| File name: | 5aca6a390464c4880d813ebc04e6822fda9c68597600d27e1c5afaa26405bf6f |
| Full analysis: | https://app.any.run/tasks/7c29050c-a32e-4eba-9cd4-e90a59712d80 |
| Verdict: | Malicious activity |
| Analysis date: | July 18, 2019, 07:53:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 949, Author: HP, Template: Normal.dotm, Last Saved By: Windows User, Revision Number: 2, Name of Creating Application: Microsoft Office Word, Total Editing Time: 02:00, Create Time/Date: Mon Sep 11 10:20:00 2017, Last Saved Time/Date: Fri Jan 19 03:12:00 2018, Number of Pages: 1, Number of Words: 0, Number of Characters: 0, Security: 0 |
| MD5: | 1AA7277DAD2FC8268C79E8295514AA06 |
| SHA1: | A79488B114F57BD3D8A7FA29E7647E2281CE21F6 |
| SHA256: | 5ACA6A390464C4880D813EBC04E6822FDA9C68597600D27E1C5AFAA26405BF6F |
| SSDEEP: | 12288:44K6BgttUJhd/I4MClEFl3+YnmD5KYf/UXRDsin:476BgttUJhd/I4MCCX3+D7ORDsy |
MALICIOUS
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 3772)
Writes to a start menu file
- WINWORD.EXE (PID: 3772)
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 3772)
Application was dropped or rewritten from another process
- dwm.exe (PID: 1440)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 3772)
SUSPICIOUS
No suspicious indicators.INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3772)
Creates files in the user directory
- WINWORD.EXE (PID: 3772)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | - |
|---|---|
| Subject: | - |
| Author: | HP |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | Windows User |
| RevisionNumber: | 2 |
| Software: | Microsoft Office Word |
| TotalEditTime: | 2.0 minutes |
| CreateDate: | 2017:09:11 09:20:00 |
| ModifyDate: | 2018:01:19 03:12:00 |
| Pages: | 1 |
| Words: | - |
| Characters: | - |
| Security: | None |
| CodePage: | Windows Korean (Unified Hangul Code) |
| Company: | - |
| Lines: | - |
| Paragraphs: | - |
| CharCountWithSpaces: | - |
| AppVersion: | 15 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
38
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1440 | C:\Users\admin\AppData\Local\Temp\.\dwm.exe /pumpingcore | C:\Users\admin\AppData\Local\Temp\dwm.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3736 | "C:\Windows\System32\cmd.exe" /c start /b C:\Users\admin\AppData\Local\Temp\.\dwm.exe /pumpingcore | C:\Windows\System32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3772 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\5aca6a390464c4880d813ebc04e6822fda9c68597600d27e1c5afaa26405bf6f.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
1 215
Read events
868
Write events
334
Delete events
13
Modification events
| (PID) Process: | (3772) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | z8< |
Value: 7A383C00BC0E0000010000000000000000000000 | |||
| (PID) Process: | (3772) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3772) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3772) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1324482590 | |||
| (PID) Process: | (3772) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1324482704 | |||
| (PID) Process: | (3772) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1324482705 | |||
| (PID) Process: | (3772) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: BC0E00005480C0E63D3DD50100000000 | |||
| (PID) Process: | (3772) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 39< |
Value: 33393C00BC0E000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3772) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | 39< |
Value: 33393C00BC0E000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3772) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
1
Suspicious files
1
Text files
1
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3772 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRF87A.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3772 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF3D5A3C7A91AF4737.TMP | — | |
MD5:— | SHA256:— | |||
| 3772 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF30A11004D0B36E20.TMP | — | |
MD5:— | SHA256:— | |||
| 3772 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{32458EEB-F366-4B83-9ACB-4E44C51BF397}.tmp | — | |
MD5:— | SHA256:— | |||
| 3772 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{75777BAA-0C05-4B7B-BBD0-8E4FD5F98B3D}.tmp | — | |
MD5:— | SHA256:— | |||
| 3772 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{CD48D8D6-5A32-4BAB-9831-4049CE820F53}.tmp | — | |
MD5:— | SHA256:— | |||
| 3772 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$ca6a390464c4880d813ebc04e6822fda9c68597600d27e1c5afaa26405bf6f.doc | pgc | |
MD5:— | SHA256:— | |||
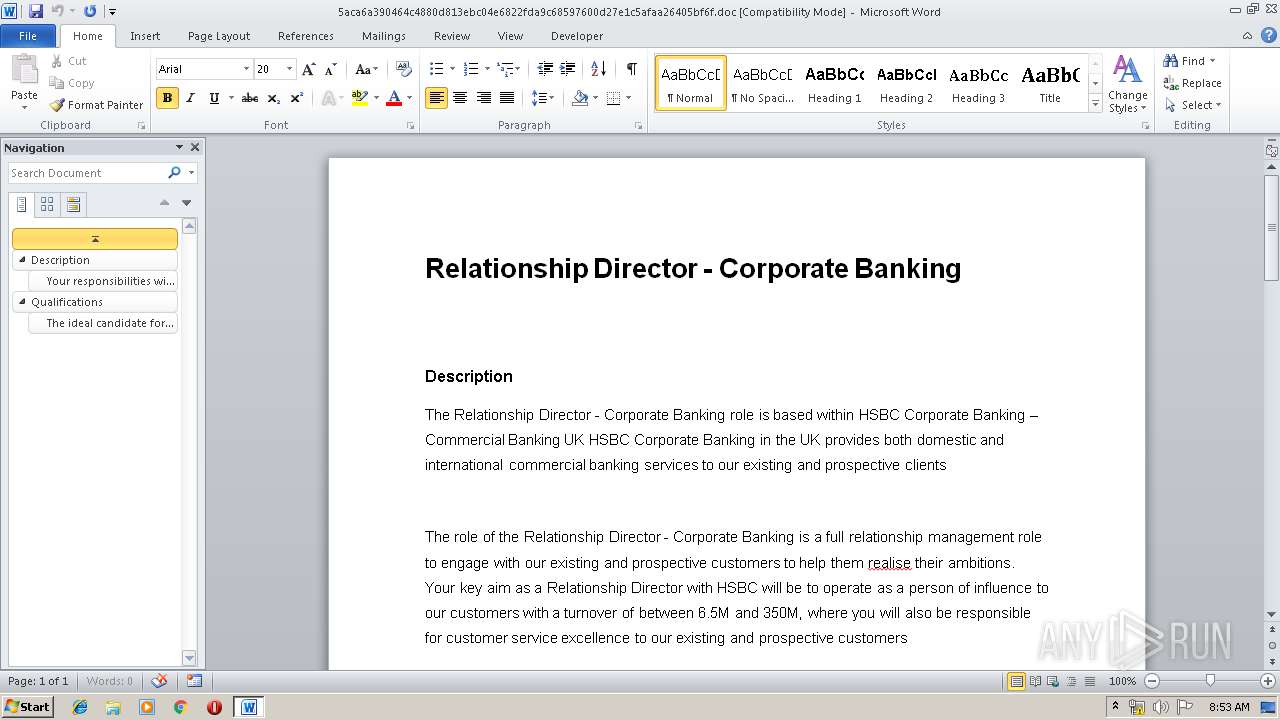
| 3772 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Job Description.doc | document | |
MD5:— | SHA256:— | |||
| 3772 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3772 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\dwm.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Domain | IP | Reputation |
|---|---|---|
deltaemis.com |
| unknown |