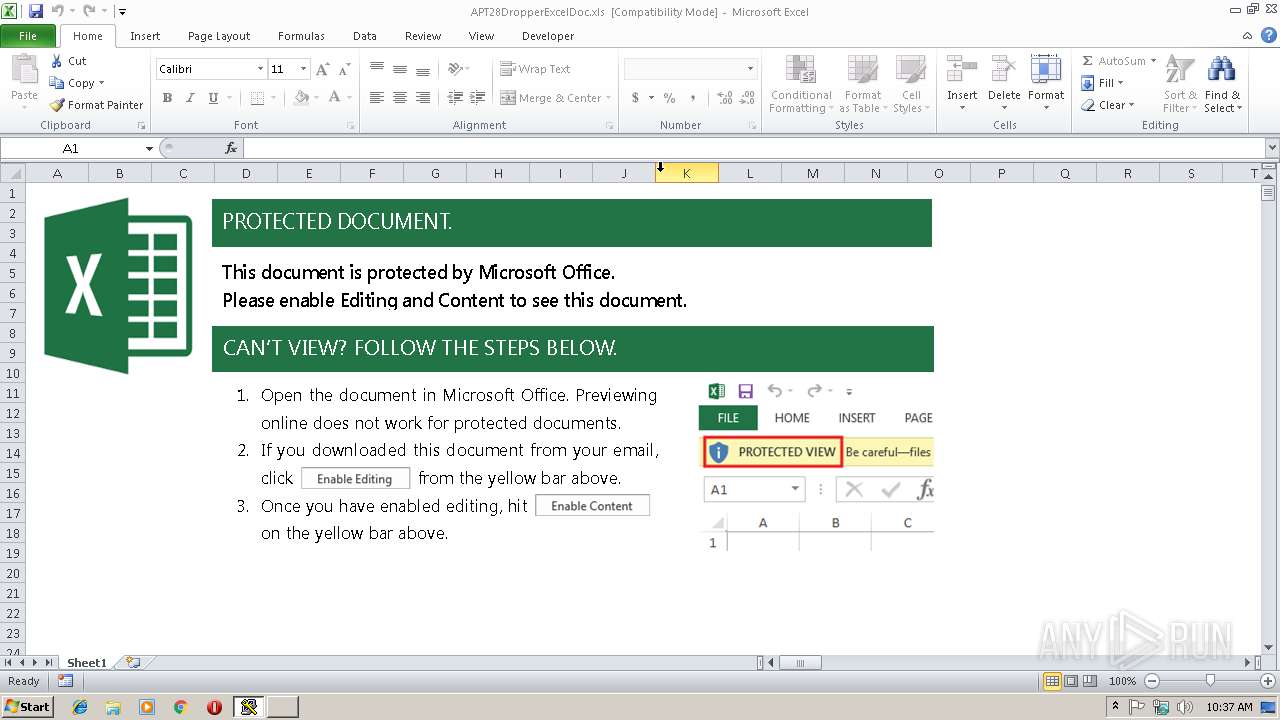
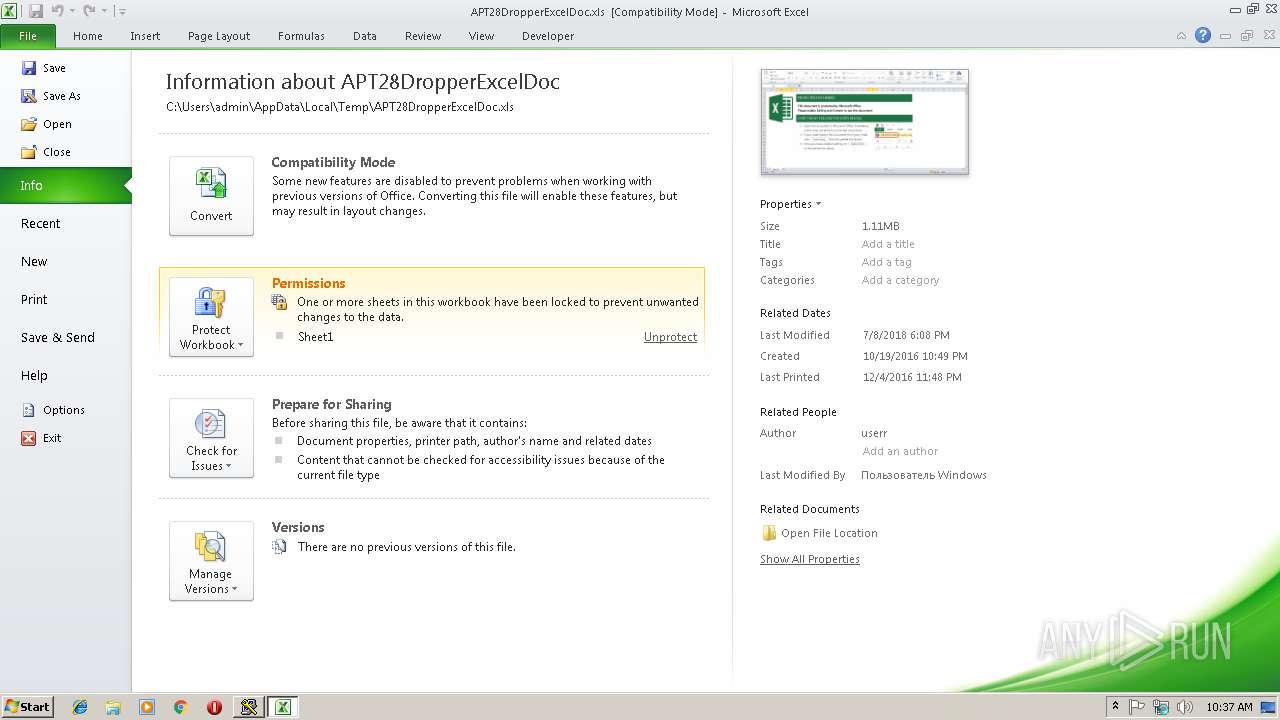
| File name: | APT28DropperExcelDoc.xls |
| Full analysis: | https://app.any.run/tasks/e36170c7-160e-4daf-b6cc-0eae22280443 |
| Verdict: | Malicious activity |
| Analysis date: | January 11, 2019, 10:36:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1251, Author: userr, Last Saved By: Windows, Name of Creating Application: Microsoft Excel, Last Printed: Sun Dec 4 23:48:47 2016, Create Time/Date: Wed Oct 19 23:49:03 2016, Last Saved Time/Date: Sun Jul 8 19:08:38 2018, Security: 0 |
| MD5: | 5DEBB3535CBA6615526C64E44D0F5E2B |
| SHA1: | ABAA744D9504C7F23A237F8220AC6A441016D518 |
| SHA256: | 5BAC7A020F173D6C35F73D76CD3745A36564DBB3DD32F2D5FC5021C353E76A54 |
| SSDEEP: | 12288:/bkdb1vJu/xtIIcnIE9A3HfOoV+4qF2KhaLZA6H/EHagqNC9:TkdbVJupvSmHfOoaF2KhaLZTx89 |
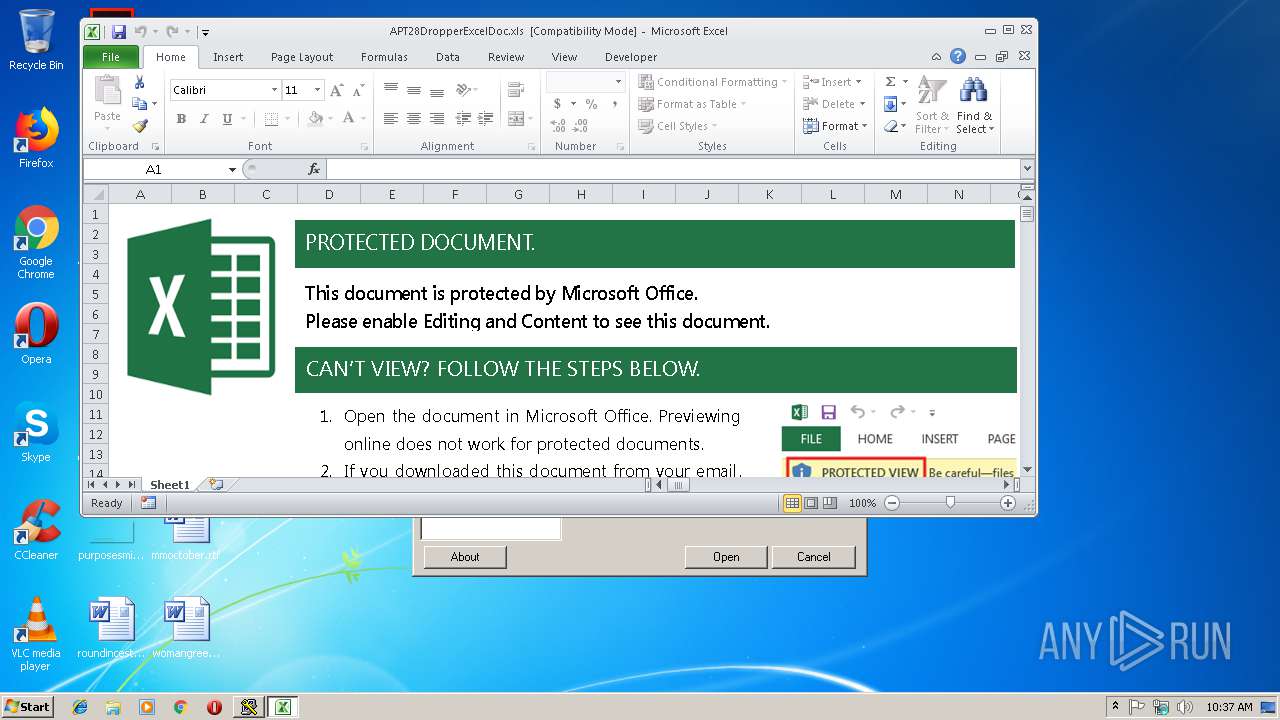
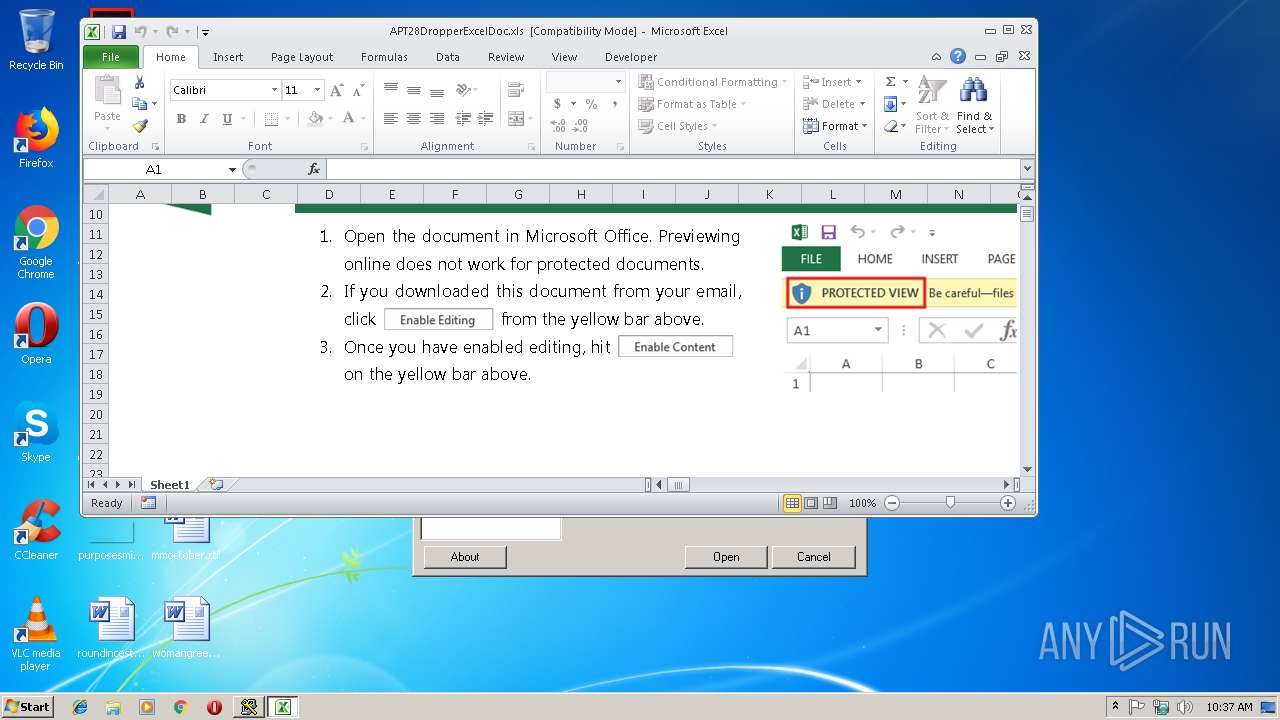
MALICIOUS
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 3000)
Application was dropped or rewritten from another process
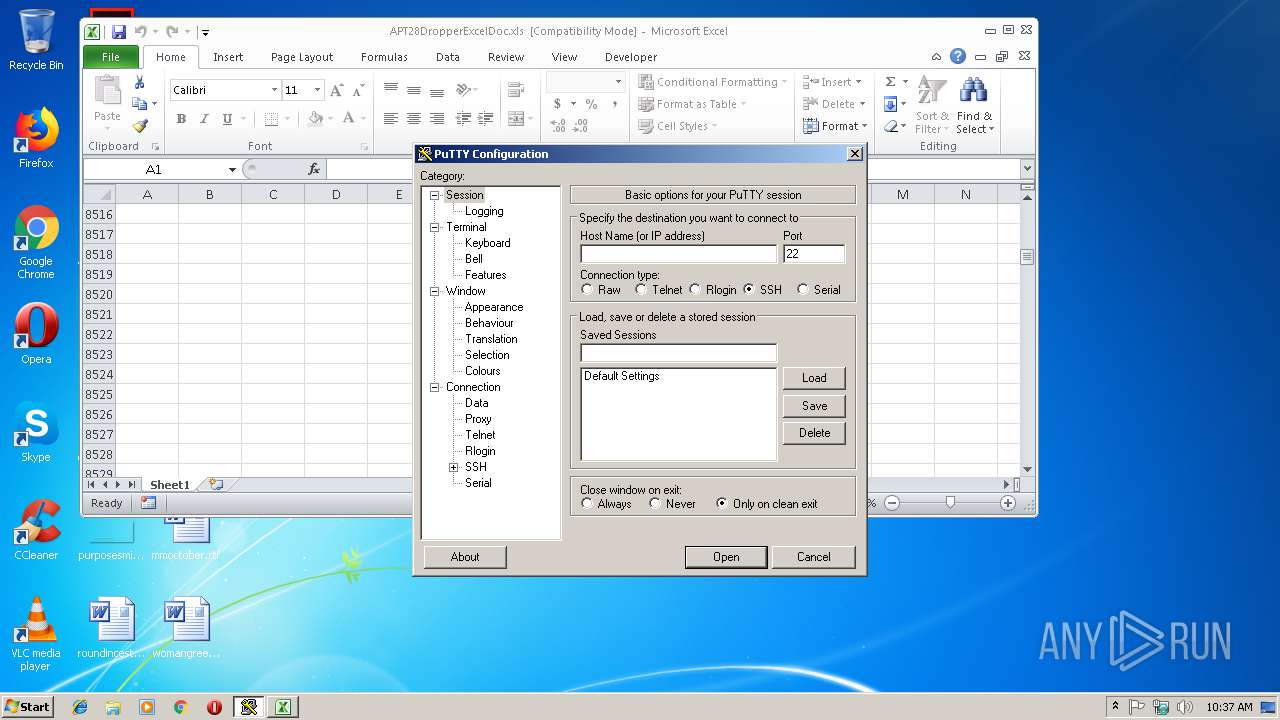
- Z4U8K1S8.exe (PID: 2920)
Starts CertUtil for decode files
- EXCEL.EXE (PID: 3000)
SUSPICIOUS
Creates files in the user directory
- certutil.exe (PID: 3500)
Executable content was dropped or overwritten
- certutil.exe (PID: 3500)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 3000)
Creates files in the user directory
- EXCEL.EXE (PID: 3000)
Dropped object may contain Bitcoin addresses
- EXCEL.EXE (PID: 3000)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (28.1) |
|---|---|---|
| .xls | | | Microsoft Excel sheet (26.4) |
| .xls | | | Microsoft Excel sheet (alternate) (21.5) |
| .doc | | | Microsoft Word document (old ver.) (16.7) |
EXIF
FlashPix
| Title: | - |
|---|---|
| Subject: | - |
| Keywords: | - |
| Template: | Normal |
| RevisionNumber: | 1 |
| TotalEditTime: | - |
| Pages: | 1 |
| Words: | 18 |
| Characters: | 106 |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 123 |
| Author: | userr |
| LastModifiedBy: | Пользователь Windows |
| Software: | Microsoft Excel |
| LastPrinted: | 2016:12:04 23:48:47 |
| CreateDate: | 2016:10:19 22:49:03 |
| ModifyDate: | 2018:07:08 18:08:38 |
| Security: | None |
| CodePage: | Unicode (UTF-8) |
| Company: | - |
| AppVersion: | 15 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | Sheet1 |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 40 |
| CompObjUserType: | Hoja de calculo de Microsoft Excel 2003 |
Total processes
34
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2920 | C:\Users\admin\AppData\Roaming\Microsoft\AddIns\Z4U8K1S8.exe | C:\Users\admin\AppData\Roaming\Microsoft\AddIns\Z4U8K1S8.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Simon Tatham Integrity Level: MEDIUM Description: SSH, Telnet and Rlogin client Exit code: 0 Version: Release 0.67 Modules
| |||||||||||||||
| 3000 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3500 | certutil -decode C:\Users\admin\AppData\Roaming\Microsoft\AddIns\T1U3H6N7.txt C:\Users\admin\AppData\Roaming\Microsoft\AddIns\Z4U8K1S8.exe | C:\Windows\system32\certutil.exe | EXCEL.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CertUtil.exe Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
660
Read events
622
Write events
26
Delete events
12
Modification events
| (PID) Process: | (3000) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | hh% |
Value: 68682500B80B0000010000000000000000000000 | |||
| (PID) Process: | (3000) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3000) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3000) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel |
| Operation: | write | Name: | MTTT |
Value: B80B000048285D9699A9D40100000000 | |||
| (PID) Process: | (3000) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete value | Name: | hh% |
Value: 68682500B80B0000010000000000000000000000 | |||
| (PID) Process: | (3000) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (3000) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (3000) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3000) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3000) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\DocumentRecovery\19930F |
| Operation: | write | Name: | 19930F |
Value: 04000000B80B00003A00000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C0041005000540032003800440072006F00700070006500720045007800630065006C0044006F0063002E0078006C007300000000002200000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C000100000000000000F029E49799A9D4010F9319000F93190000000000AC020000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
1
Suspicious files
1
Text files
1
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3000 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR8C38.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3000 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF8C39CF4968113A83.TMP | — | |
MD5:— | SHA256:— | |||
| 3000 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF23C695791E2D4A0F.TMP | — | |
MD5:— | SHA256:— | |||
| 3000 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\5C9AAAEE.emf | emf | |
MD5:— | SHA256:— | |||
| 3000 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\AddIns\T1U3H6N7.txt | text | |
MD5:— | SHA256:— | |||
| 3000 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\5338217.emf | emf | |
MD5:— | SHA256:— | |||
| 3000 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\APT28DropperExcelDoc.xls | document | |
MD5:— | SHA256:— | |||
| 3500 | certutil.exe | C:\Users\admin\AppData\Roaming\Microsoft\AddIns\Z4U8K1S8.exe | executable | |
MD5:BA78410702F0CC8453DA1AFBB2A8B670 | SHA256:9F9E74241D59ECCFE7040BFDCBBCEACB374EDA397CC53A4197B59E4F6F380A91 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report