| File name: | VIGEM_setup.msi OBRIGATÓRIO .msi |
| Full analysis: | https://app.any.run/tasks/4477e475-18be-4ccd-97f5-4e2ab6c35cd2 |
| Verdict: | Malicious activity |
| Analysis date: | June 28, 2024, 23:18:28 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
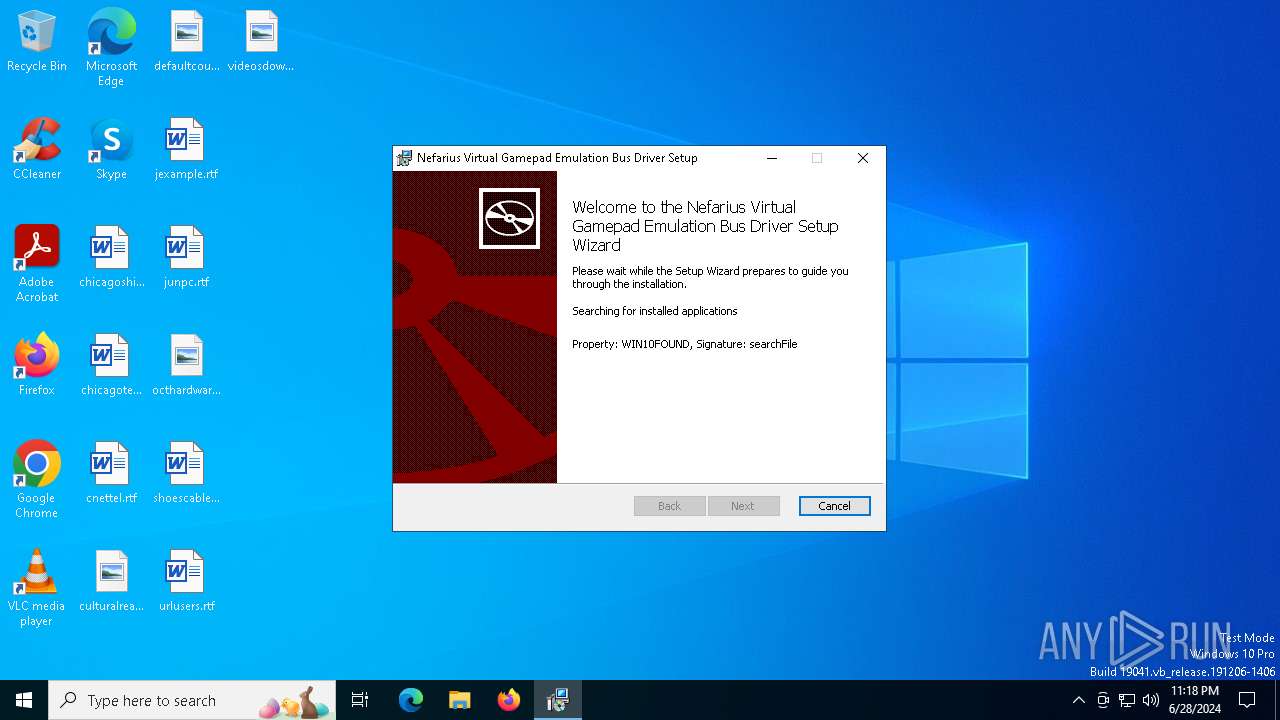
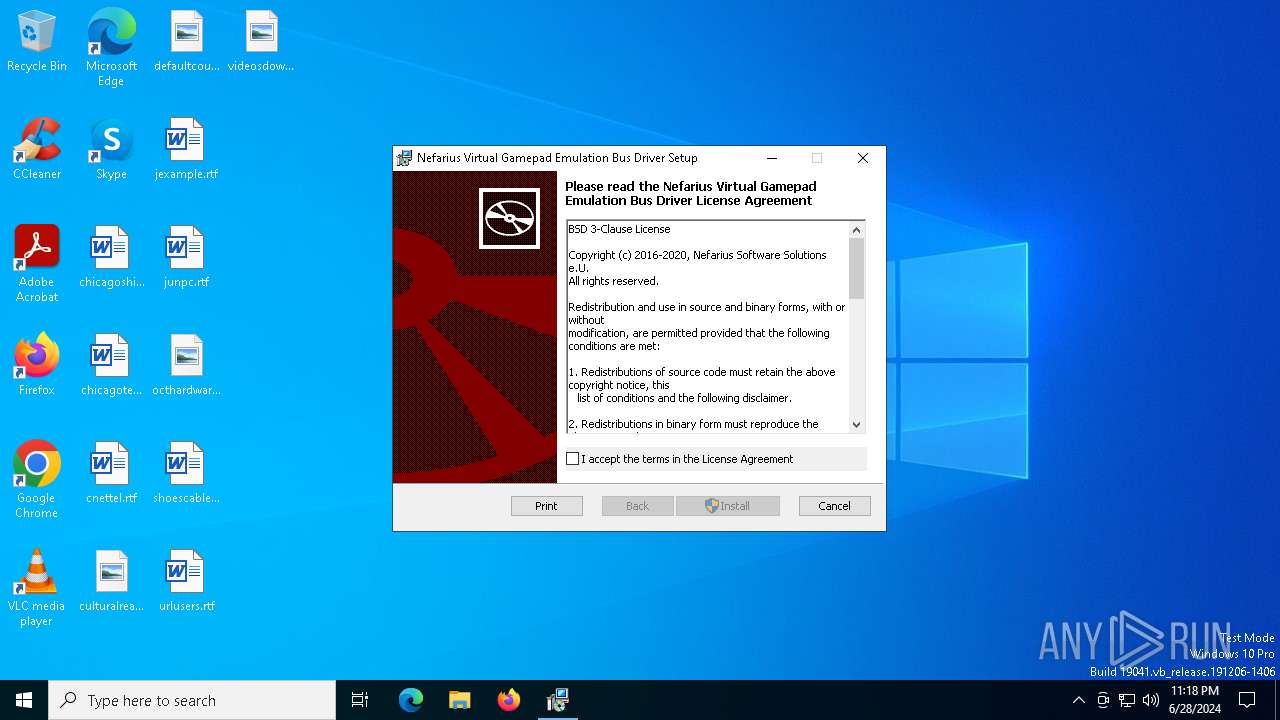
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Code page: 1252, Title: Installation Database, Subject: Nefarius Virtual Gamepad Emulation Bus Driver, Author: Nefarius Software Solutions e.U., Keywords: Installer, Comments: This installer database contains the logic and data required to install Nefarius Virtual Gamepad Emulation Bus Driver., Template: x64;1033, Revision Number: {7F4B9000-3545-4338-9F3B-4C0DAA5225EE}, Create Time/Date: Sat Dec 26 14:17:12 2020, Last Saved Time/Date: Sat Dec 26 14:17:12 2020, Number of Pages: 200, Number of Words: 2, Name of Creating Application: Windows Installer XML Toolset (3.11.2.4516), Security: 2 |
| MD5: | D8D2CFF2EAE7F1D956E3F8A2EDAF891D |
| SHA1: | BC33E35ED5D60C492BD6733462BD6CBC19C2CD59 |
| SHA256: | 5ABBBA8A4A07AAAEB50B4666183B2F243E0E5AD288026D2A9F3595ED237C4B28 |
| SSDEEP: | 24576:VJW67lorYxKSCKmCdX7mjqJ33XPqshpaa5ybHnrNcHrR:VJW6xorYxTCNCdX7mjqJ33/qsXaa5ybY |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 5036)
- msiexec.exe (PID: 5964)
- drvinst.exe (PID: 7120)
Creates a writable file in the system directory
- drvinst.exe (PID: 7120)
- devcon.exe (PID: 6916)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 5964)
- drvinst.exe (PID: 7120)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 5964)
Checks Windows Trust Settings
- msiexec.exe (PID: 5964)
- drvinst.exe (PID: 7120)
- devcon.exe (PID: 6916)
Executes as Windows Service
- VSSVC.exe (PID: 5268)
Creates files in the driver directory
- drvinst.exe (PID: 7120)
- devcon.exe (PID: 6916)
Executable content was dropped or overwritten
- drvinst.exe (PID: 7120)
Creates or modifies Windows services
- drvinst.exe (PID: 2132)
INFO
Reads security settings of Internet Explorer
- msiexec.exe (PID: 5036)
Reads the software policy settings
- msiexec.exe (PID: 5036)
- msiexec.exe (PID: 5964)
- devcon.exe (PID: 6916)
- drvinst.exe (PID: 7120)
Checks proxy server information
- msiexec.exe (PID: 5036)
Creates files or folders in the user directory
- msiexec.exe (PID: 5036)
Checks supported languages
- msiexec.exe (PID: 5964)
- msiexec.exe (PID: 6800)
- devcon.exe (PID: 6916)
- drvinst.exe (PID: 7120)
- drvinst.exe (PID: 2132)
- TextInputHost.exe (PID: 6436)
Reads the computer name
- msiexec.exe (PID: 5964)
- msiexec.exe (PID: 6800)
- devcon.exe (PID: 6916)
- TextInputHost.exe (PID: 6436)
- drvinst.exe (PID: 7120)
- drvinst.exe (PID: 2132)
Executable content was dropped or overwritten
- msiexec.exe (PID: 5964)
Reads the machine GUID from the registry
- msiexec.exe (PID: 5964)
- devcon.exe (PID: 6916)
- drvinst.exe (PID: 7120)
Creates a software uninstall entry
- msiexec.exe (PID: 5964)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | Nefarius Virtual Gamepad Emulation Bus Driver |
| Author: | Nefarius Software Solutions e.U. |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install Nefarius Virtual Gamepad Emulation Bus Driver. |
| Template: | x64;1033 |
| RevisionNumber: | {7F4B9000-3545-4338-9F3B-4C0DAA5225EE} |
| CreateDate: | 2020:12:26 14:17:12 |
| ModifyDate: | 2020:12:26 14:17:12 |
| Pages: | 200 |
| Words: | 2 |
| Software: | Windows Installer XML Toolset (3.11.2.4516) |
| Security: | Read-only recommended |
Total processes
188
Monitored processes
11
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2132 | DrvInst.exe "2" "211" "ROOT\SYSTEM\0001" "C:\WINDOWS\INF\oem1.inf" "oem1.inf:c14ce88408607219:ViGEmBus_Device:1.17.333.0:nefarius\vigembus\gen1," "429a86e87" "00000000000001C4" | C:\Windows\System32\drvinst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5036 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\VIGEM_setup.msi OBRIGATÓRIO .msi" | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5268 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5964 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6436 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 6564 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6576 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6800 | C:\Windows\syswow64\MsiExec.exe -Embedding 0C9658589ECBEB12371422A5069ACB4C E Global\MSI0000 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6916 | "C:\Program Files\Nefarius Software Solutions\Virtual Gamepad Emulation Bus Driver\devcon.exe" install "C:\Program Files\Nefarius Software Solutions\Virtual Gamepad Emulation Bus Driver\ViGEmBus.inf" Nefarius\ViGEmBus\Gen1 | C:\Program Files\Nefarius Software Solutions\Virtual Gamepad Emulation Bus Driver\devcon.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Windows (R) Win 7 DDK provider Integrity Level: SYSTEM Description: Windows Setup API Exit code: 0 Version: 10.0.10011.16384 Modules
| |||||||||||||||
| 6944 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | devcon.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
19 673
Read events
19 369
Write events
277
Delete events
27
Modification events
| (PID) Process: | (5964) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000C55F8C84B1C9DA014C17000018150000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5964) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000C55F8C84B1C9DA014C17000018150000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5964) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 48000000000000001EA41685B1C9DA014C17000018150000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5964) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000001EA41685B1C9DA014C17000018150000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5964) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 48000000000000009F912285B1C9DA014C17000018150000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5964) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000E5F62485B1C9DA014C17000018150000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5964) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (5964) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000E626DA85B1C9DA014C17000018150000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5964) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000006A8ADC85B1C9DA014C170000F8130000E80300000100000000000000000000009EB085FB9C285F4AA22DA131E1D6454C00000000000000000000000000000000 | |||
| (PID) Process: | (5268) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000003CEEDE85B1C9DA0194140000B8160000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
7
Suspicious files
25
Text files
5
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5964 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 5036 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\DA3B6E45325D5FFF28CF6BAD6065C907_9680AC525D270E357A3E938724263431 | binary | |
MD5:8C581BB173EF185CC009366753B53217 | SHA256:3D8F21EC8F28D733C9C9C4C34800E021D175F350610475A332CF93BA5AAE735B | |||
| 5964 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:57FB5BE1EA02E846748DB4C7CDC515E9 | SHA256:8D4E4C4A167420CFD19DCE8F5F5D0F627F4179582979AC151F270E8EA36530FF | |||
| 5964 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{fb85b09e-289c-4a5f-a22d-a131e1d6454c}_OnDiskSnapshotProp | binary | |
MD5:57FB5BE1EA02E846748DB4C7CDC515E9 | SHA256:8D4E4C4A167420CFD19DCE8F5F5D0F627F4179582979AC151F270E8EA36530FF | |||
| 5964 | msiexec.exe | C:\WINDOWS\TEMP\~DFE4E14CA32CC38443.TMP | binary | |
MD5:B1D9D1521F69695393B62EF6197D6713 | SHA256:460F302B4B4EB155EA600EB7E89E0682C6579E973A16AB2F6D30AE47D5D7F0E3 | |||
| 5964 | msiexec.exe | C:\Program Files\Nefarius Software Solutions\Virtual Gamepad Emulation Bus Driver\devcon-LICENSE | text | |
MD5:AAF054CD980283518EE307F0FA0EA54A | SHA256:507CEE67CFFB838349EE0E6209DEBD40686F81D5D1073088AB80C5FD8A17C5EB | |||
| 5036 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8890A77645B73478F5B1DED18ACBF795_C090A8C88B266C6FF99A97210E92B44D | binary | |
MD5:0C5DEB9E14309A4F7F56B1DE0D1EE5AD | SHA256:C6E94F4E72D9A5C8DA9565B75F79CD902C80F748E15992D78021664E1BB6A6A3 | |||
| 5036 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8890A77645B73478F5B1DED18ACBF795_C090A8C88B266C6FF99A97210E92B44D | der | |
MD5:E05A80FACEB88085DBDC919893410A03 | SHA256:F8EAFA8AD4836F4B397283E89A208D2CED5CEADCD9C0AA31B92A7A0A31B72649 | |||
| 5964 | msiexec.exe | C:\WINDOWS\Installer\{93D91F60-7C94-4A79-863F-EA713D2EB3F3}\ViGEm.ico | image | |
MD5:59DE0086D463FC413E91CFC13D519CDA | SHA256:2236616B17971F4C79E2B9D9B3B315E04CFFC3DF2E22D347DD95513294968781 | |||
| 5964 | msiexec.exe | C:\Program Files\Nefarius Software Solutions\Virtual Gamepad Emulation Bus Driver\ViGEmBus.sys | executable | |
MD5:87FE350C6FFE8D60CE58DBC16A2D091E | SHA256:8FB8402B7266FA9B9EA8841708317C8C25367B2947EEDA9B6462C0E4801F05A4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
70
DNS requests
49
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1544 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
5036 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAPxtOFfOoLxFJZ4s9fYR1w%3D | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | unknown |
5036 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSPwl%2BrBFlJbvzLXU1bGW08VysJ2wQUj%2Bh%2B8G0yagAFI8dwl2o6kP9r6tQCEAbleKgbyY4oq3sFsZHJmi0%3D | unknown | — | — | unknown |
1132 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1132 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
6636 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
4600 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
2140 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
6636 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2848 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3716 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1132 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5036 | msiexec.exe | 192.229.221.95:80 | — | EDGECAST | US | whitelisted |
1544 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1544 | svchost.exe | 192.229.221.95:80 | — | EDGECAST | US | whitelisted |
1060 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
r.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |