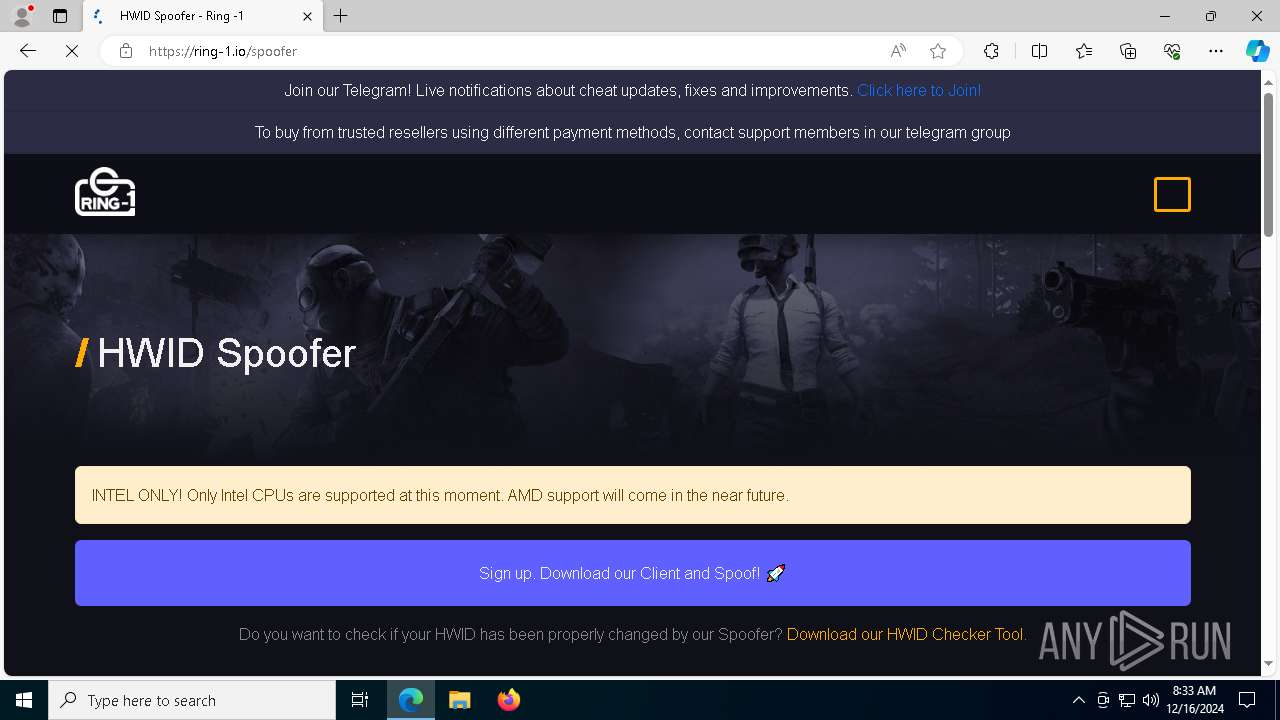
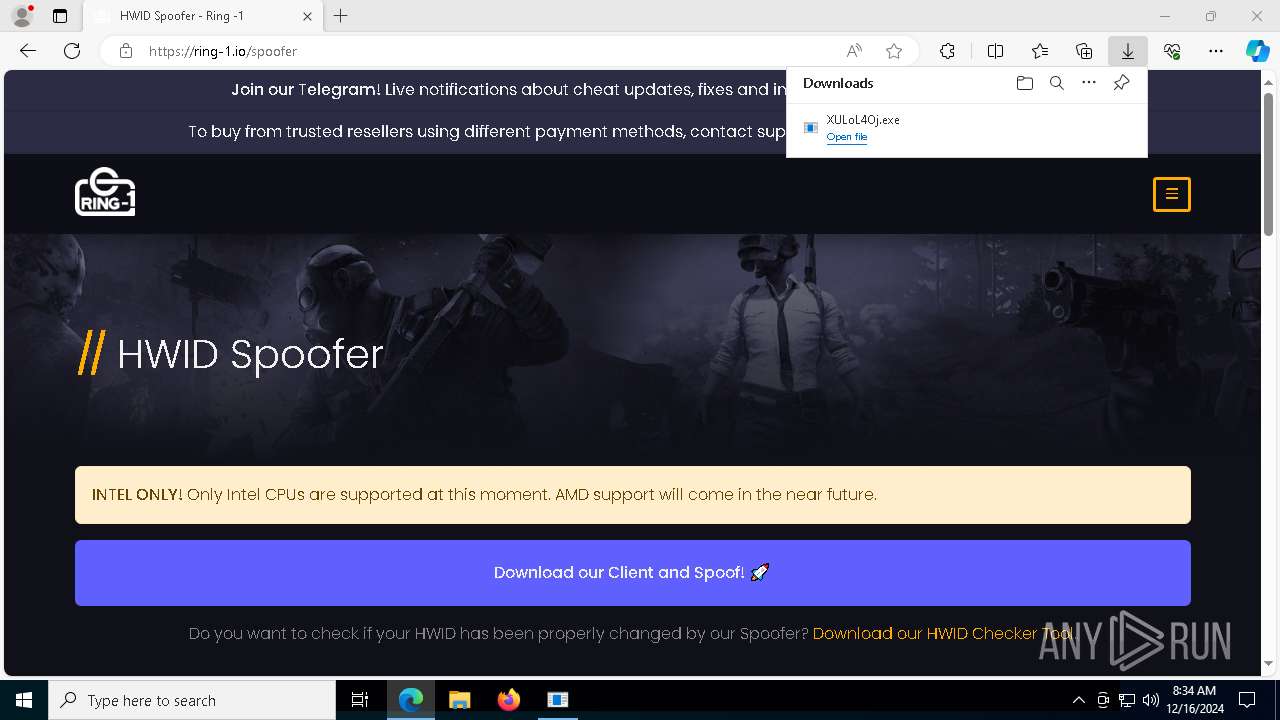
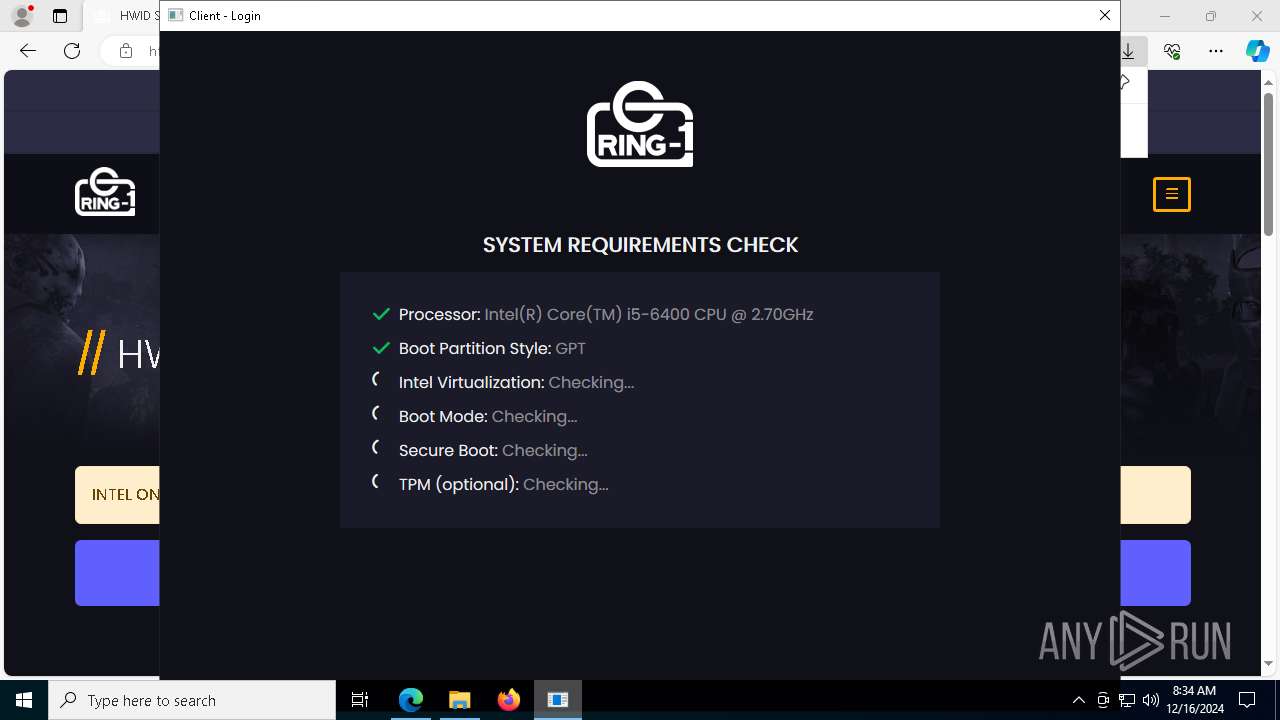
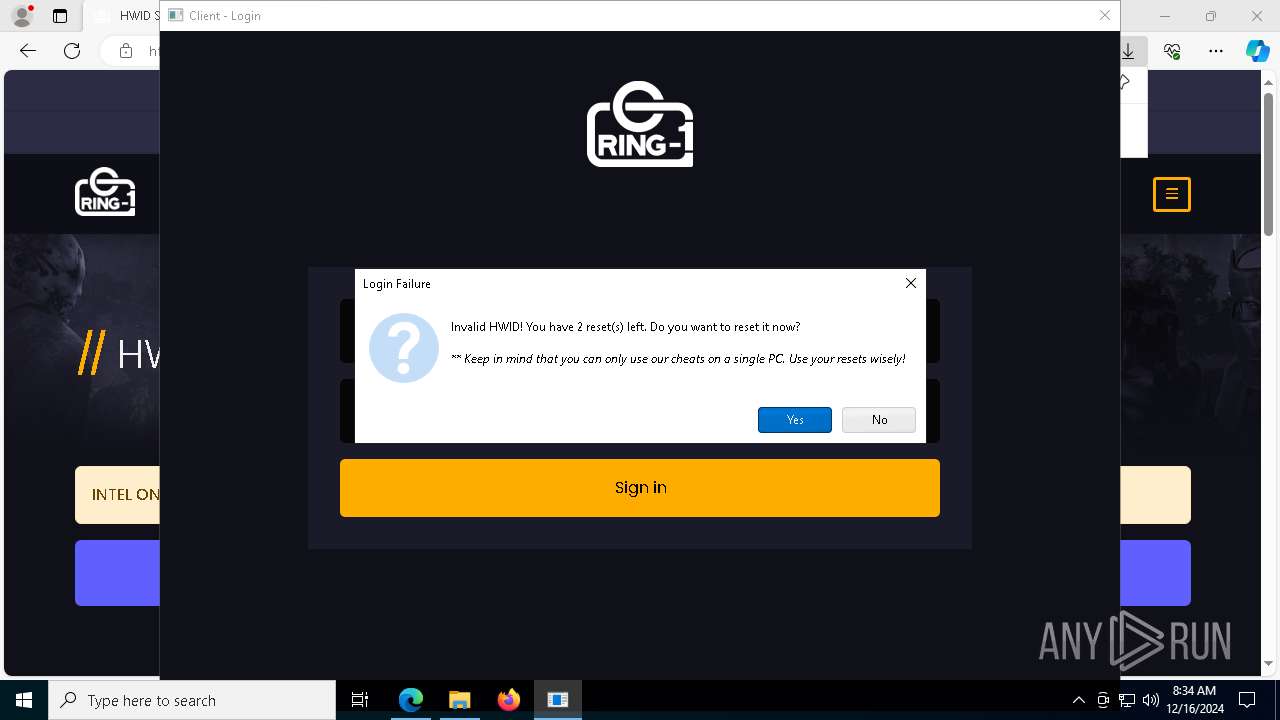
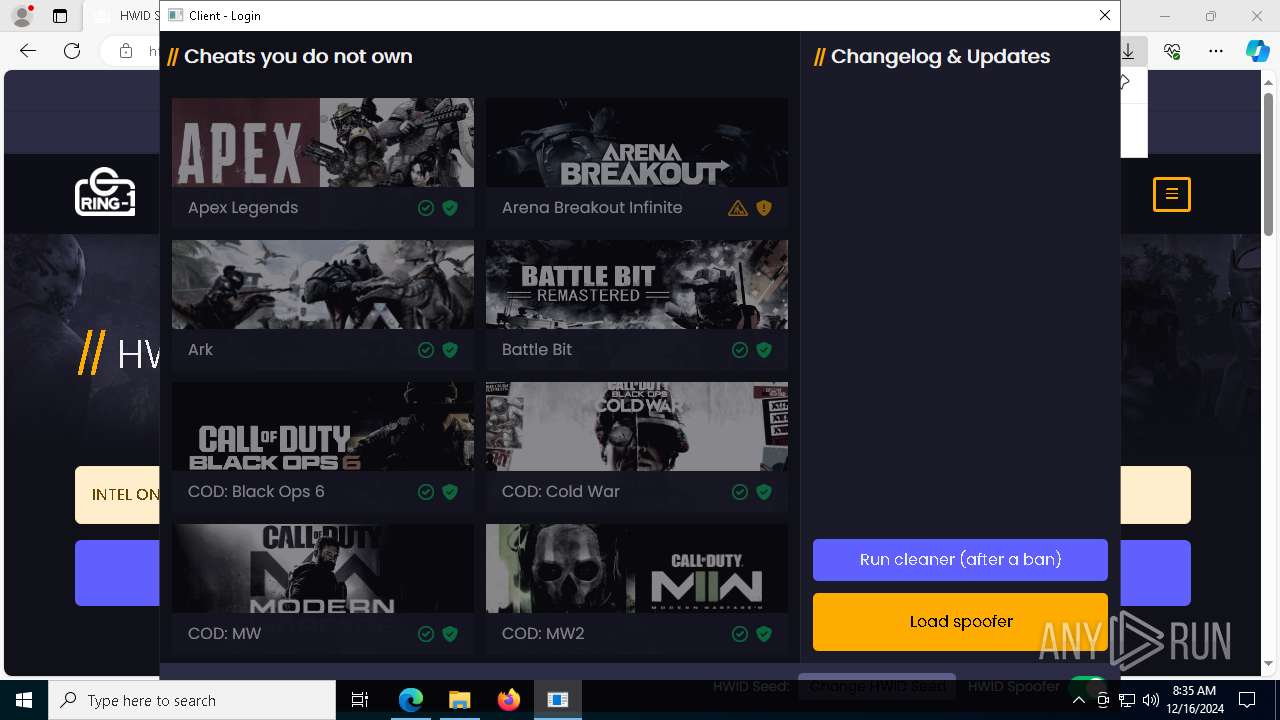
| URL: | https://ring-1.io/spoofer |
| Full analysis: | https://app.any.run/tasks/2c7dcbb1-68ed-49a9-86a2-7d2671243ae3 |
| Verdict: | Malicious activity |
| Analysis date: | December 16, 2024, 08:33:24 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | E3D5B0BA66991C333CA3D215A85A72C6 |
| SHA1: | E317EA84566ABFE6E855BAEF66FDF9B51ABBBF42 |
| SHA256: | 5AA723E39A16127D117F5CABD20D3E64A7D221732C81A03EDCE1CE8FC1960FE7 |
| SSDEEP: | 3:N8PXyn:2q |
MALICIOUS
Starts NET.EXE for service management
- net.exe (PID: 3792)
- net.exe (PID: 7556)
- XULoL4Oj.exe (PID: 4320)
- net.exe (PID: 7948)
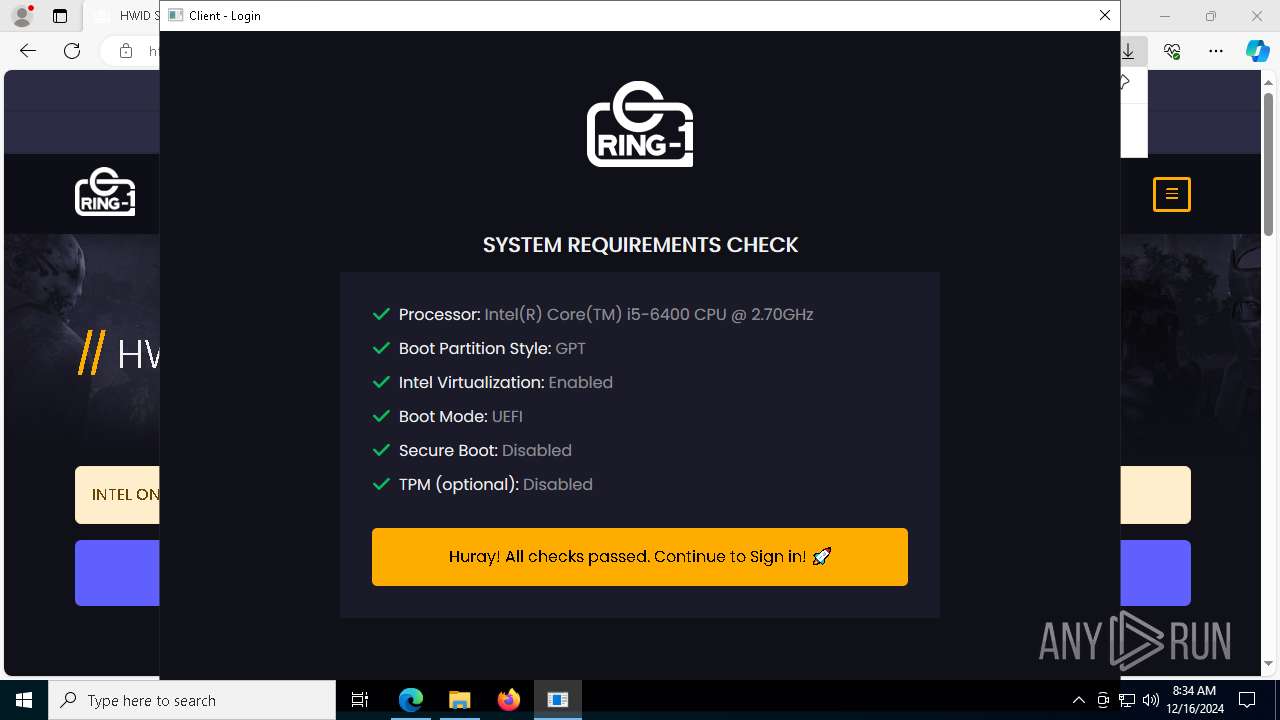
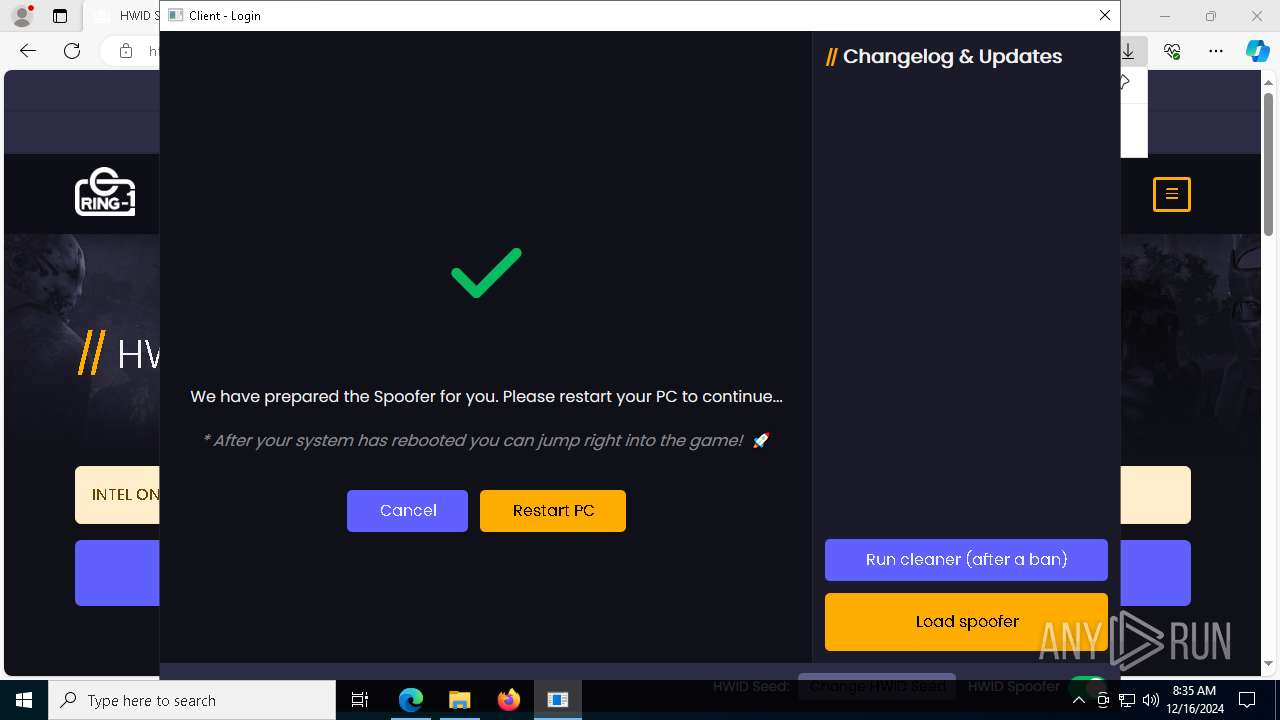
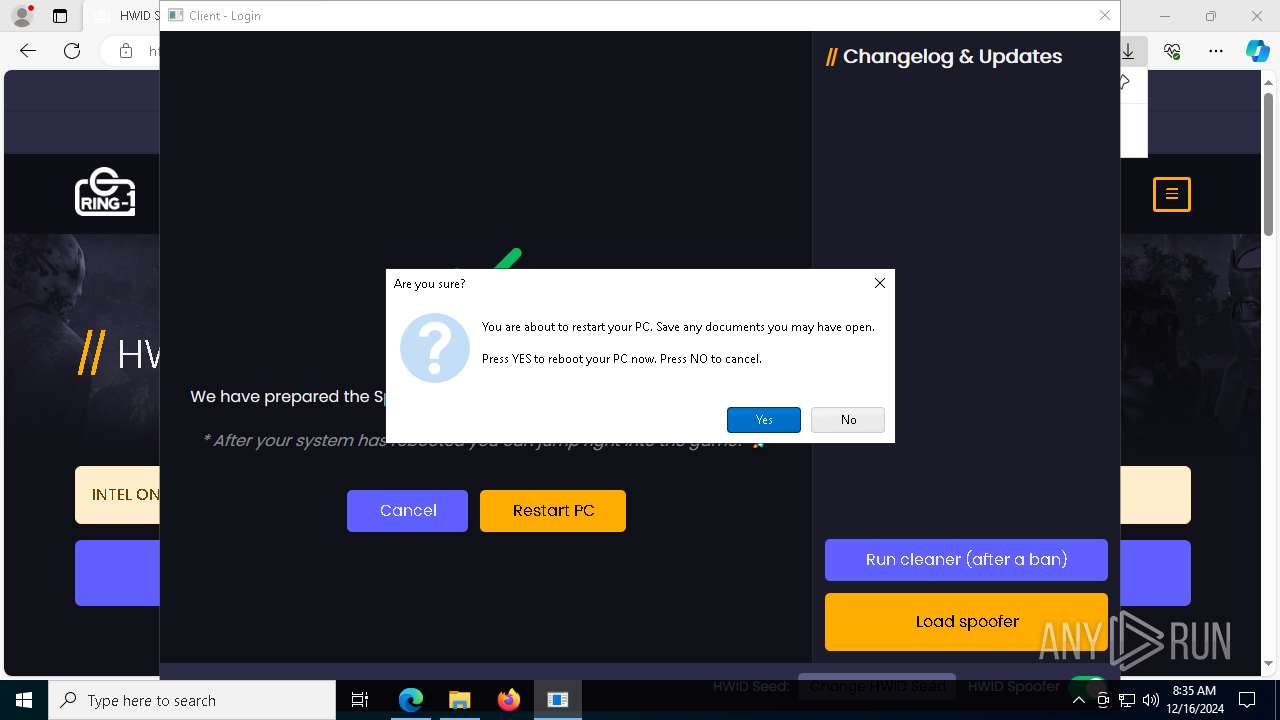
Modifies EFI boot file
- XULoL4Oj.exe (PID: 4320)
SUSPICIOUS
Uses WMIC.EXE to obtain CPU information
- XULoL4Oj.exe (PID: 4320)
Manipulates environment variables
- powershell.exe (PID: 7204)
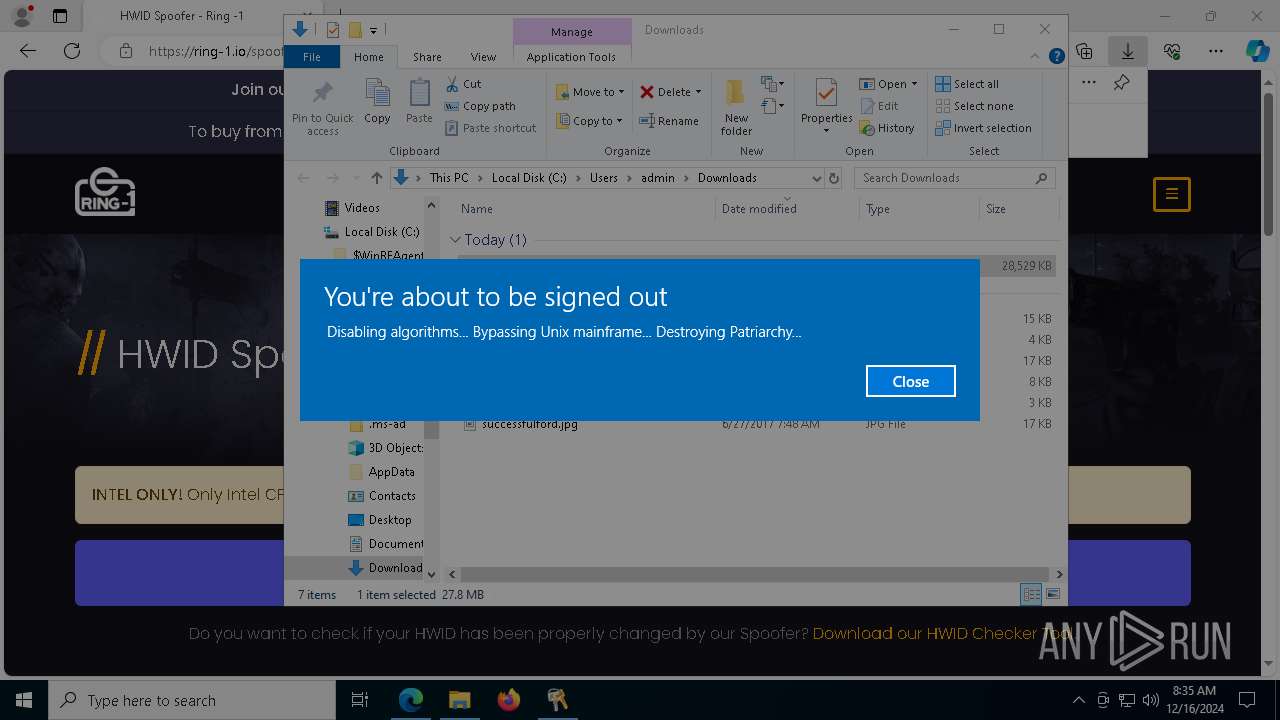
Removes files via Powershell
- powershell.exe (PID: 7872)
- powershell.exe (PID: 5576)
- powershell.exe (PID: 8016)
- powershell.exe (PID: 7472)
- powershell.exe (PID: 6756)
- powershell.exe (PID: 7832)
- powershell.exe (PID: 8156)
- powershell.exe (PID: 4160)
- powershell.exe (PID: 8128)
- powershell.exe (PID: 3032)
- powershell.exe (PID: 3144)
- powershell.exe (PID: 8160)
Starts POWERSHELL.EXE for commands execution
- XULoL4Oj.exe (PID: 4320)
Reads the BIOS version
- XULoL4Oj.exe (PID: 4320)
Starts SC.EXE for service management
- XULoL4Oj.exe (PID: 4320)
Query current time using 'w32tm.exe'
- XULoL4Oj.exe (PID: 4320)
Hides errors and continues executing the command without stopping
- powershell.exe (PID: 5576)
- powershell.exe (PID: 7472)
- powershell.exe (PID: 8016)
- powershell.exe (PID: 6756)
- powershell.exe (PID: 7832)
- powershell.exe (PID: 8156)
- powershell.exe (PID: 3032)
- powershell.exe (PID: 4160)
- powershell.exe (PID: 3144)
- powershell.exe (PID: 8128)
- powershell.exe (PID: 8160)
Starts CMD.EXE for commands execution
- XULoL4Oj.exe (PID: 4320)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 5488)
- cmd.exe (PID: 5004)
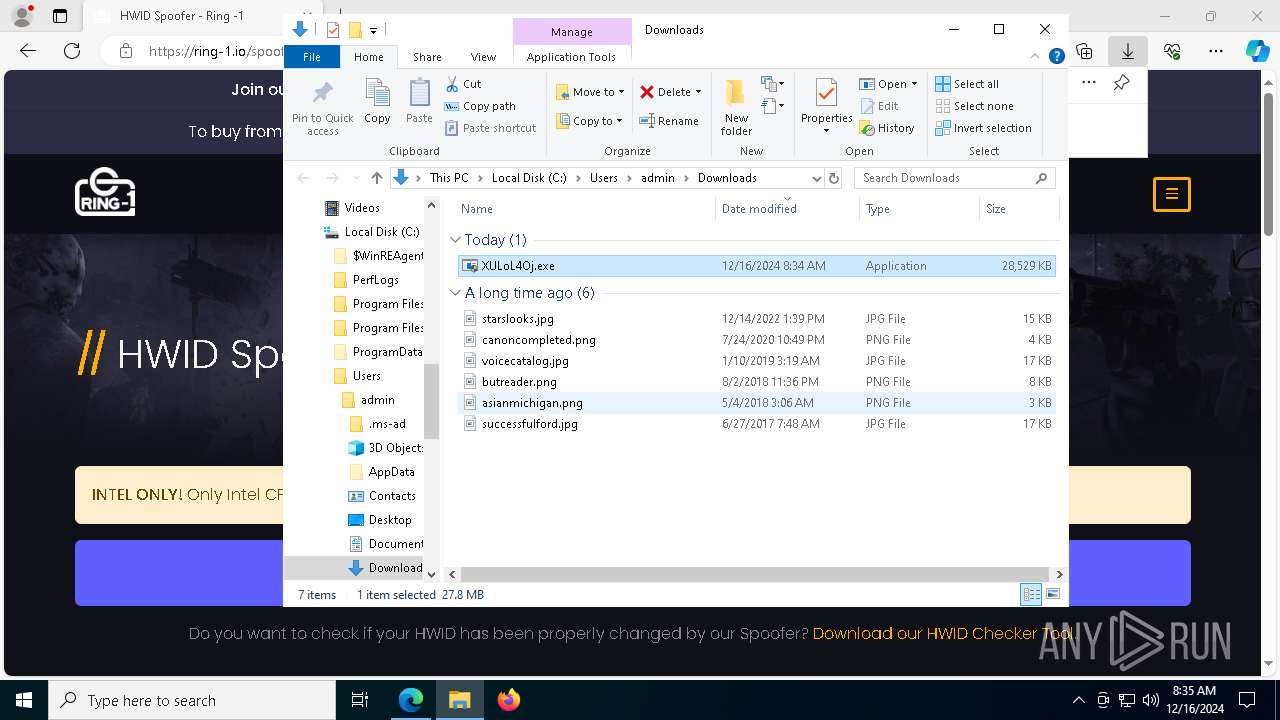
Executable content was dropped or overwritten
- XULoL4Oj.exe (PID: 4320)
Process drops legitimate windows executable
- XULoL4Oj.exe (PID: 4320)
INFO
Process checks whether UAC notifications are on
- XULoL4Oj.exe (PID: 4320)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7872)
- powershell.exe (PID: 2280)
Reads the computer name
- identity_helper.exe (PID: 7816)
Executable content was dropped or overwritten
- msedge.exe (PID: 6376)
- msedge.exe (PID: 2216)
Checks supported languages
- identity_helper.exe (PID: 7816)
- XULoL4Oj.exe (PID: 4320)
Reads Environment values
- identity_helper.exe (PID: 7816)
Sends debugging messages
- XULoL4Oj.exe (PID: 4320)
Themida protector has been detected
- XULoL4Oj.exe (PID: 4320)
Application launched itself
- msedge.exe (PID: 2216)
The sample compiled with english language support
- XULoL4Oj.exe (PID: 4320)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
417
Monitored processes
285
Malicious processes
2
Suspicious processes
11
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 68 | sc stop "SysMain" | C:\Windows\System32\sc.exe | — | XULoL4Oj.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1062 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 396 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3688 --field-trial-handle=2372,i,14186417735508817514,8526281741101954829,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 444 | C:\WINDOWS\system32\net1 stop w32time | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 524 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 640 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | fsutil.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | w32tm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 648 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | fsutil.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | mountvol P: /D | C:\Windows\System32\mountvol.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Mount Volume Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 772 | sc stop "PcaSvc" | C:\Windows\System32\sc.exe | — | XULoL4Oj.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1062 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 836 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | fsutil.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
69 965
Read events
69 773
Write events
152
Delete events
40
Modification events
| (PID) Process: | (2216) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2216) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2216) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2216) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (2216) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: C8306D51F5872F00 | |||
| (PID) Process: | (2216) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: A8C37551F5872F00 | |||
| (PID) Process: | (2216) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328474 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {3E565825-36C0-4771-BE78-75D867FF0D69} | |||
| (PID) Process: | (2216) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328474 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {409E712C-E7FF-476E-BD7F-DC06960CB9B5} | |||
| (PID) Process: | (2216) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328474 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {66F393B4-7FEC-4B85-9234-9A2D2E621FAB} | |||
| (PID) Process: | (2216) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328474 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {3F6BC8FD-C036-4975-9223-BBCDB1E998A9} | |||
Executable files
9
Suspicious files
174
Text files
90
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2216 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF135392.TMP | — | |
MD5:— | SHA256:— | |||
| 2216 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF135392.TMP | — | |
MD5:— | SHA256:— | |||
| 2216 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF135392.TMP | — | |
MD5:— | SHA256:— | |||
| 2216 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2216 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2216 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF1353a1.TMP | — | |
MD5:— | SHA256:— | |||
| 2216 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2216 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2216 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF1353c1.TMP | — | |
MD5:— | SHA256:— | |||
| 2216 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
109
DNS requests
100
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6796 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
8072 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8072 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5536 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/c08f1970-45bc-4dbe-8166-4ecef7a1f617?P1=1734853041&P2=404&P3=2&P4=ECNqKm4CKxntZAuqFoglJdhicViSMQ7im9q36bxTnIqHjwx6ikhXYFRYMdlFFicBDBatQ2A6fK7KyyHcdD0iyg%3d%3d | unknown | — | — | whitelisted |
5536 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/c08f1970-45bc-4dbe-8166-4ecef7a1f617?P1=1734853041&P2=404&P3=2&P4=ECNqKm4CKxntZAuqFoglJdhicViSMQ7im9q36bxTnIqHjwx6ikhXYFRYMdlFFicBDBatQ2A6fK7KyyHcdD0iyg%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5496 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
6376 | msedge.exe | 35.190.80.1:443 | a.nel.cloudflare.com | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2216 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6376 | msedge.exe | 188.114.96.3:443 | ring-1.io | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
ring-1.io |
| unknown |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
a.nel.cloudflare.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6376 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6376 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6376 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
6376 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
6376 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6376 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
Process | Message |
|---|---|
XULoL4Oj.exe | attempt to get/set state 'reduce' on null while media expression evaluation at (this://app/assets/fontawesome/fontawesome.css(272))
|
XULoL4Oj.exe | in @font-face statement font resource, this://app/assets/fontawesome/webfonts/fa-duotone-900.ttf is not available at (this://app/assets/fontawesome/fontawesome.css(14967))
|
XULoL4Oj.exe | in @font-face statement font resource, this://app/assets/fontawesome/webfonts/fa-light-300.ttf is not available at (this://app/assets/fontawesome/fontawesome.css(27623))
|
XULoL4Oj.exe | in @font-face statement font resource, this://app/assets/fontawesome/webfonts/fa-thin-100.ttf is not available at (this://app/assets/fontawesome/fontawesome.css(27659))
|
XULoL4Oj.exe | in @font-face statement font resource, this://app/assets/fontawesome/webfonts/fa-duotone-900.ttf is not available at (this://app/assets/fontawesome/fontawesome.css(27698))
|
XULoL4Oj.exe | in @font-face statement font resource, this://app/assets/fontawesome/webfonts/fa-light-300.ttf is not available at (this://app/assets/fontawesome/fontawesome.css(27691))
|
XULoL4Oj.exe | in @font-face statement font resource, this://app/assets/fontawesome/webfonts/fa-v4compatibility.ttf is not available at (this://app/assets/fontawesome/fontawesome.css(27724))
|
XULoL4Oj.exe | attempt to get/set state 'reduce' on null while media expression evaluation at (this://app/assets/fontawesome/fontawesome.css(272))
|
XULoL4Oj.exe | attempt to get/set state 'reduce' on null while media expression evaluation at (this://app/assets/fontawesome/fontawesome.css(272))
|
XULoL4Oj.exe | attempt to get/set state 'reduce' on null while media expression evaluation at (this://app/assets/fontawesome/fontawesome.css(272))
|