| File name: | Retrac_Launcher_1.0.8_x64_en-US.msi |
| Full analysis: | https://app.any.run/tasks/af5a983d-995b-496d-8a07-fc02ae22dff2 |
| Verdict: | Malicious activity |
| Analysis date: | July 13, 2024, 01:53:33 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: Retrac Launcher, Author: retrac, Keywords: Installer, Comments: This installer database contains the logic and data required to install Retrac Launcher., Template: x64;0, Revision Number: {E2FA1739-1182-4AE5-9A39-118B70EA0AA4}, Create Time/Date: Sun Jun 16 19:53:42 2024, Last Saved Time/Date: Sun Jun 16 19:53:42 2024, Number of Pages: 450, Number of Words: 2, Name of Creating Application: Windows Installer XML Toolset (3.11.2.4516), Security: 2 |
| MD5: | 299451386BEA3A4467A348F8389E19A1 |
| SHA1: | 9FB2A300AC905EE235BE90997239415C5F0BC1AC |
| SHA256: | 5BCA31F4A0116BC9220B06BA461B9E310C42087269FFD14A66646A650A4EE290 |
| SSDEEP: | 98304:hgGsYXfayBof9Z7IkScspAWVfls77vwR2Qh1xVOv2JcsT2ud3C6KVyIE4MRJPmoC:+NHEQZkdrIrtFU |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 1824)
- msiexec.exe (PID: 3232)
- MicrosoftEdgeWebview2Setup.exe (PID: 1296)
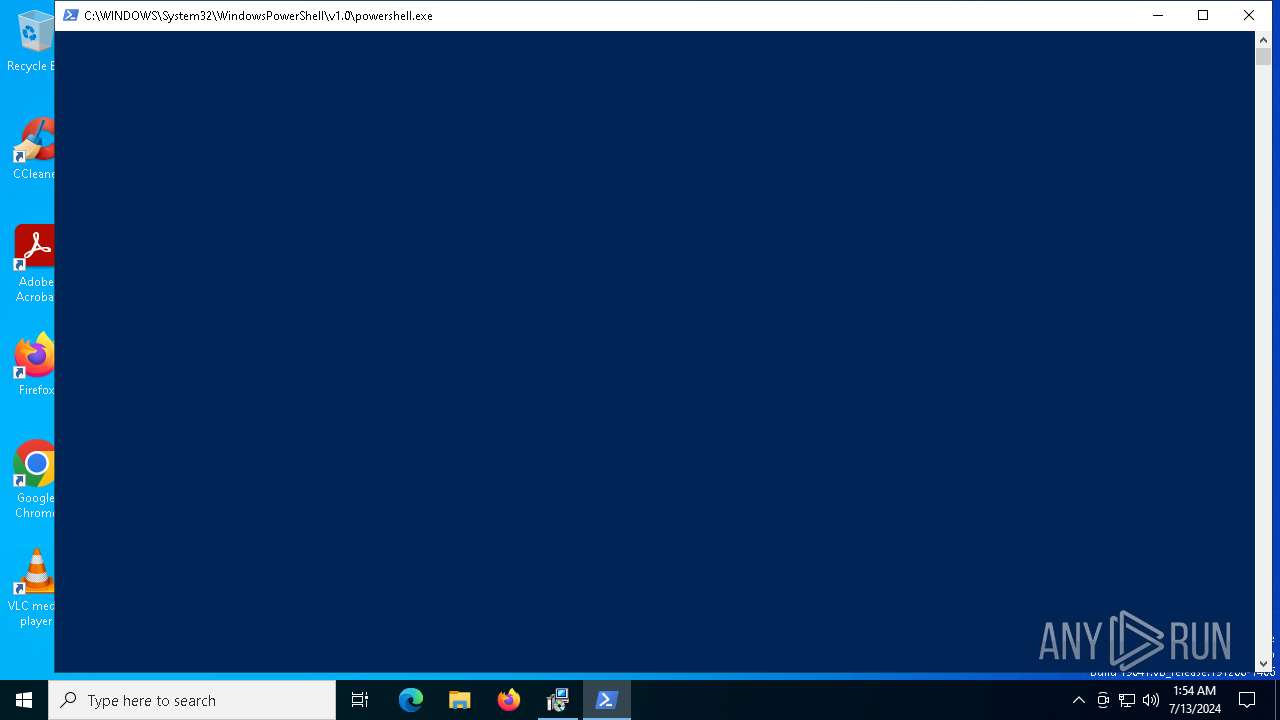
- powershell.exe (PID: 6528)
- MicrosoftEdgeUpdate.exe (PID: 2404)
Run PowerShell with an invisible window
- powershell.exe (PID: 6528)
Changes the autorun value in the registry
- MicrosoftEdgeUpdate.exe (PID: 2404)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 2080)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 3232)
Powershell scripting: start process
- msiexec.exe (PID: 3232)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 3232)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 3232)
Downloads file from URI
- powershell.exe (PID: 6528)
Request a resource from the Internet using PowerShell's cmdlet
- msiexec.exe (PID: 3232)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 6528)
Executable content was dropped or overwritten
- powershell.exe (PID: 6528)
- MicrosoftEdgeWebview2Setup.exe (PID: 1296)
- MicrosoftEdgeUpdate.exe (PID: 2404)
Process drops legitimate windows executable
- powershell.exe (PID: 6528)
- MicrosoftEdgeWebview2Setup.exe (PID: 1296)
- MicrosoftEdgeUpdate.exe (PID: 2404)
Starts a Microsoft application from unusual location
- MicrosoftEdgeWebview2Setup.exe (PID: 1296)
- MicrosoftEdgeUpdate.exe (PID: 2404)
Creates/Modifies COM task schedule object
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 7004)
- MicrosoftEdgeUpdate.exe (PID: 6724)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6808)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6752)
Starts itself from another location
- MicrosoftEdgeUpdate.exe (PID: 2404)
Reads security settings of Internet Explorer
- MicrosoftEdgeUpdate.exe (PID: 2404)
Reads the date of Windows installation
- MicrosoftEdgeUpdate.exe (PID: 2404)
INFO
Checks supported languages
- msiexec.exe (PID: 3232)
- msiexec.exe (PID: 3512)
- MicrosoftEdgeUpdate.exe (PID: 2404)
- MicrosoftEdgeWebview2Setup.exe (PID: 1296)
- MicrosoftEdgeUpdate.exe (PID: 6724)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 7004)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6808)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6752)
- MicrosoftEdgeUpdate.exe (PID: 7060)
- MicrosoftEdgeUpdate.exe (PID: 7084)
- MicrosoftEdgeUpdate.exe (PID: 4752)
Reads the computer name
- msiexec.exe (PID: 3232)
- msiexec.exe (PID: 3512)
- MicrosoftEdgeUpdate.exe (PID: 2404)
- MicrosoftEdgeUpdate.exe (PID: 6724)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 7004)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6808)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6752)
- MicrosoftEdgeUpdate.exe (PID: 7060)
- MicrosoftEdgeUpdate.exe (PID: 7084)
- MicrosoftEdgeUpdate.exe (PID: 4752)
Executable content was dropped or overwritten
- msiexec.exe (PID: 1824)
- msiexec.exe (PID: 3232)
Creates a software uninstall entry
- msiexec.exe (PID: 3232)
Checks proxy server information
- powershell.exe (PID: 6528)
- MicrosoftEdgeUpdate.exe (PID: 4752)
- MicrosoftEdgeUpdate.exe (PID: 7060)
Disables trace logs
- powershell.exe (PID: 6528)
Create files in a temporary directory
- MicrosoftEdgeWebview2Setup.exe (PID: 1296)
- MicrosoftEdgeUpdate.exe (PID: 2404)
Reads Environment values
- MicrosoftEdgeUpdate.exe (PID: 7060)
Process checks computer location settings
- MicrosoftEdgeUpdate.exe (PID: 2404)
Reads the software policy settings
- MicrosoftEdgeUpdate.exe (PID: 7060)
- MicrosoftEdgeUpdate.exe (PID: 4752)
Manual execution by a user
- Retrac Launcher.exe (PID: 7960)
- Retrac Launcher.exe (PID: 7832)
- Taskmgr.exe (PID: 8188)
- Taskmgr.exe (PID: 7288)
Creates files or folders in the user directory
- MicrosoftEdgeUpdate.exe (PID: 2404)
The executable file from the user directory is run by the Powershell process
- MicrosoftEdgeWebview2Setup.exe (PID: 1296)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | Retrac Launcher |
| Author: | retrac |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install Retrac Launcher. |
| Template: | x64;0 |
| RevisionNumber: | {E2FA1739-1182-4AE5-9A39-118B70EA0AA4} |
| CreateDate: | 2024:06:16 19:53:42 |
| ModifyDate: | 2024:06:16 19:53:42 |
| Pages: | 450 |
| Words: | 2 |
| Software: | Windows Installer XML Toolset (3.11.2.4516) |
| Security: | Read-only recommended |
Total processes
167
Monitored processes
24
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1272 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1296 | "C:\Users\admin\AppData\Local\Temp\MicrosoftEdgeWebview2Setup.exe" /silent /install | C:\Users\admin\AppData\Local\Temp\MicrosoftEdgeWebview2Setup.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Setup Version: 1.3.193.5 Modules
| |||||||||||||||
| 1824 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\Retrac_Launcher_1.0.8_x64_en-US.msi | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2080 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2404 | C:\Users\admin\AppData\Local\Temp\EU5268.tmp\MicrosoftEdgeUpdate.exe /silent /install "appguid={F3017226-FE2A-4295-8BDF-00C3A9A7E4C5}&appname=Microsoft%20Edge%20Webview2%20Runtime&needsadmin=prefers" | C:\Users\admin\AppData\Local\Temp\EU5268.tmp\MicrosoftEdgeUpdate.exe | MicrosoftEdgeWebview2Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Version: 1.3.193.5 Modules
| |||||||||||||||
| 2412 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3232 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3512 | C:\Windows\syswow64\MsiExec.exe -Embedding FBBAA6DA16424403DBE9DCFCA399D882 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4752 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" -Embedding | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Version: 1.3.193.5 Modules
| |||||||||||||||
| 6528 | powershell.exe -NoProfile -windowstyle hidden try { [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12 } catch {}; Invoke-WebRequest -Uri "https://go.microsoft.com/fwlink/p/?LinkId=2124703" -OutFile "$env:TEMP\MicrosoftEdgeWebview2Setup.exe" ; Start-Process -FilePath "$env:TEMP\MicrosoftEdgeWebview2Setup.exe" -ArgumentList ('/silent', '/install') -Wait | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
21 754
Read events
21 228
Write events
482
Delete events
44
Modification events
| (PID) Process: | (3232) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000103C1980C7D4DA01A00C0000080F0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3232) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 48000000000000004CA01B80C7D4DA01A00C0000080F0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3232) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000ACBE6080C7D4DA01A00C0000080F0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3232) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000ACBE6080C7D4DA01A00C0000080F0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3232) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 480000000000000083896580C7D4DA01A00C0000080F0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3232) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000EEEC6780C7D4DA01A00C0000080F0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3232) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (3232) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 48000000000000005A4AE680C7D4DA01A00C0000080F0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3232) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000A0ADE880C7D4DA01A00C0000940C0000E8030000010000000000000000000000A8017F32CF6A1542BFCCC0B10811145100000000000000000000000000000000 | |||
| (PID) Process: | (2080) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000000276ED80C7D4DA0120080000AC060000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
204
Suspicious files
12
Text files
7
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3232 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3232 | msiexec.exe | C:\WINDOWS\Installer\1d34fd.msi | — | |
MD5:— | SHA256:— | |||
| 3232 | msiexec.exe | C:\WINDOWS\Installer\1d34ff.msi | — | |
MD5:— | SHA256:— | |||
| 3232 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{327f01a8-6acf-4215-bfcc-c0b108111451}_OnDiskSnapshotProp | binary | |
MD5:55422731D3C8780A8AB1A6A21D7CD1FD | SHA256:1FCB9CD40FB514FCC25C24971CFA6F4263AD65237FE21E4D3BD27AFF1CD6433E | |||
| 3232 | msiexec.exe | C:\WINDOWS\Installer\MSI39DF.tmp | binary | |
MD5:287592AE3E85EAC426C04007DEE43174 | SHA256:A2C6461CD381DF5CDB9D59E82696C60265C442B5701BF2DF5E8900527BE8F596 | |||
| 3232 | msiexec.exe | C:\WINDOWS\Installer\inprogressinstallinfo.ipi | binary | |
MD5:DE0B98F6F605C823D014AC166A94EA77 | SHA256:7A68B586838C8CB94F88CDB06EDDCCC49704BC6A278F272373A6894AE12EF535 | |||
| 3232 | msiexec.exe | C:\WINDOWS\TEMP\~DF910B46EF34A81D1F.TMP | gmc | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 3232 | msiexec.exe | C:\WINDOWS\TEMP\~DFC8154C8A0FEFE631.TMP | binary | |
MD5:DE0B98F6F605C823D014AC166A94EA77 | SHA256:7A68B586838C8CB94F88CDB06EDDCCC49704BC6A278F272373A6894AE12EF535 | |||
| 1824 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIFD53.tmp | executable | |
MD5:4FDD16752561CF585FED1506914D73E0 | SHA256:AECD2D2FE766F6D439ACC2BBF1346930ECC535012CF5AD7B3273D2875237B7E7 | |||
| 3232 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:55422731D3C8780A8AB1A6A21D7CD1FD | SHA256:1FCB9CD40FB514FCC25C24971CFA6F4263AD65237FE21E4D3BD27AFF1CD6433E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
73
DNS requests
21
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
368 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
368 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3944 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6548 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6548 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6744 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.f.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/1de3d7f1-ffef-4e28-bcf3-c063e98e7191?P1=1721440451&P2=404&P3=2&P4=Ofx5p%2bRlLgyOrFFlmP3VahOyiBBGulfncCbvoG77WqhNESjp%2fmpWND73LM3x2IChey5vNlvlGEs3vI1v5LaBJg%3d%3d | unknown | — | — | whitelisted |
6744 | svchost.exe | GET | — | 199.232.210.172:80 | http://msedge.f.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/1de3d7f1-ffef-4e28-bcf3-c063e98e7191?P1=1721440451&P2=404&P3=2&P4=Ofx5p%2bRlLgyOrFFlmP3VahOyiBBGulfncCbvoG77WqhNESjp%2fmpWND73LM3x2IChey5vNlvlGEs3vI1v5LaBJg%3d%3d | unknown | — | — | whitelisted |
1280 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
368 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2124 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2448 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
368 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
368 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
368 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
2448 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3944 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
msedge.sf.dl.delivery.mp.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6744 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |