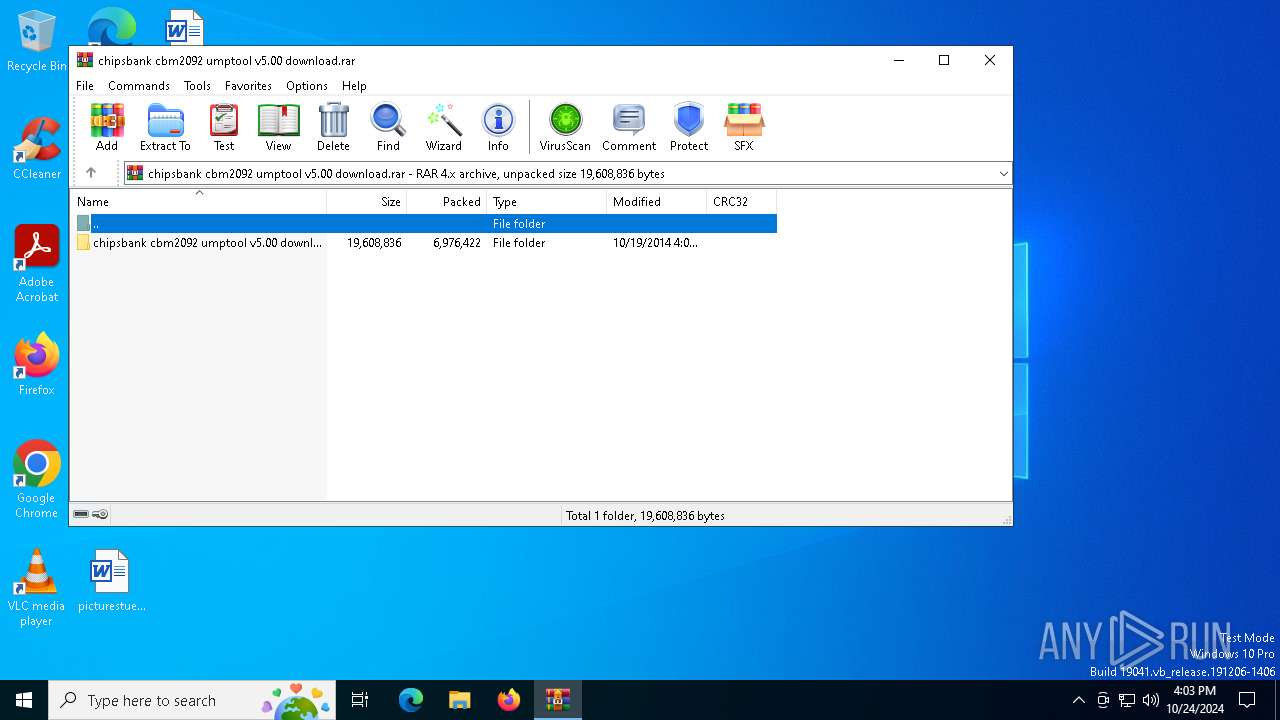
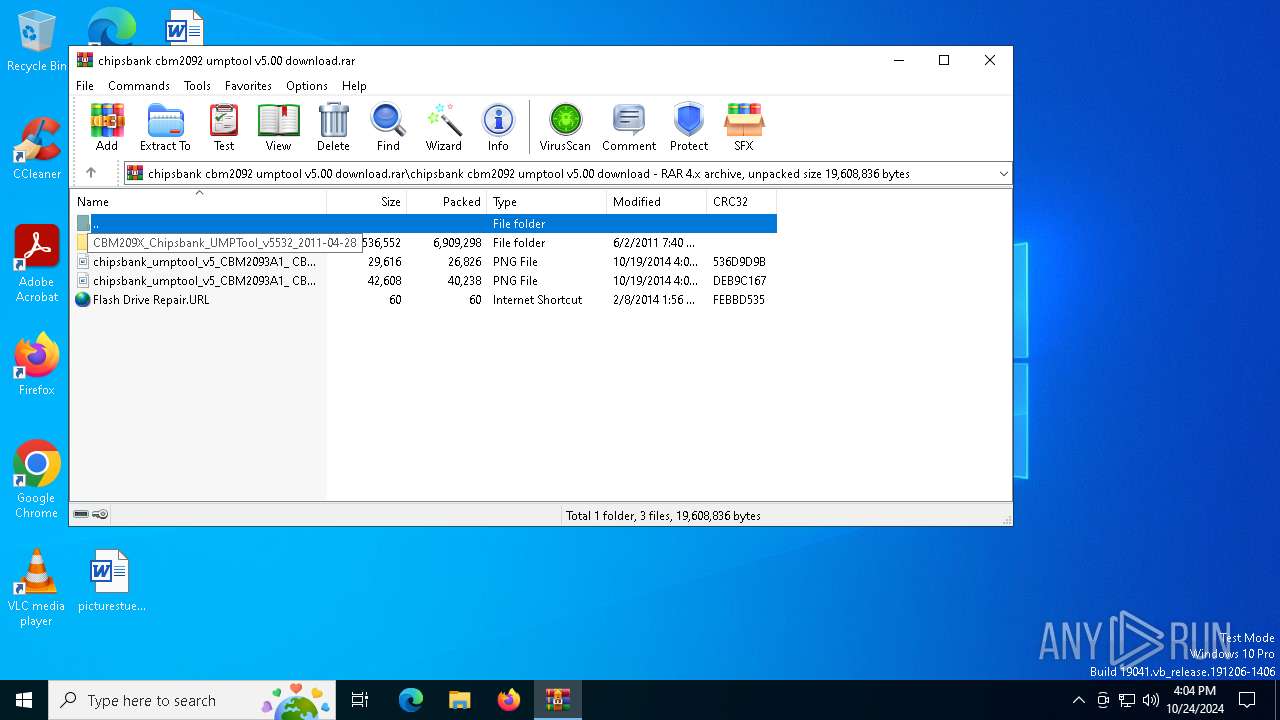
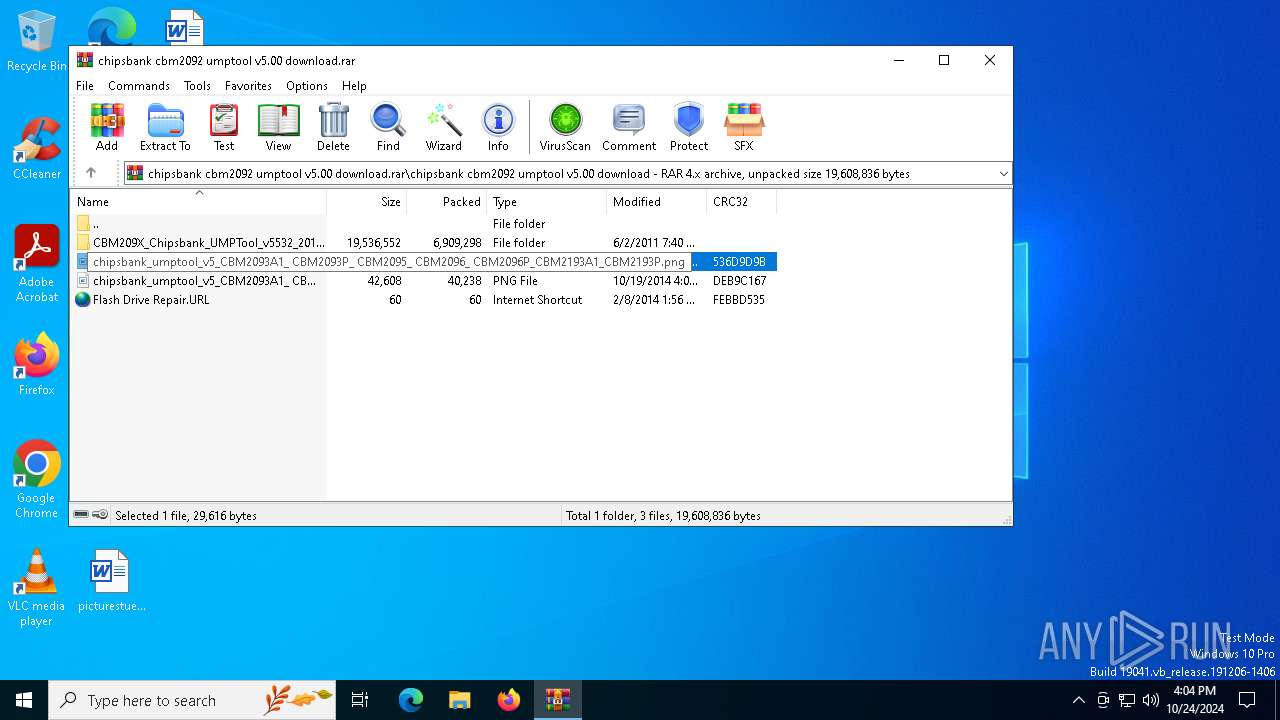
| File name: | chipsbank cbm2092 umptool v5.00 download.rar |
| Full analysis: | https://app.any.run/tasks/290a9b52-f7db-4af7-bd9f-8bcd2566e243 |
| Verdict: | Malicious activity |
| Analysis date: | October 24, 2024, 16:03:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 016683E37CC0394D8F234E72D2B88EE7 |
| SHA1: | 51D084BE6B9301E54486F645610E762E4D6AB544 |
| SHA256: | 5A66C5D28530DA151C5954E21425D3290496D5C7E5D9BD283C1A1DC0D71882E3 |
| SSDEEP: | 98304:zvo1gjzmz5UBKcAuvTV9DETVBdAp1gUHu+ip1gU+B2coTBKzczL8Fo67wP1bTVD3:T9KqrgetgdOtxawzT1r7ijN0/+V |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6220)
SUSPICIOUS
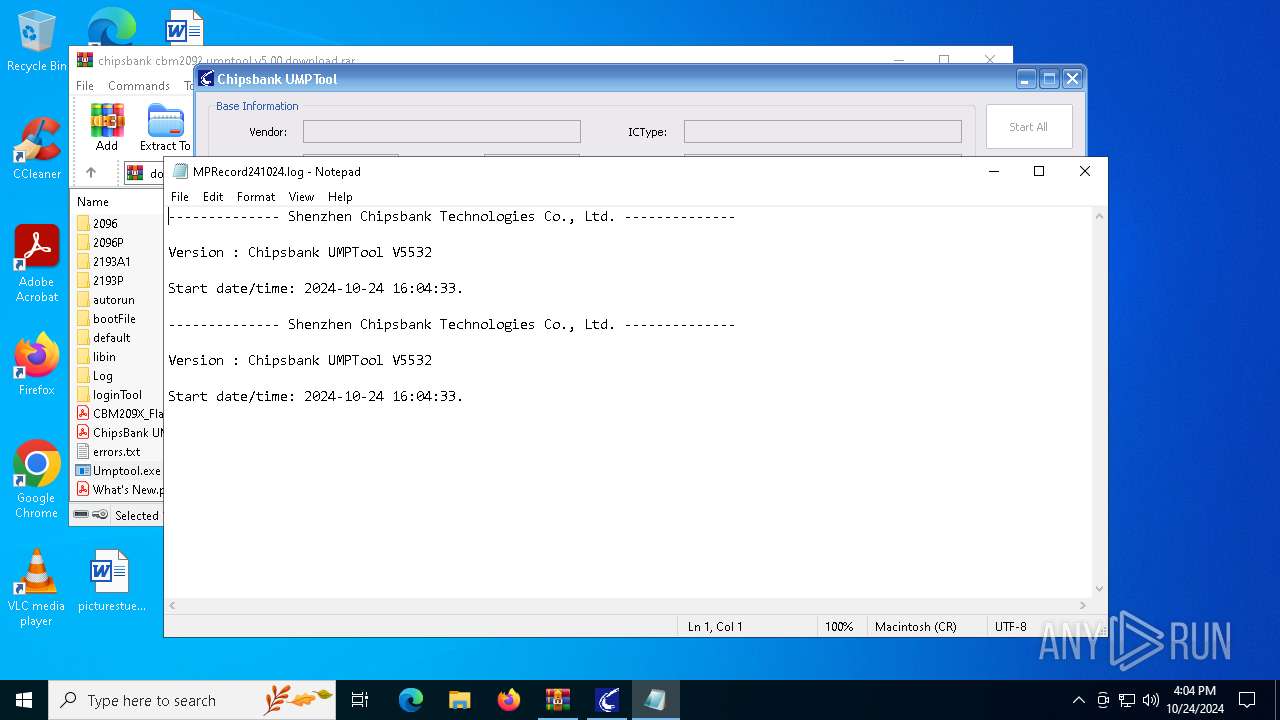
Start notepad (likely ransomware note)
- Umptool.exe (PID: 2980)
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 6220)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6220)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| FileVersion: | RAR v4 |
|---|---|
| CompressedSize: | 2902 |
| UncompressedSize: | 10312 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2010:10:30 12:16:26 |
| PackingMethod: | Normal |
| ArchivedFileName: | chipsbank cbm2092 umptool v5.00 download\CBM209X_Chipsbank_UMPTool_v5532_2011-04-28\2093A1\CodeFile\5T2F_CFG |
Total processes
137
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 948 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2980 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6220.17325\chipsbank cbm2092 umptool v5.00 download\CBM209X_Chipsbank_UMPTool_v5532_2011-04-28\Umptool.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6220.17325\chipsbank cbm2092 umptool v5.00 download\CBM209X_Chipsbank_UMPTool_v5532_2011-04-28\Umptool.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Chipsbank Integrity Level: MEDIUM Version: 0, 0, 0, 0 Modules
| |||||||||||||||
| 6220 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\chipsbank cbm2092 umptool v5.00 download.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6960 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7048 | "C:\Windows\System32\notepad.exe" C:\Users\admin\AppData\Local\Temp\Rar$EXa6220.17325\chipsbank cbm2092 umptool v5.00 download\CBM209X_Chipsbank_UMPTool_v5532_2011-04-28\Log\MPRecord241024.log | C:\Windows\SysWOW64\notepad.exe | — | Umptool.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 258
Read events
3 251
Write events
7
Delete events
0
Modification events
| (PID) Process: | (6220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\chipsbank cbm2092 umptool v5.00 download.rar | |||
| (PID) Process: | (6220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2980) Umptool.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
Executable files
22
Suspicious files
41
Text files
530
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6220.17325\chipsbank cbm2092 umptool v5.00 download\CBM209X_Chipsbank_UMPTool_v5532_2011-04-28\2093A1\CodeFile\5T2F_CFG | text | |
MD5:7EB31449F47990CA5730E10701ACAFA4 | SHA256:06934459585F9D02218443DE98C0551EDB635F4E1CC0C6126E5C98EC3DBDF831 | |||
| 6220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6220.17325\chipsbank cbm2092 umptool v5.00 download\CBM209X_Chipsbank_UMPTool_v5532_2011-04-28\2093A1\CodeFile\General_128 | text | |
MD5:A834BBCECA97307D15D11F9B55D0A2B9 | SHA256:AED94F0E06D515E07ACB5E48CE636443383F88082297AD7C2836FBBDE064C66D | |||
| 6220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6220.17325\chipsbank cbm2092 umptool v5.00 download\CBM209X_Chipsbank_UMPTool_v5532_2011-04-28\2093A1\CodeFile\General_128_P_R | text | |
MD5:3C547BE71F69F4F1805D5012F5E10F3A | SHA256:94C1535202B53B8FEB210403A29BE6F98EA1BB4FC2B0172FDD8395BD162FE252 | |||
| 6220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6220.17325\chipsbank cbm2092 umptool v5.00 download\CBM209X_Chipsbank_UMPTool_v5532_2011-04-28\2093A1\CodeFile\5T2F_CFG_P_R | text | |
MD5:851CF55863DEBD56C99ECC315F30ADB7 | SHA256:6C36C400B29B4E5E35AC8CCB88D53AF222F6B88DDA9F5FE0153BACB6CD7FF858 | |||
| 6220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6220.17325\chipsbank cbm2092 umptool v5.00 download\CBM209X_Chipsbank_UMPTool_v5532_2011-04-28\2093A1\CodeFile\General_128_P | text | |
MD5:5E6304668DC2F0CEA540B16604045559 | SHA256:7D93B944BDFF573A30981C98130636F398DEB30A0595194243BB295EA3171721 | |||
| 6220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6220.17325\chipsbank cbm2092 umptool v5.00 download\CBM209X_Chipsbank_UMPTool_v5532_2011-04-28\2093A1\CodeFile\General_128_R | text | |
MD5:7DF4CA328681F12490CF787EFF155AA7 | SHA256:4F9B361A181784DB80FBB5E3640B383C5696786D2ECF162A079A170F662BE26F | |||
| 6220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6220.17325\chipsbank cbm2092 umptool v5.00 download\CBM209X_Chipsbank_UMPTool_v5532_2011-04-28\2093A1\CodeFile\5T2F_CFG_R | text | |
MD5:851CF55863DEBD56C99ECC315F30ADB7 | SHA256:6C36C400B29B4E5E35AC8CCB88D53AF222F6B88DDA9F5FE0153BACB6CD7FF858 | |||
| 6220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6220.17325\chipsbank cbm2092 umptool v5.00 download\CBM209X_Chipsbank_UMPTool_v5532_2011-04-28\2093A1\CodeFile\General_256 | text | |
MD5:1DBB862497007EB44E202E31DFA5B581 | SHA256:4FB1461E57A0CDC3AA91D97CF0C943878D574167DD9A1DB6D5D969323283643D | |||
| 6220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6220.17325\chipsbank cbm2092 umptool v5.00 download\CBM209X_Chipsbank_UMPTool_v5532_2011-04-28\2093A1\CodeFile\General_3 | text | |
MD5:85ADA696DFA76EA03F1625882015A2FA | SHA256:4038C9E83EC83CB0245A0980E89C4083BDD79384B27F89C4FC56C592CBB224EA | |||
| 6220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6220.17325\chipsbank cbm2092 umptool v5.00 download\CBM209X_Chipsbank_UMPTool_v5532_2011-04-28\2093A1\CodeFile\General_256T_P | text | |
MD5:E519B1B3A72BAD9D7F6D7A78ED397DD2 | SHA256:74C4B11F6C84EDFBC79D497F53CECF97E44F030C78AF7C0EBE607D6FE0CA22DA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
47
DNS requests
29
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2364 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2376 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2376 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2648 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4360 | SearchApp.exe | 104.126.37.155:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2364 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |