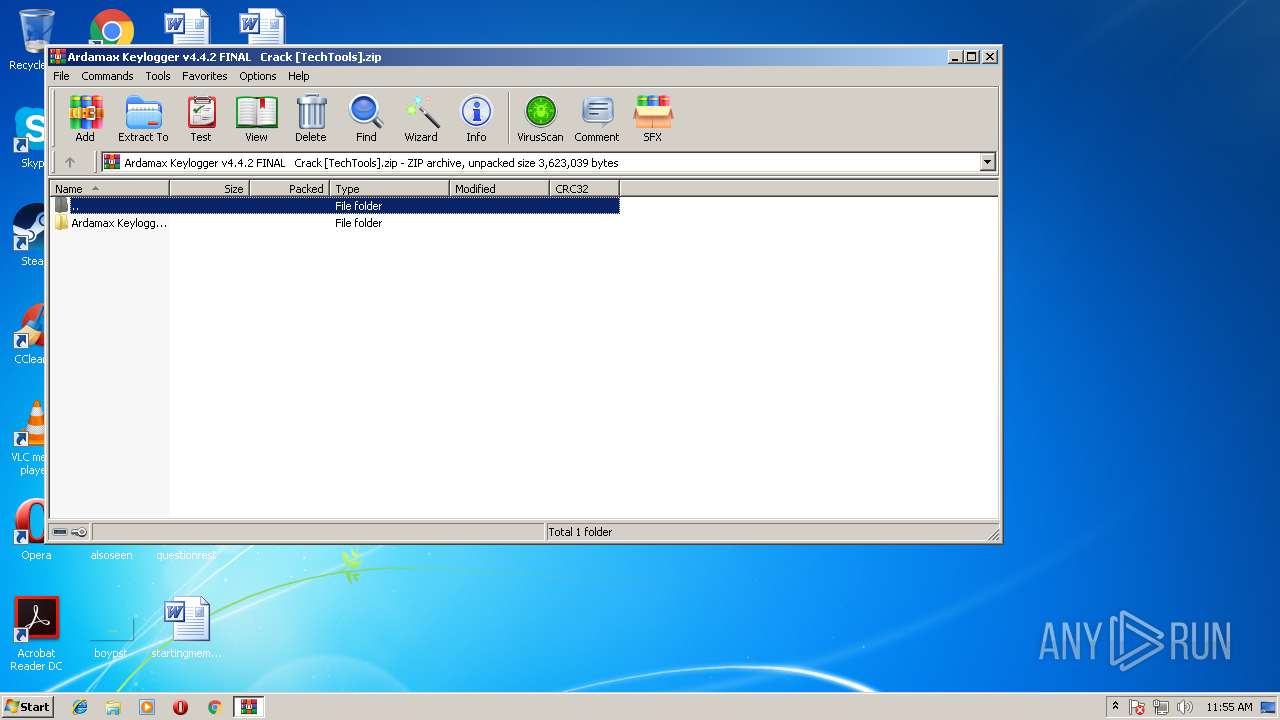
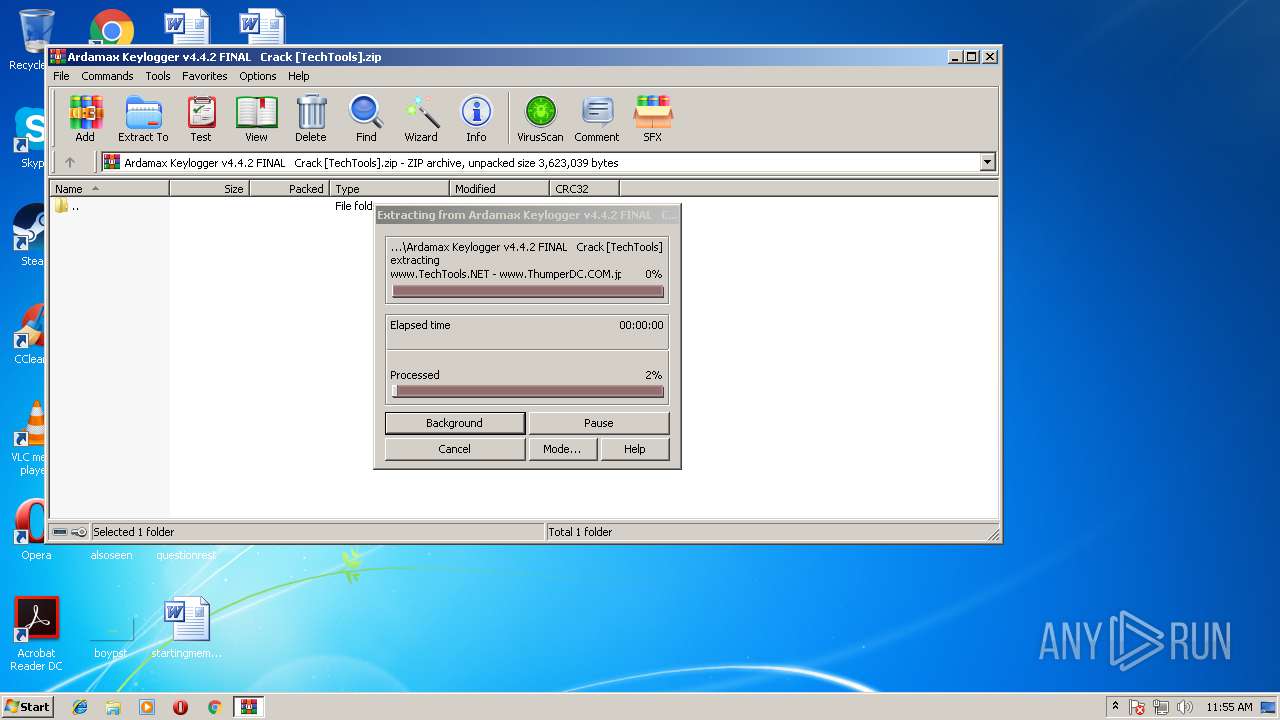
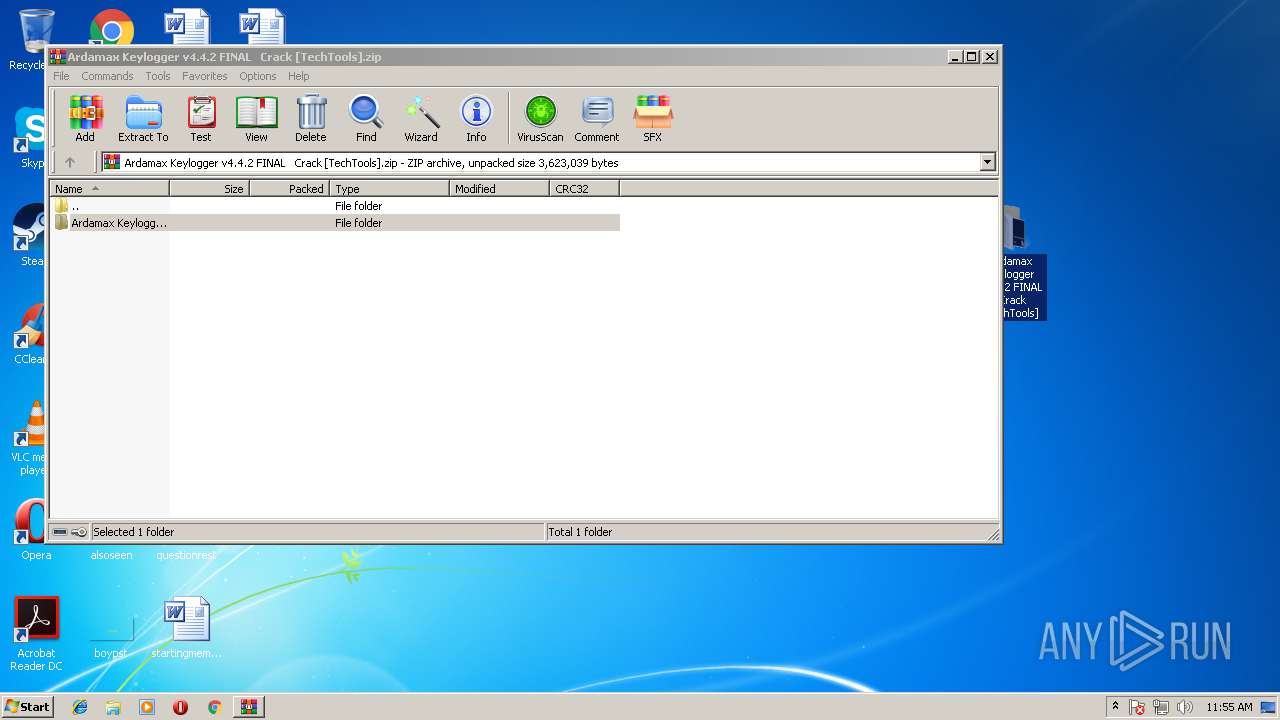
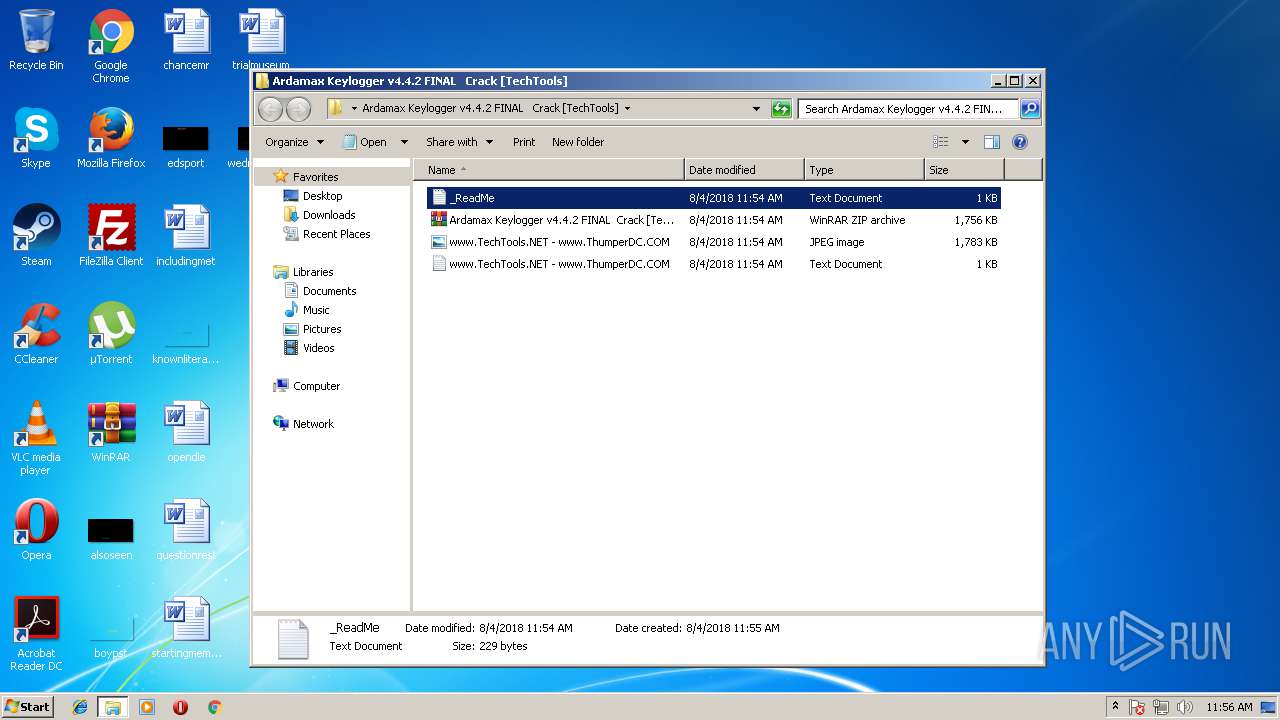
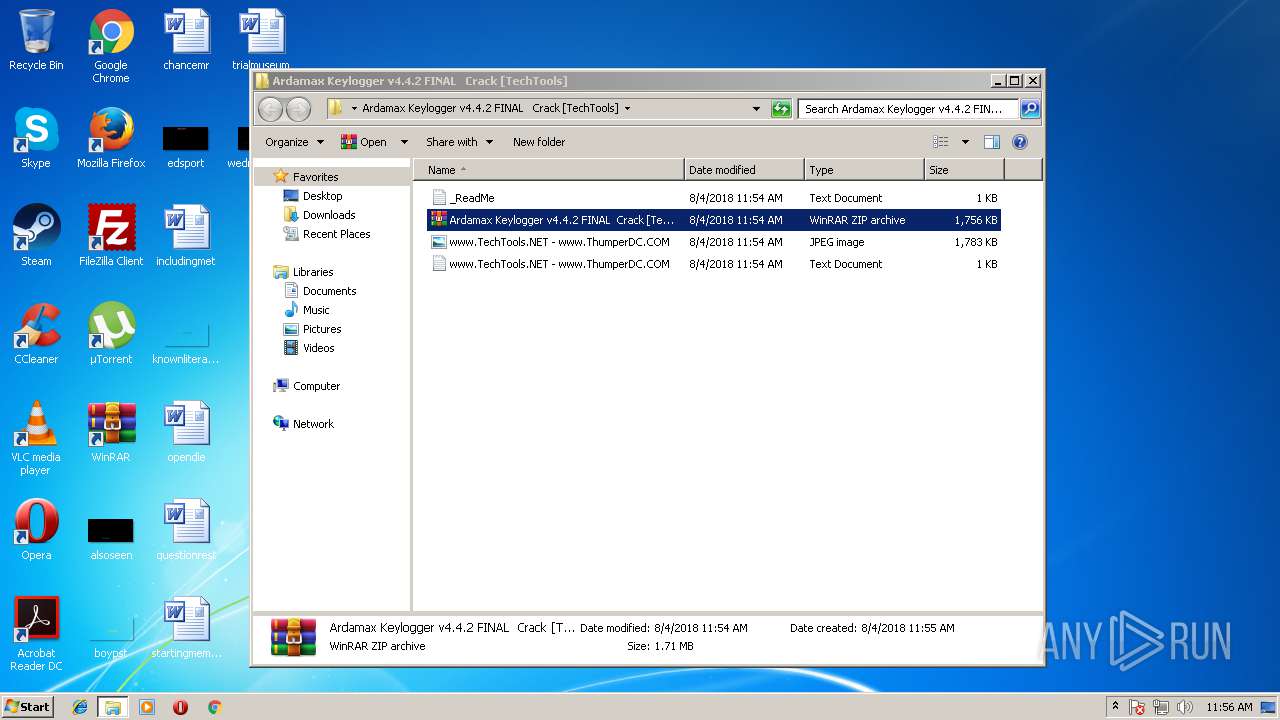
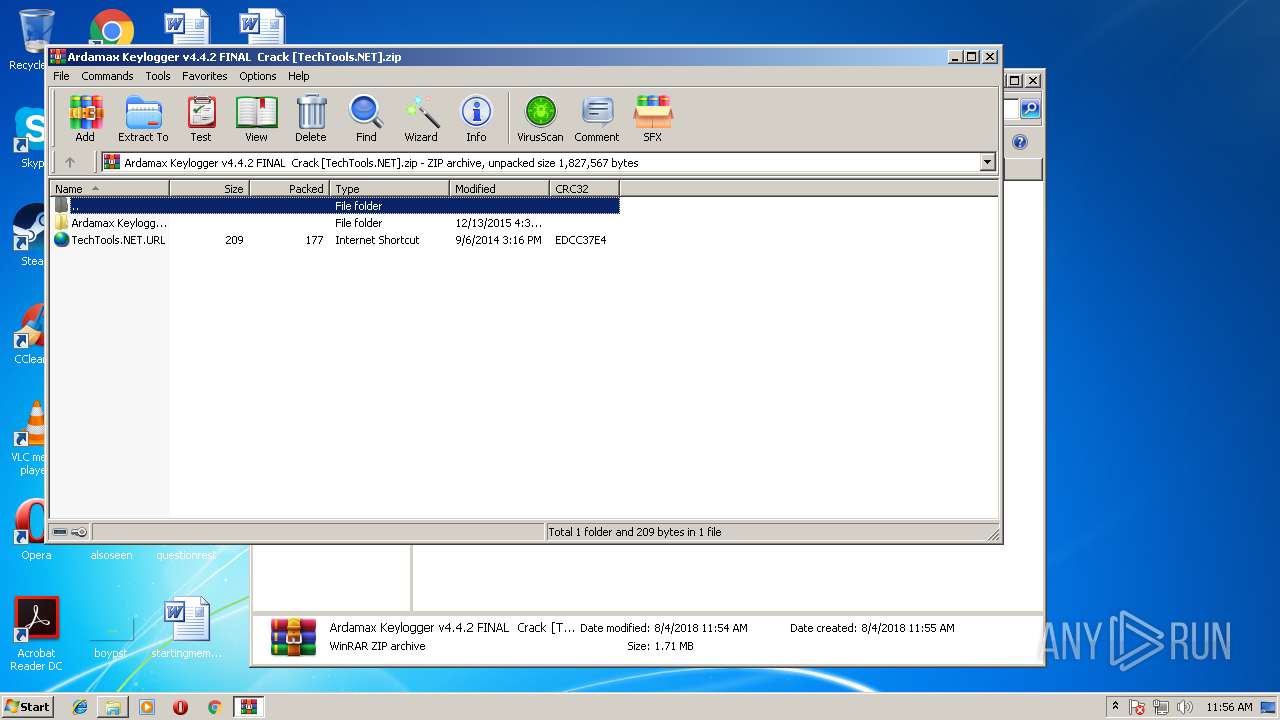
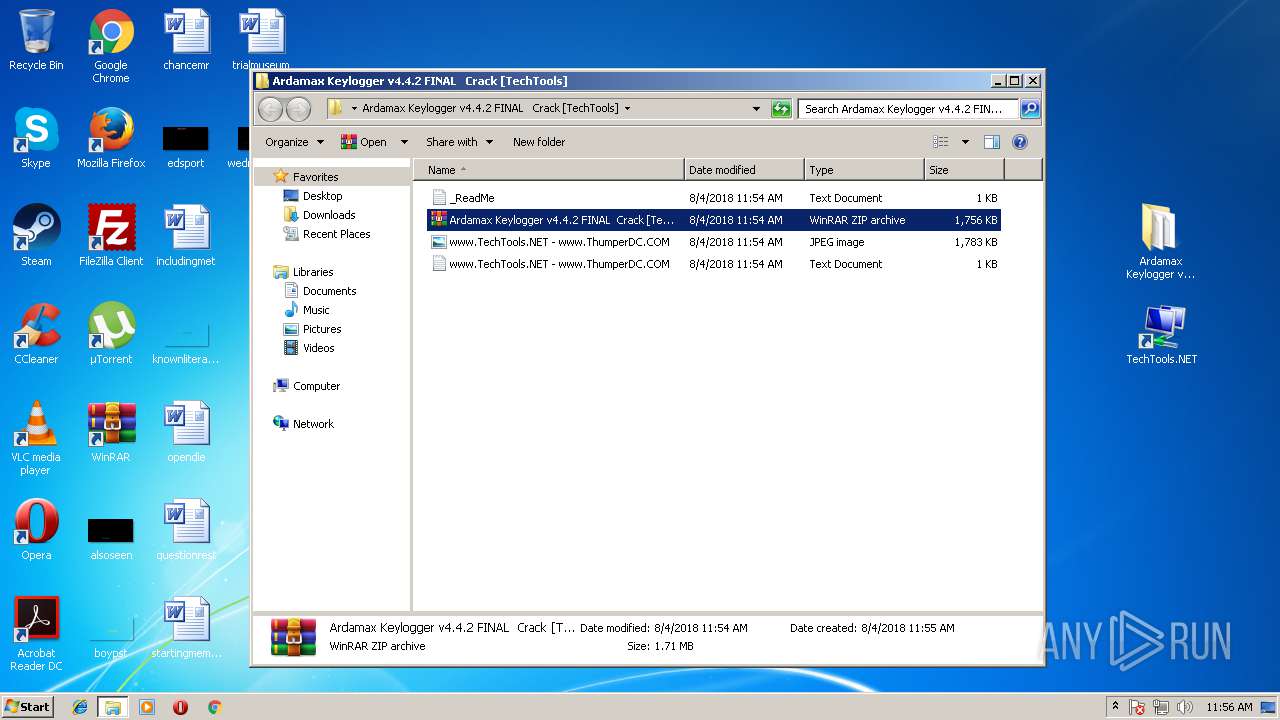
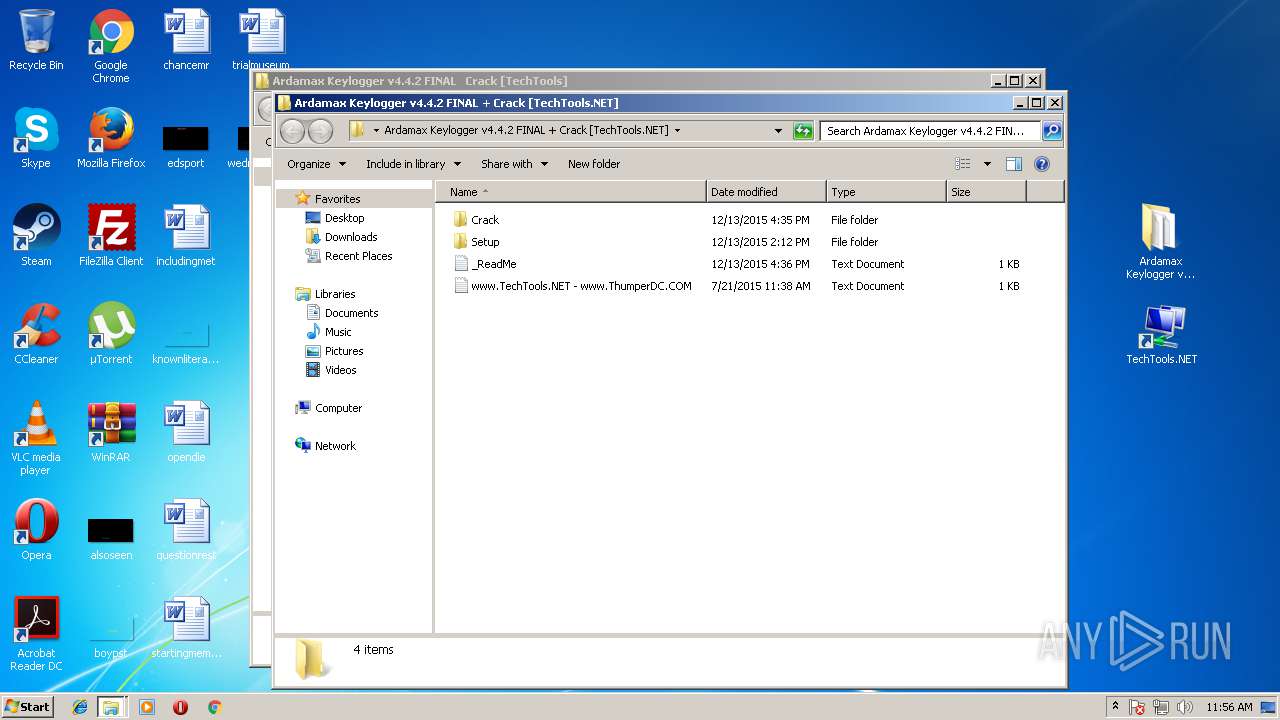
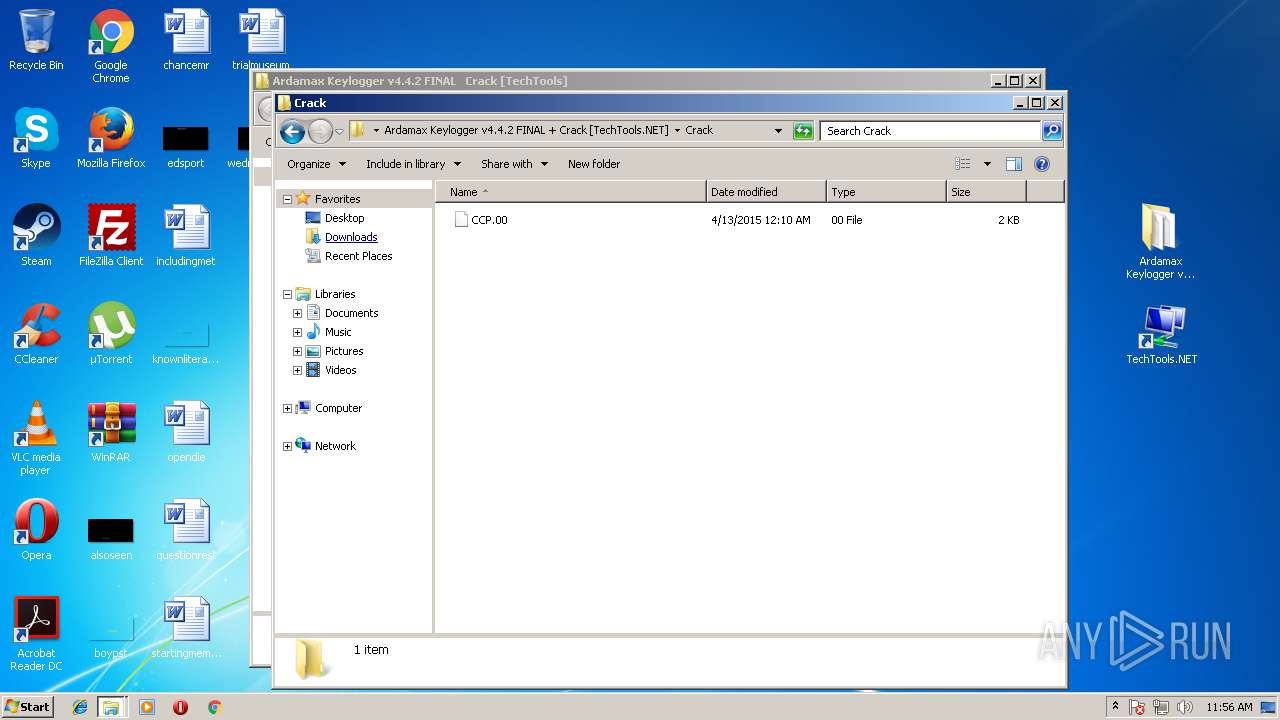
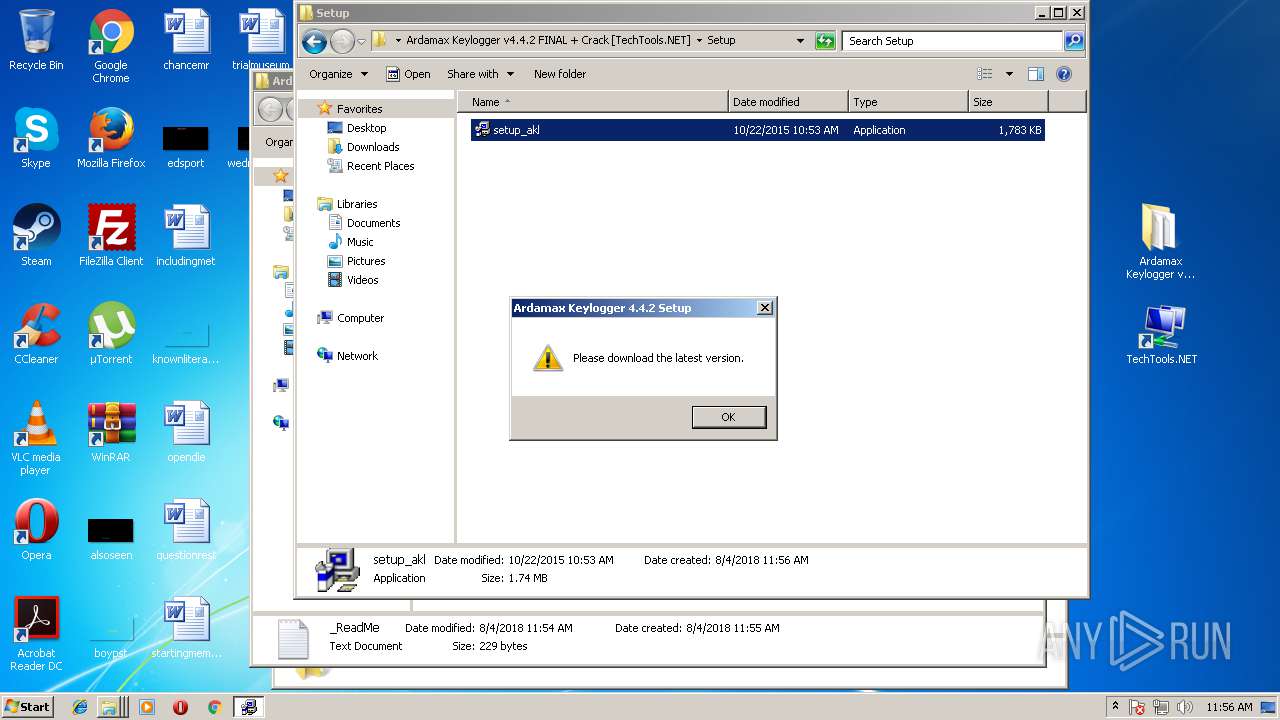
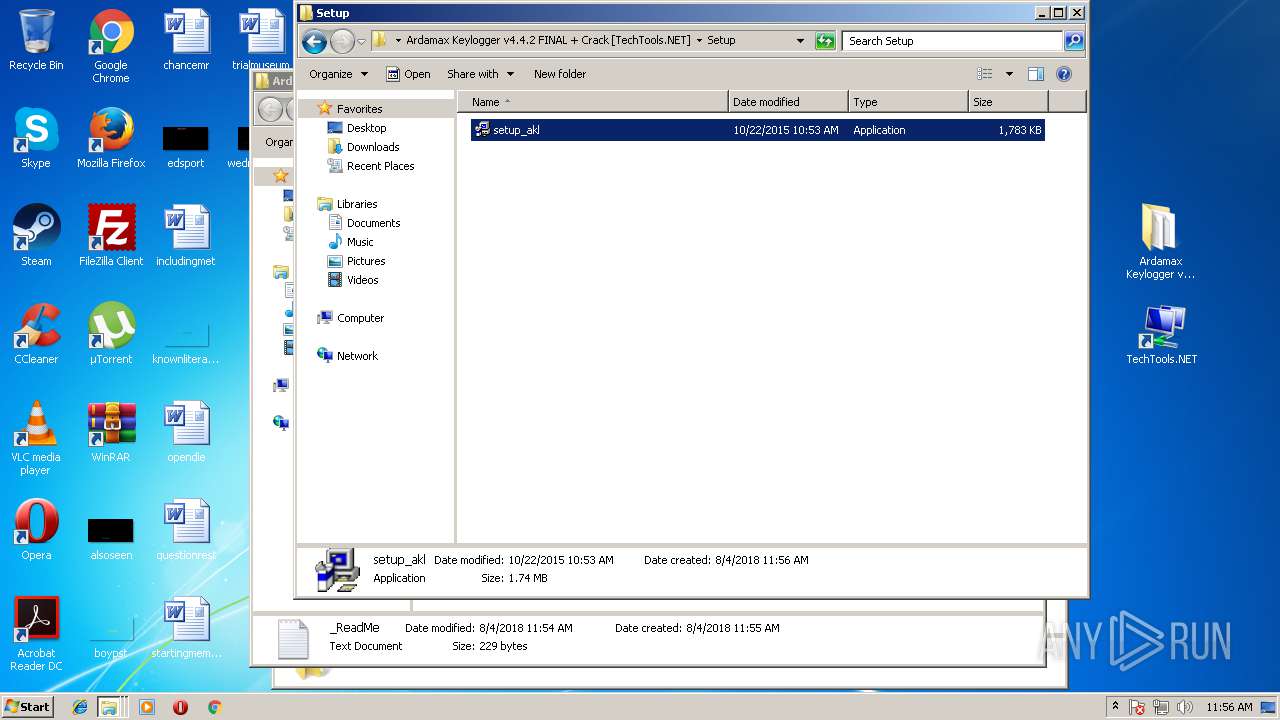
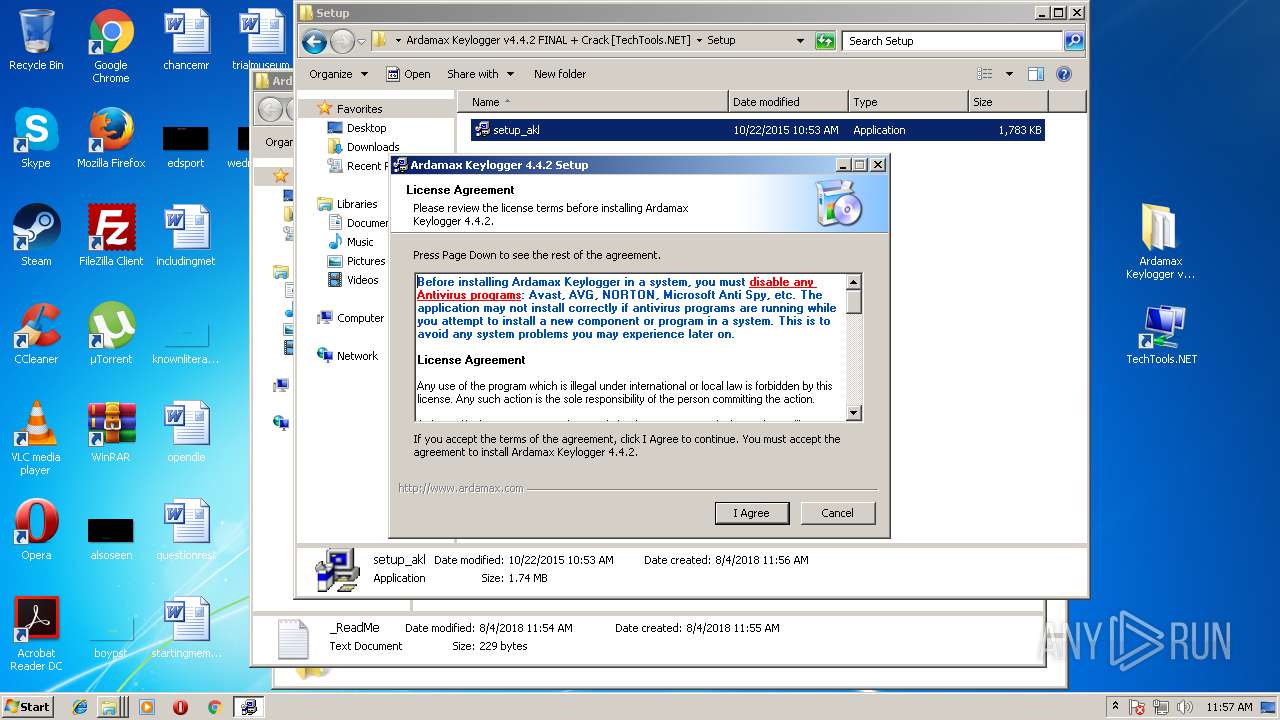
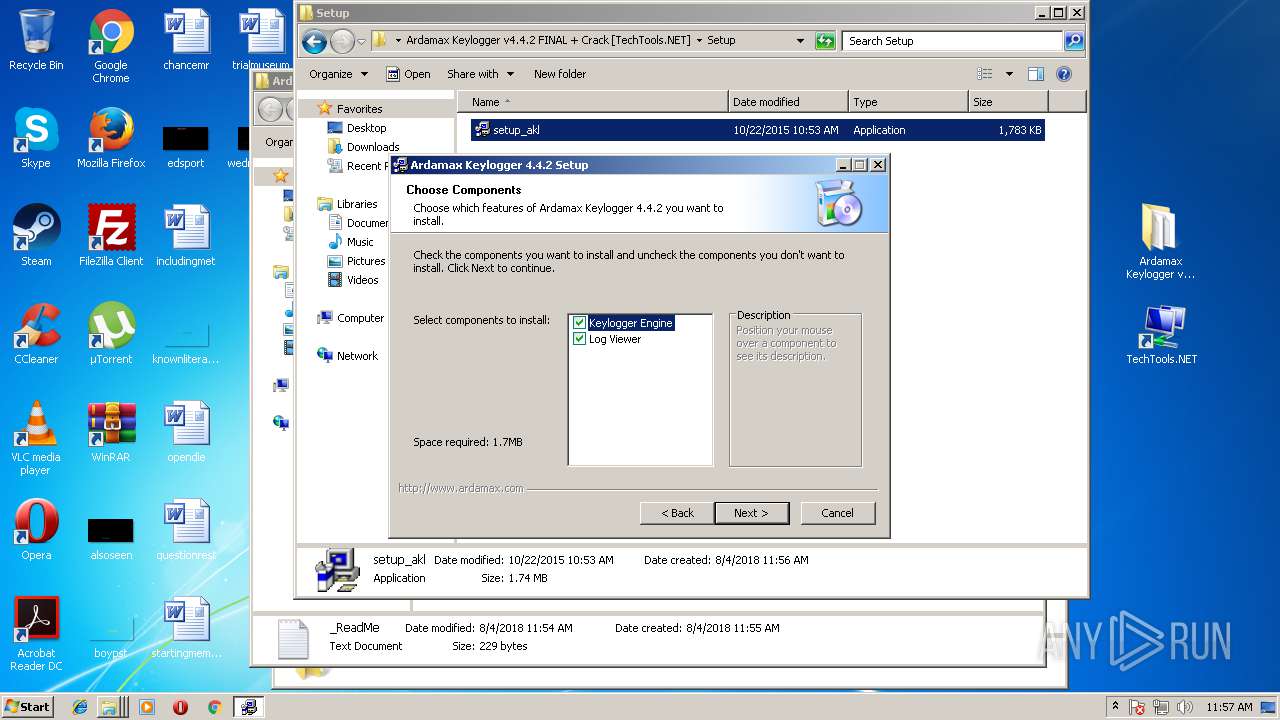
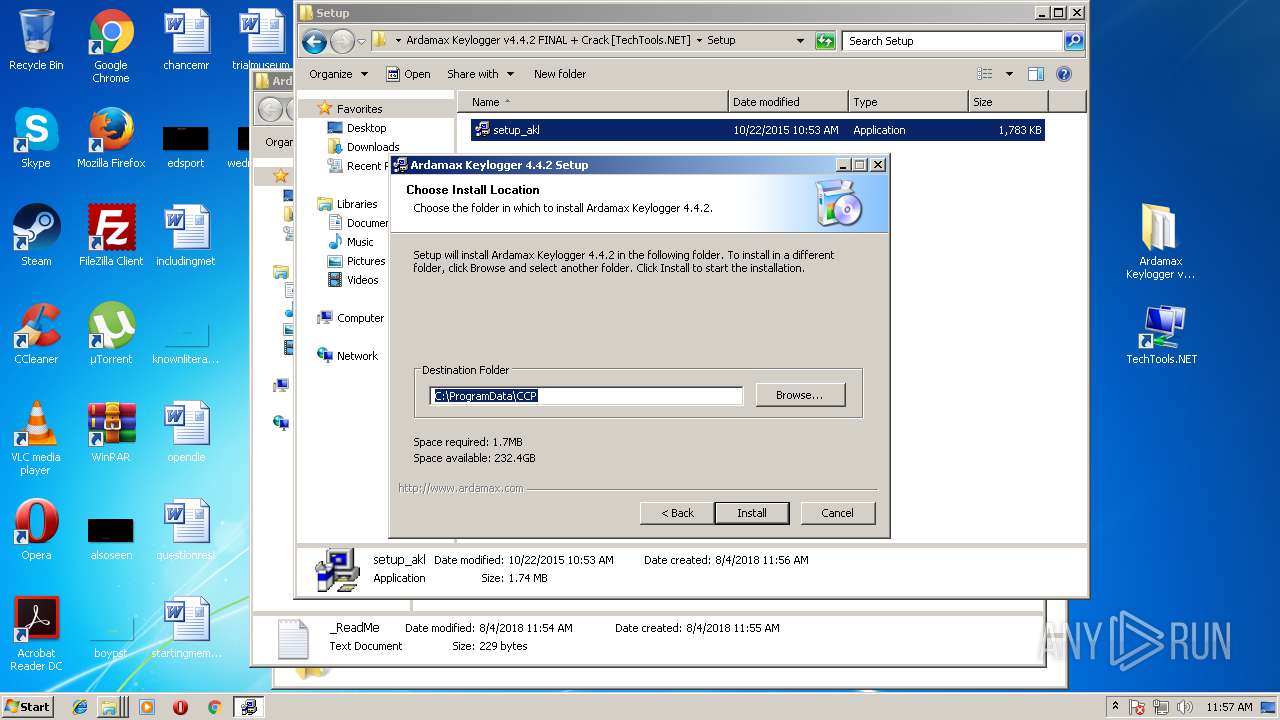
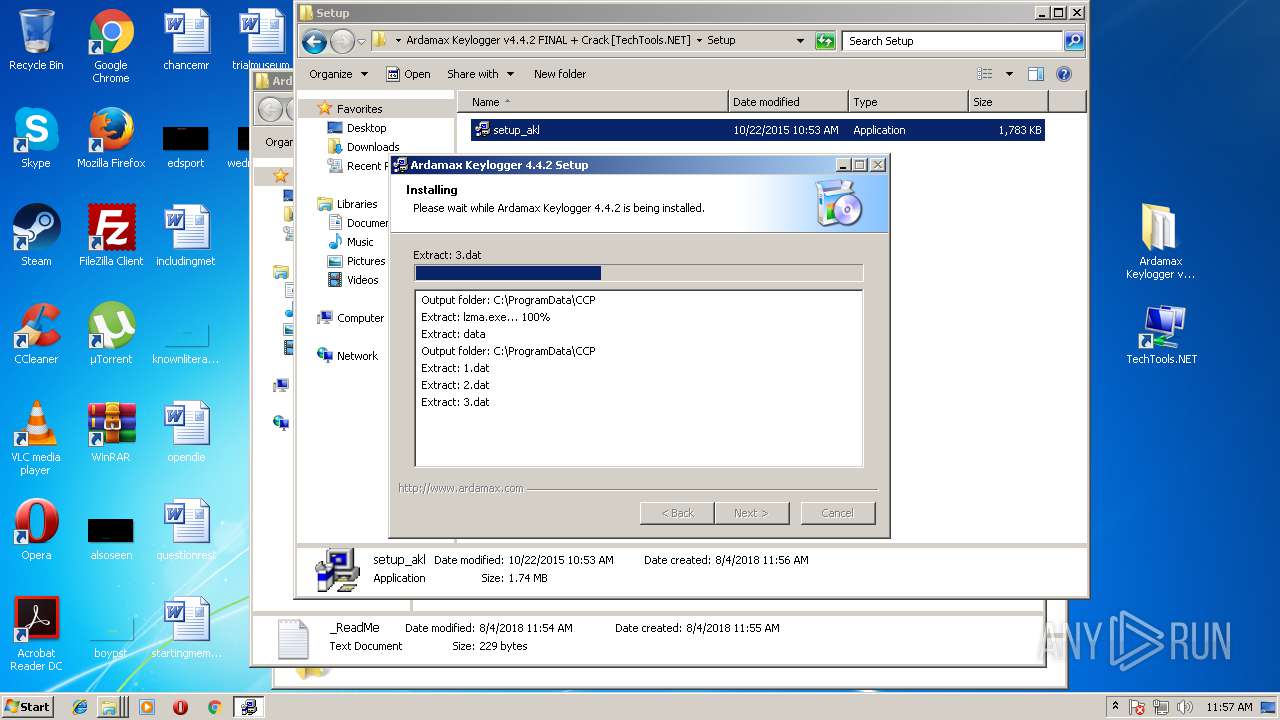
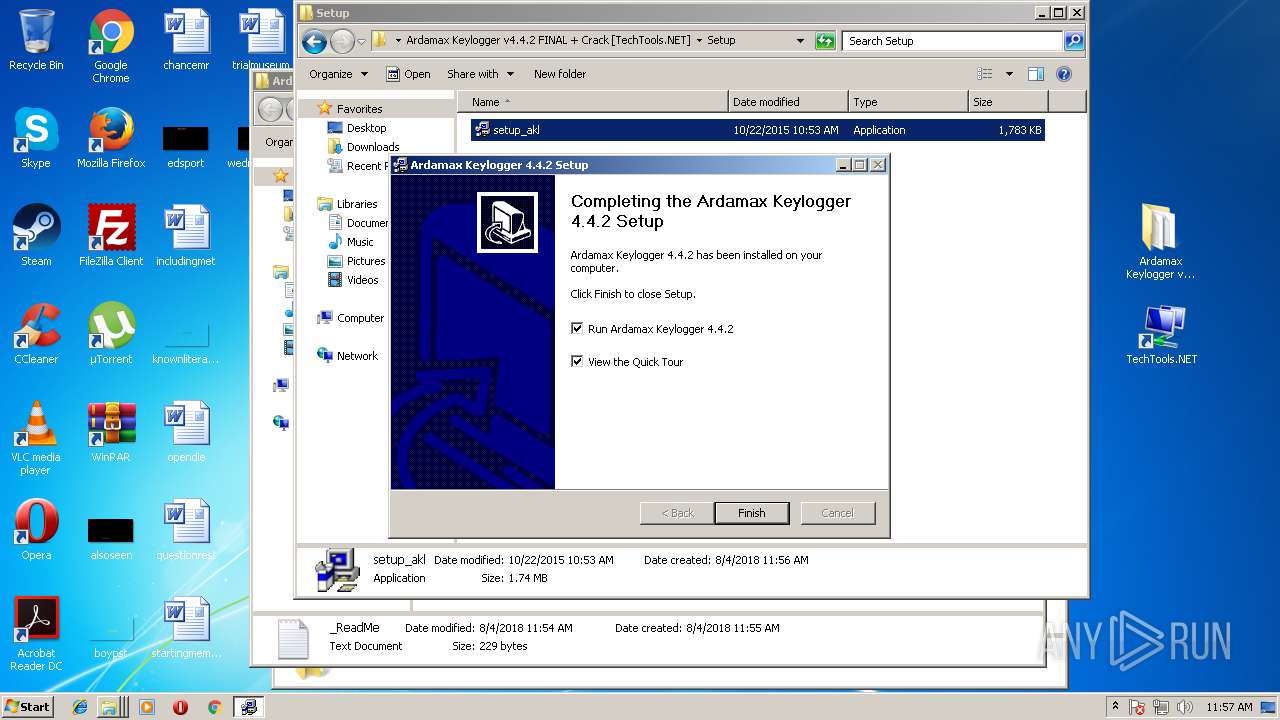
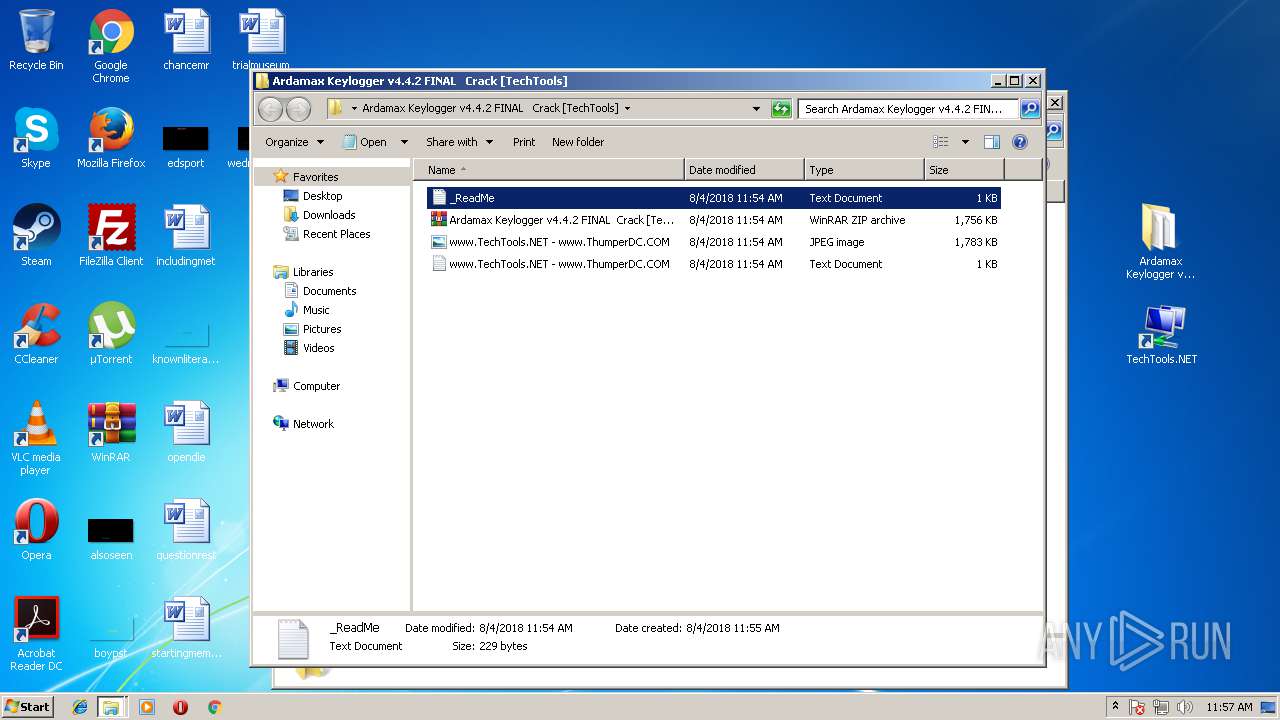
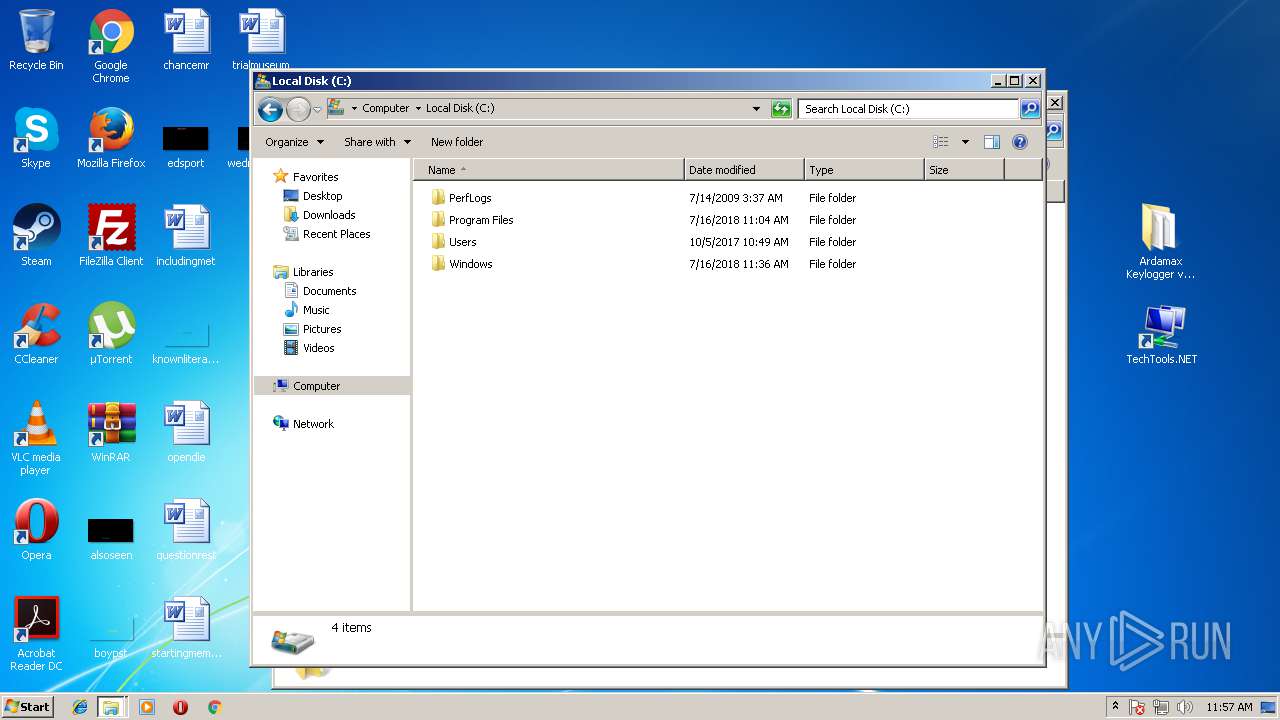
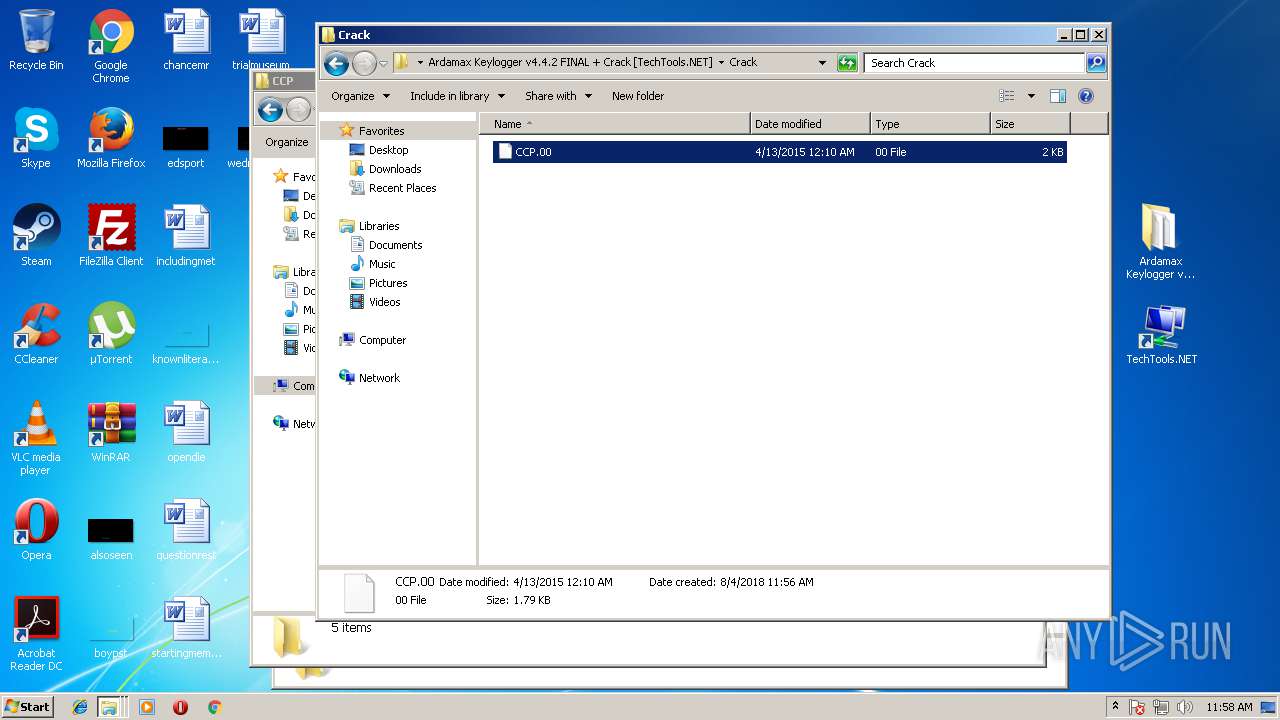
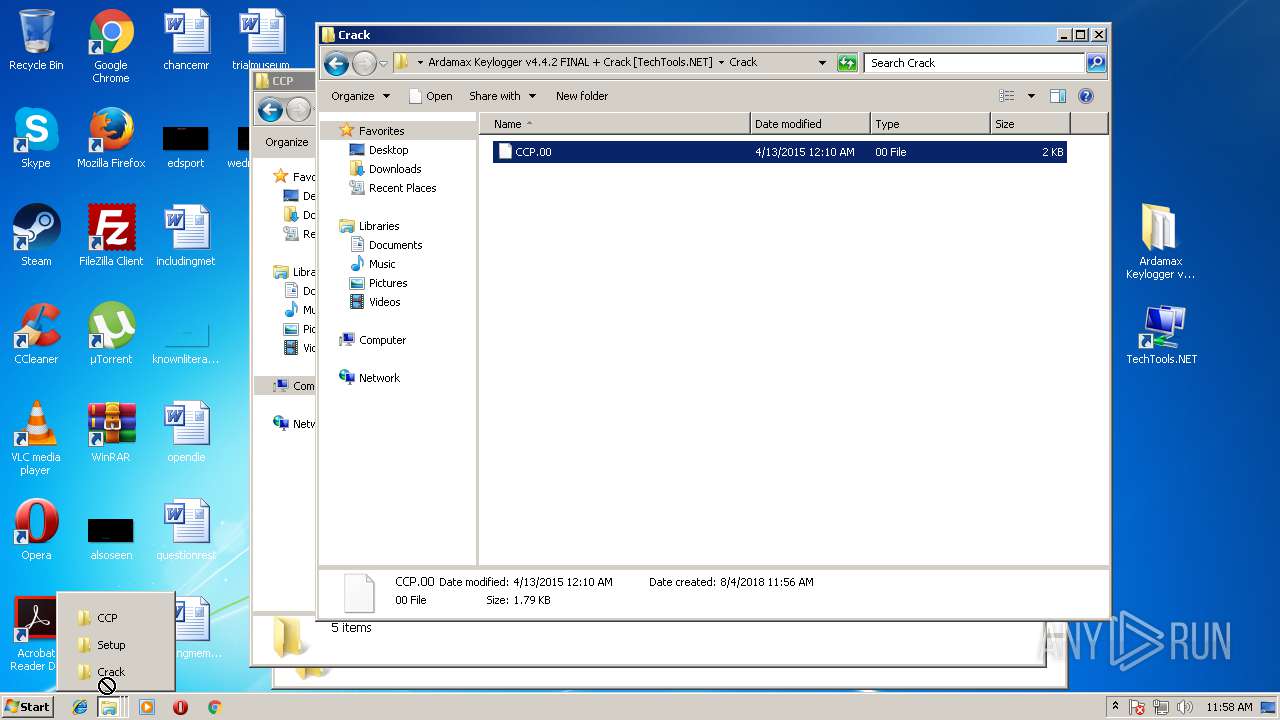
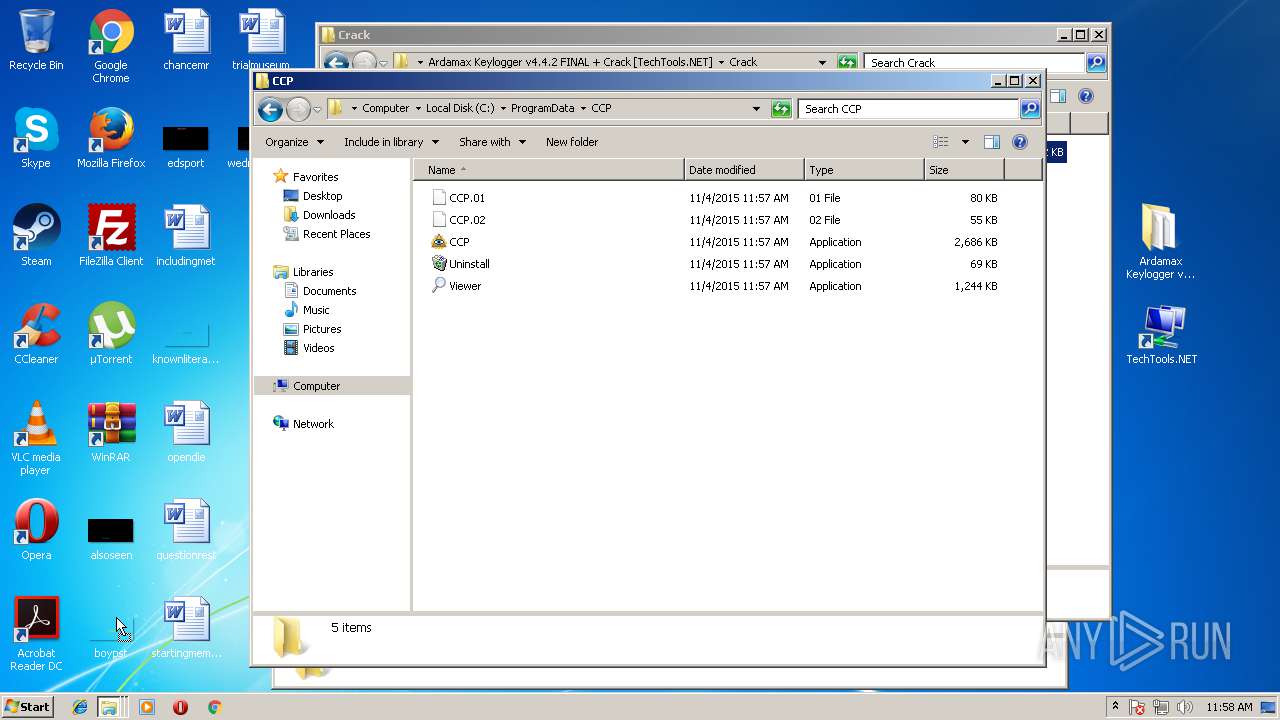
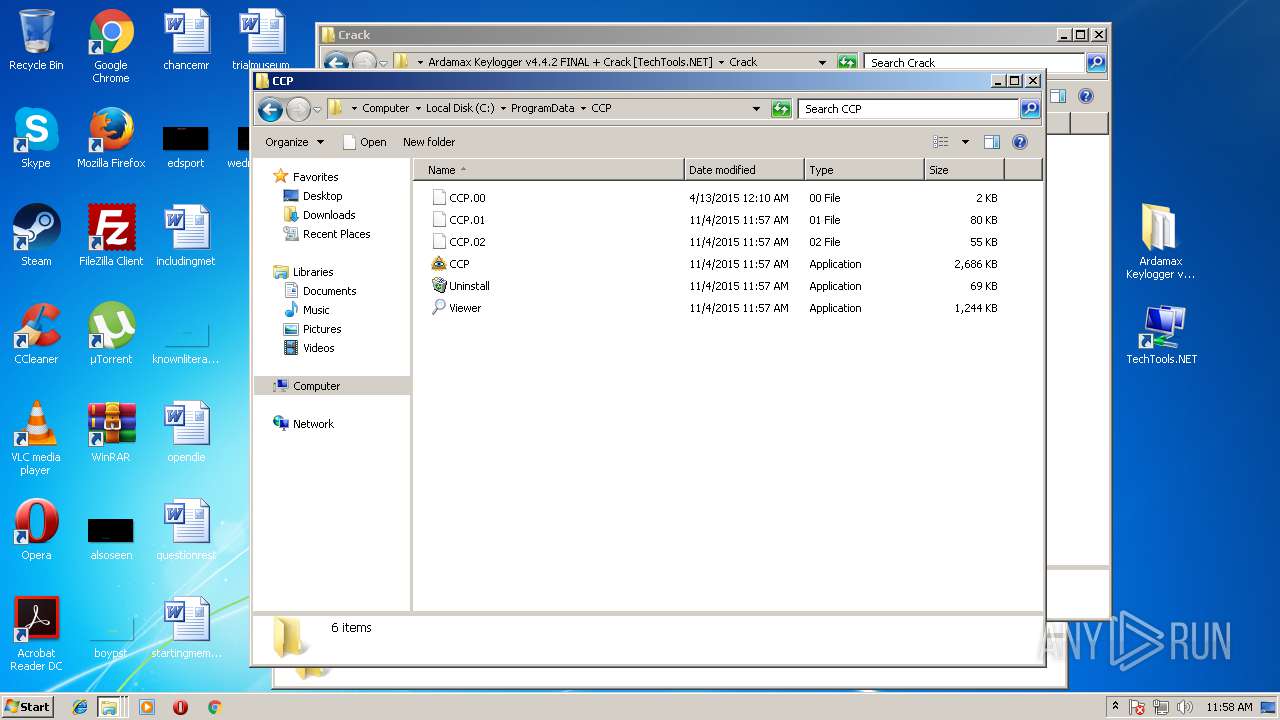
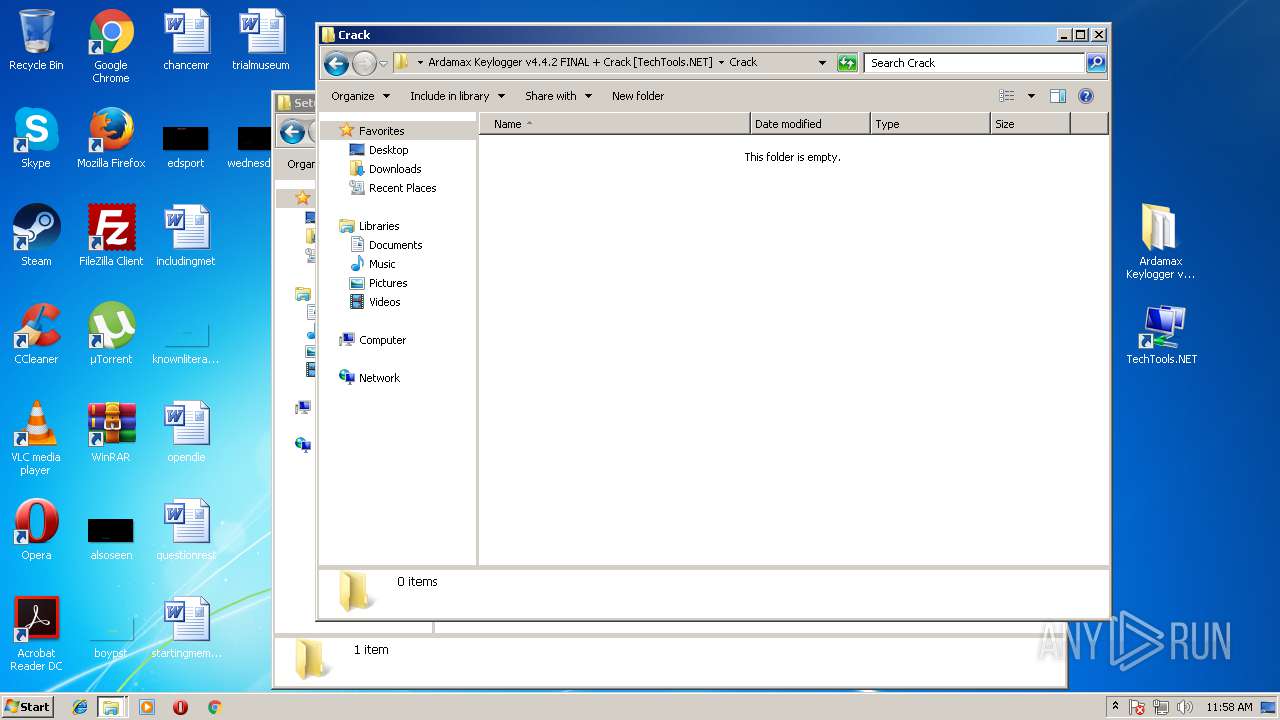
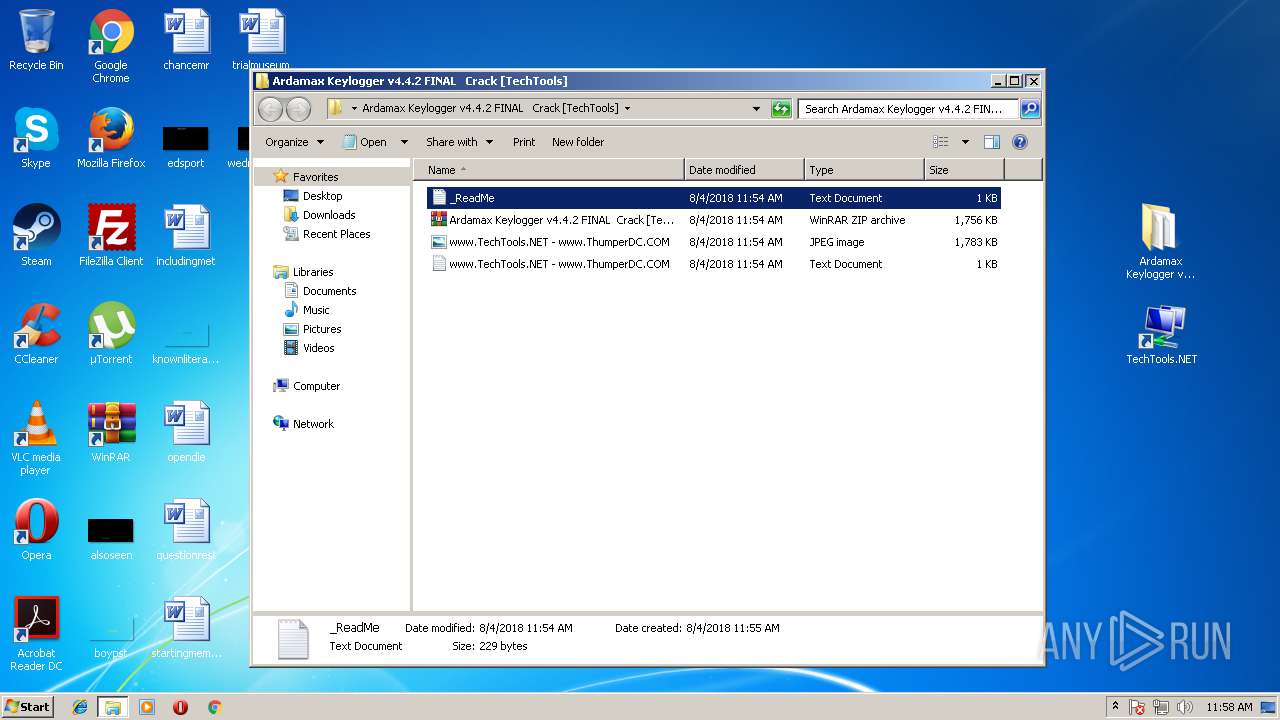
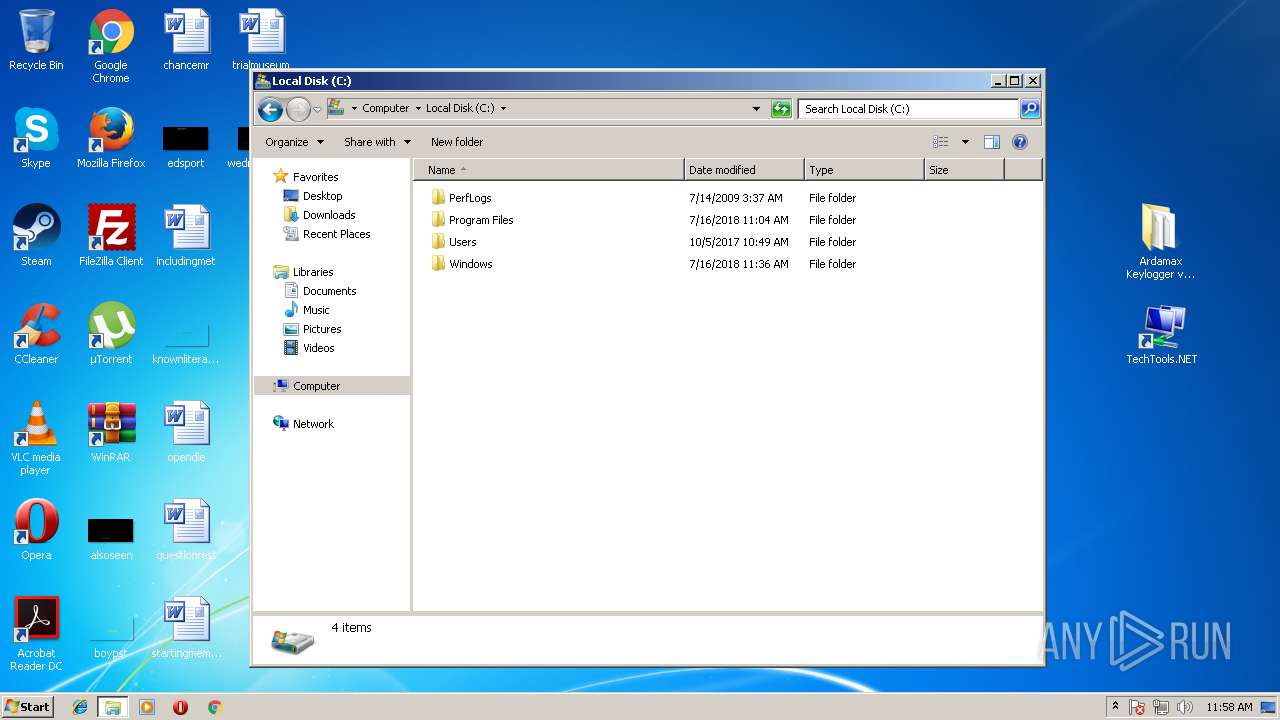
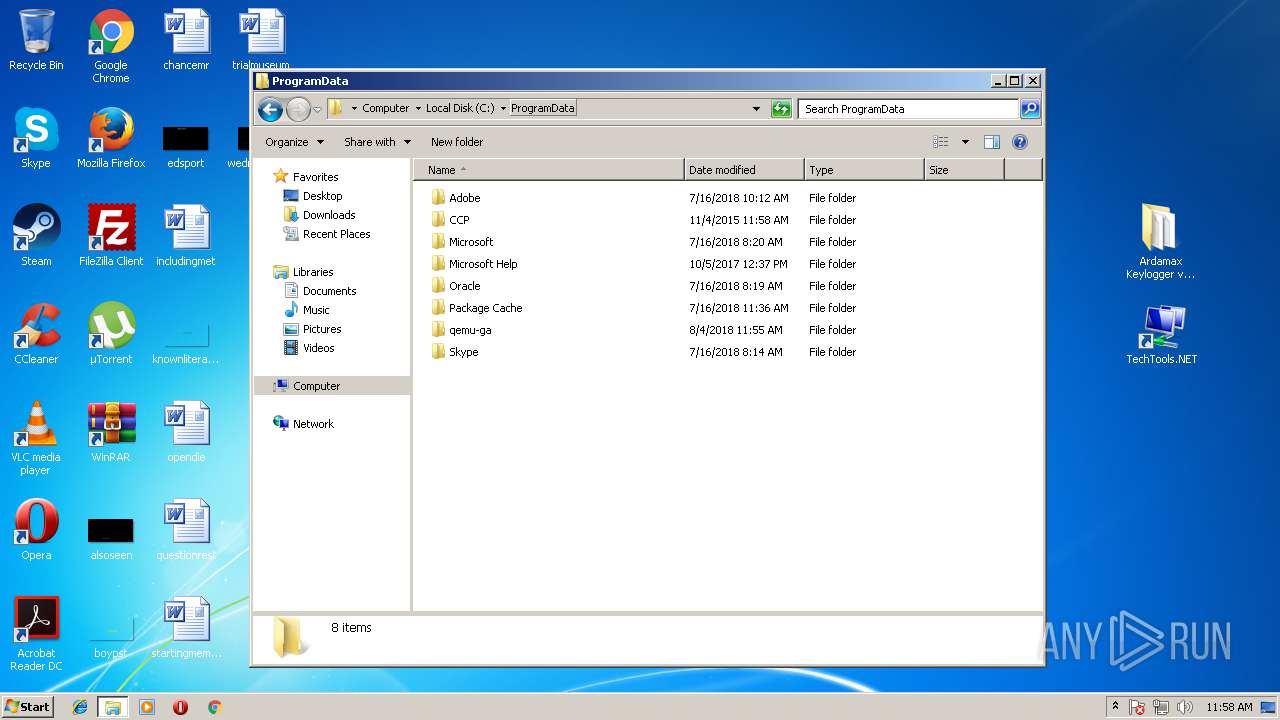
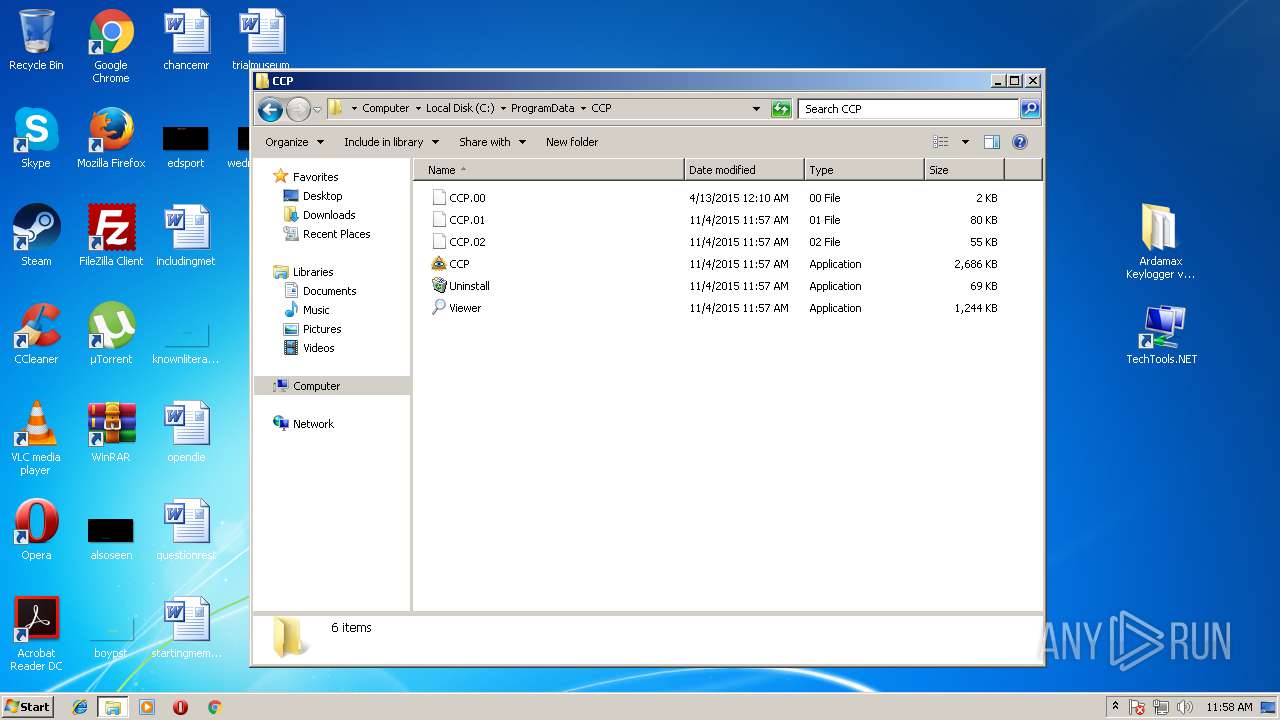
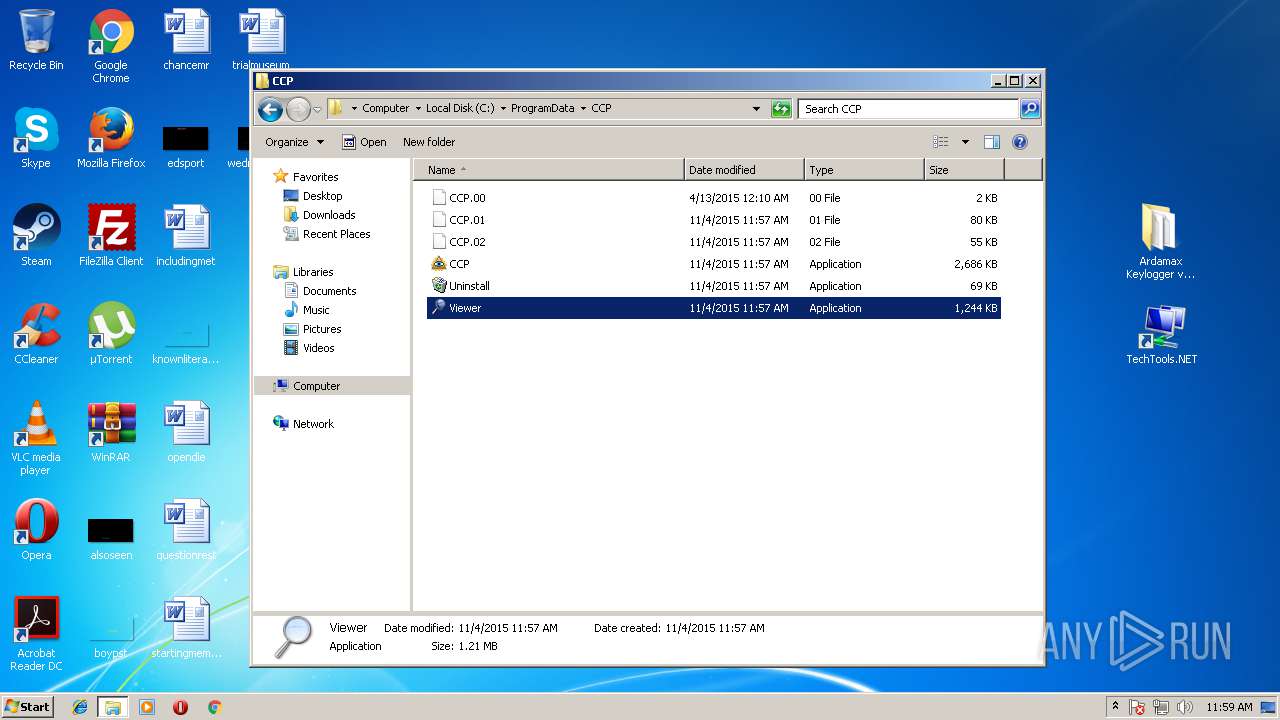
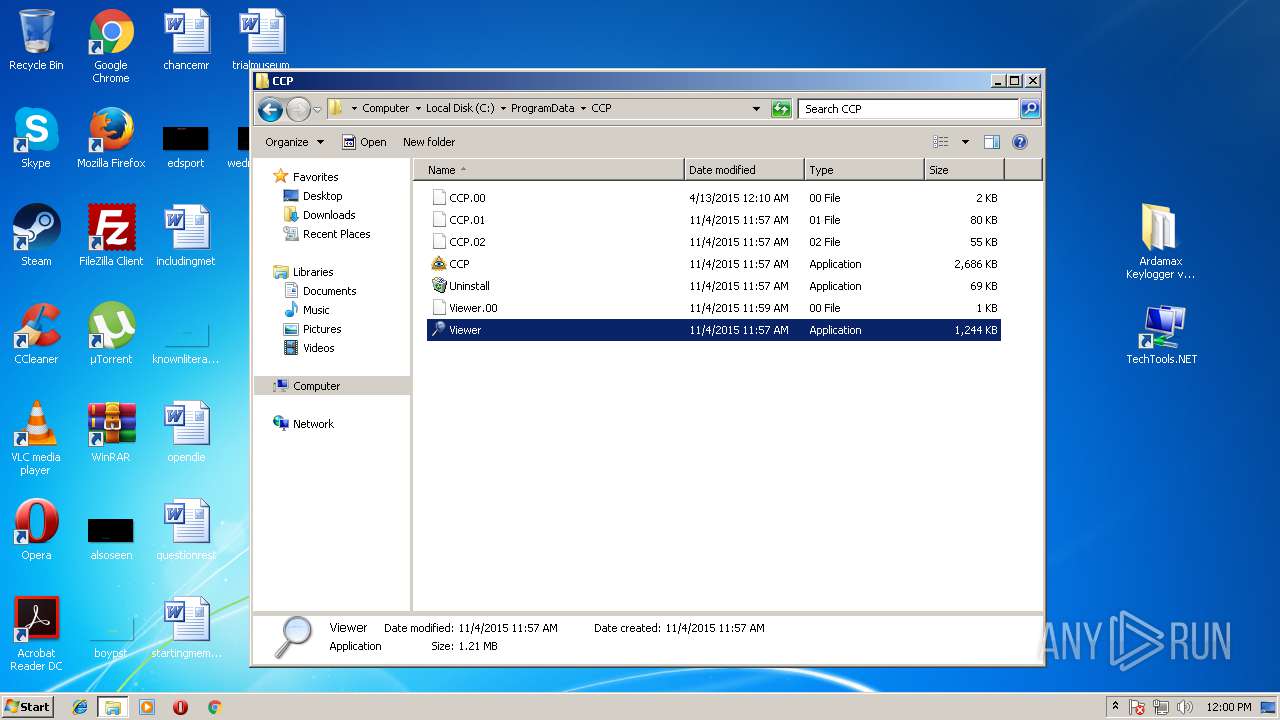
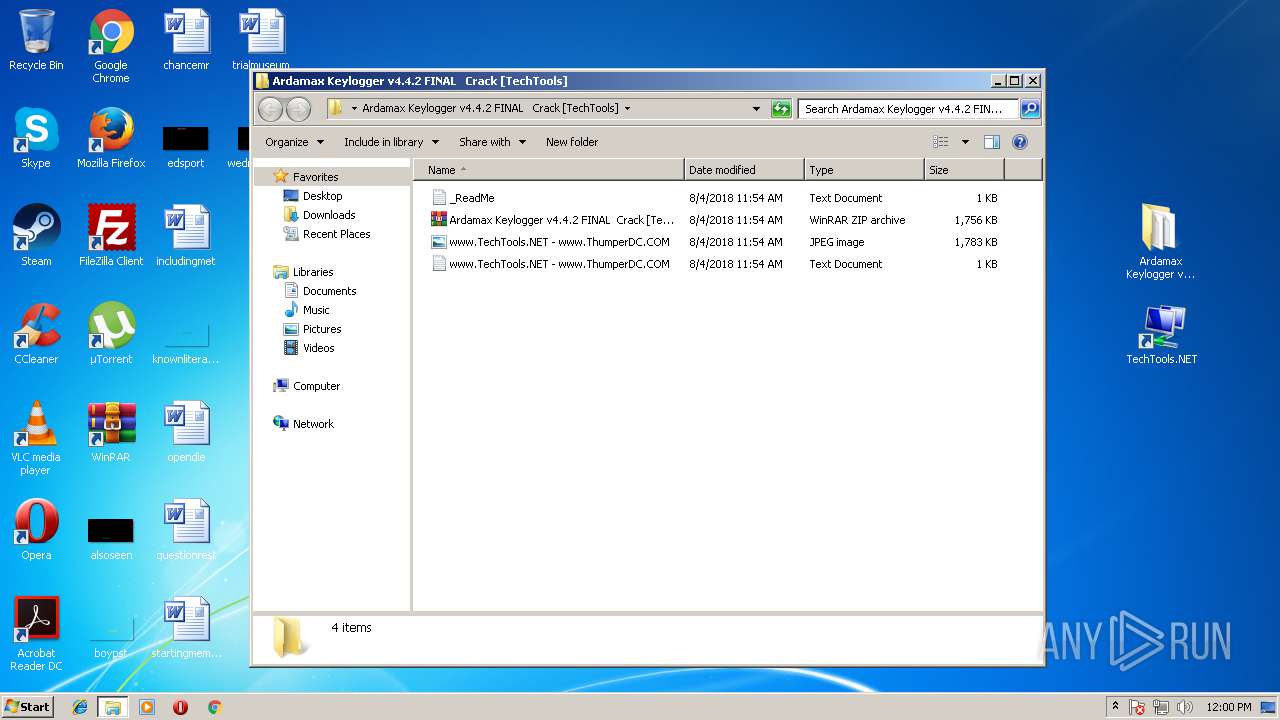
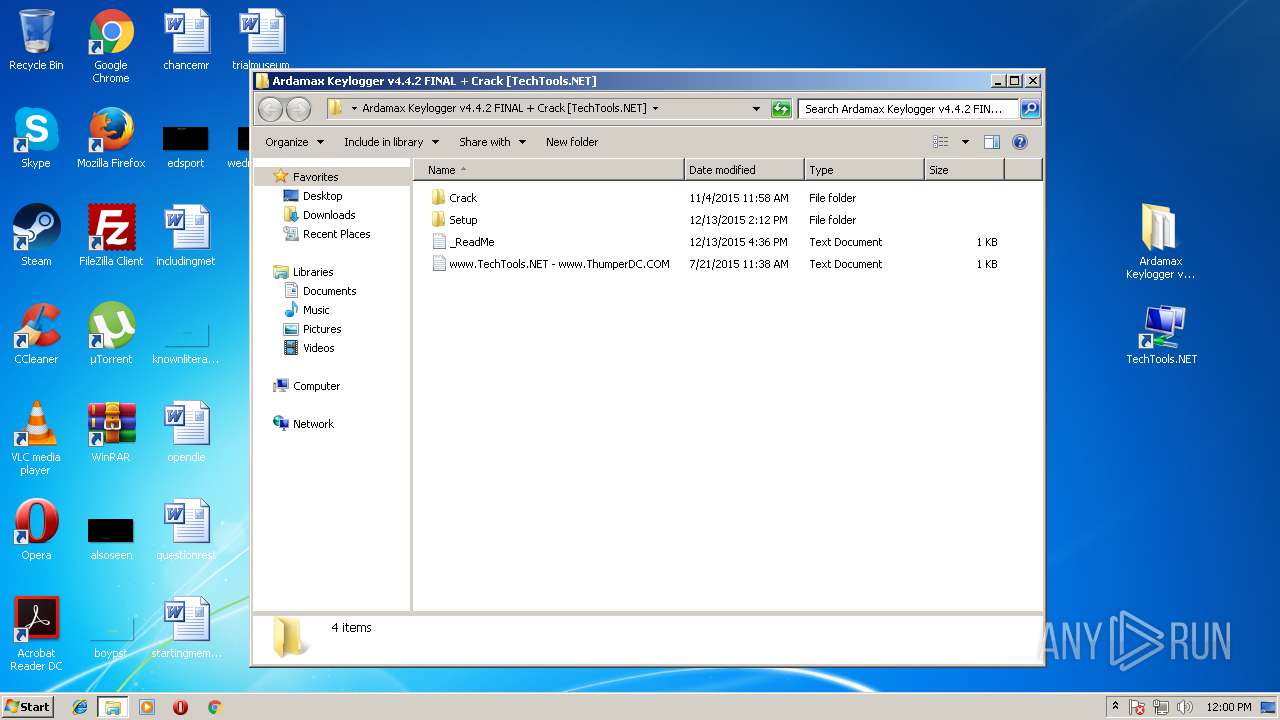
| File name: | Ardamax Keylogger v4.4.2 FINAL Crack [TechTools].zip |
| Full analysis: | https://app.any.run/tasks/cc76826d-59a6-4cf1-815a-ea1b8fd66226 |
| Verdict: | Malicious activity |
| Analysis date: | August 04, 2018, 10:55:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 8681DCB953C6957860A848C2589C281F |
| SHA1: | E25675A93D7350E149B62FA1BB26700AE18016BF |
| SHA256: | 5A659B86D1FB5A9AACD3890407DABF005654E26FABAD5679F6F06B3312AEB2DE |
| SSDEEP: | 49152:QlMni7u+B7WXrKPGZDvMmnBVE0rs3XgtnHI9X3PBLIN9zSG:QlMi7u+B/PevNj/iXgtHIpsVSG |
MALICIOUS
Loads dropped or rewritten executable
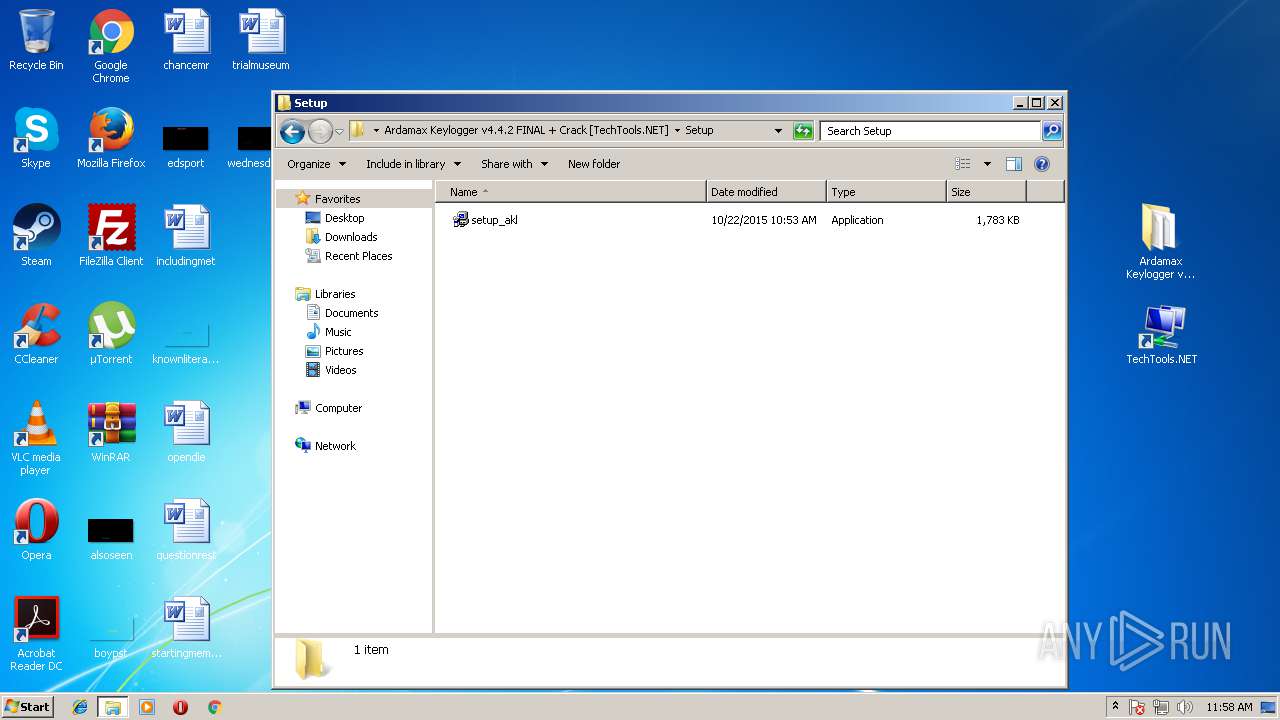
- setup_akl .exe (PID: 2536)
- setup_akl .exe (PID: 3528)
Application was dropped or rewritten from another process
- lzma.exe (PID: 4024)
- lzma.exe (PID: 980)
- lzma.exe (PID: 2188)
- ns21AE.tmp (PID: 3768)
- ns250D.tmp (PID: 3952)
- lzma.exe (PID: 1516)
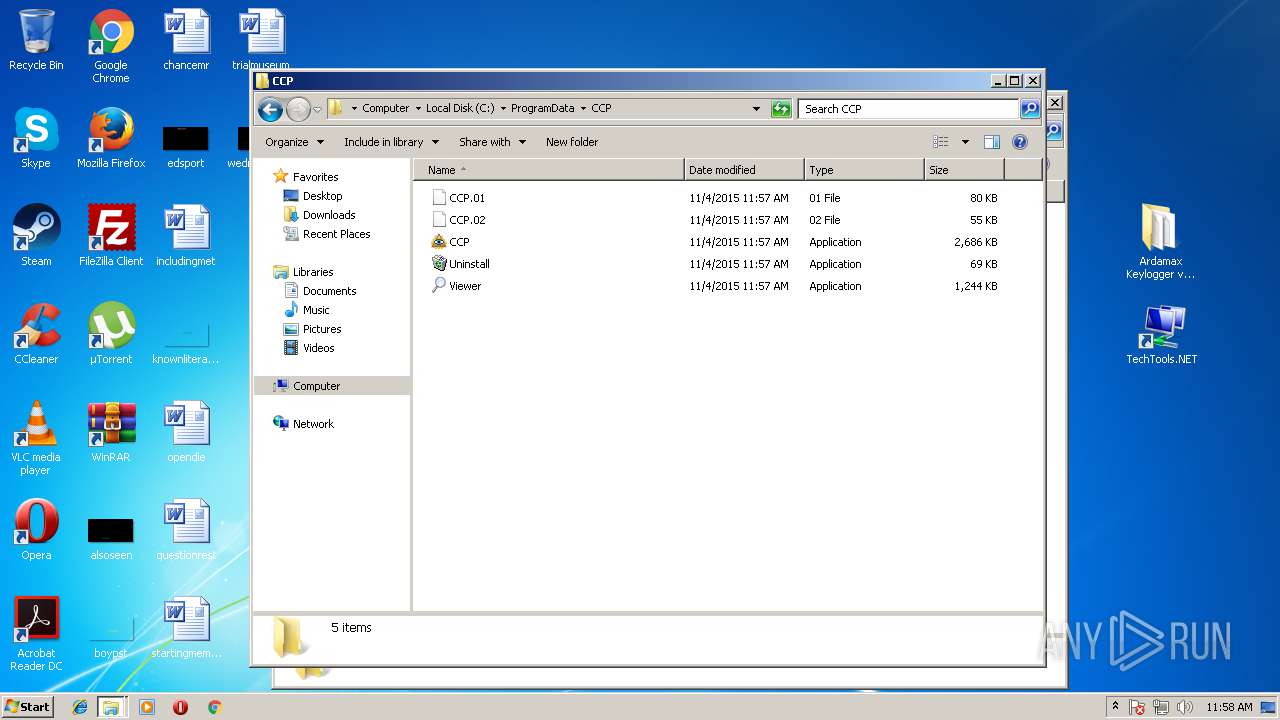
- CCP.exe (PID: 1972)
- ns2395.tmp (PID: 3876)
- CCP.exe (PID: 2076)
- CCP.exe (PID: 2648)
- ns229A.tmp (PID: 2348)
- CCP.exe (PID: 2800)
- setup_akl .exe (PID: 3528)
- setup_akl .exe (PID: 2536)
- setup_akl .exe (PID: 3760)
- Viewer.exe (PID: 3756)
- Viewer.exe (PID: 336)
- setup_akl .exe (PID: 2820)
SUSPICIOUS
Starts application with an unusual extension
- setup_akl .exe (PID: 2820)
Executable content was dropped or overwritten
- lzma.exe (PID: 980)
- lzma.exe (PID: 4024)
- setup_akl .exe (PID: 2536)
- lzma.exe (PID: 1516)
- setup_akl .exe (PID: 3760)
- setup_akl .exe (PID: 2820)
- setup_akl .exe (PID: 3528)
- lzma.exe (PID: 2188)
Application launched itself
- setup_akl .exe (PID: 3528)
- setup_akl .exe (PID: 3760)
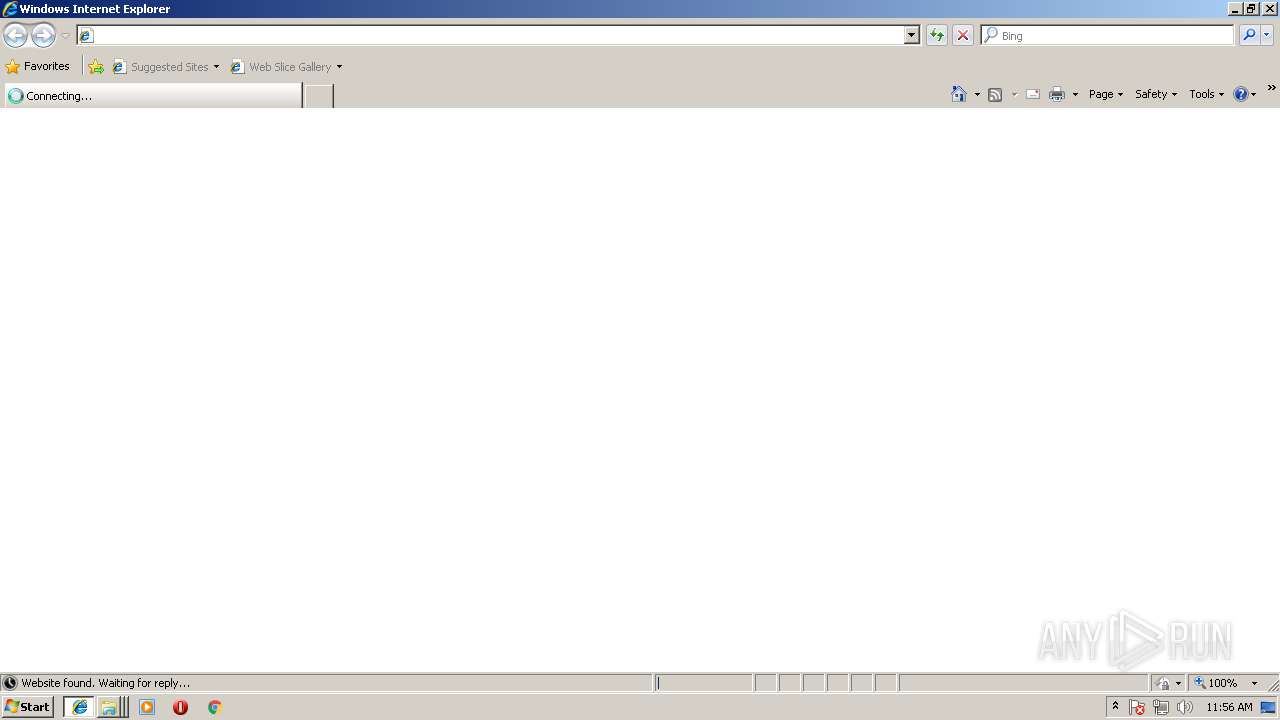
Starts Internet Explorer
- setup_akl .exe (PID: 2536)
INFO
Dropped object may contain URL's
- setup_akl .exe (PID: 2820)
- iexplore.exe (PID: 3400)
- iexplore.exe (PID: 2756)
Changes internet zones settings
- iexplore.exe (PID: 3400)
Creates files in the user directory
- iexplore.exe (PID: 2756)
Changes settings of System certificates
- iexplore.exe (PID: 2756)
Reads Internet Cache Settings
- iexplore.exe (PID: 2756)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2756)
Reads internet explorer settings
- iexplore.exe (PID: 2756)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | None |
| ZipModifyDate: | 2018:08:04 10:54:26 |
| ZipCRC: | 0x4e3b6d87 |
| ZipCompressedSize: | 1825165 |
| ZipUncompressedSize: | 1825165 |
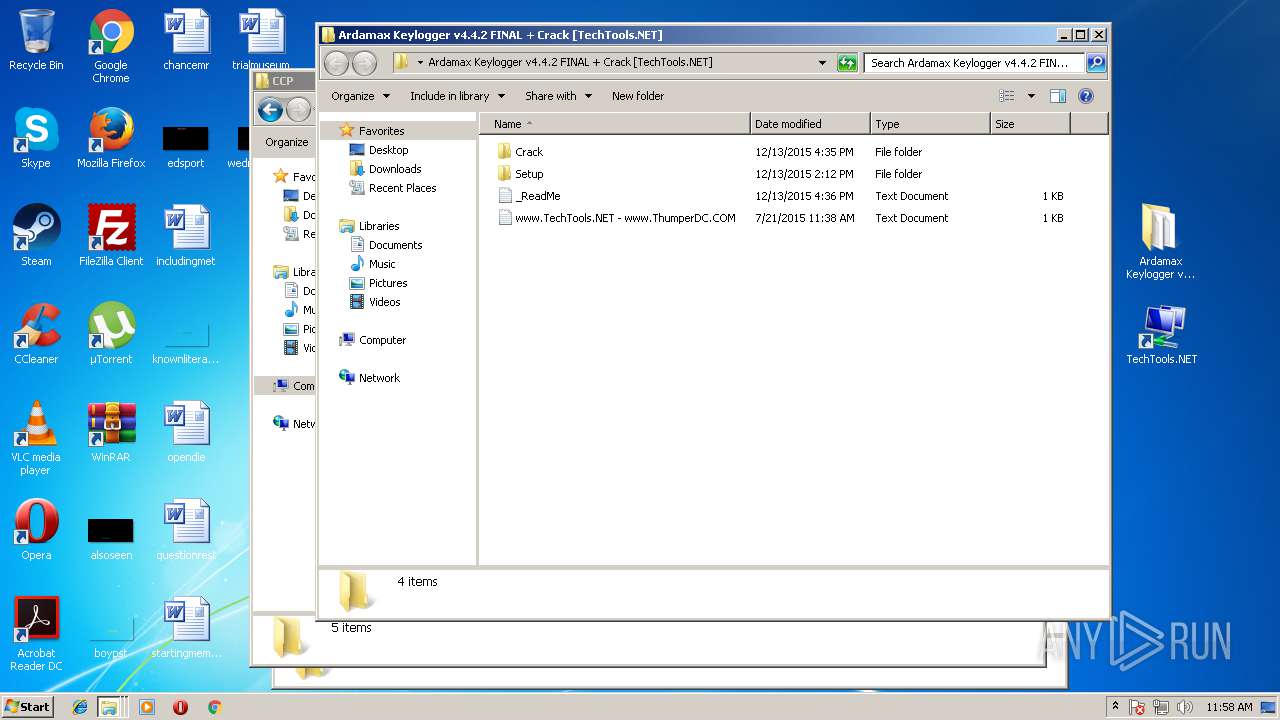
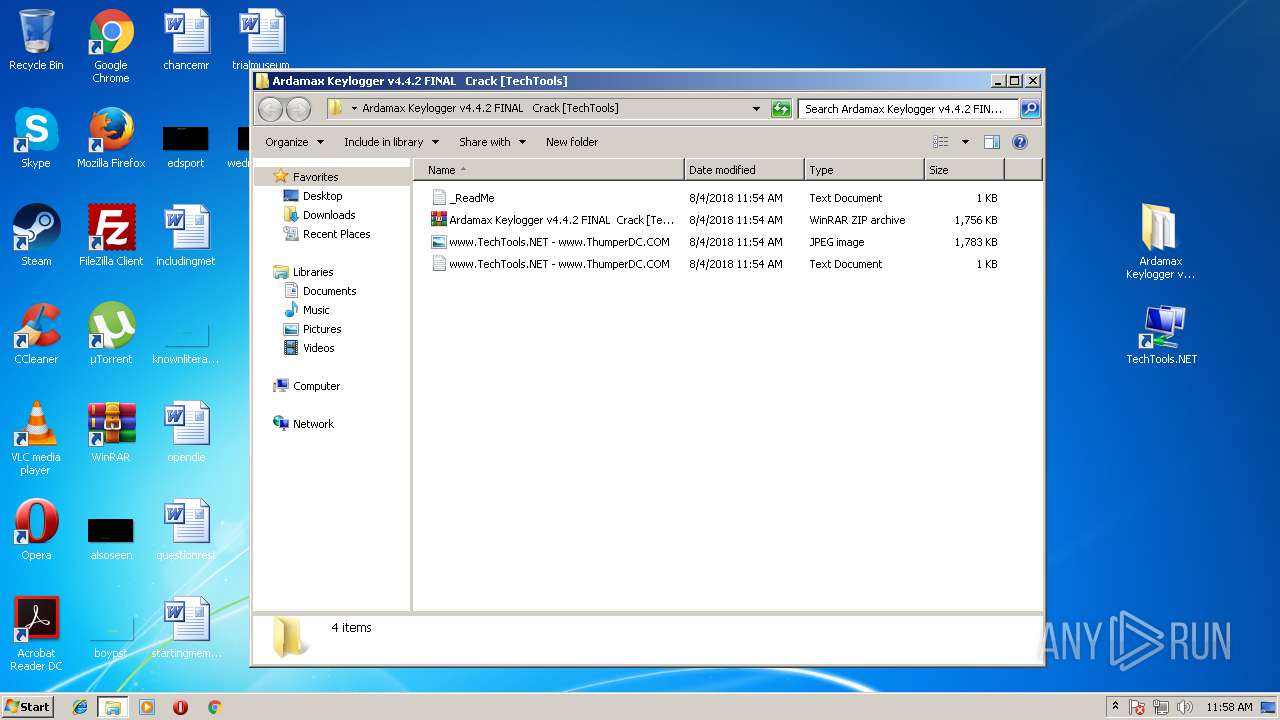
| ZipFileName: | Ardamax Keylogger v4.4.2 FINAL Crack [TechTools]/www.TechTools.NET - www.ThumperDC.COM.jpg |
Total processes
91
Monitored processes
30
Malicious processes
8
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 336 | "C:\ProgramData\CCP\Viewer.exe" | C:\ProgramData\CCP\Viewer.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 | |||||||||||||||
| 980 | "lzma.exe" "d" "1.lz" "CCP.exe" | C:\ProgramData\CCP\lzma.exe | ns21AE.tmp | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1044 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Ardamax Keylogger v4.4.2 FINAL Crack [TechTools]\Ardamax Keylogger v4.4.2 FINAL Crack [TechTools.NET].zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1148 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1516 | "lzma.exe" "d" "2.lz" "CCP.01" | C:\ProgramData\CCP\lzma.exe | ns229A.tmp | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1592 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1972 | "C:\ProgramData\CCP\CCP.exe" | C:\ProgramData\CCP\CCP.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
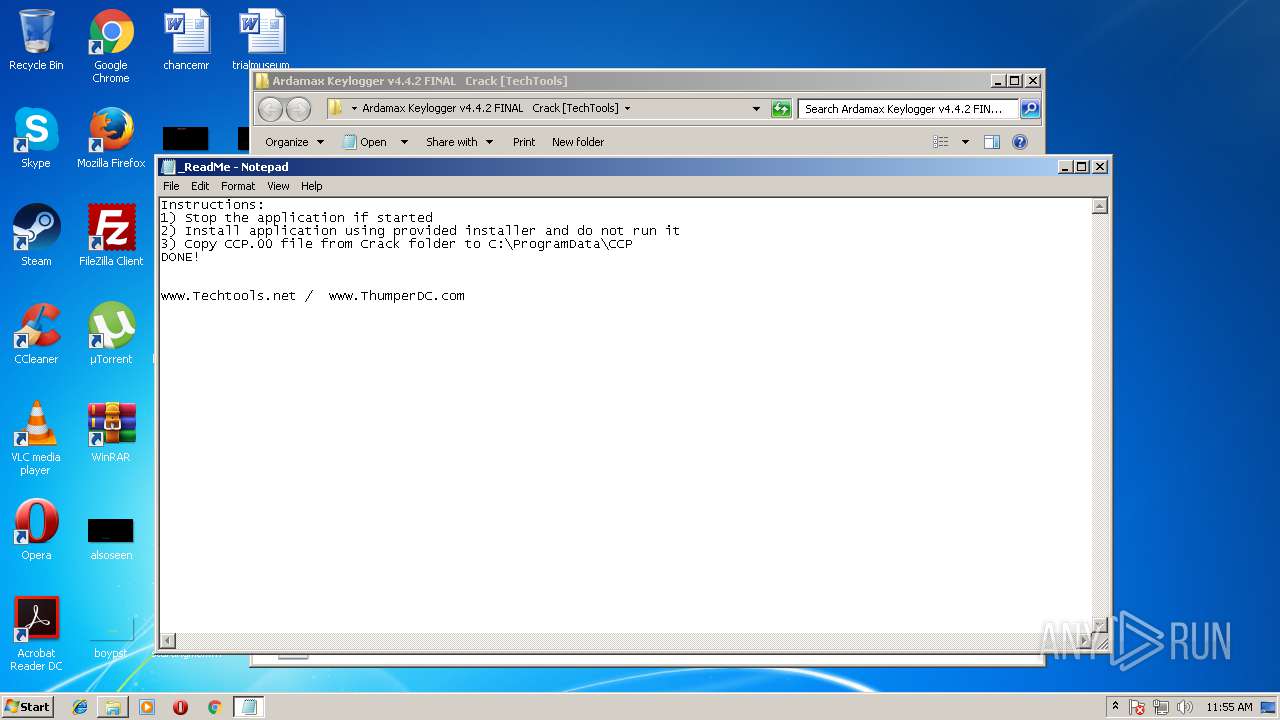
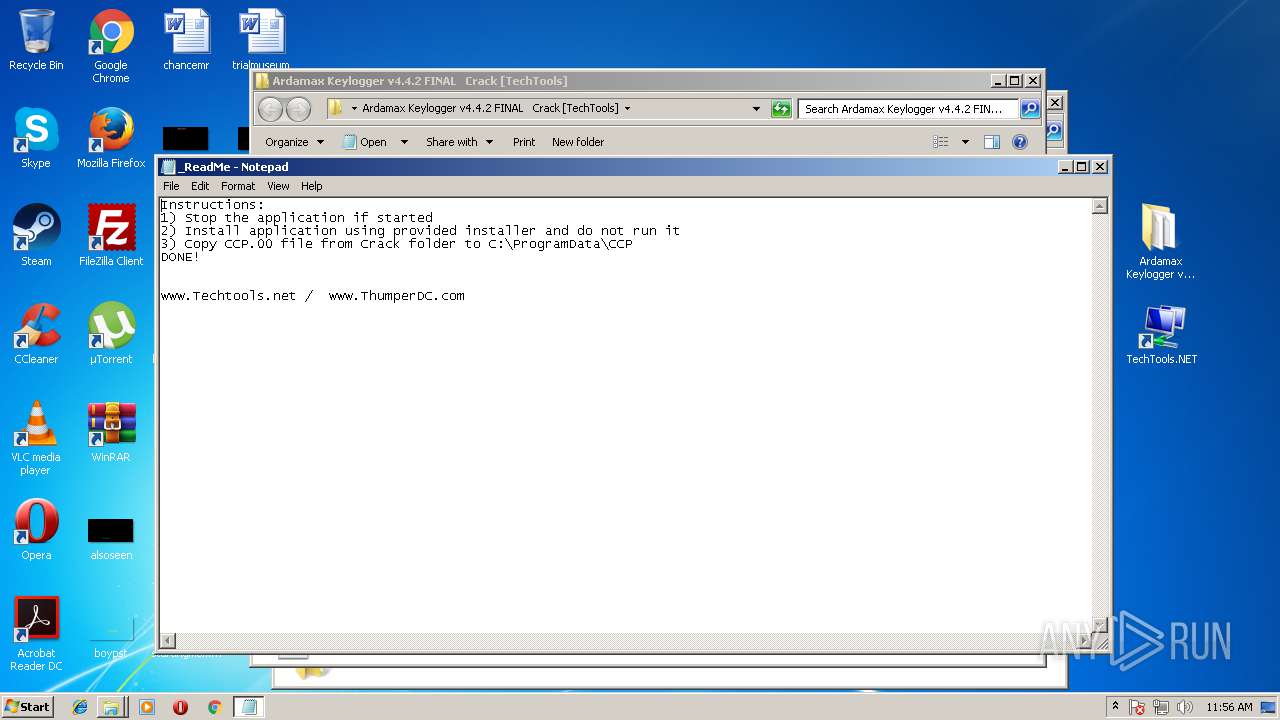
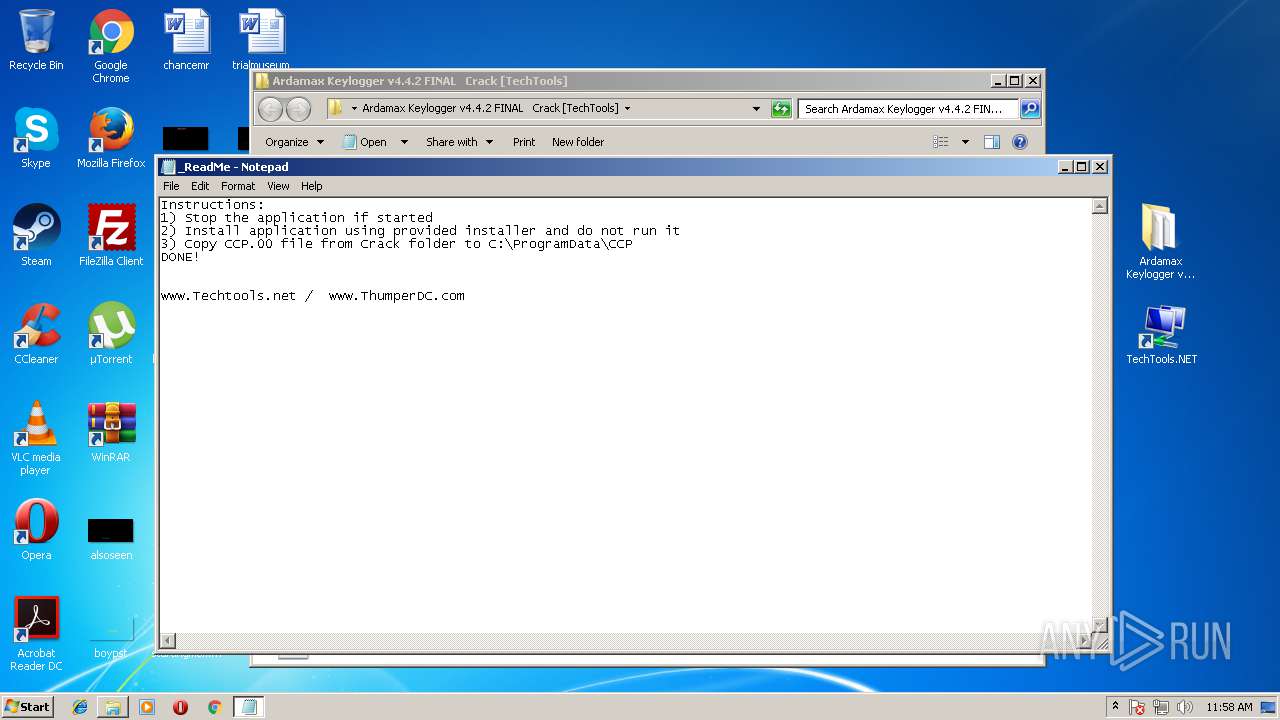
| 2032 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Ardamax Keylogger v4.4.2 FINAL Crack [TechTools]\_ReadMe.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | |||||||||||||||
| 2076 | "C:\ProgramData\CCP\CCP.exe" | C:\ProgramData\CCP\CCP.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2172 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Ardamax Keylogger v4.4.2 FINAL Crack [TechTools]\_ReadMe.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 320
Read events
1 206
Write events
113
Delete events
1
Modification events
| (PID) Process: | (3832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3832) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\59\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Ardamax Keylogger v4.4.2 FINAL Crack [TechTools].zip | |||
| (PID) Process: | (3832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF2C0000002C000000EC03000021020000 | |||
| (PID) Process: | (3832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
25
Suspicious files
22
Text files
20
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2820 | setup_akl .exe | C:\ProgramData\CCP\1.dat | — | |
MD5:— | SHA256:— | |||
| 2820 | setup_akl .exe | C:\Users\admin\AppData\Local\Temp\nsu423.tmp\ns21AE.tmp | — | |
MD5:— | SHA256:— | |||
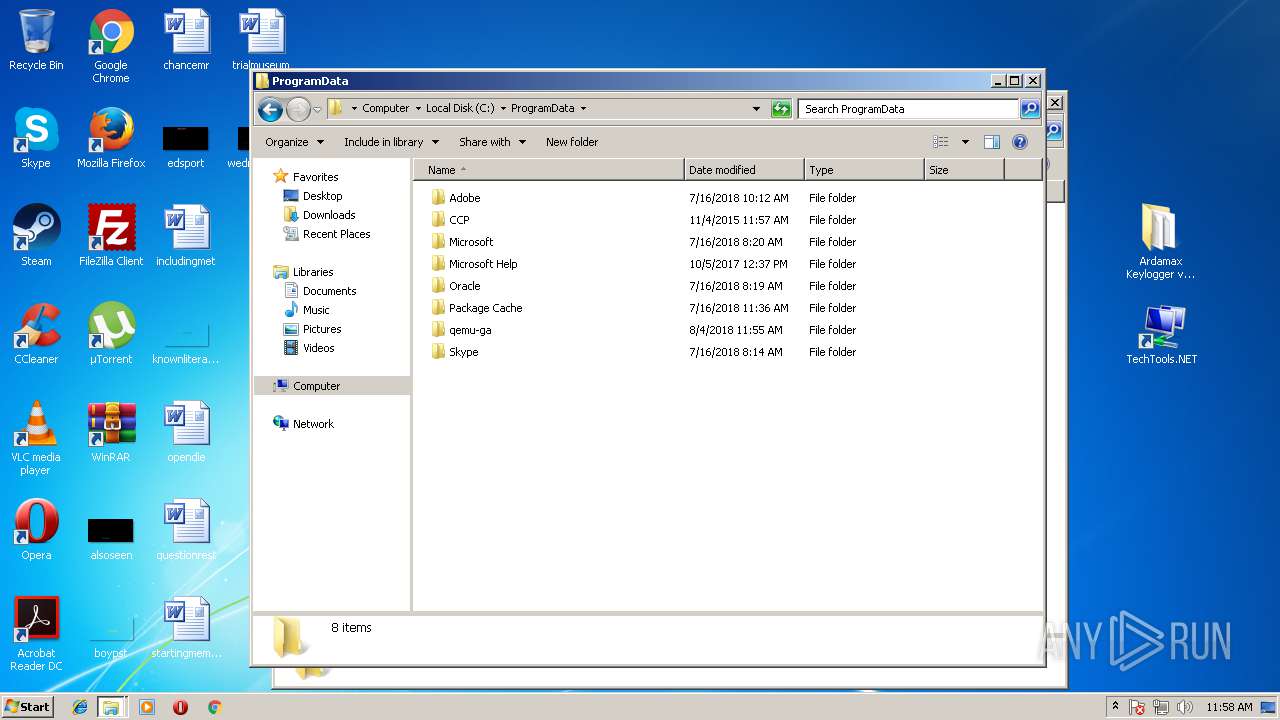
| 2820 | setup_akl .exe | C:\ProgramData\CCP\data | text | |
MD5:— | SHA256:— | |||
| 2820 | setup_akl .exe | C:\ProgramData\CCP\3.lz | — | |
MD5:— | SHA256:— | |||
| 2820 | setup_akl .exe | C:\Users\admin\AppData\Local\Temp\nsu423.tmp\ns2395.tmp | — | |
MD5:— | SHA256:— | |||
| 2820 | setup_akl .exe | C:\ProgramData\CCP\2.dat | binary | |
MD5:— | SHA256:— | |||
| 2820 | setup_akl .exe | C:\ProgramData\CCP\2.lz | lzma | |
MD5:— | SHA256:— | |||
| 2820 | setup_akl .exe | C:\Users\admin\AppData\Local\Temp\nsu423.tmp\ns229A.tmp | executable | |
MD5:— | SHA256:— | |||
| 2820 | setup_akl .exe | C:\Users\admin\AppData\Local\Temp\nsu423.tmp\DcryptDll.dll | executable | |
MD5:904BEEBEC2790EE2CA0C90FC448AC7E0 | SHA256:F730D9385BF72EAC5D579BCF1F7E4330F1D239CA1054D4EAD48E9E363D9F4222 | |||
| 980 | lzma.exe | C:\ProgramData\CCP\CCP.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
20
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2756 | iexplore.exe | GET | 301 | 69.162.154.237:80 | http://www.ardamax.com/keylogger/ | US | html | 242 b | malicious |
3400 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2756 | iexplore.exe | 69.162.154.237:443 | www.ardamax.com | Steadfast | US | unknown |
2756 | iexplore.exe | 216.58.215.234:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2756 | iexplore.exe | 216.58.215.232:443 | www.googletagmanager.com | Google Inc. | US | whitelisted |
2756 | iexplore.exe | 216.58.210.3:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
2756 | iexplore.exe | 216.58.215.238:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
2756 | iexplore.exe | 157.240.20.38:443 | www.facebook.com | Facebook, Inc. | US | whitelisted |
2756 | iexplore.exe | 74.125.143.156:443 | stats.g.doubleclick.net | Google Inc. | US | whitelisted |
3400 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2756 | iexplore.exe | 157.240.20.19:443 | connect.facebook.net | Facebook, Inc. | US | whitelisted |
2756 | iexplore.exe | 69.162.154.237:80 | www.ardamax.com | Steadfast | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.ardamax.com |
| malicious |
www.bing.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
connect.facebook.net |
| whitelisted |
www.facebook.com |
| whitelisted |
stats.g.doubleclick.net |
| whitelisted |