| File name: | wmp11-windowsxp-x64-enu.exe |
| Full analysis: | https://app.any.run/tasks/4f64f0bf-0f32-466a-8de9-62bdd6547bee |
| Verdict: | Malicious activity |
| Analysis date: | June 17, 2025, 16:08:00 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows, MS CAB-Installer self-extracting archive, 3 sections |
| MD5: | 8BC7F3CD5F20FD04A607360BBEDA46CF |
| SHA1: | 1E8522AF9B1353F9E1790D602C05D3740043D5E4 |
| SHA256: | 5AF407CF336849AFF435044EC28F066DD523BBDC22D1CE7AADDB5263084F5526 |
| SSDEEP: | 196608:Nl8FWAmuf9KM8EqjvXS16M5+wQSk/qHZ0eggWEMZiPnBGRq1w42:Q8I9cEOXS0N9SkyHp6iPkRq1a |
MALICIOUS
Executing a file with an untrusted certificate
- wmp11-windowsxp-x64-enu.exe (PID: 4916)
Changes the autorun value in the registry
- wmp11-windowsxp-x64-enu.exe (PID: 4916)
SUSPICIOUS
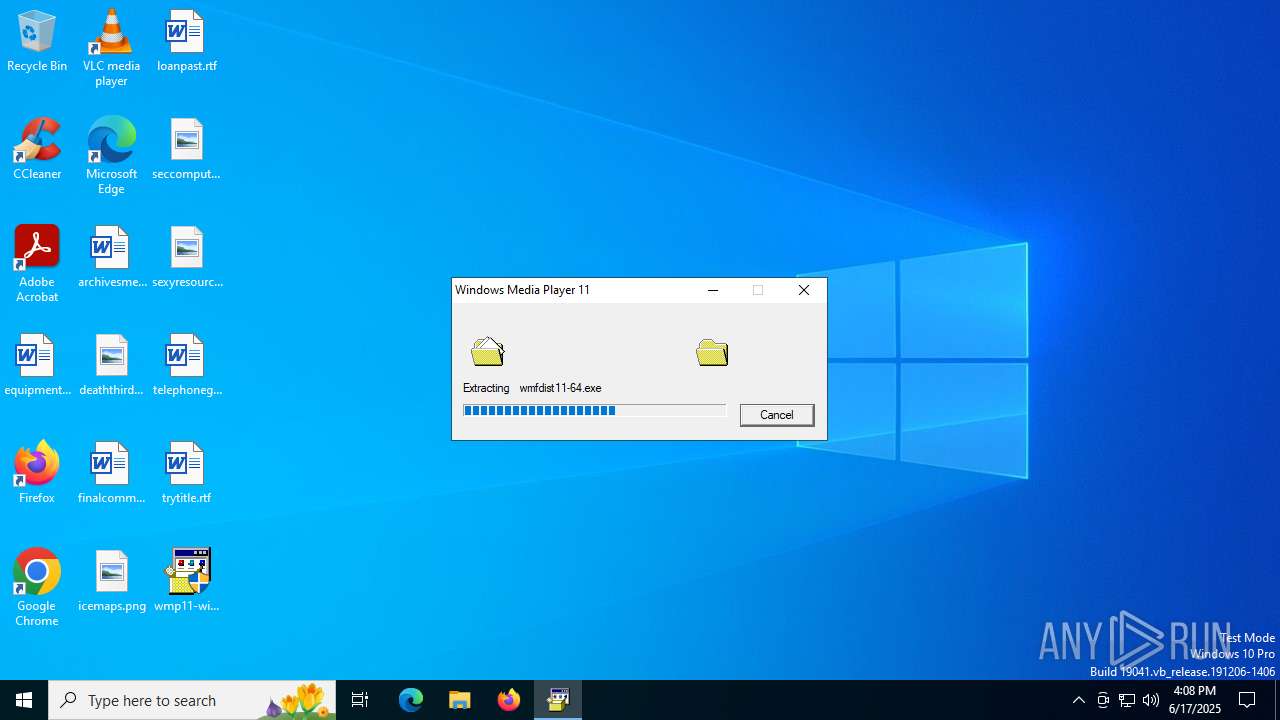
Process drops legitimate windows executable
- wmp11-windowsxp-x64-enu.exe (PID: 4916)
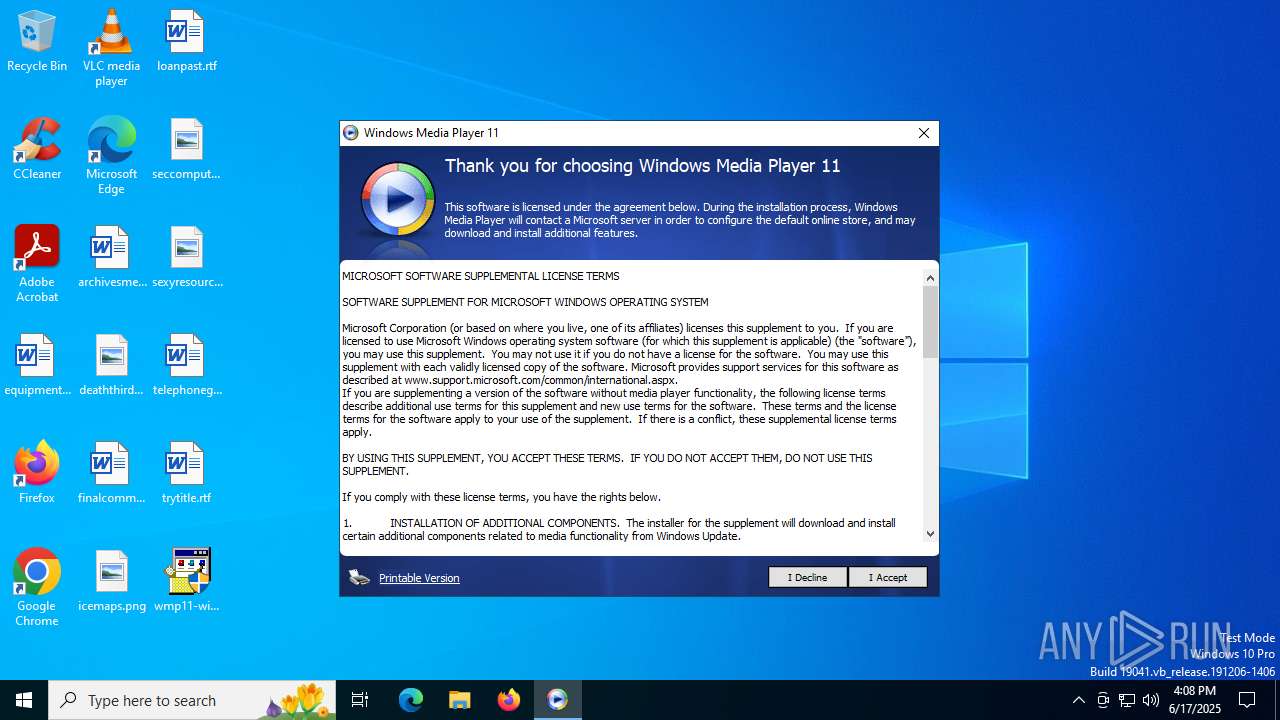
Starts a Microsoft application from unusual location
- wmp11-windowsxp-x64-enu.exe (PID: 4916)
- wmp11-windowsxp-x64-enu.exe (PID: 4968)
- setup_wm.exe (PID: 3844)
Executable content was dropped or overwritten
- wmp11-windowsxp-x64-enu.exe (PID: 4916)
INFO
The sample compiled with english language support
- wmp11-windowsxp-x64-enu.exe (PID: 4916)
Checks supported languages
- wmp11-windowsxp-x64-enu.exe (PID: 4916)
- setup_wm.exe (PID: 3844)
Reads the computer name
- wmp11-windowsxp-x64-enu.exe (PID: 4916)
- setup_wm.exe (PID: 3844)
Launching a file from a Registry key
- wmp11-windowsxp-x64-enu.exe (PID: 4916)
Create files in a temporary directory
- wmp11-windowsxp-x64-enu.exe (PID: 4916)
Manual execution by a user
- rundll32.exe (PID: 6940)
Checks proxy server information
- slui.exe (PID: 4196)
Reads the software policy settings
- slui.exe (PID: 4196)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1999:10:25 19:22:19+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 5.12 |
| CodeSize: | 34304 |
| InitializedDataSize: | 27878912 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x285d |
| OSVersion: | 5 |
| ImageVersion: | 5 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.0.2919.6304 |
| ProductVersionNumber: | 5.0.2919.6304 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Windows Media Component Setup Application |
| FileVersion: | 11.0.5721.5145 |
| InternalName: | Wextract |
| LegalCopyright: | (C) Microsoft Corporation. All rights reserved. |
| OriginalFileName: | WEXTRACT.EXE |
| ProductName: | Windows Media Component Setup Application |
| ProductVersion: | 11.0.5721.5145 |
Total processes
137
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3844 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\setup_wm.exe /P:C:\Users\admin\Desktop\wmp11-windowsxp-x64-enu.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\setup_wm.exe | — | wmp11-windowsxp-x64-enu.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Windows Media Configuration Utility Version: 11.0.5721.5146 (WMP_11.061018-2006) Modules
| |||||||||||||||
| 4196 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4916 | "C:\Users\admin\Desktop\wmp11-windowsxp-x64-enu.exe" | C:\Users\admin\Desktop\wmp11-windowsxp-x64-enu.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Media Component Setup Application Version: 11.0.5721.5145 Modules
| |||||||||||||||
| 4968 | "C:\Users\admin\Desktop\wmp11-windowsxp-x64-enu.exe" | C:\Users\admin\Desktop\wmp11-windowsxp-x64-enu.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Component Setup Application Exit code: 3221226540 Version: 11.0.5721.5145 Modules
| |||||||||||||||
| 6940 | rundll32.exe C:\WINDOWS\system32\advpack.dll,DelNodeRunDLL32 "C:\Users\admin\AppData\Local\Temp\IXP000.TMP\" | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 646
Read events
3 644
Write events
2
Delete events
0
Modification events
| (PID) Process: | (3844) setup_wm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\MediaPlayer\Services |
| Operation: | write | Name: | NoServices |
Value: 0 | |||
| (PID) Process: | (4916) wmp11-windowsxp-x64-enu.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | wextract_cleanup0 |
Value: rundll32.exe C:\WINDOWS\system32\advpack.dll,DelNodeRunDLL32 "C:\Users\admin\AppData\Local\Temp\IXP000.TMP\" | |||
Executable files
7
Suspicious files
4
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4916 | wmp11-windowsxp-x64-enu.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\control.xml | text | |
MD5:BE0EEAE3D01D122F7168ED7305531744 | SHA256:F438BE14EC900E4CBDB469A212706FEB713528553D0385056BC45FA7AE7B442F | |||
| 4916 | wmp11-windowsxp-x64-enu.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\mymusic.inf | binary | |
MD5:9AA5872731EAAE54E990C9694CF021BD | SHA256:6C88838B79ACD5765DAF1DAFA3DC63318ABAC2FA5C49363C0D2169E8D47813A7 | |||
| 4916 | wmp11-windowsxp-x64-enu.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\KB925749.cab | compressed | |
MD5:3B3923C4A69883AC83A3439F4A18B238 | SHA256:FF46BD4868100C82D602B4DCFA1F942D95F24EA208C3A0E6779EBCEDED695680 | |||
| 4916 | wmp11-windowsxp-x64-enu.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\LegitLibM.dll | executable | |
MD5:A7CA4A6D185815C9D7A1E510061DCF8E | SHA256:A559272E5DA242DD740B26DC7988B77E10930BEBD61C0FE17FF053A903011732 | |||
| 4916 | wmp11-windowsxp-x64-enu.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\Revert.wmz | compressed | |
MD5:D96A1F1EED75946B42F4A2DDDDD62A3B | SHA256:281C681885F0A119DB55A964F686AD686C46CBF3F69C9580B80A661B760F8406 | |||
| 4916 | wmp11-windowsxp-x64-enu.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\skins.inf | binary | |
MD5:1296F6E532BC4BE9ABEB5453C1846F5C | SHA256:5A5E685B16B0715A7A996502B30F77C07B8755B5EC71D12E05B3B8514D71FF83 | |||
| 4916 | wmp11-windowsxp-x64-enu.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\eula.txt | text | |
MD5:93F0486A2DC3C0B42F4B614C649D56F0 | SHA256:6D720B49D0112740BB6D9AD6D27A2BB4C997EA0F80A9B35253355BA557362139 | |||
| 4916 | wmp11-windowsxp-x64-enu.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\syncpl08.wpl | html | |
MD5:A3787A42B81FCE0E448976AD158EDD93 | SHA256:94BC17AC59BDE92FBCA00FCC69AED68FCBFE2C1754DD45F4810765F5FDF774FF | |||
| 4916 | wmp11-windowsxp-x64-enu.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\syncpl12.wpl | html | |
MD5:372D0BEEBEA5460409A6A1C53AC52A18 | SHA256:5B8B62B35E5DD8A46CCCCAF3FC3743BE9E0965D24CBCD20DA2681065EEB37EF3 | |||
| 4916 | wmp11-windowsxp-x64-enu.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\syncpl07.wpl | html | |
MD5:B9987B1F9DF6D0AFC01558B907E62A16 | SHA256:0892EFDB8459D81D4C5E1085239734D9910B9C6A1DEBD7189CF385141F0B19D1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
22
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4808 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
4808 | RUXIMICS.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4808 | RUXIMICS.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4808 | RUXIMICS.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |