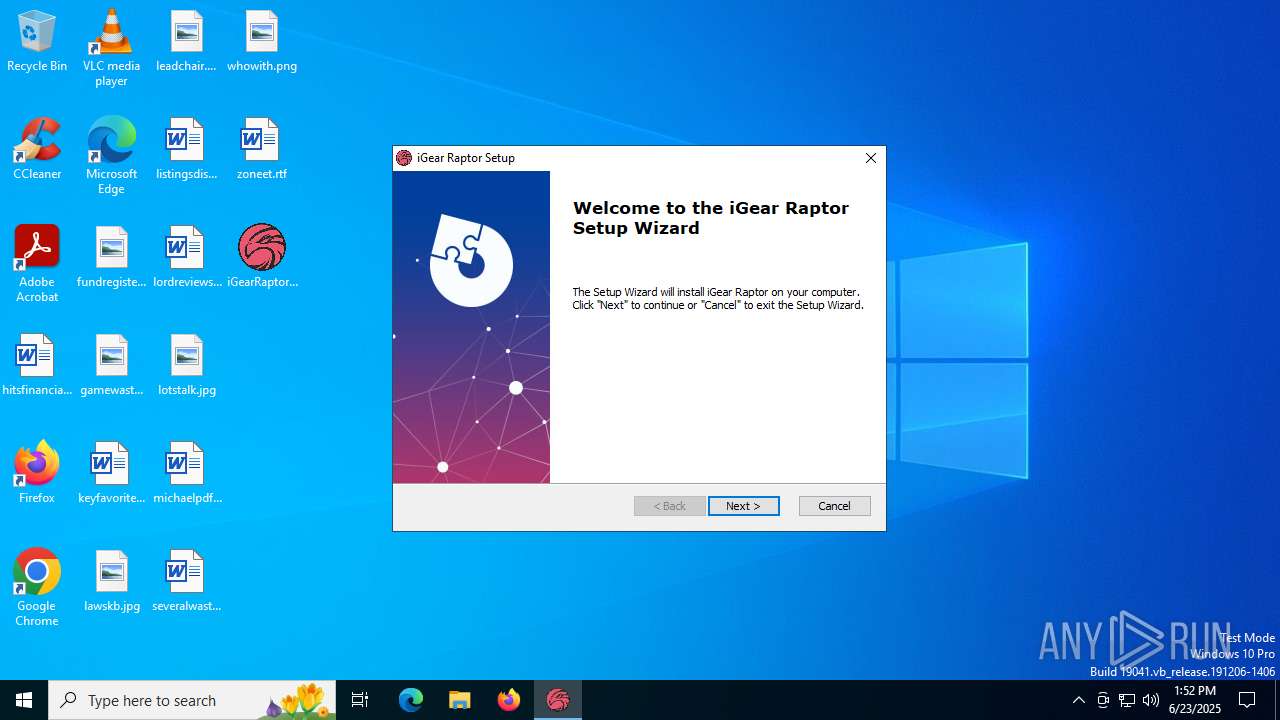
| File name: | iGearRaptor.exe |
| Full analysis: | https://app.any.run/tasks/2d522efc-e55f-4510-9929-9567f546b319 |
| Verdict: | Malicious activity |
| Analysis date: | June 23, 2025, 13:52:26 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | E2269BA1A8D80D31B76E7CFD2FFCB924 |
| SHA1: | D5529A7CE46B6B6E9A9BB36C098C1F69E41C230A |
| SHA256: | 5B3095D6FD25A01097FDD183A22DD808AE423E1E2CFBB2E96435C949CF561273 |
| SSDEEP: | 196608:589IlOnQBqY+7DZsY6sLH9Z9nIf67g2qkRKTmju+sKy:58JQxLYzL9Z9nIfogz/Tmy+sT |
MALICIOUS
No malicious indicators.SUSPICIOUS
ADVANCEDINSTALLER mutex has been found
- iGearRaptor.exe (PID: 1068)
Reads the Windows owner or organization settings
- iGearRaptor.exe (PID: 1068)
- iGearRaptor.exe (PID: 432)
- msiexec.exe (PID: 4892)
Process drops legitimate windows executable
- iGearRaptor.exe (PID: 1068)
- iGearRaptor.exe (PID: 432)
Executable content was dropped or overwritten
- iGearRaptor.exe (PID: 1068)
- iGearRaptor.exe (PID: 432)
Reads security settings of Internet Explorer
- iGearRaptor.exe (PID: 432)
- iGearRaptor.exe (PID: 1068)
Executes as Windows Service
- VSSVC.exe (PID: 6796)
There is functionality for taking screenshot (YARA)
- iGearRaptor.exe (PID: 1068)
- iGearRaptor.exe (PID: 432)
Detects AdvancedInstaller (YARA)
- iGearRaptor.exe (PID: 1068)
- iGearRaptor.exe (PID: 432)
Application launched itself
- iGearRaptor.exe (PID: 1068)
INFO
Checks supported languages
- iGearRaptor.exe (PID: 1068)
- msiexec.exe (PID: 4892)
- msiexec.exe (PID: 5424)
- iGearRaptor.exe (PID: 432)
- msiexec.exe (PID: 6380)
The sample compiled with english language support
- iGearRaptor.exe (PID: 1068)
- iGearRaptor.exe (PID: 432)
- msiexec.exe (PID: 4892)
Creates files or folders in the user directory
- iGearRaptor.exe (PID: 1068)
Reads the computer name
- iGearRaptor.exe (PID: 1068)
- msiexec.exe (PID: 4892)
- msiexec.exe (PID: 5424)
- iGearRaptor.exe (PID: 432)
- msiexec.exe (PID: 6380)
Reads Environment values
- iGearRaptor.exe (PID: 1068)
- msiexec.exe (PID: 5424)
- iGearRaptor.exe (PID: 432)
- msiexec.exe (PID: 6380)
Create files in a temporary directory
- iGearRaptor.exe (PID: 1068)
- iGearRaptor.exe (PID: 432)
Reads the machine GUID from the registry
- iGearRaptor.exe (PID: 432)
Process checks computer location settings
- iGearRaptor.exe (PID: 1068)
Executable content was dropped or overwritten
- msiexec.exe (PID: 4892)
The sample compiled with chinese language support
- msiexec.exe (PID: 4892)
Creates a software uninstall entry
- msiexec.exe (PID: 4892)
Checks proxy server information
- slui.exe (PID: 1964)
Reads the software policy settings
- slui.exe (PID: 1964)
Manages system restore points
- SrTasks.exe (PID: 3732)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (3.6) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (1.6) |
| .exe | | | DOS Executable Generic (1.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:03:20 19:48:06+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 1505792 |
| InitializedDataSize: | 649728 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x121965 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.3.0 |
| ProductVersionNumber: | 1.0.3.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Inc |
| FileDescription: | iGear Raptor Installer |
| FileVersion: | 1.0.3 |
| InternalName: | iGear Hawk |
| LegalCopyright: | Copyright (C) 2023 Inc |
| OriginalFileName: | iGear Hawk.exe |
| ProductName: | iGear Raptor |
| ProductVersion: | 1.0.3 |
Total processes
147
Monitored processes
9
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
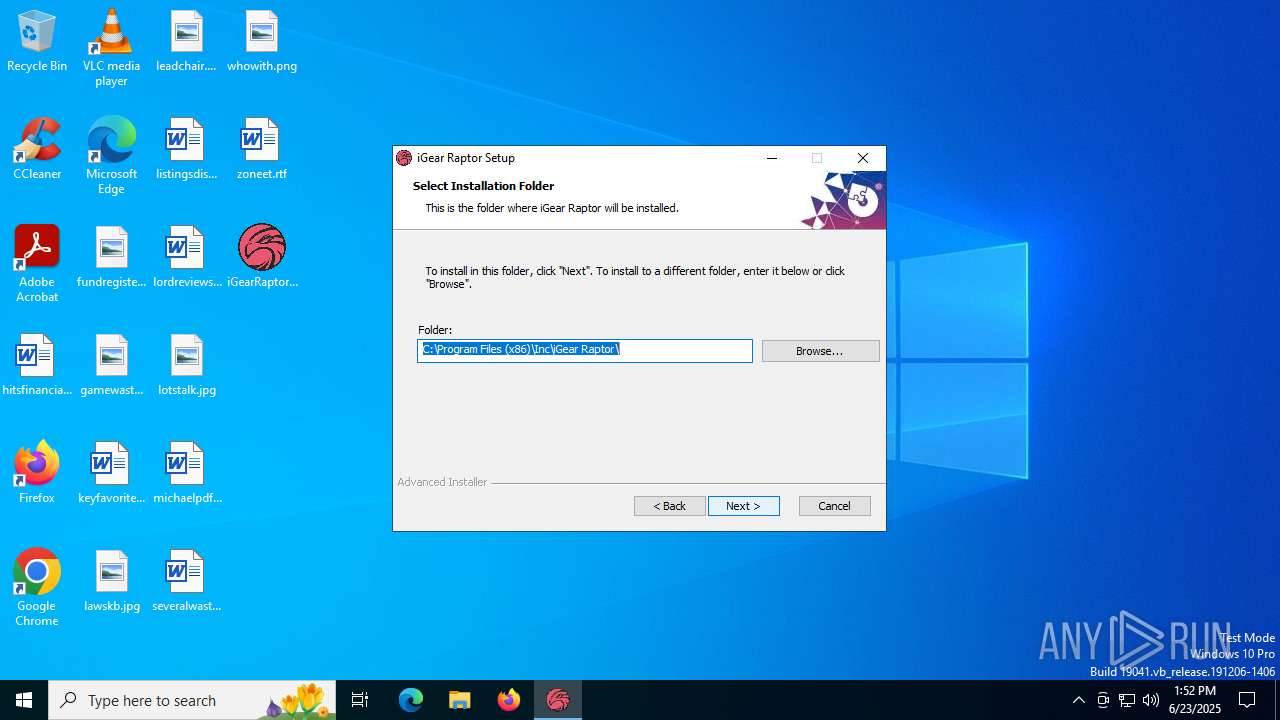
| 432 | "C:\Users\admin\Desktop\iGearRaptor.exe" /i "C:\Users\admin\AppData\Roaming\Inc\iGear Raptor 1.0.3\install\iGear Hawk.msi" AI_EUIMSI=1 APPDIR="C:\Program Files (x86)\Inc\iGear Raptor" CLIENTPROCESSID="1068" SECONDSEQUENCE="1" CHAINERUIPROCESSID="1068Chainer" ACTION="INSTALL" EXECUTEACTION="INSTALL" CLIENTUILEVEL="0" ADDLOCAL="MainFeature" PRIMARYFOLDER="APPDIR" ROOTDRIVE="C:\" AI_DETECTED_DOTNET_VERSION="4.7.2" AI_SETUPEXEPATH="C:\Users\admin\Desktop\iGearRaptor.exe" SETUPEXEDIR="C:\Users\admin\Desktop\" EXE_CMD_LINE="/exenoupdates /forcecleanup " TARGETDIR="C:\" AI_INSTALL="1" AI_SETUPEXEPATH_ORIGINAL="C:\Users\admin\Desktop\iGearRaptor.exe" | C:\Users\admin\Desktop\iGearRaptor.exe | iGearRaptor.exe | ||||||||||||
User: admin Company: Inc Integrity Level: HIGH Description: iGear Raptor Installer Exit code: 0 Version: 1.0.3 Modules
| |||||||||||||||
| 1068 | "C:\Users\admin\Desktop\iGearRaptor.exe" | C:\Users\admin\Desktop\iGearRaptor.exe | explorer.exe | ||||||||||||
User: admin Company: Inc Integrity Level: MEDIUM Description: iGear Raptor Installer Exit code: 0 Version: 1.0.3 Modules
| |||||||||||||||
| 1964 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3732 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4892 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5116 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5424 | C:\Windows\syswow64\MsiExec.exe -Embedding 4CC9F001B802EC67BBF13DBDDA80F482 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6380 | C:\Windows\syswow64\MsiExec.exe -Embedding 844EE87E335FEFC63ECBBF02B1139FC0 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6796 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 874
Read events
7 587
Write events
270
Delete events
17
Modification events
| (PID) Process: | (4892) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 48000000000000002F1D871E46E4DB011C1300008C080000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4892) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000002F1D871E46E4DB011C1300008C080000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4892) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 480000000000000080E48B1E46E4DB011C1300008C080000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4892) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000429BBB1E46E4DB011C1300008C080000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6796) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000B5F0C91E46E4DB018C1A0000FC170000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6796) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000B5F0C91E46E4DB018C1A0000FC120000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6796) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4800000000000000F5A4CE1E46E4DB018C1A0000540E0000E80300000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6796) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 48000000000000007E07D11E46E4DB018C1A0000E4140000E80300000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6796) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6796) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | write | Name: | Element |
Value: 0000000000000000000000000000000006000000000000004800000000000000715E5C2FA985EB1190A89A9B763584210000000000000000745E5C2FA985EB1190A89A9B7635842100000000000000000000000000000000 | |||
Executable files
24
Suspicious files
11
Text files
109
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1068 | iGearRaptor.exe | C:\Users\admin\AppData\Roaming\Inc\iGear Raptor 1.0.3\install\holder0.aiph | — | |
MD5:— | SHA256:— | |||
| 1068 | iGearRaptor.exe | C:\Users\admin\AppData\Local\Temp\shi6B3D.tmp | executable | |
MD5:84A34BF3486F7B9B7035DB78D78BDD1E | SHA256:F85911C910B660E528D2CF291BAA40A92D09961996D6D84E7A53A7095C7CD96E | |||
| 1068 | iGearRaptor.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_1068\repairic | image | |
MD5:D234CA0358B21BDCFC5E3F9B2E7C7A22 | SHA256:99D490C2BDEF5115F306A595964663540370141F65A25C5052352155F2603F68 | |||
| 1068 | iGearRaptor.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_1068\removico | image | |
MD5:20D25E871A244B94574C47726DE745D6 | SHA256:88DD7EE9FA22ECDBDC6B3D47DB83BC3D72360AEB43588E6A9A008B224389CB1C | |||
| 1068 | iGearRaptor.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_1068\cmdlinkarrow | image | |
MD5:983358CE03817F1CA404BEFBE1E4D96A | SHA256:7F0121322785C107BFDFE343E49F06C604C719BAFF849D07B6E099675D173961 | |||
| 1068 | iGearRaptor.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_1068\insticon | image | |
MD5:66C842AF0B4FC1C918F531D2E1087B82 | SHA256:48278165490487EE414BE65E20501B19A65EDAF1B6F473EB7D8C55023175EC88 | |||
| 1068 | iGearRaptor.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_1068\custicon | image | |
MD5:3EAEBDADE778394F06B29659C9C01ED7 | SHA256:719E644C31D0CC6B891F6A1253655DFBA39A3B78E06D24817BE1D8492B172B48 | |||
| 1068 | iGearRaptor.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_1068\info | image | |
MD5:554FF4C199562515D758C9ABFF5C2943 | SHA256:9AE4A96BF2A349667E844ACC1E2AC4F89361A6182268438F4D063DF3A6FC47BC | |||
| 1068 | iGearRaptor.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_1068\exclamic | image | |
MD5:3DBA38E7A6085876E79F162F9985618C | SHA256:593F94EF1405422B3E453F4422B22C990D84303668D60344C6FD257318E92428 | |||
| 1068 | iGearRaptor.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_1068\New | image | |
MD5:C23CBF002D82192481B61ED7EC0890F4 | SHA256:4F92E804A11453382EBFF7FB0958879BAE88FE3366306911DEC9D811CD306EED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
38
TCP/UDP connections
53
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 184.24.77.16:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 184.24.77.16:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4984 | RUXIMICS.exe | GET | 200 | 184.24.77.16:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4984 | RUXIMICS.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 40.126.32.140:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 200 | 20.190.160.20:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 16.7 Kb | whitelisted |
— | — | POST | 200 | 20.190.160.20:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
— | — | POST | 200 | 40.126.32.140:443 | https://login.live.com/RST2.srf | unknown | xml | 11.0 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4984 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 184.24.77.16:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 184.24.77.16:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4984 | RUXIMICS.exe | 184.24.77.16:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |