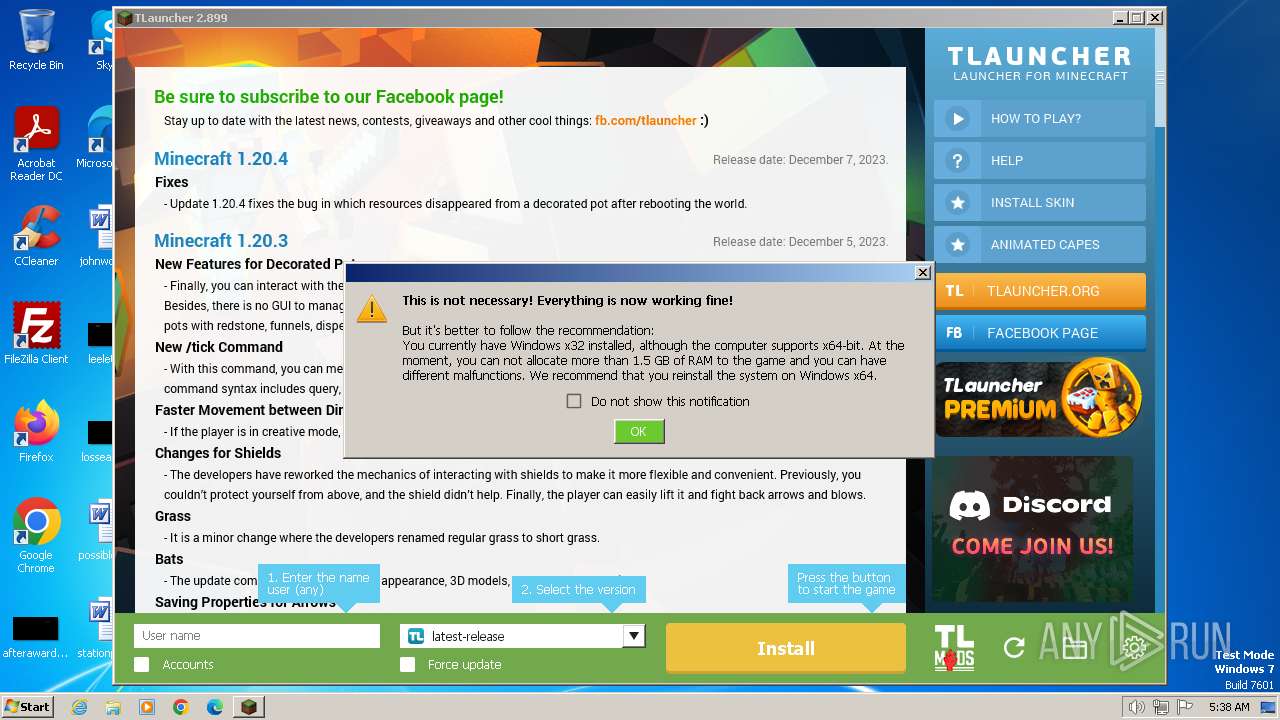
| File name: | TLauncher-2.86-Installer-1.0.1.exe |
| Full analysis: | https://app.any.run/tasks/a1ae0bbf-88be-4bae-8642-b2439ec2e25b |
| Verdict: | Malicious activity |
| Analysis date: | January 28, 2024, 05:36:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | F643BE370CC9763A17F7746B1B6A0243 |
| SHA1: | C65391F59A6E1421D783EAF43EB9661CFD476F82 |
| SHA256: | 5AB5F39D143B6FF77DF2FD5026AC8E4788EDFD3DE27A4E1FA4B420A7D2F61D38 |
| SSDEEP: | 196608:8R6LQpso7SM9BSHdBEhha1YG4GFSj0QeOFV6z/RFjp:3OHSM9BqEG1YDGFRQeiVoRFjp |
MALICIOUS
Drops the executable file immediately after the start
- TLauncher-2.86-Installer-1.0.1.exe (PID: 1880)
- irsetup.exe (PID: 2240)
- AdditionalExecuteTL.exe (PID: 2360)
- javaw.exe (PID: 3344)
Actions looks like stealing of personal data
- irsetup.exe (PID: 2240)
SUSPICIOUS
Executable content was dropped or overwritten
- TLauncher-2.86-Installer-1.0.1.exe (PID: 1880)
- irsetup.exe (PID: 2240)
- AdditionalExecuteTL.exe (PID: 2360)
- javaw.exe (PID: 3344)
Reads the Internet Settings
- TLauncher-2.86-Installer-1.0.1.exe (PID: 1880)
- irsetup.exe (PID: 2240)
- AdditionalExecuteTL.exe (PID: 2360)
- irsetup.exe (PID: 968)
- WMIC.exe (PID: 3772)
- WMIC.exe (PID: 3880)
- WMIC.exe (PID: 2340)
- WMIC.exe (PID: 3016)
Reads the Windows owner or organization settings
- irsetup.exe (PID: 2240)
- irsetup.exe (PID: 968)
Checks for Java to be installed
- irsetup.exe (PID: 2240)
- TLauncher.exe (PID: 3440)
Reads security settings of Internet Explorer
- irsetup.exe (PID: 2240)
- irsetup.exe (PID: 968)
Checks Windows Trust Settings
- irsetup.exe (PID: 2240)
- irsetup.exe (PID: 968)
Adds/modifies Windows certificates
- irsetup.exe (PID: 2240)
Reads settings of System Certificates
- irsetup.exe (PID: 2240)
- irsetup.exe (PID: 968)
- dxdiag.exe (PID: 552)
Reads Microsoft Outlook installation path
- irsetup.exe (PID: 2240)
Reads Internet Explorer settings
- irsetup.exe (PID: 2240)
Starts application with an unusual extension
- cmd.exe (PID: 3640)
- cmd.exe (PID: 3828)
- cmd.exe (PID: 296)
- cmd.exe (PID: 1892)
- cmd.exe (PID: 3528)
- cmd.exe (PID: 2808)
- cmd.exe (PID: 3076)
Starts CMD.EXE for commands execution
- javaw.exe (PID: 3344)
- javaw.exe (PID: 2132)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 3640)
- cmd.exe (PID: 3828)
Process requests binary or script from the Internet
- javaw.exe (PID: 3344)
- javaw.exe (PID: 2132)
The process drops C-runtime libraries
- javaw.exe (PID: 3344)
Process drops legitimate windows executable
- javaw.exe (PID: 3344)
Uses ICACLS.EXE to modify access control lists
- javaw.exe (PID: 2132)
Uses WMIC.EXE to obtain CPU information
- cmd.exe (PID: 296)
Uses WMIC.EXE to obtain quick Fix Engineering (patches) data
- cmd.exe (PID: 3076)
INFO
Checks supported languages
- TLauncher-2.86-Installer-1.0.1.exe (PID: 1880)
- irsetup.exe (PID: 2240)
- AdditionalExecuteTL.exe (PID: 2360)
- irsetup.exe (PID: 968)
- javaw.exe (PID: 3344)
- TLauncher.exe (PID: 3440)
- chcp.com (PID: 3752)
- chcp.com (PID: 3788)
- javaw.exe (PID: 2132)
- chcp.com (PID: 2128)
- chcp.com (PID: 1796)
- chcp.com (PID: 3504)
- chcp.com (PID: 2544)
- chcp.com (PID: 2560)
Reads the computer name
- TLauncher-2.86-Installer-1.0.1.exe (PID: 1880)
- irsetup.exe (PID: 2240)
- irsetup.exe (PID: 968)
- AdditionalExecuteTL.exe (PID: 2360)
- javaw.exe (PID: 3344)
- javaw.exe (PID: 2132)
Create files in a temporary directory
- TLauncher-2.86-Installer-1.0.1.exe (PID: 1880)
- irsetup.exe (PID: 2240)
- AdditionalExecuteTL.exe (PID: 2360)
- irsetup.exe (PID: 968)
- javaw.exe (PID: 3344)
- javaw.exe (PID: 2132)
Checks proxy server information
- irsetup.exe (PID: 2240)
- irsetup.exe (PID: 968)
Reads the machine GUID from the registry
- irsetup.exe (PID: 2240)
- irsetup.exe (PID: 968)
- javaw.exe (PID: 3344)
- javaw.exe (PID: 2132)
Creates files or folders in the user directory
- irsetup.exe (PID: 2240)
- javaw.exe (PID: 3344)
- irsetup.exe (PID: 968)
- javaw.exe (PID: 2132)
Creates files in the program directory
- irsetup.exe (PID: 2240)
- javaw.exe (PID: 3344)
- javaw.exe (PID: 2132)
Reads security settings of Internet Explorer
- dxdiag.exe (PID: 552)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE Yoda's Crypter (75.7) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.8) |
| .exe | | | Generic Win/DOS Executable (5.7) |
| .exe | | | DOS Executable Generic (5.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:01:03 20:13:08+01:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 23552 |
| InitializedDataSize: | 142336 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2ce1 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.1.0 |
| ProductVersionNumber: | 2.86.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | ASCII |
| Comments: | TLauncher Setup |
| CompanyName: | TLauncher Inc. |
| FileDescription: | TLauncher Setup |
| FileVersion: | 1.0.1.0 |
| InternalName: | TLauncher |
| LegalCopyright: | TLauncher Copyright © 2022 |
| LegalTrademarks: | TLauncher |
| OriginalFileName: | suf_launch.exe |
| ProductName: | TLauncher |
| ProductVersion: | 2.86.0.0 |
Total processes
86
Monitored processes
30
Malicious processes
8
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 296 | cmd.exe /C chcp 437 & wmic CPU get NAME | C:\Windows\System32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 552 | dxdiag /whql:off /t C:\Users\admin\AppData\Roaming\.minecraft\logs\tlauncher\dxdiag.txt | C:\Windows\System32\dxdiag.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft DirectX Diagnostic Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 968 | "C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_1\irsetup.exe" /S:C:\Users\admin\AppData\Local\Temp\setuparguments.ini __IRAOFF:1814730 "__IRAFN:C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\AdditionalExecuteTL.exe" "__IRCT:3" "__IRTSS:1839152" "__IRSID:S-1-5-21-1302019708-1500728564-335382590-1000" | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_1\irsetup.exe | AdditionalExecuteTL.exe | ||||||||||||
User: admin Company: Indigo Rose Corporation Integrity Level: HIGH Description: Setup Application Exit code: 0 Version: 9.5.3.0 Modules
| |||||||||||||||
| 1036 | "C:\Users\admin\Downloads\TLauncher-2.86-Installer-1.0.1.exe" | C:\Users\admin\Downloads\TLauncher-2.86-Installer-1.0.1.exe | — | explorer.exe | |||||||||||
User: admin Company: TLauncher Inc. Integrity Level: MEDIUM Description: TLauncher Setup Exit code: 3221226540 Version: 1.0.1.0 Modules
| |||||||||||||||
| 1796 | chcp 437 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1880 | "C:\Users\admin\Downloads\TLauncher-2.86-Installer-1.0.1.exe" | C:\Users\admin\Downloads\TLauncher-2.86-Installer-1.0.1.exe | explorer.exe | ||||||||||||
User: admin Company: TLauncher Inc. Integrity Level: HIGH Description: TLauncher Setup Exit code: 0 Version: 1.0.1.0 Modules
| |||||||||||||||
| 1892 | cmd.exe /C chcp 437 & systeminfo | C:\Windows\System32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2128 | chcp 437 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2132 | C:\Users\admin\AppData\Roaming\.tlauncher\jvms\jre1.8.0_111\bin\javaw.exe -Xmx1024m -Dfile.encoding=UTF8 -cp C:\Users\admin\AppData\Roaming\.minecraft\TLauncher.exe;C:\Users\admin\AppData\Roaming\.minecraft\tlauncher_libraries\com\google\inject\guice\4.1.0\guice-4.1.0.jar;C:\Users\admin\AppData\Roaming\.minecraft\tlauncher_libraries\com\google\inject\extentions\guice-assistedinject\4.1.0\guice-assistedinject-4.1.0.jar;C:\Users\admin\AppData\Roaming\.minecraft\tlauncher_libraries\javax\inject\javax.inject\1\javax.inject-1.jar;C:\Users\admin\AppData\Roaming\.minecraft\tlauncher_libraries\aopalliance\aopalliance\1.0\aopalliance-1.0.jar;C:\Users\admin\AppData\Roaming\.minecraft\tlauncher_libraries\com\google\guava\guava\19.0\guava-19.0.jar;C:\Users\admin\AppData\Roaming\.minecraft\tlauncher_libraries\org\apache\commons\commons-lang3\3.4\commons-lang3-3.4.jar;C:\Users\admin\AppData\Roaming\.minecraft\tlauncher_libraries\net\sf\jopt-simple\jopt-simple\4.9\jopt-simple-4.9.jar;C:\Users\admin\AppData\Roaming\.minecraft\tlauncher_libraries\log4j\log4j\1.2.17\log4j-1.2.17.jar;C:\Users\admin\AppData\Roaming\.minecraft\tlauncher_libraries\org\tukaani\xz\1.5\xz-1.5.jar;C:\Users\admin\AppData\Roaming\.minecraft\tlauncher_libraries\org\tlauncher\picture-bundle\3.72\picture-bundle-3.72.jar;C:\Users\admin\AppData\Roaming\.minecraft\tlauncher_libraries\org\tlauncher\skin-server-API\1.0\skin-server-API-1.0.jar;C:\Users\admin\AppData\Roaming\.minecraft\tlauncher_libraries\org\tlauncher\tlauncher-resource\1.4\tlauncher-resource-1.4.jar;C:\Users\admin\AppData\Roaming\.minecraft\tlauncher_libraries\com\github\junrar\junrar\0.7\junrar-0.7.jar;C:\Users\admin\AppData\Roaming\.minecraft\tlauncher_libraries\dnsjava\dnsjava\2.1.8\dnsjava-2.1.8.jar;C:\Users\admin\AppData\Roaming\.minecraft\tlauncher_libraries\org\apache\httpcomponents\fluent-hc\4.5.13\fluent-hc-4.5.13.jar;C:\Users\admin\AppData\Roaming\.minecraft\tlauncher_libraries\org\apache\logging\log4j\log4j-core\2.14.1\log4j-core-2.14.1.jar; org.tlauncher.tlauncher.rmo.TLauncher | C:\Users\admin\AppData\Roaming\.tlauncher\jvms\jre1.8.0_111\bin\javaw.exe | javaw.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.1110.14 Modules
| |||||||||||||||
| 2240 | "C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\irsetup.exe" __IRAOFF:1908426 "__IRAFN:C:\Users\admin\Downloads\TLauncher-2.86-Installer-1.0.1.exe" "__IRCT:3" "__IRTSS:22693301" "__IRSID:S-1-5-21-1302019708-1500728564-335382590-1000" | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\irsetup.exe | TLauncher-2.86-Installer-1.0.1.exe | ||||||||||||
User: admin Company: Indigo Rose Corporation Integrity Level: HIGH Description: Setup Application Exit code: 0 Version: 9.5.3.0 Modules
| |||||||||||||||
Total events
18 821
Read events
18 656
Write events
149
Delete events
16
Modification events
| (PID) Process: | (1880) TLauncher-2.86-Installer-1.0.1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1880) TLauncher-2.86-Installer-1.0.1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1880) TLauncher-2.86-Installer-1.0.1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1880) TLauncher-2.86-Installer-1.0.1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2240) irsetup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2240) irsetup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005B010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2240) irsetup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2240) irsetup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2240) irsetup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2240) irsetup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
131
Suspicious files
66
Text files
578
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2240 | irsetup.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\irsetup.dat | — | |
MD5:— | SHA256:— | |||
| 2240 | irsetup.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\IRIMG1.PNG | image | |
MD5:6EF1AF4A2154CB5D00912ABE2FAE2B1F | SHA256:CDC1A8A27707375BBF63B018350D6B5AAD10F34E3D1AF3A0FE0B039FDB0BC453 | |||
| 2240 | irsetup.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\IRIMG4.PNG | image | |
MD5:5F2C2AC250C121473845F3D6750A2244 | SHA256:6A0E8295FD59BBD53E192D6C5DBE6EECF16C6E0C10B36588B00C5436F8A4F048 | |||
| 2240 | irsetup.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\IRIMG5.PNG | image | |
MD5:A0586C49D30229FD9DE85986F9C11A65 | SHA256:8B6F15460D949D6DDE593D329B86C4C7C2B6DC5CA8E1103D6F3E5CDC5EC18510 | |||
| 1880 | TLauncher-2.86-Installer-1.0.1.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\lua5.1.dll | executable | |
MD5:80D93D38BADECDD2B134FE4699721223 | SHA256:C572A6103AF1526F97E708A229A532FD02100A52B949F721052107F1F55E0C59 | |||
| 1880 | TLauncher-2.86-Installer-1.0.1.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\irsetup.exe | executable | |
MD5:1313BB5DF6C6E0D5C358735044FBEBEF | SHA256:7590D0F21687327812A6C61D0429C6DF1345B97C53AD7115F03BD4CB2E4F4C8D | |||
| 2240 | irsetup.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\IRIMG3.PNG | image | |
MD5:07A3B8FC5002FC45C2B85B4DA8707867 | SHA256:42F065601E38B4EC134F94ABFA2FEF6E4DEE23E04A35DBAFB442460090983F87 | |||
| 2240 | irsetup.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\IRIMG7.PNG | image | |
MD5:60C4499189D11376C387660BE96A6B06 | SHA256:64018D99D1A929066EE3F0E9B66E83D014B89D30D4EEDD7D09CF92D004660041 | |||
| 2240 | irsetup.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\IRIMG14.PNG | image | |
MD5:3B9CFD5A0D35F63818CAC4F545384EE7 | SHA256:F88C02BDA30EBC3B7644DBBC58A97447BC98B8E8B52A294D7B649900536EEFAE | |||
| 2240 | irsetup.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\IRIMG17.PNG | image | |
MD5:F60D7EFEB43C03689D0ACDCEC907FE29 | SHA256:207FCD3D7FCB34BDF8DD9A69A572EBEF70D5B3F1C3325F95C3371E2E108D9066 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
37
DNS requests
15
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
968 | irsetup.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f9d50ae334969db8 | unknown | — | — | unknown |
3344 | javaw.exe | GET | 302 | 78.46.66.120:80 | http://res.tlauncher.org/b/libraries/org/tlauncher/picture-bundle/3.72/picture-bundle-3.72.jar | unknown | — | — | unknown |
3344 | javaw.exe | GET | 302 | 78.46.66.120:80 | http://res.tlauncher.org/b/client/jre/windows/jre-8u111-windows-i586.tar.gz | unknown | — | — | unknown |
968 | irsetup.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | binary | 2.18 Kb | unknown |
1080 | svchost.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?3e412f7b4eff0943 | unknown | compressed | 65.2 Kb | unknown |
2132 | javaw.exe | HEAD | 200 | 104.20.64.88:80 | http://page.tlauncher.org/ | unknown | — | — | unknown |
2132 | javaw.exe | GET | 200 | 104.21.70.46:80 | http://img.fastrepo.org/update/downloads/configs/client/video/tl-discord-en.png | unknown | image | 49.2 Kb | unknown |
2132 | javaw.exe | GET | 200 | 104.20.65.88:80 | http://repo.tlauncher.org/update/downloads/configs/inner_servers-1.1.json | unknown | text | 5.02 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2240 | irsetup.exe | 104.20.64.88:443 | dl2.tlauncher.org | CLOUDFLARENET | — | unknown |
968 | irsetup.exe | 104.20.65.88:443 | dl2.tlauncher.org | CLOUDFLARENET | — | unknown |
968 | irsetup.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
968 | irsetup.exe | 104.18.38.233:80 | ocsp.usertrust.com | CLOUDFLARENET | — | shared |
2240 | irsetup.exe | 46.4.112.215:443 | advancedrepository.com | Hetzner Online GmbH | DE | unknown |
3344 | javaw.exe | 78.46.66.120:80 | res.tlauncher.org | Hetzner Online GmbH | DE | unknown |
3344 | javaw.exe | 104.20.65.88:443 | dl2.tlauncher.org | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dl2.tlauncher.org |
| unknown |
tlauncher.org |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
advancedrepository.com |
| unknown |
res.tlauncher.org |
| whitelisted |
cl2-res.tlauncher.org |
| unknown |
page.tlauncher.org |
| unknown |
repo.tlauncher.org |
| whitelisted |
img.tlauncher.org |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3344 | javaw.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |
3344 | javaw.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |