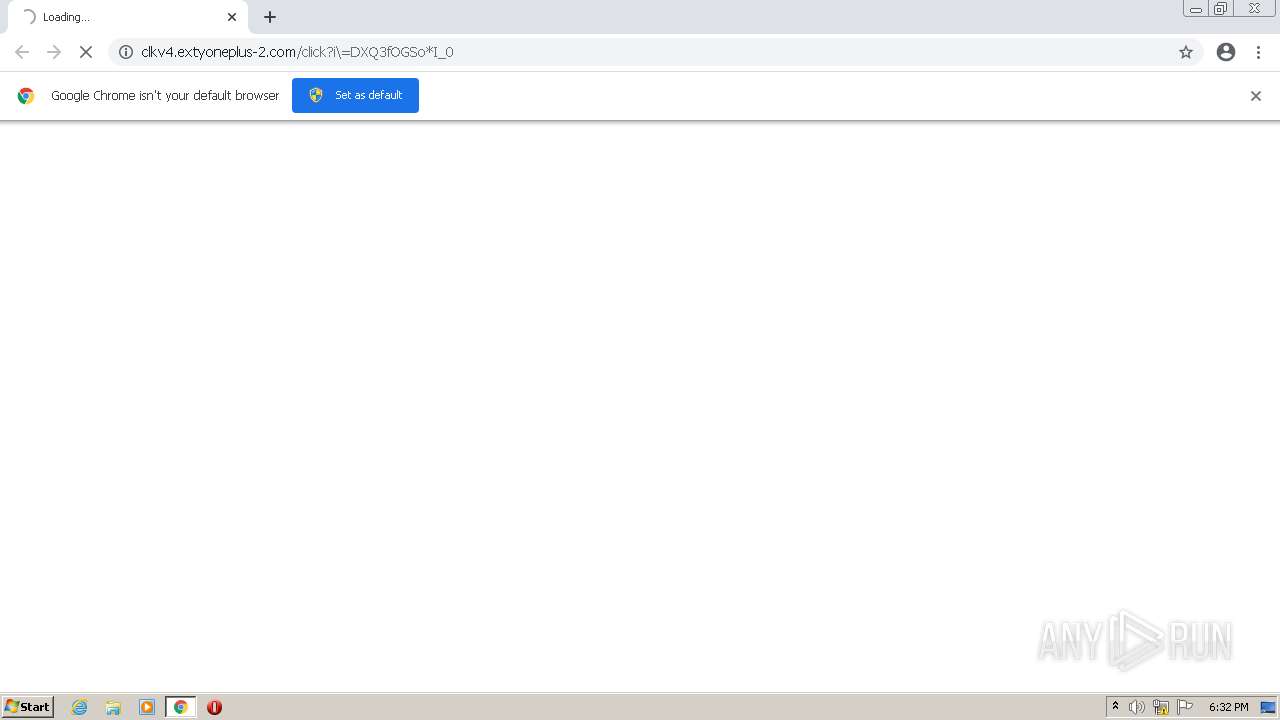
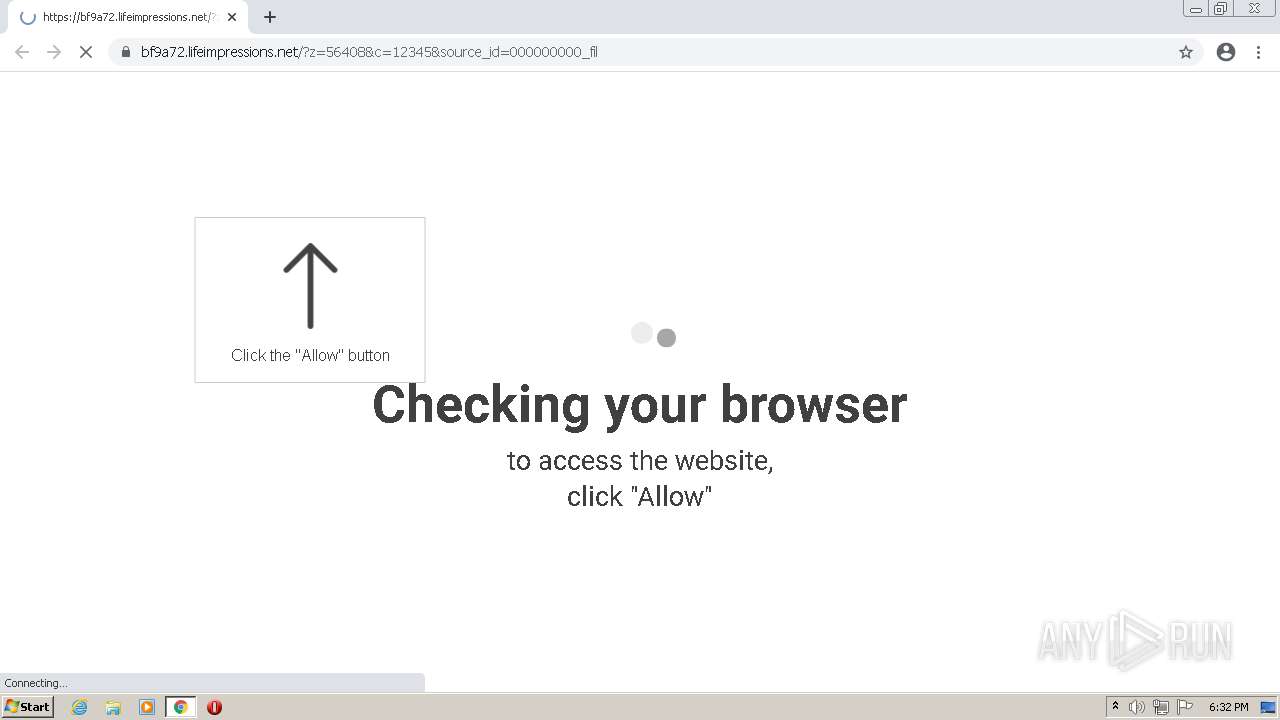
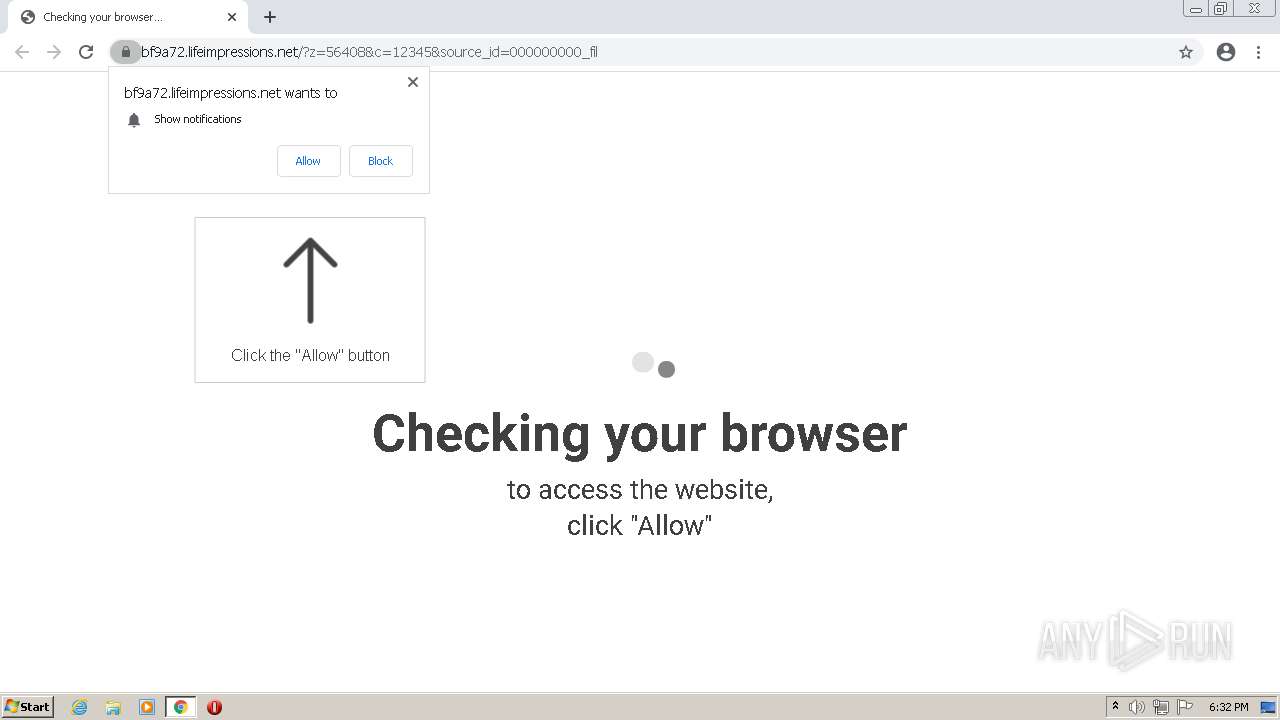
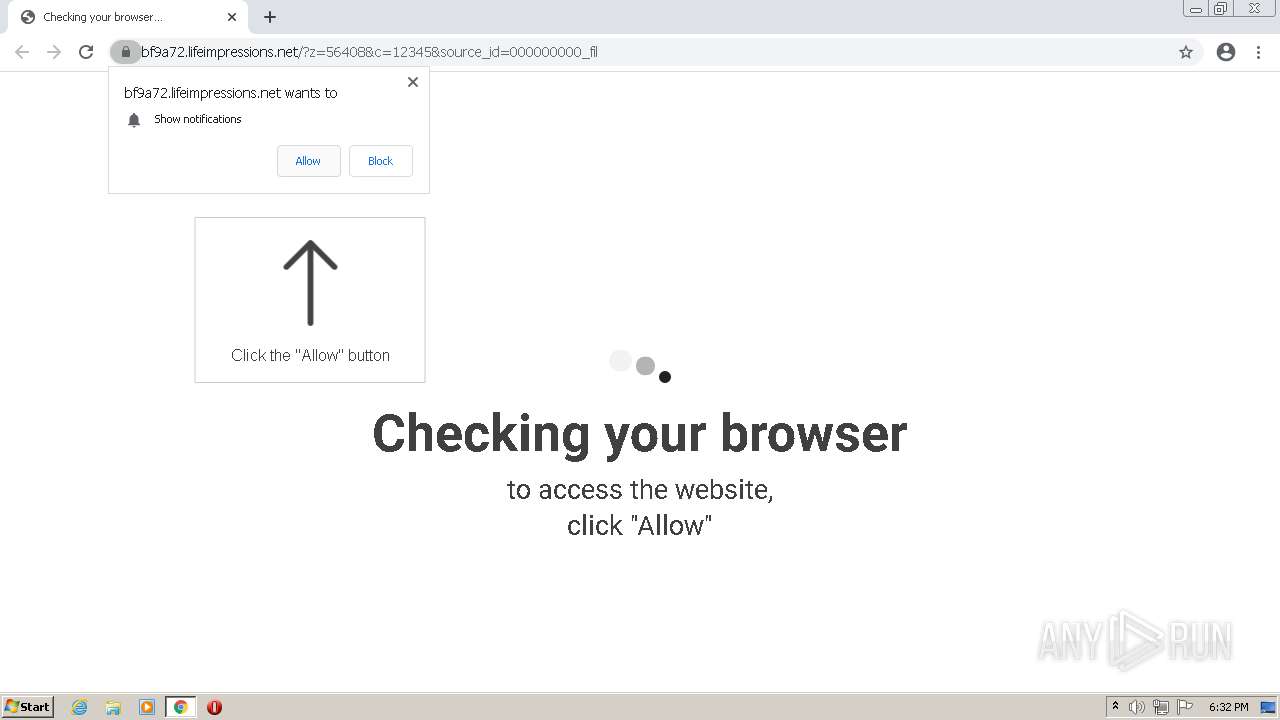
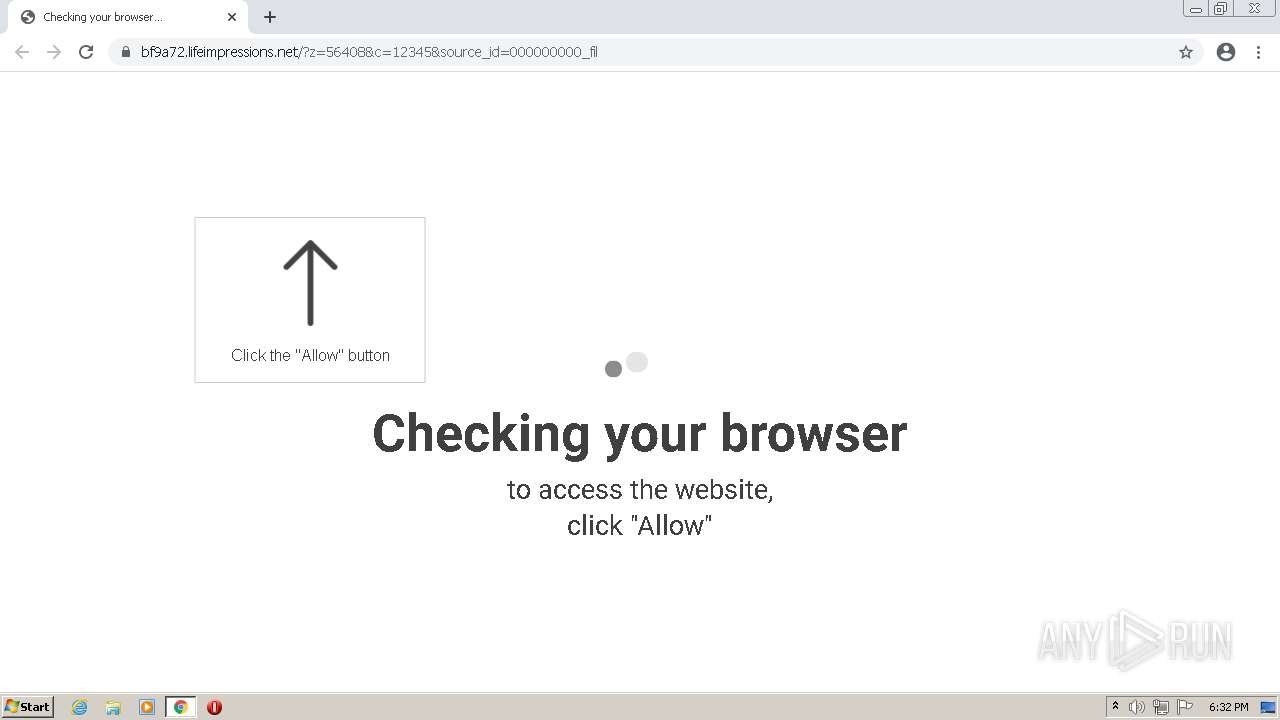
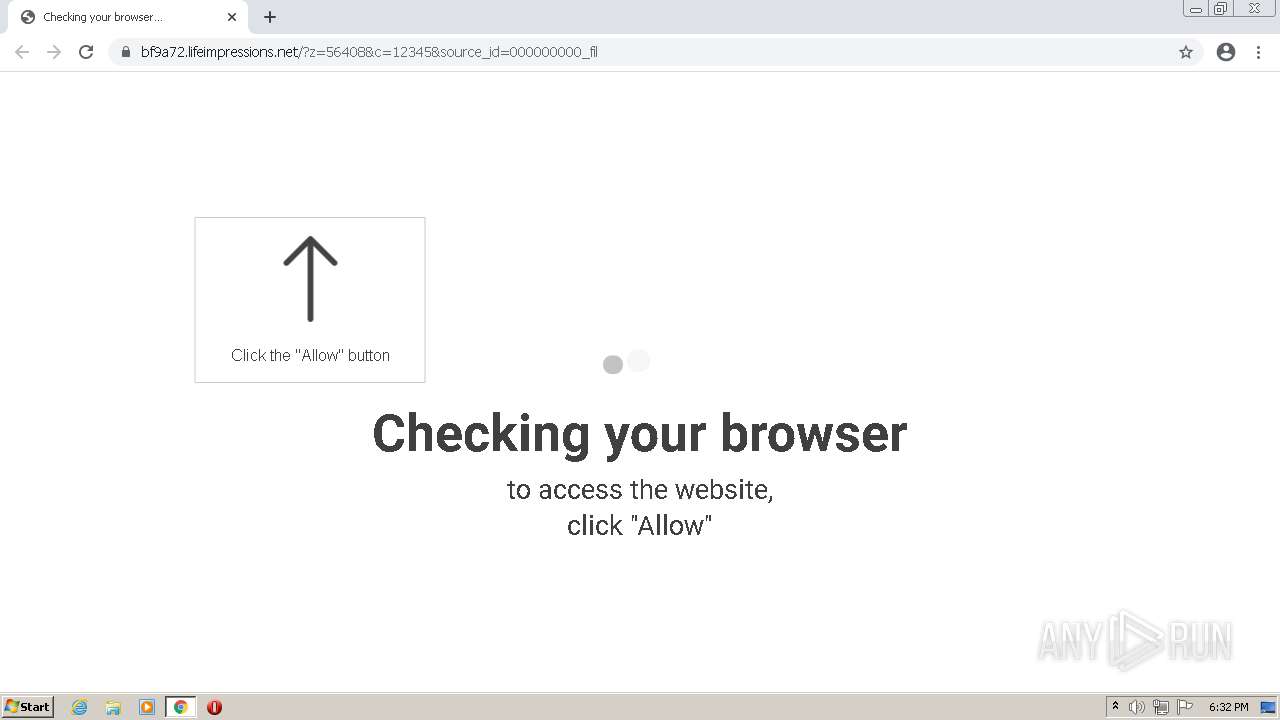
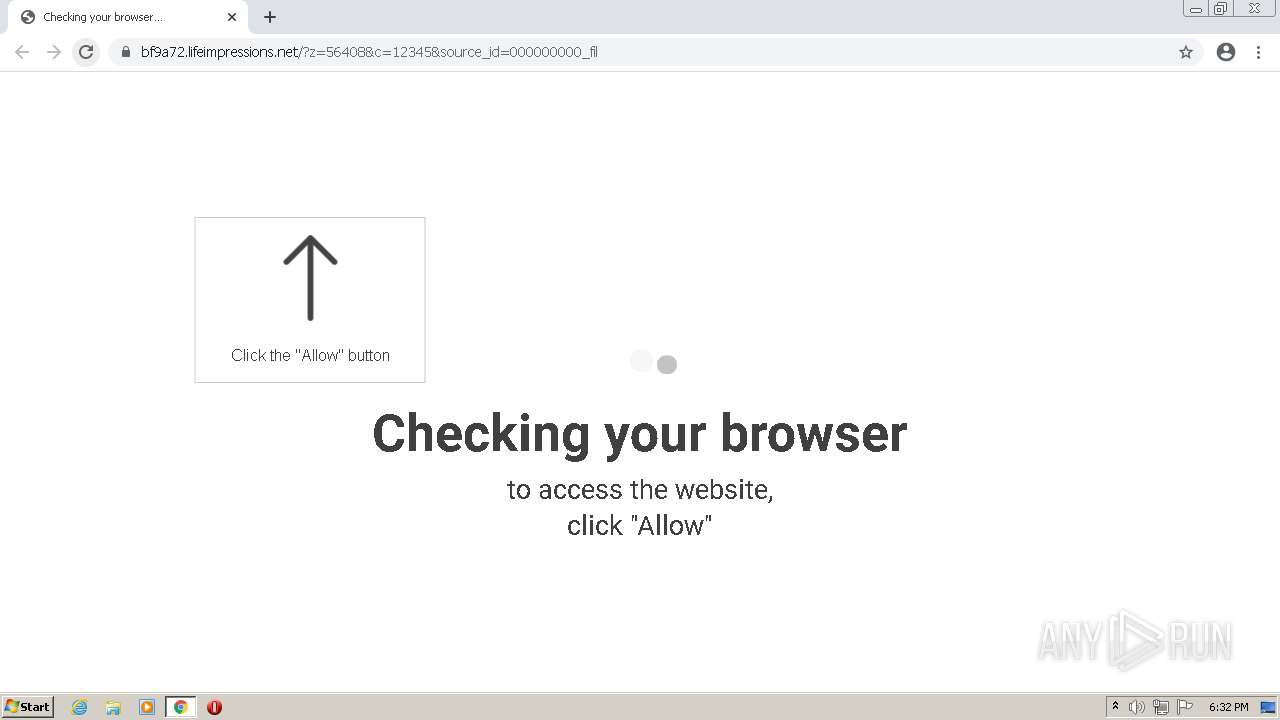
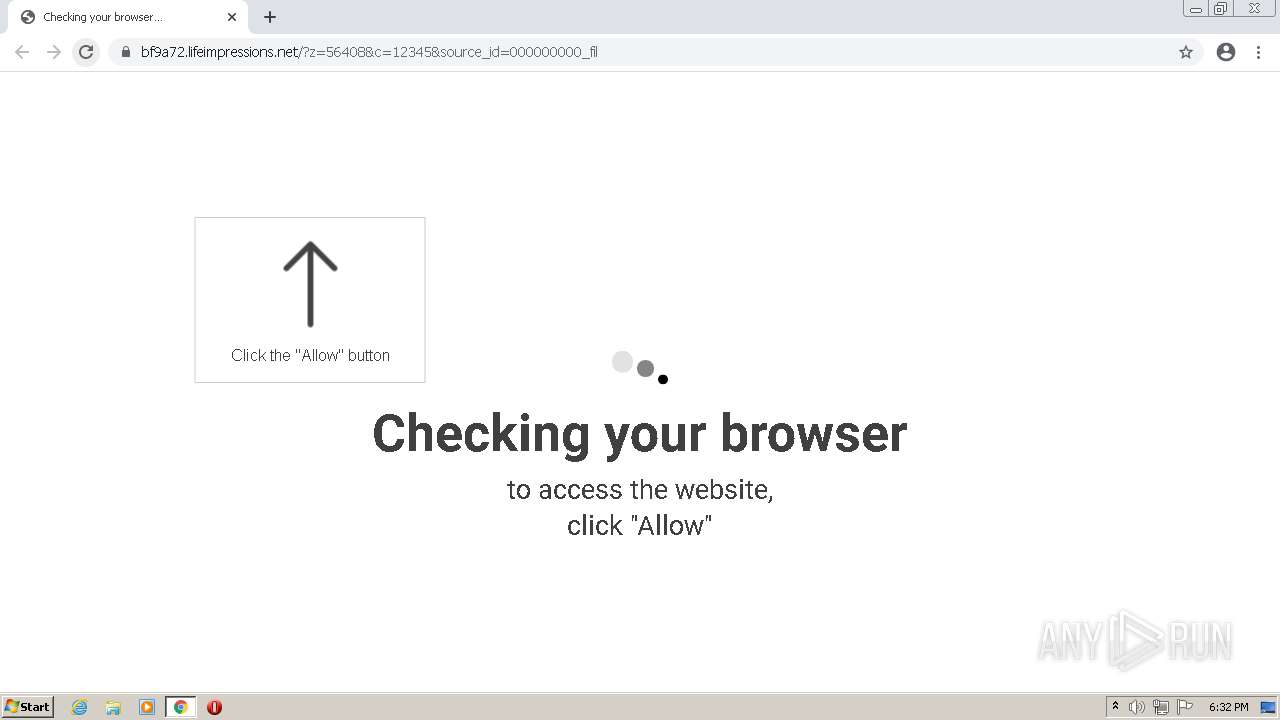
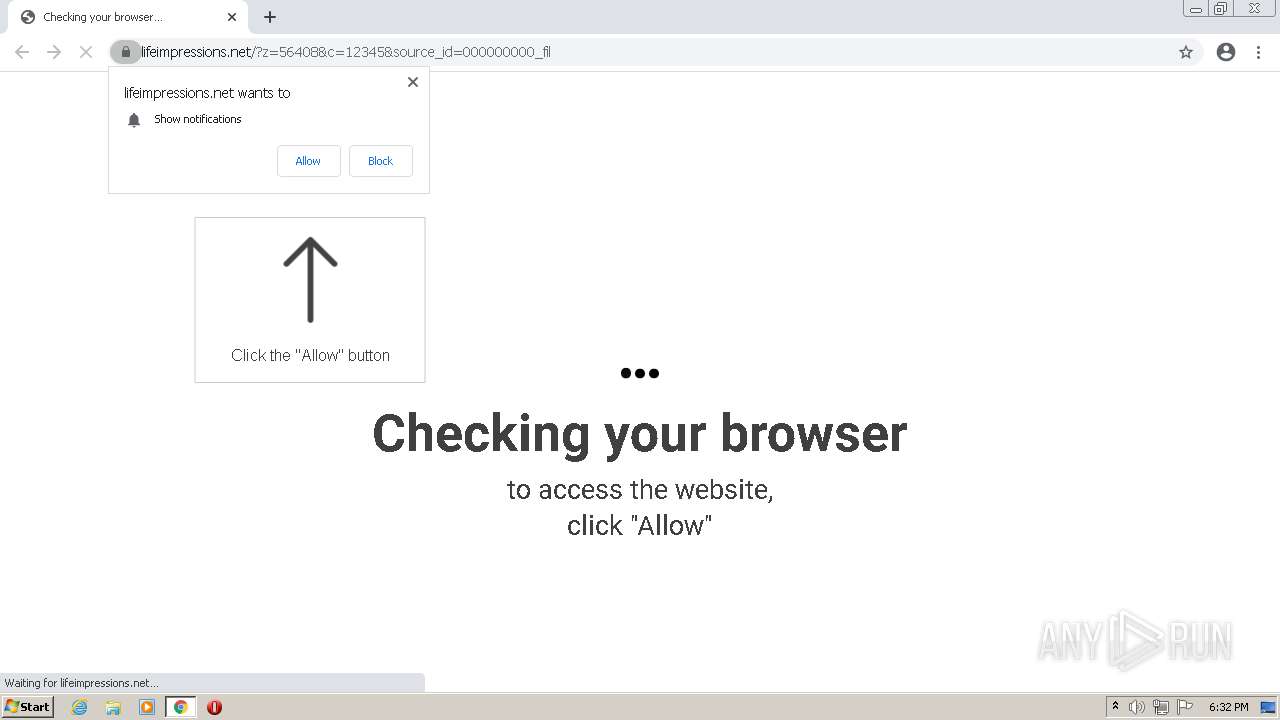
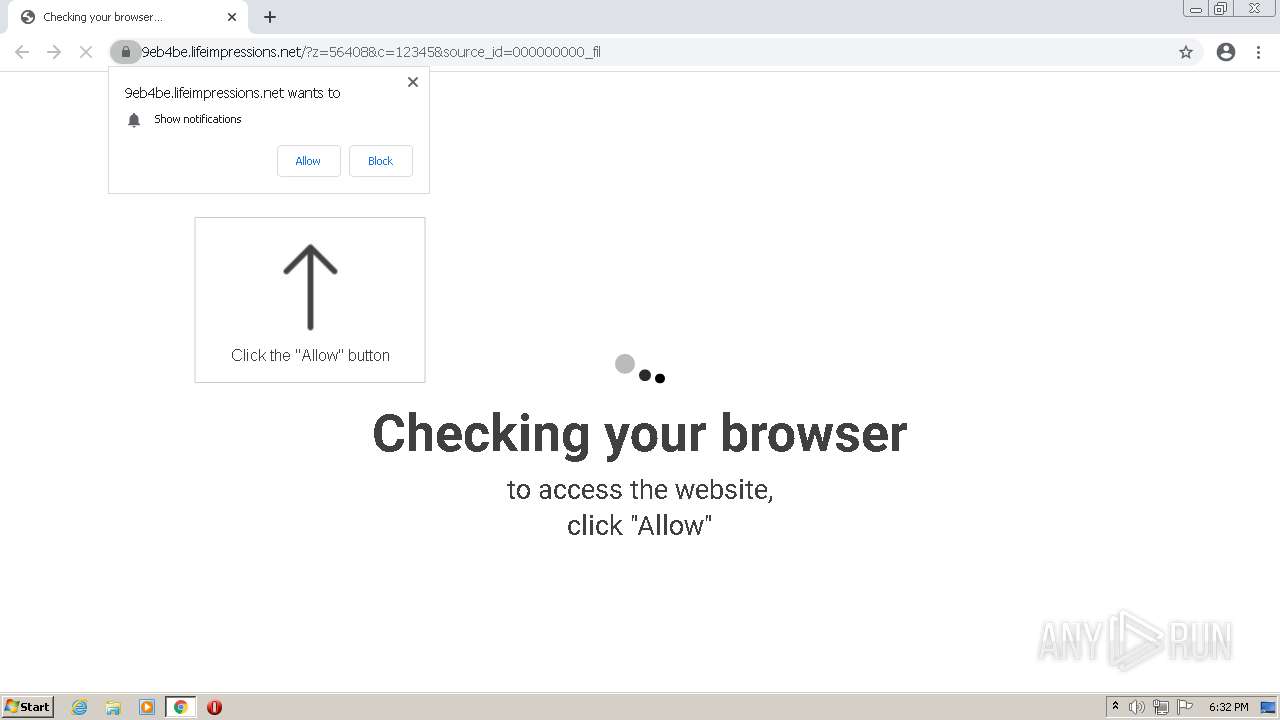
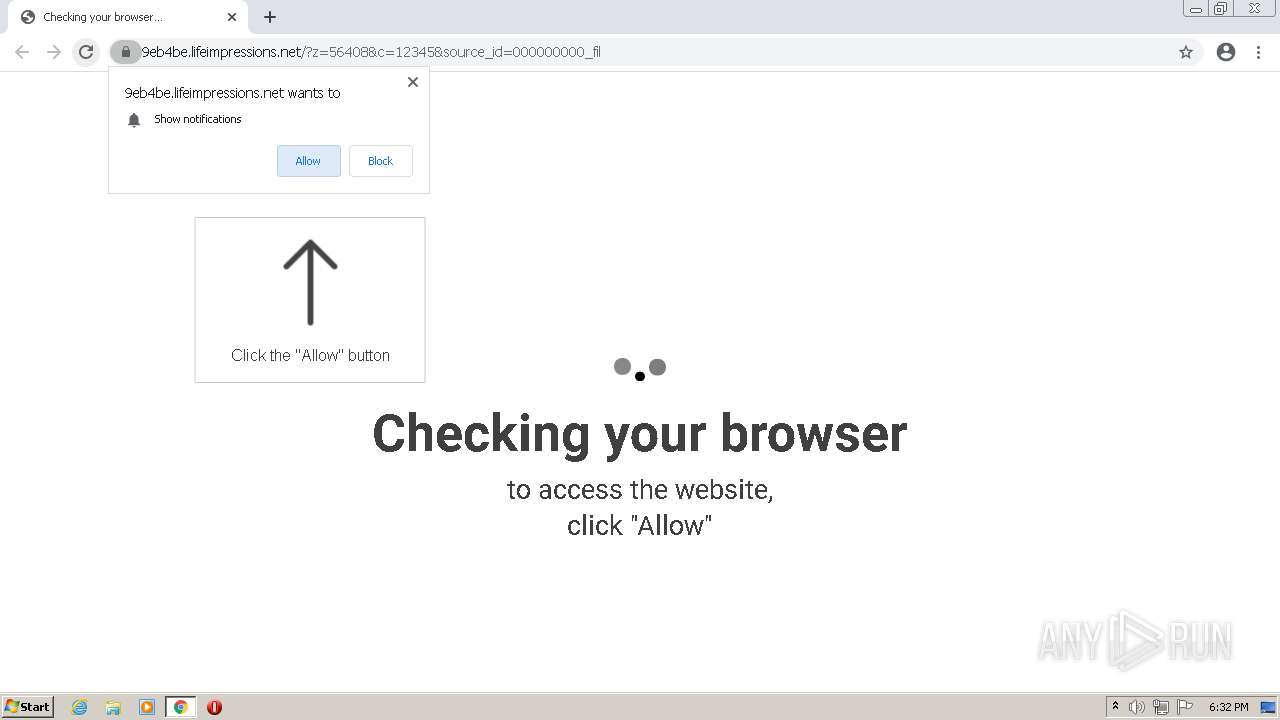
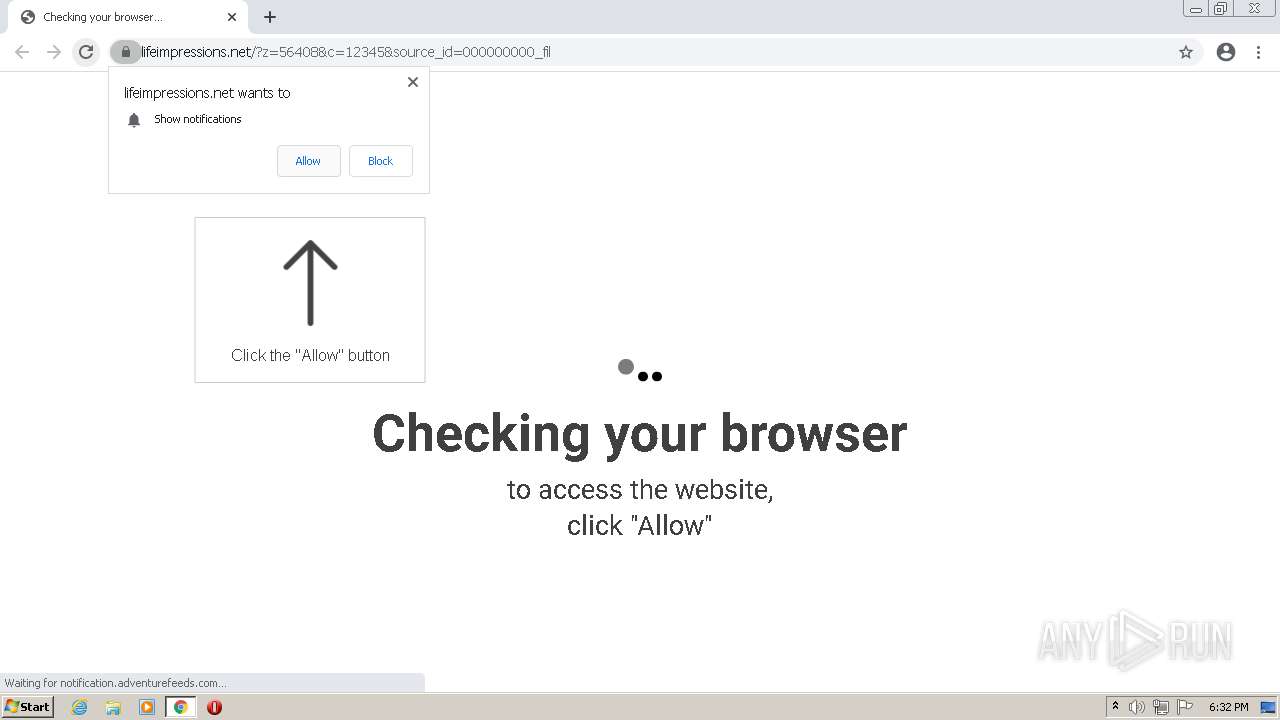
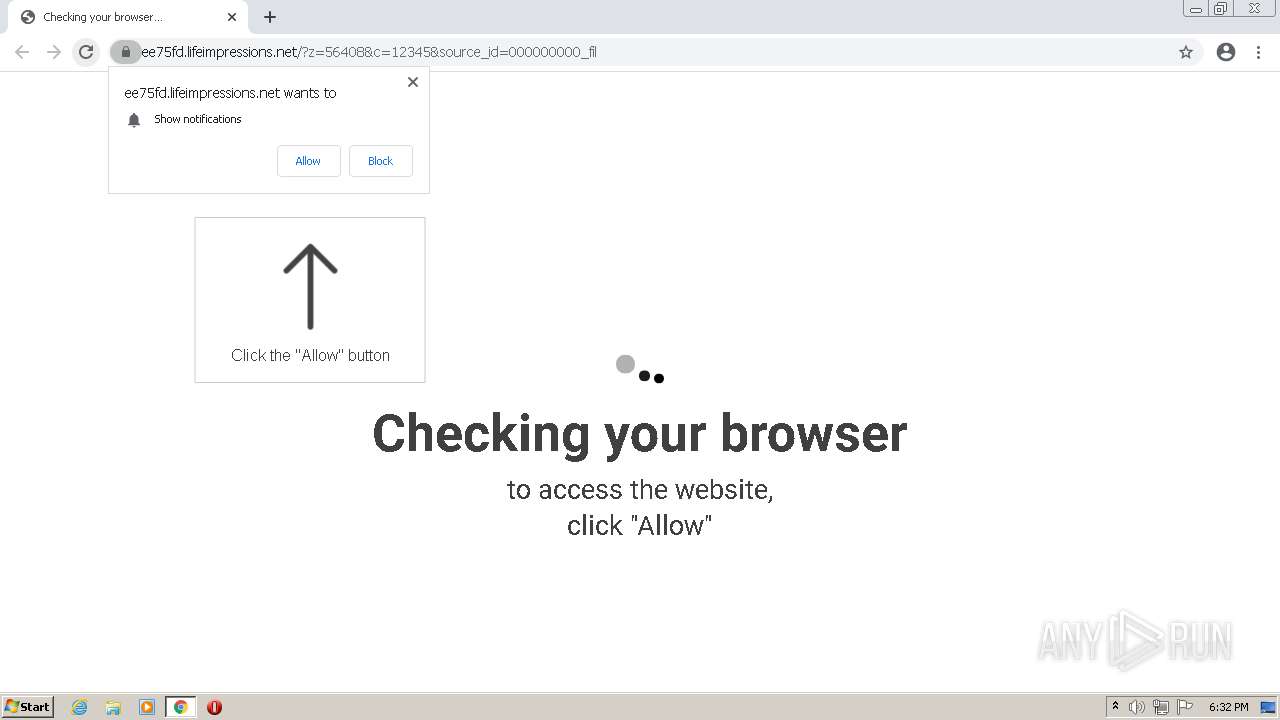
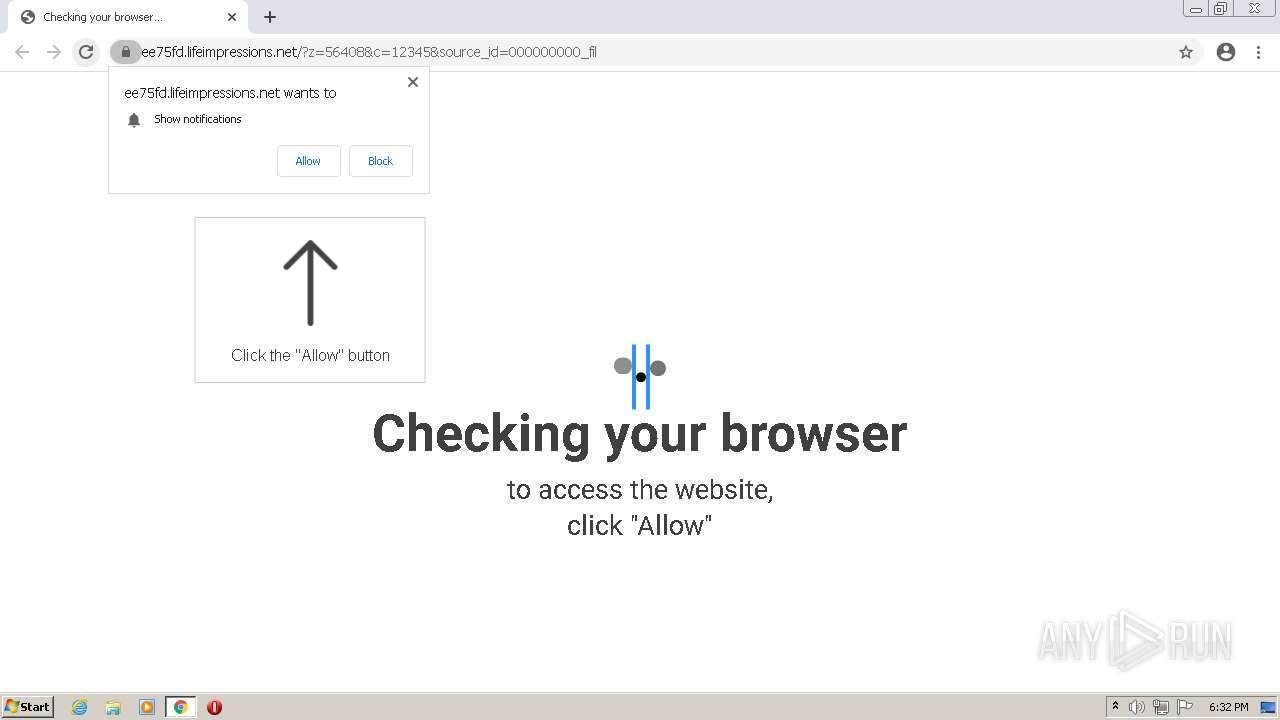
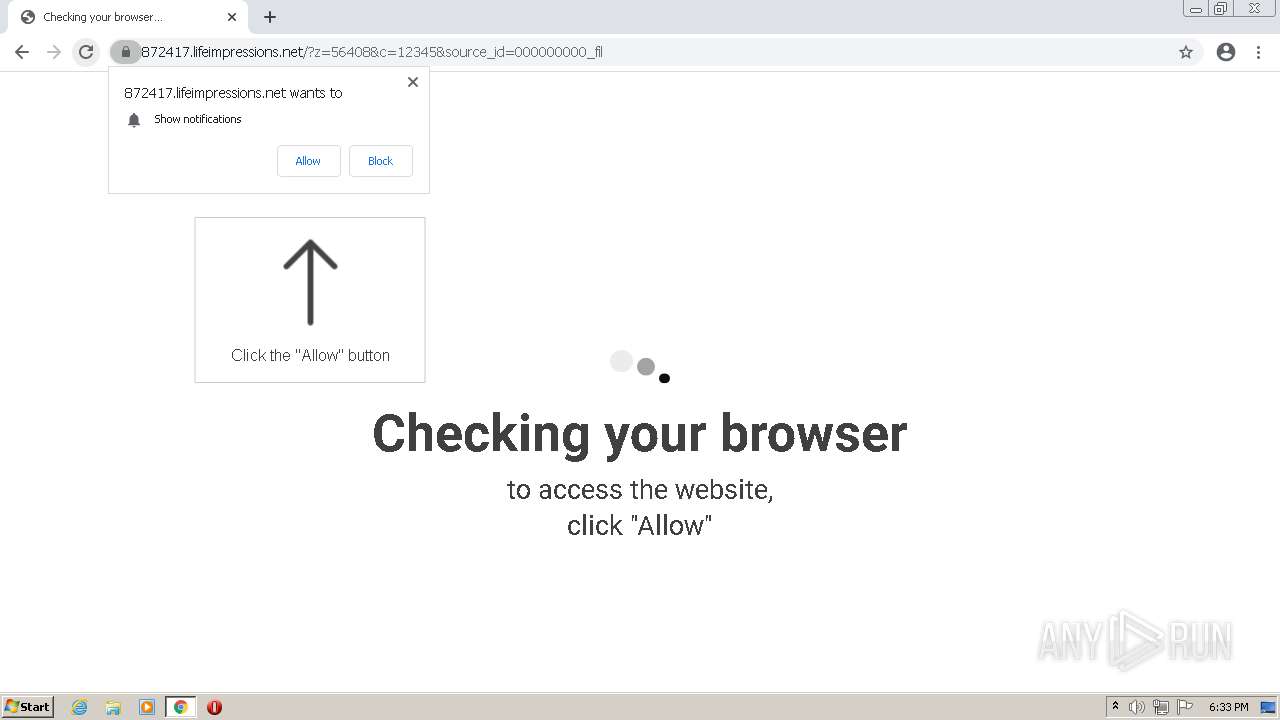
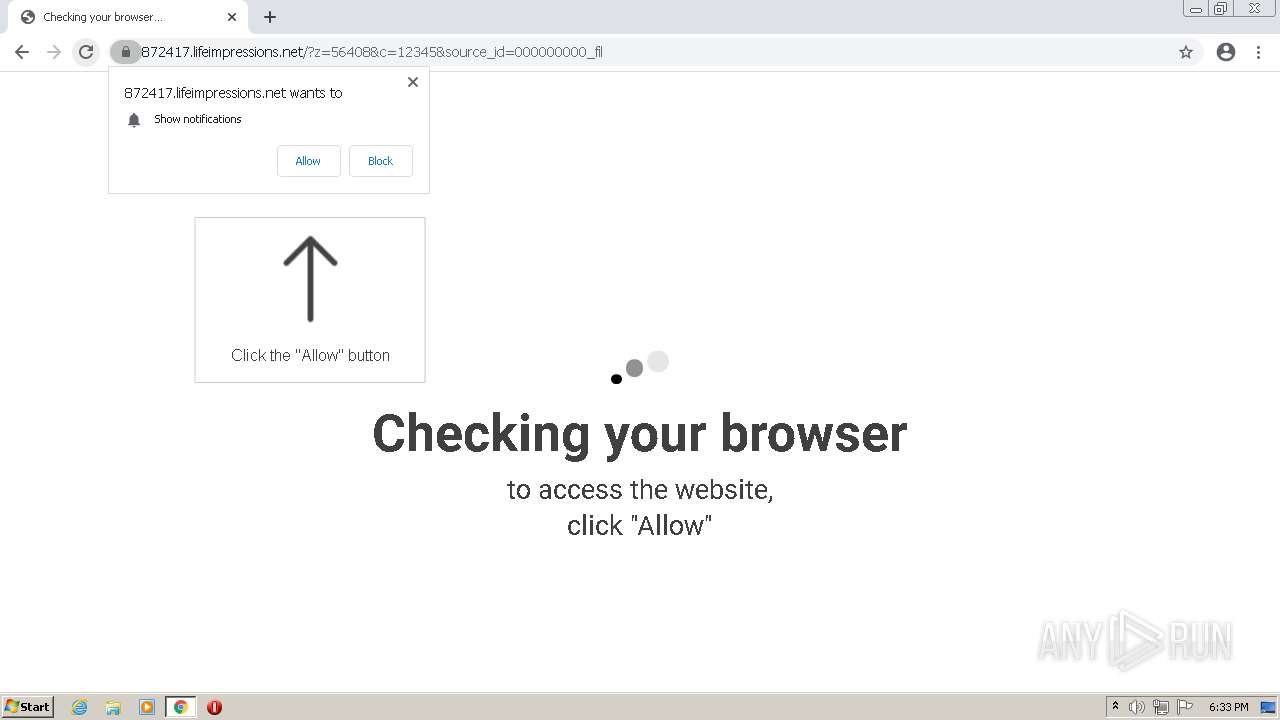
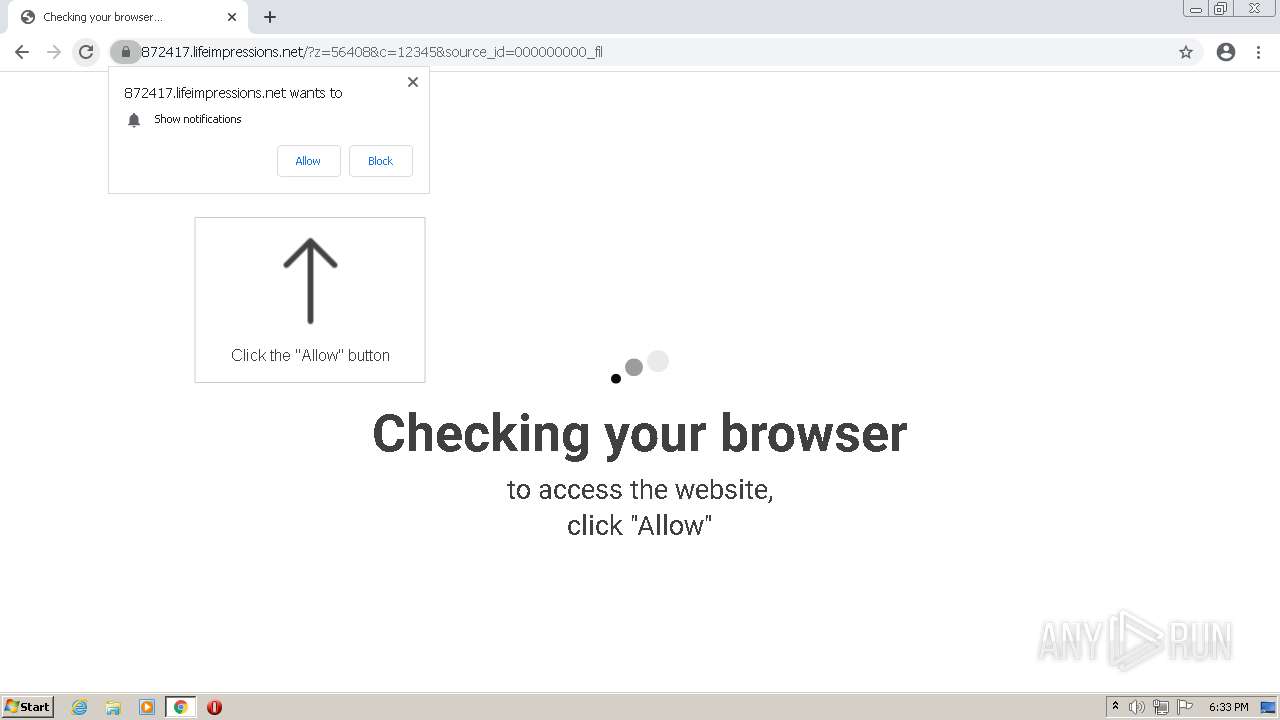
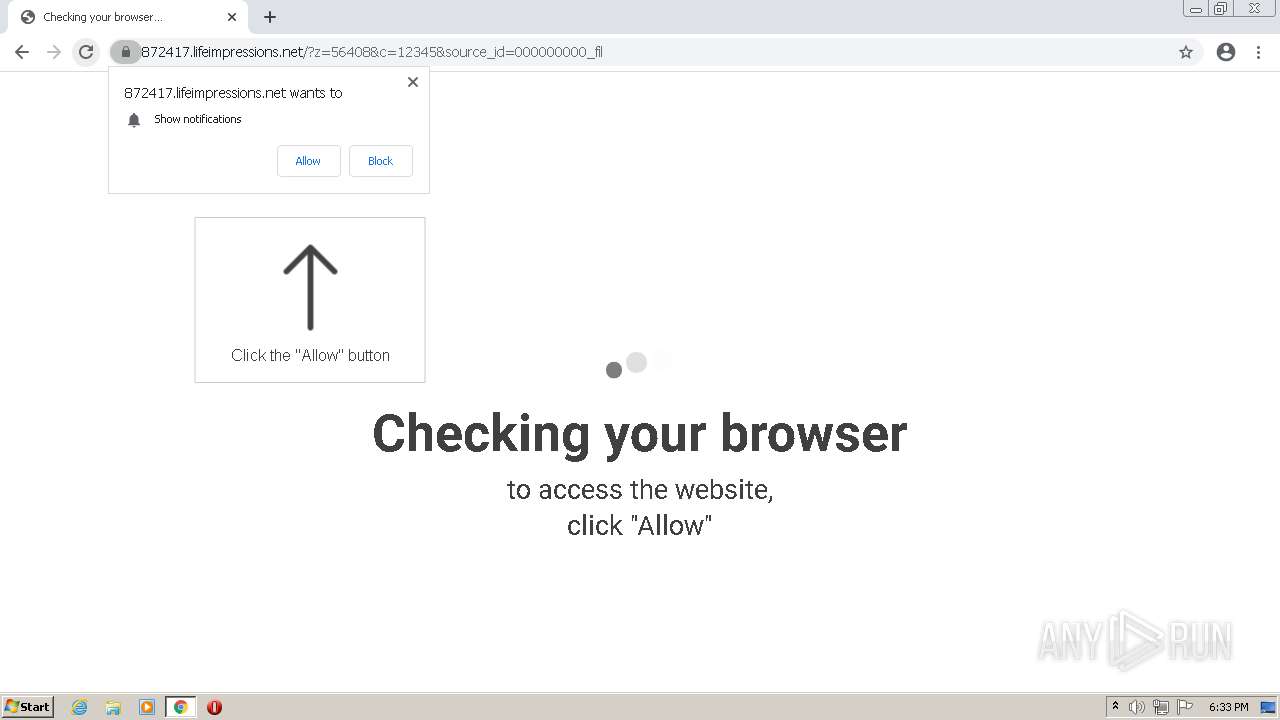
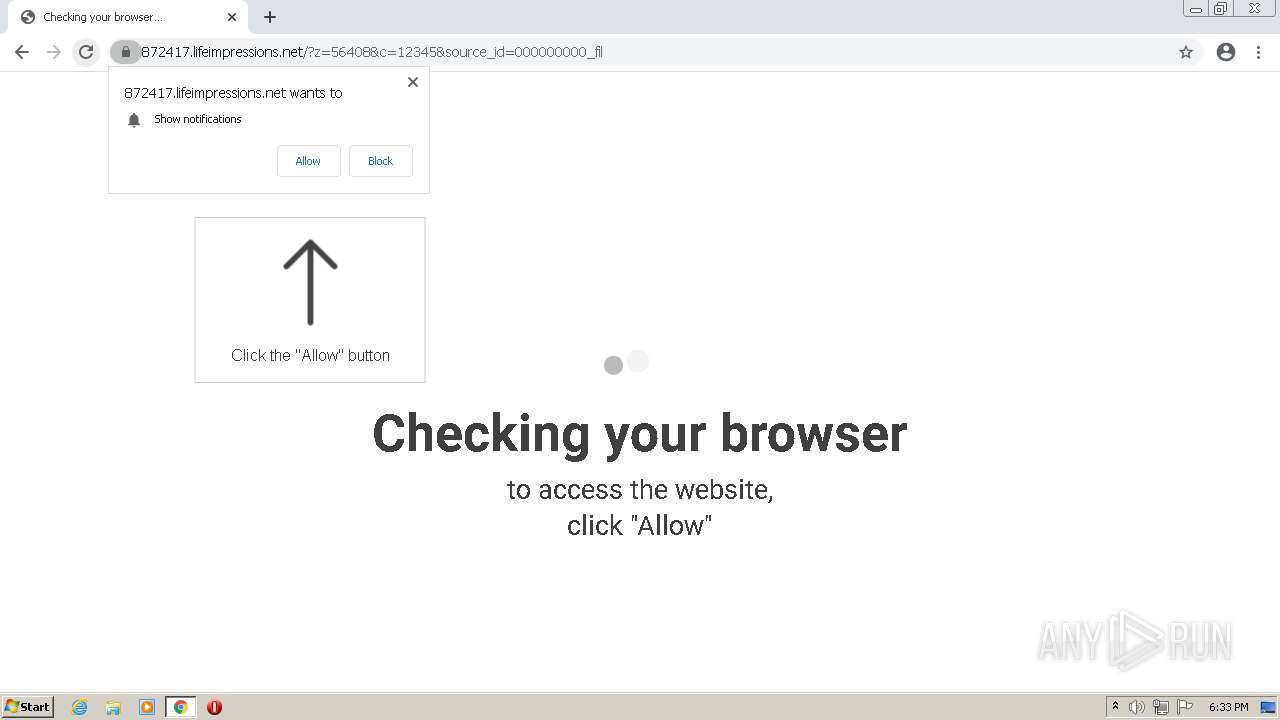
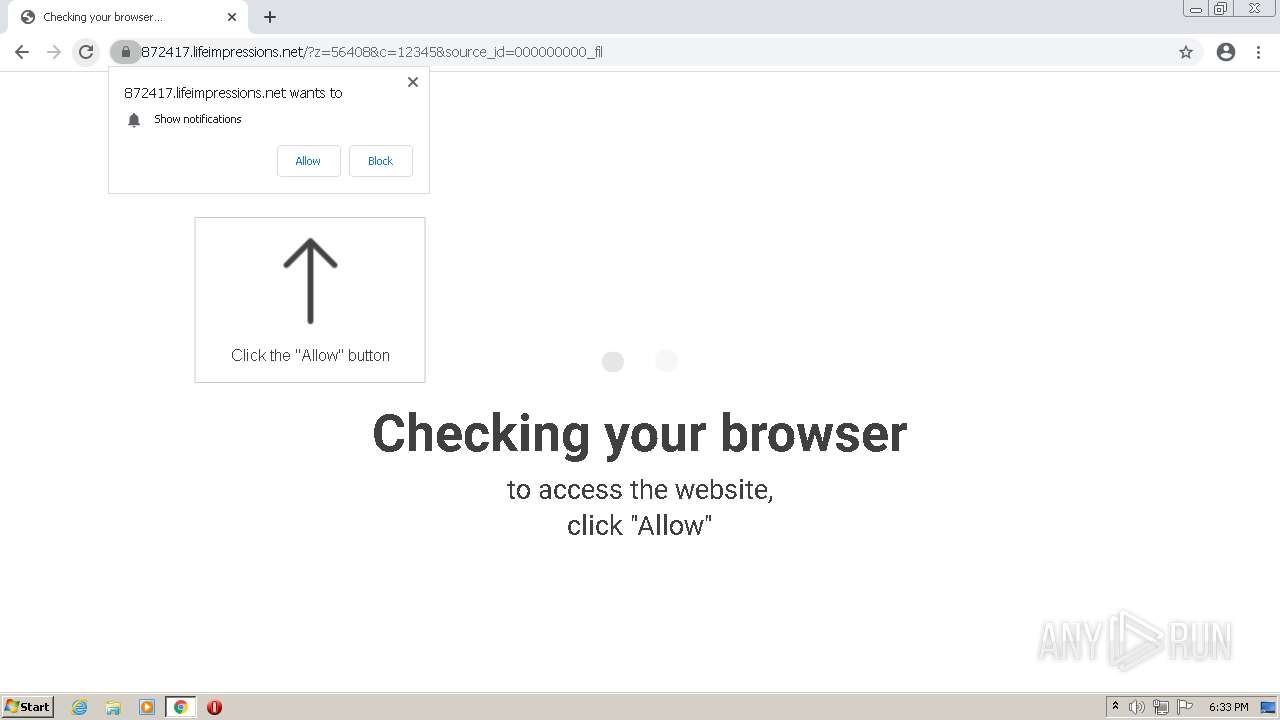
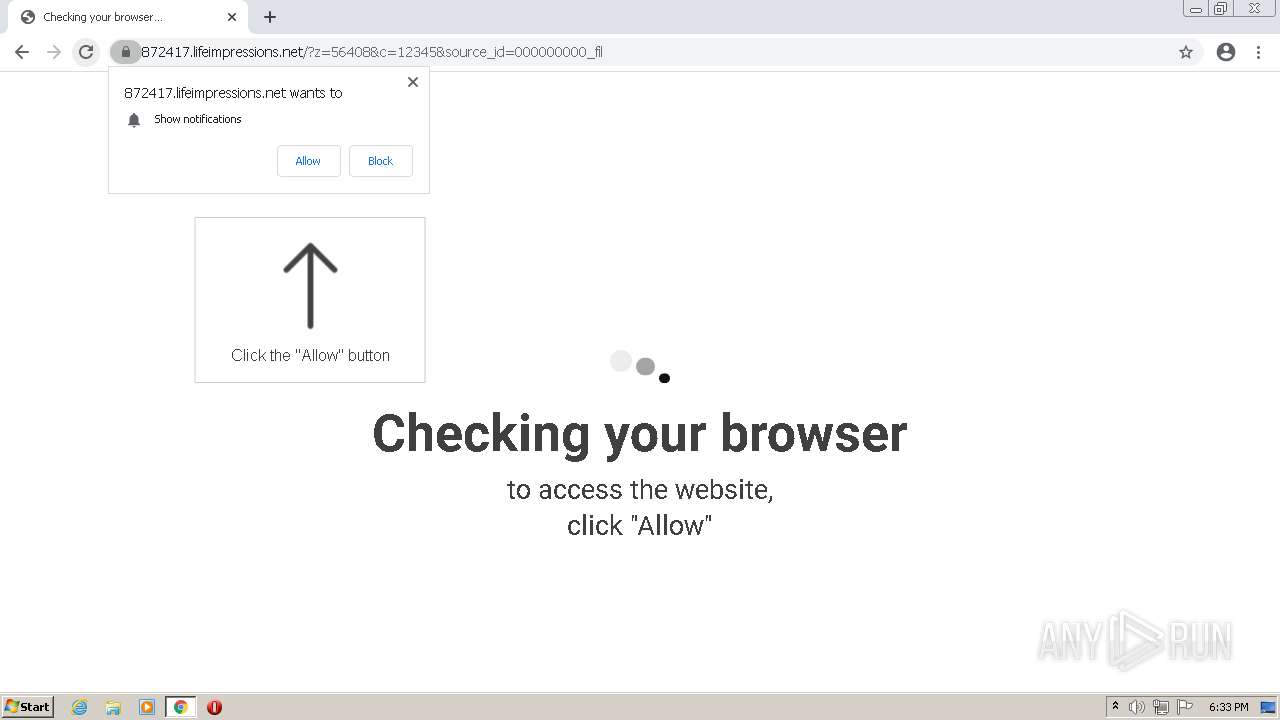
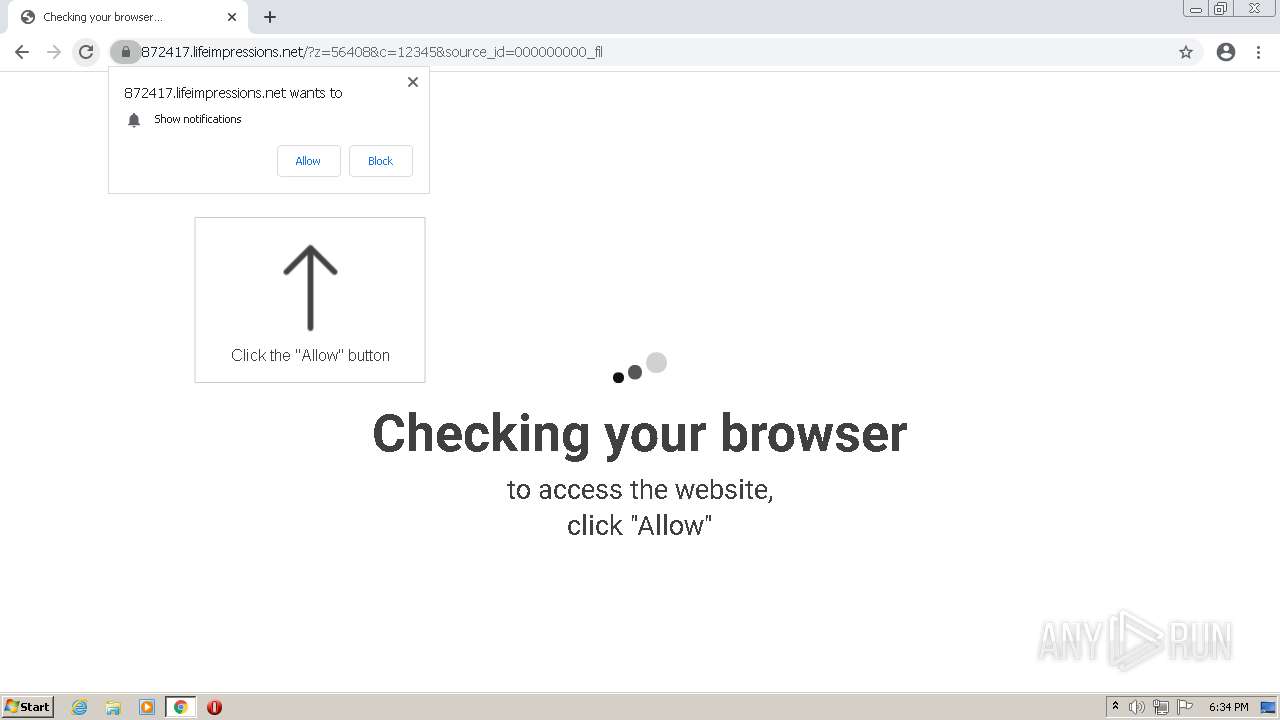
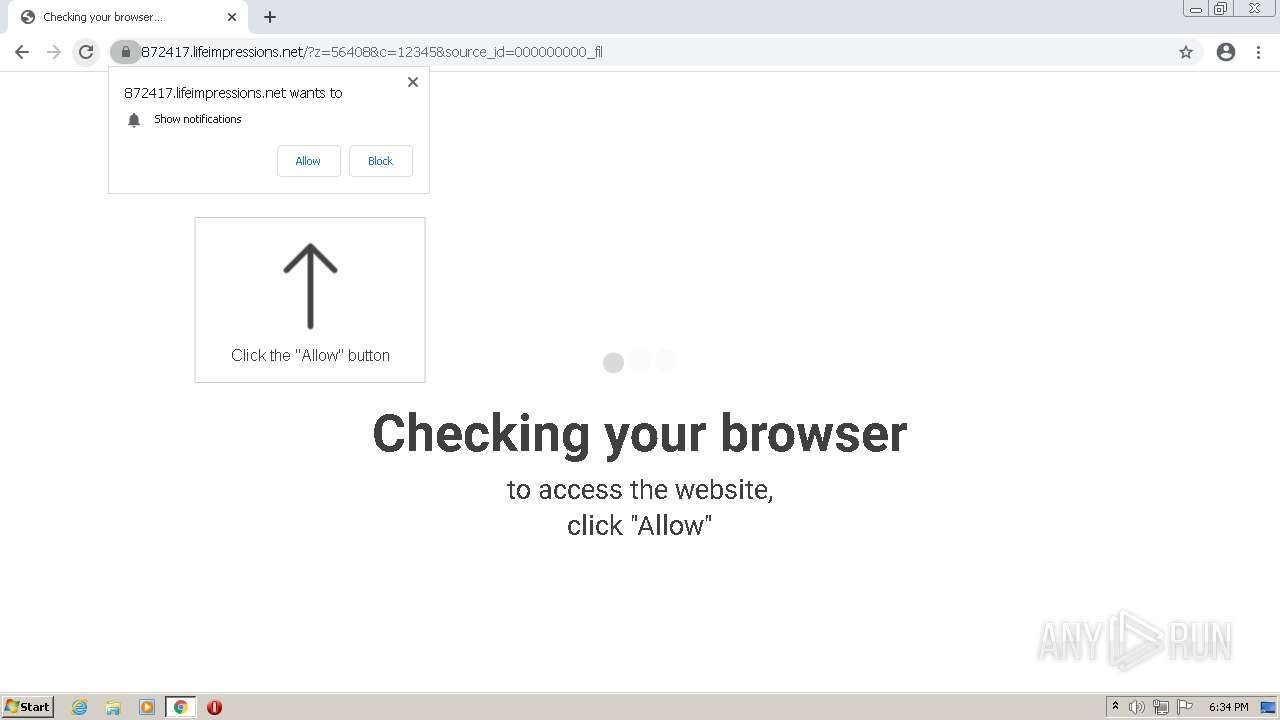
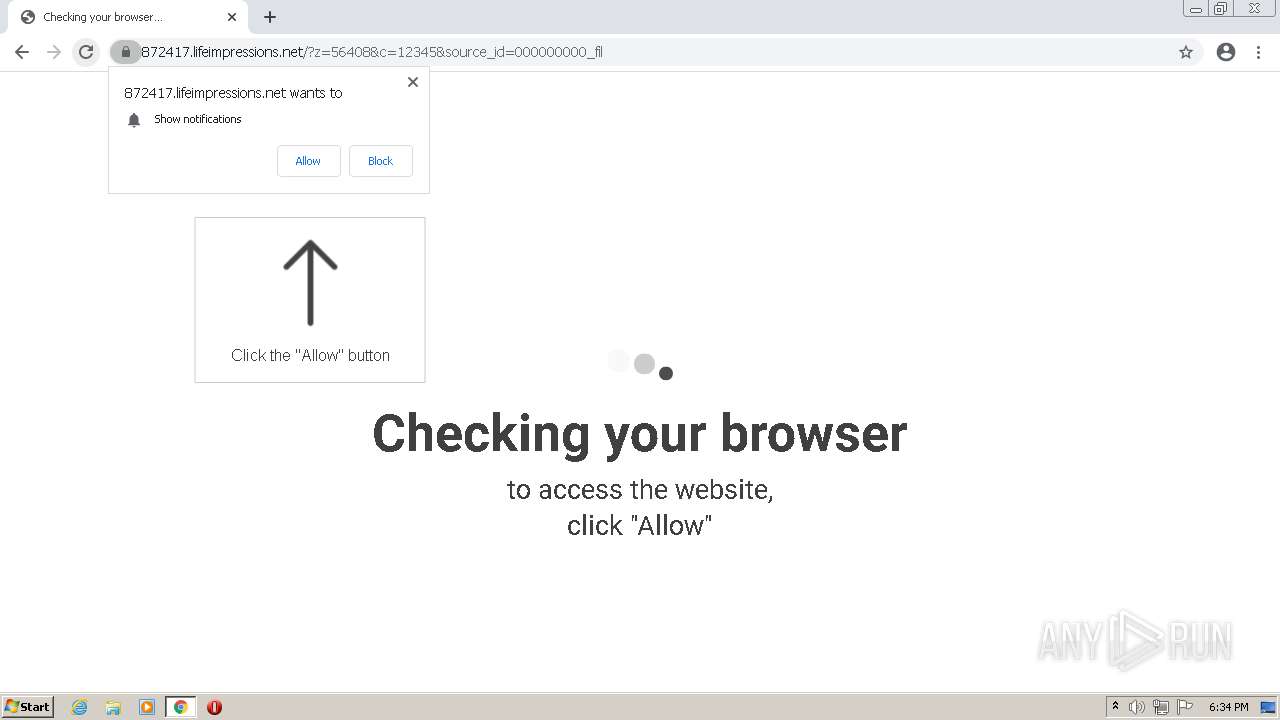
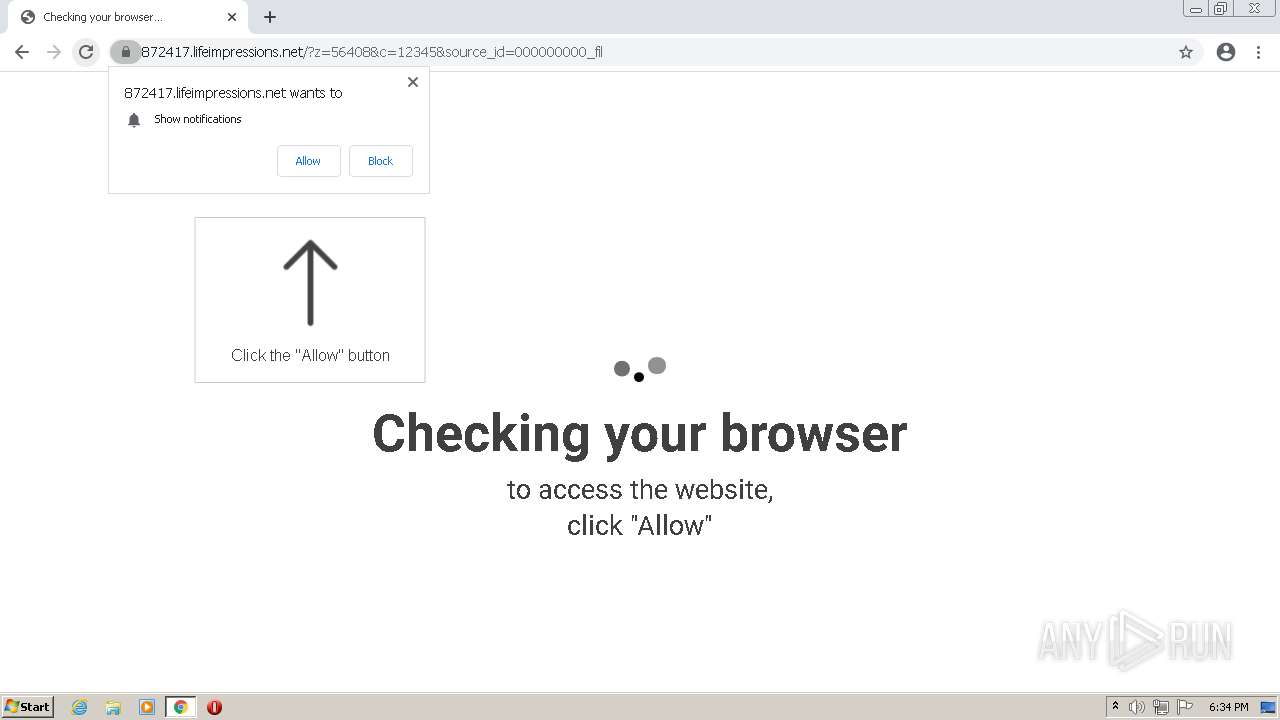
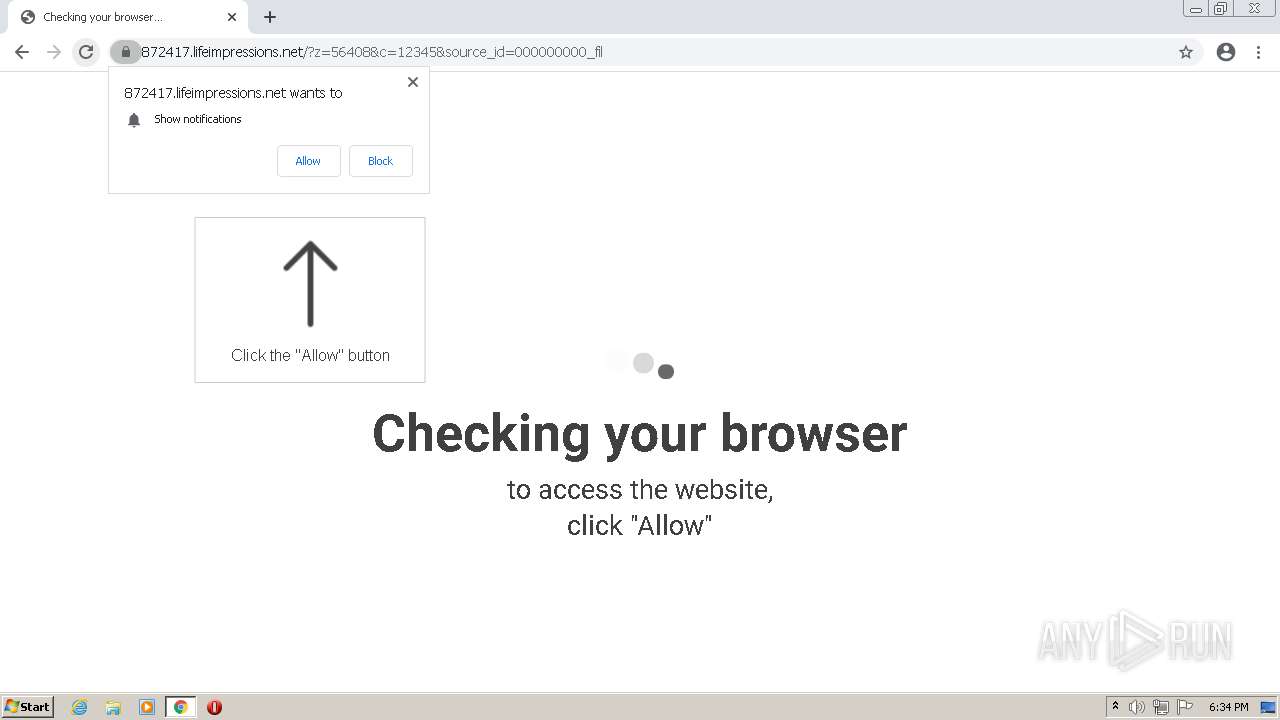
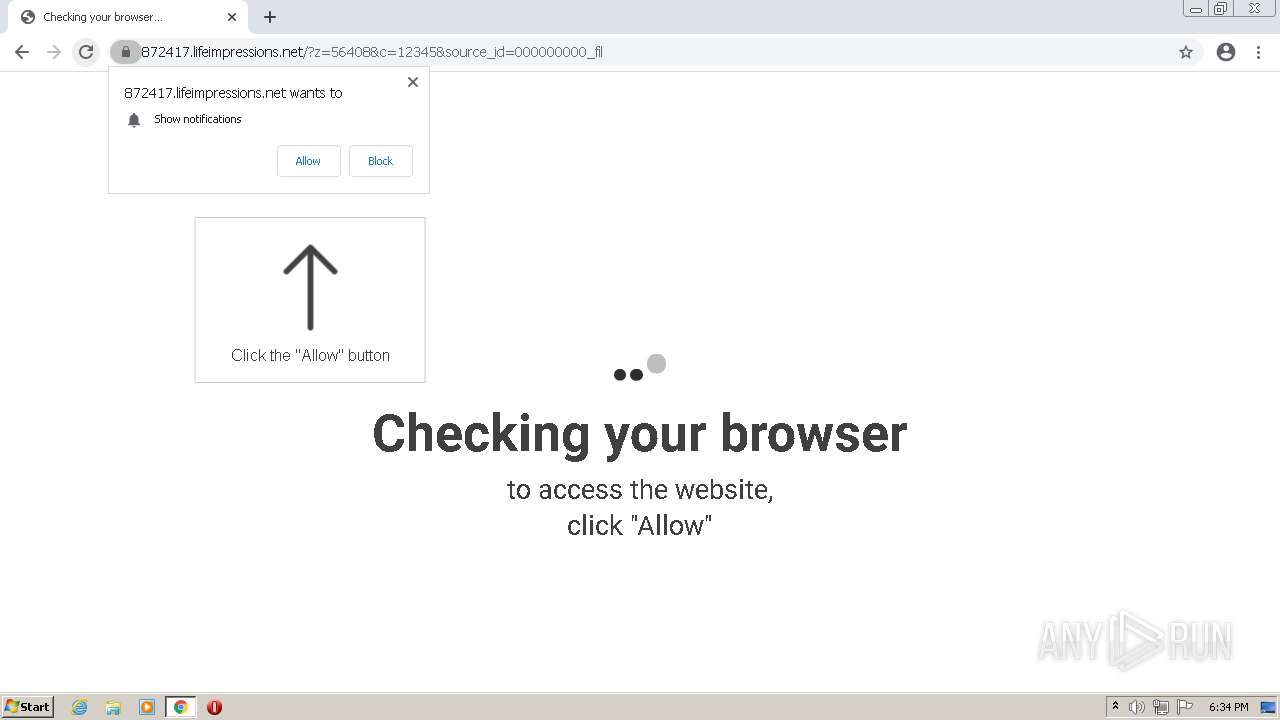
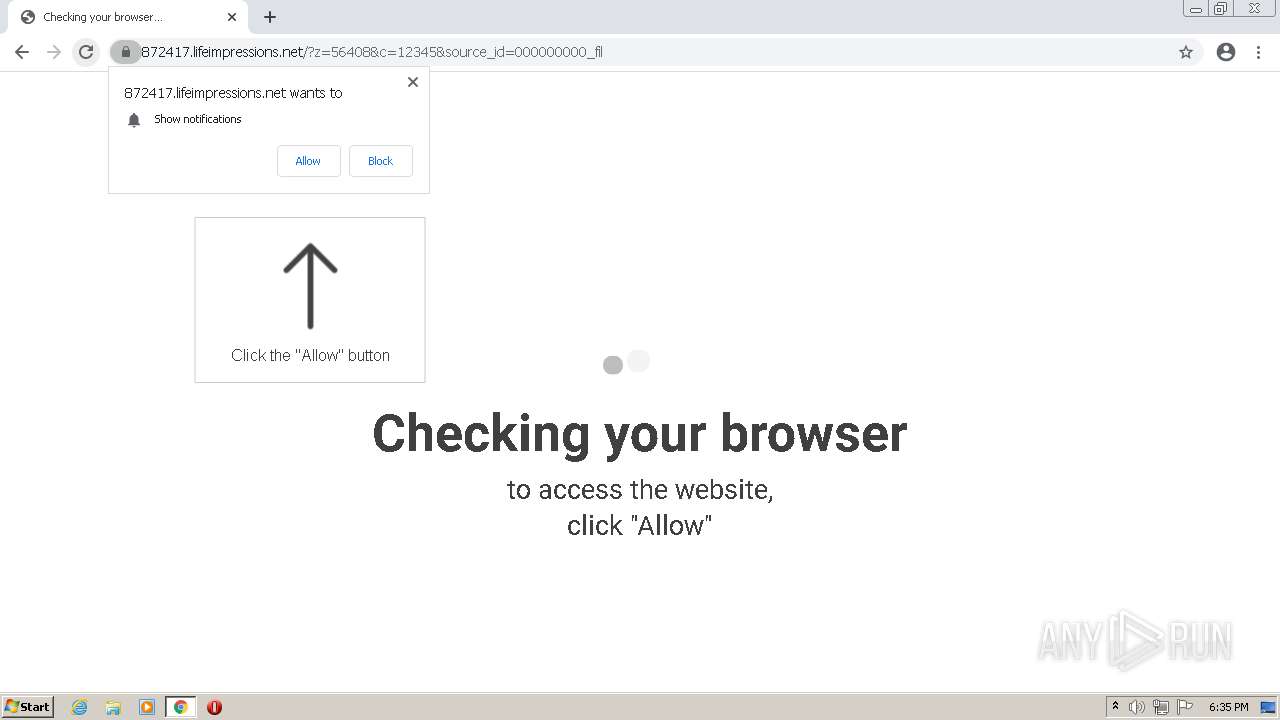
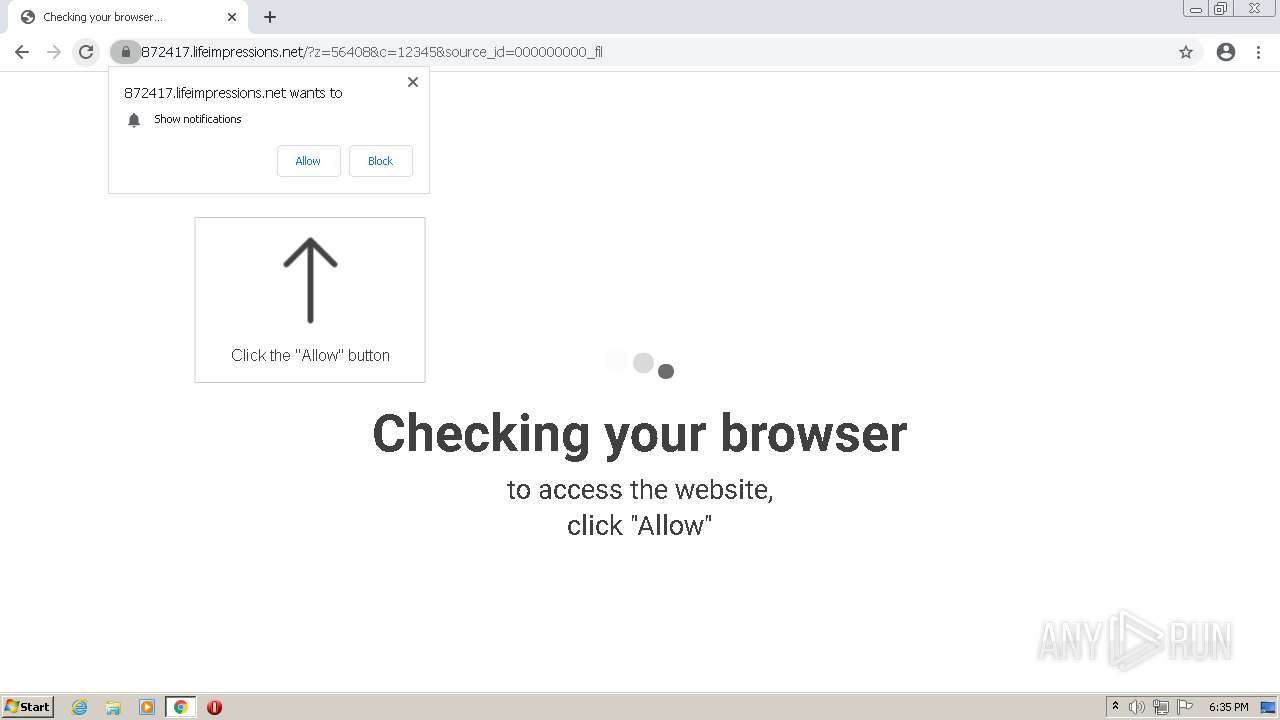
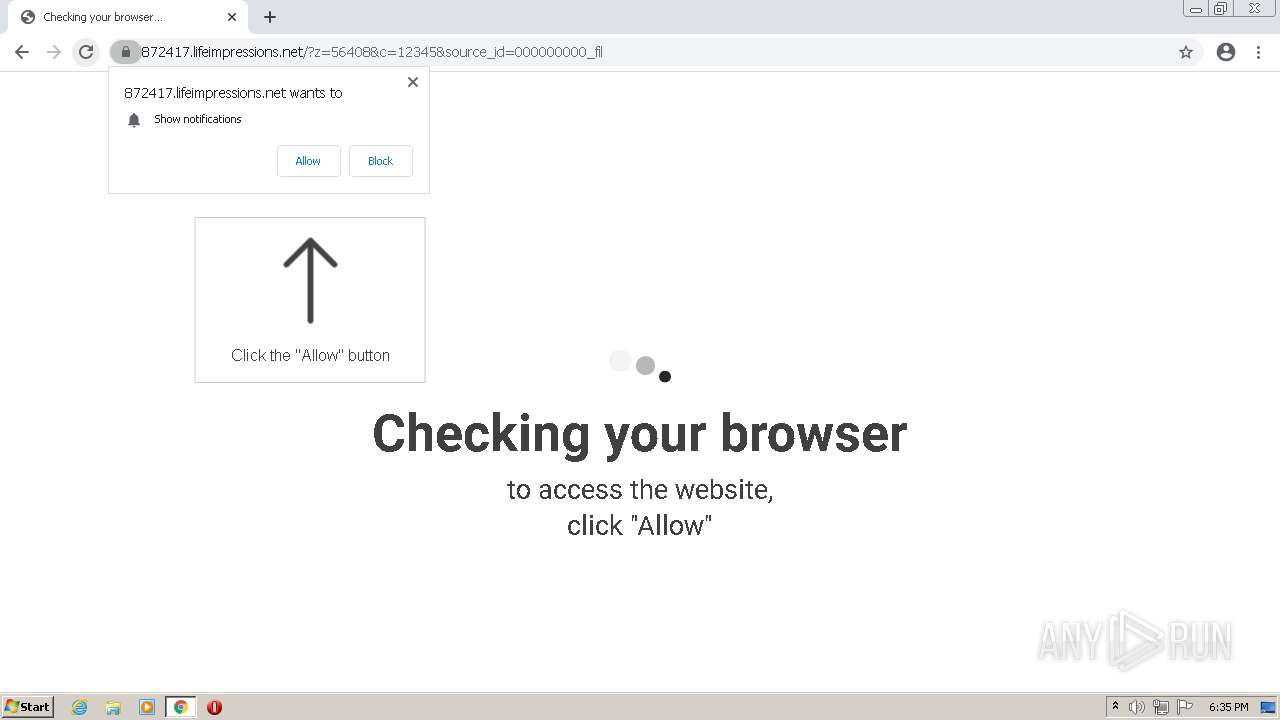
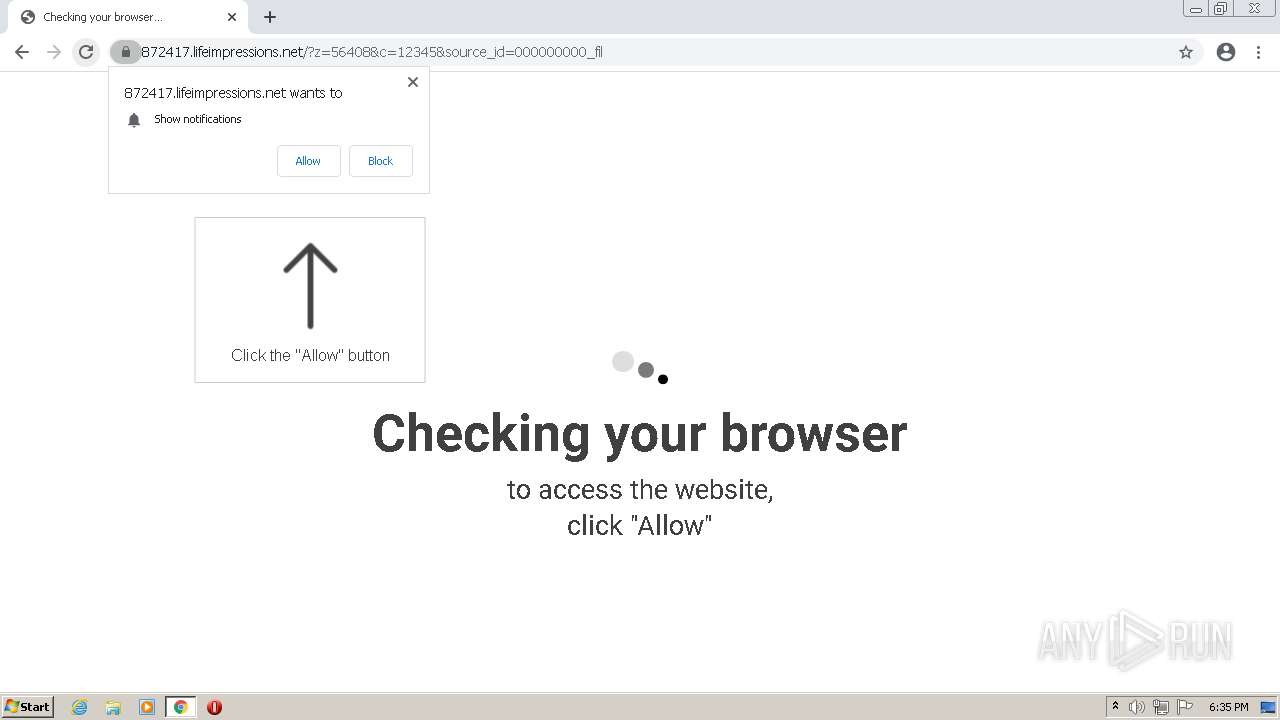
| URL: | http://clkv4.extyoneplus-2.com/click?i\=DXQ3fOGSo*I_0 |
| Full analysis: | https://app.any.run/tasks/165b394e-3333-4775-92c3-1ec2048bf458 |
| Verdict: | Malicious activity |
| Analysis date: | February 14, 2022, 18:32:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 36B82CD163DFD0602EB55BD4EE948E47 |
| SHA1: | F85D1297A9BFDEDD576CC483CB22BFFA9BD9DFF2 |
| SHA256: | 5A2926BEE321ED0DC2CD22CBA57C183B77FBBA271253B9EC518D79F45F3C7E1D |
| SSDEEP: | 3:N1KdJOTRxK0jO2dJMkL9g6V:C4RPbdJMI9g+ |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Checks supported languages
- chrome.exe (PID: 3560)
- chrome.exe (PID: 3352)
- chrome.exe (PID: 1532)
- chrome.exe (PID: 3616)
- chrome.exe (PID: 3680)
- chrome.exe (PID: 2784)
- chrome.exe (PID: 972)
- chrome.exe (PID: 2732)
- chrome.exe (PID: 2736)
- chrome.exe (PID: 2184)
- chrome.exe (PID: 2148)
- chrome.exe (PID: 2752)
- chrome.exe (PID: 3132)
- chrome.exe (PID: 1980)
- chrome.exe (PID: 1048)
- chrome.exe (PID: 2916)
- chrome.exe (PID: 3360)
- chrome.exe (PID: 2828)
- chrome.exe (PID: 1132)
- chrome.exe (PID: 3812)
- chrome.exe (PID: 3888)
- chrome.exe (PID: 3796)
- chrome.exe (PID: 1816)
- chrome.exe (PID: 2616)
- chrome.exe (PID: 3988)
- chrome.exe (PID: 2924)
- chrome.exe (PID: 3552)
Reads the computer name
- chrome.exe (PID: 3560)
- chrome.exe (PID: 3352)
- chrome.exe (PID: 3616)
- chrome.exe (PID: 2732)
- chrome.exe (PID: 2736)
- chrome.exe (PID: 2184)
- chrome.exe (PID: 2828)
- chrome.exe (PID: 1980)
- chrome.exe (PID: 2916)
Reads the hosts file
- chrome.exe (PID: 3616)
- chrome.exe (PID: 3560)
Reads settings of System Certificates
- chrome.exe (PID: 3616)
Application launched itself
- chrome.exe (PID: 3560)
Reads the date of Windows installation
- chrome.exe (PID: 2828)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
63
Monitored processes
27
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 972 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,8488715243025668231,18249990012085048492,131072 --enable-features=PasswordImport --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2164 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 | ||||
| 1048 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,8488715243025668231,18249990012085048492,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1544 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 | ||||
| 1132 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1044,8488715243025668231,18249990012085048492,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1648 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 | ||||
| 1532 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,8488715243025668231,18249990012085048492,131072 --enable-features=PasswordImport --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1856 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 | ||||
| 1816 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1044,8488715243025668231,18249990012085048492,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1496 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 | ||||
| 1980 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1044,8488715243025668231,18249990012085048492,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1544 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 | ||||
| 2148 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,8488715243025668231,18249990012085048492,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2716 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 | ||||
| 2184 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1044,8488715243025668231,18249990012085048492,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3188 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 | ||||
| 2616 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1044,8488715243025668231,18249990012085048492,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1492 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 | ||||
| 2732 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1044,8488715243025668231,18249990012085048492,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgACAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --use-gl=swiftshader-webgl --mojo-platform-channel-handle=1068 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
144
Text files
149
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3560 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-620AA032-DE8.pma | — | |
MD5:— | SHA256:— | |||
| 3560 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\201890b3-1ca0-423f-9f5b-8c39e625b172.tmp | text | |
MD5:— | SHA256:— | |||
| 3560 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Preferences | text | |
MD5:— | SHA256:— | |||
| 3560 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 3560 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:00046F773EFDD3C8F8F6D0F87A2B93DC | SHA256:593EDE11D17AF7F016828068BCA2E93CF240417563FB06DC8A579110AEF81731 | |||
| 3560 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:5BD3C311F2136A7A88D3E197E55CF902 | SHA256:FA331915E1797E59979A3E4BCC2BD0D3DEAA039B94D4DB992BE251FD02A224B9 | |||
| 3560 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RFe2c5b.TMP | text | |
MD5:64AD8ED3E666540337BA541C549F72F7 | SHA256:BECBDB08B5B37D203A85F2E974407334053BB1D2270F0B3C9A4DB963896F2206 | |||
| 3560 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:8FF312A95D60ED89857FEB720D80D4E1 | SHA256:946A57FAFDD28C3164D5AB8AB4971B21BD5EC5BFFF7554DBF832CB58CC37700B | |||
| 3680 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\CrashpadMetrics.pma | binary | |
MD5:03C4F648043A88675A920425D824E1B3 | SHA256:F91DBB7C64B4582F529C968C480D2DCE1C8727390482F31E4355A27BB3D9B450 | |||
| 3560 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RFe2c3c.TMP | text | |
MD5:936EB7280DA791E6DD28EF3A9B46D39C | SHA256:CBAF2AFD831B32F6D1C12337EE5D2F090D6AE1F4DCB40B08BEF49BF52AD9721F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
62
TCP/UDP connections
71
DNS requests
35
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3616 | chrome.exe | GET | 302 | 173.239.53.32:80 | http://xml.pdn-1.com/redirect?feed=157699&auth=WTnlA6&subid=pushredirect_new&query=push | US | — | — | malicious |
3616 | chrome.exe | GET | 302 | 173.239.53.32:80 | http://clkv4.extyoneplus-2.com/click?i\=DXQ3fOGSo*I_0 | US | — | — | suspicious |
872 | svchost.exe | HEAD | 200 | 74.125.153.202:80 | http://r5---sn-4g5edn6r.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOGMyQUFYUjhaZkNqaEUyZDFCRWM2S3dUZw/1.0.0.11_llkgjffcdpffmhiakmfcdcblohccpfmo.crx?cms_redirect=yes&mh=mM&mip=45.132.226.184&mm=28&mn=sn-4g5edn6r&ms=nvh&mt=1644863298&mv=m&mvi=5&pl=25&rmhost=r1---sn-4g5edn6r.gvt1.com&shardbypass=yes&smhost=r1---sn-4g5ednld.gvt1.com | US | — | — | whitelisted |
3616 | chrome.exe | GET | 302 | 173.239.53.32:80 | http://xml.pdn-1.com/redirect?feed=157699&auth=WTnlA6&subid=pushredirect_new&query=push | US | — | — | malicious |
872 | svchost.exe | HEAD | 200 | 74.125.162.167:80 | http://r2---sn-4g5edndl.gvt1.com/edgedl/release2/chrome_component/adktovjj3t3n7jwiiegl5h6y3v5q_1.3.36.121/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.121_win_bxugoraqoudfswxg22hsatfdbi.crx3?cms_redirect=yes&mh=bj&mip=45.132.226.184&mm=28&mn=sn-4g5edndl&ms=nvh&mt=1644863298&mv=m&mvi=2&pl=25&rmhost=r3---sn-4g5edndl.gvt1.com&shardbypass=yes&smhost=r3---sn-4g5edn6r.gvt1.com | US | — | — | whitelisted |
3616 | chrome.exe | GET | 302 | 173.239.53.32:80 | http://xml.pdn-1.com/redirect?feed=157699&auth=WTnlA6&subid=pushredirect_new&query=push | US | — | — | malicious |
872 | svchost.exe | HEAD | 302 | 142.250.185.142:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOGMyQUFYUjhaZkNqaEUyZDFCRWM2S3dUZw/1.0.0.11_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | US | — | — | whitelisted |
872 | svchost.exe | GET | 200 | 74.125.153.202:80 | http://r5---sn-4g5edn6r.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOGMyQUFYUjhaZkNqaEUyZDFCRWM2S3dUZw/1.0.0.11_llkgjffcdpffmhiakmfcdcblohccpfmo.crx?cms_redirect=yes&mh=mM&mip=45.132.226.184&mm=28&mn=sn-4g5edn6r&ms=nvh&mt=1644863298&mv=m&mvi=5&pl=25&rmhost=r1---sn-4g5edn6r.gvt1.com&shardbypass=yes&smhost=r1---sn-4g5ednld.gvt1.com | US | crx | 2.80 Kb | whitelisted |
872 | svchost.exe | HEAD | 302 | 142.250.185.142:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/adktovjj3t3n7jwiiegl5h6y3v5q_1.3.36.121/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.121_win_bxugoraqoudfswxg22hsatfdbi.crx3 | US | html | 595 b | whitelisted |
872 | svchost.exe | GET | 302 | 142.250.185.142:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOGMyQUFYUjhaZkNqaEUyZDFCRWM2S3dUZw/1.0.0.11_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | US | html | 595 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3616 | chrome.exe | 142.250.185.173:443 | accounts.google.com | Google Inc. | US | suspicious |
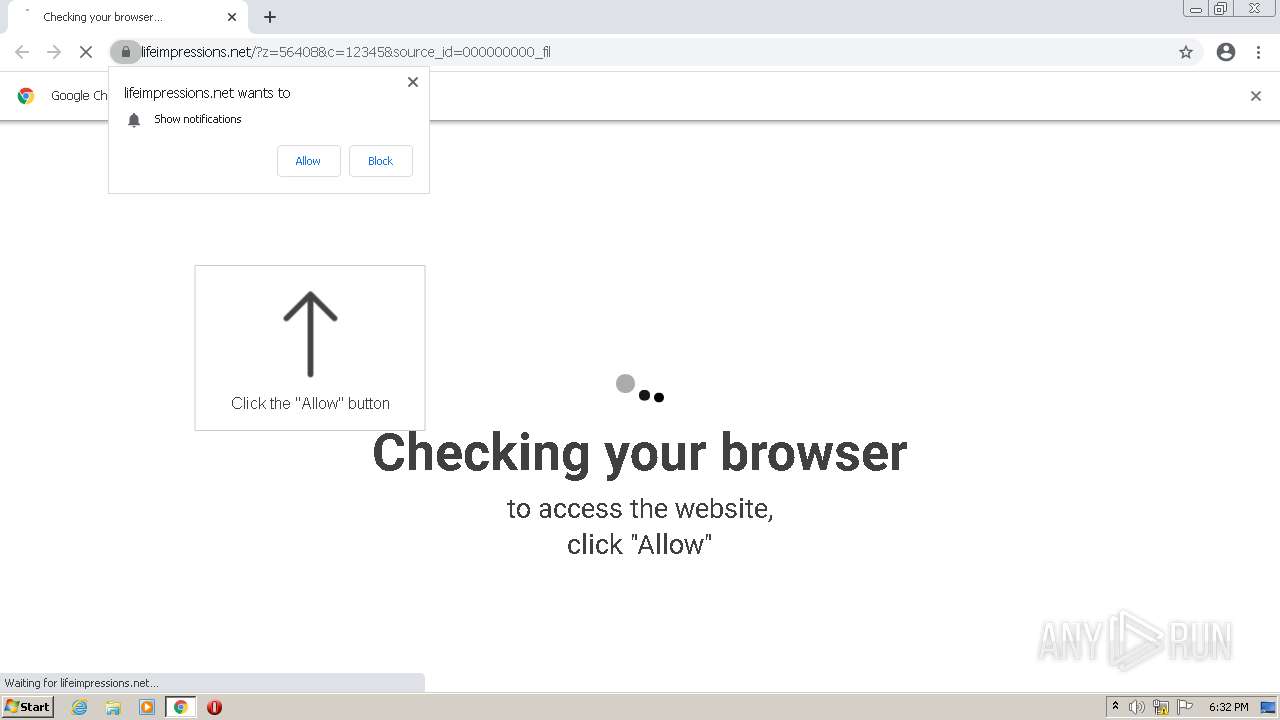
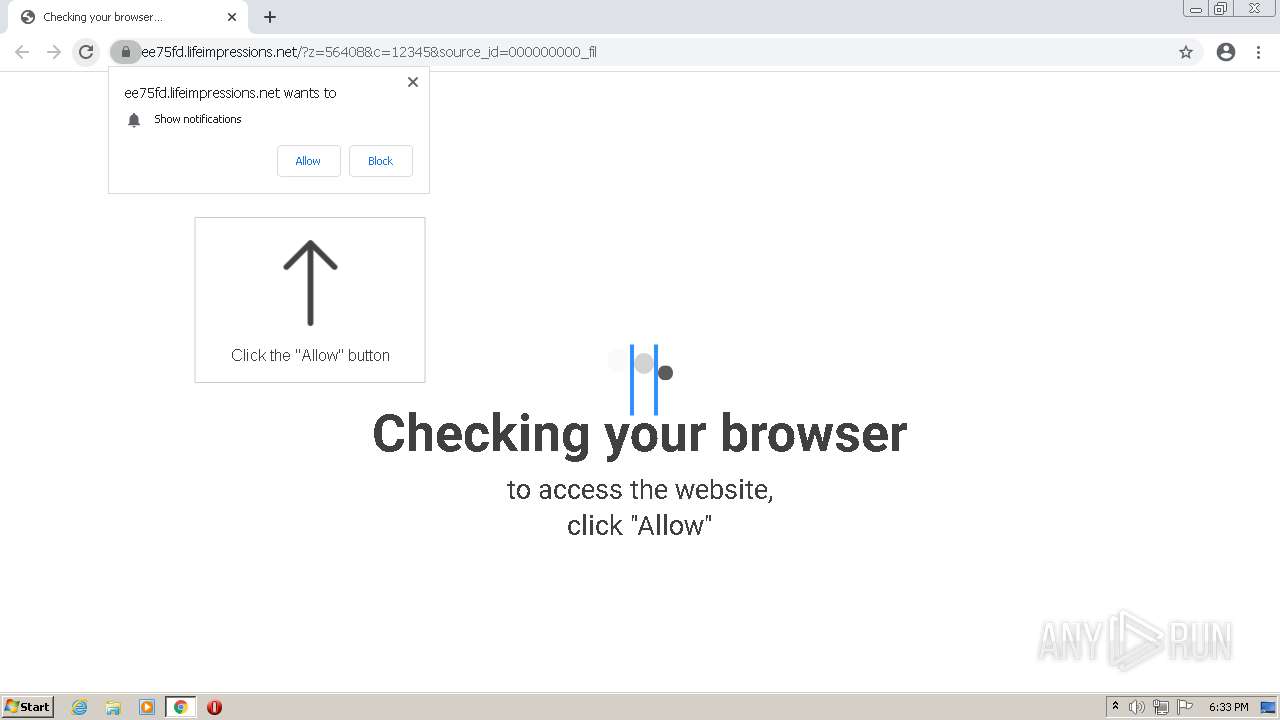
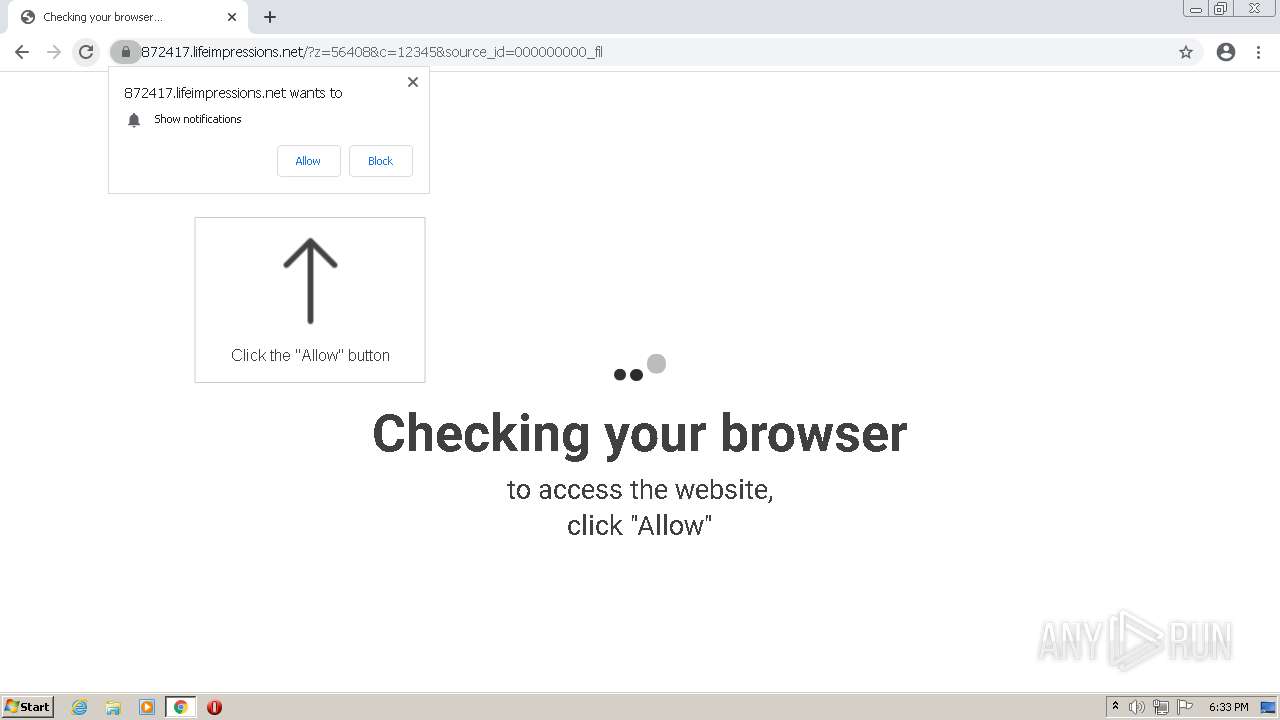
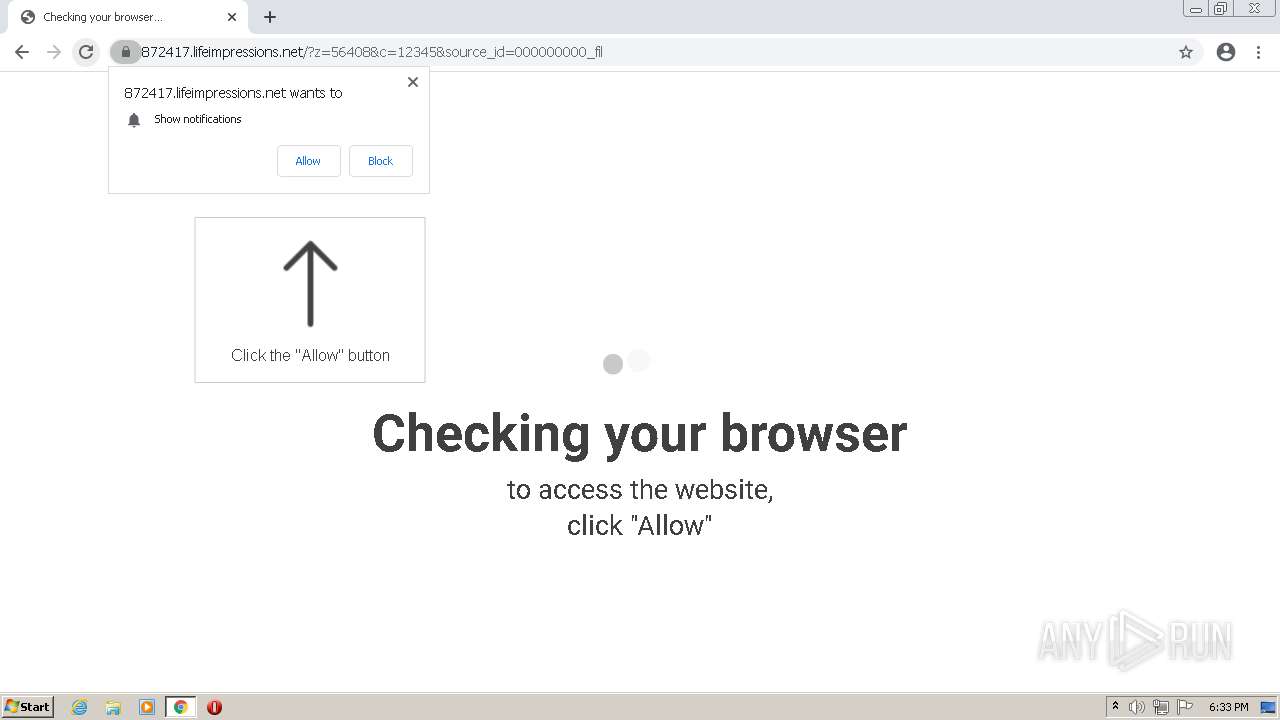
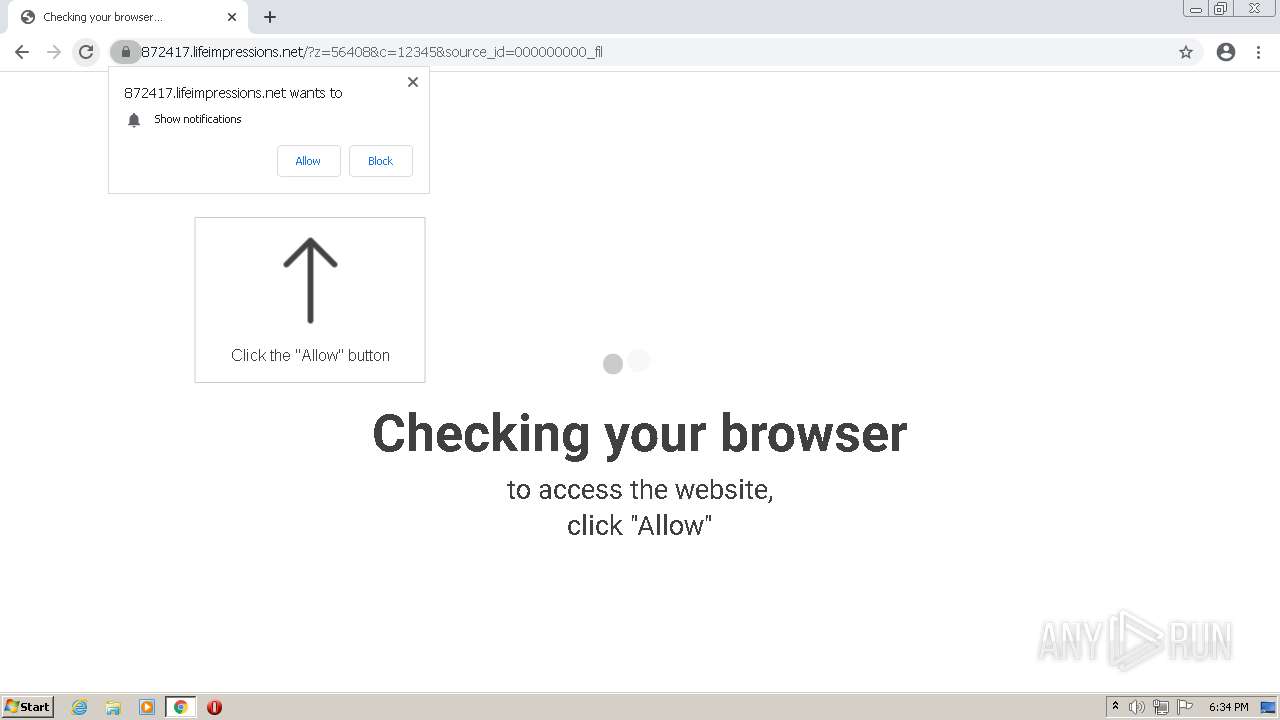
— | — | 178.128.246.195:443 | lifeimpressions.net | Forthnet | GR | suspicious |
3616 | chrome.exe | 142.250.186.131:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3616 | chrome.exe | 69.16.175.42:443 | code.jquery.com | Highwinds Network Group, Inc. | US | malicious |
— | — | 142.250.74.202:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3616 | chrome.exe | 172.217.23.104:443 | www.googletagmanager.com | Google Inc. | US | suspicious |
— | — | 142.250.186.110:443 | clients2.google.com | Google Inc. | US | whitelisted |
3616 | chrome.exe | 69.16.175.10:443 | code.jquery.com | Highwinds Network Group, Inc. | US | malicious |
3616 | chrome.exe | 216.239.36.55:443 | fcm.googleapis.com | Google Inc. | US | unknown |
872 | svchost.exe | 142.250.185.142:80 | redirector.gvt1.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clients2.google.com |
| whitelisted |
accounts.google.com |
| shared |
clkv4.extyoneplus-2.com |
| suspicious |
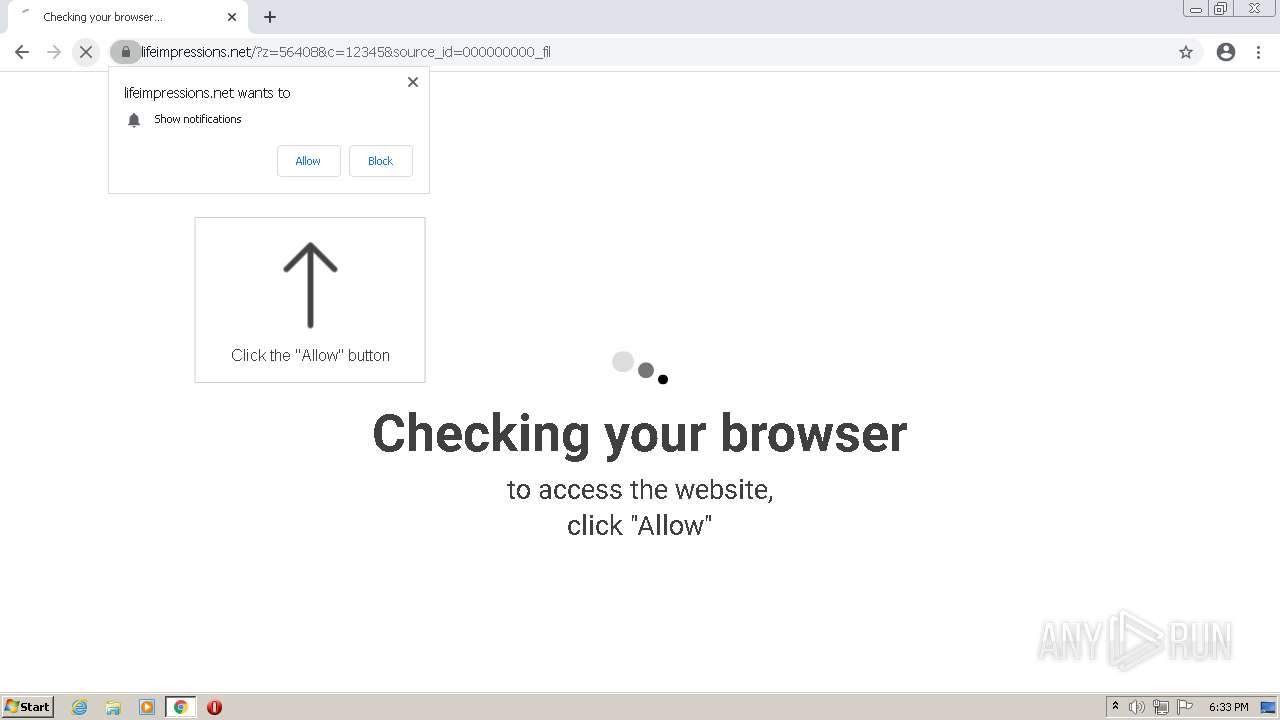
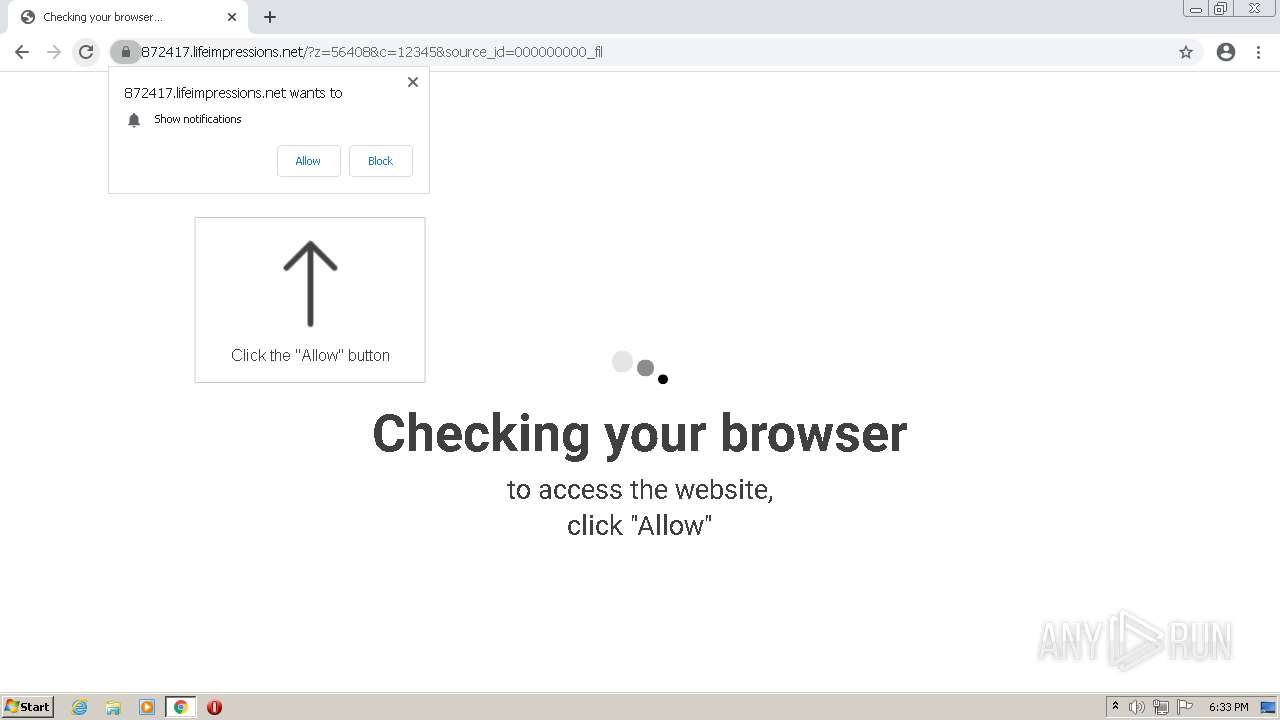
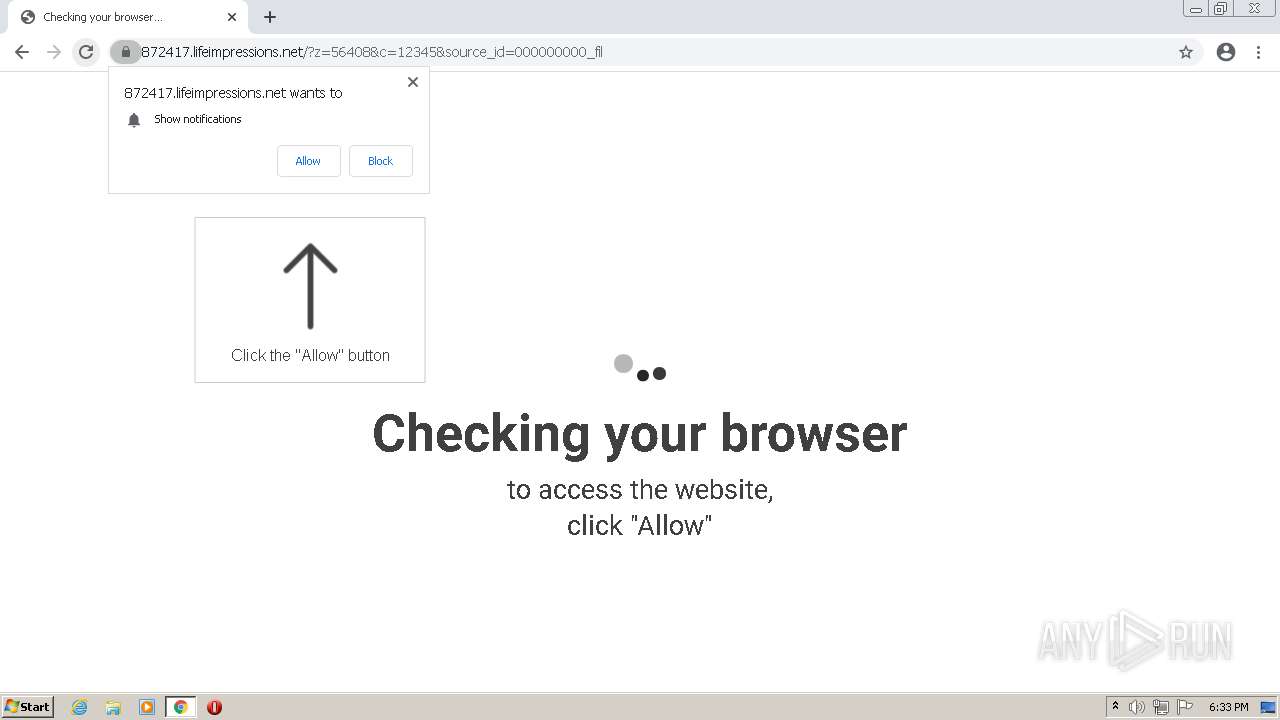
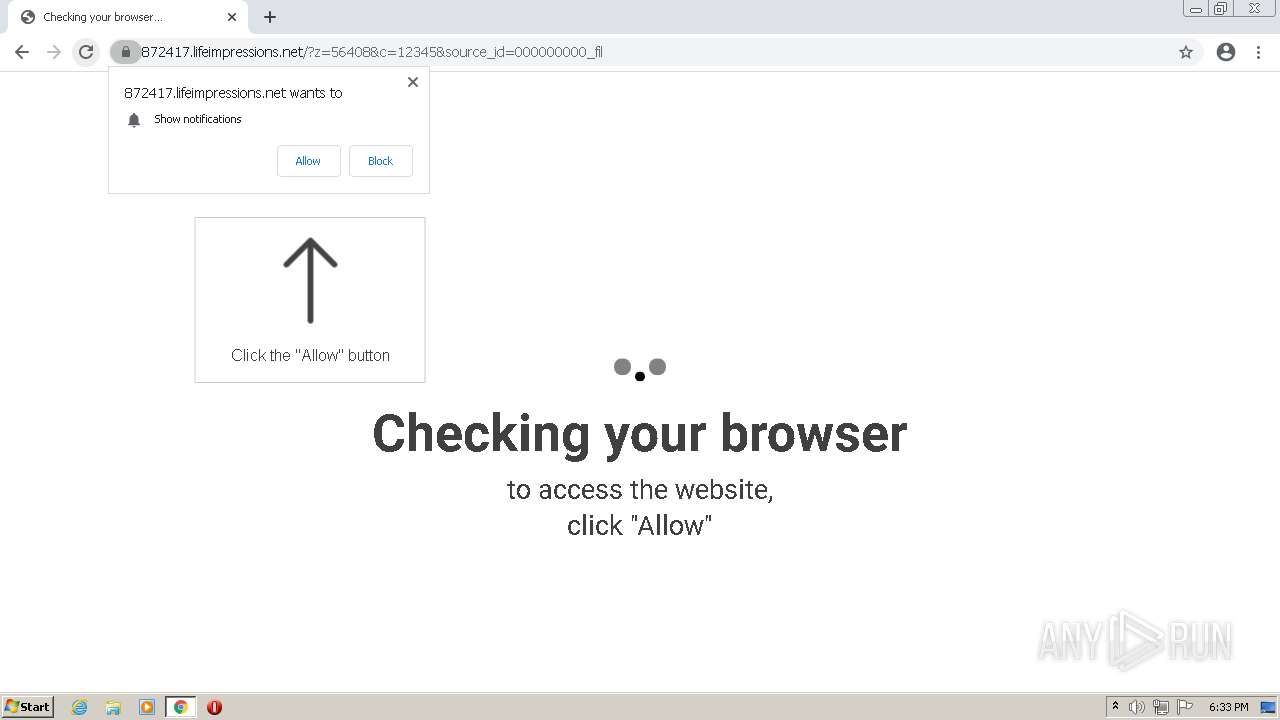
lifeimpressions.net |
| malicious |
www.gstatic.com |
| whitelisted |
code.jquery.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |