| File name: | ScaryInstaller.exe |
| Full analysis: | https://app.any.run/tasks/9194deee-9756-42c3-8f6f-9b11c6054e50 |
| Verdict: | Malicious activity |
| Analysis date: | November 17, 2024, 12:06:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, 3 sections |
| MD5: | AC9526EC75362B14410CF9A29806EFF4 |
| SHA1: | EF7C1B7181A9DC4E0A1C6B3804923B58500C263D |
| SHA256: | 5AE89B053A9C8E4AD9664B6D893998F281F2864C0F625A536400624D4FBD0164 |
| SSDEEP: | 393216:8c68zOv/h4ZPW+Fsx5QiaamSf8iqTCqcvgQYp6veX0N/9FRI9qo6xEO:8j1hY++ViaamEhF5vvY2/VI9qKO |
MALICIOUS
Create files in the Startup directory
- cmd.exe (PID: 7084)
UAC/LUA settings modification
- reg.exe (PID: 5580)
Starts NET.EXE to view/add/change user profiles
- cmd.exe (PID: 7084)
- net.exe (PID: 1588)
Disables Windows Defender
- reg.exe (PID: 5700)
SUSPICIOUS
Executable content was dropped or overwritten
- ScaryInstaller.exe (PID: 5984)
- cmd.exe (PID: 7084)
Reads security settings of Internet Explorer
- ScaryInstaller.exe (PID: 5984)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7084)
Starts CMD.EXE for commands execution
- ScaryInstaller.exe (PID: 5984)
Executing commands from ".cmd" file
- ScaryInstaller.exe (PID: 5984)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 7084)
The executable file from the user directory is run by the CMD process
- CreepScreen.exe (PID: 7144)
- melter.exe (PID: 4040)
Creates file in the systems drive root
- cmd.exe (PID: 7084)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 2500)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7084)
The system shut down or reboot
- cmd.exe (PID: 7084)
INFO
Create files in a temporary directory
- ScaryInstaller.exe (PID: 5984)
Reads the computer name
- ScaryInstaller.exe (PID: 5984)
- CreepScreen.exe (PID: 7144)
- vlc.exe (PID: 6024)
The process uses the downloaded file
- ScaryInstaller.exe (PID: 5984)
- cmd.exe (PID: 7084)
Process checks computer location settings
- ScaryInstaller.exe (PID: 5984)
Checks supported languages
- ScaryInstaller.exe (PID: 5984)
- CreepScreen.exe (PID: 7144)
- melter.exe (PID: 4040)
- vlc.exe (PID: 6024)
UPX packer has been detected
- ScaryInstaller.exe (PID: 5984)
Creates files in the program directory
- cmd.exe (PID: 7084)
Sends debugging messages
- vlc.exe (PID: 6024)
Reads the time zone
- net1.exe (PID: 3848)
Manual execution by a user
- melter.exe (PID: 5924)
- mover.exe (PID: 5952)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (43.5) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (42.7) |
| .exe | | | Win32 Executable (generic) (7.2) |
| .exe | | | Generic Win/DOS Executable (3.2) |
| .exe | | | DOS Executable Generic (3.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:11:08 13:12:07+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 22433792 |
| InitializedDataSize: | 122880 |
| UninitializedDataSize: | 4689920 |
| EntryPoint: | 0x19de1b0 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
244
Monitored processes
26
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 624 | REG add HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System /v DisableTaskMgr /t REG_DWORD /d 1 /f | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1196 | taskkill /f /im melter.exe | C:\Windows\SysWOW64\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1452 | timeout 5 /nobreak | C:\Windows\SysWOW64\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
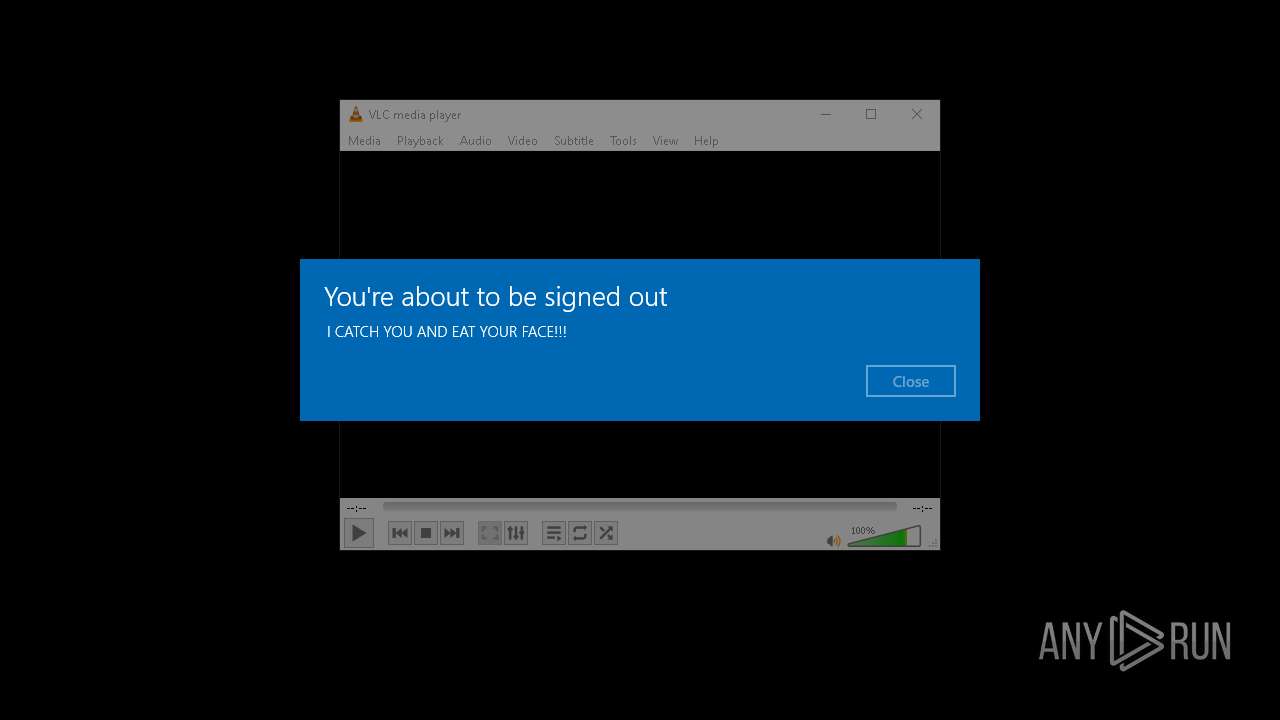
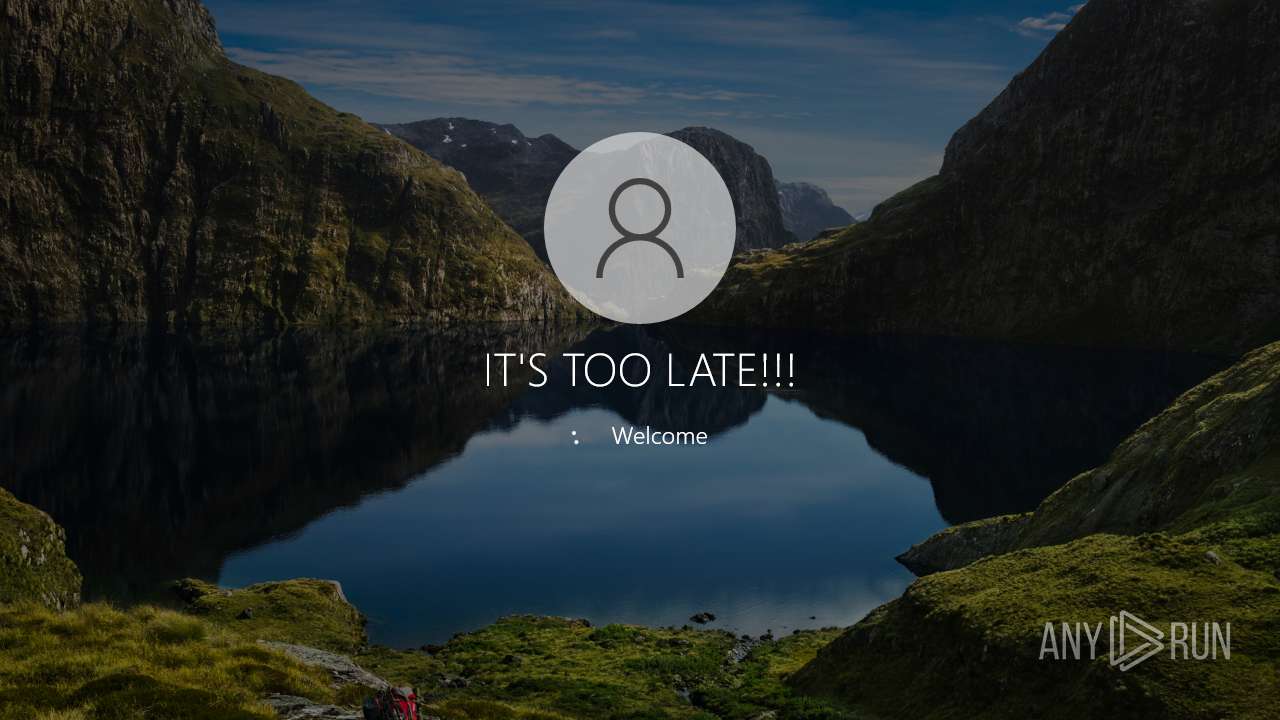
| 1588 | net user admin /fullname:"IT'S TOO LATE!!!" | C:\Windows\SysWOW64\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2500 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3020 | RUNDLL32.EXE user32.dll,UpdatePerUserSystemParameters | C:\Windows\SysWOW64\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3848 | C:\WINDOWS\system32\net1 user admin /fullname:"IT'S TOO LATE!!!" | C:\Windows\SysWOW64\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4040 | melter.exe | C:\Users\admin\AppData\Local\Temp\DD1A.tmp\melter.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 4684 | timeout 10 /nobreak | C:\Windows\SysWOW64\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5444 | reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer" /v "NoControlPanel" /t REG_DWORD /d "1" /f | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 770
Read events
2 762
Write events
8
Delete events
0
Modification events
| (PID) Process: | (7084) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.mp4\OpenWithProgids |
| Operation: | write | Name: | VLC.mp4 |
Value: | |||
| (PID) Process: | (7084) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {F81B1B56-7613-4EE4-BC05-1FAB5DE5C07E} {886D8EEB-8CF2-4446-8D02-CDBA1DBDCF99} 0xFFFF |
Value: 0100000000000000821A7F41E938DB01 | |||
| (PID) Process: | (6220) reg.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | Wallpaper |
Value: c:\bg.bmp | |||
| (PID) Process: | (6604) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\ActiveDesktop |
| Operation: | write | Name: | NoChangingWallPaper |
Value: 1 | |||
| (PID) Process: | (5580) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (5700) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender |
| Operation: | write | Name: | DisableAntiSpyware |
Value: 1 | |||
| (PID) Process: | (624) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableTaskMgr |
Value: 1 | |||
| (PID) Process: | (5444) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | NoControlPanel |
Value: 1 | |||
Executable files
7
Suspicious files
26
Text files
2
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5984 | ScaryInstaller.exe | C:\Users\admin\AppData\Local\Temp\DD1A.tmp\bg.bmp | — | |
MD5:— | SHA256:— | |||
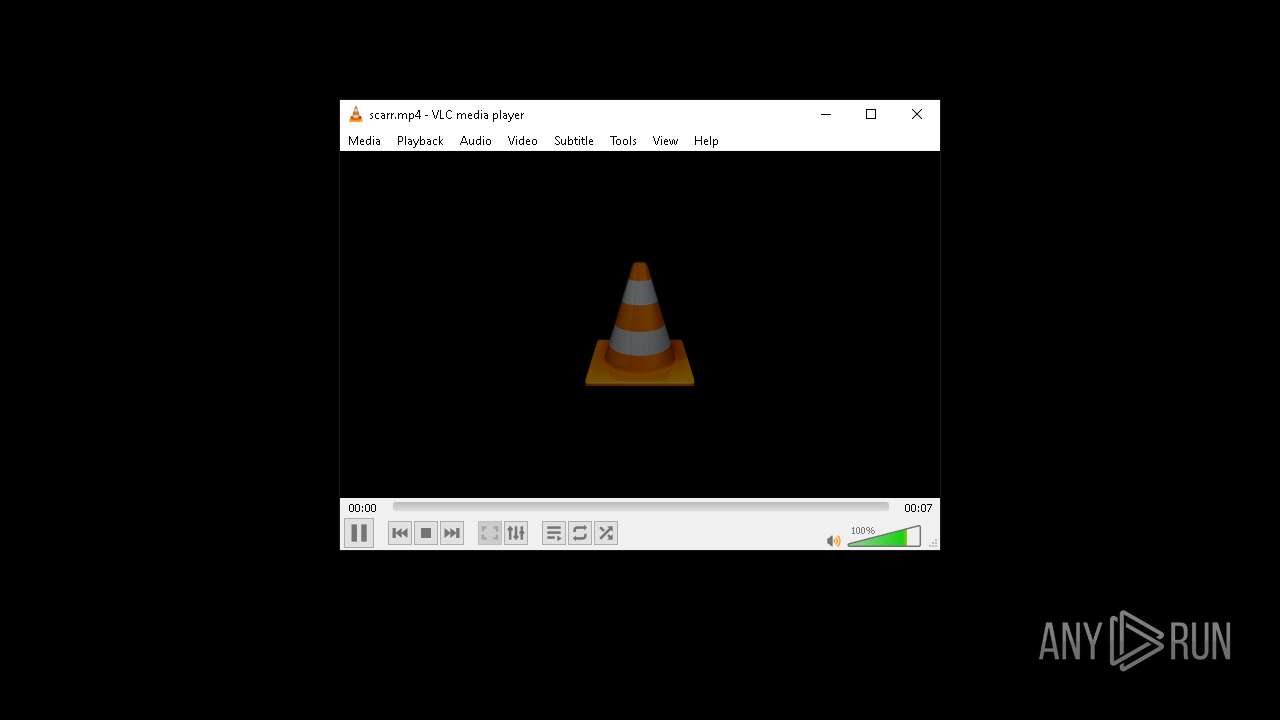
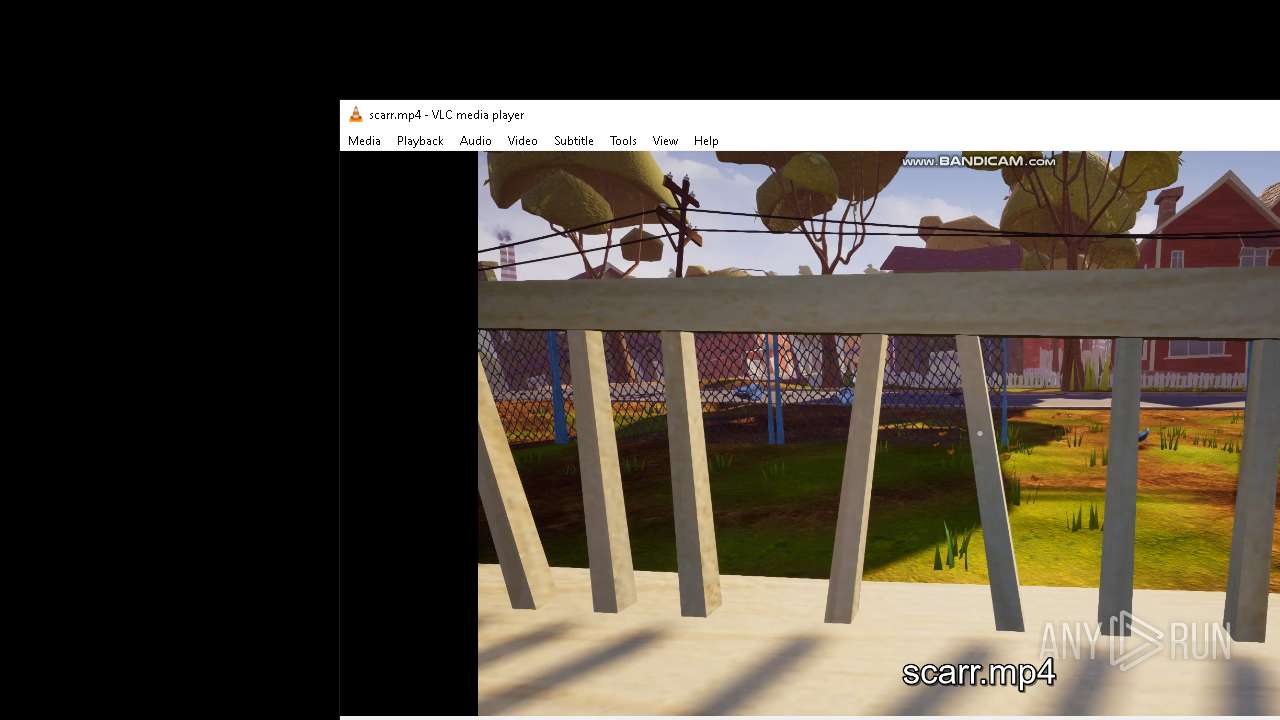
| 5984 | ScaryInstaller.exe | C:\Users\admin\AppData\Local\Temp\DD1A.tmp\scarr.mp4 | — | |
MD5:— | SHA256:— | |||
| 7084 | cmd.exe | C:\bg.bmp | — | |
MD5:— | SHA256:— | |||
| 2500 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.037.etl | etl | |
MD5:FA358BFEE9B4E1FFB7394D13CBBC4898 | SHA256:6FF97BBF8A56286A4C71623829514CC14B7F8CBBCF09748D939F733968478A22 | |||
| 6024 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini | text | |
MD5:3B47E9E21A1AAF0CA4C211FF7928EAC1 | SHA256:20E3082F2281810FFA11E353ECB207CBC456BE52F04B380A58EB96CE8481FE7D | |||
| 5984 | ScaryInstaller.exe | C:\Users\admin\AppData\Local\Temp\DD1A.tmp\melter.exe | executable | |
MD5:33B75BD8DBB430E95C70D0265EEB911F | SHA256:2F69F7EEAB4C8C2574EF38ED1BDEA531B6C549EF702F8DE0D25C42DCC4A2CA12 | |||
| 6024 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini.tb6024 | text | |
MD5:3B47E9E21A1AAF0CA4C211FF7928EAC1 | SHA256:20E3082F2281810FFA11E353ECB207CBC456BE52F04B380A58EB96CE8481FE7D | |||
| 2500 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.033.etl | etl | |
MD5:2F36C598EBFF5B5CDD898C9691D6BCCB | SHA256:8900C5931ED8E0D1B68082B45CF2F4E8C1025D36825508E0804C916D781B9F50 | |||
| 6024 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini.lock | text | |
MD5:EBE44780B7BE5F5F41D442EE0D0C7BA8 | SHA256:BF19E4BA6C4D9D316A37F31433C7D22B04A31150C34599C5C60763977243CAD9 | |||
| 7084 | cmd.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp\mover.exe | executable | |
MD5:C1978E4080D1EC7E2EDF49D6C9710045 | SHA256:C9E2A7905501745C304FFC5A70B290DB40088D9DC10C47A98A953267468284A8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
35
TCP/UDP connections
34
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 2.16.164.18:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.18:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.18:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 404 | 104.126.37.130:443 | https://r.bing.com/rb/4N/jnc,nj/WHBHN5CD2X9iLHkLc7Ck-5t1mtg.js?bu=FpIs1Cr8AeQq5yrqKuwqkSuaLOAr5RH6K4Asniz8AfwBgyjDK-MR2hHXK8gr&or=w | unknown | — | — | unknown |
— | — | GET | 200 | 104.126.37.136:443 | https://www.bing.com/fd/ls/l?IG=12D4DA20593B441E9948ECCCCB117A2E&Type=Event.ClientInst&DATA=[{%22T%22:%22CI.ClientInst%22,%22FID%22:%22CI%22,%22Name%22:%22max%20errors%20reached%22}] | unknown | — | — | unknown |
— | — | GET | 200 | 104.126.37.130:443 | https://r.bing.com/rp/-UAIppANYxiGpRWJy2NDph4qOEw.gz.js | unknown | s | 20.3 Kb | whitelisted |
— | — | GET | 200 | 52.109.28.46:443 | https://officeclient.microsoft.com/config16/?syslcid=1033&build=16.0.16026&crev=3 | unknown | xml | 176 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.23.209.130:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 2.16.164.18:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.16.164.18:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.16.164.18:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
6944 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
r.bing.com |
| whitelisted |
Threats
Process | Message |
|---|---|
vlc.exe | main libvlc debug: min period: 1 ms, max period: 1000000 ms
|
vlc.exe | main libvlc debug: Copyright © 1996-2020 the VideoLAN team
|
vlc.exe | main libvlc debug: revision 3.0.11-0-gdc0c5ced72
|
vlc.exe | main libvlc debug: VLC media player - 3.0.11 Vetinari
|
vlc.exe | main libvlc debug: configured with ../extras/package/win32/../../../configure '--enable-update-check' '--enable-lua' '--enable-faad' '--enable-flac' '--enable-theora' '--enable-avcodec' '--enable-merge-ffmpeg' '--enable-dca' '--enable-mpc' '--enable-libass' '--enable-schroedinger' '--enable-realrtsp' '--enable-live555' '--enable-dvdread' '--enable-shout' '--enable-goom' '--enable-caca' '--enable-qt' '--enable-skins2' '--enable-sse' '--enable-mmx' '--enable-libcddb' '--enable-zvbi' '--disable-telx' '--enable-nls' '--host=x86_64-w64-mingw32' '--with-breakpad=https://win.crashes.videolan.org' 'host_alias=x86_64-w64-mingw32' 'PKG_CONFIG_LIBDIR=/home/jenkins/workspace/vlc-release/windows/vlc-release-win32-x64/contrib/x86_64-w64-mingw32/lib/pkgconfig'
|
vlc.exe | main libvlc debug: using multimedia timers as clock source
|
vlc.exe | main libvlc debug: loading plugins cache file C:\Program Files\VideoLAN\VLC\plugins\plugins.dat
|
vlc.exe | main libvlc debug: searching plug-in modules
|
vlc.exe | main libvlc debug: recursively browsing `C:\Program Files\VideoLAN\VLC\plugins'
|
vlc.exe | main libvlc debug: plug-ins loaded: 494 modules
|