3196)
- setupww1.exe (PID: 7332)
- logger.exe (PID: 2392)
- chenyuying.exe (PID: 12060)
- setup.exe (PID: 9800)
- Fixfile01.exe (PID: 14144)
- installer.exe (PID: 588)
- e72756b9-3e61-49d0-98c2-5ba1255e38e8.exe (PID: 11072)
- LzmwAqmV.exe (PID: 3532)
- installer.exe (PID: 11544)
- askinstall35.exe (PID: 9528)
- random.exe (PID: 11652)
- random.exe (PID: 13072)
- random.exe (PID: 8036)
- random.exe (PID: 7128)
- 161.tmp (PID: 11692)
- tapinstall.exe (PID: 12980)
- tapinstall.exe (PID: 8924)
- DrvInst.exe (PID: 10552)
- DrvInst.exe (PID: 11508)
- PyuJGVV.exe (PID: 4908)
- powershell.exe (PID: 11076)
- WMIC.exe (PID: 11320)
- powershell.exe (PID: 10212)
- WMIC.exe (PID: 6456)
- powershell.exe (PID: 12736)
- WMIC.exe (PID: 12004)
- powershell.exe (PID: 11136)
- WMIC.exe (PID: 7720)
- powershell.EXE (PID: 12708)
- installer.exe (PID: 10404)
- random.exe (PID: 7000)
- random.exe (PID: 12864)
- mask_svc.exe (PID: 11504)
- mask_svc.exe (PID: 8408)
- autosubplayer.exe (PID: 9820)
- mask_svc.exe (PID: 9984)
- autosubplayer.exe (PID: 11196)
- powershell.exe (PID: 10536)
- powershell.exe (PID: 11404)
- wscript.exe (PID: 7788)
- powershell.exe (PID: 8700)
- WMIC.exe (PID: 13060)
- hCisxSr.exe (PID: 6272)
- powershell.exe (PID: 7876)
- WMIC.exe (PID: 4088)
- powershell.exe (PID: 7960)
- WMIC.exe (PID: 9596)
- powershell.exe (PID: 9976)
- autosubplayer.exe (PID: 2416)
- WMIC.exe (PID: 10888)
- powershell.exe (PID: 10584)
- autosubplayer.exe (PID: 10872)
- installer.exe (PID: 8492)
- autosubplayer.exe (PID: 8992)
- powershell.exe (PID: 6232)
- powershell.exe (PID: 7288)
- autosubplayer.exe (PID: 13348)
- powershell.exe (PID: 5316)
- MaskVPNUpdate.exe (PID: 13728)
- Roads License Agreement.exe (PID: 5636)
- EasyCalc License Agreement.exe (PID: 8448)
Drops a file with a compile date too recent
- setup_installer.exe (PID: 2284)
- Fri05851d7f13.exe (PID: 2688)
- 8BWzAZaUY356vapXZ3r7riFu.exe (PID: 3112)
- Fri051e1e7444.exe (PID: 2572)
- 9ZztShvlpEcbYXbhysio6quv.tmp (PID: 3308)
- _qPnAfbohQzsKyRjIAPGwvSD.tmp (PID: 768)
- 2IDx4MjyyKCzrWVqZ7oRpu0L.exe (PID: 2568)
- HSMNMHTbjtwpdzFM1XzkF8cR.exe (PID: 2732)
- Fri05b5df5106928d62.exe (PID: 1472)
- Bouderbela.exe (PID: 5212)
- Bouderbela.exe (PID: 4824)
- Vo8NvV9gwIArTRJTTs1VZ4WN.exe (PID: 2300)
- v00LWkGSaWY4x3B_h3ybD_hd.tmp (PID: 4756)
- whn8M8ZOzPDNHOMoUALHk6bF.tmp (PID: 4124)
- Bouderbela.exe (PID: 6116)
- AF8rGFxccUKYCIBH33I5lTUI.exe (PID: 3620)
- Bouderbela.exe (PID: 6972)
- UG4OUxxiIM92aDb0mIZeo27n.exe (PID: 4064)
- KdfEj_2TX4Gp0Nu_7E2BBvGy.exe (PID: 10048)
- Funywacaefa.exe (PID: 6924)
- RegAsm.exe (PID: 448)
- e3dwefw.exe (PID: 10540)
- Wizhagaevaeko.exe (PID: 4004)
- jTZNXyp8ZD8XCh_p6Bwy1ozw.tmp (PID: 8020)
- AW3v1Pv1azQc96UgcSRj2eON.tmp (PID: 12972)
- SdJonBkhYaN9iMb9EsPUKK1Q.exe (PID: 4500)
- Bouderbela.exe (PID: 13180)
- Bouderbela.exe (PID: 7820)
- Nohululito.exe (PID: 4532)
- o0u1oYVCSrrEorCJhdBq8sAb.exe (PID: 12860)
- LzmwAqmV.exe (PID: 13900)
- setupww1.exe (PID: 7332)
- RobCleanerInstll33132.exe (PID: 11196)
- Xugovocylae.exe (PID: 8108)
- askinstall35.exe (PID: 9528)
- Cidaecashehu.exe (PID: 2080)
- SHazhobajaezhae.exe (PID: 7596)
- EasyCalc License Agreement.exe (PID: 8448)
- Roads License Agreement.exe (PID: 5636)
Checks supported languages
- 5bfb87691070668037df7a6bc1eac92bdb683ada3159b83c136146632835cb7f.exe (PID: 4000)
- setup_installer.exe (PID: 2284)
- cmd.exe (PID: 3740)
- setup_install.exe (PID: 2148)
- powershell.exe (PID: 3032)
- powershell.exe (PID: 2940)
- cmd.exe (PID: 2380)
- cmd.exe (PID: 3200)
- cmd.exe (PID: 1400)
- Fri05eeb2dae7b88520a.exe (PID: 3872)
- cmd.exe (PID: 2276)
- cmd.exe (PID: 480)
- cmd.exe (PID: 1292)
- cmd.exe (PID: 2072)
- cmd.exe (PID: 460)
- cmd.exe (PID: 2252)
- cmd.exe (PID: 3644)
- Fri05cc28ce70b.exe (PID: 2216)
- Fri05a277b9a3d2.exe (PID: 1832)
- cmd.exe (PID: 444)
- cmd.exe (PID: 2084)
- cmd.exe (PID: 2496)
- cmd.exe (PID: 3680)
- Fri05851d7f13.exe (PID: 2688)
- Fri055cc2a6e65.exe (PID: 2564)
- Fri05f84fa77402bf.exe (PID: 2428)
- Fri0541e16ce794d258f.exe (PID: 3808)
- Fri05eeb2dae7b88520a.tmp (PID: 3732)
- Fri051e1e7444.exe (PID: 2572)
- Fri05890d11cdb13f95e.exe (PID: 3704)
- Fri05b5df5106928d62.exe (PID: 1472)
- mshta.exe (PID: 1144)
- Fri0575b7d291a755f8.exe (PID: 2196)
- Fri05eeb2dae7b88520a.exe (PID: 1284)
- Fri05eeb2dae7b88520a.tmp (PID: 3656)
- Fri053f5694ea31c9a.exe (PID: 2492)
- cmd.exe (PID: 2980)
- mshta.exe (PID: 2104)
- EiV4.Exe (PID: 3856)
- cmd.exe (PID: 3160)
- mshta.exe (PID: 2744)
- cmd.exe (PID: 2512)
- cmd.exe (PID: 904)
- cmd.exe (PID: 3008)
- Fri05f84fa77402bf.exe (PID: 3116)
- Fri05a277b9a3d2.exe (PID: 2432)
- Fri053f5694ea31c9a.exe (PID: 3008)
- ag7CVdjSW97W3oRaIOR4Q3oQ.exe (PID: 2100)
- 8BWzAZaUY356vapXZ3r7riFu.exe (PID: 3112)
- vbJgmru47WuZkTuLzaHrweCH.exe (PID: 2888)
- cC95N5mvhiND9SaOJgZL_GrP.exe (PID: 3392)
- UXSvpgMlC9m9bBKQDE2JZTmm.exe (PID: 3664)
- HSMNMHTbjtwpdzFM1XzkF8cR.exe (PID: 2732)
- IHyVJ19EQJnOQjW7pnzDJQaJ.exe (PID: 3288)
- EjrVa4svUGraKSpsvKX0OSEG.exe (PID: 2980)
- jjMhwD8vifrmbi3EoANo0n87.exe (PID: 3816)
- 38WaMQDe4eShkMw3z66q_F6i.exe (PID: 2300)
- mj_FCKU_1Gvo6WnWeDAwFlk1.exe (PID: 1788)
- UG4OUxxiIM92aDb0mIZeo27n.exe (PID: 4064)
- powershell.exe (PID: 688)
- 2IDx4MjyyKCzrWVqZ7oRpu0L.exe (PID: 2568)
- _plqVbpyQ72EAcDdXQafZHDS.exe (PID: 2204)
- IHyVJ19EQJnOQjW7pnzDJQaJ.exe (PID: 3428)
- enJg7NoG88QfYbCNfm8CGIxY.exe (PID: 1832)
- powershell.exe (PID: 2616)
- CU3YoKS1pKwuxjVJDC_wI_9H.exe (PID: 2184)
- powershell.exe (PID: 2624)
- gFsr_46eH9u5HTXyOeXC9r1V.exe (PID: 3756)
- rIB1BkwDhthKpnxajOOpLgh3.exe (PID: 2060)
- _qPnAfbohQzsKyRjIAPGwvSD.exe (PID: 3956)
- 9ZztShvlpEcbYXbhysio6quv.exe (PID: 3288)
- 9ZztShvlpEcbYXbhysio6quv.tmp (PID: 3308)
- _qPnAfbohQzsKyRjIAPGwvSD.tmp (PID: 768)
- RegAsm.exe (PID: 448)
- 1A9E.tmp.exe (PID: 1028)
- cmd.exe (PID: 3120)
- m2TfQKJPCNVe5CpJOH7aekp7.exe (PID: 268)
- 76NC6H3jxnj41tBn5ReACOJx.exe (PID: 5488)
- jhEkDR4LiF_xoKM1IRc2oolq.exe (PID: 5460)
- ov1snh4Tg6kf928AODelm4Og.exe (PID: 4592)
- P9Ccbs2yHGCPGAbWuC9lVqzm.exe (PID: 4372)
- Bouderbela.exe (PID: 4824)
- Bouderbela.exe (PID: 5212)
- xPHmzo8wfnyjd5SrJma_zmw8.exe (PID: 6140)
- 378E.tmp.exe (PID: 4192)
- PH1uwTXFZdm6S9tdW3hhxu1f.exe (PID: 4320)
- cmd.exe (PID: 4568)
- lmrRudIW6hC8f4tZCEZFScX1.exe (PID: 4768)
- dhadvB8_Quoe9xPDdD0Q5CQD.exe (PID: 5320)
- AF8rGFxccUKYCIBH33I5lTUI.exe (PID: 3620)
- Vo8NvV9gwIArTRJTTs1VZ4WN.exe (PID: 2300)
- whn8M8ZOzPDNHOMoUALHk6bF.exe (PID: 5872)
- v00LWkGSaWY4x3B_h3ybD_hd.exe (PID: 5828)
- LPHjJF5n47iOwNngscTzzVj4.exe (PID: 5044)
- kLWXU7ly_PJqLRZqDfxkkISG.exe (PID: 5060)
- whn8M8ZOzPDNHOMoUALHk6bF.tmp (PID: 4124)
- bpQalRIkWhtCbaq_LU6Sjqxc.exe (PID: 4932)
- ZHuruwiwawu.exe (PID: 5888)
- v00LWkGSaWY4x3B_h3ybD_hd.tmp (PID: 4756)
- powershell.exe (PID: 5240)
- JKe45826Dcj8CCzvf708WPoJ.exe (PID: 4416)
- ZHuruwiwawu.exe (PID: 4272)
- svchost.exe (PID: 884)
- cmd.exe (PID: 5760)
- 7484765222.exe (PID: 6120)
- 4F4A.tmp.exe (PID: 2608)
- RegAsm.exe (PID: 5984)
- powershell.exe (PID: 3772)
- powershell.exe (PID: 5120)
- PQyjub4sGtiOLkeJS8qnzwIH.exe (PID: 3940)
- Nohululito.exe (PID: 4532)
- SdJonBkhYaN9iMb9EsPUKK1Q.exe (PID: 4500)
- 68FE.tmp.exe (PID: 6132)
- cmd.exe (PID: 5804)
- Bouderbela.exe (PID: 6116)
- 4iGZ806jNW1O_2JG8hY1OHgP.exe (PID: 876)
- Bouderbela.exe (PID: 6972)
- SHazhobajaezhae.exe (PID: 7596)
- cmd.exe (PID: 6992)
- cmd.exe (PID: 6520)
- 8587610666.exe (PID: 6752)
- iwKI0DEILCOs0EA7JE_ZYkrd.exe (PID: 8428)
- ULwnBgtUX9nTwZWP9MzQIxOh.exe (PID: 10152)
- inst2.exe (PID: 5880)
- jg1_1faf.exe (PID: 7552)
- Wizhagaevaeko.exe (PID: 4004)
- Caehyxicaqe.exe (PID: 6732)
- cmd.exe (PID: 6184)
- Funywacaefa.exe (PID: 6924)
- KdfEj_2TX4Gp0Nu_7E2BBvGy.exe (PID: 10048)
- cmd.exe (PID: 13676)
- rSHu1NJFyRf28EYfj0aYOh9q.exe (PID: 13412)
- xeyKz1D17PVy_DXmozuhOdcw.exe (PID: 8028)
- cmd.exe (PID: 10952)
- AdvancedRun.exe (PID: 9072)
- AdvancedRun.exe (PID: 9964)
- powershell.exe (PID: 9700)
- cmd.exe (PID: 3948)
- installer.exe (PID: 5028)
- MAOJnCpxxB5VrEICaKPP1TBL.exe (PID: 13276)
- _dpOQFqSEbu1yisLxJYasR8i.exe (PID: 5420)
- 2mfRD25PYb2qCl_Lq_jTnazX.exe (PID: 13660)
- meZPURcXNeNqpioAjuoodB1K.exe (PID: 8960)
- _dpOQFqSEbu1yisLxJYasR8i.exe (PID: 12800)
- cmd.exe (PID: 7264)
- installer.exe (PID: 7904)
- cmd.exe (PID: 7900)
- cmd.exe (PID: 7840)
- cmd.exe (PID: 4908)
- whw.exe (PID: 11240)
- random.exe (PID: 9792)
- random.exe (PID: 3224)
- e3dwefw.exe (PID: 10540)
- jTZNXyp8ZD8XCh_p6Bwy1ozw.exe (PID: 7712)
- AW3v1Pv1azQc96UgcSRj2eON.exe (PID: 12444)
- jTZNXyp8ZD8XCh_p6Bwy1ozw.tmp (PID: 8020)
- AW3v1Pv1azQc96UgcSRj2eON.tmp (PID: 12972)
- o0u1oYVCSrrEorCJhdBq8sAb.exe (PID: 12860)
- GcleanerEU.exe (PID: 7780)
- GcleanerEU.exe (PID: 5792)
- 0GT0VvHyDZrSeiPVmt2rOb3t.exe (PID: 10052)
- cmd.exe (PID: 8892)
- BdsF_xHbWSiaAiRHpSBd66U8.exe (PID: 8808)
- Install.exe (PID: 10980)
- Install.exe (PID: 10484)
- cmd.exe (PID: 13636)
- cmd.exe (PID: 8928)
- random.exe (PID: 11892)
- powershell.exe (PID: 9236)
- random.exe (PID: 8752)
- WMIC.exe (PID: 9164)
- powershell.exe (PID: 12476)
- WMIC.exe (PID: 10876)
- powershell.exe (PID: 3716)
- WMIC.exe (PID: 6852)
- AdvancedRun.exe (PID: 11784)
- AdvancedRun.exe (PID: 2260)
- powershell.exe (PID: 5712)
- powershell.exe (PID: 3460)
- Bouderbela.exe (PID: 13180)
- WMIC.exe (PID: 4804)
- Bouderbela.exe (PID: 7820)
- Bk8YtZl4A3N6x8qYcOCqCeqX.exe (PID: 10876)
- cmd.exe (PID: 2964)
- sdfsd.exe (PID: 12528)
- Xugovocylae.exe (PID: 8108)
- Cidaecashehu.exe (PID: 2080)
- installer.exe (PID: 10108)
- cmd.exe (PID: 4256)
- cmd.exe (PID: 2928)
- 0zXGRheNbfb6gDNyfNaowrnY.exe (PID: 9880)
- powershell.EXE (PID: 7668)
- Install.exe (PID: 14176)
- askinstall42.exe (PID: 9000)
- cmd.exe (PID: 8508)
- cmd.exe (PID: 8016)
- AppLaunch.exe (PID: 12012)
- random.exe (PID: 13228)
- Install.exe (PID: 4668)
- clipper.exe (PID: 8572)
- cmd.exe (PID: 13468)
- random.exe (PID: 9968)
- powershell.exe (PID: 8676)
- WMIC.exe (PID: 1372)
- cmd.exe (PID: 12060)
- powershell.exe (PID: 10616)
- WMIC.exe (PID: 12540)
- WMIC.exe (PID: 11264)
- powershell.exe (PID: 8224)
- WMIC.exe (PID: 5668)
- cmd.exe (PID: 6752)
- gcleaner.exe (PID: 12824)
- powershell.exe (PID: 11120)
- gcleaner.exe (PID: 14284)
- powershell.EXE (PID: 3168)
- RobCleanerInstll33132.exe (PID: 11196)
- Proxyupd.exe (PID: 12164)
- cmd.exe (PID: 2396)
- LzmwAqmV.exe (PID: 13900)
- inst.exe (PID: 13920)
- jli.exe (PID: 13800)
- Fixfile01.exe (PID: 14144)
- jli.exe (PID: 9852)
- anytime2.exe (PID: 12468)
- setup.exe (PID: 9800)
- MyNotes Installation.exe (PID: 6928)
- askinstall25.exe (PID: 13712)
- anytime1.exe (PID: 13460)
- cmd.exe (PID: 3640)
- logger.exe (PID: 2392)
- anytime4.exe (PID: 3196)
- anytime3.exe (PID: 3444)
- askinstall35.exe (PID: 9528)
- setupww1.exe (PID: 7332)
- chenyuying.exe (PID: 12060)
- chenyuying.exe (PID: 9236)
- cmd.exe (PID: 8864)
- installer.exe (PID: 588)
- e72756b9-3e61-49d0-98c2-5ba1255e38e8.exe (PID: 11072)
- cmd.exe (PID: 8552)
- cmd.exe (PID: 4100)
- installer.exe (PID: 11544)
- LzmwAqmV.exe (PID: 3532)
- random.exe (PID: 11652)
- cmd.exe (PID: 10576)
- cmd.exe (PID: 11724)
- random.exe (PID: 7128)
- random.exe (PID: 13072)
- random.exe (PID: 8036)
- 161.exe (PID: 6548)
- 161.tmp (PID: 11692)
- cmd.exe (PID: 7176)
- cmd.exe (PID: 10696)
- cmd.exe (PID: 10344)
- tapinstall.exe (PID: 8924)
- tapinstall.exe (PID: 12980)
- cmd.exe (PID: 8788)
- DrvInst.exe (PID: 10552)
- DrvInst.exe (PID: 11508)
- PyuJGVV.exe (PID: 4908)
- cmd.exe (PID: 5224)
- powershell.exe (PID: 11076)
- WMIC.exe (PID: 11320)
- powershell.exe (PID: 10212)
- WMIC.exe (PID: 6456)
- powershell.exe (PID: 12736)
- powershell.exe (PID: 11136)
- WMIC.exe (PID: 7720)
- WMIC.exe (PID: 12004)
- powershell.EXE (PID: 12708)
- cmd.exe (PID: 7368)
- installer.exe (PID: 10404)
- cmd.exe (PID: 2192)
- random.exe (PID: 7000)
- random.exe (PID: 12864)
- mask_svc.exe (PID: 11504)
- mask_svc.exe (PID: 8408)
- mask_svc.exe (PID: 9984)
- cmd.exe (PID: 5540)
- autosubplayer.exe (PID: 9820)
- cmd.exe (PID: 13684)
- toolspab3.exe (PID: 9508)
- cmd.exe (PID: 8276)
- autosubplayer.exe (PID: 11196)
- ns8315.tmp (PID: 9328)
- powershell.exe (PID: 10536)
- toolspab3.exe (PID: 4176)
- ns8BB1.tmp (PID: 2980)
- lighteningplayer-cache-gen.exe (PID: 7028)
- ns94D9.tmp (PID: 7188)
- lighteningplayer-cache-gen.exe (PID: 11624)
- ns8E60.tmp (PID: 9732)
- powershell.exe (PID: 11404)
- cmd.exe (PID: 6644)
- cmd.exe (PID: 7064)
- wscript.exe (PID: 7788)
- cmd.exe (PID: 13160)
- cmd.exe (PID: 10276)
- powershell.exe (PID: 8700)
- WMIC.exe (PID: 13060)
- hCisxSr.exe (PID: 6272)
- powershell.exe (PID: 7876)
- WMIC.exe (PID: 4088)
- WMIC.exe (PID: 9596)
- powershell.exe (PID: 9976)
- WMIC.exe (PID: 10888)
- powershell.exe (PID: 7960)
- autosubplayer.exe (PID: 2416)
- cmd.exe (PID: 4504)
- nsB57F.tmp (PID: 13808)
- cmd.exe (PID: 10264)
- cmd.exe (PID: 7784)
- nsBC76.tmp (PID: 13736)
- lighteningplayer-cache-gen.exe (PID: 2004)
- cmd.exe (PID: 7928)
- powershell.exe (PID: 10584)
- autosubplayer.exe (PID: 10872)
- cmd.exe (PID: 8044)
- installer.exe (PID: 8492)
- autosubplayer.exe (PID: 8992)
- cmd.exe (PID: 7984)
- nsCCEF.tmp (PID: 5284)
- nsCCFF.tmp (PID: 6956)
- powershell.exe (PID: 6232)
- powershell.exe (PID: 7288)
- nsD491.tmp (PID: 7776)
- nsD4B1.tmp (PID: 13408)
- lighteningplayer-cache-gen.exe (PID: 11744)
- lighteningplayer-cache-gen.exe (PID: 5792)
- cmd.exe (PID: 12820)
- cmd.exe (PID: 13668)
- nsBEC.tmp (PID: 2596)
- powershell.exe (PID: 5316)
- cmd.exe (PID: 11796)
- autosubplayer.exe (PID: 13348)
- MaskVPNUpdate.exe (PID: 13728)
- Roads License Agreement.exe (PID: 5636)
- lighteningplayer-cache-gen.exe (PID: 5748)
- ns1217.tmp (PID: 6176)
- EasyCalc License Agreement.exe (PID: 8448)
Executable content was dropped or overwritten
- 5bfb87691070668037df7a6bc1eac92bdb683ada3159b83c136146632835cb7f.exe (PID: 4000)
- setup_installer.exe (PID: 2284)
- Fri05eeb2dae7b88520a.exe (PID: 3872)
- Fri05eeb2dae7b88520a.tmp (PID: 3732)
- Fri05eeb2dae7b88520a.exe (PID: 1284)
- Fri05eeb2dae7b88520a.tmp (PID: 3656)
- cmd.exe (PID: 2980)
- cmd.exe (PID: 2512)
- Fri051e1e7444.exe (PID: 2572)
- ag7CVdjSW97W3oRaIOR4Q3oQ.exe (PID: 2100)
- vbJgmru47WuZkTuLzaHrweCH.exe (PID: 2888)
- 8BWzAZaUY356vapXZ3r7riFu.exe (PID: 3112)
- cC95N5mvhiND9SaOJgZL_GrP.exe (PID: 3392)
- UXSvpgMlC9m9bBKQDE2JZTmm.exe (PID: 3664)
- Fri05851d7f13.exe (PID: 2688)
- Fri05b5df5106928d62.exe (PID: 1472)
- _qPnAfbohQzsKyRjIAPGwvSD.exe (PID: 3956)
- 9ZztShvlpEcbYXbhysio6quv.exe (PID: 3288)
- _qPnAfbohQzsKyRjIAPGwvSD.tmp (PID: 768)
- 9ZztShvlpEcbYXbhysio6quv.tmp (PID: 3308)
- 2IDx4MjyyKCzrWVqZ7oRpu0L.exe (PID: 2568)
- jhEkDR4LiF_xoKM1IRc2oolq.exe (PID: 5460)
- 76NC6H3jxnj41tBn5ReACOJx.exe (PID: 5488)
- P9Ccbs2yHGCPGAbWuC9lVqzm.exe (PID: 4372)
- enJg7NoG88QfYbCNfm8CGIxY.exe (PID: 1832)
- EjrVa4svUGraKSpsvKX0OSEG.exe (PID: 2980)
- HSMNMHTbjtwpdzFM1XzkF8cR.exe (PID: 2732)
- whn8M8ZOzPDNHOMoUALHk6bF.exe (PID: 5872)
- whn8M8ZOzPDNHOMoUALHk6bF.tmp (PID: 4124)
- Bouderbela.exe (PID: 5212)
- Bouderbela.exe (PID: 4824)
- v00LWkGSaWY4x3B_h3ybD_hd.exe (PID: 5828)
- 378E.tmp.exe (PID: 4192)
- Vo8NvV9gwIArTRJTTs1VZ4WN.exe (PID: 2300)
- v00LWkGSaWY4x3B_h3ybD_hd.tmp (PID: 4756)
- PH1uwTXFZdm6S9tdW3hhxu1f.exe (PID: 4320)
- 68FE.tmp.exe (PID: 6132)
- Bouderbela.exe (PID: 6116)
- AF8rGFxccUKYCIBH33I5lTUI.exe (PID: 3620)
- bpQalRIkWhtCbaq_LU6Sjqxc.exe (PID: 4932)
- Bouderbela.exe (PID: 6972)
- RegAsm.exe (PID: 448)
- Nohululito.exe (PID: 4532)
- UG4OUxxiIM92aDb0mIZeo27n.exe (PID: 4064)
- KdfEj_2TX4Gp0Nu_7E2BBvGy.exe (PID: 10048)
- Wizhagaevaeko.exe (PID: 4004)
- MAOJnCpxxB5VrEICaKPP1TBL.exe (PID: 13276)
- Funywacaefa.exe (PID: 6924)
- installer.exe (PID: 5028)
- msiexec.exe (PID: 9636)
- e3dwefw.exe (PID: 10540)
- jTZNXyp8ZD8XCh_p6Bwy1ozw.exe (PID: 7712)
- AW3v1Pv1azQc96UgcSRj2eON.exe (PID: 12444)
- AW3v1Pv1azQc96UgcSRj2eON.tmp (PID: 12972)
- 0GT0VvHyDZrSeiPVmt2rOb3t.exe (PID: 10052)
- Install.exe (PID: 10980)
- SdJonBkhYaN9iMb9EsPUKK1Q.exe (PID: 4500)
- jTZNXyp8ZD8XCh_p6Bwy1ozw.tmp (PID: 8020)
- Bouderbela.exe (PID: 13180)
- Bouderbela.exe (PID: 7820)
- 0zXGRheNbfb6gDNyfNaowrnY.exe (PID: 9880)
- Install.exe (PID: 14176)
- o0u1oYVCSrrEorCJhdBq8sAb.exe (PID: 12860)
- MyNotes Installation.exe (PID: 6928)
- LzmwAqmV.exe (PID: 13900)
- setupww1.exe (PID: 7332)
- chenyuying.exe (PID: 12060)
- Install.exe (PID: 10484)
- RobCleanerInstll33132.exe (PID: 11196)
- Cidaecashehu.exe (PID: 2080)
- Xugovocylae.exe (PID: 8108)
- askinstall35.exe (PID: 9528)
- Fixfile01.exe (PID: 14144)
- Install.exe (PID: 4668)
- 161.exe (PID: 6548)
- SHazhobajaezhae.exe (PID: 7596)
- 161.tmp (PID: 11692)
- tapinstall.exe (PID: 12980)
- DrvInst.exe (PID: 10552)
- DrvInst.exe (PID: 11508)
- autosubplayer.exe (PID: 9820)
- autosubplayer.exe (PID: 11196)
- PyuJGVV.exe (PID: 4908)
- hCisxSr.exe (PID: 6272)
- autosubplayer.exe (PID: 2416)
- autosubplayer.exe (PID: 8992)
- autosubplayer.exe (PID: 10872)
- autosubplayer.exe (PID: 13348)
- Roads License Agreement.exe (PID: 5636)
- EasyCalc License Agreement.exe (PID: 8448)
Drops a file that was compiled in debug mode
- setup_installer.exe (PID: 2284)
- Fri05eeb2dae7b88520a.tmp (PID: 3732)
- Fri05eeb2dae7b88520a.tmp (PID: 3656)
- cmd.exe (PID: 2980)
- Fri051e1e7444.exe (PID: 2572)
- _qPnAfbohQzsKyRjIAPGwvSD.tmp (PID: 768)
- 9ZztShvlpEcbYXbhysio6quv.tmp (PID: 3308)
- enJg7NoG88QfYbCNfm8CGIxY.exe (PID: 1832)
- Fri05b5df5106928d62.exe (PID: 1472)
- 2IDx4MjyyKCzrWVqZ7oRpu0L.exe (PID: 2568)
- whn8M8ZOzPDNHOMoUALHk6bF.tmp (PID: 4124)
- Bouderbela.exe (PID: 4824)
- Bouderbela.exe (PID: 5212)
- 378E.tmp.exe (PID: 4192)
- v00LWkGSaWY4x3B_h3ybD_hd.tmp (PID: 4756)
- bpQalRIkWhtCbaq_LU6Sjqxc.exe (PID: 4932)
- Vo8NvV9gwIArTRJTTs1VZ4WN.exe (PID: 2300)
- 68FE.tmp.exe (PID: 6132)
- Bouderbela.exe (PID: 6116)
- Bouderbela.exe (PID: 6972)
- Nohululito.exe (PID: 4532)
- UG4OUxxiIM92aDb0mIZeo27n.exe (PID: 4064)
- Wizhagaevaeko.exe (PID: 4004)
- KdfEj_2TX4Gp0Nu_7E2BBvGy.exe (PID: 10048)
- Funywacaefa.exe (PID: 6924)
- installer.exe (PID: 5028)
- msiexec.exe (PID: 9636)
- AW3v1Pv1azQc96UgcSRj2eON.tmp (PID: 12972)
- SdJonBkhYaN9iMb9EsPUKK1Q.exe (PID: 4500)
- jTZNXyp8ZD8XCh_p6Bwy1ozw.tmp (PID: 8020)
- Bouderbela.exe (PID: 13180)
- Bouderbela.exe (PID: 7820)
- LzmwAqmV.exe (PID: 13900)
- setupww1.exe (PID: 7332)
- Cidaecashehu.exe (PID: 2080)
- Xugovocylae.exe (PID: 8108)
- askinstall35.exe (PID: 9528)
- Fixfile01.exe (PID: 14144)
- LzmwAqmV.exe (PID: 3532)
- 161.tmp (PID: 11692)
- DrvInst.exe (PID: 10552)
- tapinstall.exe (PID: 12980)
- DrvInst.exe (PID: 11508)
- SHazhobajaezhae.exe (PID: 7596)
- Roads License Agreement.exe (PID: 5636)
- EasyCalc License Agreement.exe (PID: 8448)
Starts CMD.EXE for commands execution
- setup_install.exe (PID: 2148)
- mshta.exe (PID: 1144)
- mshta.exe (PID: 2104)
- cmd.exe (PID: 2512)
- mshta.exe (PID: 2744)
- rIB1BkwDhthKpnxajOOpLgh3.exe (PID: 2060)
- 2IDx4MjyyKCzrWVqZ7oRpu0L.exe (PID: 2568)
- EjrVa4svUGraKSpsvKX0OSEG.exe (PID: 2980)
- Vo8NvV9gwIArTRJTTs1VZ4WN.exe (PID: 2300)
- 4iGZ806jNW1O_2JG8hY1OHgP.exe (PID: 876)
- PH1uwTXFZdm6S9tdW3hhxu1f.exe (PID: 4320)
- enJg7NoG88QfYbCNfm8CGIxY.exe (PID: 1832)
- bpQalRIkWhtCbaq_LU6Sjqxc.exe (PID: 4932)
- Nohululito.exe (PID: 4532)
- Wizhagaevaeko.exe (PID: 4004)
- Funywacaefa.exe (PID: 6924)
- meZPURcXNeNqpioAjuoodB1K.exe (PID: 8960)
- Install.exe (PID: 10484)
- forfiles.exe (PID: 8684)
- forfiles.exe (PID: 7552)
- forfiles.exe (PID: 14076)
- forfiles.exe (PID: 8832)
- forfiles.exe (PID: 13596)
- forfiles.exe (PID: 9836)
- GcleanerEU.exe (PID: 5792)
- forfiles.exe (PID: 9440)
- Install.exe (PID: 4668)
- forfiles.exe (PID: 7004)
- forfiles.exe (PID: 10228)
- forfiles.exe (PID: 11400)
- forfiles.exe (PID: 10752)
- forfiles.exe (PID: 13688)
- gcleaner.exe (PID: 14284)
- setup.exe (PID: 9800)
- Cidaecashehu.exe (PID: 2080)
- Xugovocylae.exe (PID: 8108)
- Fixfile01.exe (PID: 14144)
- SHazhobajaezhae.exe (PID: 7596)
- 161.tmp (PID: 11692)
- PyuJGVV.exe (PID: 4908)
- forfiles.exe (PID: 10104)
- forfiles.exe (PID: 9844)
- forfiles.exe (PID: 12572)
- forfiles.exe (PID: 13840)
- forfiles.exe (PID: 2556)
- hCisxSr.exe (PID: 6272)
- forfiles.exe (PID: 3892)
- forfiles.exe (PID: 5624)
- forfiles.exe (PID: 7180)
Drops a file with too old compile date
- setup_installer.exe (PID: 2284)
- Fri05eeb2dae7b88520a.exe (PID: 3872)
- Fri05eeb2dae7b88520a.tmp (PID: 3732)
- Fri05eeb2dae7b88520a.exe (PID: 1284)
- Fri05eeb2dae7b88520a.tmp (PID: 3656)
- cmd.exe (PID: 2512)
- Fri051e1e7444.exe (PID: 2572)
- _qPnAfbohQzsKyRjIAPGwvSD.exe (PID: 3956)
- 9ZztShvlpEcbYXbhysio6quv.exe (PID: 3288)
- _qPnAfbohQzsKyRjIAPGwvSD.tmp (PID: 768)
- 9ZztShvlpEcbYXbhysio6quv.tmp (PID: 3308)
- Fri05b5df5106928d62.exe (PID: 1472)
- whn8M8ZOzPDNHOMoUALHk6bF.exe (PID: 5872)
- whn8M8ZOzPDNHOMoUALHk6bF.tmp (PID: 4124)
- v00LWkGSaWY4x3B_h3ybD_hd.exe (PID: 5828)
- v00LWkGSaWY4x3B_h3ybD_hd.tmp (PID: 4756)
- RegAsm.exe (PID: 448)
- KdfEj_2TX4Gp0Nu_7E2BBvGy.exe (PID: 10048)
- jTZNXyp8ZD8XCh_p6Bwy1ozw.exe (PID: 7712)
- AW3v1Pv1azQc96UgcSRj2eON.exe (PID: 12444)
- AW3v1Pv1azQc96UgcSRj2eON.tmp (PID: 12972)
- Funywacaefa.exe (PID: 6924)
- setupww1.exe (PID: 7332)
- chenyuying.exe (PID: 12060)
- 161.tmp (PID: 11692)
- autosubplayer.exe (PID: 9820)
Starts MSHTA.EXE for opening HTA or HTMLS files
- Fri05cc28ce70b.exe (PID: 2216)
- EiV4.Exe (PID: 3856)
Application launched itself
- Fri05a277b9a3d2.exe (PID: 1832)
- Fri053f5694ea31c9a.exe (PID: 2492)
- Fri05f84fa77402bf.exe (PID: 2428)
- cmd.exe (PID: 2512)
- IHyVJ19EQJnOQjW7pnzDJQaJ.exe (PID: 3288)
- msiexec.exe (PID: 9636)
- _dpOQFqSEbu1yisLxJYasR8i.exe (PID: 5420)
- random.exe (PID: 9792)
- GcleanerEU.exe (PID: 7780)
- random.exe (PID: 11892)
- gcleaner.exe (PID: 12824)
- jli.exe (PID: 13800)
- random.exe (PID: 7128)
- random.exe (PID: 11652)
- random.exe (PID: 9968)
- random.exe (PID: 7000)
- toolspab3.exe (PID: 9508)
Reads Environment values
- Fri05890d11cdb13f95e.exe (PID: 3704)
- Fri0575b7d291a755f8.exe (PID: 2196)
- RegAsm.exe (PID: 448)
- 38WaMQDe4eShkMw3z66q_F6i.exe (PID: 2300)
- 1A9E.tmp.exe (PID: 1028)
- jjMhwD8vifrmbi3EoANo0n87.exe (PID: 3816)
- Bouderbela.exe (PID: 5212)
- Bouderbela.exe (PID: 4824)
- ZHuruwiwawu.exe (PID: 5888)
- ZHuruwiwawu.exe (PID: 4272)
- 4F4A.tmp.exe (PID: 2608)
- lmrRudIW6hC8f4tZCEZFScX1.exe (PID: 4768)
- RegAsm.exe (PID: 5984)
- Nohululito.exe (PID: 4532)
- Bouderbela.exe (PID: 6972)
- Bouderbela.exe (PID: 6116)
- SHazhobajaezhae.exe (PID: 7596)
- enJg7NoG88QfYbCNfm8CGIxY.exe (PID: 1832)
- Wizhagaevaeko.exe (PID: 4004)
- Caehyxicaqe.exe (PID: 6732)
- bpQalRIkWhtCbaq_LU6Sjqxc.exe (PID: 4932)
- Funywacaefa.exe (PID: 6924)
- UG4OUxxiIM92aDb0mIZeo27n.exe (PID: 4064)
- installer.exe (PID: 5028)
- MsiExec.exe (PID: 2440)
- MsiExec.exe (PID: 10032)
- o0u1oYVCSrrEorCJhdBq8sAb.exe (PID: 12860)
- whw.exe (PID: 11240)
- Bouderbela.exe (PID: 13180)
- SdJonBkhYaN9iMb9EsPUKK1Q.exe (PID: 4500)
- Bouderbela.exe (PID: 7820)
- Xugovocylae.exe (PID: 8108)
- Cidaecashehu.exe (PID: 2080)
- RobCleanerInstll33132.exe (PID: 11196)
- anytime2.exe (PID: 12468)
- anytime1.exe (PID: 13460)
- anytime3.exe (PID: 3444)
- anytime4.exe (PID: 3196)
- logger.exe (PID: 2392)
- Proxyupd.exe (PID: 12164)
- LzmwAqmV.exe (PID: 3532)
- e72756b9-3e61-49d0-98c2-5ba1255e38e8.exe (PID: 11072)
- Fixfile01.exe (PID: 14144)
- vssvc.exe (PID: 7072)
- DrvInst.exe (PID: 11508)
- 161.tmp (PID: 11692)
Reads Windows owner or organization settings
- Fri05eeb2dae7b88520a.tmp (PID: 3732)
- Fri05eeb2dae7b88520a.tmp (PID: 3656)
- 9ZztShvlpEcbYXbhysio6quv.tmp (PID: 3308)
- _qPnAfbohQzsKyRjIAPGwvSD.tmp (PID: 768)
- whn8M8ZOzPDNHOMoUALHk6bF.tmp (PID: 4124)
- v00LWkGSaWY4x3B_h3ybD_hd.tmp (PID: 4756)
- installer.exe (PID: 5028)
- msiexec.exe (PID: 9636)
- jTZNXyp8ZD8XCh_p6Bwy1ozw.tmp (PID: 8020)
- AW3v1Pv1azQc96UgcSRj2eON.tmp (PID: 12972)
- 161.tmp (PID: 11692)
Reads the Windows organization settings
- Fri05eeb2dae7b88520a.tmp (PID: 3732)
- Fri05eeb2dae7b88520a.tmp (PID: 3656)
- _qPnAfbohQzsKyRjIAPGwvSD.tmp (PID: 768)
- 9ZztShvlpEcbYXbhysio6quv.tmp (PID: 3308)
- whn8M8ZOzPDNHOMoUALHk6bF.tmp (PID: 4124)
- v00LWkGSaWY4x3B_h3ybD_hd.tmp (PID: 4756)
- installer.exe (PID: 5028)
- msiexec.exe (PID: 9636)
- jTZNXyp8ZD8XCh_p6Bwy1ozw.tmp (PID: 8020)
- AW3v1Pv1azQc96UgcSRj2eON.tmp (PID: 12972)
- 161.tmp (PID: 11692)
Reads Microsoft Outlook installation path
- mshta.exe (PID: 1144)
- mshta.exe (PID: 2104)
- mshta.exe (PID: 2744)
- iexplore.exe (PID: 5308)
- iexplore.exe (PID: 2348)
- iexplore.exe (PID: 6260)
Adds / modifies Windows certificates
- Fri05851d7f13.exe (PID: 2688)
- Fri051e1e7444.exe (PID: 2572)
- HSMNMHTbjtwpdzFM1XzkF8cR.exe (PID: 2732)
- RegAsm.exe (PID: 448)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2980)
- cmd.exe (PID: 3120)
- cmd.exe (PID: 6992)
- cmd.exe (PID: 6184)
- cmd.exe (PID: 13676)
- MsiExec.exe (PID: 10032)
- cmd.exe (PID: 7840)
- cmd.exe (PID: 2964)
- cmd.exe (PID: 4256)
- cmd.exe (PID: 2928)
- cmd.exe (PID: 2396)
- cmd.exe (PID: 8864)
- cmd.exe (PID: 7176)
Executed via WMI
- rundll32.exe (PID: 3180)
- rundll32.exe (PID: 9884)
- rundll32.exe (PID: 6464)
- rundll32.exe (PID: 3092)
- rundll32.exe (PID: 13316)
- rundll32.exe (PID: 11536)
- rundll32.exe (PID: 9180)
- rundll32.exe (PID: 10696)
- rundll32.exe (PID: 10764)
Checks for external IP
- Fri051e1e7444.exe (PID: 2572)
- Fri05b5df5106928d62.exe (PID: 1472)
- HSMNMHTbjtwpdzFM1XzkF8cR.exe (PID: 2732)
- AF8rGFxccUKYCIBH33I5lTUI.exe (PID: 3620)
- KdfEj_2TX4Gp0Nu_7E2BBvGy.exe (PID: 10048)
Executes PowerShell scripts
- UG4OUxxiIM92aDb0mIZeo27n.exe (PID: 4064)
- SdJonBkhYaN9iMb9EsPUKK1Q.exe (PID: 4500)
- AdvancedRun.exe (PID: 9964)
- cmd.exe (PID: 3228)
- cmd.exe (PID: 5032)
- cmd.exe (PID: 7956)
- cmd.exe (PID: 5128)
- AdvancedRun.exe (PID: 2260)
- cmd.exe (PID: 6416)
- cmd.exe (PID: 13792)
- cmd.exe (PID: 10188)
- cmd.exe (PID: 6112)
- cmd.exe (PID: 8888)
- cmd.exe (PID: 5212)
- cmd.exe (PID: 14284)
- cmd.exe (PID: 9008)
- ns8315.tmp (PID: 9328)
- ns8E60.tmp (PID: 9732)
- cmd.exe (PID: 7872)
- cmd.exe (PID: 2396)
- cmd.exe (PID: 9784)
- cmd.exe (PID: 12624)
- nsB57F.tmp (PID: 13808)
- nsCCFF.tmp (PID: 6956)
- nsCCEF.tmp (PID: 5284)
- nsBEC.tmp (PID: 2596)
Uses IPCONFIG.EXE to discover IP address
- powershell.exe (PID: 688)
- powershell.exe (PID: 2616)
- powershell.exe (PID: 5240)
- powershell.exe (PID: 5120)
Creates files in the user directory
- 2IDx4MjyyKCzrWVqZ7oRpu0L.exe (PID: 2568)
- 378E.tmp.exe (PID: 4192)
- Vo8NvV9gwIArTRJTTs1VZ4WN.exe (PID: 2300)
- EjrVa4svUGraKSpsvKX0OSEG.exe (PID: 2980)
- 68FE.tmp.exe (PID: 6132)
- UG4OUxxiIM92aDb0mIZeo27n.exe (PID: 4064)
- installer.exe (PID: 5028)
- RegAsm.exe (PID: 448)
- e3dwefw.exe (PID: 10540)
- powershell.EXE (PID: 7668)
- powershell.EXE (PID: 3168)
- powershell.EXE (PID: 12708)
- autosubplayer.exe (PID: 9820)
- hCisxSr.exe (PID: 6272)
- Roads License Agreement.exe (PID: 5636)
- EasyCalc License Agreement.exe (PID: 8448)
Reads CPU info
- RegAsm.exe (PID: 448)
- RegAsm.exe (PID: 5984)
- enJg7NoG88QfYbCNfm8CGIxY.exe (PID: 1832)
- bpQalRIkWhtCbaq_LU6Sjqxc.exe (PID: 4932)
- Fixfile01.exe (PID: 14144)
Dropped object may contain URLs of mainers pools
- 2IDx4MjyyKCzrWVqZ7oRpu0L.exe (PID: 2568)
- Vo8NvV9gwIArTRJTTs1VZ4WN.exe (PID: 2300)
Reads the cookies of Google Chrome
- jjMhwD8vifrmbi3EoANo0n87.exe (PID: 3816)
- 38WaMQDe4eShkMw3z66q_F6i.exe (PID: 2300)
- RegAsm.exe (PID: 448)
- lmrRudIW6hC8f4tZCEZFScX1.exe (PID: 4768)
- RegAsm.exe (PID: 5984)
- whw.exe (PID: 11240)
- askinstall35.exe (PID: 9528)
- Proxyupd.exe (PID: 12164)
Reads the cookies of Mozilla Firefox
- jjMhwD8vifrmbi3EoANo0n87.exe (PID: 3816)
- 38WaMQDe4eShkMw3z66q_F6i.exe (PID: 2300)
- RegAsm.exe (PID: 448)
- lmrRudIW6hC8f4tZCEZFScX1.exe (PID: 4768)
- RegAsm.exe (PID: 5984)
- jg1_1faf.exe (PID: 7552)
- whw.exe (PID: 11240)
- Proxyupd.exe (PID: 12164)
- askinstall35.exe (PID: 9528)
Reads default file associations for system extensions
- m2TfQKJPCNVe5CpJOH7aekp7.exe (PID: 268)
Searches for installed software
- jjMhwD8vifrmbi3EoANo0n87.exe (PID: 3816)
- 38WaMQDe4eShkMw3z66q_F6i.exe (PID: 2300)
- RegAsm.exe (PID: 448)
- lmrRudIW6hC8f4tZCEZFScX1.exe (PID: 4768)
- enJg7NoG88QfYbCNfm8CGIxY.exe (PID: 1832)
- bpQalRIkWhtCbaq_LU6Sjqxc.exe (PID: 4932)
- RegAsm.exe (PID: 5984)
- whw.exe (PID: 11240)
- Proxyupd.exe (PID: 12164)
- e72756b9-3e61-49d0-98c2-5ba1255e38e8.exe (PID: 11072)
- Fixfile01.exe (PID: 14144)
Uses RUNDLL32.EXE to load library
- control.exe (PID: 6036)
Creates files in the program directory
- enJg7NoG88QfYbCNfm8CGIxY.exe (PID: 1832)
- HSMNMHTbjtwpdzFM1XzkF8cR.exe (PID: 2732)
- iwKI0DEILCOs0EA7JE_ZYkrd.exe (PID: 8428)
- AF8rGFxccUKYCIBH33I5lTUI.exe (PID: 3620)
- bpQalRIkWhtCbaq_LU6Sjqxc.exe (PID: 4932)
- jg1_1faf.exe (PID: 7552)
- msiexec.exe (PID: 9636)
- setupww1.exe (PID: 7332)
- Fixfile01.exe (PID: 14144)
- svchost.exe (PID: 884)
- askinstall35.exe (PID: 9528)
- lighteningplayer-cache-gen.exe (PID: 7028)
- lighteningplayer-cache-gen.exe (PID: 11624)
- autosubplayer.exe (PID: 9820)
- hCisxSr.exe (PID: 6272)
- lighteningplayer-cache-gen.exe (PID: 2004)
- lighteningplayer-cache-gen.exe (PID: 5792)
- lighteningplayer-cache-gen.exe (PID: 11744)
- lighteningplayer-cache-gen.exe (PID: 5748)
Creates a directory in Program Files
- HSMNMHTbjtwpdzFM1XzkF8cR.exe (PID: 2732)
- Bouderbela.exe (PID: 4824)
- Bouderbela.exe (PID: 5212)
- iwKI0DEILCOs0EA7JE_ZYkrd.exe (PID: 8428)
- Bouderbela.exe (PID: 6972)
- msiexec.exe (PID: 9636)
- 161.tmp (PID: 11692)
- autosubplayer.exe (PID: 9820)
- hCisxSr.exe (PID: 6272)
Starts CMD.EXE for self-deleting
- 2IDx4MjyyKCzrWVqZ7oRpu0L.exe (PID: 2568)
- Vo8NvV9gwIArTRJTTs1VZ4WN.exe (PID: 2300)
- enJg7NoG88QfYbCNfm8CGIxY.exe (PID: 1832)
- bpQalRIkWhtCbaq_LU6Sjqxc.exe (PID: 4932)
- Fixfile01.exe (PID: 14144)
Creates files in the Windows directory
- svchost.exe (PID: 884)
- powershell.exe (PID: 9700)
- powershell.exe (PID: 5712)
- schtasks.exe (PID: 9112)
- DrvInst.exe (PID: 10552)
- DrvInst.exe (PID: 11508)
- powershell.exe (PID: 11076)
- powershell.exe (PID: 10212)
- powershell.exe (PID: 12736)
- powershell.exe (PID: 11136)
- cmd.exe (PID: 7064)
- PyuJGVV.exe (PID: 4908)
- schtasks.exe (PID: 1460)
- powershell.exe (PID: 8700)
- powershell.exe (PID: 7876)
- powershell.exe (PID: 9976)
- powershell.exe (PID: 7960)
- schtasks.exe (PID: 5524)
- hCisxSr.exe (PID: 6272)
- schtasks.exe (PID: 3188)
Reads mouse settings
- 7484765222.exe (PID: 6120)
- 8587610666.exe (PID: 6752)
Starts Internet Explorer
- ZHuruwiwawu.exe (PID: 4272)
- ZHuruwiwawu.exe (PID: 5888)
- Caehyxicaqe.exe (PID: 6732)
Creates a software uninstall entry
- iwKI0DEILCOs0EA7JE_ZYkrd.exe (PID: 8428)
- msiexec.exe (PID: 9636)
- setupww1.exe (PID: 7332)
- autosubplayer.exe (PID: 9820)
- autosubplayer.exe (PID: 11196)
- autosubplayer.exe (PID: 2416)
- autosubplayer.exe (PID: 8992)
- autosubplayer.exe (PID: 10872)
- hCisxSr.exe (PID: 6272)
- autosubplayer.exe (PID: 13348)
Removes files from Windows directory
- powershell.exe (PID: 9700)
- powershell.exe (PID: 5712)
- svchost.exe (PID: 884)
- DrvInst.exe (PID: 10552)
- powershell.exe (PID: 11076)
- DrvInst.exe (PID: 11508)
- powershell.exe (PID: 10212)
- powershell.exe (PID: 11136)
- powershell.exe (PID: 12736)
- PyuJGVV.exe (PID: 4908)
- powershell.exe (PID: 8700)
- powershell.exe (PID: 7876)
- powershell.exe (PID: 9976)
- powershell.exe (PID: 7960)
Starts itself from another location
- UG4OUxxiIM92aDb0mIZeo27n.exe (PID: 4064)
- 0GT0VvHyDZrSeiPVmt2rOb3t.exe (PID: 10052)
- SdJonBkhYaN9iMb9EsPUKK1Q.exe (PID: 4500)
- 0zXGRheNbfb6gDNyfNaowrnY.exe (PID: 9880)
- chenyuying.exe (PID: 12060)
Executed as Windows Service
- msiexec.exe (PID: 9636)
- vssvc.exe (PID: 7072)
- mask_svc.exe (PID: 9984)
Starts Microsoft Installer
- installer.exe (PID: 5028)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 11888)
- cmd.exe (PID: 9004)
- cmd.exe (PID: 7984)
- cmd.exe (PID: 13324)
- cmd.exe (PID: 13160)
- wscript.exe (PID: 7788)
- cmd.exe (PID: 6644)
- cmd.exe (PID: 10264)
- cmd.exe (PID: 7784)
- cmd.exe (PID: 12820)
- cmd.exe (PID: 13668)
Executed via Task Scheduler
- powershell.EXE (PID: 7668)
- powershell.EXE (PID: 3168)
- PyuJGVV.exe (PID: 4908)
- powershell.EXE (PID: 12708)
- hCisxSr.exe (PID: 6272)
- rundll32.EXE (PID: 5848)
PowerShell script executed
- powershell.EXE (PID: 7668)
- powershell.EXE (PID: 3168)
- powershell.EXE (PID: 12708)
Reads the date of Windows installation
- powershell.EXE (PID: 7668)
- powershell.EXE (PID: 3168)
- powershell.EXE (PID: 12708)
Creates files in the driver directory
- DrvInst.exe (PID: 10552)
- DrvInst.exe (PID: 11508)
Executed via COM
- DrvInst.exe (PID: 10552)
- DrvInst.exe (PID: 11508)
Starts application with an unusual extension
- autosubplayer.exe (PID: 11196)
- autosubplayer.exe (PID: 9820)
- autosubplayer.exe (PID: 2416)
- autosubplayer.exe (PID: 8992)
- autosubplayer.exe (PID: 10872)
- autosubplayer.exe (PID: 13348)
Executes scripts
- PyuJGVV.exe (PID: 4908)
INFO
Checks Windows Trust Settings
- powershell.exe (PID: 3032)
- powershell.exe (PID: 2940)
- Fri055cc2a6e65.exe (PID: 2564)
- Fri051e1e7444.exe (PID: 2572)
- Fri05b5df5106928d62.exe (PID: 1472)
- UXSvpgMlC9m9bBKQDE2JZTmm.exe (PID: 3664)
- cC95N5mvhiND9SaOJgZL_GrP.exe (PID: 3392)
- powershell.exe (PID: 688)
- 2IDx4MjyyKCzrWVqZ7oRpu0L.exe (PID: 2568)
- powershell.exe (PID: 2616)
- powershell.exe (PID: 2624)
- enJg7NoG88QfYbCNfm8CGIxY.exe (PID: 1832)
- Vo8NvV9gwIArTRJTTs1VZ4WN.exe (PID: 2300)
- powershell.exe (PID: 5240)
- powershell.exe (PID: 5120)
- bpQalRIkWhtCbaq_LU6Sjqxc.exe (PID: 4932)
- iexplore.exe (PID: 5308)
- powershell.exe (PID: 3772)
- iexplore.exe (PID: 2348)
- iexplore.exe (PID: 5252)
- iexplore.exe (PID: 6128)
- iexplore.exe (PID: 6260)
- KdfEj_2TX4Gp0Nu_7E2BBvGy.exe (PID: 10048)
- powershell.exe (PID: 9700)
- installer.exe (PID: 5028)
- msiexec.exe (PID: 9636)
- MsiExec.exe (PID: 10032)
- powershell.exe (PID: 9236)
- powershell.exe (PID: 12476)
- powershell.exe (PID: 3716)
- powershell.exe (PID: 3460)
- powershell.exe (PID: 5712)
- powershell.exe (PID: 8676)
- powershell.exe (PID: 10616)
- powershell.exe (PID: 8224)
- powershell.exe (PID: 11120)
- powershell.EXE (PID: 7668)
- powershell.EXE (PID: 3168)
- MyNotes Installation.exe (PID: 6928)
- Fixfile01.exe (PID: 14144)
- tapinstall.exe (PID: 12980)
- DrvInst.exe (PID: 10552)
- DrvInst.exe (PID: 11508)
- powershell.exe (PID: 11076)
- powershell.exe (PID: 10212)
- powershell.exe (PID: 12736)
- powershell.exe (PID: 11136)
- powershell.EXE (PID: 12708)
- powershell.exe (PID: 10536)
- powershell.exe (PID: 11404)
- wscript.exe (PID: 7788)
- powershell.exe (PID: 8700)
- powershell.exe (PID: 7876)
- powershell.exe (PID: 9976)
- powershell.exe (PID: 7960)
- hCisxSr.exe (PID: 6272)
- powershell.exe (PID: 10584)
- powershell.exe (PID: 6232)
- powershell.exe (PID: 7288)
- powershell.exe (PID: 5316)
Reads internet explorer settings
- mshta.exe (PID: 1144)
- mshta.exe (PID: 2104)
- mshta.exe (PID: 2744)
- iexplore.exe (PID: 5308)
- iexplore.exe (PID: 2348)
- iexplore.exe (PID: 6260)
Reads settings of System Certificates
- Fri05890d11cdb13f95e.exe (PID: 3704)
- Fri05851d7f13.exe (PID: 2688)
- powershell.exe (PID: 3032)
- powershell.exe (PID: 2940)
- Fri0575b7d291a755f8.exe (PID: 2196)
- Fri055cc2a6e65.exe (PID: 2564)
- Fri051e1e7444.exe (PID: 2572)
- Fri05b5df5106928d62.exe (PID: 1472)
- UXSvpgMlC9m9bBKQDE2JZTmm.exe (PID: 3664)
- HSMNMHTbjtwpdzFM1XzkF8cR.exe (PID: 2732)
- cC95N5mvhiND9SaOJgZL_GrP.exe (PID: 3392)
- 2IDx4MjyyKCzrWVqZ7oRpu0L.exe (PID: 2568)
- RegAsm.exe (PID: 448)
- enJg7NoG88QfYbCNfm8CGIxY.exe (PID: 1832)
- Bouderbela.exe (PID: 5212)
- Bouderbela.exe (PID: 4824)
- AF8rGFxccUKYCIBH33I5lTUI.exe (PID: 3620)
- Vo8NvV9gwIArTRJTTs1VZ4WN.exe (PID: 2300)
- kLWXU7ly_PJqLRZqDfxkkISG.exe (PID: 5060)
- ZHuruwiwawu.exe (PID: 4272)
- ZHuruwiwawu.exe (PID: 5888)
- RegAsm.exe (PID: 5984)
- bpQalRIkWhtCbaq_LU6Sjqxc.exe (PID: 4932)
- iexplore.exe (PID: 5308)
- Nohululito.exe (PID: 4532)
- iexplore.exe (PID: 2348)
- Bouderbela.exe (PID: 6116)
- Bouderbela.exe (PID: 6972)
- SHazhobajaezhae.exe (PID: 7596)
- iexplore.exe (PID: 5252)
- iexplore.exe (PID: 6128)
- Wizhagaevaeko.exe (PID: 4004)
- Caehyxicaqe.exe (PID: 6732)
- iexplore.exe (PID: 6260)
- Funywacaefa.exe (PID: 6924)
- KdfEj_2TX4Gp0Nu_7E2BBvGy.exe (PID: 10048)
- UG4OUxxiIM92aDb0mIZeo27n.exe (PID: 4064)
- installer.exe (PID: 5028)
- msiexec.exe (PID: 9636)
- _dpOQFqSEbu1yisLxJYasR8i.exe (PID: 12800)
- random.exe (PID: 3224)
- MsiExec.exe (PID: 10032)
- random.exe (PID: 8752)
- Bouderbela.exe (PID: 13180)
- o0u1oYVCSrrEorCJhdBq8sAb.exe (PID: 12860)
- Bouderbela.exe (PID: 7820)
- SdJonBkhYaN9iMb9EsPUKK1Q.exe (PID: 4500)
- Xugovocylae.exe (PID: 8108)
- Cidaecashehu.exe (PID: 2080)
- random.exe (PID: 13228)
- RobCleanerInstll33132.exe (PID: 11196)
- jli.exe (PID: 9852)
- MyNotes Installation.exe (PID: 6928)
- anytime1.exe (PID: 13460)
- anytime2.exe (PID: 12468)
- logger.exe (PID: 2392)
- anytime3.exe (PID: 3444)
- Fixfile01.exe (PID: 14144)
- anytime4.exe (PID: 3196)
- LzmwAqmV.exe (PID: 3532)
- random.exe (PID: 13072)
- random.exe (PID: 8036)
- e72756b9-3e61-49d0-98c2-5ba1255e38e8.exe (PID: 11072)
- tapinstall.exe (PID: 12980)
- 161.tmp (PID: 11692)
- DrvInst.exe (PID: 10552)
- DrvInst.exe (PID: 11508)
- random.exe (PID: 12864)
- hCisxSr.exe (PID: 6272)
- mask_svc.exe (PID: 9984)
Checks supported languages
- taskkill.exe (PID: 2456)
- msiexec.exe (PID: 3696)
- rundll32.exe (PID: 3180)
- ipconfig.exe (PID: 2080)
- ipconfig.exe (PID: 3180)
- taskkill.exe (PID: 4072)
- control.exe (PID: 6036)
- rundll32.exe (PID: 2440)
- PING.EXE (PID: 5088)
- schtasks.exe (PID: 5108)
- schtasks.exe (PID: 3320)
- ipconfig.exe (PID: 4688)
- ipconfig.exe (PID: 2352)
- iexplore.exe (PID: 5252)
- iexplore.exe (PID: 5308)
- iexplore.exe (PID: 6128)
- iexplore.exe (PID: 2348)
- PING.EXE (PID: 6120)
- taskkill.exe (PID: 7228)
- taskkill.exe (PID: 7536)
- timeout.exe (PID: 4260)
- schtasks.exe (PID: 6864)
- schtasks.exe (PID: 6504)
- iexplore.exe (PID: 6260)
- iexplore.exe (PID: 9932)
- taskkill.exe (PID: 14064)
- timeout.exe (PID: 14156)
- sc.exe (PID: 1832)
- msiexec.exe (PID: 9636)
- MsiExec.exe (PID: 2440)
- msiexec.exe (PID: 13508)
- MsiExec.exe (PID: 10032)
- taskkill.exe (PID: 13464)
- taskkill.exe (PID: 14096)
- MsiExec.exe (PID: 12312)
- rundll32.exe (PID: 9884)
- forfiles.exe (PID: 8684)
- cmd.exe (PID: 3228)
- forfiles.exe (PID: 7552)
- cmd.exe (PID: 5032)
- forfiles.exe (PID: 14076)
- cmd.exe (PID: 7956)
- forfiles.exe (PID: 8832)
- sc.exe (PID: 14164)
- cmd.exe (PID: 5128)
- rundll32.exe (PID: 6464)
- forfiles.exe (PID: 13596)
- taskkill.exe (PID: 496)
- cmd.exe (PID: 11888)
- forfiles.exe (PID: 9836)
- reg.exe (PID: 7204)
- reg.exe (PID: 3240)
- cmd.exe (PID: 9004)
- regsvr32.exe (PID: 3300)
- schtasks.exe (PID: 9076)
- schtasks.exe (PID: 11360)
- taskkill.exe (PID: 13884)
- taskkill.exe (PID: 14276)
- rundll32.exe (PID: 3092)
- cmd.exe (PID: 6416)
- forfiles.exe (PID: 9440)
- forfiles.exe (PID: 7004)
- cmd.exe (PID: 13792)
- forfiles.exe (PID: 10228)
- cmd.exe (PID: 10188)
- forfiles.exe (PID: 11400)
- cmd.exe (PID: 6112)
- forfiles.exe (PID: 10752)
- cmd.exe (PID: 7984)
- forfiles.exe (PID: 13688)
- cmd.exe (PID: 13324)
- reg.exe (PID: 14004)
- reg.exe (PID: 7696)
- schtasks.exe (PID: 2488)
- gpupdate.exe (PID: 8008)
- schtasks.exe (PID: 2980)
- gpupdate.exe (PID: 12460)
- rundll32.exe (PID: 13316)
- taskkill.exe (PID: 8548)
- schtasks.exe (PID: 3996)
- taskkill.exe (PID: 4456)
- schtasks.exe (PID: 9112)
- rundll32.exe (PID: 11536)
- schtasks.exe (PID: 12148)
- schtasks.exe (PID: 12668)
- rundll32.exe (PID: 10696)
- rundll32.exe (PID: 9180)
- taskkill.exe (PID: 9336)
- timeout.exe (PID: 9104)
- vssvc.exe (PID: 7072)
- forfiles.exe (PID: 10104)
- cmd.exe (PID: 8888)
- forfiles.exe (PID: 9844)
- cmd.exe (PID: 5212)
- forfiles.exe (PID: 12572)
- cmd.exe (PID: 14284)
- forfiles.exe (PID: 13840)
- cmd.exe (PID: 9008)
- schtasks.exe (PID: 9144)
- schtasks.exe (PID: 4704)
- gpupdate.exe (PID: 9784)
- rundll32.exe (PID: 10764)
- schtasks.exe (PID: 7204)
- reg.exe (PID: 7008)
- reg.exe (PID: 7240)
- reg.exe (PID: 10544)
- reg.exe (PID: 12512)
- reg.exe (PID: 332)
- reg.exe (PID: 7592)
- reg.exe (PID: 5816)
- reg.exe (PID: 13992)
- reg.exe (PID: 12680)
- reg.exe (PID: 13020)
- reg.exe (PID: 14332)
- reg.exe (PID: 9788)
- reg.exe (PID: 9312)
- reg.exe (PID: 3904)
- reg.exe (PID: 11836)
- reg.exe (PID: 9368)
- schtasks.exe (PID: 1460)
- schtasks.exe (PID: 11040)
- reg.exe (PID: 8668)
- reg.exe (PID: 10452)
- forfiles.exe (PID: 2556)
- cmd.exe (PID: 7872)
- forfiles.exe (PID: 5624)
- forfiles.exe (PID: 3892)
- cmd.exe (PID: 9784)
- forfiles.exe (PID: 7180)
- cmd.exe (PID: 12624)
- cmd.exe (PID: 2396)
- schtasks.exe (PID: 9944)
- schtasks.exe (PID: 5524)
- reg.exe (PID: 3404)
- reg.exe (PID: 14148)
- schtasks.exe (PID: 736)
- schtasks.exe (PID: 7544)
- schtasks.exe (PID: 6564)
- schtasks.exe (PID: 6484)
- schtasks.exe (PID: 13992)
- schtasks.exe (PID: 2596)
- schtasks.exe (PID: 5844)
- schtasks.exe (PID: 3188)
- schtasks.exe (PID: 4504)
- rundll32.EXE (PID: 5848)
- reg.exe (PID: 3360)
- schtasks.exe (PID: 10104)
- reg.exe (PID: 12972)
- schtasks.exe (PID: 10668)
Reads the computer name
- taskkill.exe (PID: 2456)
- rundll32.exe (PID: 3180)
- ipconfig.exe (PID: 2080)
- ipconfig.exe (PID: 3180)
- taskkill.exe (PID: 4072)
- control.exe (PID: 6036)
- PING.EXE (PID: 5088)
- schtasks.exe (PID: 3320)
- schtasks.exe (PID: 5108)
- ipconfig.exe (PID: 4688)
- ipconfig.exe (PID: 2352)
- iexplore.exe (PID: 5252)
- iexplore.exe (PID: 6128)
- iexplore.exe (PID: 5308)
- iexplore.exe (PID: 2348)
- PING.EXE (PID: 6120)
- taskkill.exe (PID: 7228)
- taskkill.exe (PID: 7536)
- schtasks.exe (PID: 6504)
- schtasks.exe (PID: 6864)
- iexplore.exe (PID: 9932)
- iexplore.exe (PID: 6260)
- taskkill.exe (PID: 14064)
- sc.exe (PID: 1832)
- msiexec.exe (PID: 9636)
- MsiExec.exe (PID: 2440)
- msiexec.exe (PID: 13508)
- MsiExec.exe (PID: 10032)
- taskkill.exe (PID: 13464)
- taskkill.exe (PID: 14096)
- MsiExec.exe (PID: 12312)
- rundll32.exe (PID: 9884)
- sc.exe (PID: 14164)
- taskkill.exe (PID: 496)
- rundll32.exe (PID: 6464)
- schtasks.exe (PID: 11360)
- taskkill.exe (PID: 13884)
- taskkill.exe (PID: 14276)
- schtasks.exe (PID: 9076)
- rundll32.exe (PID: 3092)
- schtasks.exe (PID: 2980)
- schtasks.exe (PID: 2488)
- gpupdate.exe (PID: 8008)
- gpupdate.exe (PID: 12460)
- rundll32.exe (PID: 13316)
- taskkill.exe (PID: 8548)
- schtasks.exe (PID: 3996)
- taskkill.exe (PID: 4456)
- schtasks.exe (PID: 9112)
- rundll32.exe (PID: 11536)
- schtasks.exe (PID: 12668)
- schtasks.exe (PID: 12148)
- rundll32.exe (PID: 9180)
- rundll32.exe (PID: 10696)
- taskkill.exe (PID: 9336)
- vssvc.exe (PID: 7072)
- schtasks.exe (PID: 9144)
- schtasks.exe (PID: 4704)
- gpupdate.exe (PID: 9784)
- rundll32.exe (PID: 10764)
- schtasks.exe (PID: 7204)
- schtasks.exe (PID: 1460)
- schtasks.exe (PID: 11040)
- schtasks.exe (PID: 9944)
- schtasks.exe (PID: 5524)
- schtasks.exe (PID: 736)
- schtasks.exe (PID: 2596)
- schtasks.exe (PID: 6564)
- schtasks.exe (PID: 6484)
- schtasks.exe (PID: 7544)
- schtasks.exe (PID: 5844)
- schtasks.exe (PID: 3188)
- schtasks.exe (PID: 4504)
- schtasks.exe (PID: 13992)
- rundll32.EXE (PID: 5848)
- schtasks.exe (PID: 10104)
- schtasks.exe (PID: 10668)
Loads dropped or rewritten executable
- Fri05eeb2dae7b88520a.tmp (PID: 3732)
- Fri05eeb2dae7b88520a.tmp (PID: 3656)
- _qPnAfbohQzsKyRjIAPGwvSD.tmp (PID: 768)
- 9ZztShvlpEcbYXbhysio6quv.tmp (PID: 3308)
- whn8M8ZOzPDNHOMoUALHk6bF.tmp (PID: 4124)
- v00LWkGSaWY4x3B_h3ybD_hd.tmp (PID: 4756)
- jTZNXyp8ZD8XCh_p6Bwy1ozw.tmp (PID: 8020)
- AW3v1Pv1azQc96UgcSRj2eON.tmp (PID: 12972)
- 161.tmp (PID: 11692)
Application was dropped or rewritten from another process
- Fri05eeb2dae7b88520a.tmp (PID: 3732)
- Fri05eeb2dae7b88520a.tmp (PID: 3656)
- 9ZztShvlpEcbYXbhysio6quv.tmp (PID: 3308)
- _qPnAfbohQzsKyRjIAPGwvSD.tmp (PID: 768)
- Bouderbela.exe (PID: 4824)
- Bouderbela.exe (PID: 5212)
- whn8M8ZOzPDNHOMoUALHk6bF.tmp (PID: 4124)
- v00LWkGSaWY4x3B_h3ybD_hd.tmp (PID: 4756)
- Bouderbela.exe (PID: 6116)
- Bouderbela.exe (PID: 6972)
- jTZNXyp8ZD8XCh_p6Bwy1ozw.tmp (PID: 8020)
- AW3v1Pv1azQc96UgcSRj2eON.tmp (PID: 12972)
- Bouderbela.exe (PID: 13180)
- Bouderbela.exe (PID: 7820)
- 161.tmp (PID: 11692)
Dropped object may contain Bitcoin addresses
- Fri051e1e7444.exe (PID: 2572)
- Fri05b5df5106928d62.exe (PID: 1472)
- UG4OUxxiIM92aDb0mIZeo27n.exe (PID: 4064)
- RegAsm.exe (PID: 448)
- e3dwefw.exe (PID: 10540)
- SdJonBkhYaN9iMb9EsPUKK1Q.exe (PID: 4500)
Changes internet zones settings
- iexplore.exe (PID: 5252)
- iexplore.exe (PID: 6128)
Application launched itself
- iexplore.exe (PID: 5252)
- iexplore.exe (PID: 6128)
Creates files in the program directory
- Bouderbela.exe (PID: 4824)
- Bouderbela.exe (PID: 5212)
- Bouderbela.exe (PID: 6972)
- 161.tmp (PID: 11692)
Creates files in the user directory
- iexplore.exe (PID: 5308)
- iexplore.exe (PID: 5252)
Check for Java to be installed
- MsiExec.exe (PID: 2440)
- MsiExec.exe (PID: 10032)
Reads Microsoft Office registry keys
- MsiExec.exe (PID: 2440)
- MsiExec.exe (PID: 10032)
Changes settings of System certificates
- iexplore.exe (PID: 5252)
Adds / modifies Windows certificates
- iexplore.exe (PID: 5252)
Creates a software uninstall entry
- 161.tmp (PID: 11692)
Searches for installed software
- DrvInst.exe (PID: 10552)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| Subsystem: | Windows GUI |
|---|---|
| SubsystemVersion: | 4 |
| ImageVersion: | 6 |
| OSVersion: | 4 |
| EntryPoint: | 0x35d8 |
| UninitializedDataSize: | 2048 |
| InitializedDataSize: | 141824 |
| CodeSize: | 26112 |
| LinkerVersion: | 6 |
| PEType: | PE32 |
| TimeStamp: | 2020:08:01 04:44:18+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 01-Aug-2020 02:44:18 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 01-Aug-2020 02:44:18 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00006572 | 0x00006600 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.45392 |
.rdata | 0x00008000 | 0x00001398 | 0x00001400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.13672 |
.data | 0x0000A000 | 0x00020378 | 0x00000600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.09681 |
.ndata | 0x0002B000 | 0x00010000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x0003B000 | 0x00000A60 | 0x00000C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.20969 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.29035 | 843 | UNKNOWN | English - United States | RT_MANIFEST |
103 | 2.16096 | 20 | UNKNOWN | English - United States | RT_GROUP_ICON |
105 | 2.66174 | 256 | UNKNOWN | English - United States | RT_DIALOG |
106 | 2.88094 | 284 | UNKNOWN | English - United States | RT_DIALOG |
111 | 2.48825 | 96 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
739
Monitored processes
511
Malicious processes
156
Suspicious processes
80
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | "C:\Users\admin\Pictures\Adobe Films\m2TfQKJPCNVe5CpJOH7aekp7.exe" | C:\Users\admin\Pictures\Adobe Films\m2TfQKJPCNVe5CpJOH7aekp7.exe | — | Fri051e1e7444.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1001 Modules
| |||||||||||||||
| 332 | "C:\Windows\System32\reg.exe" ADD "HKLM\SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths" /f /v "C:\Program Files\ltUxslkTDwcU2" /t REG_DWORD /d 0 | C:\Windows\System32\reg.exe | — | wscript.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 444 | C:\Windows\system32\cmd.exe /c Fri05890d11cdb13f95e.exe | C:\Windows\system32\cmd.exe | — | setup_install.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 448 | #cmd | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | _plqVbpyQ72EAcDdXQafZHDS.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
| 460 | C:\Windows\system32\cmd.exe /c Fri05851d7f13.exe | C:\Windows\system32\cmd.exe | — | setup_install.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 480 | C:\Windows\system32\cmd.exe /c Fri05cc28ce70b.exe | C:\Windows\system32\cmd.exe | — | setup_install.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 496 | taskkill /im "GcleanerEU.exe" /f | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 588 | C:\Users\admin\AppData\Local\Temp\3zjlzgfv.5hh\installer.exe /qn CAMPAIGN="654" | C:\Users\admin\AppData\Local\Temp\3zjlzgfv.5hh\installer.exe | — | cmd.exe | |||||||||||
User: admin Company: AW Manager Integrity Level: HIGH Description: Windows Manager Installer Exit code: 0 Version: 1.0.0 Modules
| |||||||||||||||
| 688 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -enc aQBwAGMAbwBuAGYAaQBnACAALwByAGUAbABlAGEAcwBlAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | UG4OUxxiIM92aDb0mIZeo27n.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 736 | schtasks /CREATE /TN "GdnhtbLklpMPYjM2" /F /xml "C:\Program Files\bGfPtQlxU\WEwmSSR.xml" /RU "SYSTEM" | C:\Windows\system32\schtasks.exe | — | hCisxSr.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
423 059
Read events
417 922
Write events
4 914
Delete events
223
Modification events
| (PID) Process: | (4000) 5bfb87691070668037df7a6bc1eac92bdb683ada3159b83c136146632835cb7f.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4000) 5bfb87691070668037df7a6bc1eac92bdb683ada3159b83c136146632835cb7f.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4000) 5bfb87691070668037df7a6bc1eac92bdb683ada3159b83c136146632835cb7f.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4000) 5bfb87691070668037df7a6bc1eac92bdb683ada3159b83c136146632835cb7f.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2284) setup_installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2284) setup_installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2284) setup_installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2284) setup_installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3704) Fri05890d11cdb13f95e.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Fri05890d11cdb13f95e_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3704) Fri05890d11cdb13f95e.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Fri05890d11cdb13f95e_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
413
Suspicious files
244
Text files
279
Unknown types
106
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 884 | svchost.exe | C:\Windows\appcompat\programs\RecentFileCache.bcf | txt | |
MD5:— | SHA256:— | |||
| 4000 | 5bfb87691070668037df7a6bc1eac92bdb683ada3159b83c136146632835cb7f.exe | C:\Users\admin\AppData\Local\Temp\setup_installer.exe | executable | |
MD5:C46908531375BAB2AF1AA2868BA6B7DD | SHA256:3E74A31C3E282AB53D039B04905EA50CAFACAF3D293656E1E05C0E9156B689FD | |||
| 2284 | setup_installer.exe | C:\Users\admin\AppData\Local\Temp\7zSCE868A29\Fri053f5694ea31c9a.exe | executable | |
MD5:BAD58C651D1048581F4862E6C6539417 | SHA256:F52E1EBC1A294F9F4413A4069DD27F6926E4C64E4A0FDB21957BEB3F8EC12271 | |||
| 2284 | setup_installer.exe | C:\Users\admin\AppData\Local\Temp\7zSCE868A29\Fri0575b7d291a755f8.exe | executable | |
MD5:3399436F50FAD870CADE4F68DE68A76D | SHA256:9E9519DB3A55DD28CC85DDB8E02990758FA23D0F387E006DE073E30277BCE862 | |||
| 2284 | setup_installer.exe | C:\Users\admin\AppData\Local\Temp\7zSCE868A29\Fri051e1e7444.exe | executable | |
MD5:B4C503088928EEF0E973A269F66A0DD2 | SHA256:2A95CE43C87B8A26BE71A459EAE796A572422BD99CF0B9A3580A3A68E7DBD1A2 | |||
| 2284 | setup_installer.exe | C:\Users\admin\AppData\Local\Temp\7zSCE868A29\Fri0541e16ce794d258f.exe | executable | |
MD5:DEC69C757CE1AE8454F97EF6966AA817 | SHA256:2B396AE1FA95EF655BB7B0EB45532A857D882BB601ADEB8FB1B5D43DCFF9EC31 | |||
| 2284 | setup_installer.exe | C:\Users\admin\AppData\Local\Temp\7zSCE868A29\Fri05851d7f13.exe | executable | |
MD5:91E3BED725A8399D72B182E5E8132524 | SHA256:18AF3C7BDEB815AF9ABE9DCC4F524B2FB2A33AC9CC6784F31E302C10A8D09A0D | |||
| 2284 | setup_installer.exe | C:\Users\admin\AppData\Local\Temp\7zSCE868A29\Fri055cc2a6e65.exe | executable | |
MD5:619AA73B97D9D55DF2AB142B8A7D9AE4 | SHA256:8164FCC1805D268C83BB84CFD42A21E9F85752C13C4D2033F191ED50FC8C47ED | |||
| 2284 | setup_installer.exe | C:\Users\admin\AppData\Local\Temp\7zSCE868A29\Fri05a277b9a3d2.exe | executable | |
MD5:8958066E38EB4B70F922DB2C23457C18 | SHA256:3F3A020F63DAEF5FFA7C2EB9014452DFA913CC6FF977E5747E6F0C854D849358 | |||
| 2284 | setup_installer.exe | C:\Users\admin\AppData\Local\Temp\7zSCE868A29\Fri05beb1e355.exe | executable | |
MD5:BDBBF4F034C9F43E4AB00002EB78B990 | SHA256:2DA3696E82B2A874191A6F4E3BFD26D4B7E5AA5D187C5AFDEBBE52263DCCD5AE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
373
TCP/UDP connections
723
DNS requests
245
Threats
706
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2572 | Fri051e1e7444.exe | GET | — | 45.133.1.107:80 | http://45.133.1.107/server.txt | unknown | — | — | malicious |
1472 | Fri05b5df5106928d62.exe | GET | — | 45.133.1.107:80 | http://45.133.1.107/server.txt | unknown | — | — | malicious |
2572 | Fri051e1e7444.exe | HEAD | 200 | 45.144.225.57:80 | http://45.144.225.57/download/NiceProcessX32.bmp | unknown | — | — | malicious |
2572 | Fri051e1e7444.exe | GET | 200 | 2.56.59.42:80 | http://2.56.59.42/base/api/statistics.php | unknown | binary | 94 b | malicious |
2572 | Fri051e1e7444.exe | POST | 200 | 2.56.59.42:80 | http://2.56.59.42/base/api/getData.php | unknown | text | 108 b | malicious |
2572 | Fri051e1e7444.exe | POST | 200 | 2.56.59.42:80 | http://2.56.59.42/base/api/getData.php | unknown | text | 108 b | malicious |
2564 | Fri055cc2a6e65.exe | GET | 200 | 93.184.220.29:80 | http://statuse.digitalcertvalidation.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRJrF0xYA49jC3D83fgDGesaUkzIQQUf9OZ86BHDjEAVlYijrfMnt3KAYoCEAYJR5FkG19ljPHMaGsuvmc%3D | US | der | 471 b | whitelisted |
1472 | Fri05b5df5106928d62.exe | GET | 200 | 2.56.59.42:80 | http://2.56.59.42/base/api/statistics.php | unknown | binary | 94 b | malicious |
2492 | svchost.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/?fields=8198 | unknown | binary | 61 b | malicious |
2572 | Fri051e1e7444.exe | GET | 200 | 45.144.225.57:80 | http://45.144.225.57/download/NiceProcessX32.bmp | unknown | executable | 259 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2688 | Fri05851d7f13.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
2432 | Fri05a277b9a3d2.exe | 91.121.67.60:23325 | — | OVH SAS | FR | malicious |
3116 | Fri05f84fa77402bf.exe | 194.104.136.5:46013 | — | — | NL | malicious |
2564 | Fri055cc2a6e65.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
2564 | Fri055cc2a6e65.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3008 | Fri053f5694ea31c9a.exe | 135.181.129.119:4805 | — | — | CA | malicious |
1472 | Fri05b5df5106928d62.exe | 45.133.1.107:80 | — | — | — | malicious |
2572 | Fri051e1e7444.exe | 45.133.1.107:80 | — | — | — | malicious |
2688 | Fri05851d7f13.exe | 172.67.204.112:443 | t.gogamec.com | — | US | suspicious |
2564 | Fri055cc2a6e65.exe | 149.28.253.196:443 | www.listincode.com | — | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
marianu.xyz |
| whitelisted |
www.listincode.com |
| whitelisted |
t.gogamec.com |
| malicious |
cdn.discordapp.com |
| shared |
niemannbest.me |
| unknown |
ppgggb.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
statuse.digitalcertvalidation.com |
| whitelisted |
iplogger.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2492 | svchost.exe | Potential Corporate Privacy Violation | ET DNS Non-DNS or Non-Compliant DNS traffic on DNS port Reserved Bit Set |
2492 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
2492 | svchost.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
2572 | Fri051e1e7444.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2572 | Fri051e1e7444.exe | Generic Protocol Command Decode | SURICATA Applayer Mismatch protocol both directions |
— | — | Potentially Bad Traffic | ET DNS Query for .cc TLD |
2572 | Fri051e1e7444.exe | Generic Protocol Command Decode | SURICATA Applayer Mismatch protocol both directions |
2572 | Fri051e1e7444.exe | A Network Trojan was detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
2572 | Fri051e1e7444.exe | Potential Corporate Privacy Violation | ET POLICY Possible External IP Lookup SSL Cert Observed (ipinfo.io) |
2572 | Fri051e1e7444.exe | A Network Trojan was detected | ET TROJAN Win32/Unk.HRESQ! MultiDownloader Checkin |
250 ETPRO signatures available at the full report
Process | Message |
|---|---|
lighteningplayer-cache-gen.exe | main libvlc debug: VLC media player - 3.0.7 Vetinari
|
lighteningplayer-cache-gen.exe | main libvlc debug: Copyright � 1996-2018 the VideoLAN team
|
lighteningplayer-cache-gen.exe | main libvlc debug: revision 3.0.2-225-gc9e3360dd4
|
lighteningplayer-cache-gen.exe | main libvlc debug: configured with ../extras/package/win32/../../../configure '--enable-update-check' '--enable-lua' '--enable-faad' '--enable-flac' '--enable-theora' '--enable-twolame' '--enable-avcodec' '--enable-merge-ffmpeg' '--enable-dca' '--enable-mpc' '--enable-libass' '--enable-x264' '--enable-schroedinger' '--enable-realrtsp' '--enable-live555' '--enable-dvdread' '--enable-shout' '--enable-goom' '--enable-caca' '--enable-qt' '--enable-skins2' '--enable-sse' '--enable-mmx' '--enable-libcddb' '--enable-zvbi' '--disable-telx' '--enable-nls' '--host=i686-w64-mingw32' '--build=x86_64-pc-linux-gnu' 'build_alias=x86_64-pc-linux-gnu' 'host_alias=i686-w64-mingw32'
|
lighteningplayer-cache-gen.exe | main libvlc debug: using multimedia timers as clock source
|
lighteningplayer-cache-gen.exe | main libvlc debug: min period: 1 ms, max period: 1000000 ms
|
lighteningplayer-cache-gen.exe | main libvlc debug: searching plug-in modules
|
lighteningplayer-cache-gen.exe | main libvlc debug: ignoring plugins cache file
|
lighteningplayer-cache-gen.exe | main libvlc debug: recursively browsing `C:\Program Files\lighteningplayer\plugins'
|
lighteningplayer-cache-gen.exe | main libvlc debug: saving plugins cache C:\Program Files\lighteningplayer\plugins\plugins.dat
|