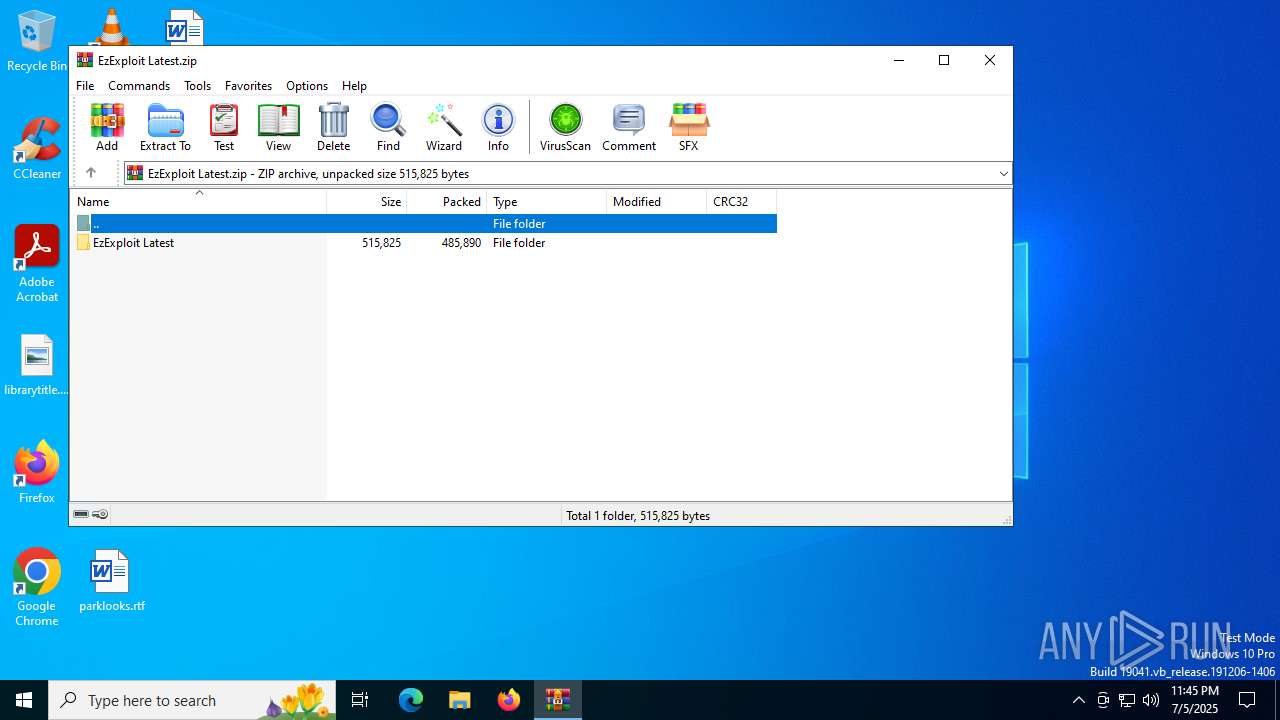
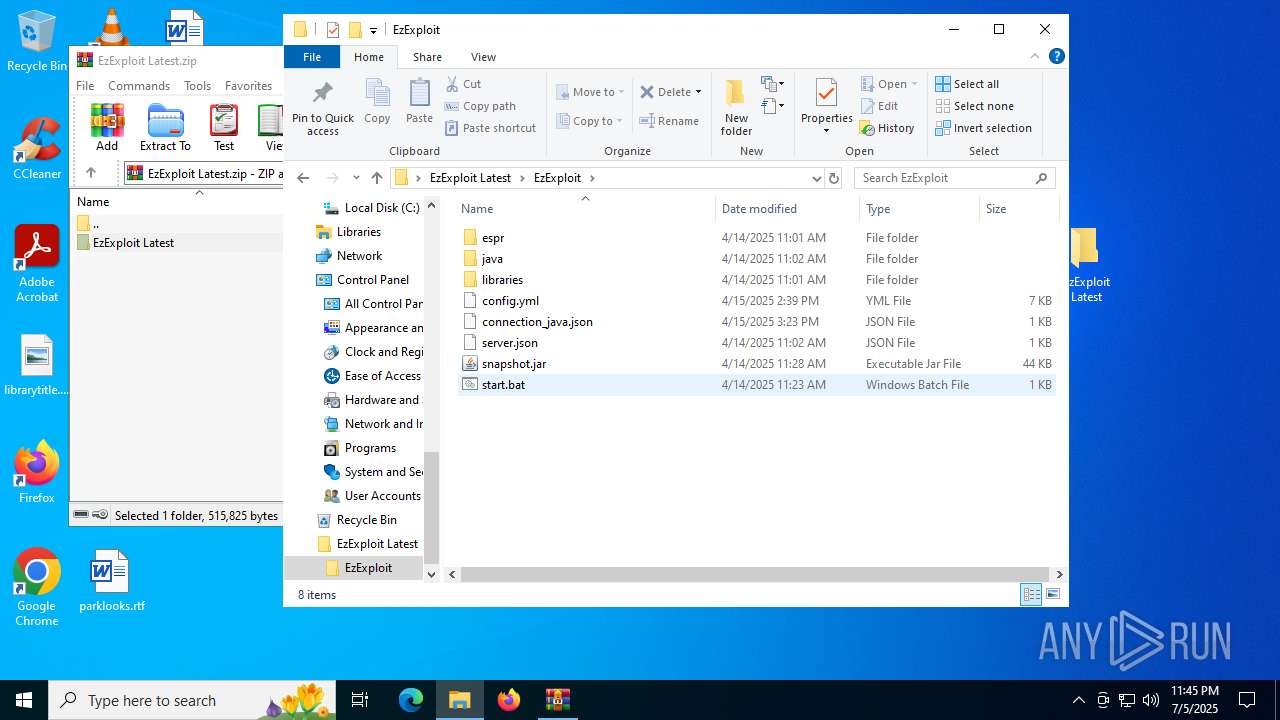
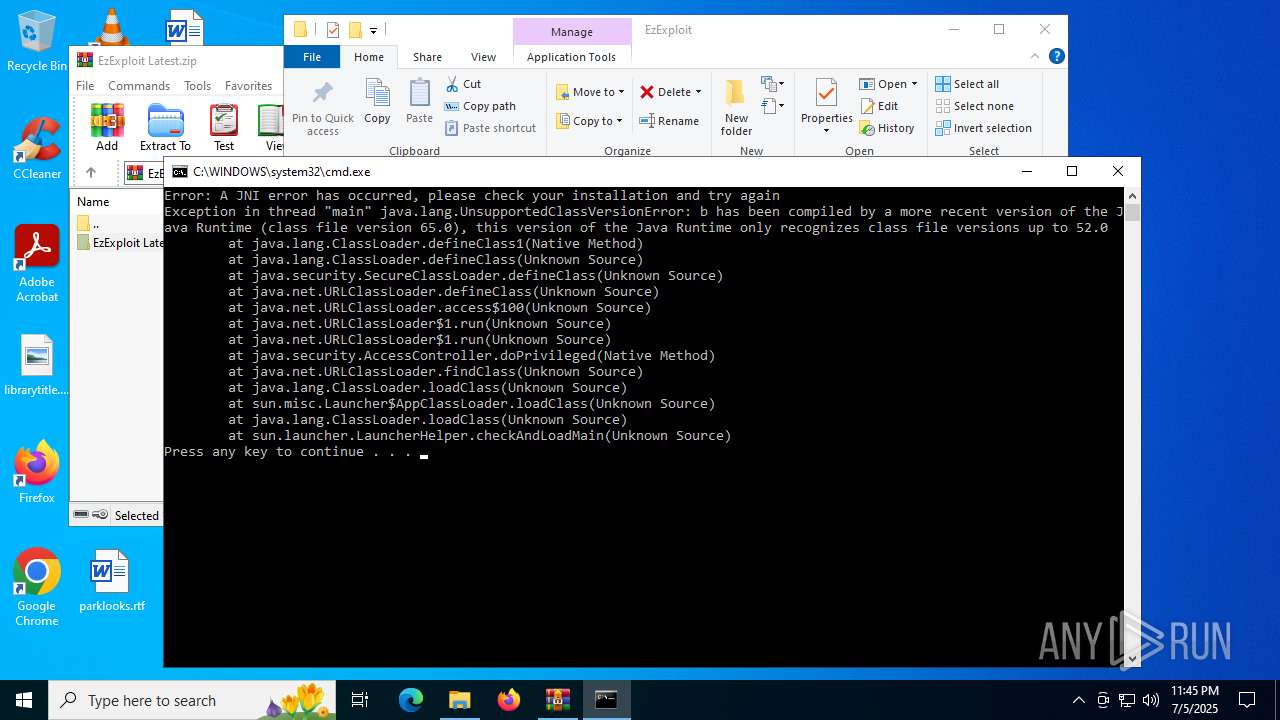
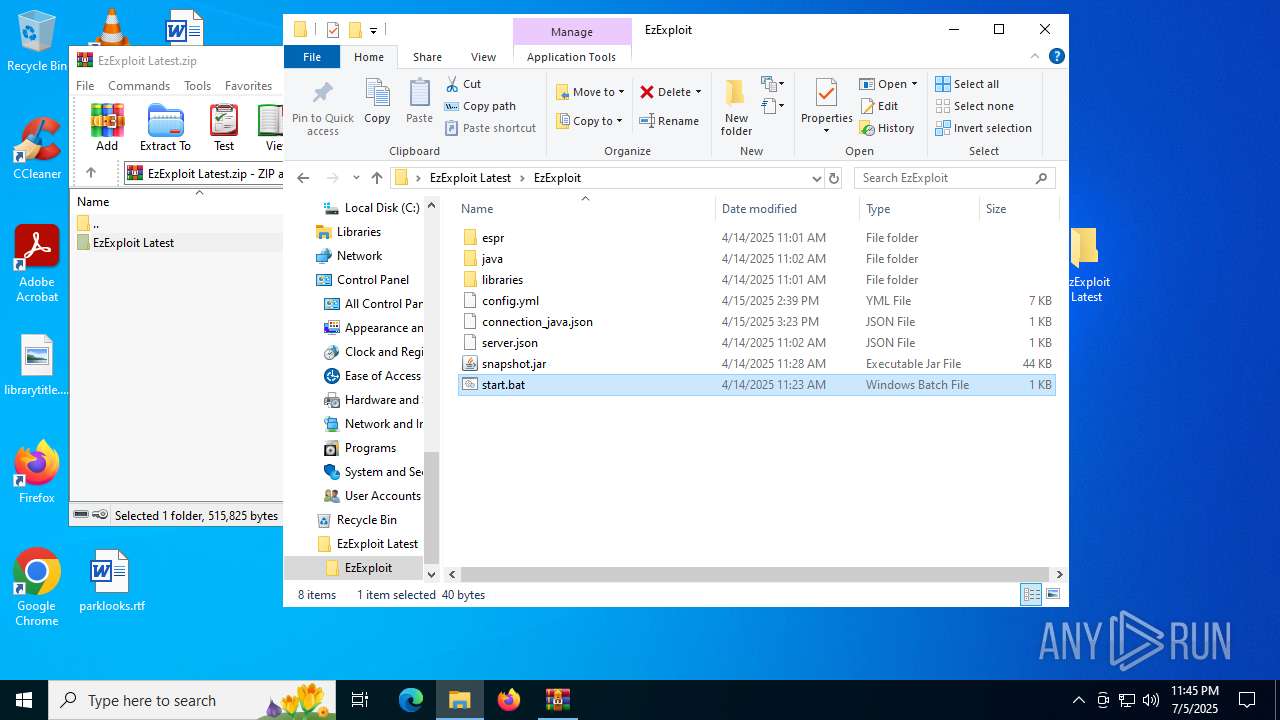
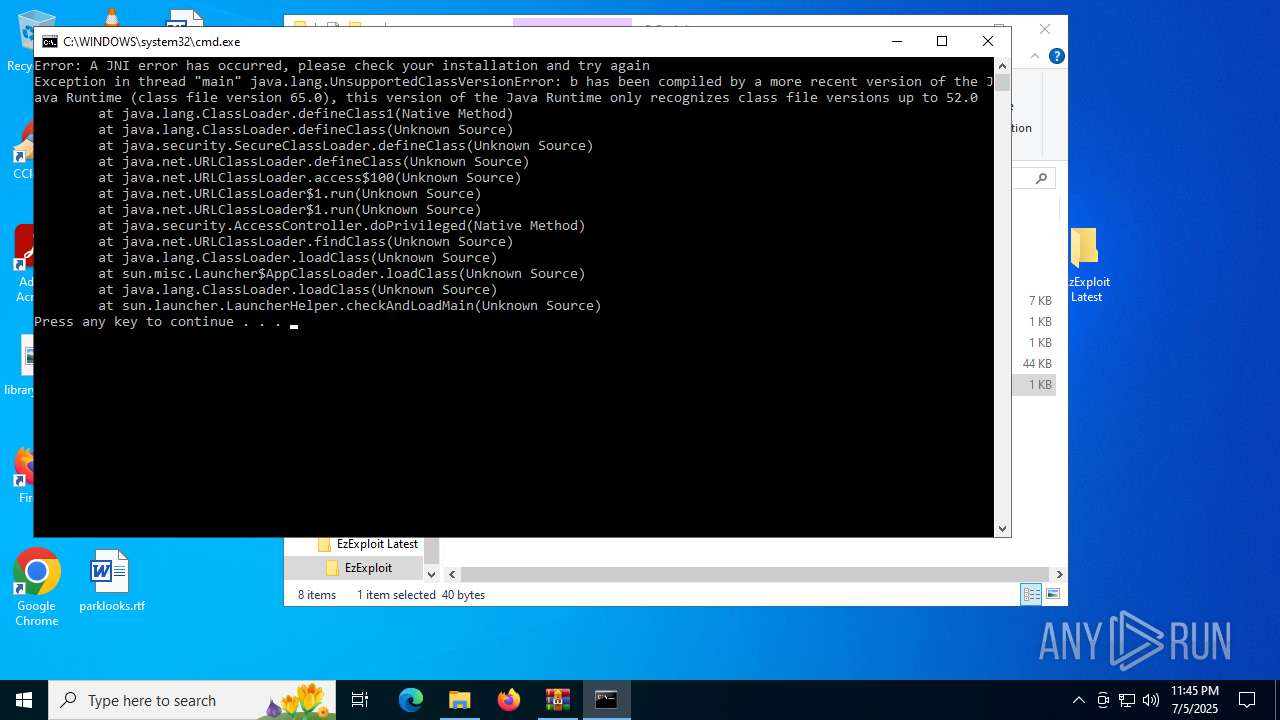
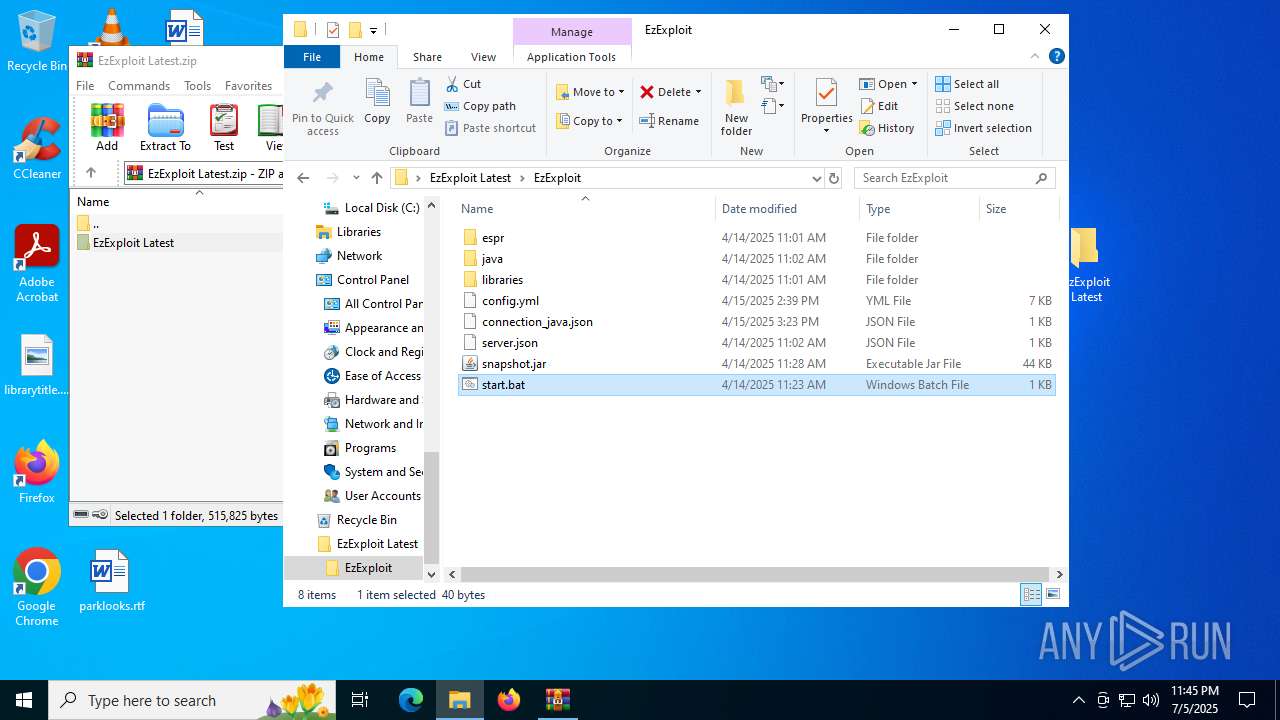
| File name: | EzExploit Latest.zip |
| Full analysis: | https://app.any.run/tasks/3641f97c-1955-4b47-ba37-4a618647ea6d |
| Verdict: | Malicious activity |
| Analysis date: | July 05, 2025, 23:44:56 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 5996C2043B7521C8E597C835A9AF9185 |
| SHA1: | C353EF679FDF9DCB51CD4D20F7EA7BB49A03B9F9 |
| SHA256: | 5A5EC4036808E7CA225BA397729B98B5CA4D1E8073B05E650CF50E53A66B7E2E |
| SSDEEP: | 12288:CludmdD3o5EDN8mDDt9Dl0HwcLDxbE0DTsvLEydq:2udID3o5EDNjDt9DlywcDxbE0DTdn |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7052)
SUSPICIOUS
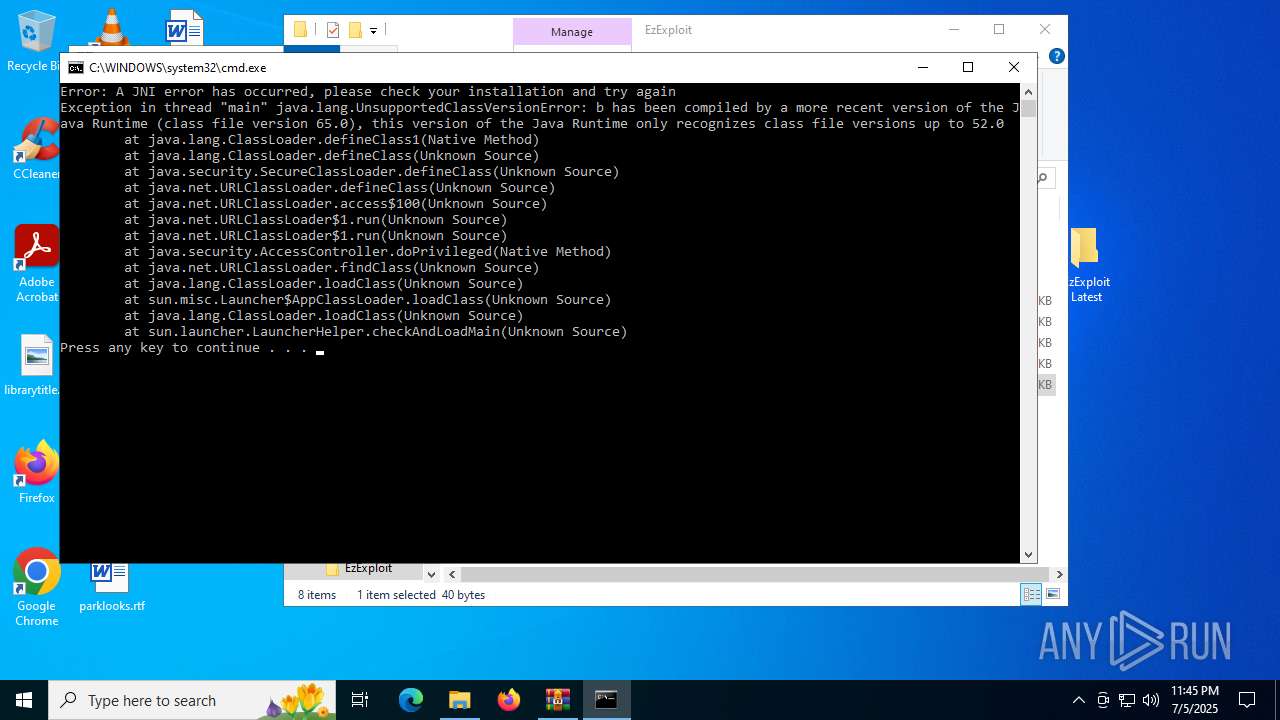
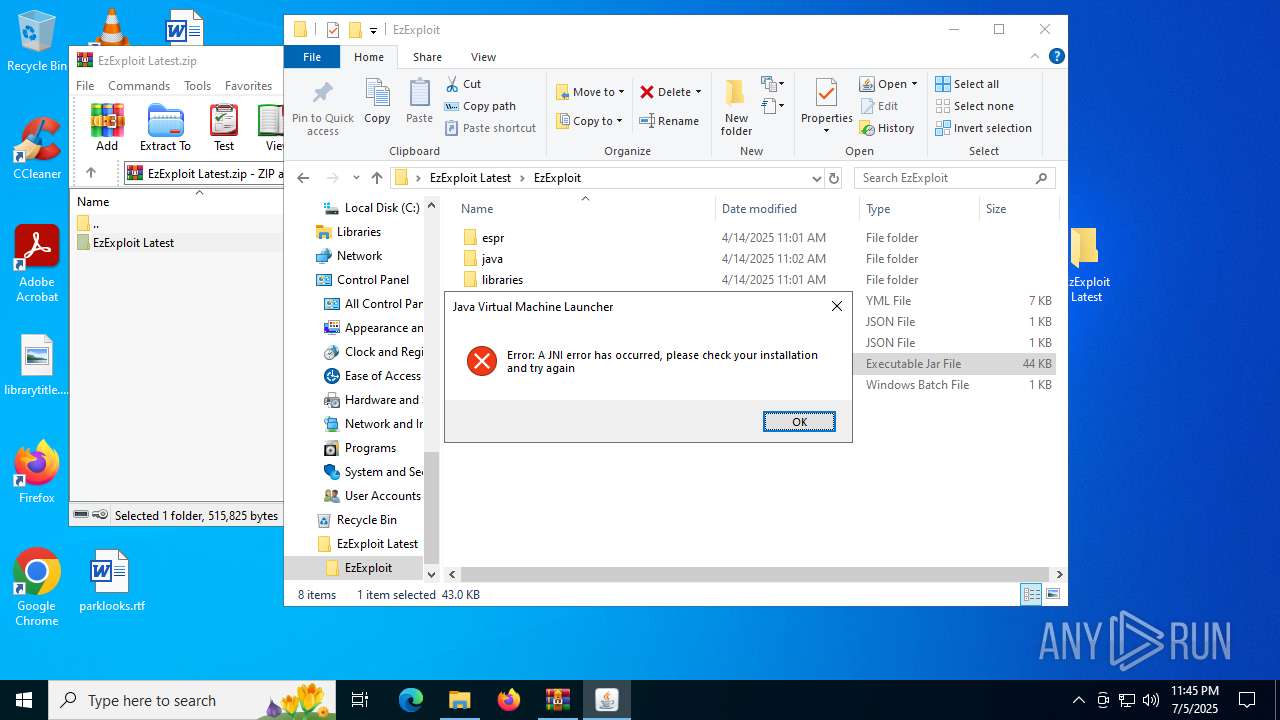
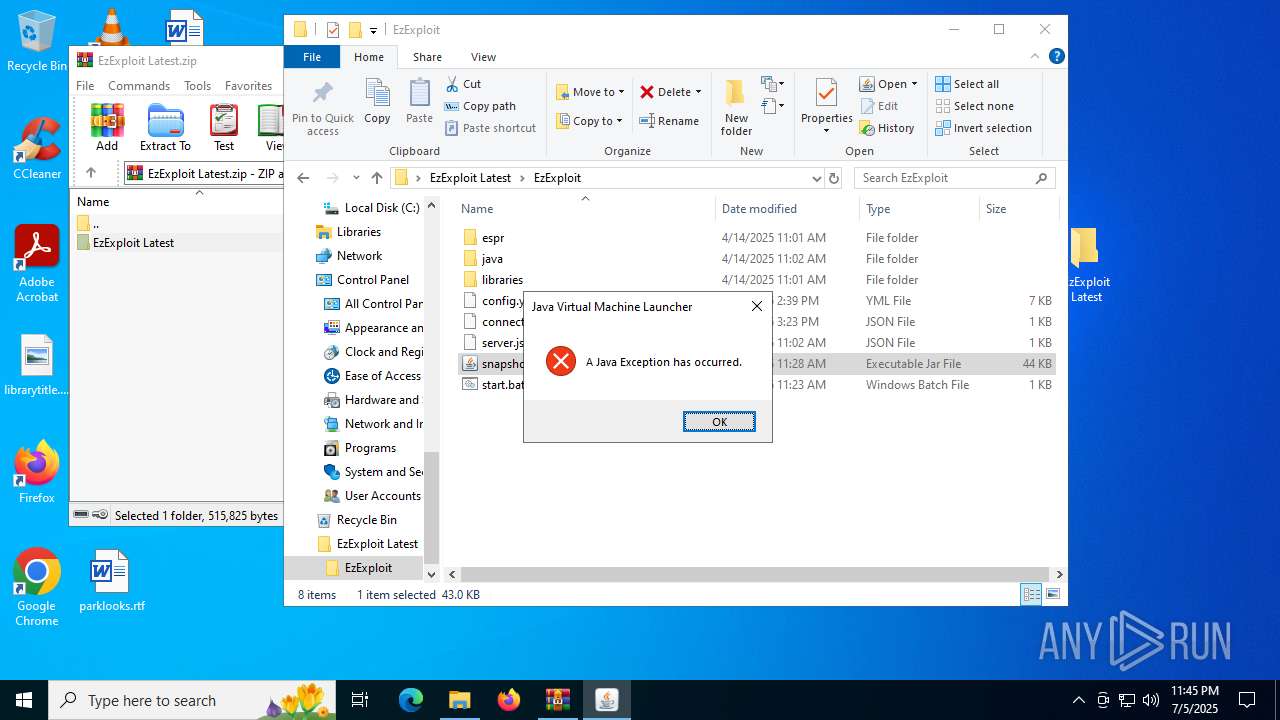
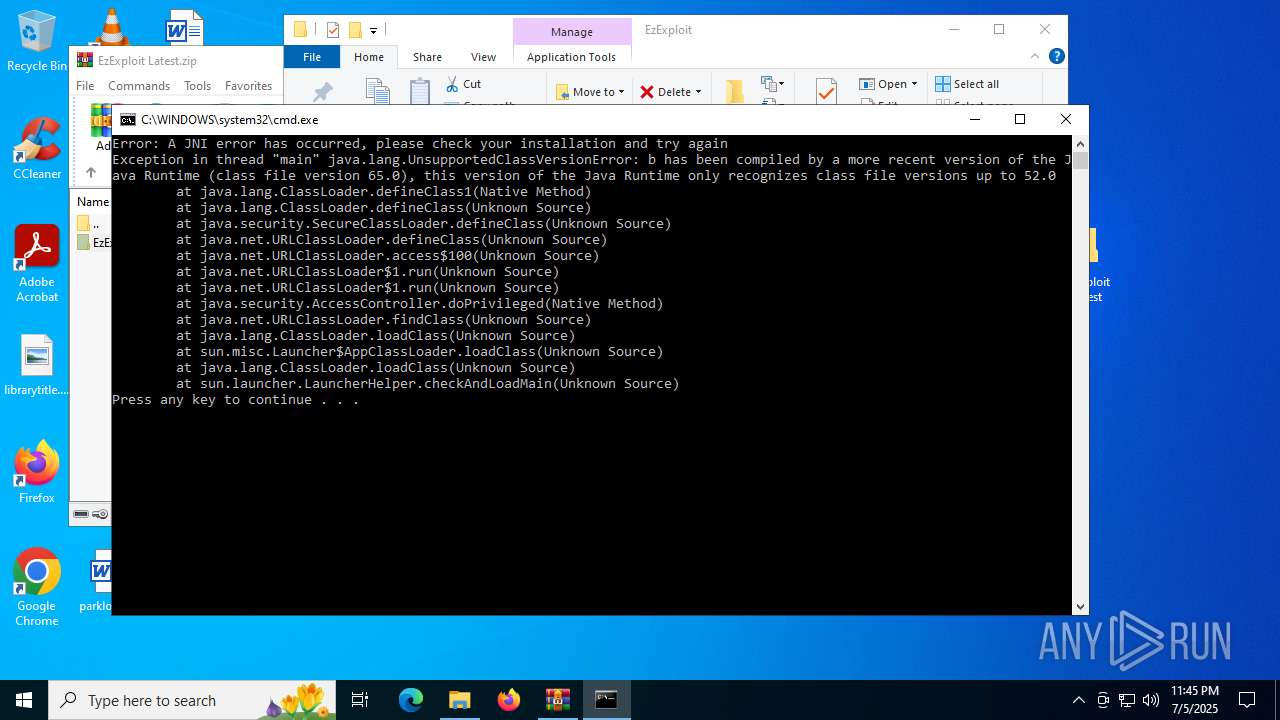
Checks for Java to be installed
- java.exe (PID: 1036)
- java.exe (PID: 4808)
- java.exe (PID: 4860)
- java.exe (PID: 856)
INFO
Manual execution by a user
- cmd.exe (PID: 4572)
- cmd.exe (PID: 2428)
- cmd.exe (PID: 7136)
- cmd.exe (PID: 4552)
Checks supported languages
- java.exe (PID: 1036)
- java.exe (PID: 4860)
- java.exe (PID: 4808)
- javaw.exe (PID: 1216)
- java.exe (PID: 856)
Create files in a temporary directory
- java.exe (PID: 1036)
- java.exe (PID: 4808)
- java.exe (PID: 4860)
- javaw.exe (PID: 1216)
- java.exe (PID: 856)
Creates files in the program directory
- java.exe (PID: 1036)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 5552)
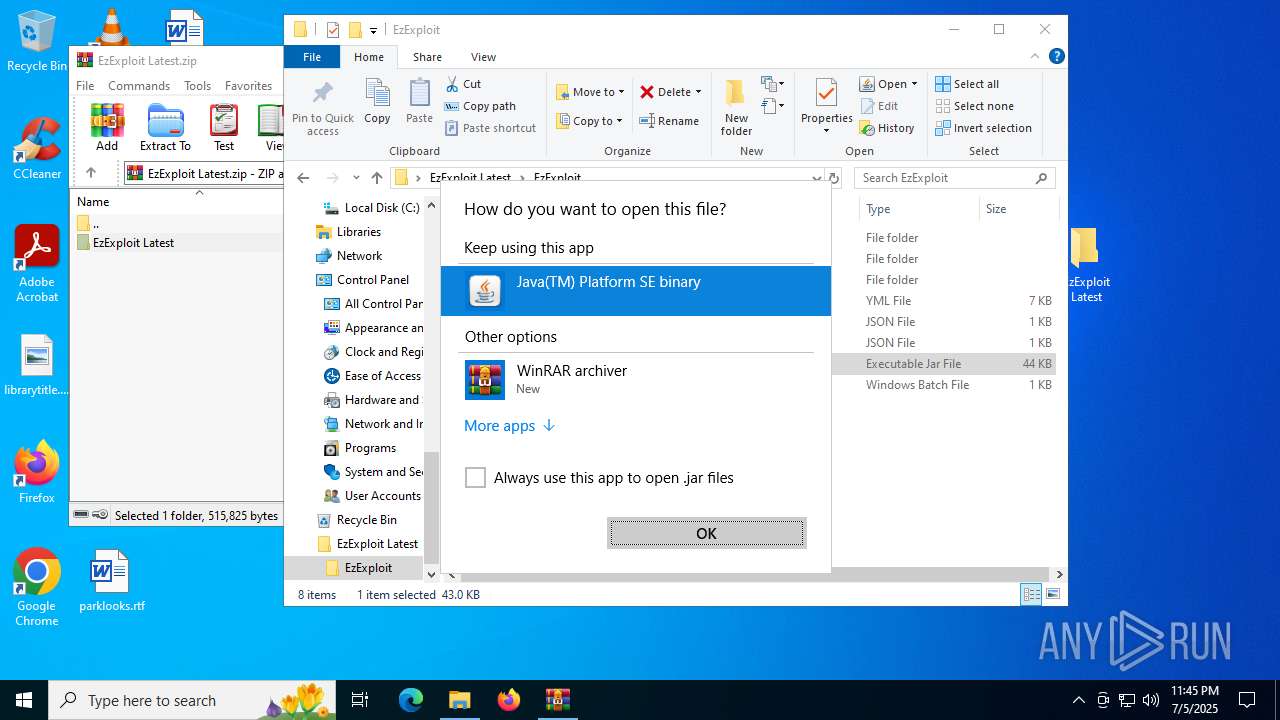
Application based on Java
- javaw.exe (PID: 1216)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 5552)
Reads the computer name
- javaw.exe (PID: 1216)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:04:15 20:29:38 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | EzExploit Latest/EzExploit/ |
Total processes
155
Monitored processes
19
Malicious processes
4
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 856 | java -jar snapshot.jar | C:\Program Files (x86)\Common Files\Oracle\Java\javapath_target_2989500\java.exe | — | cmd.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 1036 | java -jar snapshot.jar | C:\Program Files (x86)\Common Files\Oracle\Java\javapath_target_2989500\java.exe | — | cmd.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 1132 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | icacls.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1216 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar "C:\Users\admin\Desktop\EzExploit Latest\EzExploit\snapshot.jar" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | OpenWith.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 1700 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2040 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2428 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\EzExploit Latest\EzExploit\start.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2648 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4552 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\EzExploit Latest\EzExploit\start.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4572 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\EzExploit Latest\EzExploit\start.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 609
Read events
7 596
Write events
13
Delete events
0
Modification events
| (PID) Process: | (7052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\EzExploit Latest.zip | |||
| (PID) Process: | (7052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (7052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
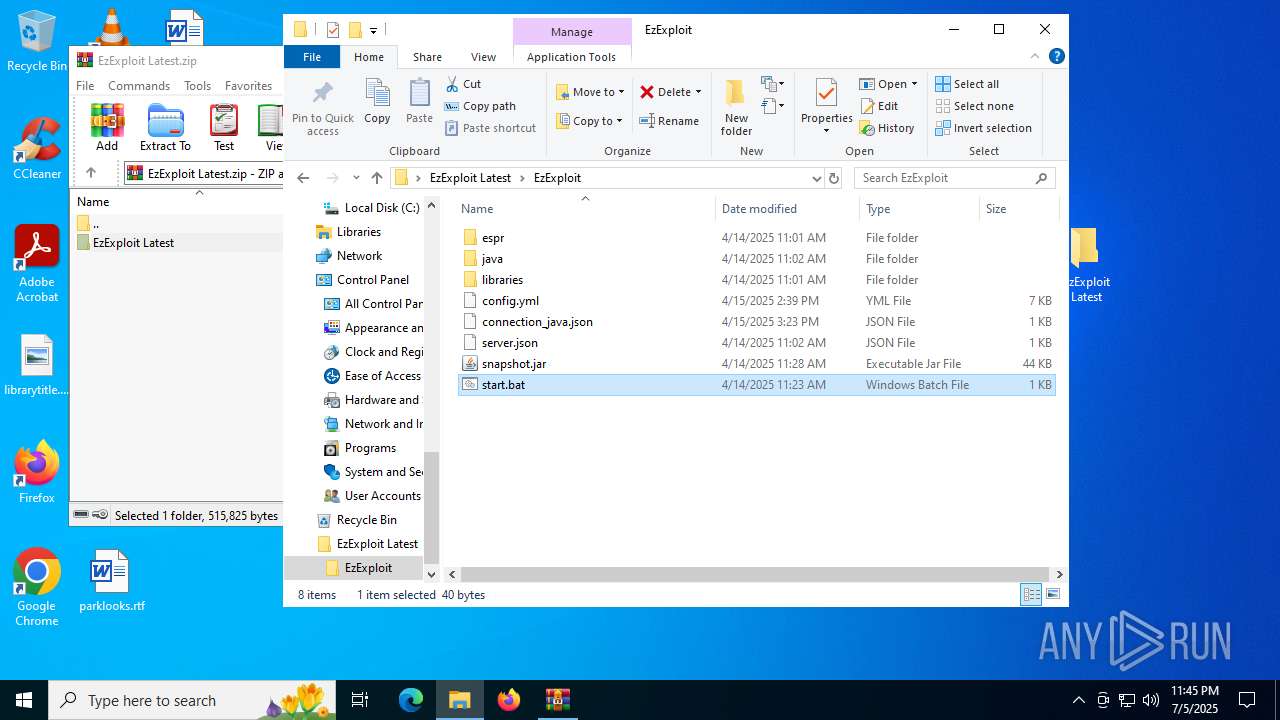
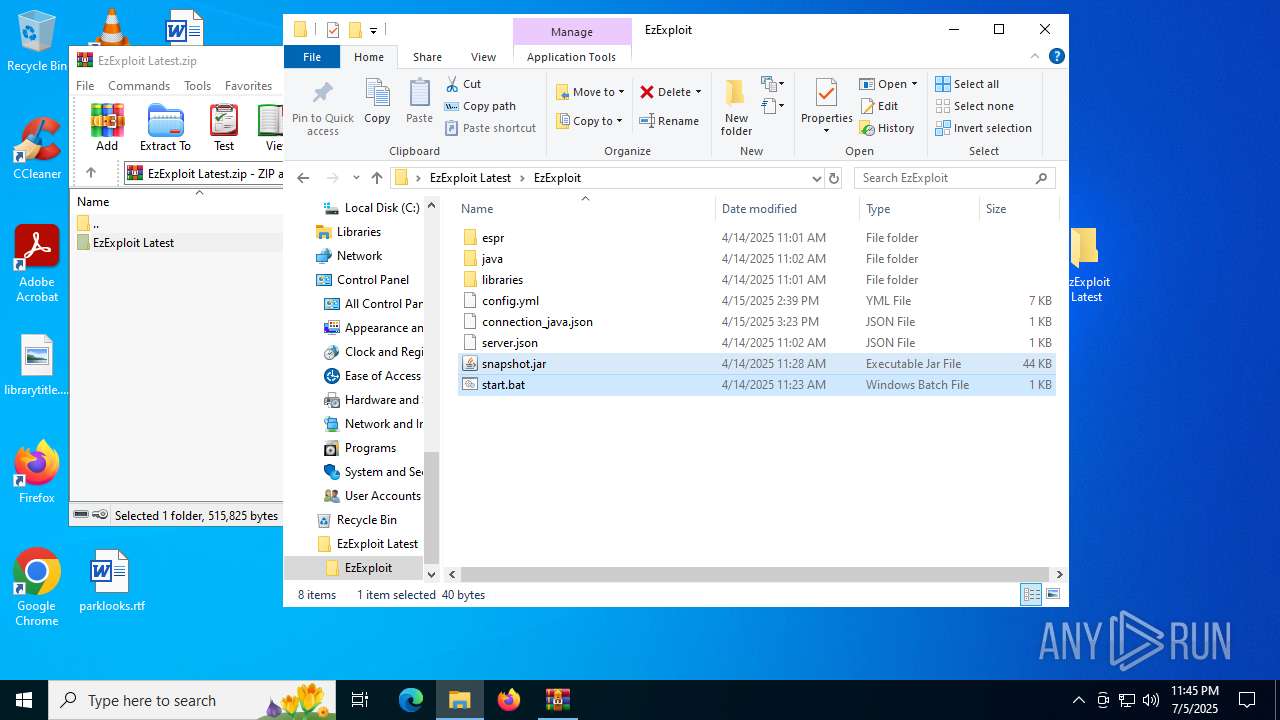
Executable files
8
Suspicious files
1
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7052.41888\EzExploit Latest\EzExploit\config.yml | text | |
MD5:6231121A75F5D415FDC54C9E50DA3B1F | SHA256:FB6EC7C1A4B05F4F0725580156EA053ECE1C4730FE525FA60B4A897A4A549565 | |||
| 7052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7052.41888\EzExploit Latest\EzExploit\libraries\cmd_alert.jar | java | |
MD5:3053817C36BD1DFA1CE52C303D1328E6 | SHA256:56E2A960F11637F31DC30D652532950E834161D2AB36A10C0C57C9E445F8DACE | |||
| 7052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7052.41888\EzExploit Latest\EzExploit\espr\RconFix.jar | java | |
MD5:BB0199FAD177D12AC638D2DA61F9A4DF | SHA256:87E3C42B1CDBA0B17983EE04ED656D94EBC2101923F4BA4F6DD96DEA83705751 | |||
| 7052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7052.41888\EzExploit Latest\EzExploit\libraries\cmd_find.jar | java | |
MD5:B06259D414BE6C61547B7D3F6ED9A9E0 | SHA256:3584FE183A1F50F9A8A8346EA81D691B7C715355F95348EEBCFDFFA49AD5C38B | |||
| 7052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7052.41888\EzExploit Latest\EzExploit\libraries\cmd_send.jar | java | |
MD5:B06755DEDD8D7D81F80C17013C47B16E | SHA256:5002C806A46F7736B85FB6ED1ECB7E555A8A284C01752CB3C6F58EBF4F6E34F6 | |||
| 7052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7052.41888\EzExploit Latest\EzExploit\server.json | text | |
MD5:17F934A21B3B06241EAEBB4569A93F29 | SHA256:B1A2A0E78820439176DA8F338982EB15F78E10F8F161D8FEA0F42F45845089D9 | |||
| 1036 | java.exe | C:\ProgramData\Oracle\Java\.oracle_jre_usage\17dfc292991c8061.timestamp | text | |
MD5:7A96E58ECC4FA6D00EA2014C708F80EC | SHA256:4BC048195D667EFCE43D8F024A7DDD358F1A96EFB267C18D1EE8919BD02866F5 | |||
| 7052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7052.41888\EzExploit Latest\EzExploit\connection_java.json | text | |
MD5:E8E115095DD2DAEFEF14CD3F7B0DEA3C | SHA256:57FB050319AEC3BD6E76DCF18B6B535A29D581EF07AF743636E360C043224DC4 | |||
| 7052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7052.41888\EzExploit Latest\EzExploit\java\net\md_5\bungee\module\cmd\server\CommandServer.java | text | |
MD5:6E40F8CCD6CE7BEAD2376C595B86DB87 | SHA256:EDC15FA70BC5604A75286885B91D481B098401A8A08CBDCED747FCCCEDD3D1C9 | |||
| 7052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7052.41888\EzExploit Latest\EzExploit\java\net\md_5\bungee\module\cmd\server\PluginServer.java | text | |
MD5:51889CCEE78F54E288B1B123574263A6 | SHA256:9C62C485CDAA6E9CBFF1DC7E56097678BEB62B8CF394A94C1275002F3E29D8ED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
22
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.55.104.172:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7060 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2180 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2180 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5708 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.55.104.172:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
7060 | svchost.exe | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7060 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |