| download: | download |
| Full analysis: | https://app.any.run/tasks/dde99165-50c9-4aca-9936-e877e6709d58 |
| Verdict: | Malicious activity |
| Analysis date: | January 19, 2021, 20:42:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-msi |
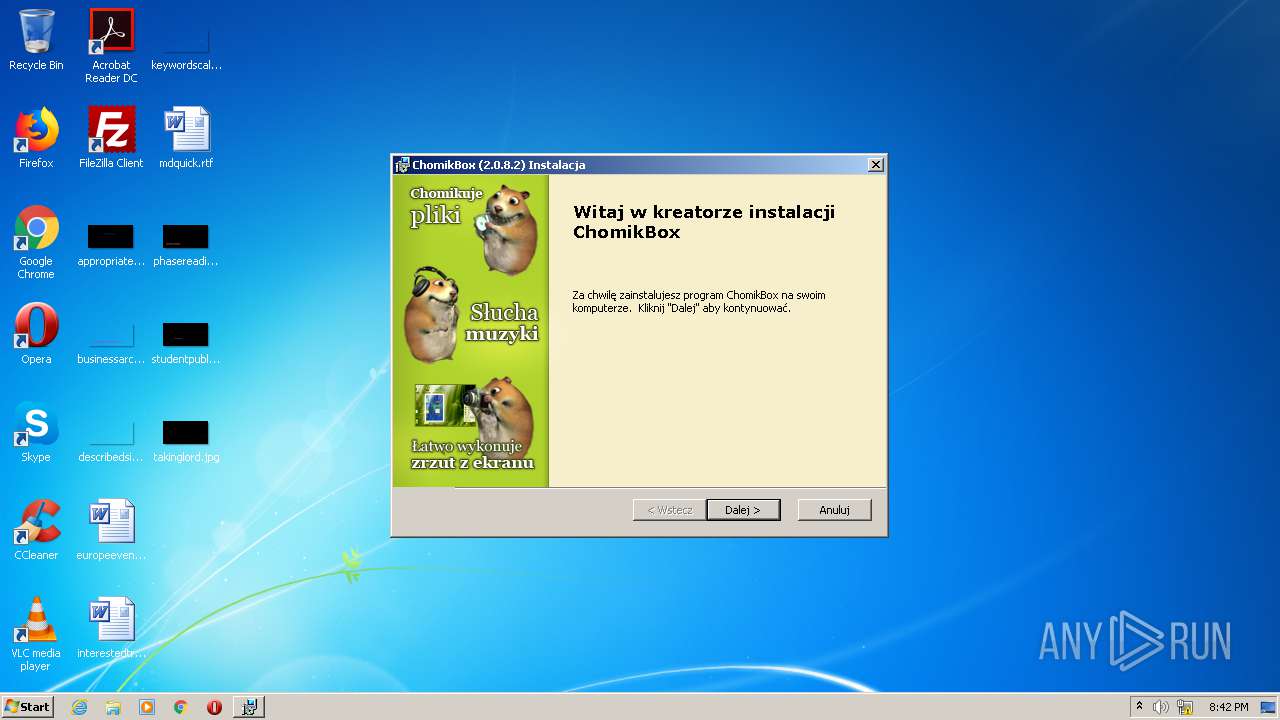
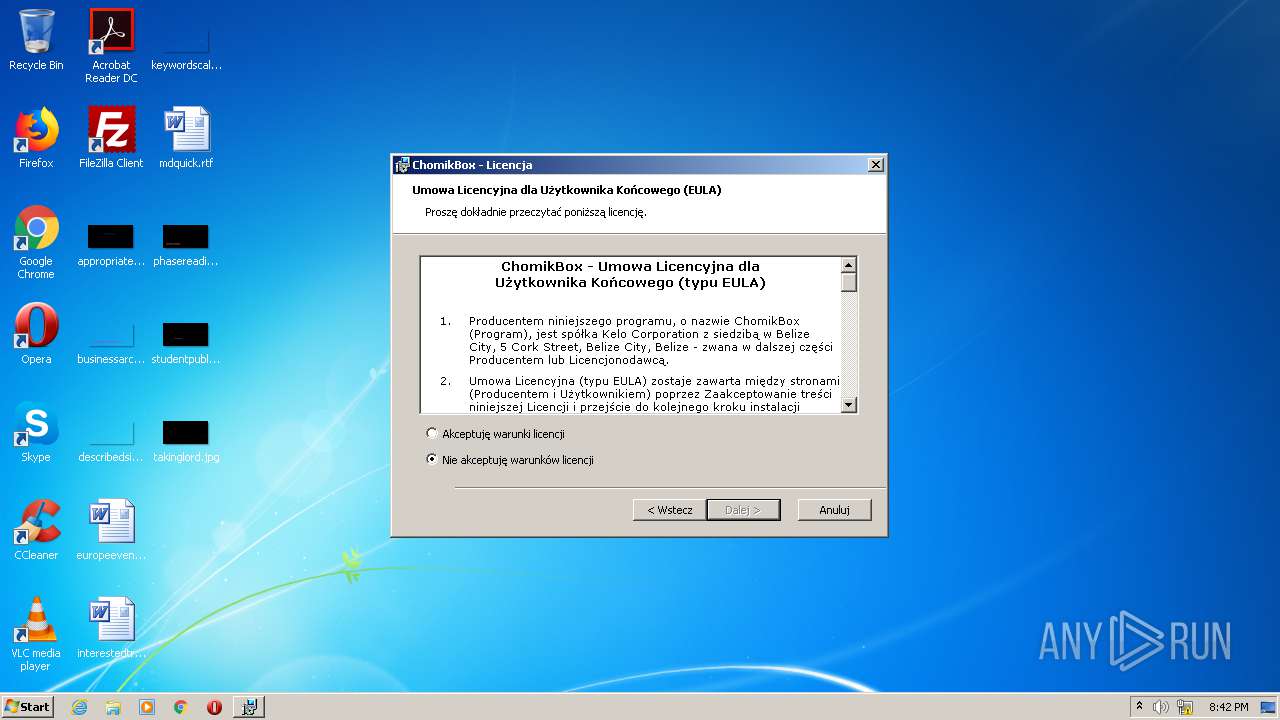
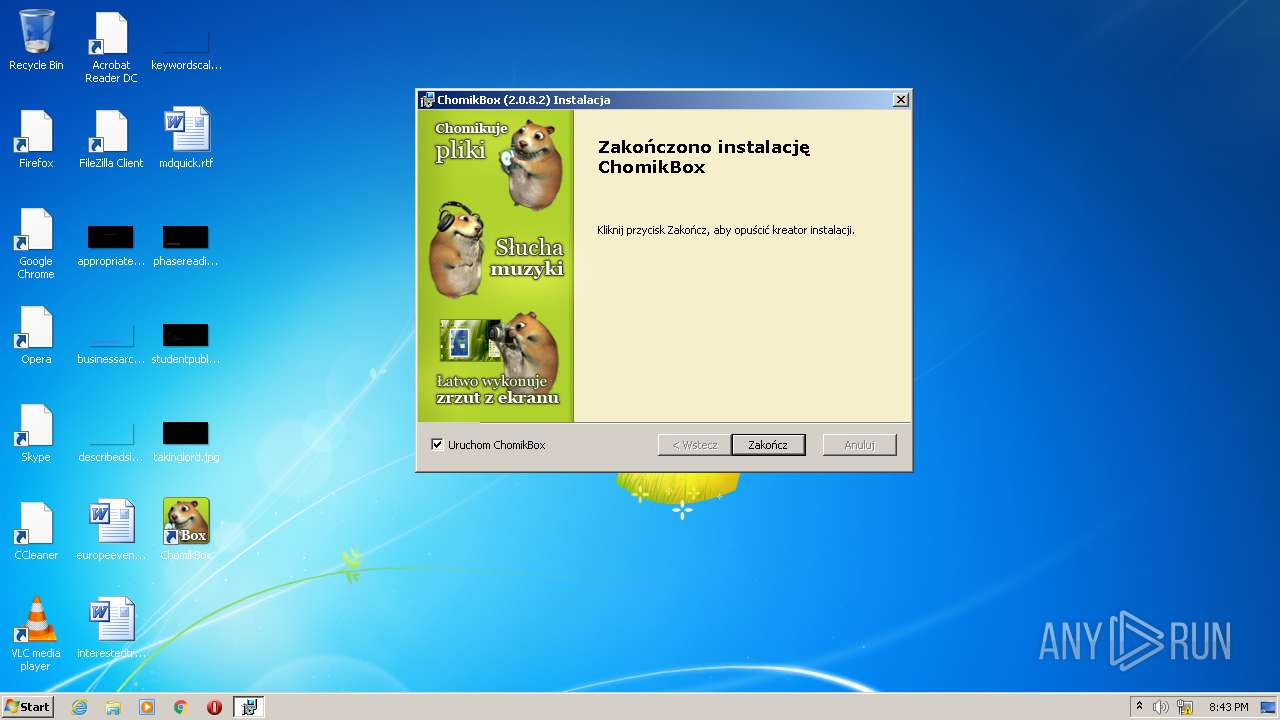
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, MSI Installer, Security: 0, Revision Number: {CBF865E4-BC72-4969-97A0-E5E4A82161DF}, Number of Words: 2, Create Time/Date: Sat Oct 21 00:37:15 2017, Total Editing Time: Sat Oct 21 00:37:15 2017, Comments: Przyjazny chomik na twj pulpit, Template: Intel;0,1045, Code page: 1250, Title: ChomikBox, Author: Chomikuj.pl, Keywords: Installer,Msi,ChomikBox, Last Saved By: Chomikuj.pl, Name of Creating Application: [ProductName] [Version], Number of Pages: 150 |
| MD5: | 7D342A648B4A385A512C845E93DBD090 |
| SHA1: | A2182080E9EC87A8F03E92E302A77BDF1C3277F6 |
| SHA256: | 5B36C942E2CA08FAC35404D9FBA8F2AAA946F63912FFB3B73EF8140033FE991B |
| SSDEEP: | 786432:jvex6e4d/FtTCFcOgSYGnRW0KysRf3LdsGSAXbgXmr0:jGxt4d/rTC+olRW0KysRP+GS6gWr0 |
MALICIOUS
Loads dropped or rewritten executable
- chomikbox1conf.exe (PID: 3116)
- ChomikBox.exe (PID: 3480)
- ChomikBox.exe (PID: 3152)
Application was dropped or rewritten from another process
- chomikbox1conf.exe (PID: 3116)
- ChomikBox.exe (PID: 3480)
- ChomikBox.exe (PID: 3152)
Changes the autorun value in the registry
- ChomikBox.exe (PID: 3152)
SUSPICIOUS
Creates a directory in Program Files
- msiexec.exe (PID: 3780)
Changes default file association
- msiexec.exe (PID: 3780)
Drops a file that was compiled in debug mode
- msiexec.exe (PID: 3780)
Creates files in the user directory
- msiexec.exe (PID: 3780)
Executed as Windows Service
- vssvc.exe (PID: 2804)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 3780)
Creates files in the Windows directory
- msiexec.exe (PID: 3780)
Removes files from Windows directory
- msiexec.exe (PID: 3780)
Executable content was dropped or overwritten
- msiexec.exe (PID: 3780)
- ChomikBox.exe (PID: 3152)
INFO
Creates a software uninstall entry
- msiexec.exe (PID: 3780)
Dropped object may contain Bitcoin addresses
- msiexec.exe (PID: 3780)
Searches for installed software
- msiexec.exe (PID: 3780)
Manual execution by user
- ChomikBox.exe (PID: 3152)
Loads dropped or rewritten executable
- msiexec.exe (PID: 3780)
Creates files in the program directory
- msiexec.exe (PID: 3780)
Low-level read access rights to disk partition
- vssvc.exe (PID: 2804)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (90.2) |
|---|---|---|
| .msp | | | Windows Installer Patch (8.4) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| Security: | None |
|---|---|
| RevisionNumber: | {CBF865E4-BC72-4969-97A0-E5E4A82161DF} |
| Words: | 2 |
| CreateDate: | 2017:10:20 23:37:15 |
| TotalEditTime: | 2017:10:20 23:37:15 |
| Comments: | Przyjazny chomik na tw?j pulpit |
| Template: | Intel;0,1045 |
| CodePage: | Windows Latin 2 (Central European) |
| Title: | ChomikBox |
| Subject: | - |
| Author: | Chomikuj.pl |
| Keywords: | Installer,Msi,ChomikBox |
| LastModifiedBy: | Chomikuj.pl |
| Software: | [ProductName] [Version] |
| Pages: | 150 |
Total processes
57
Monitored processes
7
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 272 | "C:\Windows\system32\Cmd.exe" /c "start /b chomikbox1conf.exe" | C:\Windows\system32\Cmd.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2144 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\download.msi" | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2804 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3116 | chomikbox1conf.exe | C:\Program Files\ChomikBox\chomikbox1conf.exe | Cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3152 | "C:\Program Files\ChomikBox\ChomikBox.exe" | C:\Program Files\ChomikBox\ChomikBox.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: chomikbox.exe Exit code: 0 Version: 2.0.8.2 Modules
| |||||||||||||||
| 3480 | "C:\Program Files\ChomikBox\\ChomikBox.exe" | C:\Program Files\ChomikBox\ChomikBox.exe | — | msiexec.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: chomikbox.exe Exit code: 0 Version: 2.0.8.2 Modules
| |||||||||||||||
| 3780 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 172
Read events
670
Write events
490
Delete events
12
Modification events
| (PID) Process: | (3780) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 400000000000000028D069BAA3EED601C40E0000340A0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3780) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 400000000000000028D069BAA3EED601C40E0000340A0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3780) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 43 | |||
| (PID) Process: | (3780) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4000000000000000681BB6BAA3EED601C40E0000340A0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3780) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000C27DB8BAA3EED601C40E000008090000E80300000100000000000000000000005C223A1508547041AE06BBDB035244FA0000000000000000 | |||
| (PID) Process: | (2804) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000009290CBBAA3EED601F40A0000000D0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2804) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000009290CBBAA3EED601F40A0000A0090000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2804) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000009290CBBAA3EED601F40A0000040D0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2804) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000009290CBBAA3EED601F40A0000B4090000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2804) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4000000000000000A0B7D2BAA3EED601F40A0000B4090000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
114
Suspicious files
43
Text files
12
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3780 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3780 | msiexec.exe | C:\Windows\Installer\1ca21.msi | — | |
MD5:— | SHA256:— | |||
| 3780 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF0408EB6C7E490209.TMP | — | |
MD5:— | SHA256:— | |||
| 2804 | vssvc.exe | C: | — | |
MD5:— | SHA256:— | |||
| 3780 | msiexec.exe | C:\Windows\Installer\1ca22.ipi | binary | |
MD5:— | SHA256:— | |||
| 3780 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:— | SHA256:— | |||
| 3780 | msiexec.exe | C:\Program Files\ChomikBox\avformat-lgpl-52.dll | executable | |
MD5:9520F4B0E807D0F9AE7210F947E5A53D | SHA256:9C6591CBE6A14460BEF1EA9EA4EF65DB55D95A6170CC10C4CE8989389EFB5A89 | |||
| 3780 | msiexec.exe | C:\Program Files\ChomikBox\installeru.exe | executable | |
MD5:2F11C54C40EFAE333D89EFD70CD51BC2 | SHA256:C8530EE06A21431BB9FDDD839AFE8EBB5A76F984CBF4AF55E2C58533BD0F97C9 | |||
| 3780 | msiexec.exe | C:\Program Files\ChomikBox\base.ini | text | |
MD5:A8FC877CA8AE5D2841B72BEDC6976CC8 | SHA256:0565B4DEB35C676A27D9C8DAA67FD55032DD17B8DBD6E7E335E23784661D0AAA | |||
| 3780 | msiexec.exe | C:\Program Files\ChomikBox\configurator.exe | executable | |
MD5:3A0772E69B77997BF1A158B81F85E1CD | SHA256:A7387B9C557AF2D61E7C95575911A1F2CA2D8461D7EFA7F20A47C947FFFEFDD7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
1
DNS requests
1
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3152 | ChomikBox.exe | GET | 301 | 95.211.227.131:80 | http://download.box.chomikuj.pl/updates/win32/packages.xml | NL | html | 189 b | suspicious |
3152 | ChomikBox.exe | GET | 200 | 95.211.227.131:80 | http://download.box.chomikuj.pl/updates/2.0.8.2/win32/chomikbox.exe.gz | NL | compressed | 1.47 Mb | suspicious |
3152 | ChomikBox.exe | GET | 200 | 95.211.227.131:80 | http://download.box.chomikuj.pl/updates/2.0.8.2/win32/packages.xml | NL | xml | 10.1 Kb | suspicious |
3152 | ChomikBox.exe | GET | 200 | 95.211.227.131:80 | http://download.box.chomikuj.pl/updates/2.0.8.2/win32/chomikbox1conf.exe.gz | NL | compressed | 153 Kb | suspicious |
3152 | ChomikBox.exe | GET | 200 | 95.211.227.131:80 | http://download.box.chomikuj.pl/updates/2.0.8.2/win32/installer.exe.gz | NL | compressed | 55.4 Kb | suspicious |
3152 | ChomikBox.exe | GET | 200 | 95.211.227.131:80 | http://download.box.chomikuj.pl/updates/2.0.8.2/win32/installeru.exe.gz | NL | compressed | 55.4 Kb | suspicious |
3152 | ChomikBox.exe | GET | 200 | 95.211.227.131:80 | http://download.box.chomikuj.pl/updates/2.0.8.2/win32/configurator.exe.gz | NL | compressed | 102 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3152 | ChomikBox.exe | 95.211.227.131:80 | download.box.chomikuj.pl | LeaseWeb Netherlands B.V. | NL | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download.box.chomikuj.pl |
| suspicious |
Threats
7 ETPRO signatures available at the full report
Process | Message |
|---|---|
chomikbox1conf.exe | # 3116
-------------------
----- start -----
-------------------
|
chomikbox1conf.exe | debug: version: "" ulevel: -1 gui: true pid: 3116
|
chomikbox1conf.exe | "OS: Windows 7 (ver. 6.1) Build(7601) Architecture: x86 Service Pack 1.0"
|
chomikbox1conf.exe | App location: "C:/Program Files/ChomikBox/"
|
chomikbox1conf.exe | Data location: "C:/Users/admin/AppData/Local/ChomikBox/"
|
chomikbox1conf.exe | Temp location: "C:/Users/admin/AppData/Local/Temp"
|
chomikbox1conf.exe | App name: "ChomikBox" title: "ChomikBox"
|
chomikbox1conf.exe | BaseApplication::forceSkin(, 1, 0): green
|
chomikbox1conf.exe | # 3116
----- end -----
|
ChomikBox.exe | # 3152
-------------------
----- start -----
-------------------
|