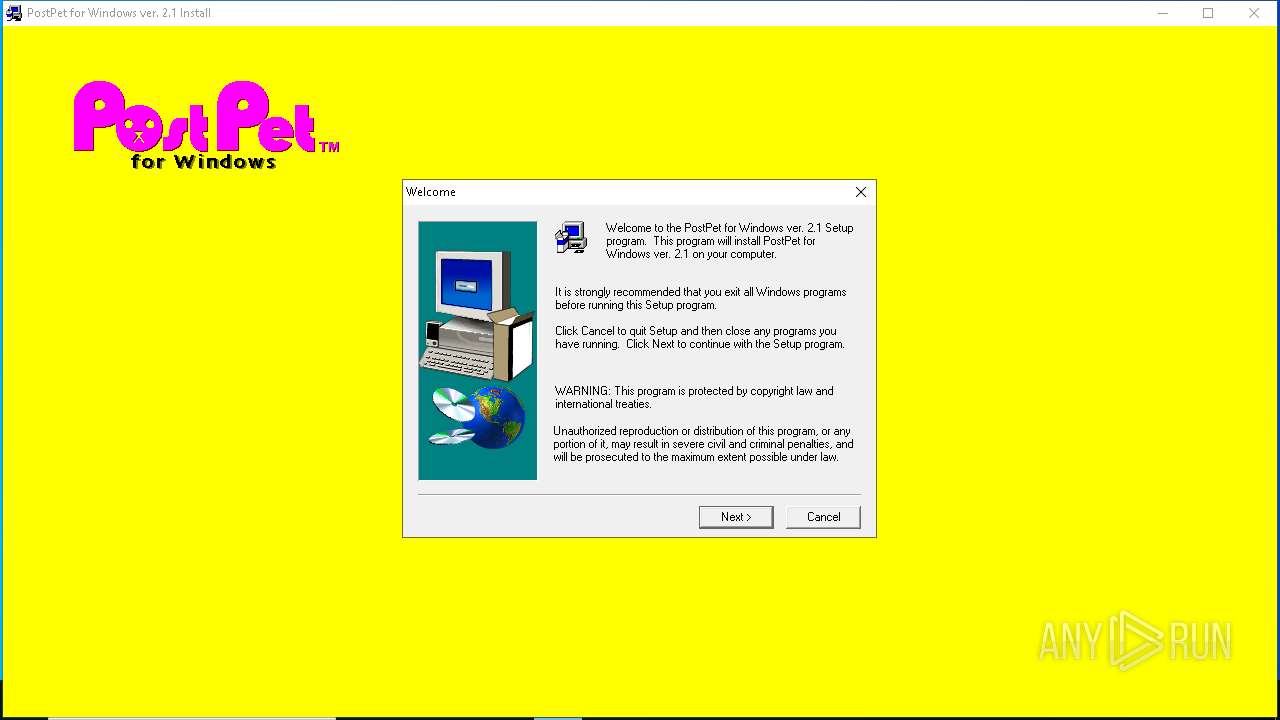
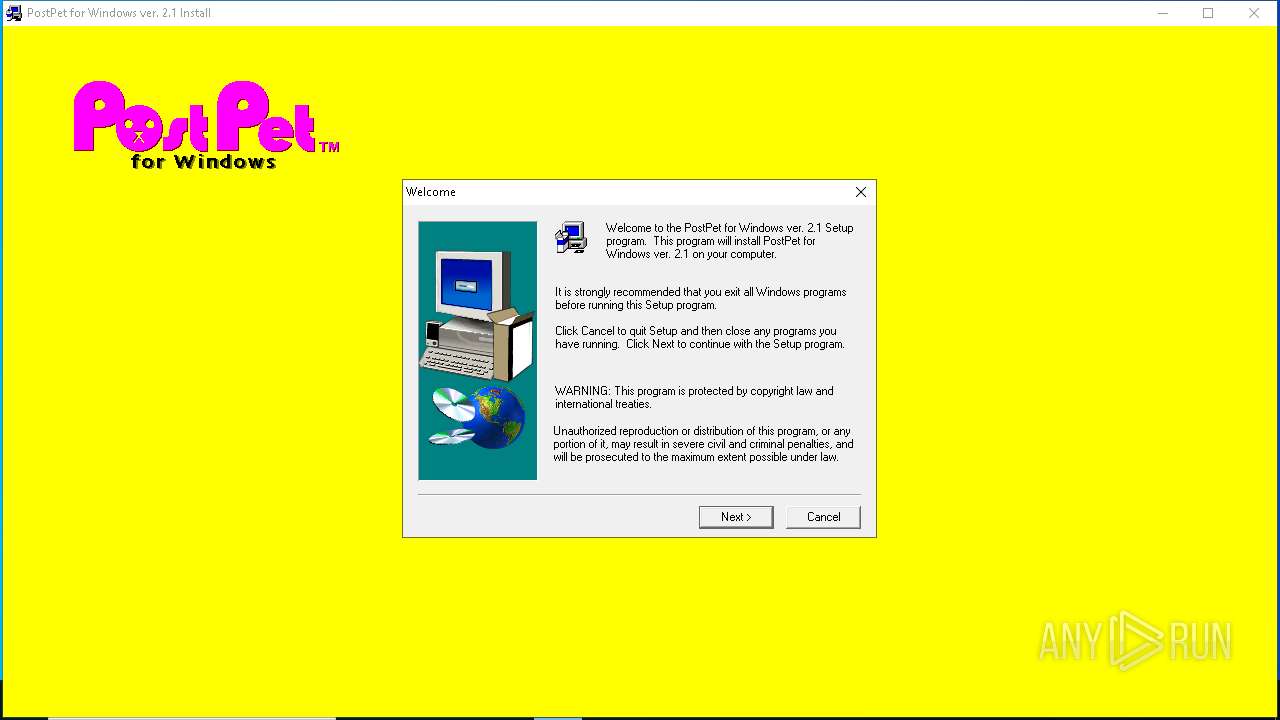
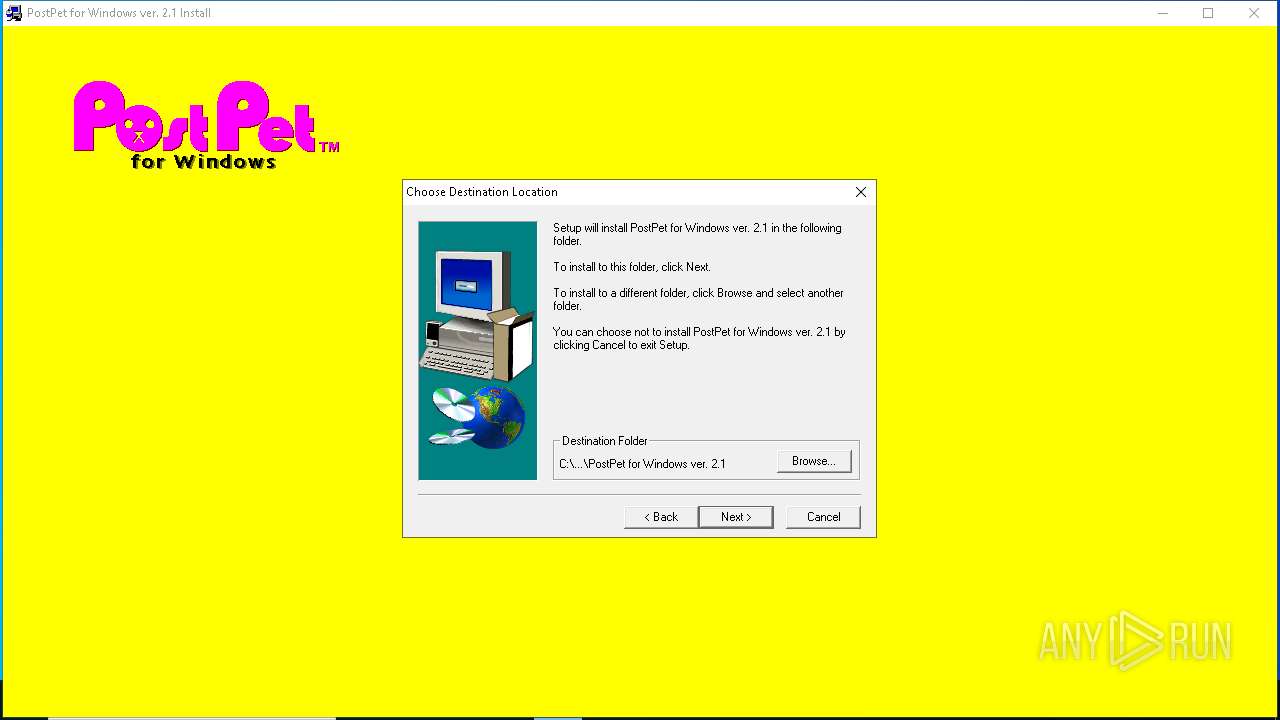
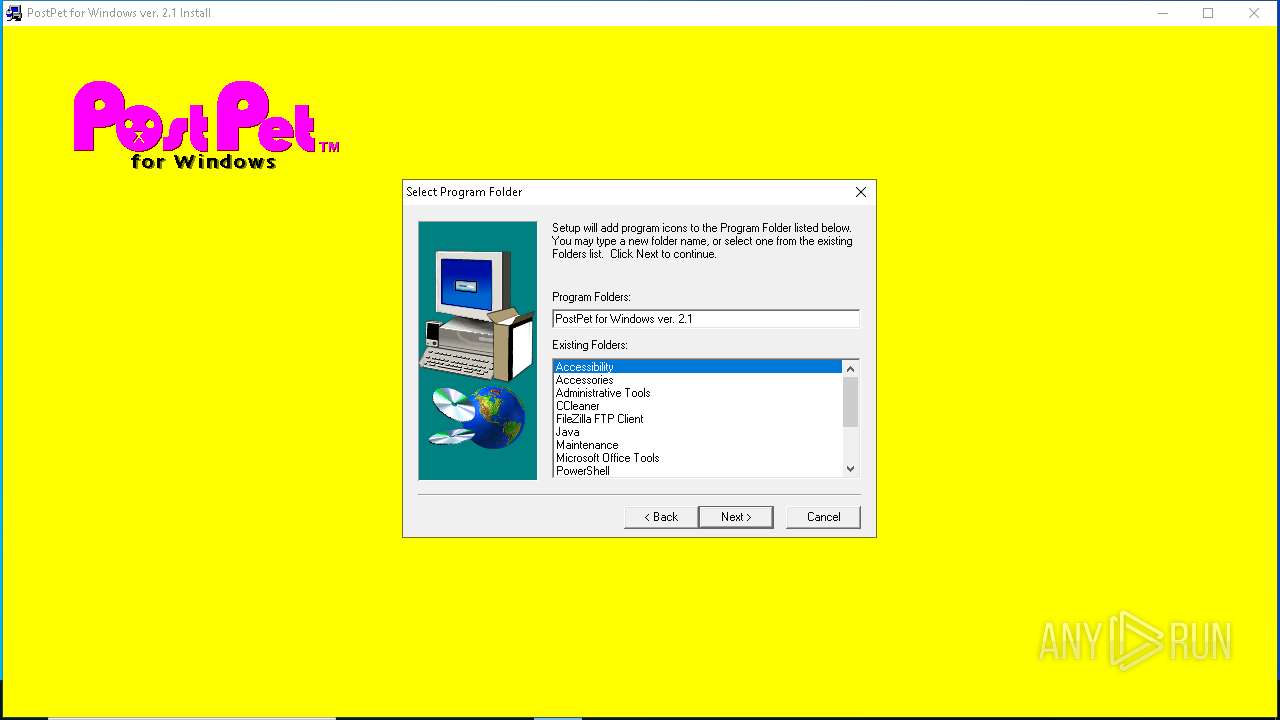
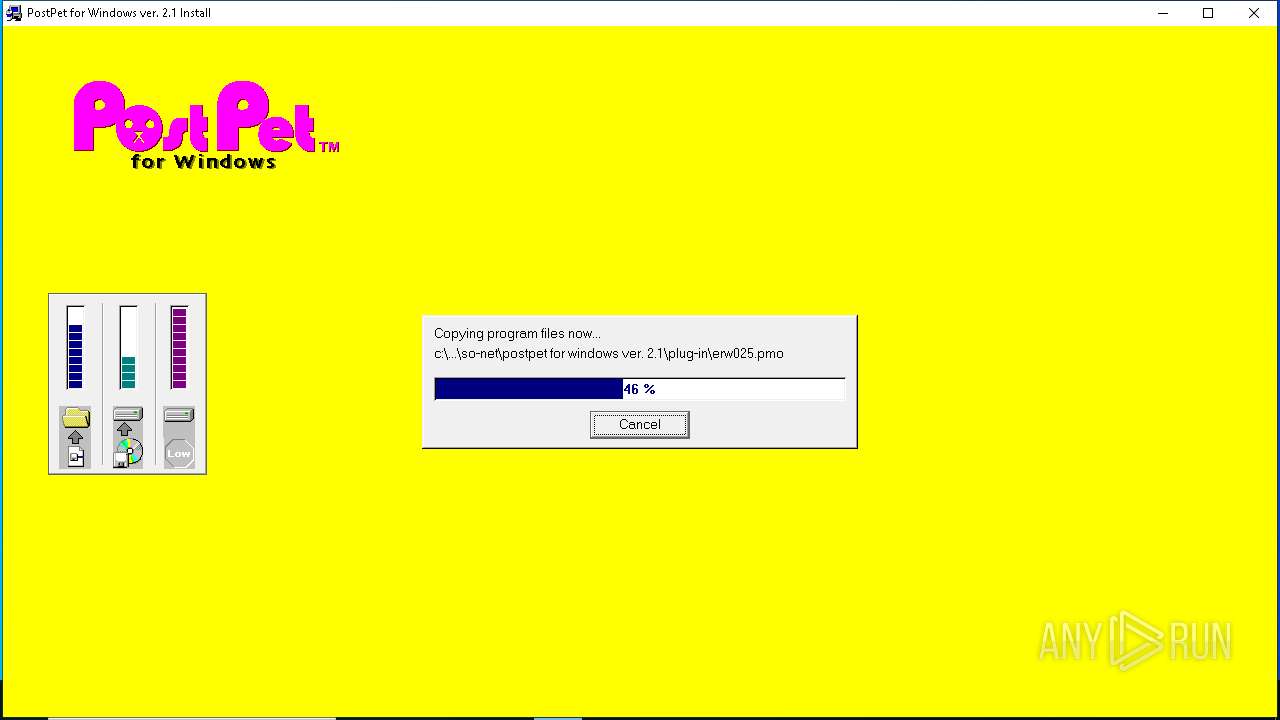
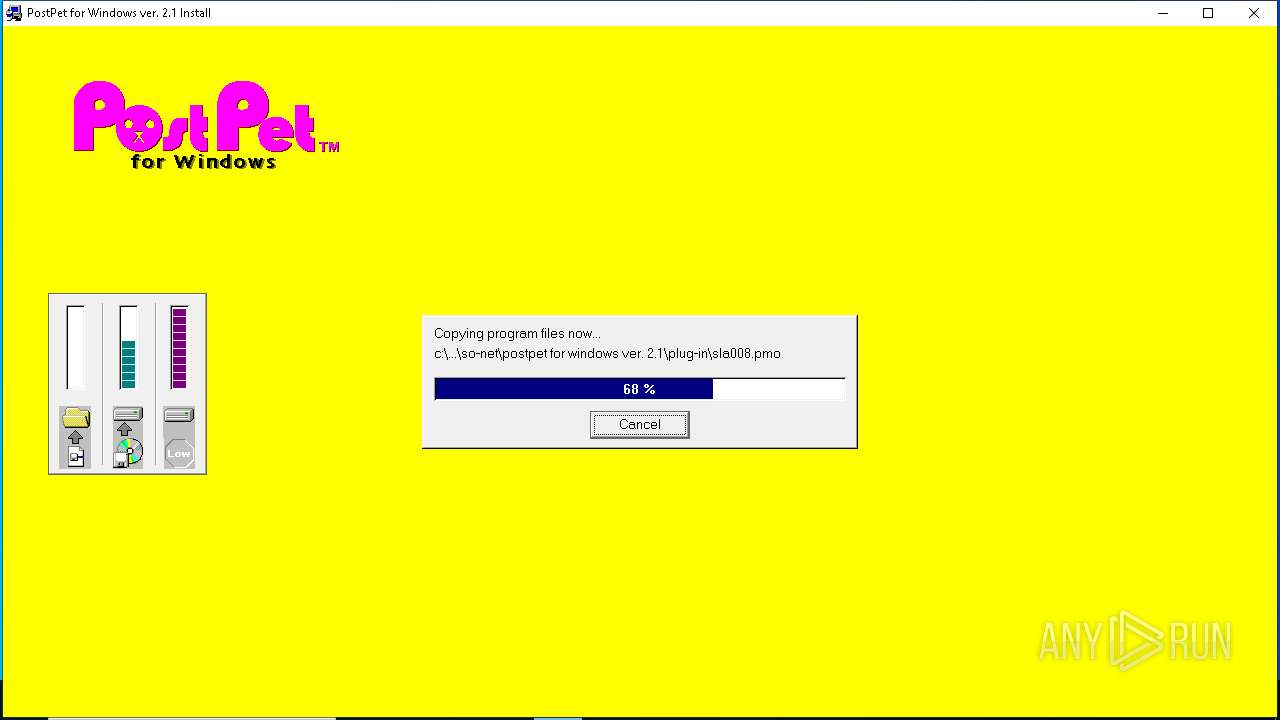
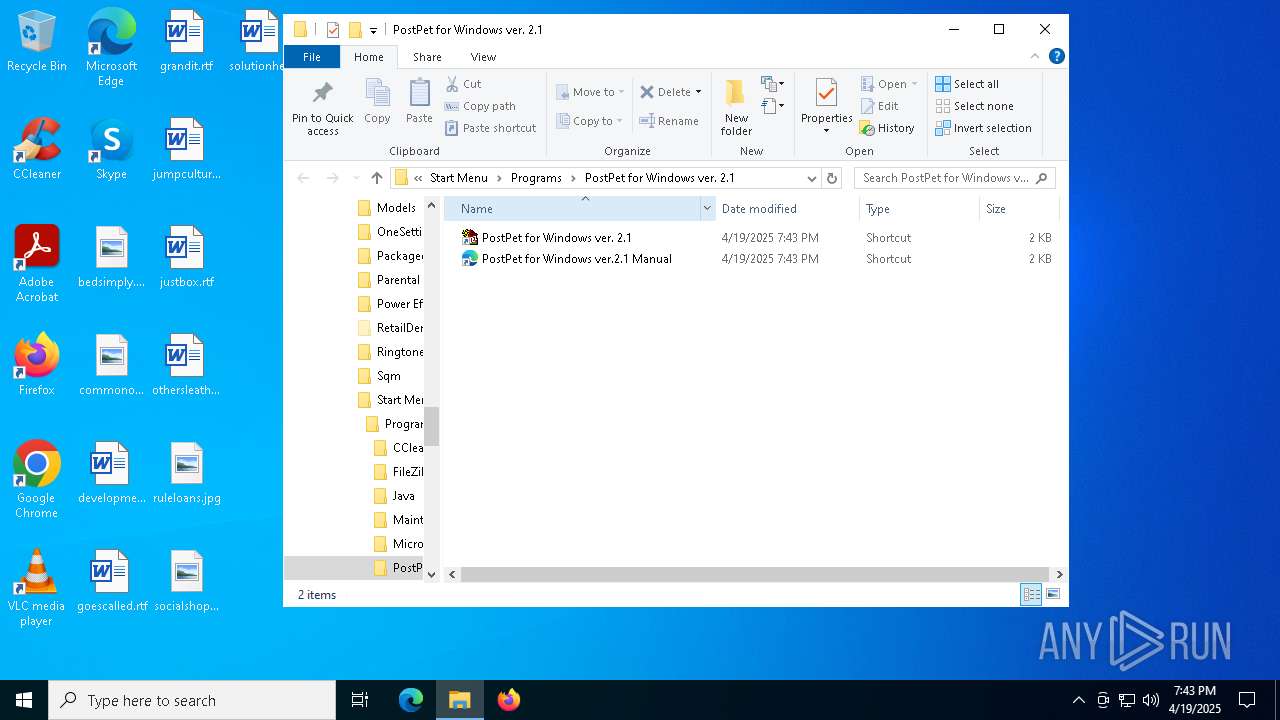
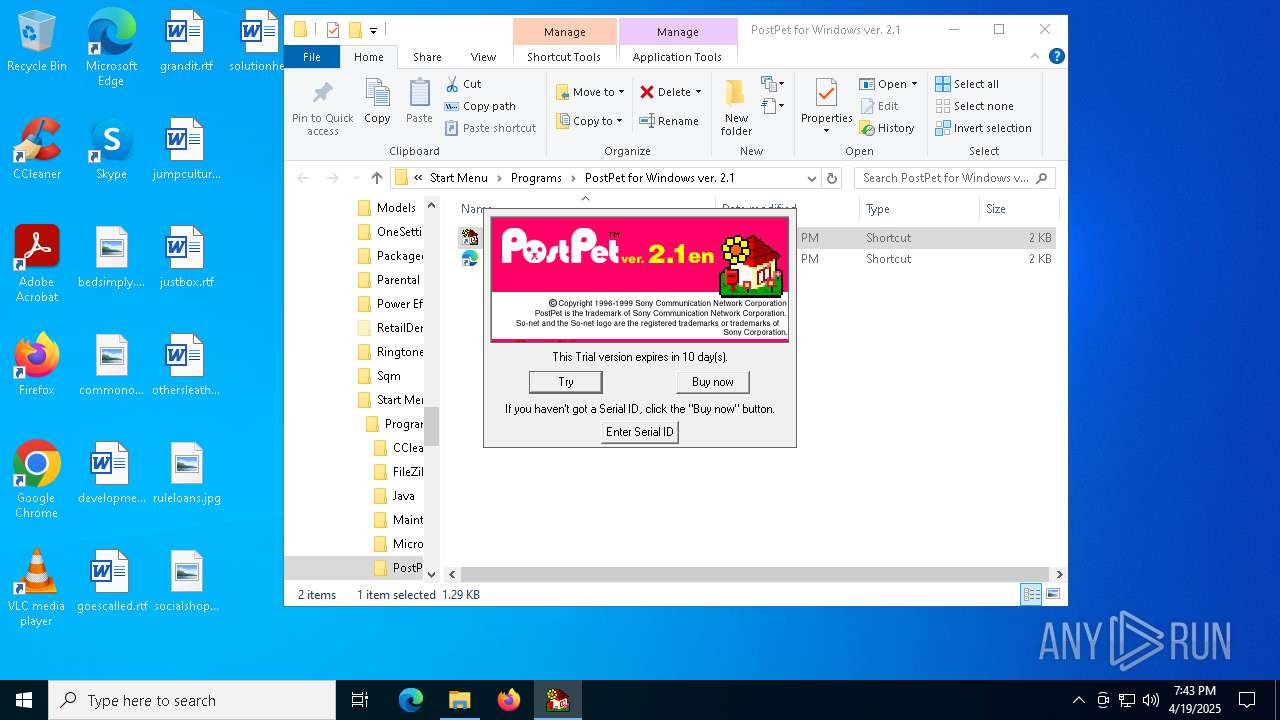
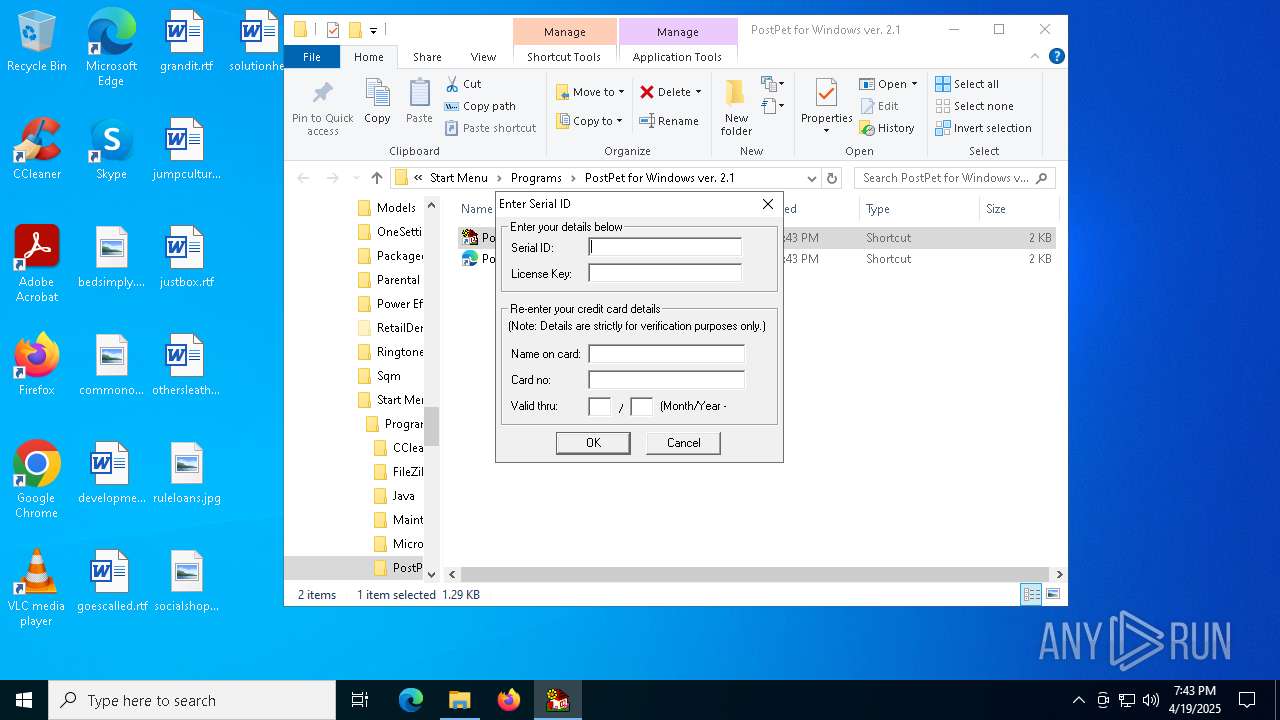
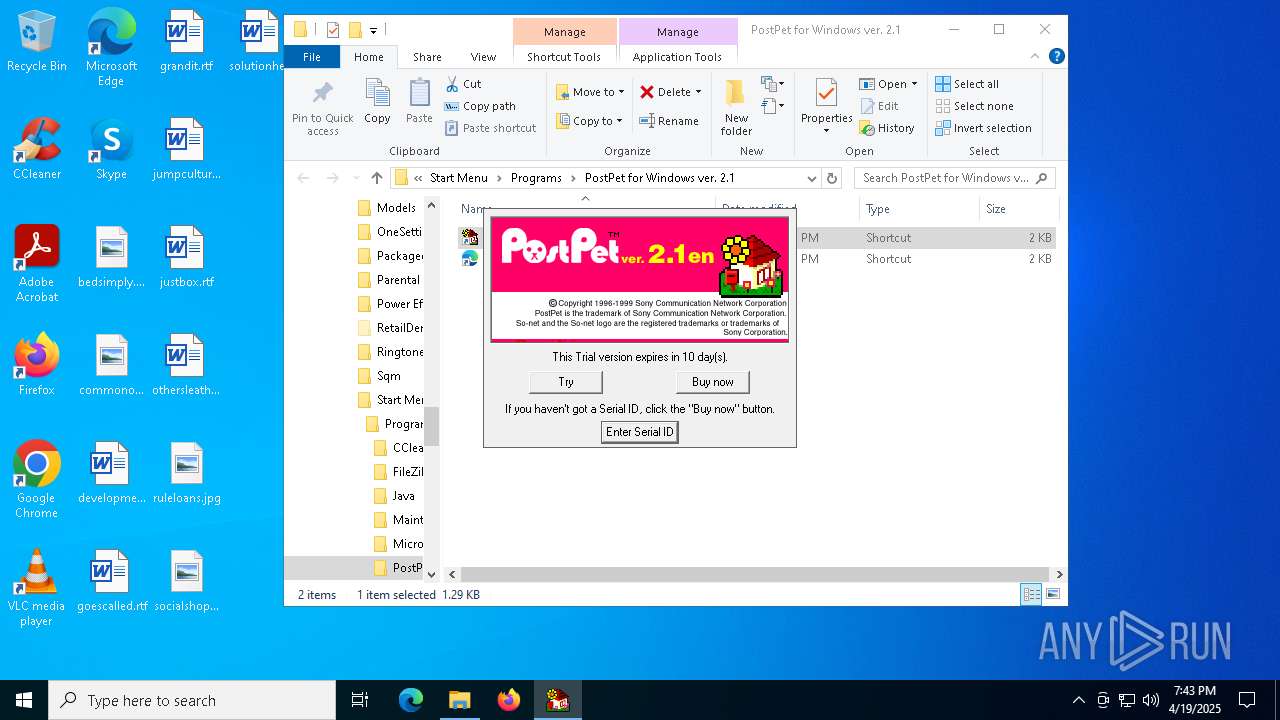
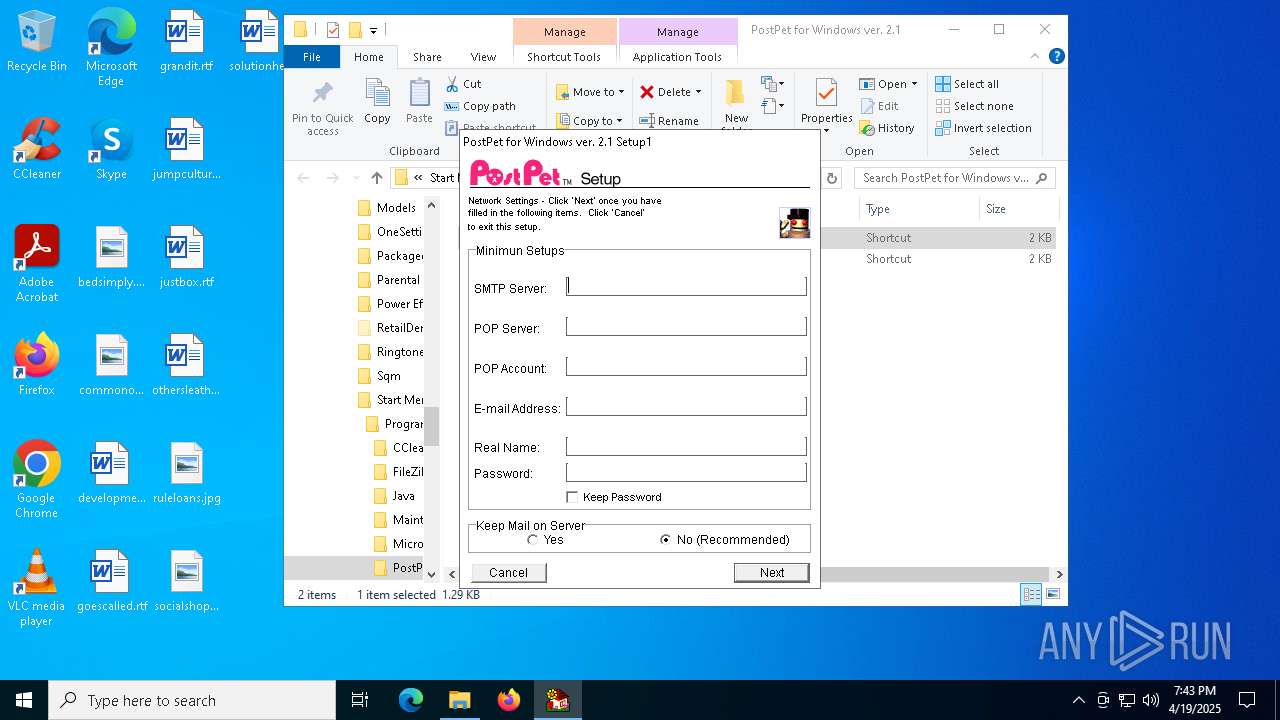
| File name: | pp21en.exe |
| Full analysis: | https://app.any.run/tasks/0ec43c0f-0be2-4d8f-9692-155f88835b37 |
| Verdict: | Malicious activity |
| Analysis date: | April 19, 2025, 19:42:59 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, InstallShield self-extracting archive, 5 sections |
| MD5: | 3B4BBD58498EED5EC4350411F59FFE1D |
| SHA1: | ACF002E118CE3CC2F43722583AEC75C4BC32DB51 |
| SHA256: | 5A46E13FC1C9A37882E338FA107232898FF182ED362B0165BF44362A1113AE15 |
| SSDEEP: | 98304:5Bi671dqumjdo9J6UxNpF+swVNLVHphWOT9o8bIfzrpKU8fdiywhTiOssZa/eoFM:eP0G+h1RbpEWz/ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates file in the systems drive root
- pp21en.exe (PID: 4652)
- _isdel.exe (PID: 6372)
- explorer.exe (PID: 5156)
Executable content was dropped or overwritten
- pp21en.exe (PID: 4652)
- setup.exe (PID: 5512)
- _INS5176._MP (PID: 4380)
Starts application with an unusual extension
- setup.exe (PID: 5512)
Process drops legitimate windows executable
- _INS5176._MP (PID: 4380)
Creates a software uninstall entry
- _INS5176._MP (PID: 4380)
There is functionality for taking screenshot (YARA)
- setup.exe (PID: 5512)
- pp21en.exe (PID: 4652)
INFO
The sample compiled with english language support
- pp21en.exe (PID: 4652)
- setup.exe (PID: 5512)
- _INS5176._MP (PID: 4380)
Checks supported languages
- pp21en.exe (PID: 4652)
- setup.exe (PID: 5512)
- _INS5176._MP (PID: 4380)
- _isdel.exe (PID: 6372)
- PP21.exe (PID: 4112)
Reads the computer name
- setup.exe (PID: 5512)
- pp21en.exe (PID: 4652)
- _INS5176._MP (PID: 4380)
- PP21.exe (PID: 4112)
Create files in a temporary directory
- pp21en.exe (PID: 4652)
- setup.exe (PID: 5512)
- _INS5176._MP (PID: 4380)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5156)
Creates files in the program directory
- _INS5176._MP (PID: 4380)
Creates files or folders in the user directory
- PP21.exe (PID: 4112)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ 4.x (53) |
|---|---|---|
| .exe | | | InstallShield setup (16.9) |
| .exe | | | Win32 Executable MS Visual C++ (generic) (12.2) |
| .exe | | | Win64 Executable (generic) (10.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (2.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1999:01:07 18:10:41+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 5 |
| CodeSize: | 72192 |
| InitializedDataSize: | 72704 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xce00 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.4.1.0 |
| ProductVersionNumber: | 2.4.1.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | InstallShield Software Corporation |
| FileDescription: | PackageForTheWeb Stub |
| FileVersion: | 2.04.001 |
| InternalName: | STUB.EXE |
| LegalCopyright: | Copyright © 1996-1999 InstallShield Software Corporation |
| OriginalFileName: | STUB32.EXE |
| ProductName: | PackageForTheWeb Stub |
| ProductVersion: | 2.04.001 |
Total processes
141
Monitored processes
11
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1052 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | explorer.exe "C:\ProgramData\Microsoft\Windows\Start Menu\Programs\PostPet for Windows ver. 2.1" | C:\Windows\SysWOW64\explorer.exe | — | _INS5176._MP | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2516 | "C:\Users\admin\AppData\Local\Temp\pp21en.exe" | C:\Users\admin\AppData\Local\Temp\pp21en.exe | — | explorer.exe | |||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: MEDIUM Description: PackageForTheWeb Stub Exit code: 3221226540 Version: 2.04.001 Modules
| |||||||||||||||
| 4112 | "C:\Program Files (x86)\So-net\PostPet for Windows ver. 2.1\PP21.exe" | C:\Program Files (x86)\So-net\PostPet for Windows ver. 2.1\PP21.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4380 | C:\Users\admin\AppData\Local\Temp\_ISTMP1.DIR\_INS5176._MP | C:\Users\admin\AppData\Local\Temp\_ISTMP1.DIR\_INS5176._MP | setup.exe | ||||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: HIGH Description: InstallShield Engine Exit code: 0 Version: 5.10.145.0 Modules
| |||||||||||||||
| 4408 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4652 | "C:\Users\admin\AppData\Local\Temp\pp21en.exe" | C:\Users\admin\AppData\Local\Temp\pp21en.exe | explorer.exe | ||||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: HIGH Description: PackageForTheWeb Stub Exit code: 0 Version: 2.04.001 Modules
| |||||||||||||||
| 4980 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5156 | C:\WINDOWS\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5512 | "C:\Users\admin\AppData\Local\Temp\pftB894~tmp\SETUP.EXE" -isw64"C:\Users\admin\AppData\Local\Temp\pftB894~tmp\SETUP.EXE" /SMS | C:\Windows\SysWOW64\InstallShield\setup.exe | pp21en.exe | ||||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: HIGH Description: 32-bit Setup Launcher Exit code: 0 Version: 5, 54, 001, 0 Modules
| |||||||||||||||
Total events
8 028
Read events
7 989
Write events
38
Delete events
1
Modification events
| (PID) Process: | (4380) _INS5176._MP | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\PostPet for Windows ver. 2.1 |
| Operation: | write | Name: | UninstallString |
Value: C:\WINDOWS\IsUninst.exe -f"C:\Program Files (x86)\So-net\PostPet for Windows ver. 2.1\Uninst.isu" | |||
| (PID) Process: | (4380) _INS5176._MP | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\Pp21.exe |
| Operation: | write | Name: | Path |
Value: C:\Program Files (x86)\So-net\PostPet for Windows ver. 2.1 | |||
| (PID) Process: | (4380) _INS5176._MP | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\PostPet for Windows ver. 2.1 |
| Operation: | write | Name: | DisplayName |
Value: PostPet for Windows ver. 2.1 | |||
| (PID) Process: | (5156) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (5156) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 04000000030000000E00000000000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (5156) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Toolbar |
| Operation: | write | Name: | Locked |
Value: 1 | |||
| (PID) Process: | (5156) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Toolbar\ShellBrowser |
| Operation: | write | Name: | ITBar7Layout |
Value: 13000000000000000000000020000000100000000000000001000000010700005E01000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5156) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4\0\8\4\0\0\0 |
| Operation: | write | Name: | 1 |
Value: 8400310000000000935A709D1020504F535450457E312E3100006A0009000400EFBE935A709D935A709D2E000000A564050000000700000000000000000000000000000024B4750050006F0073007400500065007400200066006F0072002000570069006E0064006F007700730020007600650072002E00200032002E00310000001A000000 | |||
| (PID) Process: | (5156) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4\0\8\4\0\0\0\1 |
| Operation: | delete value | Name: | MRUList |
Value: | |||
| (PID) Process: | (5156) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4\0\8\4\0\0\0 |
| Operation: | write | Name: | MRUListEx |
Value: 0100000000000000FFFFFFFF | |||
Executable files
20
Suspicious files
361
Text files
81
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4652 | pp21en.exe | C:\Users\admin\AppData\Local\Temp\pftB894~tmp\pftw1.pkg | — | |
MD5:— | SHA256:— | |||
| 4652 | pp21en.exe | C:\Users\admin\AppData\Local\Temp\pftB894~tmp\data1.cab | — | |
MD5:— | SHA256:— | |||
| 4652 | pp21en.exe | C:\Users\admin\AppData\Local\Temp\pftB894~tmp\SETUP.EXE | executable | |
MD5:AFE10D250B2C1850B37827C1D4E01EEF | SHA256:26ADEA53490125FD31E300DA97EF48B9DDC583753789051746B9A31406B418CF | |||
| 4652 | pp21en.exe | C:\Users\admin\AppData\Local\Temp\pftB894~tmp\_INST32I.EX_ | binary | |
MD5:4251C8E7962CE3CA98FDCBE096C1D270 | SHA256:065443568C396564EC51C72F54F81990C49E4B0CECE780ACBFC6A7494B65A3E0 | |||
| 4652 | pp21en.exe | C:\Users\admin\AppData\Local\Temp\pftB894~tmp\os.dat | text | |
MD5:AF1D8D9435CB10FE2F4B4215EAF6BEC4 | SHA256:2F148CB3D32AB70A315B5A853761C2702B6DEEF6FFAFF6AA76D513B945CE7EF7 | |||
| 4652 | pp21en.exe | C:\Users\admin\AppData\Local\Temp\pftB894~tmp\_SETUP.DLL | executable | |
MD5:8C6DC2367841533E1FE0C2E402CABD03 | SHA256:2178D6BBB5A3CDB803341C516CB7B06019A2183E3F3572177F186802252209E5 | |||
| 4652 | pp21en.exe | C:\Users\admin\AppData\Local\Temp\pftB894~tmp\lang.dat | text | |
MD5:90E64689804B4F4B0197C07290965A3C | SHA256:EB1E8EA9707BC2F6EB4B4CC4D022E6ACF0B79E0C66F8406478269EEAB05693B8 | |||
| 4652 | pp21en.exe | C:\Users\admin\AppData\Local\Temp\pftB894~tmp\setup.ins | binary | |
MD5:84172EDF290294B24BD1BA4A73E24196 | SHA256:EC386F1C54CC91F0CD9D24C9798642852B7579E40D2E471350B8531FA8E758B6 | |||
| 4652 | pp21en.exe | C:\Users\admin\AppData\Local\Temp\pftB894~tmp\_sys1.cab | compressed | |
MD5:346057BFDCB39BDD4D1A749EF9529A85 | SHA256:8F3A3BFB80E1AF806A87DA87ED8E295B550DD6364A9245284CA1F3B9C25972F9 | |||
| 4652 | pp21en.exe | C:\Users\admin\AppData\Local\Temp\pftB894~tmp\_ISDEL.EXE | executable | |
MD5:1F9BBFAAB8DEC9AC4416E5BE2D22E315 | SHA256:DAD294B71F24B1EB140D3536AB7ABD0336977FE92A18BE38ABE4F1A5BE91939A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
19
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
616 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
616 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
616 | SIHClient.exe | 52.149.20.212:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
616 | SIHClient.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |