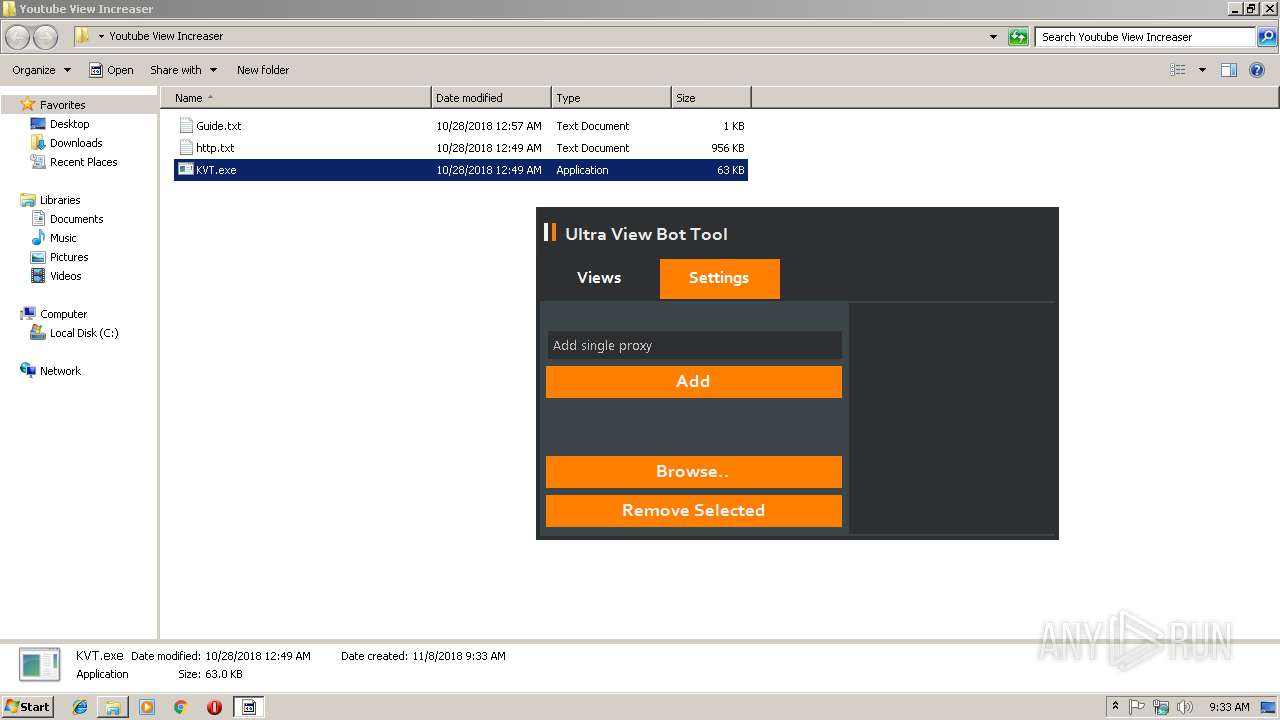
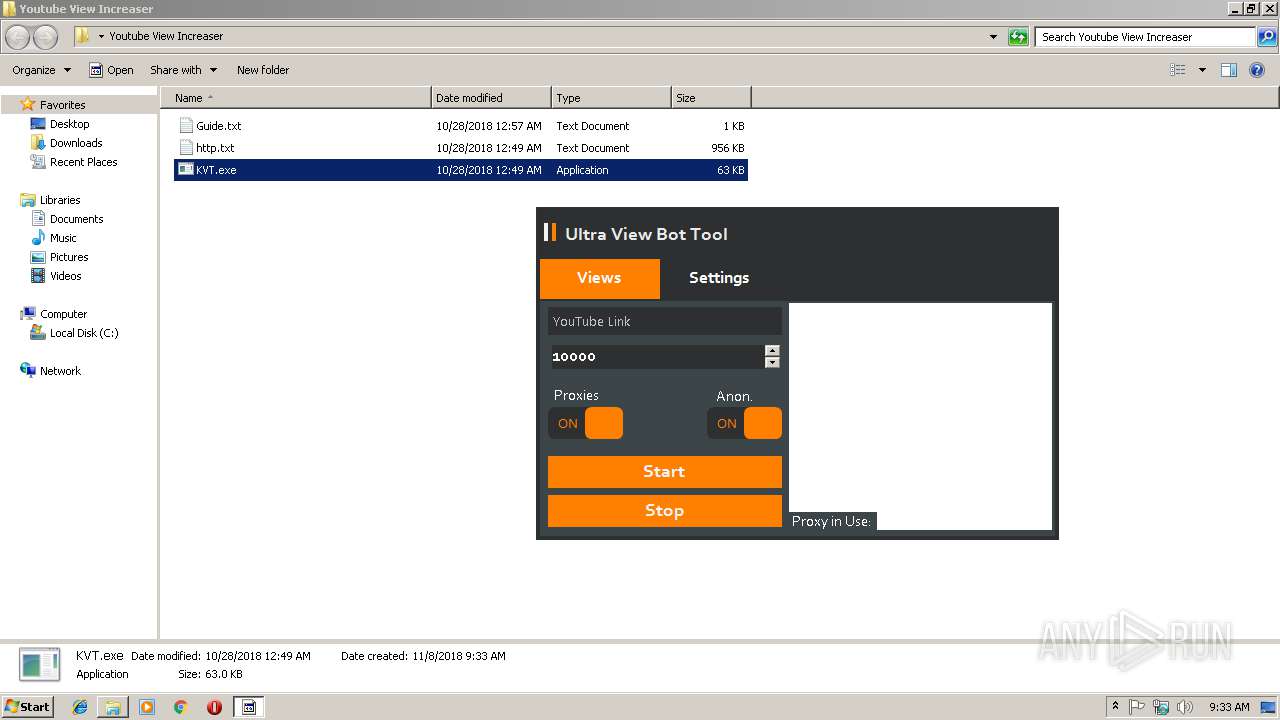
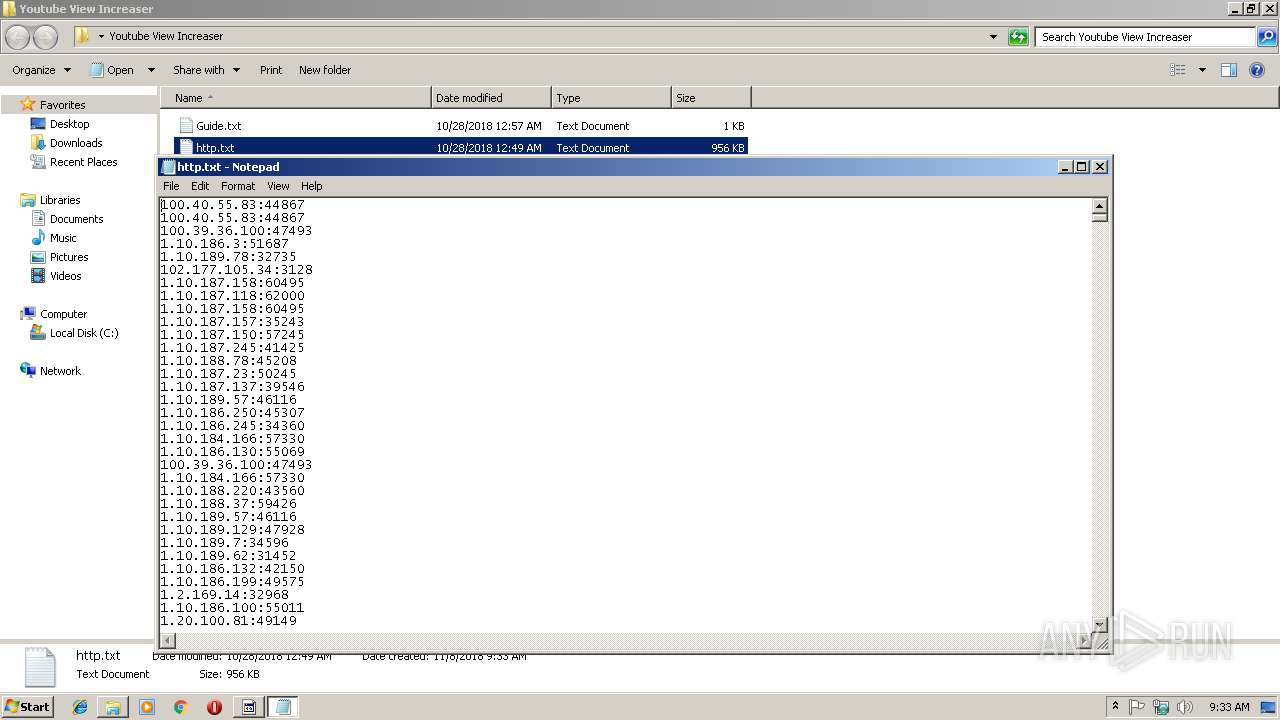
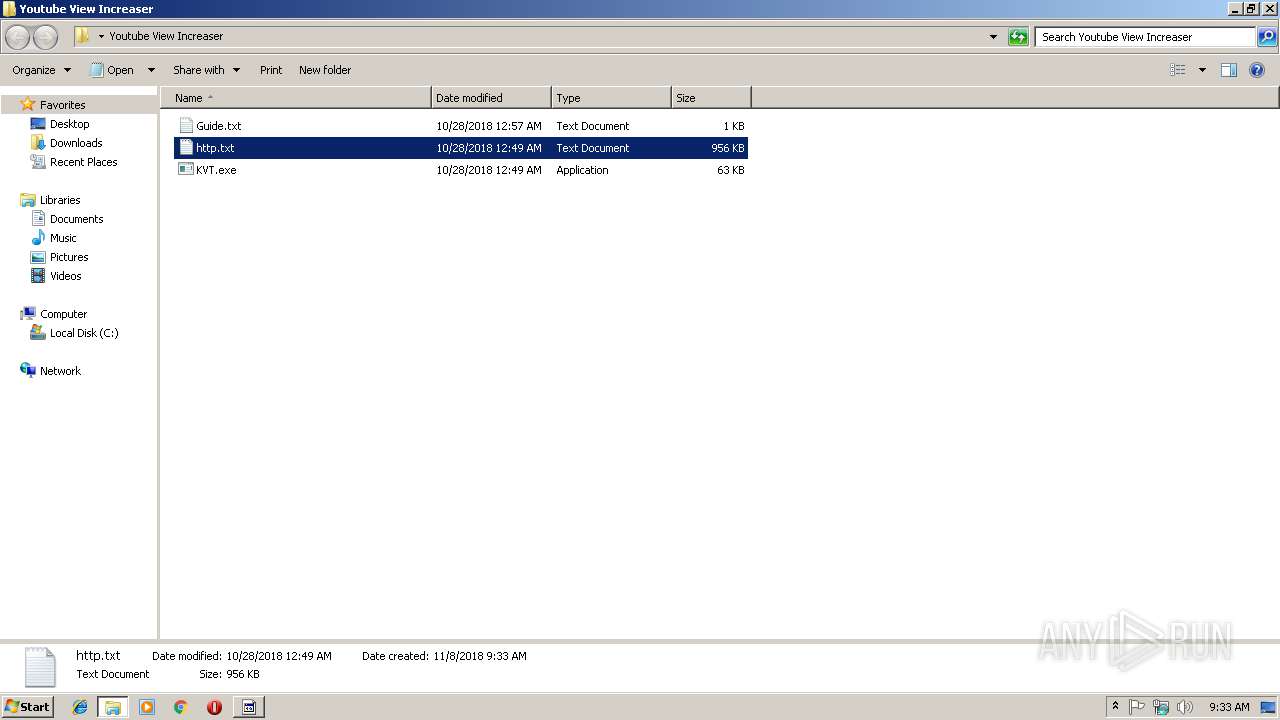
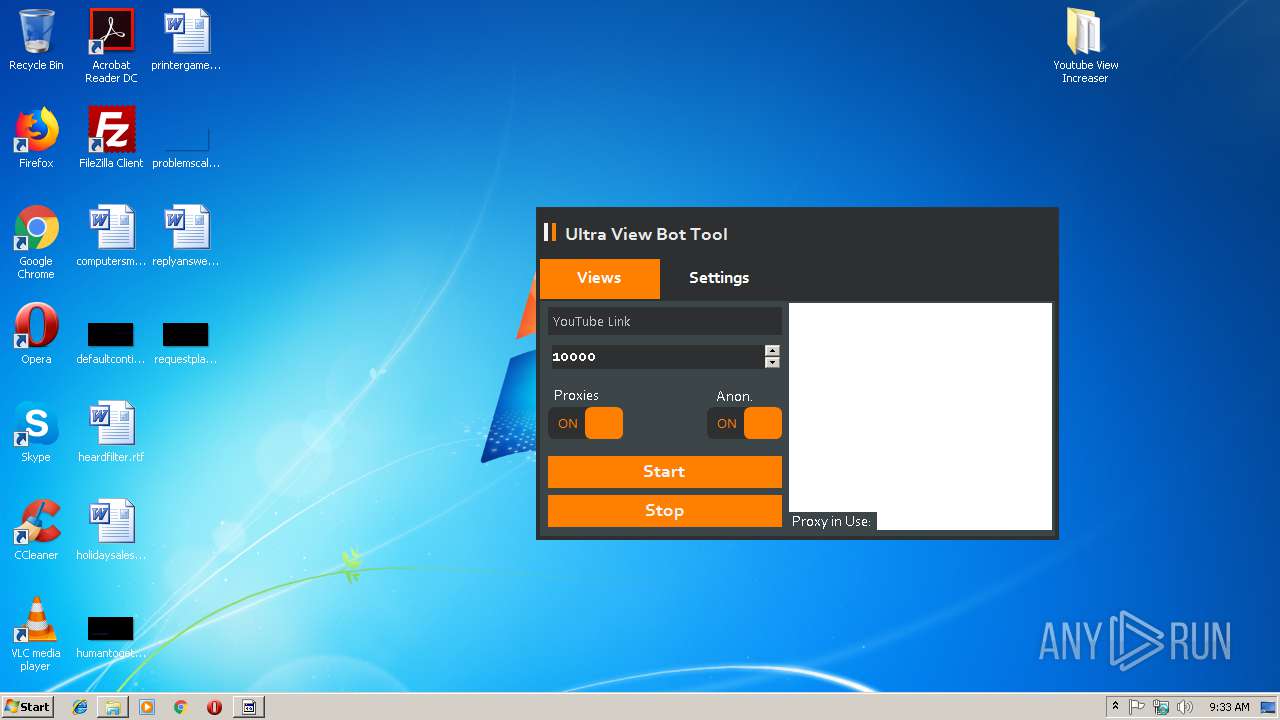
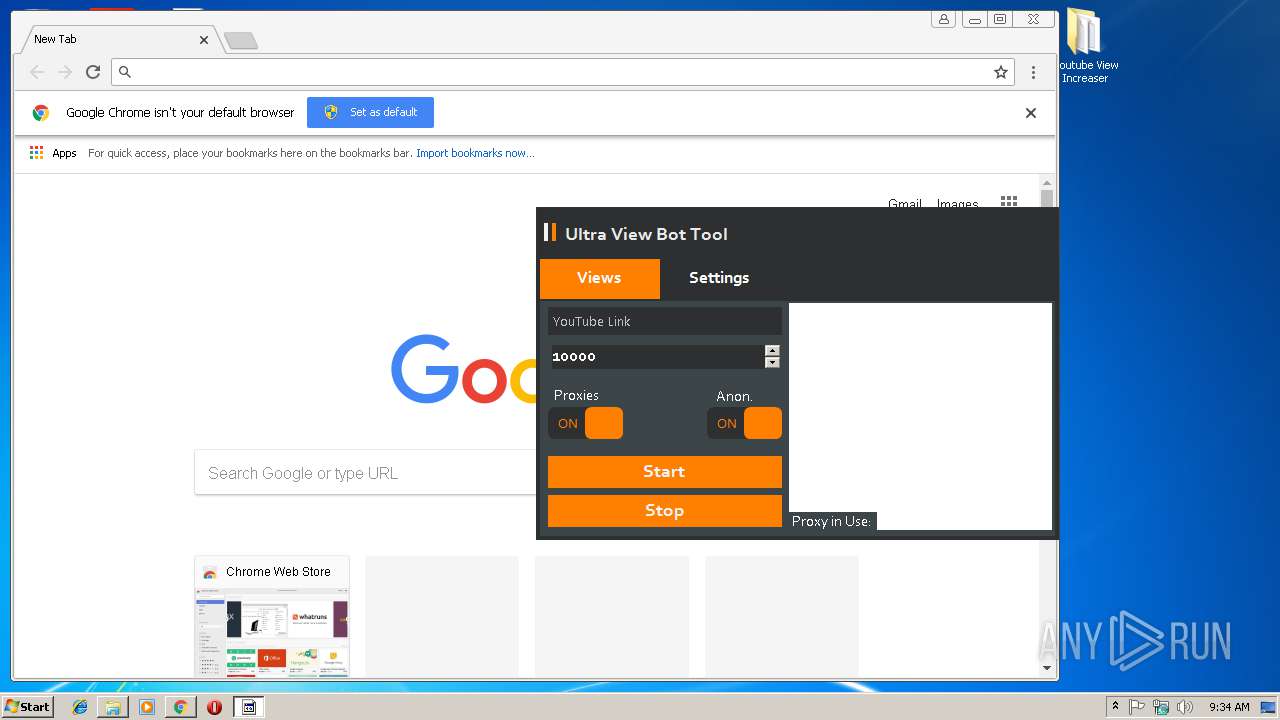
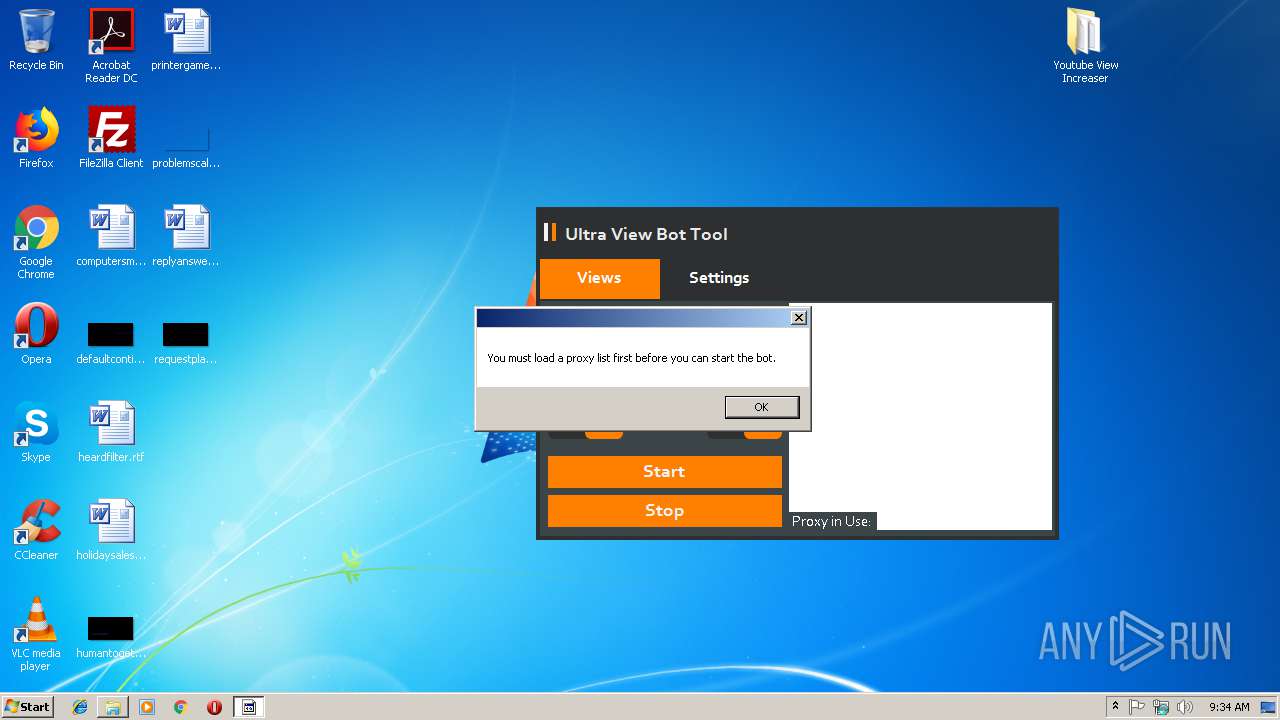
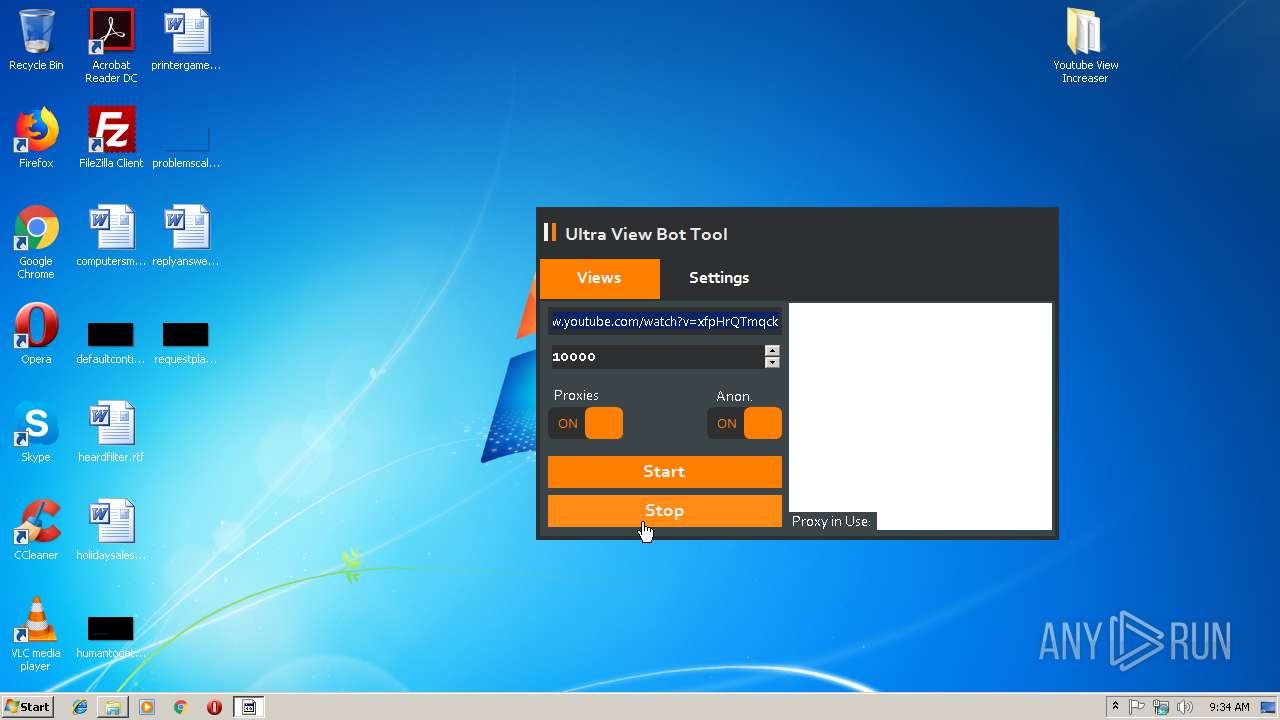
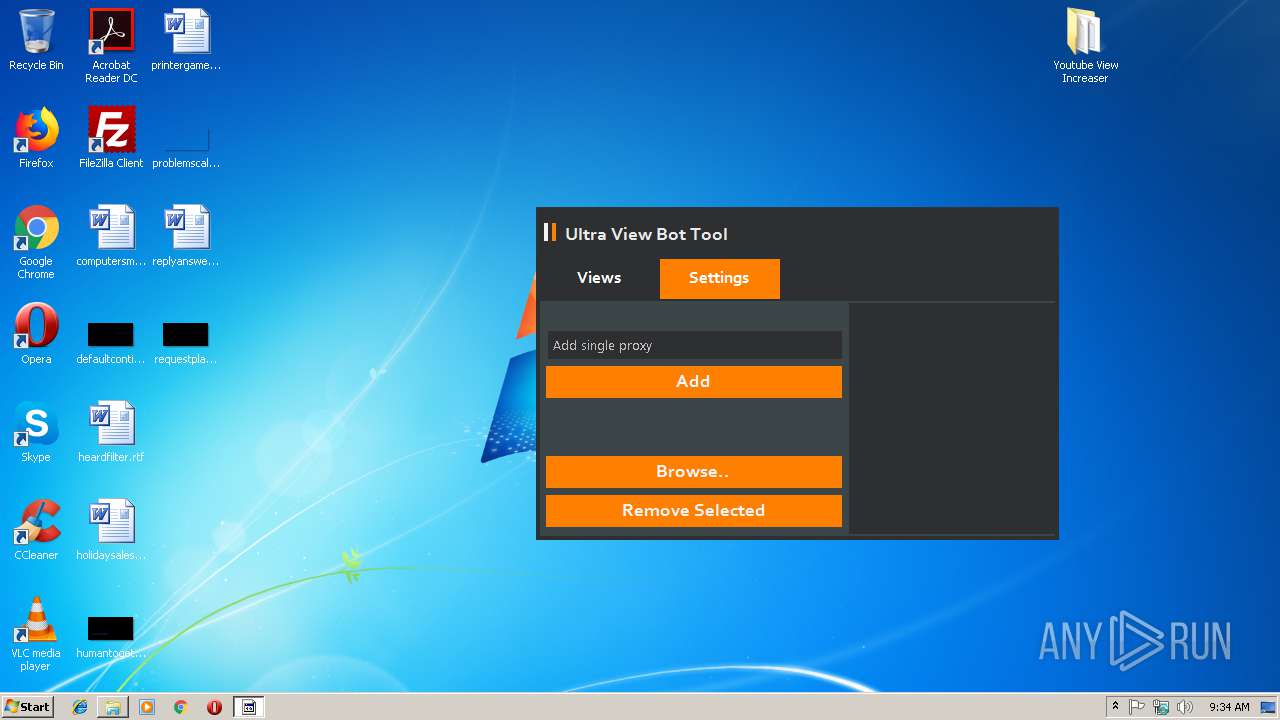
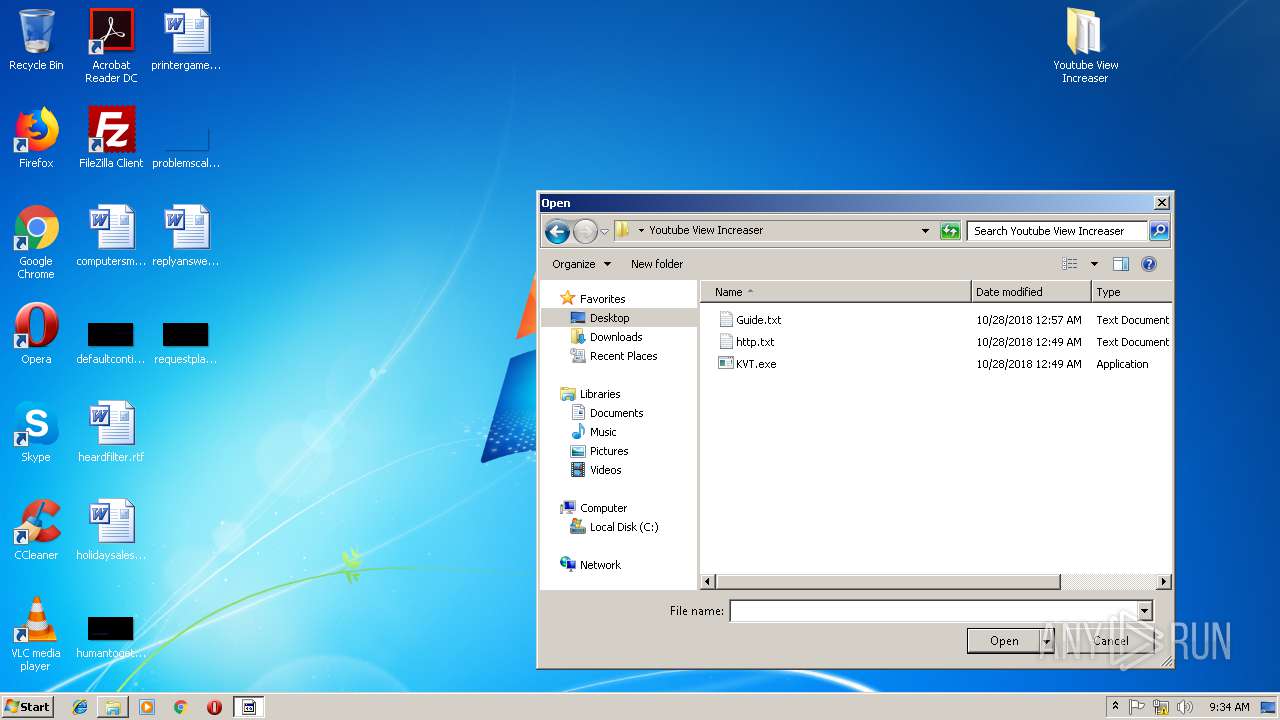
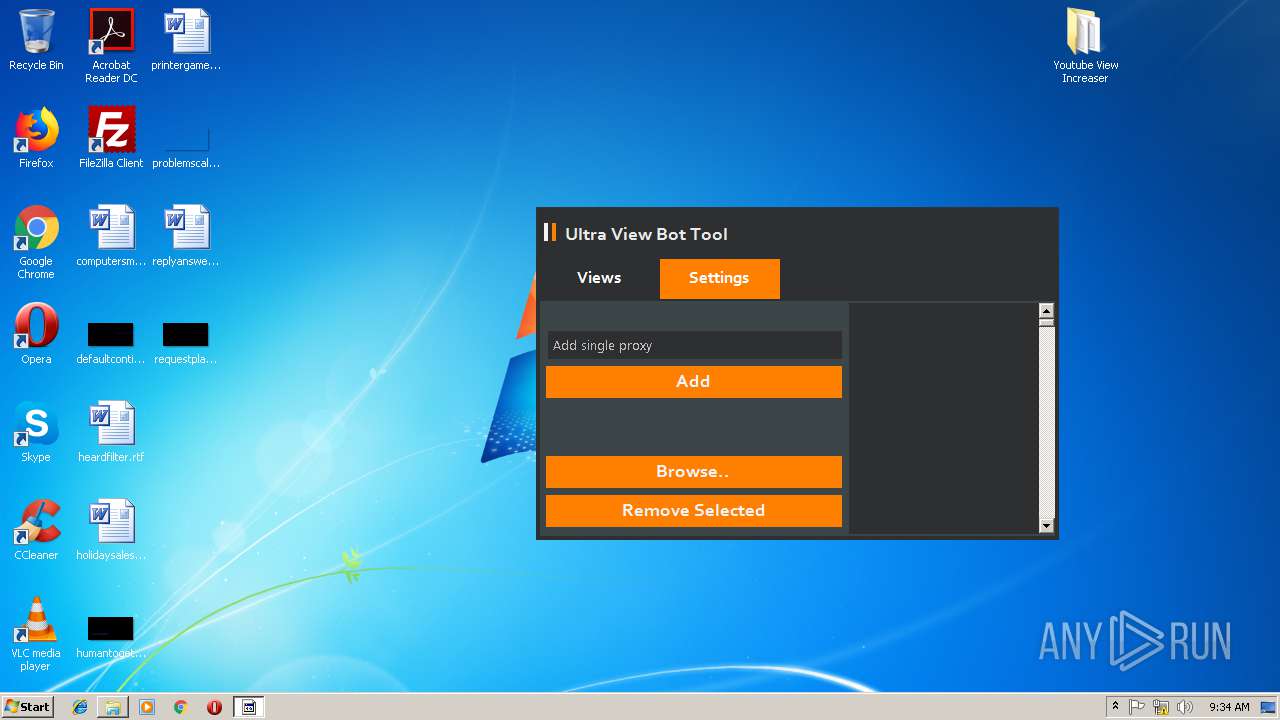
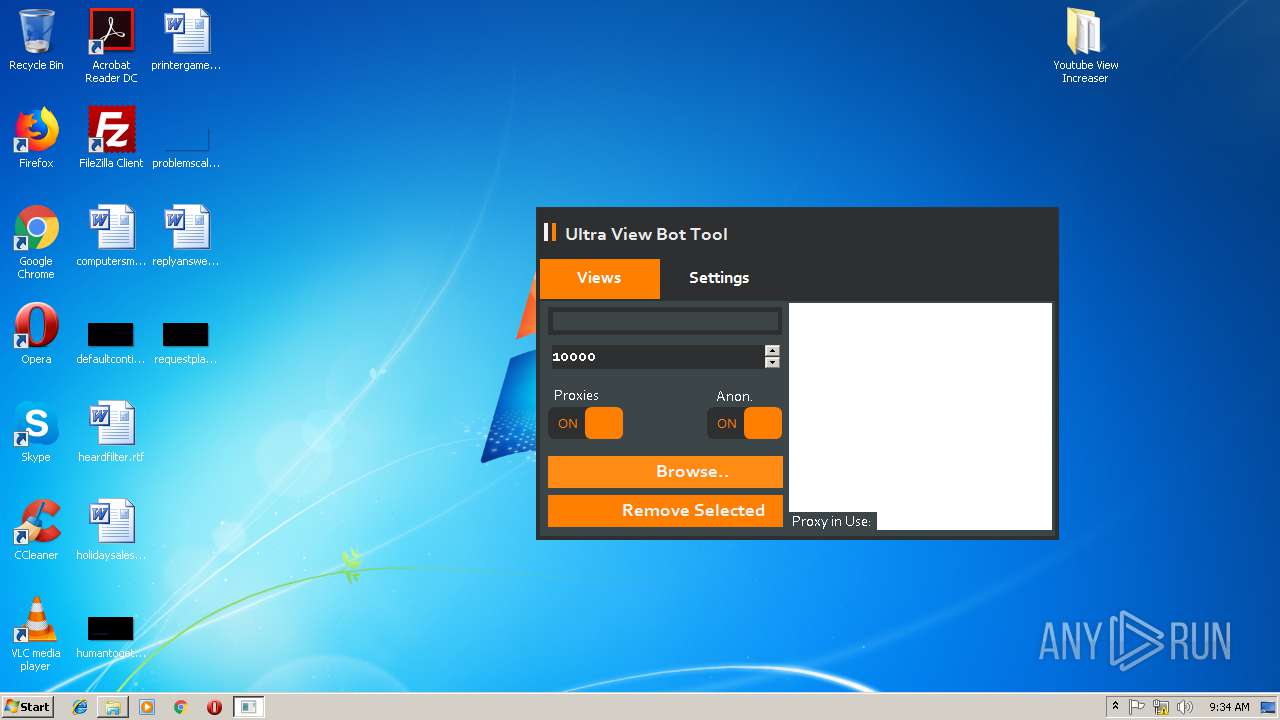
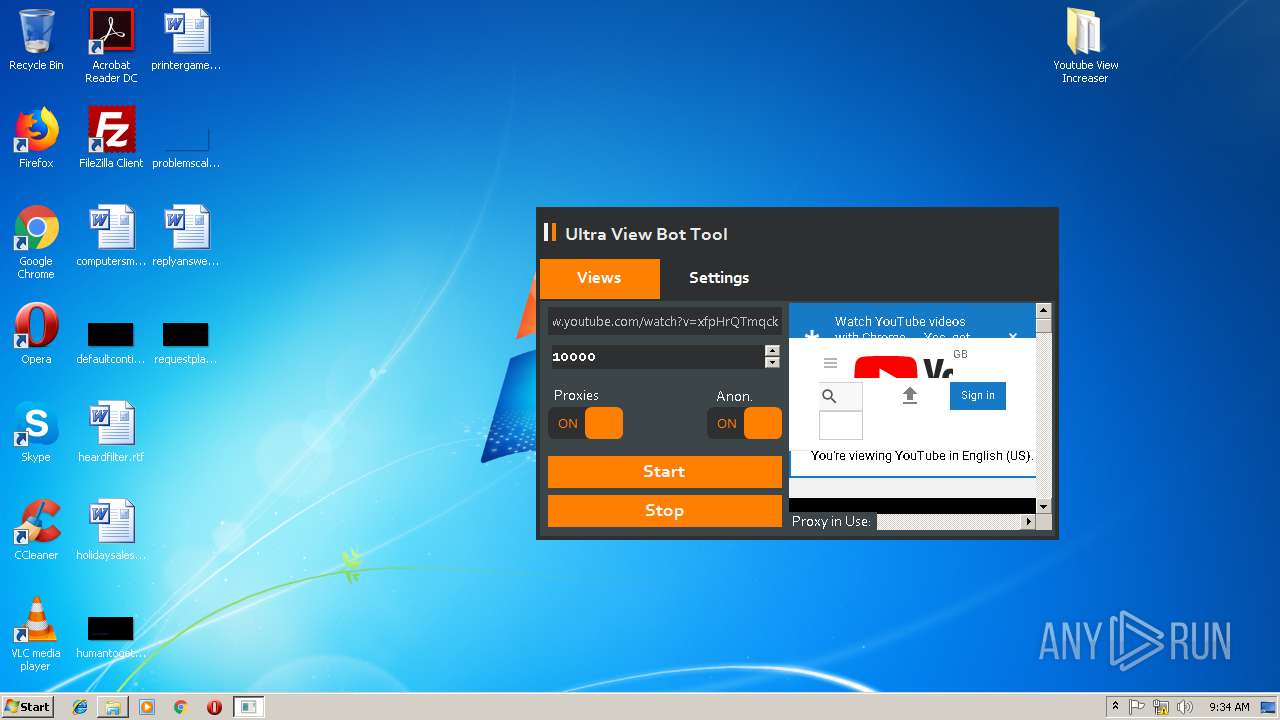
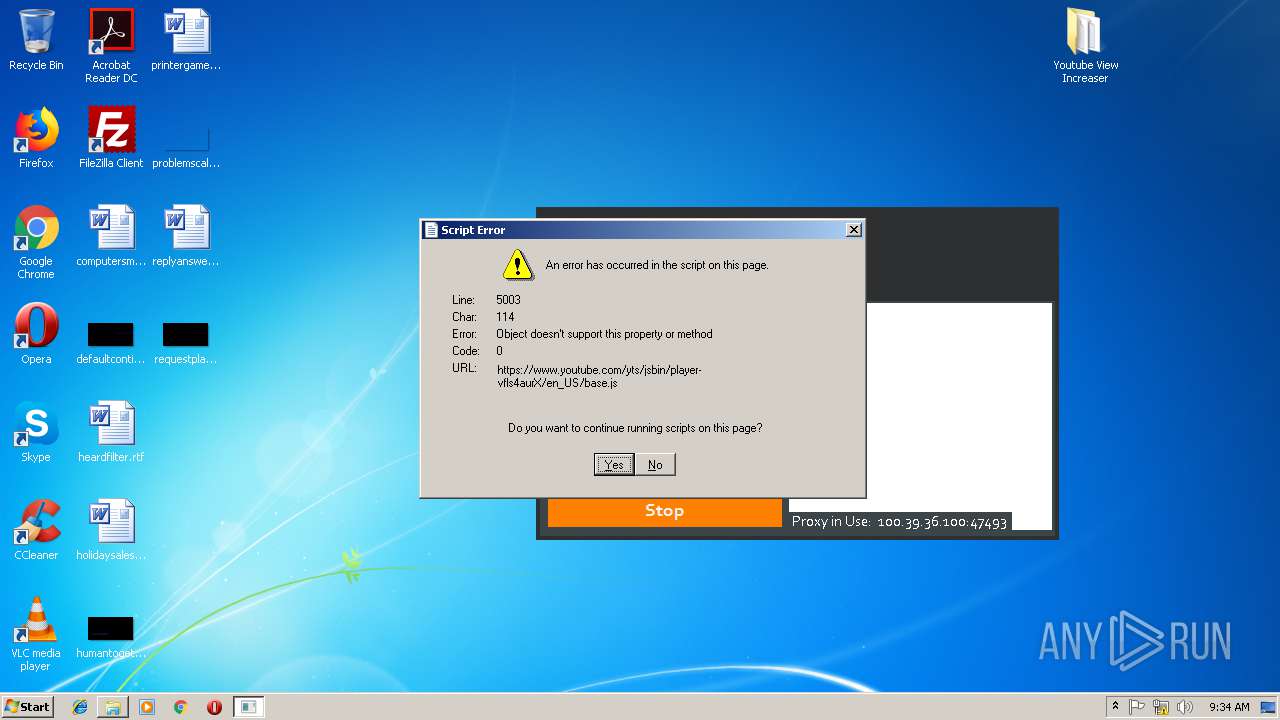
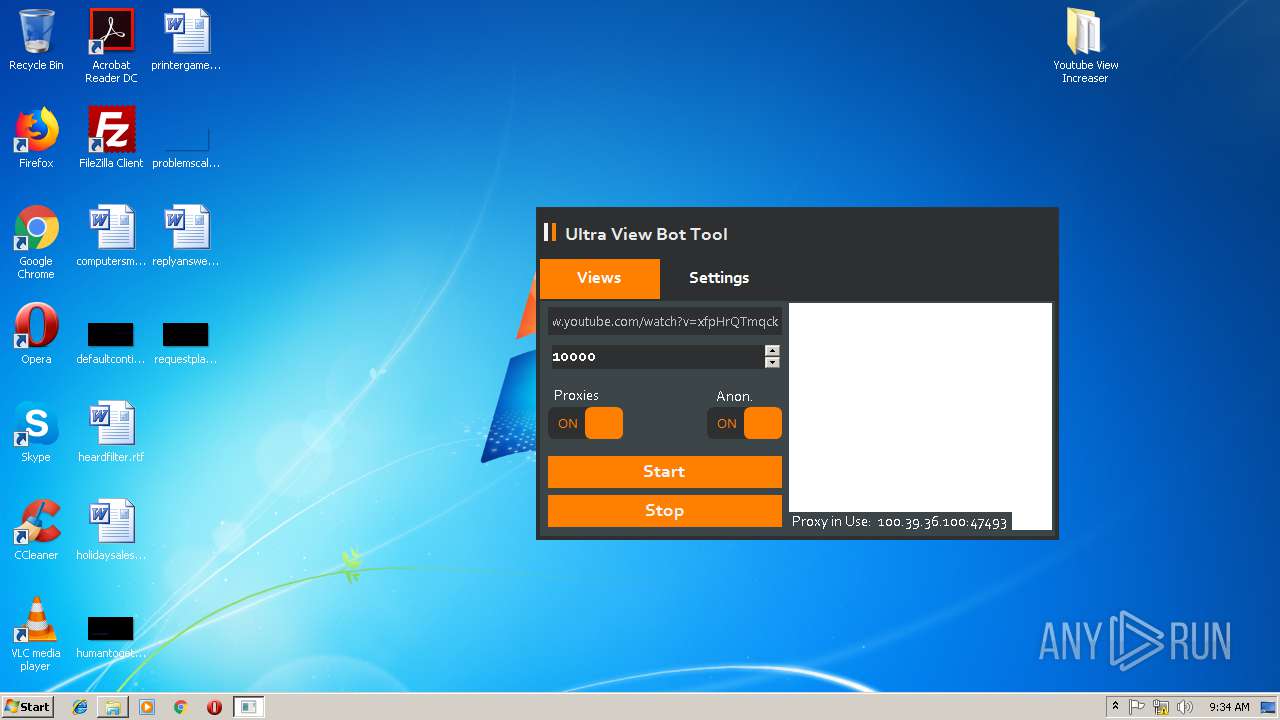
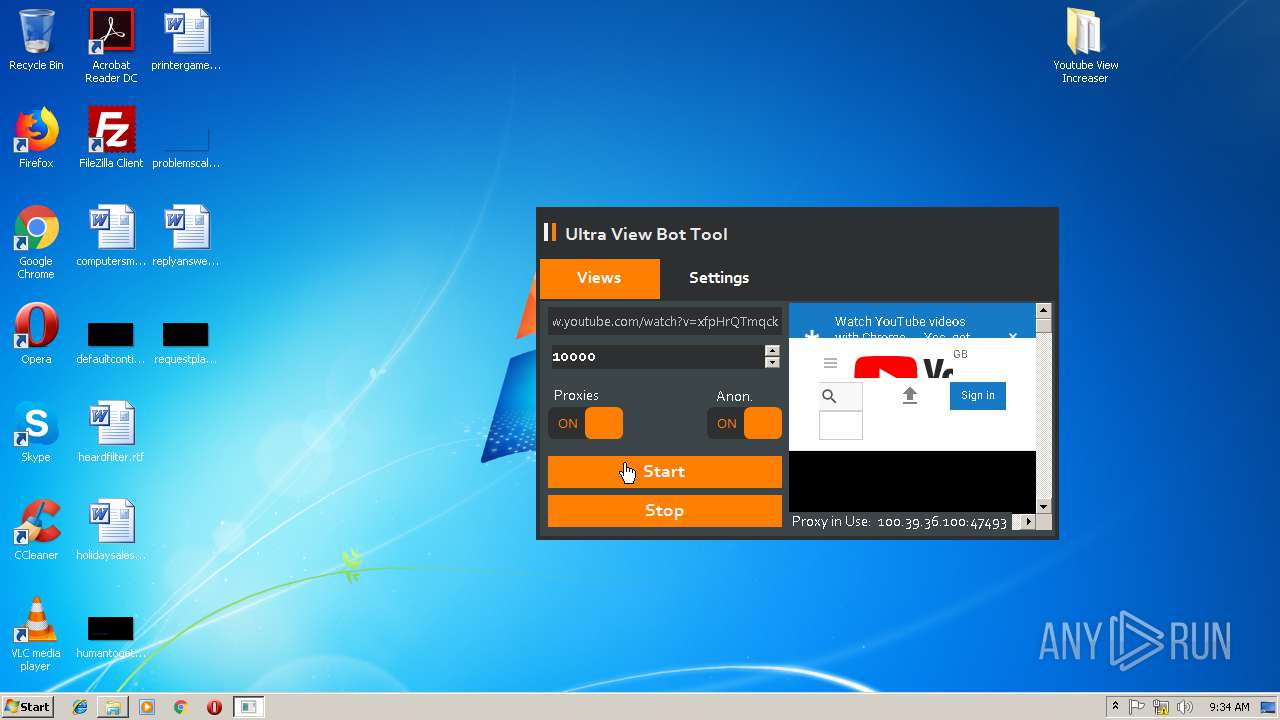
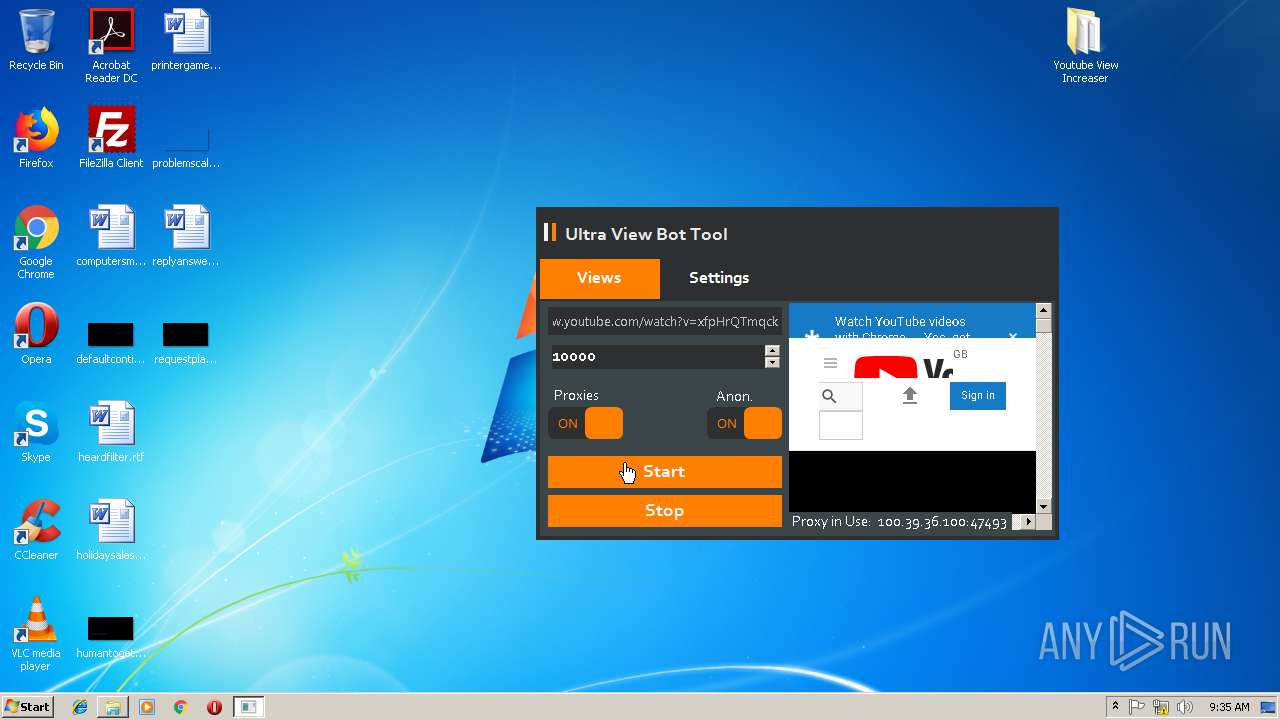
| File name: | Youtube View Increaser.zip |
| Full analysis: | https://app.any.run/tasks/47853415-8b3a-4123-95dc-2d5313141e9c |
| Verdict: | Malicious activity |
| Analysis date: | November 08, 2018, 09:33:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 2A86915434FC35BCCF6E16303F5FCEB9 |
| SHA1: | B664AD4CF6E3FF783F3BE219CC10788C6B0608EA |
| SHA256: | 5BD2F26B37BCA6B76C964929F86A9322B9CE2B4DF7D888821BB6293A9305B038 |
| SSDEEP: | 6144:HN0JpMa7JNJg4zCr2inJOH3lJJeTN/lpZfJv+Q:+R8uUTNH/v+Q |
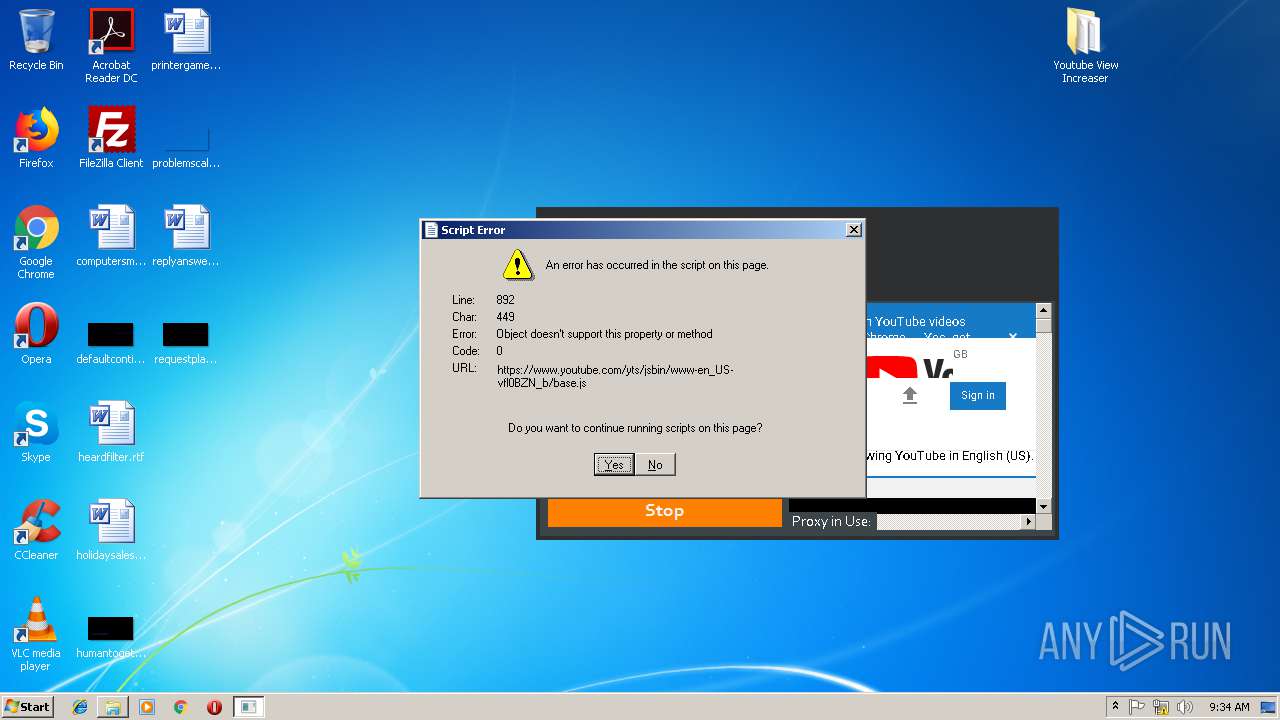
MALICIOUS
Changes settings of System certificates
- KVT.exe (PID: 1832)
SUSPICIOUS
Adds / modifies Windows certificates
- KVT.exe (PID: 1832)
Creates files in the user directory
- KVT.exe (PID: 1832)
Reads Internet Cache Settings
- KVT.exe (PID: 1832)
Reads internet explorer settings
- KVT.exe (PID: 1832)
INFO
Application launched itself
- chrome.exe (PID: 2384)
Reads settings of System Certificates
- KVT.exe (PID: 1832)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0808 |
| ZipCompression: | None |
| ZipModifyDate: | 2018:10:28 00:57:14 |
| ZipCRC: | 0xa4a033ec |
| ZipCompressedSize: | 593 |
| ZipUncompressedSize: | 593 |
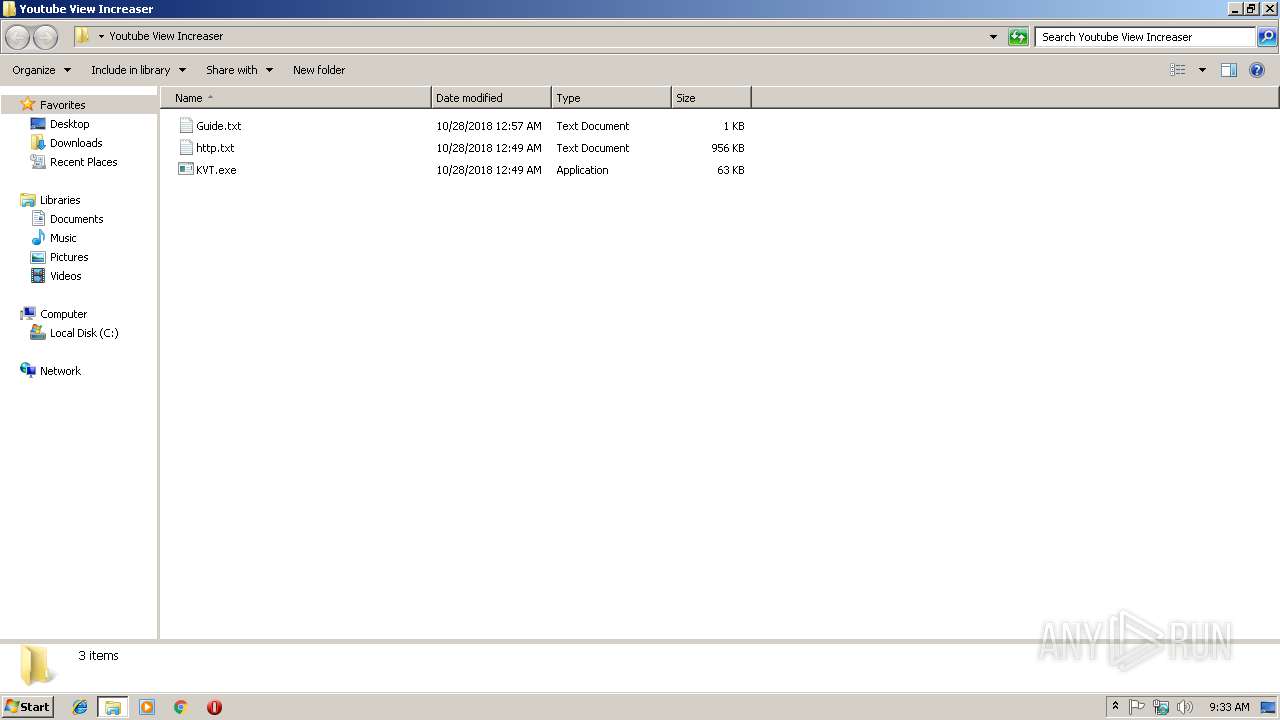
| ZipFileName: | Youtube View Increaser/Guide.txt |
Total processes
51
Monitored processes
14
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 756 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=920,9926936065791306617,8915650776833341515,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=00905C29E39BDEBC71CC3DE51A97829E --mojo-platform-channel-handle=3848 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 788 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=920,9926936065791306617,8915650776833341515,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=FCCCF6DDB1A1CCB45C0479333FF575A4 --mojo-platform-channel-handle=984 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 940 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=920,9926936065791306617,8915650776833341515,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=C1B83D37181FE478D29032E8E3D92639 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=C1B83D37181FE478D29032E8E3D92639 --renderer-client-id=8 --mojo-platform-channel-handle=4020 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1504 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=920,9926936065791306617,8915650776833341515,131072 --enable-features=PasswordImport --service-pipe-token=31D8783E894F7DE5101695CED070E1B9 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=31D8783E894F7DE5101695CED070E1B9 --renderer-client-id=5 --mojo-platform-channel-handle=1896 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
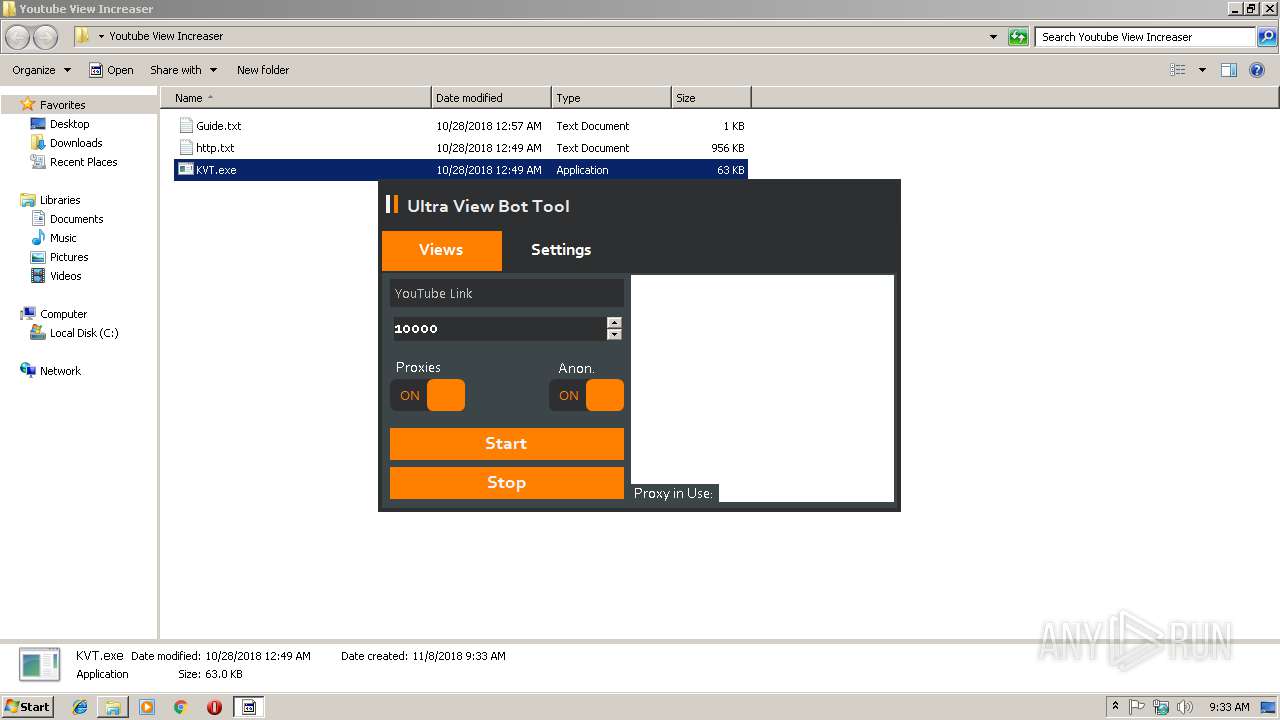
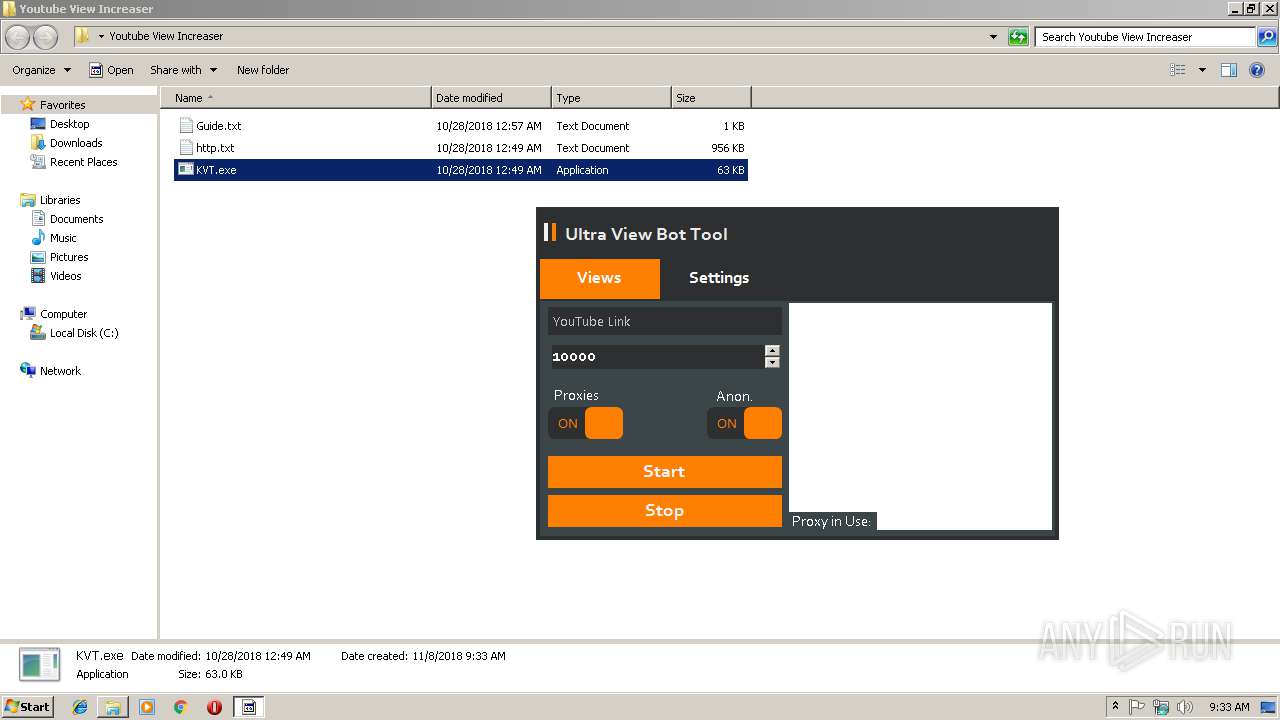
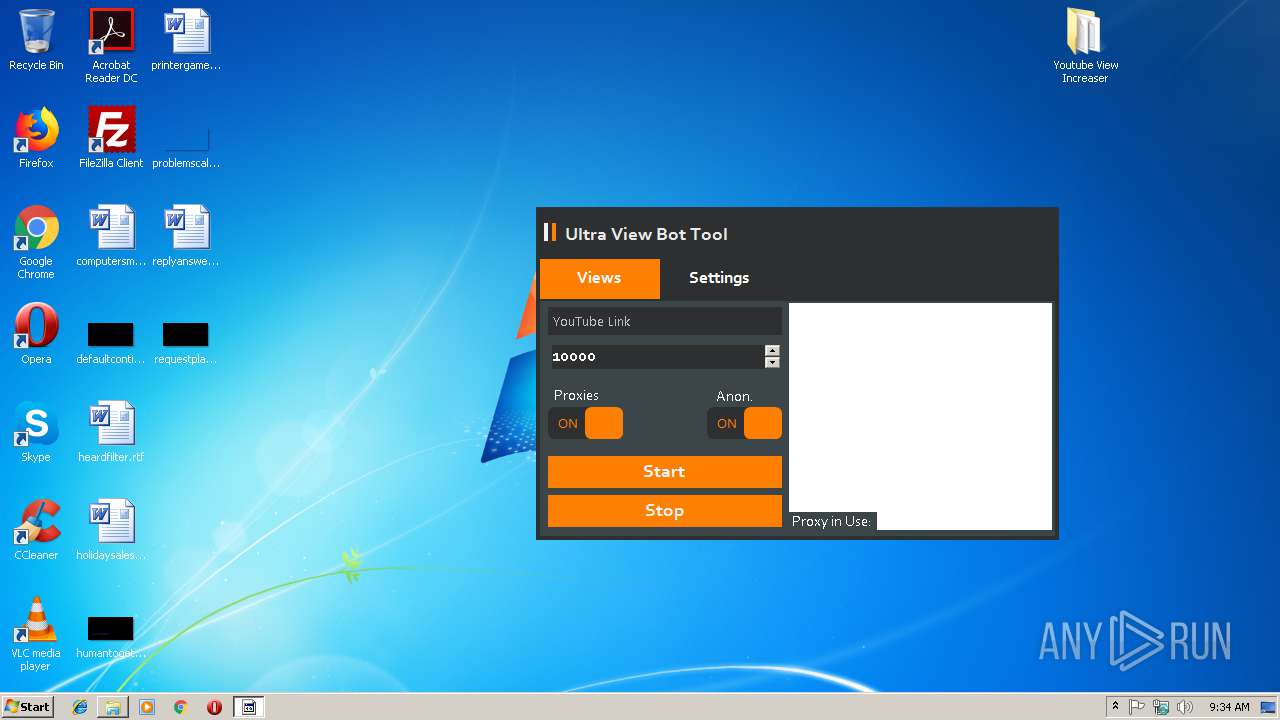
| 1832 | "C:\Users\admin\Desktop\Youtube View Increaser\KVT.exe" | C:\Users\admin\Desktop\Youtube View Increaser\KVT.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: KVT Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2032 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=920,9926936065791306617,8915650776833341515,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=7312D91A25FD5A0F6CE7EE77C4D6C3F1 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7312D91A25FD5A0F6CE7EE77C4D6C3F1 --renderer-client-id=6 --mojo-platform-channel-handle=3612 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2384 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2576 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2556 --on-initialized-event-handle=304 --parent-handle=308 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2992 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Youtube View Increaser.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3136 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=920,9926936065791306617,8915650776833341515,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=FD9AE6D64490CAD1395746491779FF93 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=FD9AE6D64490CAD1395746491779FF93 --renderer-client-id=10 --mojo-platform-channel-handle=3612 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
Total events
1 593
Read events
1 347
Write events
242
Delete events
4
Modification events
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Youtube View Increaser.zip | |||
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
0
Suspicious files
102
Text files
128
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2992.11898\Youtube View Increaser\Guide.txt | — | |
MD5:— | SHA256:— | |||
| 2992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2992.11898\Youtube View Increaser\http.txt | — | |
MD5:— | SHA256:— | |||
| 2992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2992.11898\Youtube View Increaser\KVT.exe | — | |
MD5:— | SHA256:— | |||
| 2384 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\795e4007-a42a-4769-8c23-1ac09e162112.tmp | — | |
MD5:— | SHA256:— | |||
| 2384 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2384 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2384 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ea814d5c-3e52-4e80-a0b1-9d319e1e9baf.tmp | — | |
MD5:— | SHA256:— | |||
| 2384 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Translate Ranker Model | binary | |
MD5:— | SHA256:— | |||
| 2384 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\CacheStorage\e6622492fa163609ddd4212f54512baa07929ed3\caecb3bd-7969-4305-84d6-3a376453ec73\index-dir\temp-index | — | |
MD5:— | SHA256:— | |||
| 2384 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
62
DNS requests
35
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2384 | chrome.exe | 172.217.168.3:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2384 | chrome.exe | 172.217.168.10:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
2384 | chrome.exe | 216.58.215.227:443 | www.google.de | Google Inc. | US | whitelisted |
2384 | chrome.exe | 172.217.168.78:443 | apis.google.com | Google Inc. | US | whitelisted |
2384 | chrome.exe | 172.217.168.68:443 | www.google.com | Google Inc. | US | whitelisted |
2384 | chrome.exe | 172.217.168.74:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2384 | chrome.exe | 172.217.168.14:443 | www.youtube.com | Google Inc. | US | whitelisted |
2384 | chrome.exe | 172.217.168.67:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2384 | chrome.exe | 172.217.168.1:443 | yt3.ggpht.com | Google Inc. | US | whitelisted |
2384 | chrome.exe | 172.217.168.86:443 | i.ytimg.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
www.google.de |
| whitelisted |
www.gstatic.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
www.google.com |
| malicious |
www.google.co.uk |
| whitelisted |
fonts.googleapis.com |
| whitelisted |