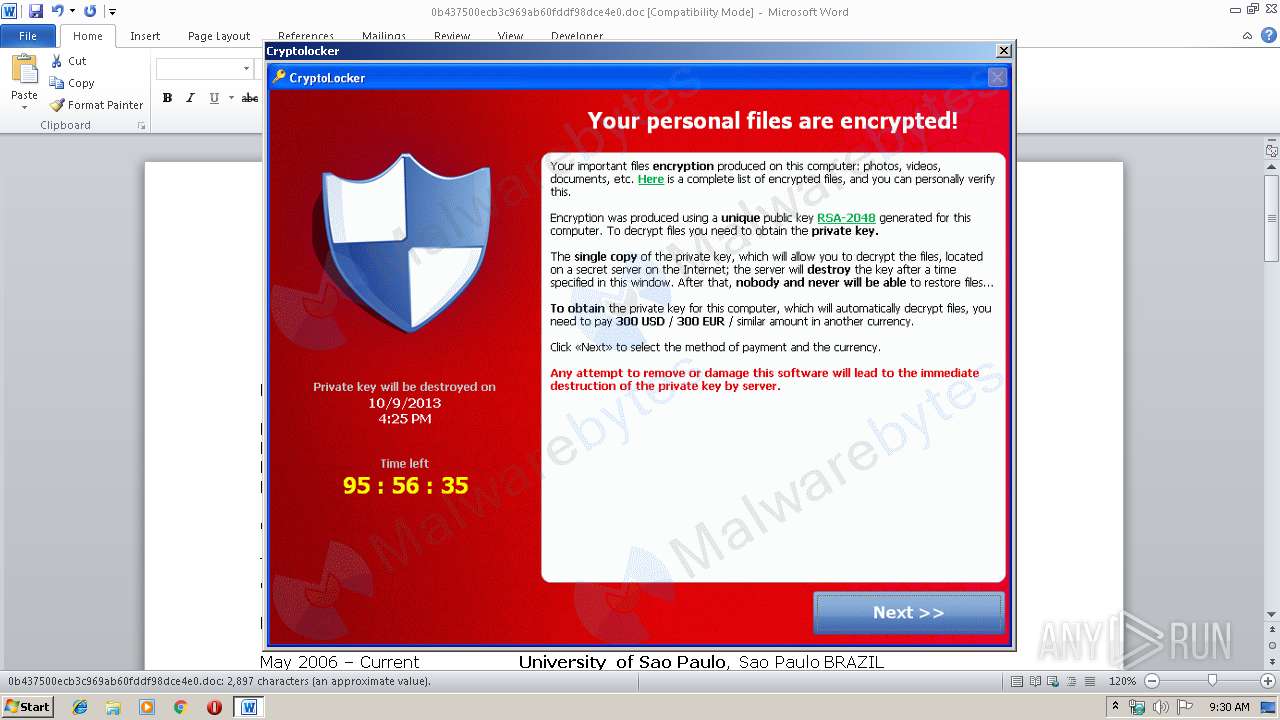
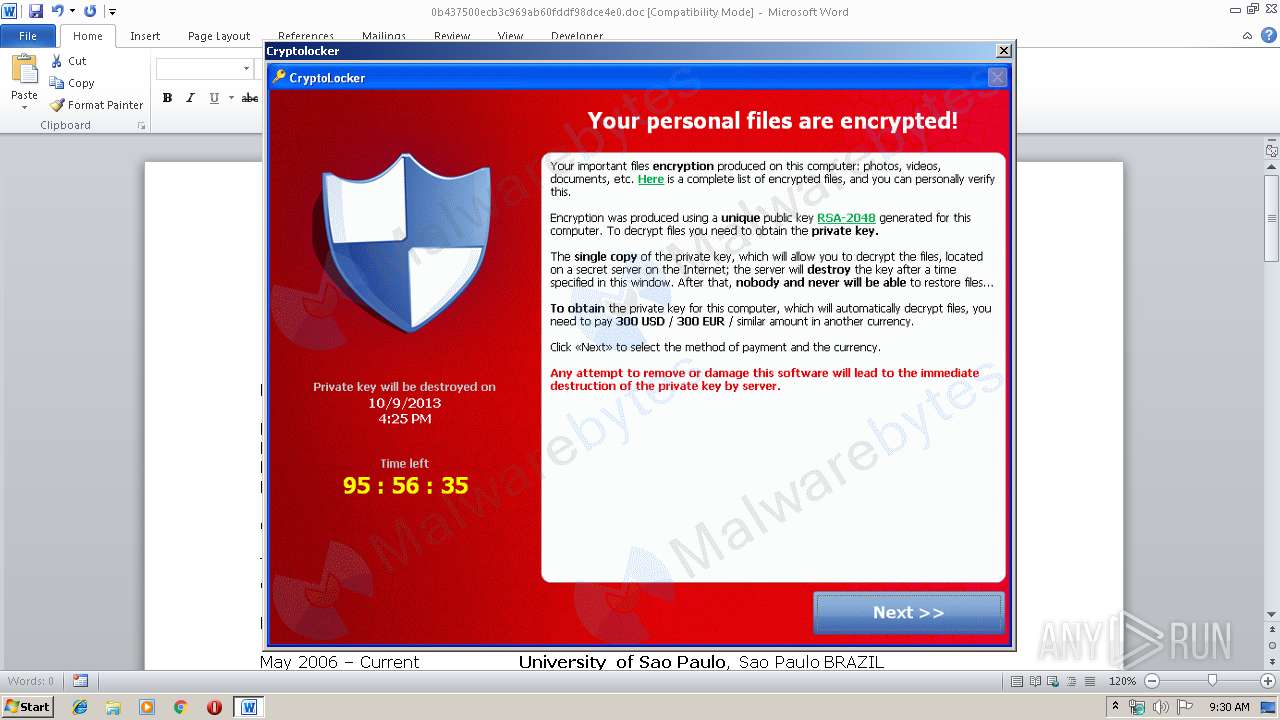
| File name: | 0b437500ecb3c969ab60fddf98dce4e0.doc |
| Full analysis: | https://app.any.run/tasks/cd712824-ac0d-4c4b-bc32-ea5ac7046992 |
| Verdict: | Malicious activity |
| Analysis date: | April 15, 2019, 08:29:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1255, Title: Word Template, Author: Sagy Kratu, Template: Normal.dotm, Last Saved By: admin, Revision Number: 226, Name of Creating Application: Microsoft Office Word, Total Editing Time: 15:00:00, Last Printed: Sat Jan 30 01:17:00 2010, Create Time/Date: Thu Aug 13 08:29:00 2015, Last Saved Time/Date: Wed Jul 4 19:24:00 2018, Number of Pages: 3, Number of Words: 585, Number of Characters: 2930, Security: 0 |
| MD5: | 0B437500ECB3C969AB60FDDF98DCE4E0 |
| SHA1: | 35B71F1E6FB9DF9EDA6DE0A93F7AE8C7E2E21BC0 |
| SHA256: | 5A493F66EE1780271C5BEB9C4C003EB16E8C160C0B301C8E49244A54C1A2C67B |
| SSDEEP: | 6144:9VBYujMpODRFluwAnwL6I94Mj1UoT2KJo81wmefyc6D02h4oahZnwm0t:9kuo5wA44MdT8fy9LhXeZnwj |
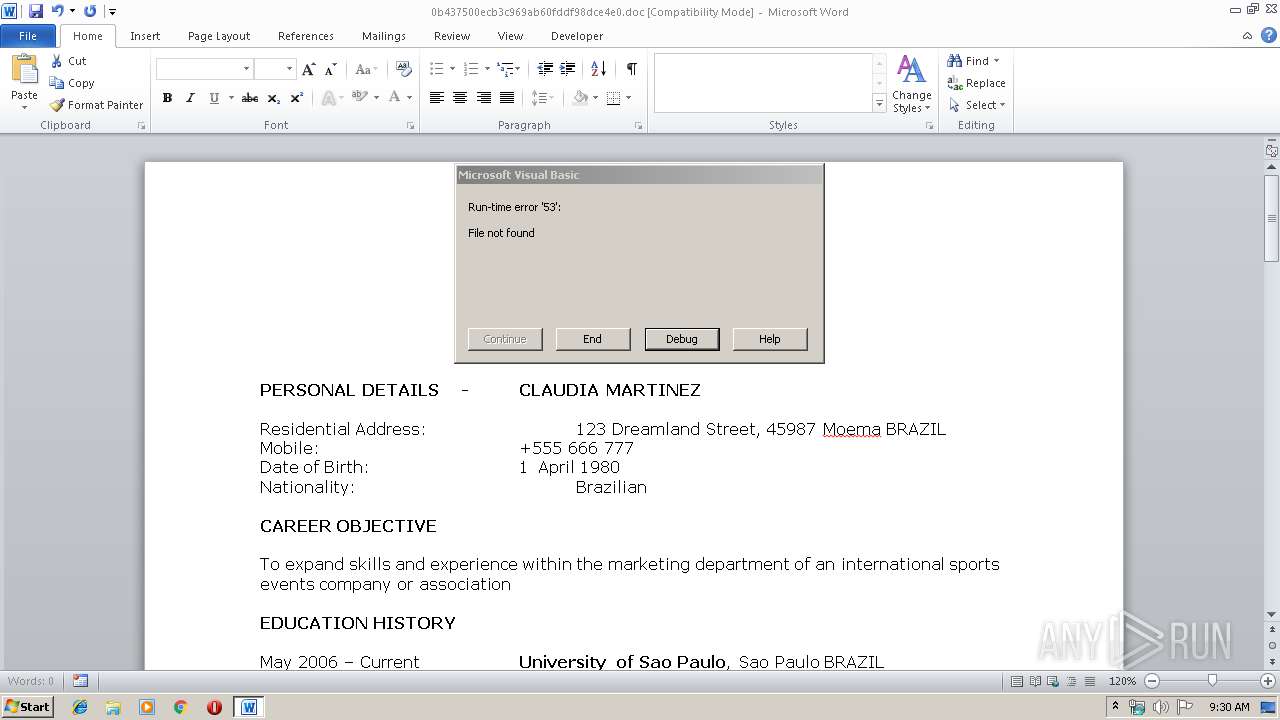
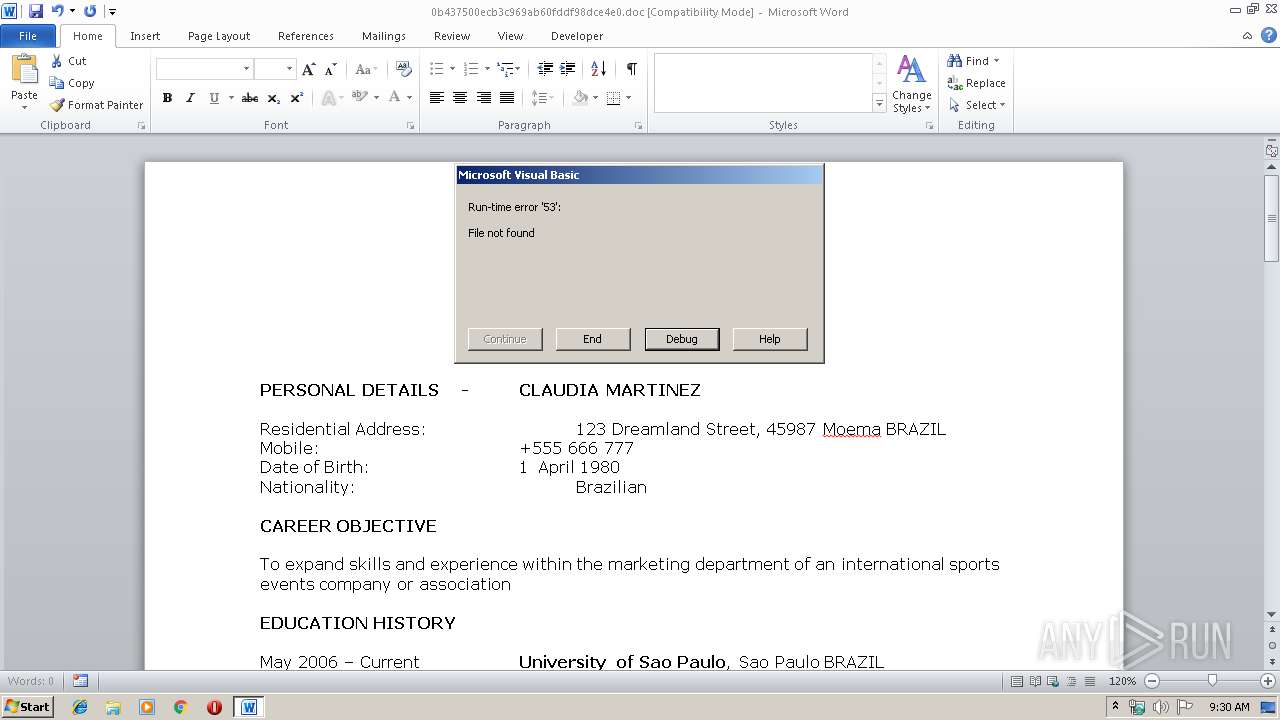
MALICIOUS
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 2940)
SUSPICIOUS
Creates executable files which already exist in Windows
- WINWORD.EXE (PID: 2940)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 2940)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2940)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (35.3) |
|---|---|---|
| .pps/ppt | | | Microsoft PowerPoint document (34.8) |
| .doc | | | Microsoft Word document (old ver.) (20.9) |
EXIF
FlashPix
| Title: | Word Template |
|---|---|
| Subject: | - |
| Author: | Sagy Kratu |
| Keywords: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | admin |
| RevisionNumber: | 226 |
| Software: | Microsoft Office Word |
| TotalEditTime: | 15.0 hours |
| LastPrinted: | 2010:01:30 01:17:00 |
| CreateDate: | 2015:08:13 07:29:00 |
| ModifyDate: | 2018:07:04 18:24:00 |
| Pages: | 3 |
| Words: | 585 |
| Characters: | 2930 |
| Security: | None |
| Company: | Check Point |
| Lines: | 24 |
| Paragraphs: | 7 |
| CharCountWithSpaces: | 3508 |
| AppVersion: | 14 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | Word Template |
| HeadingPairs: |
|
| CodePage: | Windows Hebrew |
| Classification: | Restricted |
| ClassificationDisplay: | [Restricted] ONLY for designated groups and individuals |
| Verifier: | Pyo3PTQgJjCDMw== |
| PolicyName: | Pyo3PTQgJjCDMw== |
| Version: | Xw== |
| PolicyID: | VHlwenZ7Jn1LNEAxLn1xajBsXnAncjZaeDFwW1xGcHaScXMn |
| DomainID: | XX90eXZ5dXRLZ0Bif311YmRpXnh1dWRaeWR4X1tEeHVDeHV1 |
| HText: | - |
| FText: | Np0hOjI7LCeSMpSPb5+Lno15lSc3ZTCSOj0vgYqALSFTLzcqIZmXU56CgEGZkYWciZmWmpGJgQ== |
| WMark: | TQ== |
| Set: | OT0xLA== |
| ClassificationEntries: | 1 |
| Classification_1: | VWB1eml7dXVTd0FidWJ8aGRqU4mIfoaSOiA6hoiALSFIc5aEkzBJK01cVUxH |
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
31
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2940 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\0b437500ecb3c969ab60fddf98dce4e0.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
875
Read events
762
Write events
109
Delete events
4
Modification events
| (PID) Process: | (2940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | j~> |
Value: 6A7E3E007C0B0000010000000000000000000000 | |||
| (PID) Process: | (2940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2940) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1317994526 | |||
| (PID) Process: | (2940) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1317994648 | |||
| (PID) Process: | (2940) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1317994649 | |||
| (PID) Process: | (2940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 7C0B0000FA0EA26B65F3D40100000000 | |||
| (PID) Process: | (2940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | d> |
Value: 647F3E007C0B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | d> |
Value: 647F3E007C0B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
3
Suspicious files
0
Text files
7
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2940 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRFEEA.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2940 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2940 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$437500ecb3c969ab60fddf98dce4e0.doc | pgc | |
MD5:— | SHA256:— | |||
| 2940 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 2940 | WINWORD.EXE | C:\temp\Command&Control.txt | text | |
MD5:9E25D20C989C6F85CDCC56778AB2CB63 | SHA256:D79FD90ED33D7201A28CEDD4B81E71F70BA38FBC72DBC024E8DD0DDC8D6E2DB2 | |||
| 2940 | WINWORD.EXE | C:\temp\services.exe | text | |
MD5:9E25D20C989C6F85CDCC56778AB2CB63 | SHA256:D79FD90ED33D7201A28CEDD4B81E71F70BA38FBC72DBC024E8DD0DDC8D6E2DB2 | |||
| 2940 | WINWORD.EXE | C:\temp\googservices.exe | text | |
MD5:9E25D20C989C6F85CDCC56778AB2CB63 | SHA256:D79FD90ED33D7201A28CEDD4B81E71F70BA38FBC72DBC024E8DD0DDC8D6E2DB2 | |||
| 2940 | WINWORD.EXE | C:\temp\dns.com | text | |
MD5:9E25D20C989C6F85CDCC56778AB2CB63 | SHA256:D79FD90ED33D7201A28CEDD4B81E71F70BA38FBC72DBC024E8DD0DDC8D6E2DB2 | |||
| 2940 | WINWORD.EXE | C:\temp\nntp.exe | text | |
MD5:9E25D20C989C6F85CDCC56778AB2CB63 | SHA256:D79FD90ED33D7201A28CEDD4B81E71F70BA38FBC72DBC024E8DD0DDC8D6E2DB2 | |||
| 2940 | WINWORD.EXE | C:\temp\Control.exe | text | |
MD5:9E25D20C989C6F85CDCC56778AB2CB63 | SHA256:D79FD90ED33D7201A28CEDD4B81E71F70BA38FBC72DBC024E8DD0DDC8D6E2DB2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report