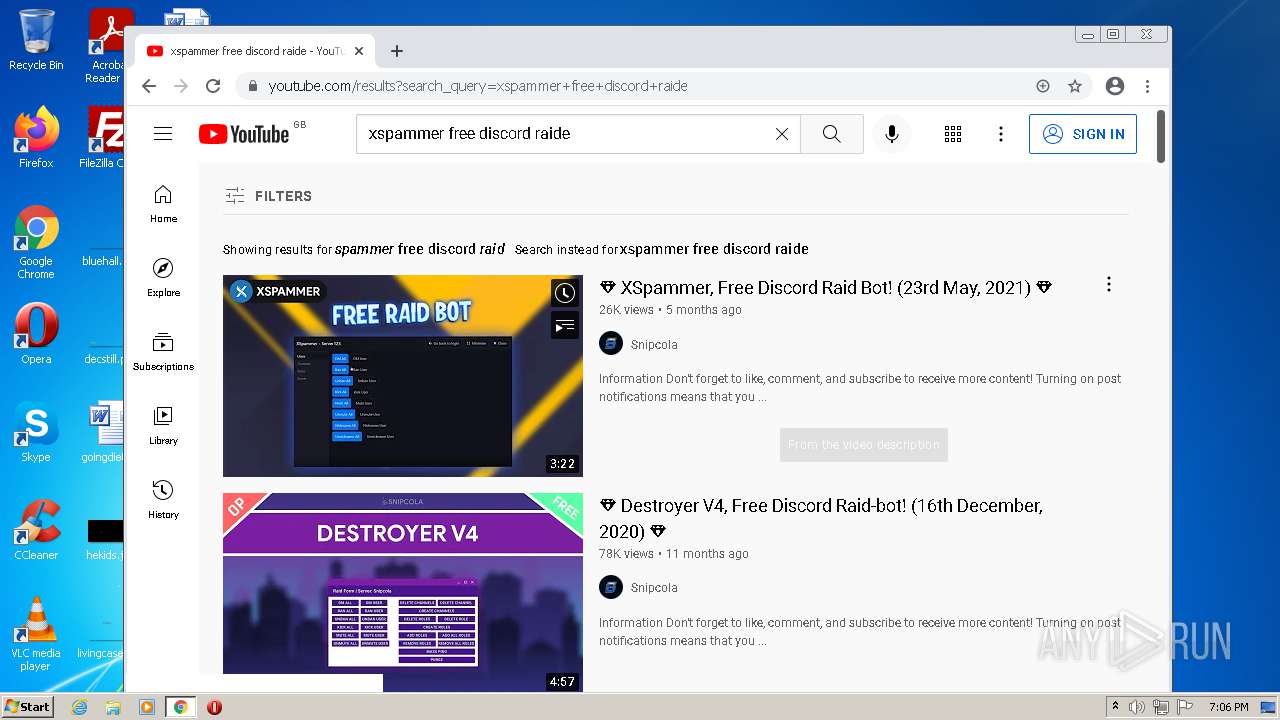
| URL: | https://linkvertise.download/download/73936/xspammer/umXwadTfxHNIvB7DtxMGHXIUa3qEJXhT |
| Full analysis: | https://app.any.run/tasks/7ff857c7-09b2-4d53-b141-e7bf248e6422 |
| Verdict: | Malicious activity |
| Analysis date: | November 18, 2021, 19:03:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 2F9B0DD3DE3E2D4E9EDA9B0C18BEA5FA |
| SHA1: | F3D59D9E20FBD747AC7825517E2E83A45D4D5C96 |
| SHA256: | 5B4EFDE0D1F52100E5E5434F321E13740EFEB66ABEBE20169CBF46B98DC10A9A |
| SSDEEP: | 3:N8MLRBXA1zKXXJkSbWKFAX8HSTnS9oiPswESjn:2MNi1zolyKxHST+oiPREOn |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3784)
- iexplore.exe (PID: 3232)
- iexplore.exe (PID: 2608)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3860)
INFO
Checks supported languages
- iexplore.exe (PID: 3232)
- iexplore.exe (PID: 3784)
- iexplore.exe (PID: 2608)
- chrome.exe (PID: 3860)
- chrome.exe (PID: 2276)
- chrome.exe (PID: 2180)
- chrome.exe (PID: 2864)
- chrome.exe (PID: 2844)
- chrome.exe (PID: 1180)
- chrome.exe (PID: 2552)
- chrome.exe (PID: 3480)
- chrome.exe (PID: 2080)
- chrome.exe (PID: 2780)
- chrome.exe (PID: 2428)
- chrome.exe (PID: 3320)
- chrome.exe (PID: 2724)
- chrome.exe (PID: 2144)
- chrome.exe (PID: 3272)
- chrome.exe (PID: 2628)
- chrome.exe (PID: 480)
- chrome.exe (PID: 2728)
- chrome.exe (PID: 2796)
- chrome.exe (PID: 2068)
- chrome.exe (PID: 972)
- chrome.exe (PID: 2948)
- chrome.exe (PID: 3924)
- chrome.exe (PID: 2444)
- chrome.exe (PID: 2704)
- chrome.exe (PID: 2376)
- chrome.exe (PID: 3772)
- chrome.exe (PID: 3492)
- chrome.exe (PID: 4048)
- chrome.exe (PID: 2852)
- chrome.exe (PID: 3340)
Reads the computer name
- iexplore.exe (PID: 3232)
- iexplore.exe (PID: 3784)
- iexplore.exe (PID: 2608)
- chrome.exe (PID: 2180)
- chrome.exe (PID: 2276)
- chrome.exe (PID: 2780)
- chrome.exe (PID: 3860)
- chrome.exe (PID: 3492)
- chrome.exe (PID: 2704)
- chrome.exe (PID: 2376)
- chrome.exe (PID: 2852)
Application launched itself
- iexplore.exe (PID: 3232)
- chrome.exe (PID: 3860)
Reads settings of System Certificates
- iexplore.exe (PID: 3784)
- iexplore.exe (PID: 3232)
- chrome.exe (PID: 2180)
Creates files in the user directory
- iexplore.exe (PID: 3784)
- iexplore.exe (PID: 3232)
Changes internet zones settings
- iexplore.exe (PID: 3232)
Checks Windows Trust Settings
- iexplore.exe (PID: 3784)
- iexplore.exe (PID: 3232)
Reads internet explorer settings
- iexplore.exe (PID: 3784)
- iexplore.exe (PID: 2608)
Reads the date of Windows installation
- iexplore.exe (PID: 3232)
- chrome.exe (PID: 2376)
Reads the hosts file
- chrome.exe (PID: 3860)
- chrome.exe (PID: 2180)
Manual execution by user
- chrome.exe (PID: 3860)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
70
Monitored processes
34
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 480 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,6307112270669889200,9469870073604978430,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=17 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2120 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 972 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,6307112270669889200,9469870073604978430,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=20 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2788 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1180 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=86.0.4240.198 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6e9dd988,0x6e9dd998,0x6e9dd9a4 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2068 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1024,6307112270669889200,9469870073604978430,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3576 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2080 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1024,6307112270669889200,9469870073604978430,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2928 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2144 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1024,6307112270669889200,9469870073604978430,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3460 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2180 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1024,6307112270669889200,9469870073604978430,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1344 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2276 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1024,6307112270669889200,9469870073604978430,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1052 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2376 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1024,6307112270669889200,9469870073604978430,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3280 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2428 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1024,6307112270669889200,9469870073604978430,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3448 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
27 671
Read events
27 406
Write events
263
Delete events
2
Modification events
| (PID) Process: | (3232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30923950 | |||
| (PID) Process: | (3232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30923950 | |||
| (PID) Process: | (3232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
256
Text files
183
Unknown types
39
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3784 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3784 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
| 3232 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_1DC6D7385EA816C957BA2B715AC5C442 | der | |
MD5:— | SHA256:— | |||
| 3232 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_1DC6D7385EA816C957BA2B715AC5C442 | binary | |
MD5:— | SHA256:— | |||
| 3784 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\umXwadTfxHNIvB7DtxMGHXIUa3qEJXhT[1].htm | html | |
MD5:— | SHA256:— | |||
| 3784 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 3784 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\82CB34DD3343FE727DF8890D352E0D8F | der | |
MD5:— | SHA256:— | |||
| 3784 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\82CB34DD3343FE727DF8890D352E0D8F | binary | |
MD5:— | SHA256:— | |||
| 3784 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\polyfills-es2015.1736b721c9dceedbc82d[1].js | text | |
MD5:— | SHA256:— | |||
| 3784 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\styles.1f0942e4e6f32f991d97[1].css | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
145
DNS requests
67
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3784 | iexplore.exe | GET | — | 142.250.185.131:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | — | — | whitelisted |
3232 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
3784 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/Omniroot2025.crl | US | der | 7.68 Kb | whitelisted |
3784 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
3784 | iexplore.exe | GET | 200 | 104.18.31.182:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
3784 | iexplore.exe | GET | 200 | 13.225.84.97:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
3784 | iexplore.exe | GET | 200 | 143.204.101.124:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
3784 | iexplore.exe | GET | 200 | 104.18.30.182:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQCCpp%2FB6wb3ghw0FkPuQvUm | US | der | 472 b | whitelisted |
3232 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
3784 | iexplore.exe | GET | 200 | 143.204.101.190:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | der | 1.39 Kb | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 172.67.195.136:443 | linkvertise.download | — | US | suspicious |
3784 | iexplore.exe | 172.67.195.136:443 | linkvertise.download | — | US | suspicious |
3784 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3784 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
3232 | iexplore.exe | 13.107.21.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3232 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3784 | iexplore.exe | 104.21.68.126:443 | linkvertise.download | Cloudflare Inc | US | unknown |
3784 | iexplore.exe | 142.250.186.106:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3784 | iexplore.exe | 104.16.18.94:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | unknown |
3784 | iexplore.exe | 104.18.11.207:443 | stackpath.bootstrapcdn.com | Cloudflare Inc | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
linkvertise.download |
| suspicious |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
maxst.icons8.com |
| whitelisted |
stackpath.bootstrapcdn.com |
| whitelisted |