| File name: | ef274d62fd8b447b68f031a13500e37fe991a6f0bec09b731e936769917076d4.zip |
| Full analysis: | https://app.any.run/tasks/2758b169-6ac5-495f-9293-f5c3139e3e97 |
| Verdict: | Malicious activity |
| Analysis date: | March 28, 2024, 17:02:24 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| MIME: | application/zip |
| File info: | Zip archive data, at least v4.5 to extract, compression method=deflate |
| MD5: | 648C5A29F00EB3CEE1E6844A2CBF3675 |
| SHA1: | 39E2ADBC4D897EA200B0B5F76090271929C22F12 |
| SHA256: | 5BA303549B6FC5497F40D607E83C9CB7DA2627F568E02DA8EDEF6C02EE924464 |
| SSDEEP: | 384:N6KQvSZXWNGT3ORBXpyvUg068A2gDPB3m95b4UdzJQCKq81uwyuoVT:NlQvOGNEyXpKfX2gDZ3sd7KqYfET |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
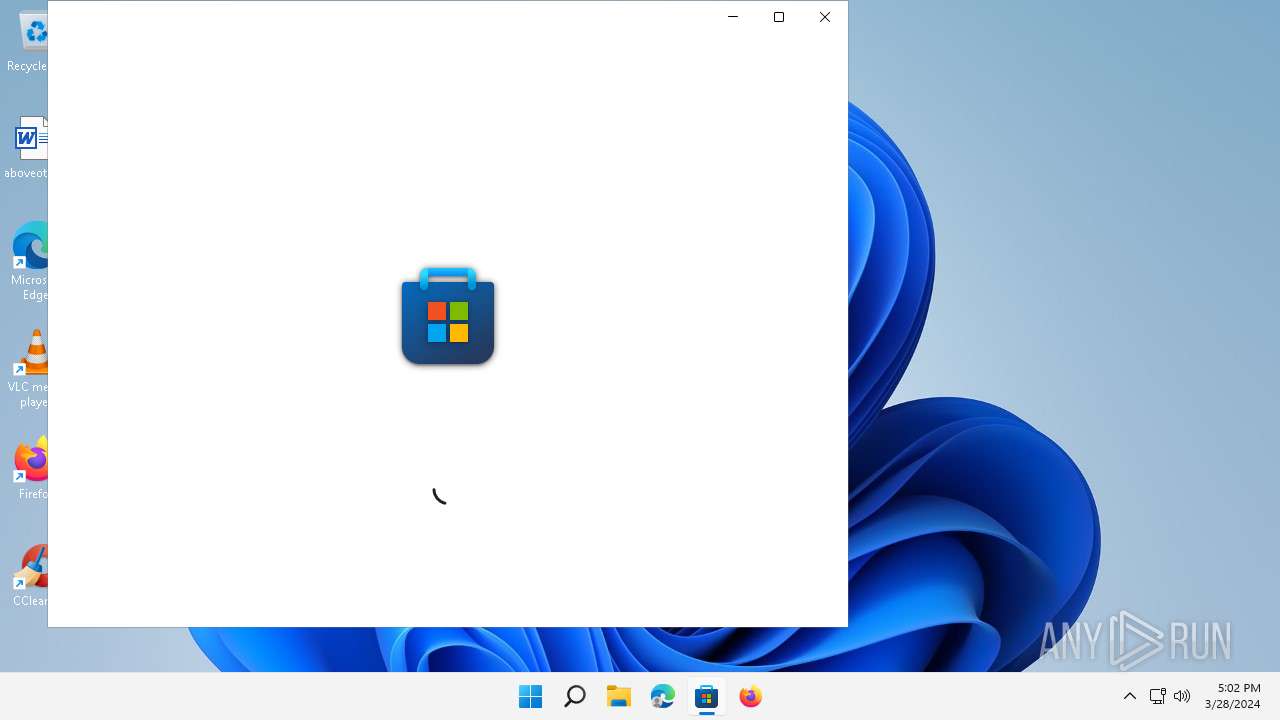
- WinStore.App.exe (PID: 1152)
Reads the Internet Settings
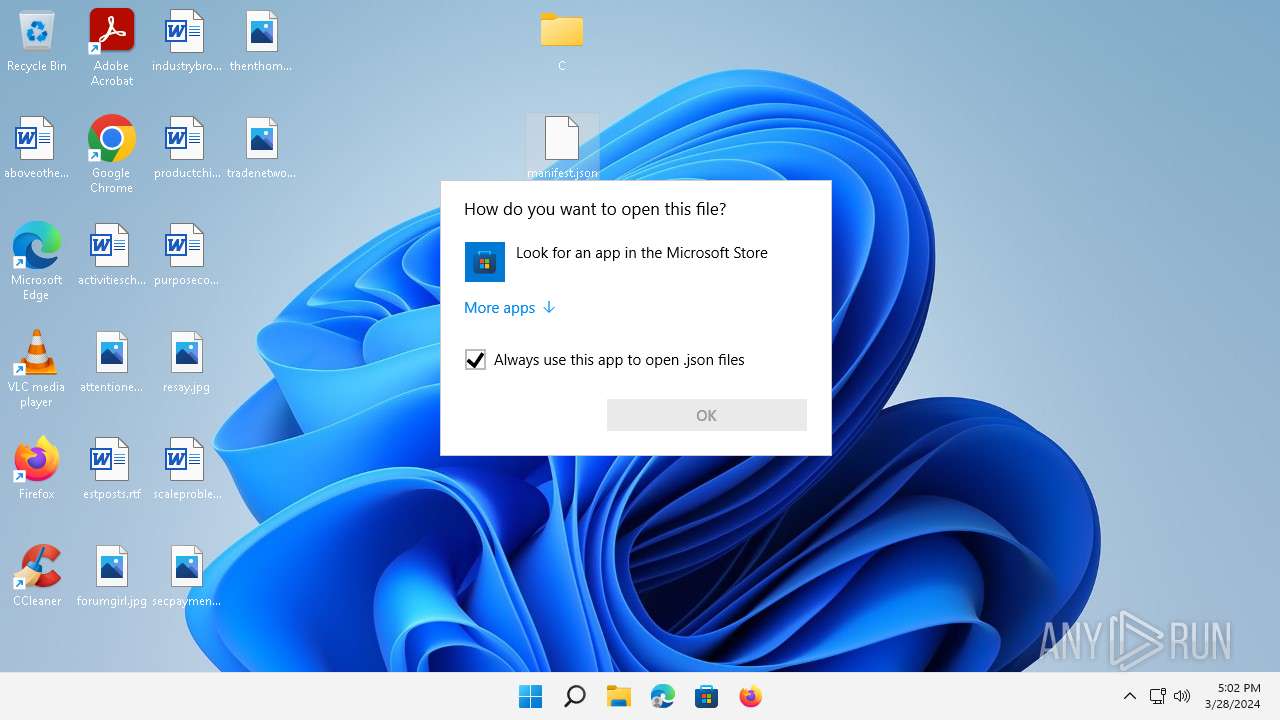
- OpenWith.exe (PID: 3892)
- WinStore.App.exe (PID: 1152)
Checks Windows Trust Settings
- WinStore.App.exe (PID: 1152)
INFO
Reads the computer name
- WinStore.App.exe (PID: 1152)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 3892)
Checks supported languages
- WinStore.App.exe (PID: 1152)
Reads product name
- WinStore.App.exe (PID: 1152)
Checks proxy server information
- WinStore.App.exe (PID: 1152)
Reads the machine GUID from the registry
- WinStore.App.exe (PID: 1152)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 3892)
Reads Environment values
- WinStore.App.exe (PID: 1152)
Reads the software policy settings
- WinStore.App.exe (PID: 1152)
Creates files or folders in the user directory
- WinStore.App.exe (PID: 1152)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0801 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0xcd0d1edd |
| ZipCompressedSize: | 15292 |
| ZipUncompressedSize: | 16426 |
| ZipFileName: | C/ProgramData/Sentinel/AFUCache/ef274d62fd8b447b68f031a13500e37fe991a6f0bec09b731e936769917076d4 |
Total processes
112
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1152 | "C:\Program Files\WindowsApps\Microsoft.WindowsStore_22205.1401.13.0_x64__8wekyb3d8bbwe\WinStore.App.exe" -ServerName:App.AppXc75wvwned5vhz4xyxxecvgdjhdkgsdza.mca | C:\Program Files\WindowsApps\Microsoft.WindowsStore_22205.1401.13.0_x64__8wekyb3d8bbwe\WinStore.App.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Store Version: 0.0.0.0 Modules
| |||||||||||||||
| 2388 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\ef274d62fd8b447b68f031a13500e37fe991a6f0bec09b731e936769917076d4.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3016 | C:\Windows\system32\ApplicationFrameHost.exe -Embedding | C:\Windows\System32\ApplicationFrameHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Application Frame Host Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3892 | C:\Windows\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 610
Read events
13 513
Write events
61
Delete events
36
Modification events
| (PID) Process: | (2388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | VerInfo |
Value: 005B0500F95763B93181DA01 | |||
| (PID) Process: | (2388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\ef274d62fd8b447b68f031a13500e37fe991a6f0bec09b731e936769917076d4.zip | |||
| (PID) Process: | (2388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF82000000820000004204000065020000 | |||
Executable files
1
Suspicious files
5
Text files
12
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2388 | WinRAR.exe | C:\USERS\ADMIN\APPDATA\ROAMING\WINRAR\VERSION.DAT | binary | |
MD5:— | SHA256:— | |||
| 2388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2388.33957\C\ProgramData\Sentinel\AFUCache\ef274d62fd8b447b68f031a13500e37fe991a6f0bec09b731e936769917076d4 | document | |
MD5:— | SHA256:— | |||
| 2388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2388.33957\manifest.json | text | |
MD5:— | SHA256:— | |||
| 1152 | WinStore.App.exe | C:\USERS\ADMIN\APPDATA\LOCAL\PACKAGES\MICROSOFT.WINDOWSSTORE_8WEKYB3D8BBWE\LOCALCACHE\PERUSERCACHE_0\INDEX | binary | |
MD5:— | SHA256:— | |||
| 1152 | WinStore.App.exe | C:\Users\admin\AppData\Local\Packages\microsoft.windowsstore_8wekyb3d8bbwe\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:— | SHA256:— | |||
| 1152 | WinStore.App.exe | C:\Users\admin\AppData\Local\Packages\microsoft.windowsstore_8wekyb3d8bbwe\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:— | SHA256:— | |||
| 1152 | WinStore.App.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.WindowsStore_8wekyb3d8bbwe\LocalCache\perUserCache_0\a40e07e9-199d-4183-9b50-46c63c780add | binary | |
MD5:— | SHA256:— | |||
| 1152 | WinStore.App.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.WindowsStore_8wekyb3d8bbwe\LocalCache\perUserCache_0\32d2b925-f82f-4940-9dea-2219c864c9f2 | binary | |
MD5:— | SHA256:— | |||
| 1152 | WinStore.App.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.WindowsStore_8wekyb3d8bbwe\LocalCache\perUserCache_0\21c7e93d-b387-45e4-b24c-84a09cca015d | text | |
MD5:— | SHA256:— | |||
| 1152 | WinStore.App.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.WindowsStore_8wekyb3d8bbwe\LocalCache\perUserCache_0\934c2426-30d5-4f1f-a6d6-7d07daae1a20 | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
24
DNS requests
6
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1412 | svchost.exe | GET | 200 | 2.21.20.150:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | unknown |
3752 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
1152 | WinStore.App.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
3752 | svchost.exe | GET | 200 | 184.24.77.199:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?69418a771e6f34c6 | unknown | — | — | unknown |
1152 | WinStore.App.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
1152 | WinStore.App.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1412 | svchost.exe | 2.21.20.140:80 | — | Akamai International B.V. | DE | unknown |
5944 | svchost.exe | 23.35.236.109:443 | — | AKAMAI-AS | DE | unknown |
4588 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1412 | svchost.exe | 2.21.20.150:80 | — | Akamai International B.V. | DE | unknown |
3752 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
3752 | svchost.exe | 184.24.77.199:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3752 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1152 | WinStore.App.exe | 23.218.209.198:443 | storeedgefd.dsx.mp.microsoft.com | AKAMAI-AS | DE | unknown |
1152 | WinStore.App.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
storeedgefd.dsx.mp.microsoft.com |
| whitelisted |
store-images.s-microsoft.com |
| whitelisted |
sparkcdnwus2.azureedge.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1412 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |