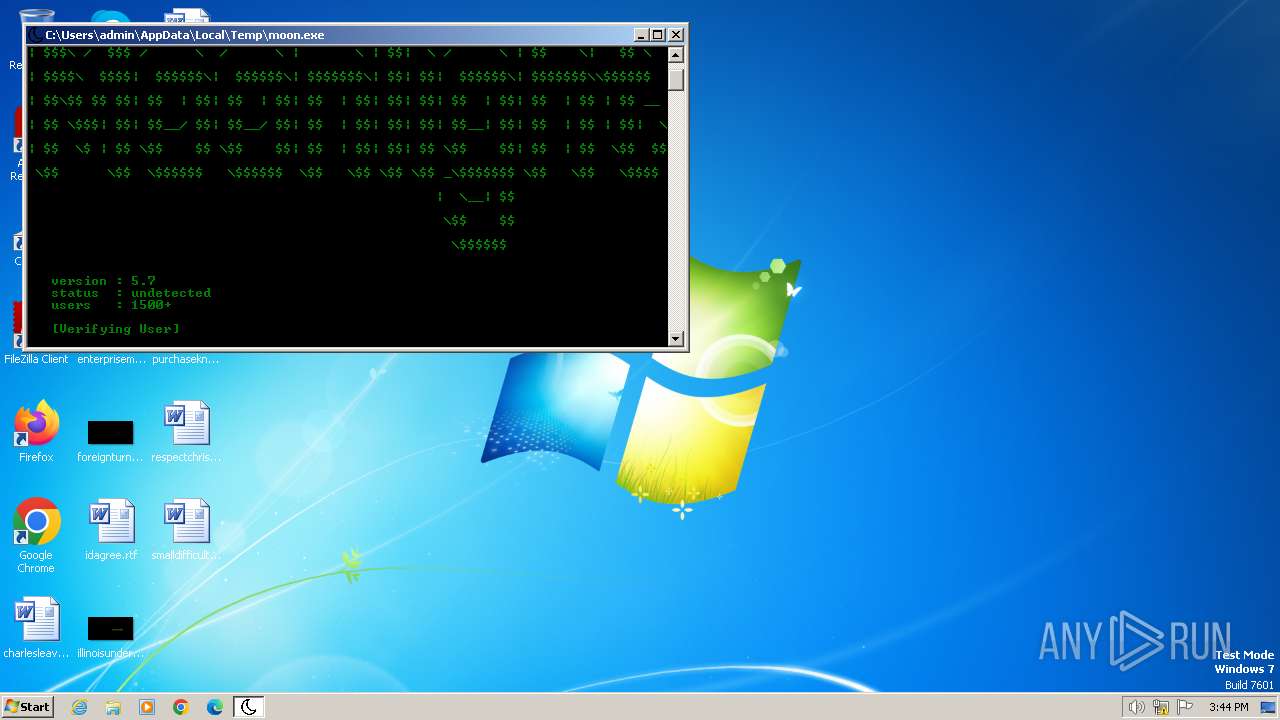
| File name: | moon.exe |
| Full analysis: | https://app.any.run/tasks/888244ae-c6e9-48bd-99a5-2c3340442ef6 |
| Verdict: | Malicious activity |
| Analysis date: | October 29, 2024, 15:43:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, 6 sections |
| MD5: | 0A0698E9B85864FDC3803A574A8D12C8 |
| SHA1: | 9351E3C6F43066C393599D394186A5F94AEC44E1 |
| SHA256: | 5A9EC98D04D88858793AFC0F80E841DFA223F8904AE32B04B48075EEC04FB6BA |
| SSDEEP: | 98304:OBU87Vne17Jd/qv2vnDc0RENHVpfvl10uydJx6vk6glycOyqyND0OrD1q+tSO2CX:Fpe0nP0CWy |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- moon.exe (PID: 3500)
Reads the Internet Settings
- moon.exe (PID: 3500)
Reads settings of System Certificates
- moon.exe (PID: 3500)
Checks Windows Trust Settings
- moon.exe (PID: 3500)
Starts CMD.EXE for commands execution
- moon.exe (PID: 3500)
Potential Corporate Privacy Violation
- svchost.exe (PID: 1060)
INFO
Reads the computer name
- moon.exe (PID: 3500)
Checks supported languages
- moon.exe (PID: 3500)
Checks proxy server information
- moon.exe (PID: 3500)
Reads the machine GUID from the registry
- moon.exe (PID: 3500)
Manual execution by a user
- wmpnscfg.exe (PID: 1568)
VMProtect protector has been detected
- moon.exe (PID: 3500)
Reads the software policy settings
- moon.exe (PID: 3500)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (61.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.6) |
| .exe | | | Win32 Executable (generic) (10) |
| .exe | | | Win16/32 Executable Delphi generic (4.6) |
| .exe | | | Generic Win/DOS Executable (4.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:10:22 09:55:09+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.29 |
| CodeSize: | 25600 |
| InitializedDataSize: | 2587648 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa715af |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
43
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1060 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1100 | C:\Windows\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | moon.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1568 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3500 | "C:\Users\admin\AppData\Local\Temp\moon.exe" | C:\Users\admin\AppData\Local\Temp\moon.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 3660 | "C:\Users\admin\AppData\Local\Temp\moon.exe" | C:\Users\admin\AppData\Local\Temp\moon.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3696 | C:\Windows\system32\cmd.exe /c Color 02 | C:\Windows\System32\cmd.exe | — | moon.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
7 818
Read events
7 769
Write events
43
Delete events
6
Modification events
| (PID) Process: | (1060) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Nla\Cache\Intranet |
| Operation: | write | Name: | {4040CF00-1B3E-486A-B407-FA14C56B6FC0} |
Value: 525400363EFF | |||
| (PID) Process: | (3500) moon.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3500) moon.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3500) moon.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3500) moon.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3500) moon.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3500) moon.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyServer |
Value: | |||
| (PID) Process: | (3500) moon.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyOverride |
Value: | |||
| (PID) Process: | (3500) moon.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoConfigURL |
Value: | |||
| (PID) Process: | (3500) moon.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoDetect |
Value: | |||
Executable files
0
Suspicious files
12
Text files
5
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1060 | svchost.exe | C:\Windows\ServiceProfiles\NetworkService\AppData\Local\Temp\TarD2CE.tmp | binary | |
MD5:78785956AB4E54D6116D673C3491EDFF | SHA256:C514DBDBB13632CBB378C59086C1EBB0BC9B25FFB0A349F2B052B065C0D913E6 | |||
| 3500 | moon.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:A1A4D4E02BC3A3E98A4AFA6380B60BE5 | SHA256:17DDF53DDD96CD3D36E44460B543BD07C0FBB703CC000DD37A3F57C1216F1779 | |||
| 3500 | moon.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\RP95SSNT.txt | text | |
MD5:FDC009D8DEF1E02F60E78A6B618CEA2D | SHA256:4295F61C2D7F10150EFA1785631CBDB88DCD00814814C65D91AA2568AB25A5AF | |||
| 3500 | moon.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:375BD6F40C6BA0A80D57E372A43A34E0 | SHA256:9EC6757D82FDAEE07DF21C43F2ABE0E1FFBA6AA5C09B48163508AF9C8DBF1291 | |||
| 3500 | moon.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7FD6B1DF4E991C74C18FBA2A610DC1B8 | binary | |
MD5:1779D6A6273CB822CEF22534A1592683 | SHA256:2A9262151976875A0A2B9318CCDBD88480792876F1F7FE1F9358CD2B23F829C0 | |||
| 3500 | moon.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\73FELDYB.txt | text | |
MD5:85A2AC7AA2A40E5761816617B14506D0 | SHA256:4AC42C0CD0A86CF4AF2B0EFB4C81B15B9DA7C6AC807158B177853FC4A8312FB6 | |||
| 3500 | moon.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7FD6B1DF4E991C74C18FBA2A610DC1B8 | binary | |
MD5:F52CDE2A934EF191ADBD2EE0D41C9CC7 | SHA256:EB25E2833C213A9E9A164A394A88E9DDB910A8F1D65689BEBAC32414800115FD | |||
| 1060 | svchost.exe | C:\Windows\ServiceProfiles\NetworkService\AppData\Local\Temp\CabD2CD.tmp | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 1060 | svchost.exe | C:\Windows\ServiceProfiles\NetworkService\AppData\Local\Temp\Cab48CA.tmp | compressed | |
MD5:49AEBF8CBD62D92AC215B2923FB1B9F5 | SHA256:B33EFCB95235B98B48508E019AFA4B7655E80CF071DEFABD8B2123FC8B29307F | |||
| 1060 | svchost.exe | C:\Windows\ServiceProfiles\NetworkService\AppData\Local\Temp\Tar48CB.tmp | binary | |
MD5:4EA6026CF93EC6338144661BF1202CD1 | SHA256:8EFBC21559EF8B1BCF526800D8070BAAD42474CE7198E26FA771DBB41A76B1D8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
18
DNS requests
10
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3500 | moon.exe | GET | 200 | 72.246.169.163:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
3500 | moon.exe | GET | 304 | 23.53.40.35:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?de243428eafece54 | unknown | — | — | whitelisted |
1060 | svchost.exe | GET | 200 | 23.53.40.35:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?3c4d1c7aa342ad0e | unknown | — | — | whitelisted |
3500 | moon.exe | GET | 403 | 91.195.240.85:80 | http://ww16.moonlight.uno/donaldtrump.html?sub1=20241030-0244-034a-852f-f78238e03548 | unknown | — | — | unknown |
3500 | moon.exe | GET | 403 | 185.176.43.98:80 | http://moonsoft.eu3.biz/id.php | unknown | — | — | malicious |
1060 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3500 | moon.exe | GET | 200 | 199.59.243.227:80 | http://ww25.moonlight.uno/music/welcometomlmaster.wav?subid1=20241030-0244-0206-838e-fb3f13e2ca75 | unknown | — | — | unknown |
3500 | moon.exe | GET | 200 | 195.138.255.19:80 | http://r11.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBQaUrm0WeTDM5ghfoZtS72KO9ZnzgQUCLkRO6XQhRi06g%2BgrZ%2BGHo78OCcCEgRx5%2Fk0fJHj59OoaM1Ns7xDwA%3D%3D | unknown | — | — | whitelisted |
3500 | moon.exe | GET | 403 | 185.176.43.98:80 | http://moonsoft.eu3.biz/uwu.php | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3500 | moon.exe | 103.224.182.253:443 | moonlight.uno | Trellian Pty. Limited | AU | suspicious |
3500 | moon.exe | 23.53.40.35:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | whitelisted |
3500 | moon.exe | 72.246.169.163:80 | x1.c.lencr.org | AKAMAI-AS | DE | whitelisted |
3500 | moon.exe | 195.138.255.19:80 | r11.o.lencr.org | AS33891 Netzbetrieb GmbH | DE | whitelisted |
3500 | moon.exe | 199.59.243.227:80 | ww25.moonlight.uno | AMAZON-02 | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
moonlight.uno |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r11.o.lencr.org |
| whitelisted |
ww25.moonlight.uno |
| unknown |
moonsoft.eu3.biz |
| malicious |
ww16.moonlight.uno |
| unknown |
crl.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1060 | svchost.exe | Potential Corporate Privacy Violation | ET GAMES Moonlight Hack Domain in DNS Lookup |
3500 | moon.exe | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
1060 | svchost.exe | Potential Corporate Privacy Violation | ET GAMES Moonlight Hack Domain in DNS Lookup |