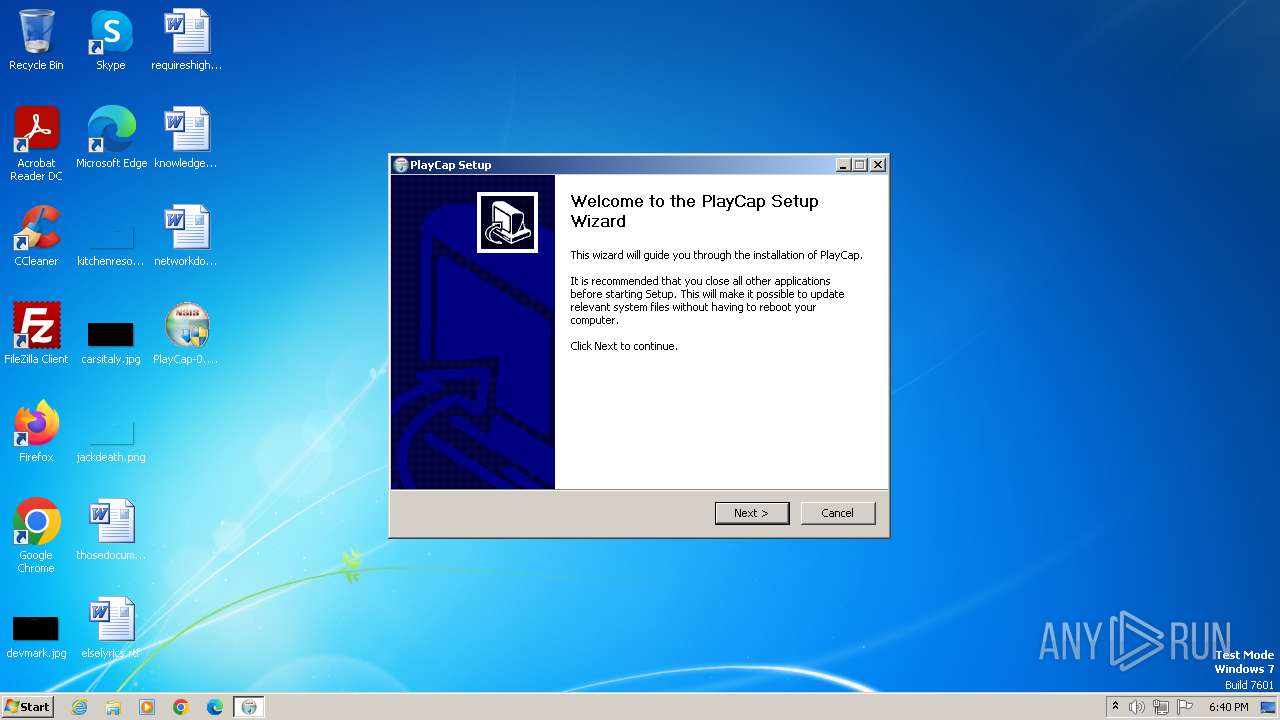
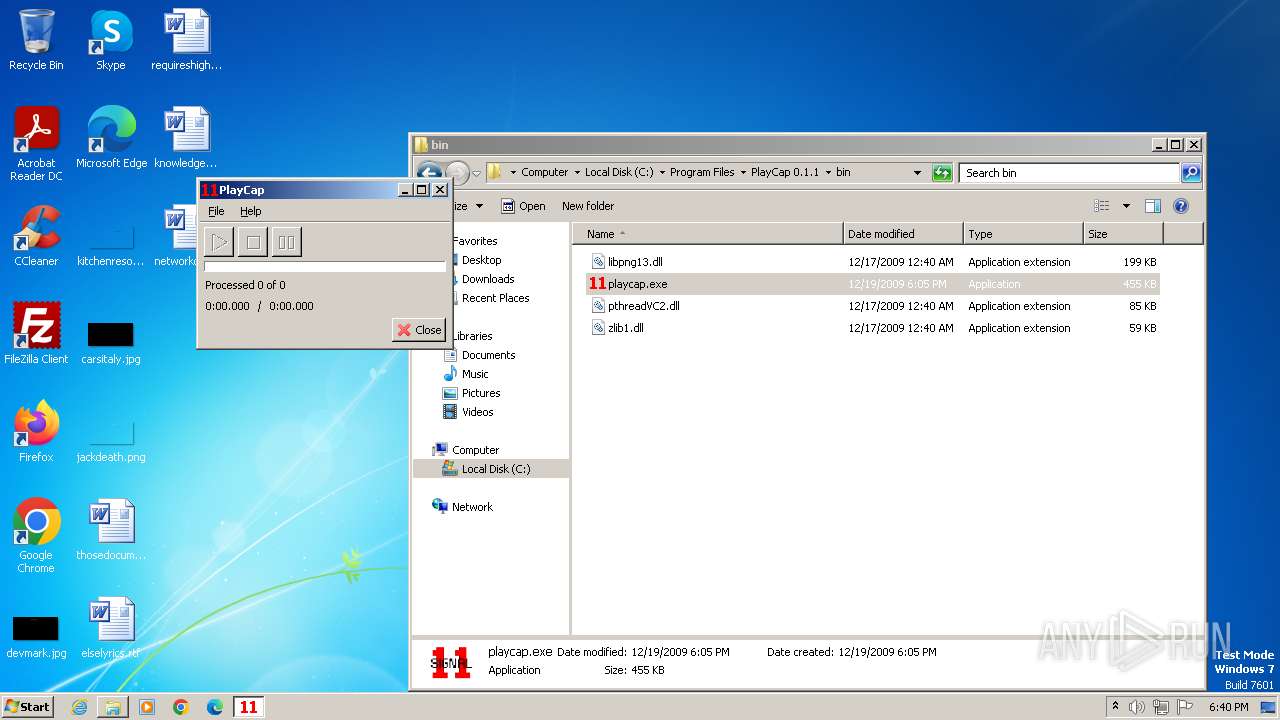
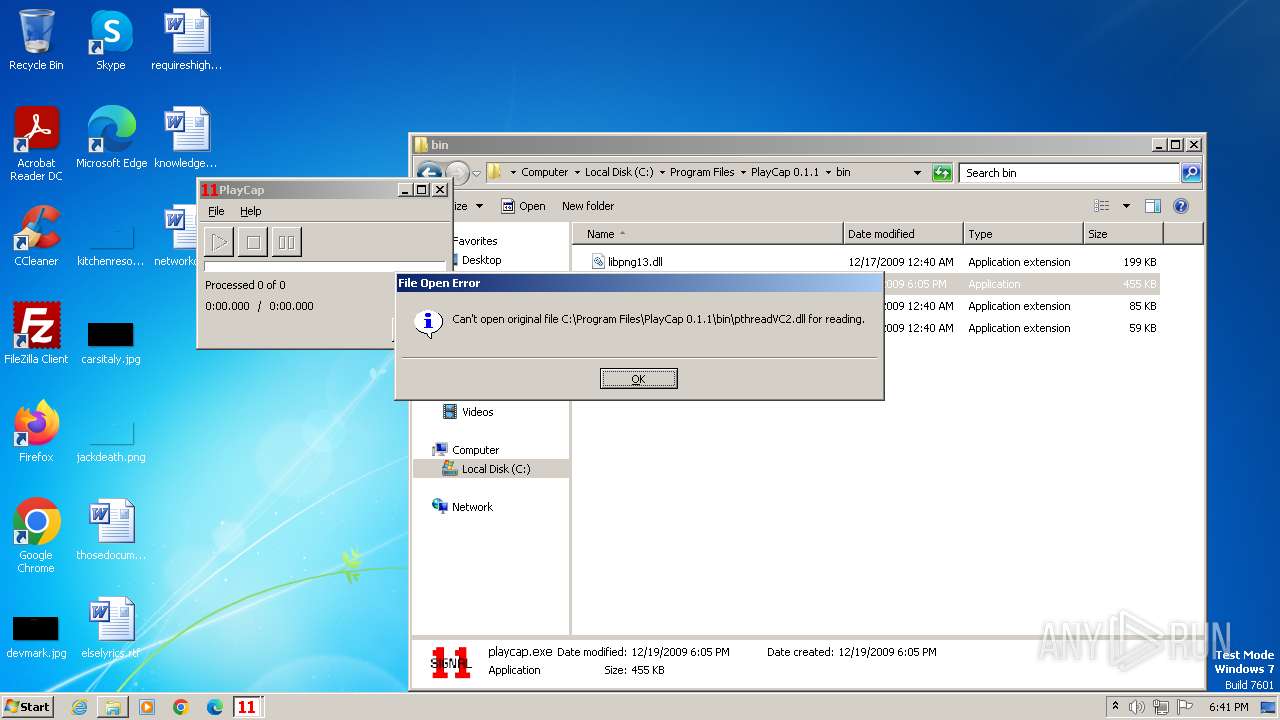
| File name: | PlayCap-0.1.1-win32.exe |
| Full analysis: | https://app.any.run/tasks/62c52787-22e5-4b73-8fa7-0b16632b3271 |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2023, 17:40:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | ED94C5BF820AC5CDD1F627D8330970B4 |
| SHA1: | 5E1D6FBBFD495DB68FF70B07E4055DD158083E9D |
| SHA256: | 5BD66F2B0A5C017063D9F1D2F424181163A02D95651009C373DC7708B4B81C17 |
| SSDEEP: | 49152:tGFjR3xH8XdyhFO3/w/pEVVcBOSxWbrYlqbttnNUjm2gOQz1lWLIzpseywKcus6z:tG7BH4F/wuVVcB7sQcbttnNUjpQz1fW9 |
MALICIOUS
Loads dropped or rewritten executable
- PlayCap-0.1.1-win32.exe (PID: 2888)
- WinPcap_4_1_1.exe (PID: 792)
- playcap.exe (PID: 3184)
Drops the executable file immediately after the start
- PlayCap-0.1.1-win32.exe (PID: 2888)
- WinPcap_4_1_1.exe (PID: 792)
Application was dropped or rewritten from another process
- WinPcap_4_1_1.exe (PID: 792)
- PlayCap-0.1.1-win32.exe (PID: 2888)
- PlayCap-0.1.1-win32.exe (PID: 1396)
- playcap.exe (PID: 3184)
Creates a writable file the system directory
- WinPcap_4_1_1.exe (PID: 792)
Starts NET.EXE for service management
- net.exe (PID: 1240)
- WinPcap_4_1_1.exe (PID: 792)
SUSPICIOUS
Reads the Internet Settings
- WinPcap_4_1_1.exe (PID: 792)
Reads Microsoft Outlook installation path
- WinPcap_4_1_1.exe (PID: 792)
Reads Internet Explorer settings
- WinPcap_4_1_1.exe (PID: 792)
Creates files in the driver directory
- WinPcap_4_1_1.exe (PID: 792)
The process creates files with name similar to system file names
- WinPcap_4_1_1.exe (PID: 792)
Drops a system driver (possible attempt to evade defenses)
- WinPcap_4_1_1.exe (PID: 792)
Malware-specific behavior (creating "System.dll" in Temp)
- WinPcap_4_1_1.exe (PID: 792)
Creates or modifies Windows services
- WinPcap_4_1_1.exe (PID: 792)
INFO
Checks supported languages
- PlayCap-0.1.1-win32.exe (PID: 2888)
- WinPcap_4_1_1.exe (PID: 792)
- playcap.exe (PID: 3184)
Reads the computer name
- PlayCap-0.1.1-win32.exe (PID: 2888)
- WinPcap_4_1_1.exe (PID: 792)
- playcap.exe (PID: 3184)
Create files in a temporary directory
- PlayCap-0.1.1-win32.exe (PID: 2888)
- WinPcap_4_1_1.exe (PID: 792)
Creates files in the program directory
- PlayCap-0.1.1-win32.exe (PID: 2888)
- WinPcap_4_1_1.exe (PID: 792)
Reads Environment values
- WinPcap_4_1_1.exe (PID: 792)
Checks proxy server information
- WinPcap_4_1_1.exe (PID: 792)
Reads the machine GUID from the registry
- WinPcap_4_1_1.exe (PID: 792)
- playcap.exe (PID: 3184)
Manual execution by a user
- explorer.exe (PID: 3936)
- playcap.exe (PID: 3184)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (94.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.5) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:12:05 23:50:41+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 23040 |
| InitializedDataSize: | 119808 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x30cb |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
50
Monitored processes
7
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 792 | "C:\Program Files\PlayCap 0.1.1\WinPcap_4_1_1.exe" | C:\Program Files\PlayCap 0.1.1\WinPcap_4_1_1.exe | — | PlayCap-0.1.1-win32.exe | |||||||||||
User: admin Company: CACE Technologies, Inc. Integrity Level: HIGH Description: WinPcap 4.1.1 installer Exit code: 0 Version: 4.1.0.1753 Modules
| |||||||||||||||
| 1240 | net start npf | C:\Windows\System32\net.exe | — | WinPcap_4_1_1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1396 | "C:\Users\admin\Desktop\PlayCap-0.1.1-win32.exe" | C:\Users\admin\Desktop\PlayCap-0.1.1-win32.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2484 | C:\Windows\system32\net1 start npf | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2888 | "C:\Users\admin\Desktop\PlayCap-0.1.1-win32.exe" | C:\Users\admin\Desktop\PlayCap-0.1.1-win32.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3184 | "C:\Program Files\PlayCap 0.1.1\bin\playcap.exe" | C:\Program Files\PlayCap 0.1.1\bin\playcap.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3936 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
5 465
Read events
5 432
Write events
32
Delete events
1
Modification events
| (PID) Process: | (792) WinPcap_4_1_1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (792) WinPcap_4_1_1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (792) WinPcap_4_1_1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (792) WinPcap_4_1_1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (792) WinPcap_4_1_1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (792) WinPcap_4_1_1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (792) WinPcap_4_1_1.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\NPF |
| Operation: | write | Name: | Start |
Value: 3 | |||
| (PID) Process: | (3184) playcap.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3184) playcap.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 01000000020000000000000007000000060000000C0000000B0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (3184) playcap.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\201\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Generic | |||
Executable files
24
Suspicious files
4
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2888 | PlayCap-0.1.1-win32.exe | C:\Program Files\PlayCap 0.1.1\WinPcap_4_1_1.exe | executable | |
MD5:2CAA5498171B21388168C13AD4F4A157 | SHA256:8E57D910173FB471F4A02911D652A4A65C1632CACB67F759472B1D7EC9995F87 | |||
| 2888 | PlayCap-0.1.1-win32.exe | C:\Users\admin\AppData\Local\Temp\nsuBDC1.tmp\NSIS.InstallOptions.ini | text | |
MD5:88A551B08A847414E1C6FFB478EB65BF | SHA256:0954A787F0FAC0A5E82C0173DAD46AA22B1D451C3C2C9C8D227773F043308EA6 | |||
| 2888 | PlayCap-0.1.1-win32.exe | C:\Users\admin\AppData\Local\Temp\nsuBDC1.tmp\ioSpecial.ini | text | |
MD5:E2D5070BC28DB1AC745613689FF86067 | SHA256:D95AED234F932A1C48A2B1B0D98C60CA31F962310C03158E2884AB4DDD3EA1E0 | |||
| 2888 | PlayCap-0.1.1-win32.exe | C:\Users\admin\AppData\Local\Temp\nsuBDC1.tmp\InstallOptions.dll | executable | |
MD5:325B008AEC81E5AAA57096F05D4212B5 | SHA256:C9CD5C9609E70005926AE5171726A4142FFBCCCC771D307EFCD195DAFC1E6B4B | |||
| 792 | WinPcap_4_1_1.exe | C:\Users\admin\AppData\Local\Temp\nsoE1E3.tmp\ioSpecial.ini | text | |
MD5:E2D5070BC28DB1AC745613689FF86067 | SHA256:D95AED234F932A1C48A2B1B0D98C60CA31F962310C03158E2884AB4DDD3EA1E0 | |||
| 792 | WinPcap_4_1_1.exe | C:\Users\admin\AppData\Local\Temp\NetSol.jpg | image | |
MD5:A21A163808D01B16069B7F9C0031B787 | SHA256:B3C7B792E066DF8C012D47BEB1394E79A0553D930DC86255DDA9262FB67EF0A4 | |||
| 2888 | PlayCap-0.1.1-win32.exe | C:\Program Files\PlayCap 0.1.1\bin\libpng13.dll | executable | |
MD5:04865CBF31FF163A422D44C39747F011 | SHA256:BCC18FAEE81A2362B2BEBC58208FF23E8A9641DD5843DD6692C19F942E0259BC | |||
| 2888 | PlayCap-0.1.1-win32.exe | C:\Program Files\PlayCap 0.1.1\bin\zlib1.dll | executable | |
MD5:80E41408F6D641DC1C0F5353A0CC8125 | SHA256:B09537250201236472CCD3CAFF5C0C12A5FAD262E1E951350E9E5ED2A81D9DDE | |||
| 2888 | PlayCap-0.1.1-win32.exe | C:\Program Files\PlayCap 0.1.1\Uninstall.exe | executable | |
MD5:45D394860066EA4B66E91688D999EE75 | SHA256:3CB387842ED5CF346D5BC4797E998337D9FE527ECCB13240967BE8A8B6C512E1 | |||
| 792 | WinPcap_4_1_1.exe | C:\Users\admin\AppData\Local\Temp\CACE_Banner.htm | html | |
MD5:E2E69E49126D7E7DBD4C6573121AC56F | SHA256:5738ED20F0727FB06587483AC2CEF9E813D1C26676516EE2713A782DE9BFD240 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |