| File name: | HEU_KMS_Activator.exe |
| Full analysis: | https://app.any.run/tasks/d6bae109-360b-4acf-b6ba-9e26736c3a47 |
| Verdict: | No threats detected |
| Analysis date: | June 09, 2020, 08:19:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 1A48E0E1DD4473EB30A45D8860DBA038 |
| SHA1: | 47BDE7AB37BADEBD731C3F8579BB3BB15B773163 |
| SHA256: | 5AD3BA6A79E8C71C06738C0AC0A078B43D208D99BC458B5DD9724682894FD204 |
| SSDEEP: | 98304:lssAdQ7j6bkTyeI8VMcrmEpuaEAO2MFqfVR+xGo2KnuncB:i1gjtI8ecKaEX2MiVR+x12muncB |
MALICIOUS
Application was dropped or rewritten from another process
- 7Z.EXE (PID: 1940)
- kms.exe (PID: 1788)
SUSPICIOUS
Executable content was dropped or overwritten
- kms.exe (PID: 1788)
- HEU_KMS_Activator.exe (PID: 2848)
- 7Z.EXE (PID: 1940)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (49.4) |
|---|---|---|
| .scr | | | Windows screen saver (23.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (11.7) |
| .exe | | | Win32 Executable (generic) (8) |
| .exe | | | Generic Win/DOS Executable (3.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:02:04 23:43:24+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 544768 |
| InitializedDataSize: | 196608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x17520 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 11.2.0.0 |
| ProductVersionNumber: | 3.3.9.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
| FileVersion: | 11.2.0.0 |
| Comments: | 本地KMS激活,无需联网 |
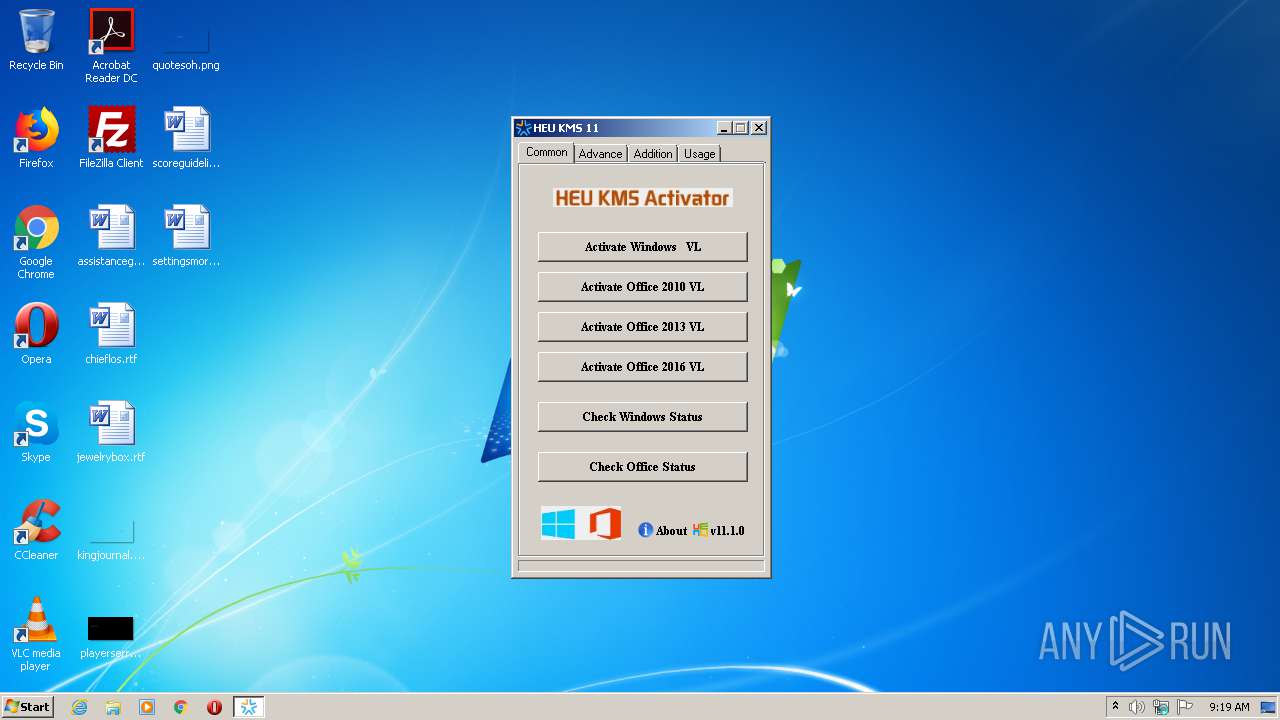
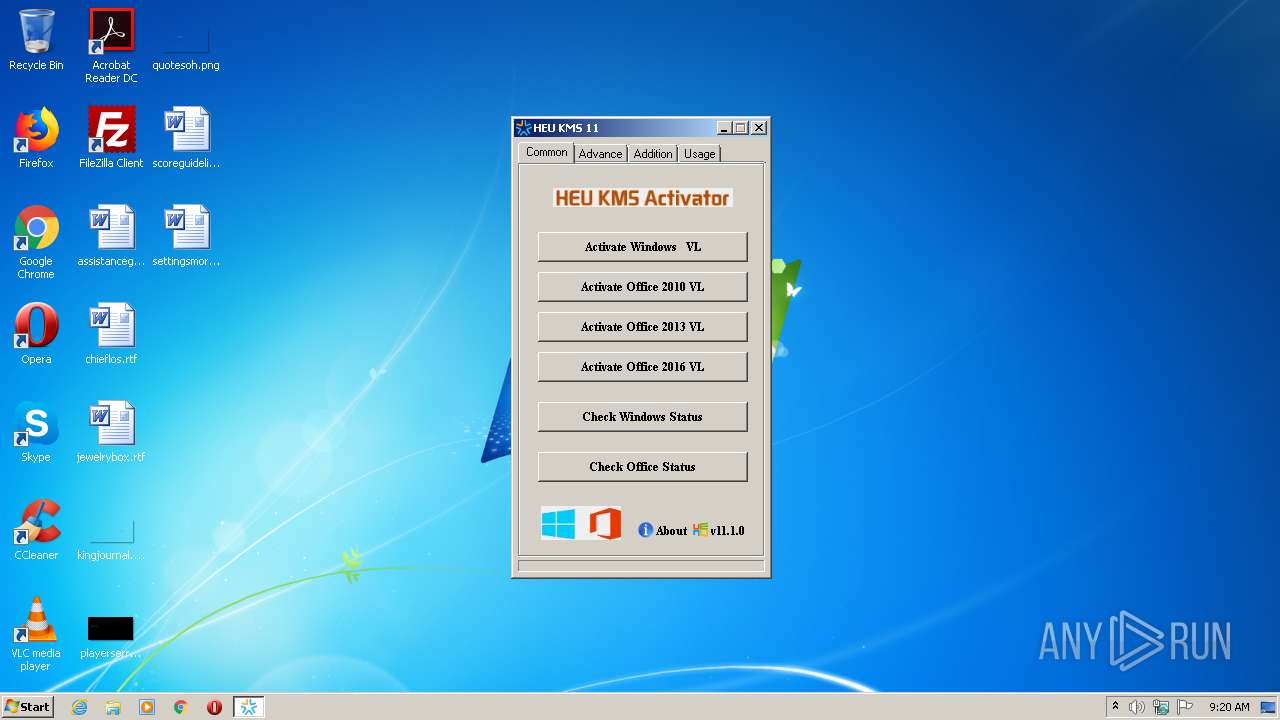
| FileDescription: | HEU KMS Activator |
| LegalCopyright: | Copyright(C) 2012-2013 By Zbezj |
| CompanyName: | HEU CNST |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 04-Feb-2012 22:43:24 |
| Detected languages: |
|
| FileVersion: | 11.2.0.0 |
| Comments: | 本地KMS激活,无需联网 |
| FileDescription: | HEU KMS Activator |
| LegalCopyright: | Copyright(C) 2012-2013 By Zbezj |
| CompanyName: | HEU CNST |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 04-Feb-2012 22:43:24 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00084F73 | 0x00085000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.70842 |
.rdata | 0x00086000 | 0x00019B08 | 0x00019C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.94077 |
.data | 0x000A0000 | 0x0001A7D8 | 0x00006800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.14453 |
.rsrc | 0x000BB000 | 0x0000FB48 | 0x0000FC00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.48239 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.09117 | 791 | Latin 1 / Western European | Chinese - PRC | RT_MANIFEST |
2 | 3.66371 | 296 | Latin 1 / Western European | English - United Kingdom | RT_ICON |
3 | 2.25499 | 296 | Latin 1 / Western European | English - United Kingdom | RT_ICON |
4 | 7.93927 | 21348 | Latin 1 / Western European | English - United Kingdom | RT_ICON |
5 | 7.94706 | 11612 | Latin 1 / Western European | English - United Kingdom | RT_ICON |
6 | 7.94111 | 13824 | Latin 1 / Western European | English - United Kingdom | RT_ICON |
7 | 5.28917 | 542 | Latin 1 / Western European | English - United Kingdom | RT_STRING |
8 | 5.19363 | 720 | Latin 1 / Western European | English - United Kingdom | RT_STRING |
9 | 5.54701 | 574 | Latin 1 / Western European | English - United Kingdom | RT_STRING |
10 | 5.19841 | 760 | Latin 1 / Western European | English - United Kingdom | RT_STRING |
Imports
ADVAPI32.dll |
COMCTL32.dll |
COMDLG32.dll |
GDI32.dll |
KERNEL32.dll |
MPR.dll |
OLEAUT32.dll |
PSAPI.DLL |
SHELL32.dll |
USER32.dll |
Total processes
41
Monitored processes
4
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1096 | "C:\Users\admin\AppData\Local\Temp\HEU_KMS_Activator.exe" | C:\Users\admin\AppData\Local\Temp\HEU_KMS_Activator.exe | — | explorer.exe | |||||||||||
User: admin Company: HEU CNST Integrity Level: MEDIUM Description: HEU KMS Activator Exit code: 3221226540 Version: 11.2.0.0 Modules
| |||||||||||||||
| 1788 | C:\Users\admin\AppData\Local\Temp\HEU_KMS_Mini_112\kms.exe | C:\Users\admin\AppData\Local\Temp\HEU_KMS_Mini_112\kms.exe | HEU_KMS_Activator.exe | ||||||||||||
User: admin Company: HEU CNST Integrity Level: HIGH Description: HEU KMS Activator Exit code: 0 Version: 0.0.0.224 Modules
| |||||||||||||||
| 1940 | C:\Users\admin\AppData\Local\Temp\7Z.EXE x C:\Users\admin\AppData\Local\Temp\KMSmini.7z -y -oC:\Users\admin\AppData\Local\Temp\HEU_KMS_Mini_112\ | C:\Users\admin\AppData\Local\Temp\7Z.EXE | HEU_KMS_Activator.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip 独立命令行 Exit code: 0 Version: 9.17 beta Modules
| |||||||||||||||
| 2848 | "C:\Users\admin\AppData\Local\Temp\HEU_KMS_Activator.exe" | C:\Users\admin\AppData\Local\Temp\HEU_KMS_Activator.exe | explorer.exe | ||||||||||||
User: admin Company: HEU CNST Integrity Level: HIGH Description: HEU KMS Activator Exit code: 0 Version: 11.2.0.0 Modules
| |||||||||||||||
Total events
27
Read events
27
Write events
0
Delete events
0
Modification events
Executable files
17
Suspicious files
4
Text files
200
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2848 | HEU_KMS_Activator.exe | C:\Users\admin\AppData\Local\Temp\aut7035.tmp | — | |
MD5:— | SHA256:— | |||
| 2848 | HEU_KMS_Activator.exe | C:\Users\admin\AppData\Local\Temp\aut70E2.tmp | — | |
MD5:— | SHA256:— | |||
| 2848 | HEU_KMS_Activator.exe | C:\Users\admin\AppData\Local\Temp\KMSmini.7z | compressed | |
MD5:— | SHA256:— | |||
| 1940 | 7Z.EXE | C:\Users\admin\AppData\Local\Temp\HEU_KMS_Mini_112\help.htm | html | |
MD5:— | SHA256:— | |||
| 1940 | 7Z.EXE | C:\Users\admin\AppData\Local\Temp\HEU_KMS_Mini_112\cert\kmscert2010\standard\office.reg | text | |
MD5:F1AF5CC277F538D585FB0A8F8094CC06 | SHA256:9F6F5B1368B98D1A57321203EDC71CB2E1F12CE1D22F8AB1E2DCCC9E53111917 | |||
| 2848 | HEU_KMS_Activator.exe | C:\Users\admin\AppData\Local\Temp\7Z.EXE | executable | |
MD5:2C3378903654F844D818FC2F0D619617 | SHA256:C360CA3555F426D0C66D23998E4FB01BE4D1FDFA71FC29102C8CFE821303ABDF | |||
| 1940 | 7Z.EXE | C:\Users\admin\AppData\Local\Temp\HEU_KMS_Mini_112\theme.jpg | image | |
MD5:8106FE4184C10CD16E50D7D991FAAD53 | SHA256:CD78691DFE096DC99D2A46C921884922511616937EFE51018EAF500C8C77314A | |||
| 1940 | 7Z.EXE | C:\Users\admin\AppData\Local\Temp\HEU_KMS_Mini_112\cert\kmscert2010\projectpro\office.reg | text | |
MD5:1A6565629E4872BB95C2022ACFCF2E50 | SHA256:9E290EF54058EE29B82490D4BCEA81EA58FC07158807B0ACFFDBB2C724499A03 | |||
| 1940 | 7Z.EXE | C:\Users\admin\AppData\Local\Temp\HEU_KMS_Mini_112\cert\kmscert2010\proplus\office.reg | text | |
MD5:357014AB3AC43DC1CC9360374AAA1DE6 | SHA256:D854E15F0C0639CFB0B2CC6A7064D6A8B0CE21A97E17B359D2DE97724117C063 | |||
| 1940 | 7Z.EXE | C:\Users\admin\AppData\Local\Temp\HEU_KMS_Mini_112\cert\kmscert2013\visiopro\office.reg | text | |
MD5:7C103254B45C83D2E44D7C89259112F9 | SHA256:077F921F30F9440FF3F9C30889B0B34FAD1DDB99B06FCD88D1F96D49BF26B991 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report