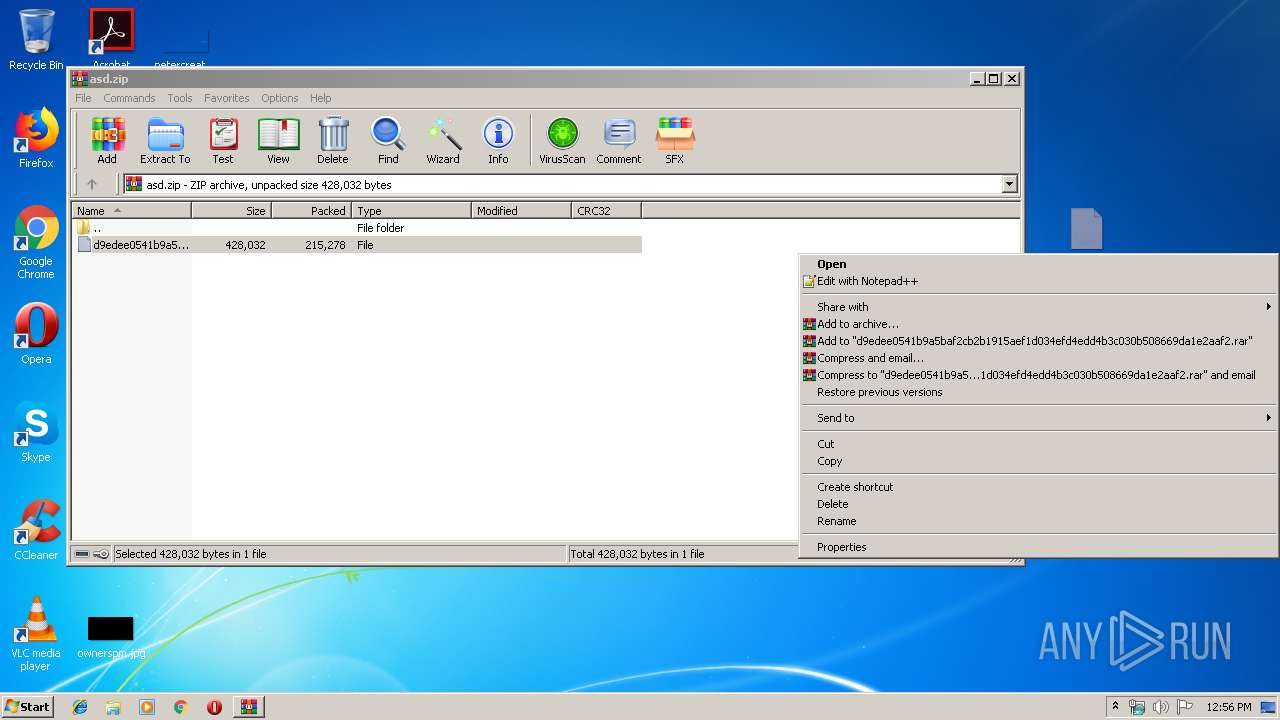
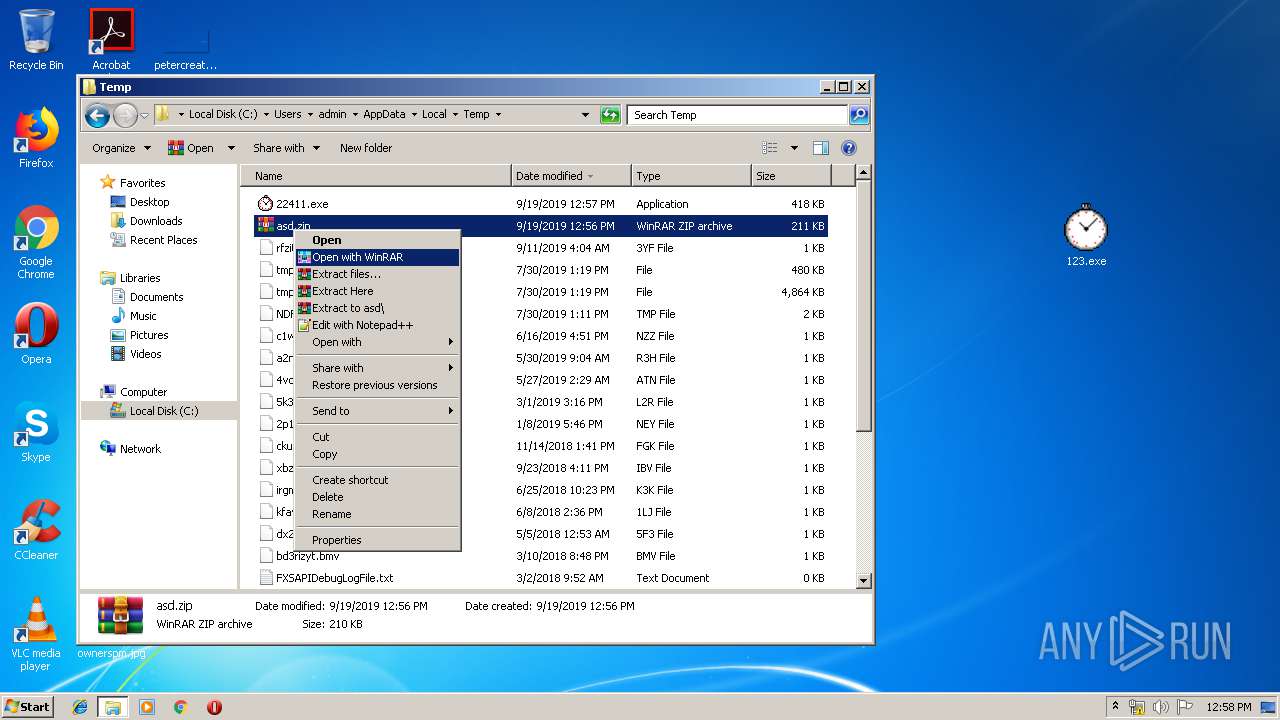
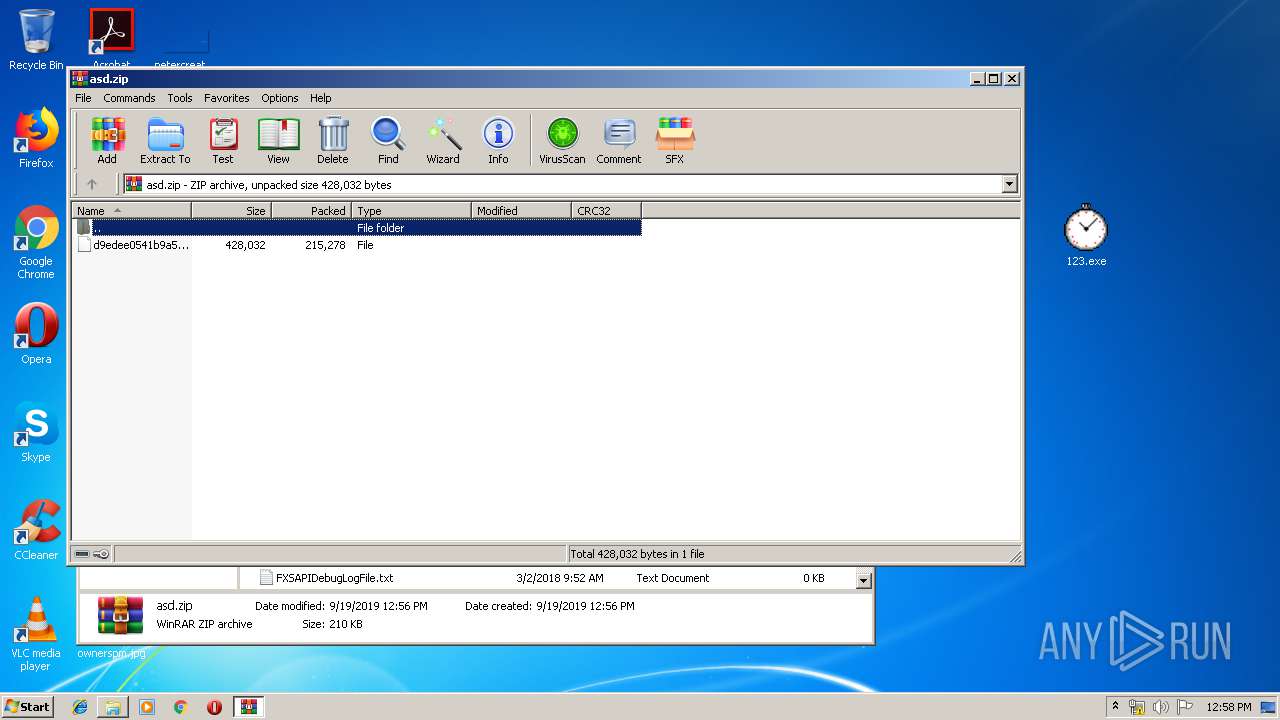
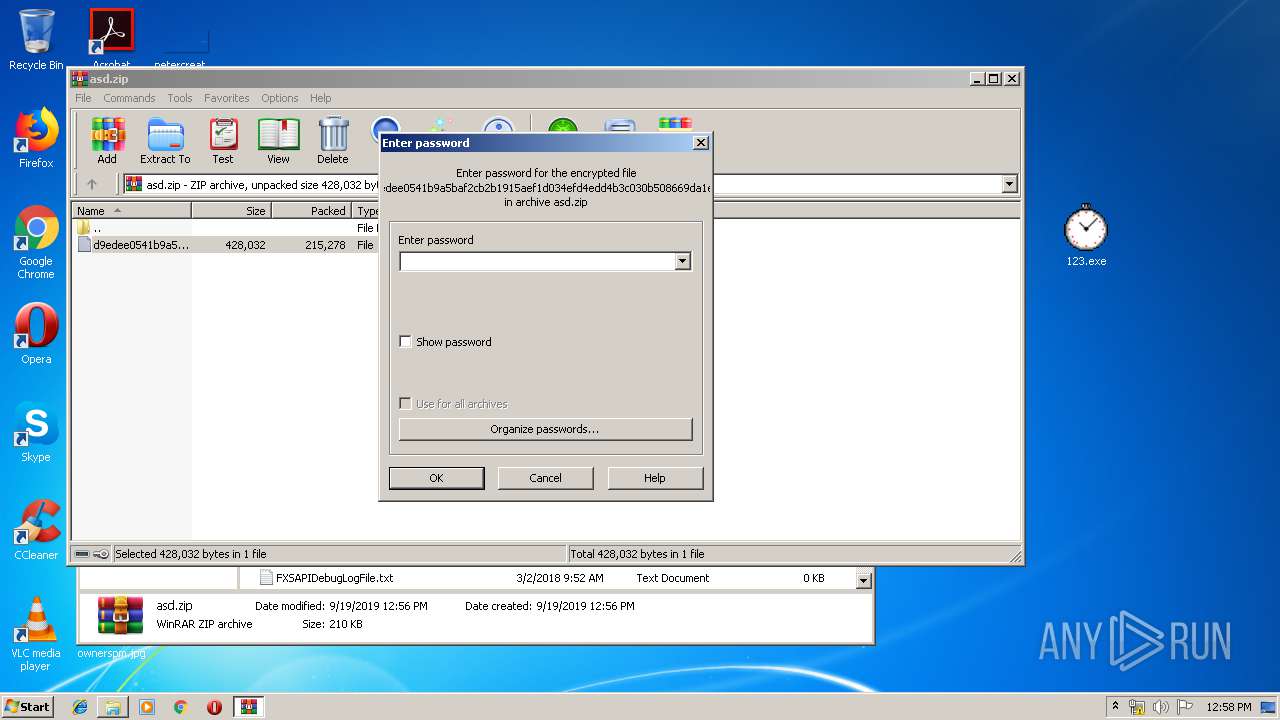
| File name: | asd.zip |
| Full analysis: | https://app.any.run/tasks/4ecf695d-d9c3-4b7a-956f-bbef273391ef |
| Verdict: | Malicious activity |
| Threats: | Phorpiex is a malicious software that has been a significant threat in the cybersecurity landscape since 2016. It is a modular malware known for its ability to maintain an extensive botnet. Unlike other botnets, Phorpiex does not concentrate on DDoS attacks. Instead, it has been involved in numerous large-scale spam email campaigns and the distribution of other malicious payloads, such as LockBit. |
| Analysis date: | September 19, 2019, 11:56:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | F8B588E89E952D86D784653EFCE78F3C |
| SHA1: | CC4D9F15A321F68C8CBAF90E8F0C292B4F943A77 |
| SHA256: | 5A29A80E99884FFC14968BCA48A025AC4F88A3AD59774436B911EFDACF9B8E87 |
| SSDEEP: | 6144:zqB7J+VM7VlposGX/ibNyle8+4ACpHDOGvygU8zJ4z0F:gV+e7VlZGqEp+opiJKf |
MALICIOUS
Application was dropped or rewritten from another process
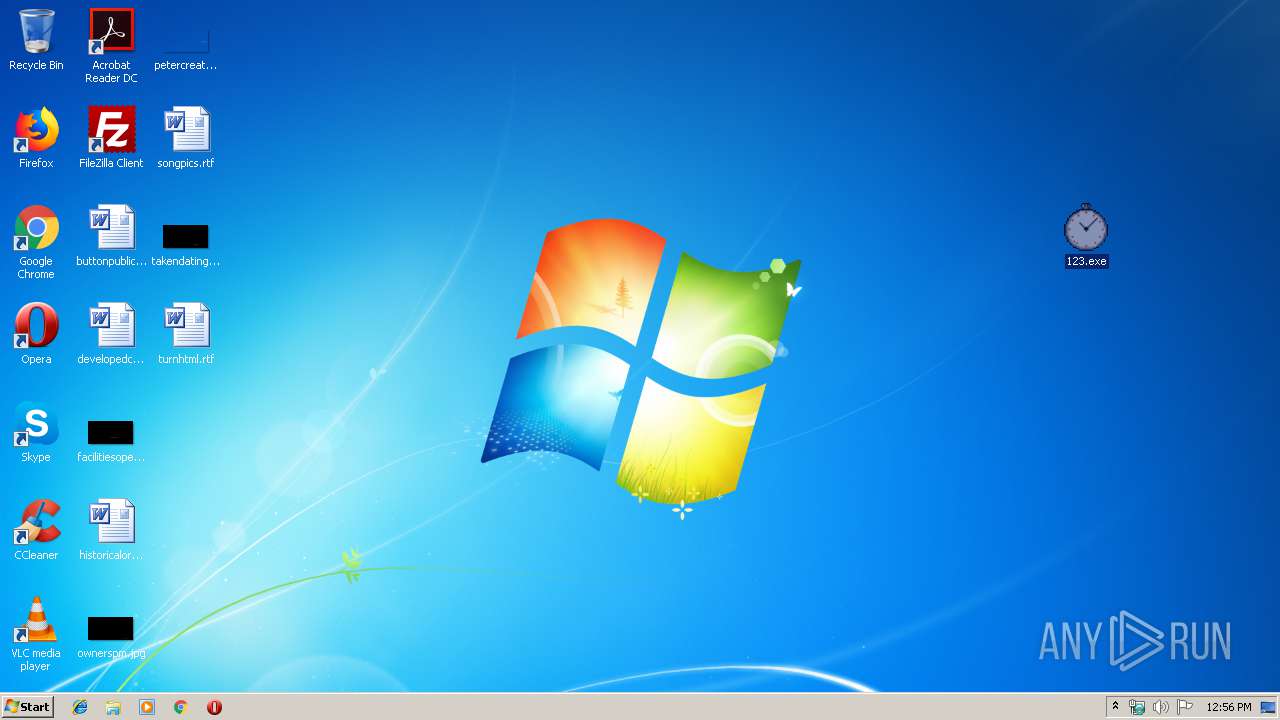
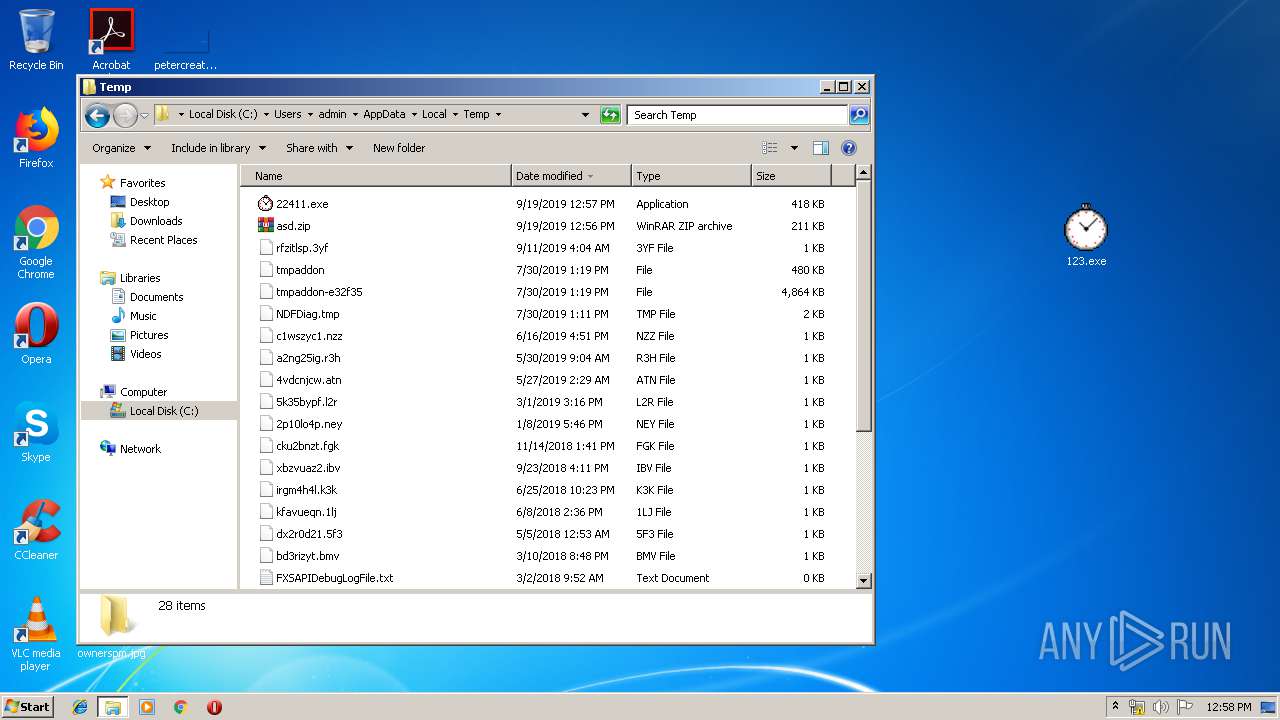
- 123.exe (PID: 2844)
- sysinii.exe (PID: 3600)
- 22411.exe (PID: 3696)
PHORPIEX was detected
- sysinii.exe (PID: 3600)
Changes the autorun value in the registry
- 123.exe (PID: 2844)
SUSPICIOUS
Creates files in the user directory
- sysinii.exe (PID: 3600)
Executable content was dropped or overwritten
- 123.exe (PID: 2844)
- sysinii.exe (PID: 3600)
Starts itself from another location
- sysinii.exe (PID: 3600)
- 123.exe (PID: 2844)
Reads Internet Cache Settings
- sysinii.exe (PID: 3600)
INFO
Manual execution by user
- 123.exe (PID: 2844)
- explorer.exe (PID: 3580)
- NOTEPAD.EXE (PID: 2872)
- WinRAR.exe (PID: 364)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 215278 |
| ZipUncompressedSize: | 428032 |
| ZipFileName: | d9edee0541b9a5baf2cb2b1915aef1d034efd4edd4b3c030b508669da1e2aaf2 |
Total processes
47
Monitored processes
7
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 364 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\asd.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2844 | "C:\Users\admin\Desktop\123.exe" | C:\Users\admin\Desktop\123.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: DTConverter Application Exit code: 0 Version: 2.1 Modules
| |||||||||||||||
| 2852 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\asd.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2872 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Roaming\winsvcs.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3580 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3600 | C:\Users\admin\1528814089\sysinii.exe | C:\Users\admin\1528814089\sysinii.exe | 123.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: DTConverter Application Exit code: 0 Version: 2.1 Modules
| |||||||||||||||
| 3696 | C:\Users\admin\AppData\Local\Temp\22411.exe | C:\Users\admin\AppData\Local\Temp\22411.exe | — | sysinii.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: DTConverter Application Exit code: 0 Version: 2.1 Modules
| |||||||||||||||
Total events
979
Read events
916
Write events
63
Delete events
0
Modification events
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\asd.zip | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
2
Suspicious files
5
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2852.20224\d9edee0541b9a5baf2cb2b1915aef1d034efd4edd4b3c030b508669da1e2aaf2 | — | |
MD5:— | SHA256:— | |||
| 3600 | sysinii.exe | C: | — | |
MD5:— | SHA256:— | |||
| 364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb364.33451\d9edee0541b9a5baf2cb2b1915aef1d034efd4edd4b3c030b508669da1e2aaf2 | — | |
MD5:— | SHA256:— | |||
| 3600 | sysinii.exe | C:\Users\admin\AppData\Local\Temp\22411.exe | binary | |
MD5:— | SHA256:— | |||
| 2844 | 123.exe | C:\Users\admin\1528814089\sysinii.exe | executable | |
MD5:— | SHA256:— | |||
| 3600 | sysinii.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\2[1] | binary | |
MD5:— | SHA256:— | |||
| 3600 | sysinii.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\3[1] | binary | |
MD5:— | SHA256:— | |||
| 3600 | sysinii.exe | C:\Users\admin\AppData\Local\Temp\33076.exe | binary | |
MD5:— | SHA256:— | |||
| 3600 | sysinii.exe | C:\Users\admin\AppData\Local\Temp\17135.exe | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
5
DNS requests
120
Threats
71
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3600 | sysinii.exe | GET | — | 7.5.0.4:80 | http://thaus.top/1 | US | — | — | malicious |
3600 | sysinii.exe | GET | — | 7.5.0.4:80 | http://thaus.top/t.php?new=1 | US | — | — | malicious |
3600 | sysinii.exe | GET | — | 185.176.27.132:80 | http://185.176.27.132/2 | GB | — | — | malicious |
3600 | sysinii.exe | GET | 200 | 185.176.27.132:80 | http://185.176.27.132/2 | GB | binary | 418 Kb | malicious |
3600 | sysinii.exe | GET | — | 185.176.27.132:80 | http://185.176.27.132/3 | GB | — | — | malicious |
3600 | sysinii.exe | GET | 404 | 185.176.27.132:80 | http://185.176.27.132/t.php?new=1 | GB | html | 178 b | malicious |
3600 | sysinii.exe | GET | 404 | 185.176.27.132:80 | http://185.176.27.132/6 | GB | html | 178 b | malicious |
3600 | sysinii.exe | GET | 404 | 185.176.27.132:80 | http://185.176.27.132/8 | GB | html | 178 b | malicious |
3600 | sysinii.exe | GET | 404 | 185.176.27.132:80 | http://185.176.27.132/5 | GB | html | 178 b | malicious |
3600 | sysinii.exe | GET | 404 | 185.176.27.132:80 | http://185.176.27.132/7 | GB | html | 178 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3600 | sysinii.exe | 7.5.0.4:80 | thaus.top | — | US | suspicious |
3600 | sysinii.exe | 185.176.27.132:80 | — | — | GB | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urusurofhsorhfuuhr.su |
| unknown |
aeifaeifhutuhuhusr.su |
| unknown |
rzhsudhugugfugugsr.su |
| unknown |
bfagzzezgaegzgfair.su |
| unknown |
eaeuafhuaegfugeudr.su |
| unknown |
aeufuaehfiuehfuhfr.su |
| unknown |
daedagheauehfuuhfr.su |
| unknown |
aeoughaoheguaoehdr.su |
| unknown |
eguaheoghouughahsr.su |
| unknown |
huaeokaefoaeguaehr.su |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1060 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
3600 | sysinii.exe | Misc Attack | ET DROP Dshield Block Listed Source group 1 |
1060 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
1060 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
1060 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
1060 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
1060 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
1060 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
1060 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
1060 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
4 ETPRO signatures available at the full report