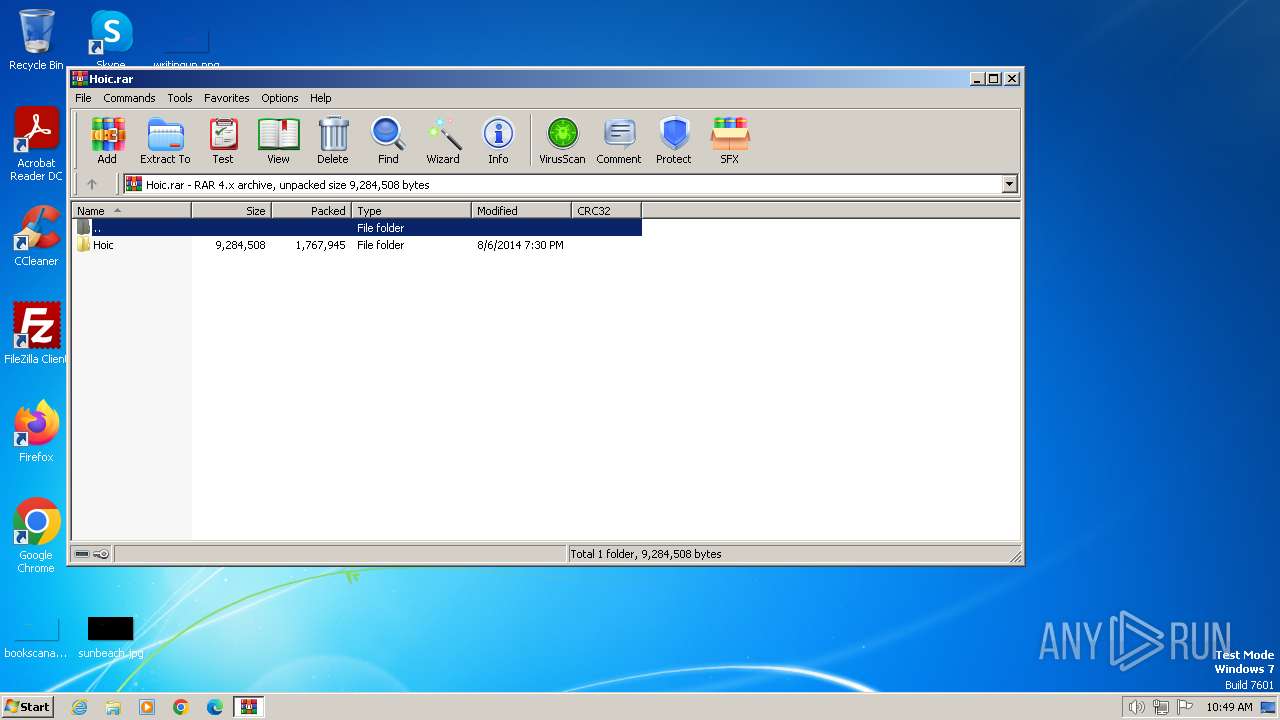
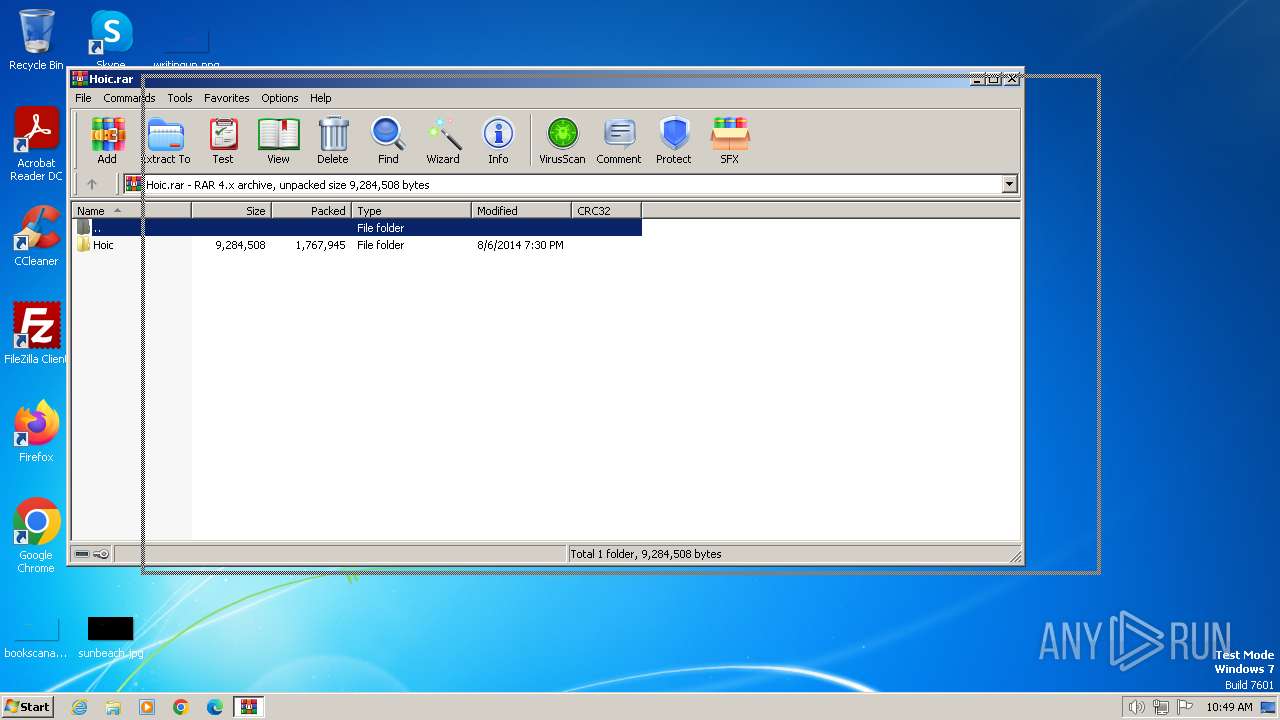
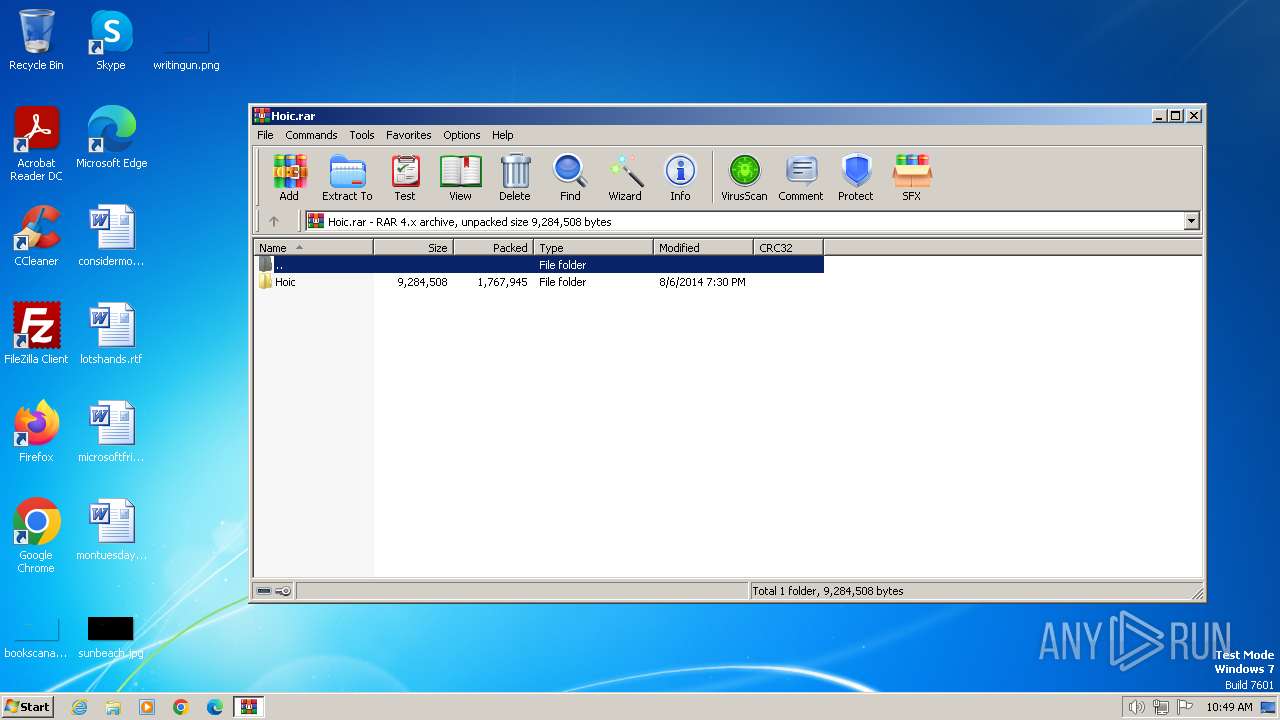
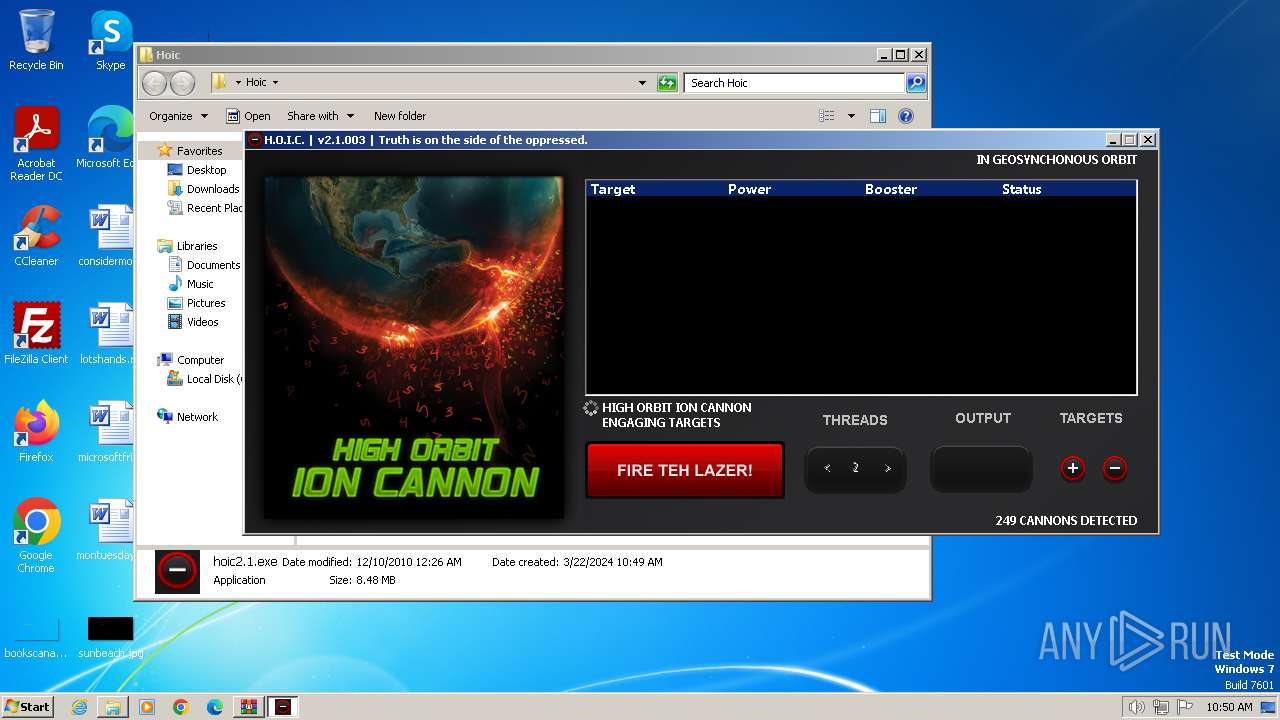
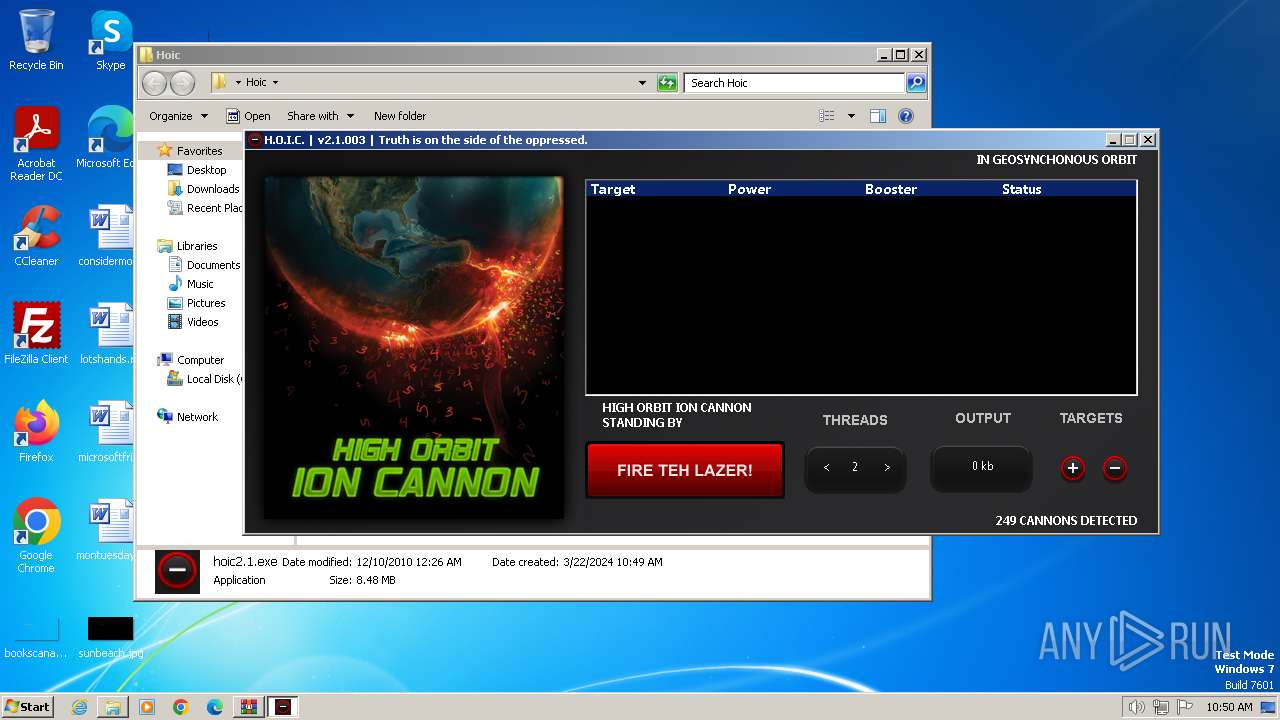
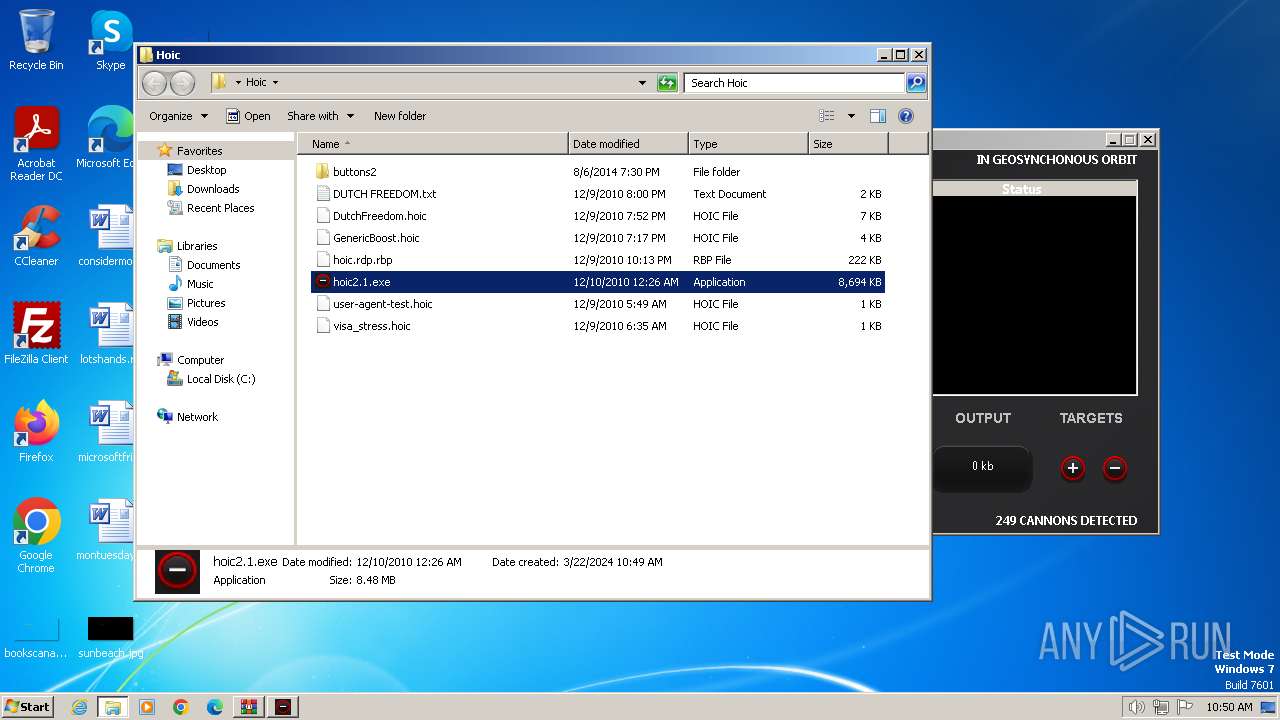
| File name: | Hoic.rar |
| Full analysis: | https://app.any.run/tasks/4eb4015b-fe70-43c9-9bc1-266729894aaa |
| Verdict: | Malicious activity |
| Analysis date: | March 22, 2024, 10:49:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | BA60FE26A85D5F5B6338D562930AEFF2 |
| SHA1: | 499B6643DD5A7F1DD4D57506041C1207E657BCE0 |
| SHA256: | 59E0D15FCDF92551A204C7E71776A88F54EA9DF74E2BA2CFB04E7582C04DEC81 |
| SSDEEP: | 49152:YQs04R8oXUEgIRnwN/INLZw8NoibprkwSIdwHQa:zSRYfNANLZw8NLbZudh |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3500)
SUSPICIOUS
Connects to the server without a host name
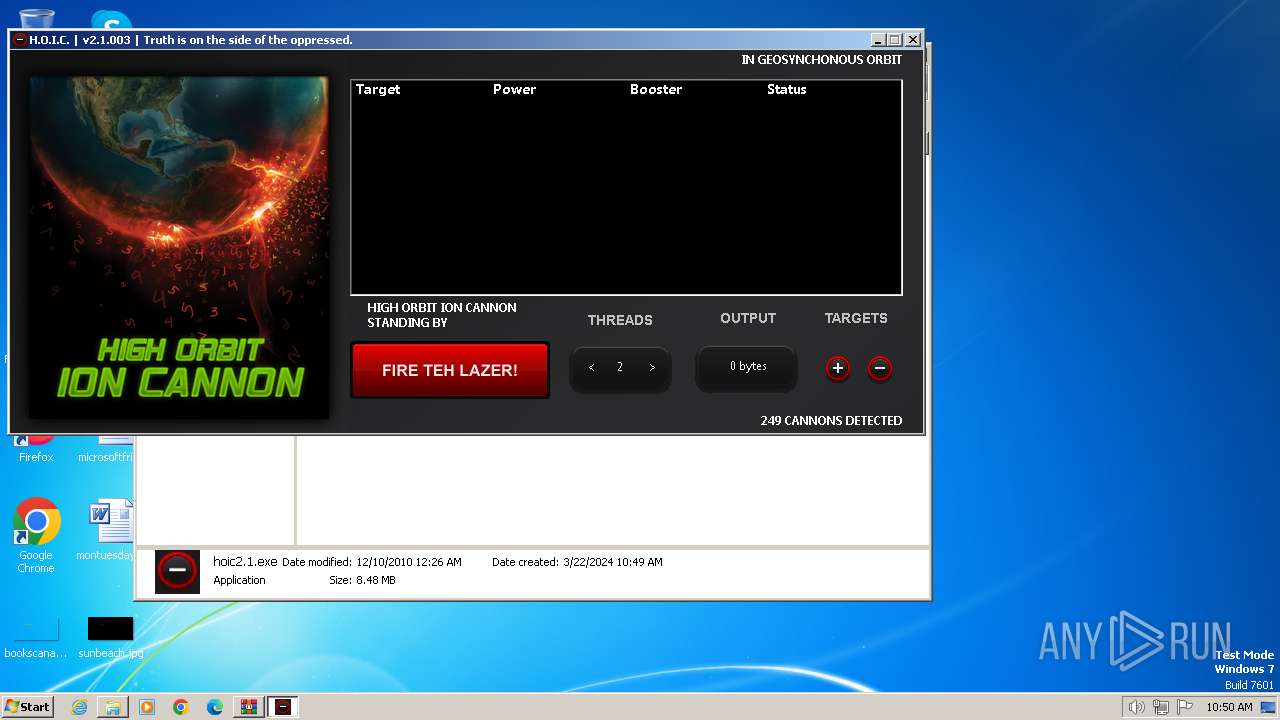
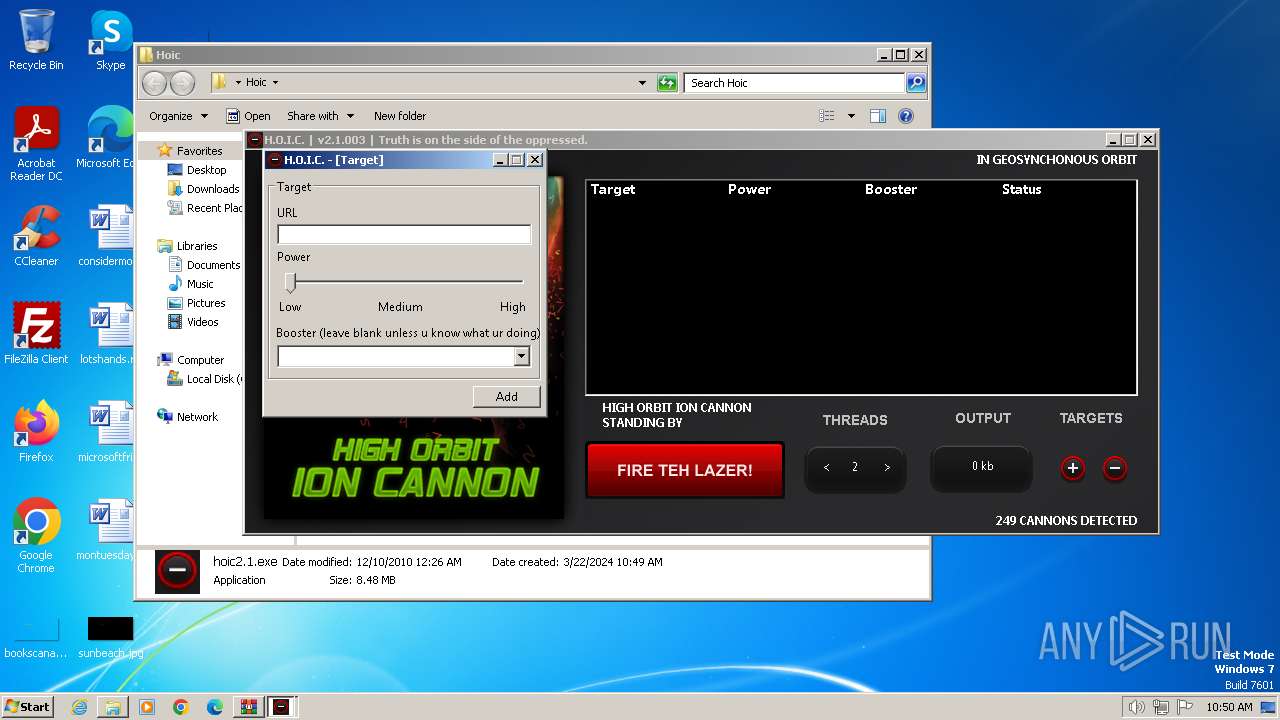
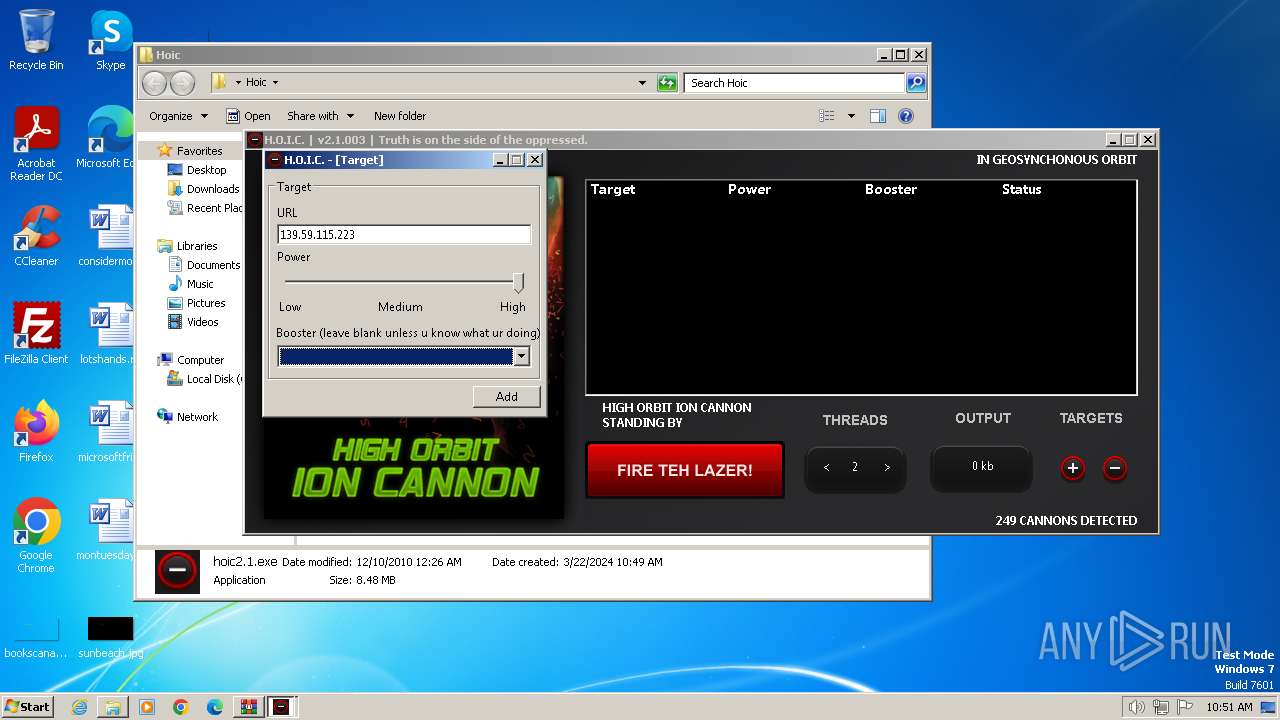
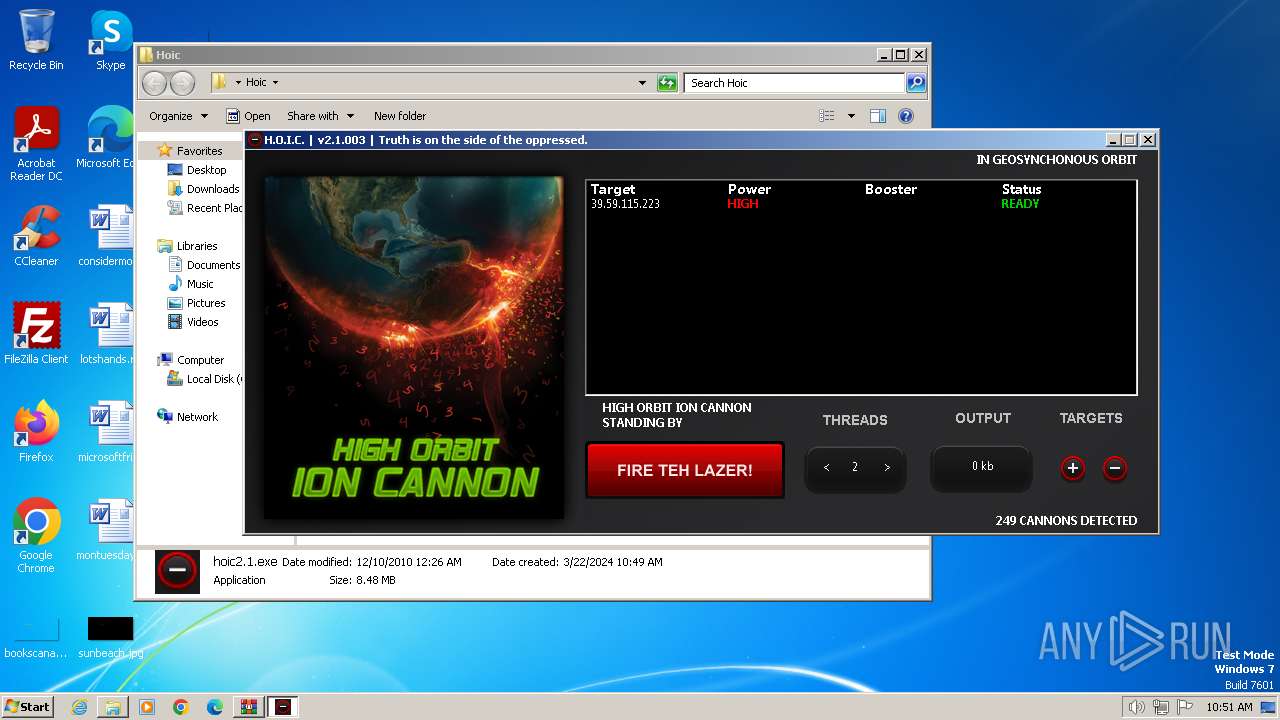
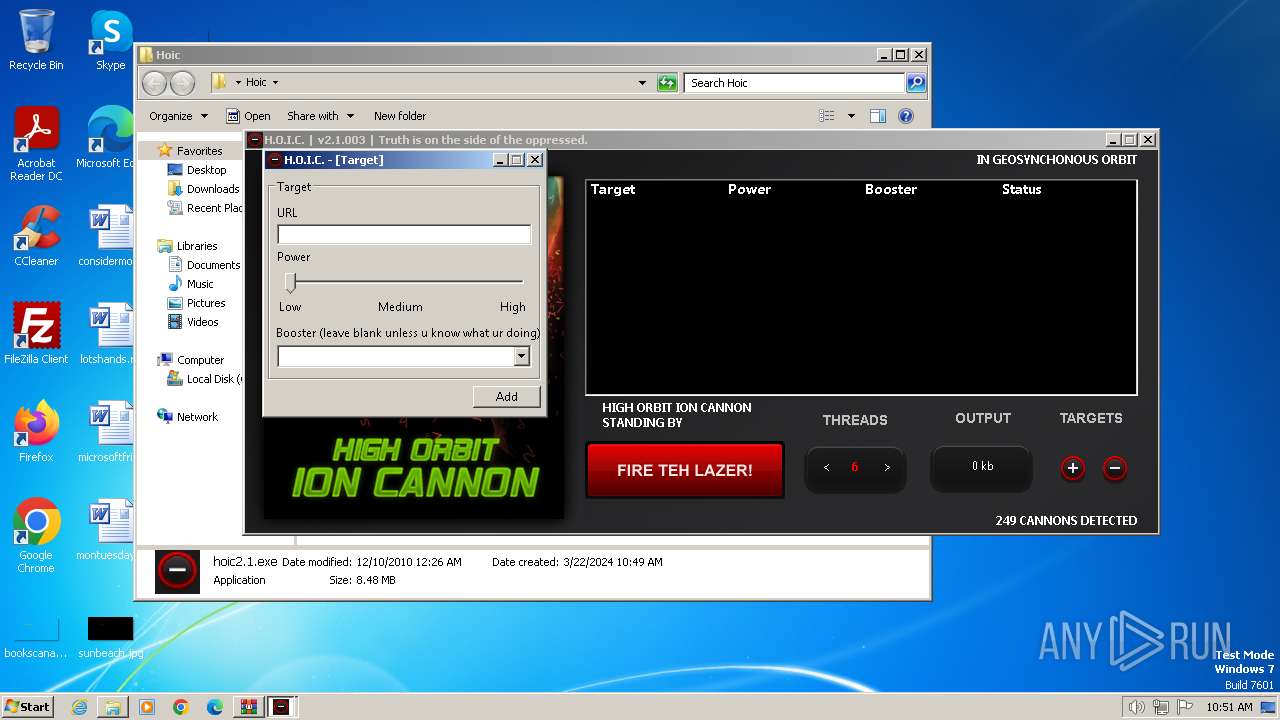
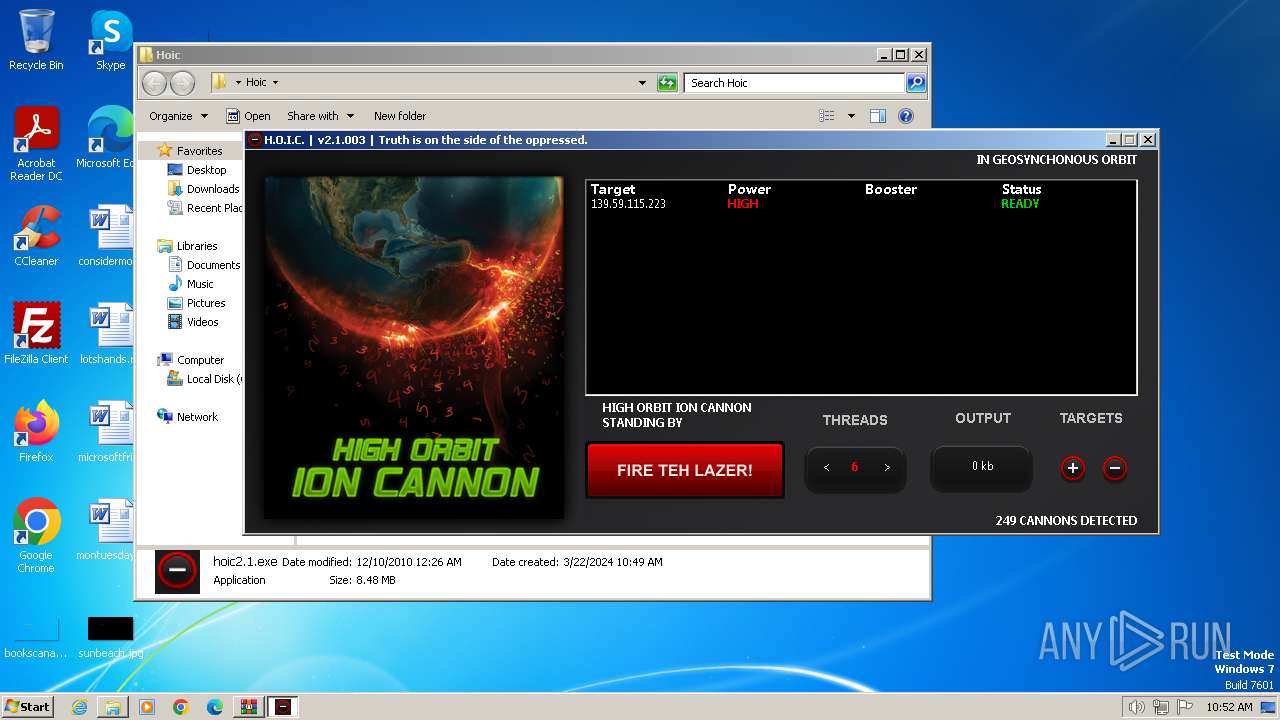
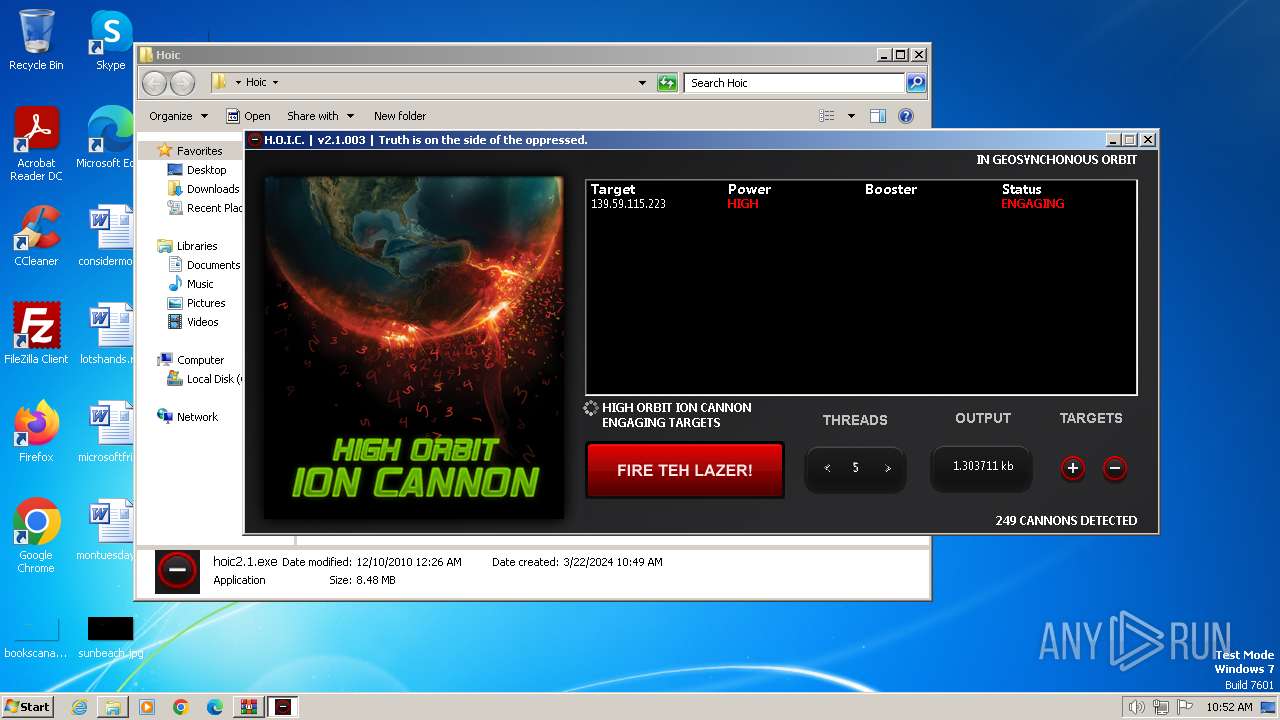
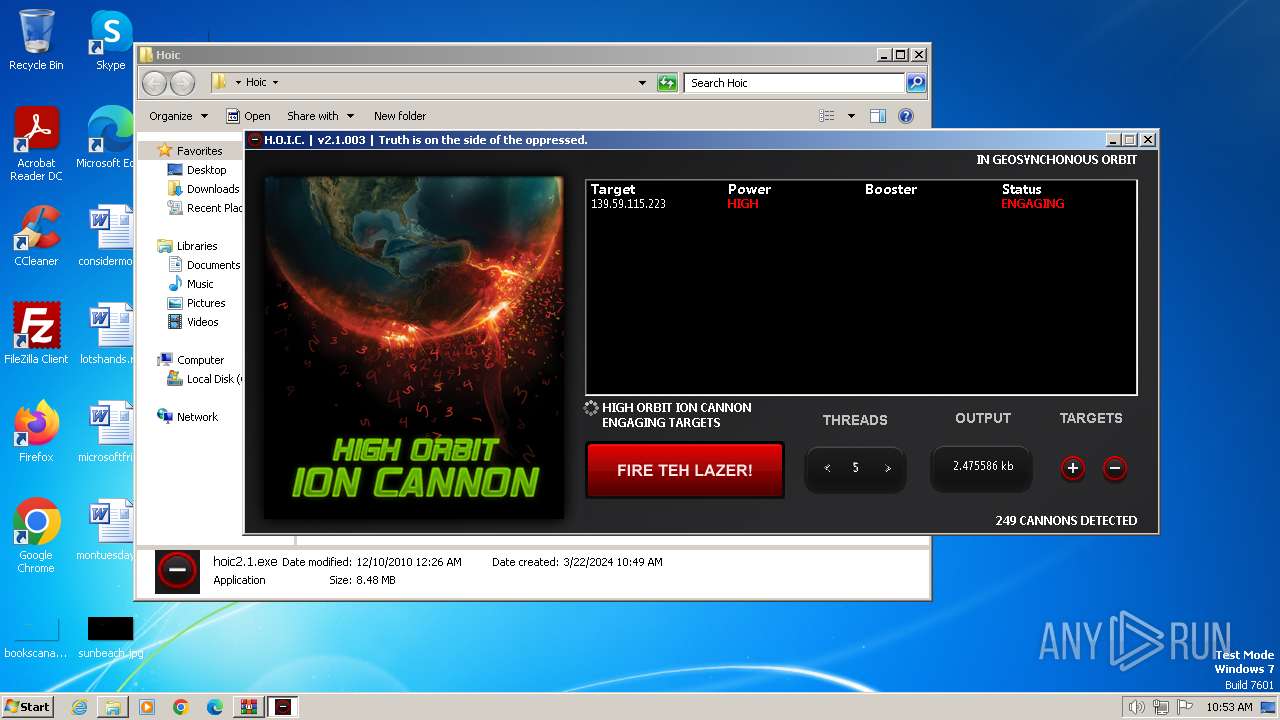
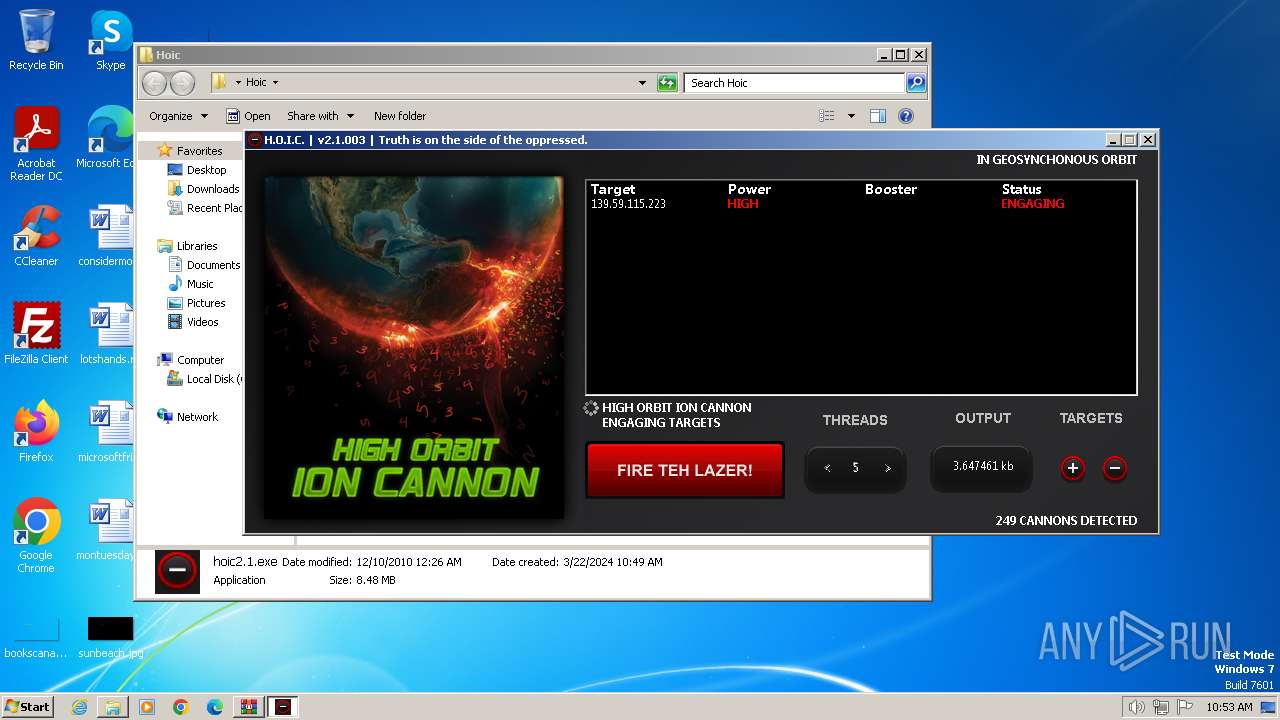
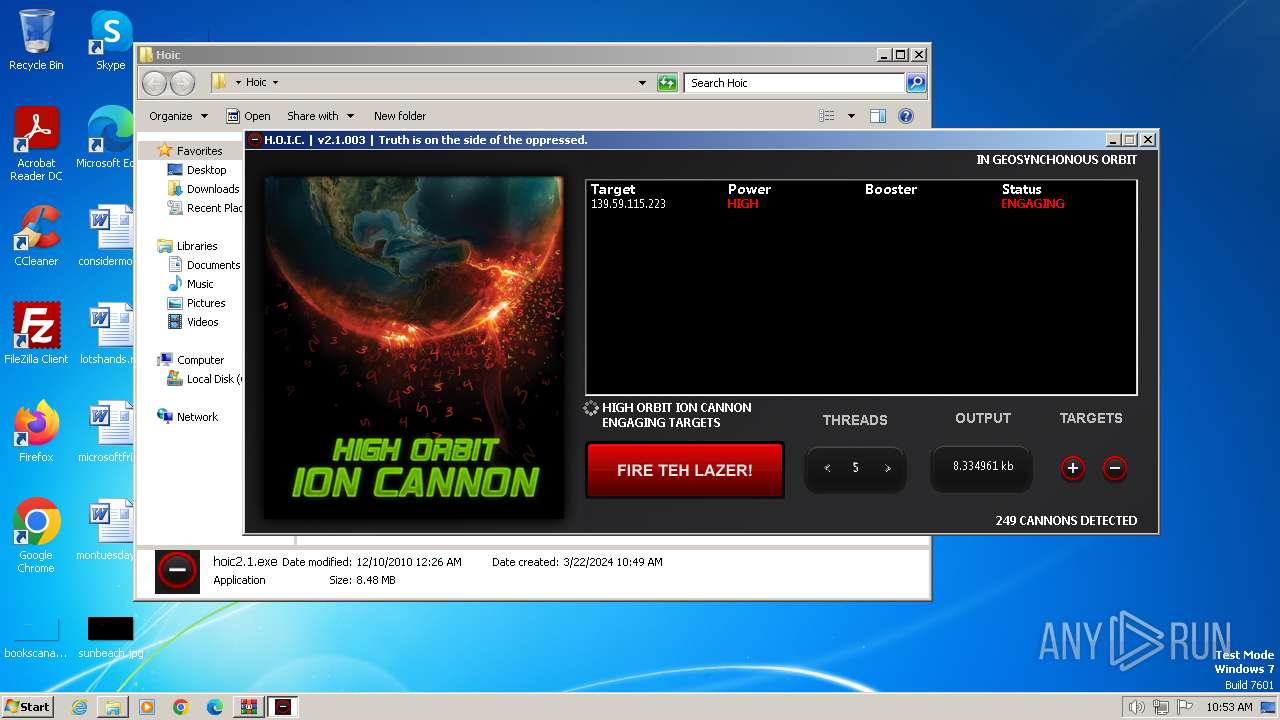
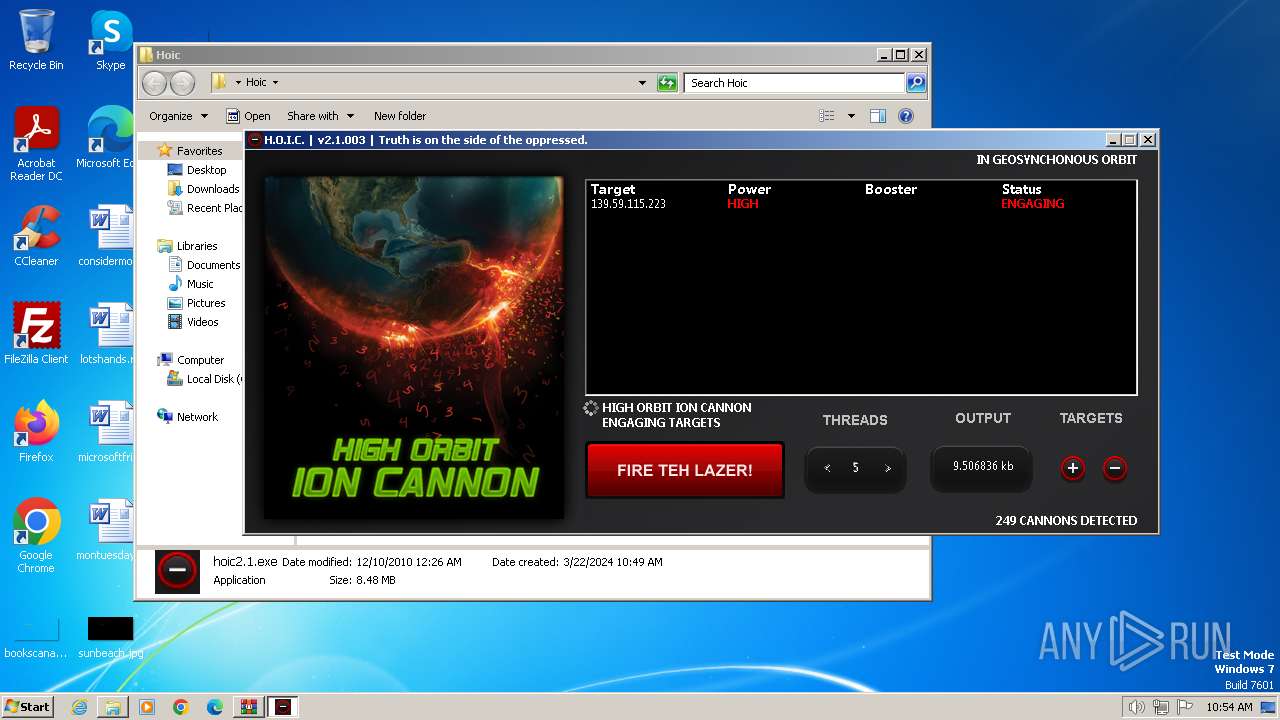
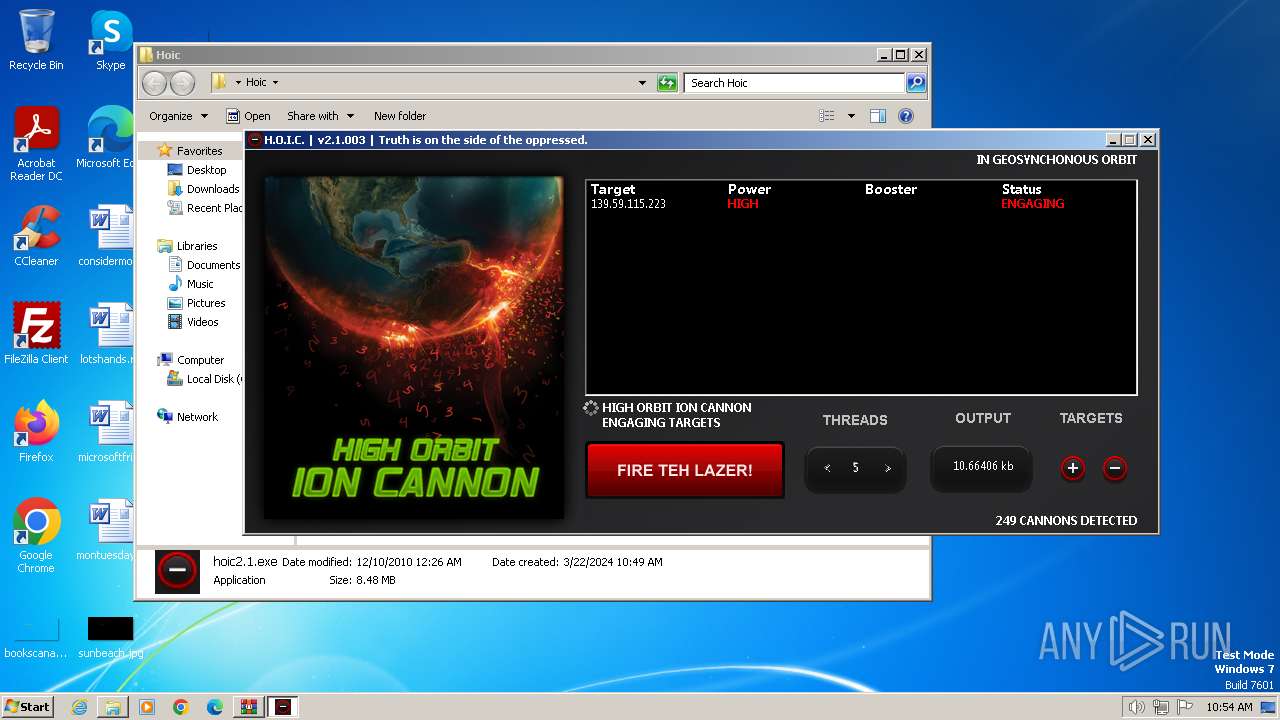
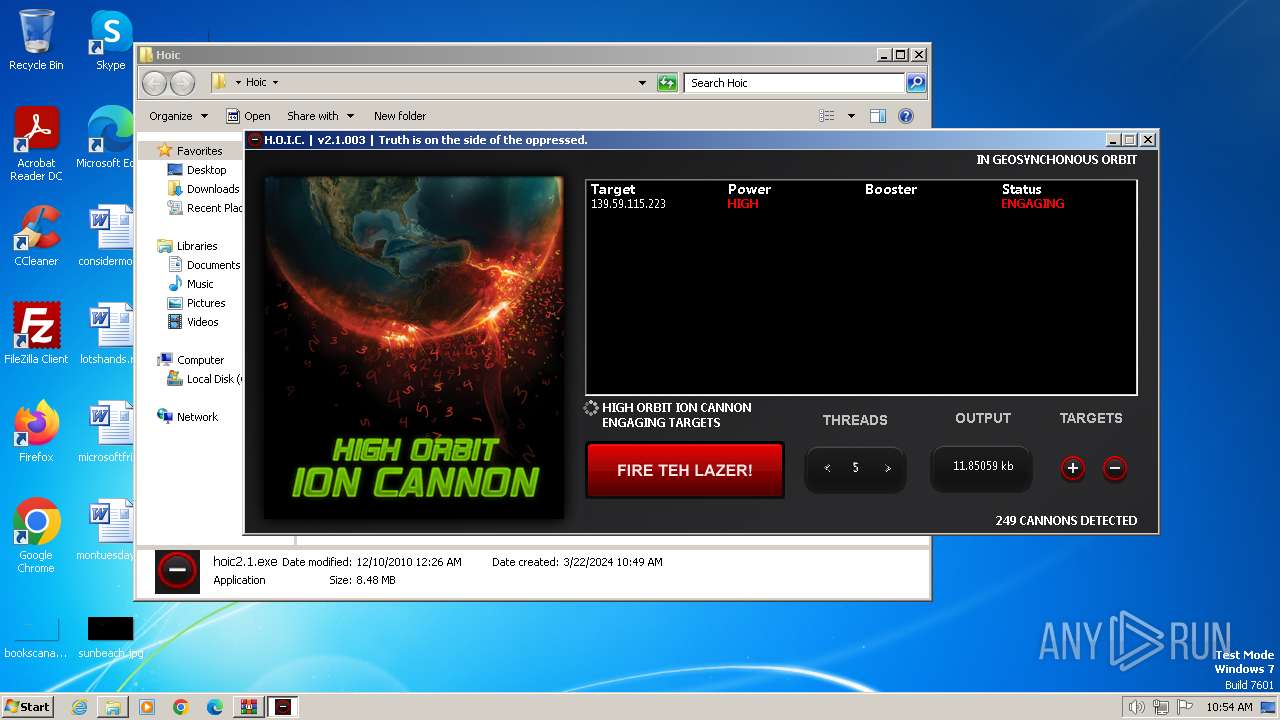
- hoic2.1.exe (PID: 3996)
INFO
Checks supported languages
- hoic2.1.exe (PID: 3996)
Manual execution by a user
- hoic2.1.exe (PID: 3996)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3500)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 4091 |
|---|---|
| UncompressedSize: | 4040 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2010:12:09 03:32:12 |
| PackingMethod: | Stored |
| ArchivedFileName: | Hoic\buttons2\buttons\4add.png |
Total processes
38
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3500 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Hoic.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3996 | "C:\Users\admin\Desktop\Hoic\hoic2.1.exe" | C:\Users\admin\Desktop\Hoic\hoic2.1.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
3 805
Read events
3 791
Write events
14
Delete events
0
Modification events
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Hoic.rar | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
1
Suspicious files
2
Text files
24
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Hoic\buttons2\buttons\button.png | image | |
MD5:3E759A1FDC0A9CB94239284AF36AE651 | SHA256:F094C46AAB2663470C88BF883E8B641941DE70FF4D198C56A568D0EF74EEF94F | |||
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Hoic\buttons2\buttons\lazer.png | image | |
MD5:5DFC0A47F6309048AE3A68208685C3B8 | SHA256:4D9D71BFF3429CA055DFFF9DADE55CADA219C495153B51D8F1D7831B7C66ECB5 | |||
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Hoic\buttons2\buttons\remo4ve.png | image | |
MD5:1D1172A772171F24B0615E59442BD329 | SHA256:6931AA90EA0249BE54432FD47D7E702BD16FA89D96E6820D1D36C6BEAFB1B9D9 | |||
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Hoic\buttons2\buttons\add3.png | image | |
MD5:AE39F32971BA9B649E1E817C2CF61E8E | SHA256:A92E7C8347EE769A0A3D69866A7925C79E2AC885D14116DD882223B6D752572A | |||
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Hoic\buttons2\buttons\add.png | image | |
MD5:8ADE13213352F64D34E561D2E0A0F454 | SHA256:720EDC5F500B86904DA5161206834EE942D3B60040A856898BD95F61DA53B2DA | |||
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Hoic\buttons2\buttons\button4.png | image | |
MD5:01DCD72AB51E145129EC54CAE7CBF1E5 | SHA256:0CFC00FEE98B9E9560F2BF5EDA15F664FB8AD73343E1FE6E3F99AB3A8CE0DC34 | |||
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Hoic\buttons2\buttons\666.png | image | |
MD5:59FF8D3A3539122B35142116A3A8A0AC | SHA256:B40B057BF44E38C0C2B69CB78BE8E95AE40A0A20B2FAC826D5AAF97F931C660C | |||
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Hoic\buttons2\buttons\turbo.png | image | |
MD5:E8B3AC5DEBF7542E40526AEDCB02F90A | SHA256:485EE241F1DFDC80DA75D314F84CA7966E23FEB007BC51F0F2F595E9AFA4CFDD | |||
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Hoic\buttons2\buttons\Thumbs.db | binary | |
MD5:7268BE82981A13C3B024FBAB1A19E53B | SHA256:AC73249A057F9338FCA8DC5C50EDB7E3655AF708B2196E2F56C04CFD9C6D3773 | |||
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Hoic\buttons2\buttons\scripts.png | image | |
MD5:ED2D9AC71A3B1FD52877D43BFEC87ACA | SHA256:E68EACD0954A1043F2E3C5DACE4EC42BA5F0A3340D1CA898BAF46065DF6EFC74 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4 408
TCP/UDP connections
4 429
DNS requests
0
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3996 | hoic2.1.exe | GET | — | 139.59.115.223:80 | http://139.59.115.223/ | unknown | — | — | unknown |
3996 | hoic2.1.exe | GET | — | 139.59.115.223:80 | http://139.59.115.223/ | unknown | — | — | unknown |
3996 | hoic2.1.exe | GET | — | 139.59.115.223:80 | http://139.59.115.223/ | unknown | — | — | unknown |
3996 | hoic2.1.exe | GET | — | 139.59.115.223:80 | http://139.59.115.223/ | unknown | — | — | unknown |
3996 | hoic2.1.exe | GET | — | 139.59.115.223:80 | http://139.59.115.223/ | unknown | — | — | unknown |
3996 | hoic2.1.exe | GET | — | 139.59.115.223:80 | http://139.59.115.223/ | unknown | — | — | unknown |
3996 | hoic2.1.exe | GET | — | 139.59.115.223:80 | http://139.59.115.223/ | unknown | — | — | unknown |
3996 | hoic2.1.exe | GET | — | 139.59.115.223:80 | http://139.59.115.223/ | unknown | — | — | unknown |
3996 | hoic2.1.exe | GET | — | 139.59.115.223:80 | http://139.59.115.223/ | unknown | — | — | unknown |
3996 | hoic2.1.exe | GET | — | 139.59.115.223:80 | http://139.59.115.223/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3996 | hoic2.1.exe | 139.59.115.223:80 | — | DIGITALOCEAN-ASN | SG | unknown |