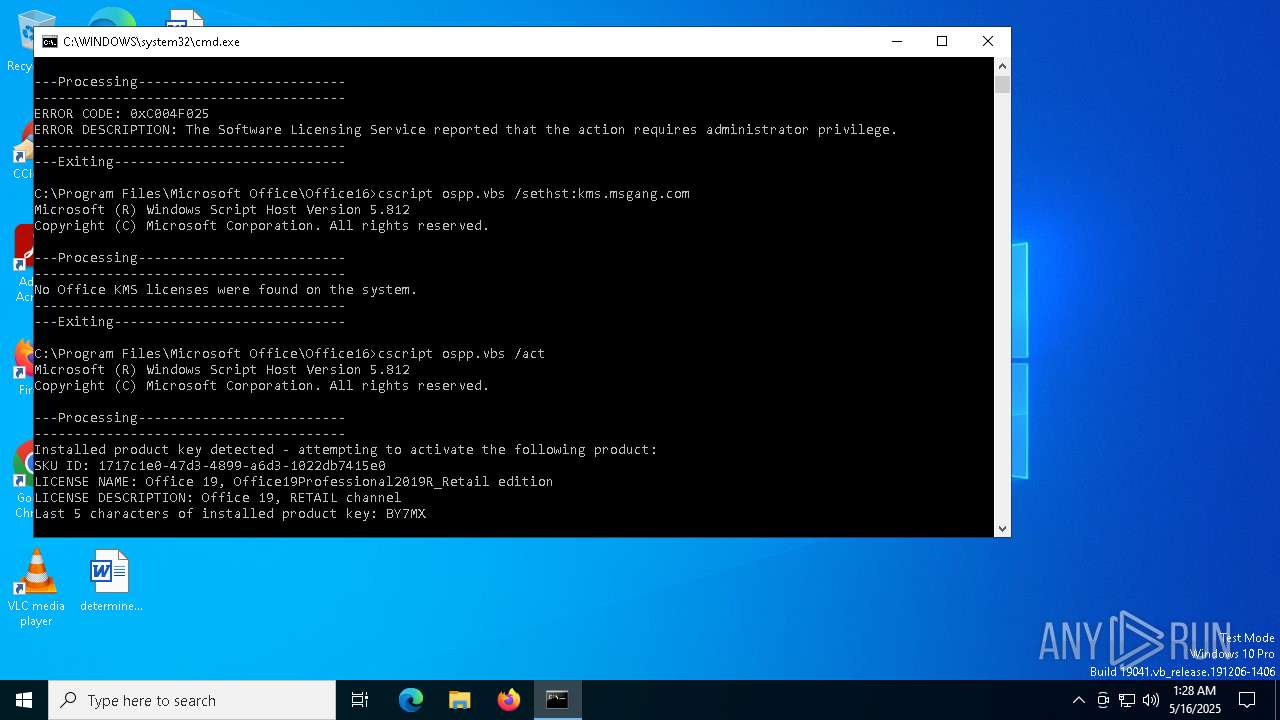
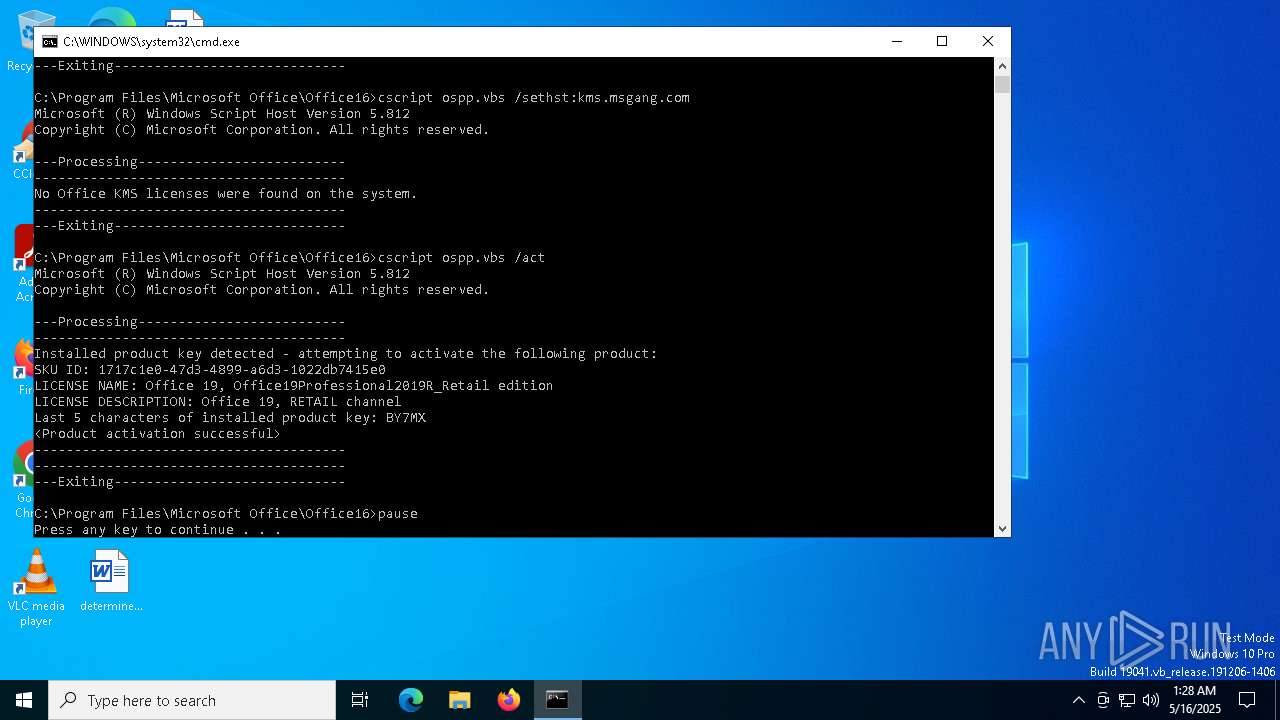
| File name: | oppsrearm.bat |
| Full analysis: | https://app.any.run/tasks/a1379aba-f7c6-46af-997c-05fc81ebab79 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 01:27:57 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | D9E30B6BAB33590A13AE8ACDB1609CDE |
| SHA1: | 24ADCC1184D45C47F6896480701E151F79FB98CF |
| SHA256: | 59DF9F5434B182C6F56CAD461BB9194FA323769F1D18374AF7B58476A2FF8497 |
| SSDEEP: | 6:C2g+Y0ED+9m5oeY0ER5oegoEVCFseZcV3mpMLWFiHHmpMLSNhBgt8SmpWrompEGA:u+Q+Yz+zMCFsMIhi4HhujBo8SHopGA |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts CMD.EXE for commands execution
- cmd.exe (PID: 4776)
The process executes VB scripts
- cmd.exe (PID: 4776)
Application launched itself
- cmd.exe (PID: 4776)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 7244)
- cscript.exe (PID: 7768)
- cscript.exe (PID: 8028)
- cscript.exe (PID: 3176)
- cscript.exe (PID: 6700)
- cscript.exe (PID: 5892)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 7244)
- cscript.exe (PID: 7768)
- cscript.exe (PID: 8028)
- cscript.exe (PID: 3176)
- cscript.exe (PID: 6700)
- cscript.exe (PID: 5892)
Gets the drive type (SCRIPT)
- cscript.exe (PID: 7244)
- cscript.exe (PID: 7768)
- cscript.exe (PID: 8028)
- cscript.exe (PID: 3176)
- cscript.exe (PID: 6700)
- cscript.exe (PID: 5892)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- cscript.exe (PID: 7244)
- cscript.exe (PID: 7768)
- cscript.exe (PID: 3176)
- cscript.exe (PID: 8028)
- cscript.exe (PID: 5892)
- cscript.exe (PID: 6700)
Accesses computer name via WMI (SCRIPT)
- cscript.exe (PID: 7244)
- cscript.exe (PID: 7768)
- cscript.exe (PID: 8028)
- cscript.exe (PID: 3176)
- cscript.exe (PID: 5892)
- cscript.exe (PID: 6700)
Gets a collection of all available drive names (SCRIPT)
- cscript.exe (PID: 7244)
- cscript.exe (PID: 7768)
- cscript.exe (PID: 8028)
- cscript.exe (PID: 3176)
- cscript.exe (PID: 6700)
- cscript.exe (PID: 5892)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- cscript.exe (PID: 7244)
- cscript.exe (PID: 7768)
- cscript.exe (PID: 8028)
Executes application which crashes
- cscript.exe (PID: 7244)
- cscript.exe (PID: 7768)
- cscript.exe (PID: 8028)
The process creates files with name similar to system file names
- WerFault.exe (PID: 7624)
- WerFault.exe (PID: 7984)
- WerFault.exe (PID: 8108)
Sets XML DOM element text (SCRIPT)
- cscript.exe (PID: 3176)
INFO
Reads the software policy settings
- cscript.exe (PID: 7244)
- cscript.exe (PID: 7768)
- cscript.exe (PID: 8028)
- cscript.exe (PID: 6700)
- cscript.exe (PID: 3176)
- cscript.exe (PID: 5892)
Reads security settings of Internet Explorer
- cscript.exe (PID: 7244)
- cscript.exe (PID: 7768)
- cscript.exe (PID: 8028)
- cscript.exe (PID: 3176)
- cscript.exe (PID: 6700)
- cscript.exe (PID: 5892)
Checks proxy server information
- cscript.exe (PID: 7244)
Creates files or folders in the user directory
- cscript.exe (PID: 7244)
- WerFault.exe (PID: 7624)
- WerFault.exe (PID: 7984)
- WerFault.exe (PID: 8108)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .669 | | | Composer 669 module (100) |
|---|
Total processes
149
Monitored processes
14
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
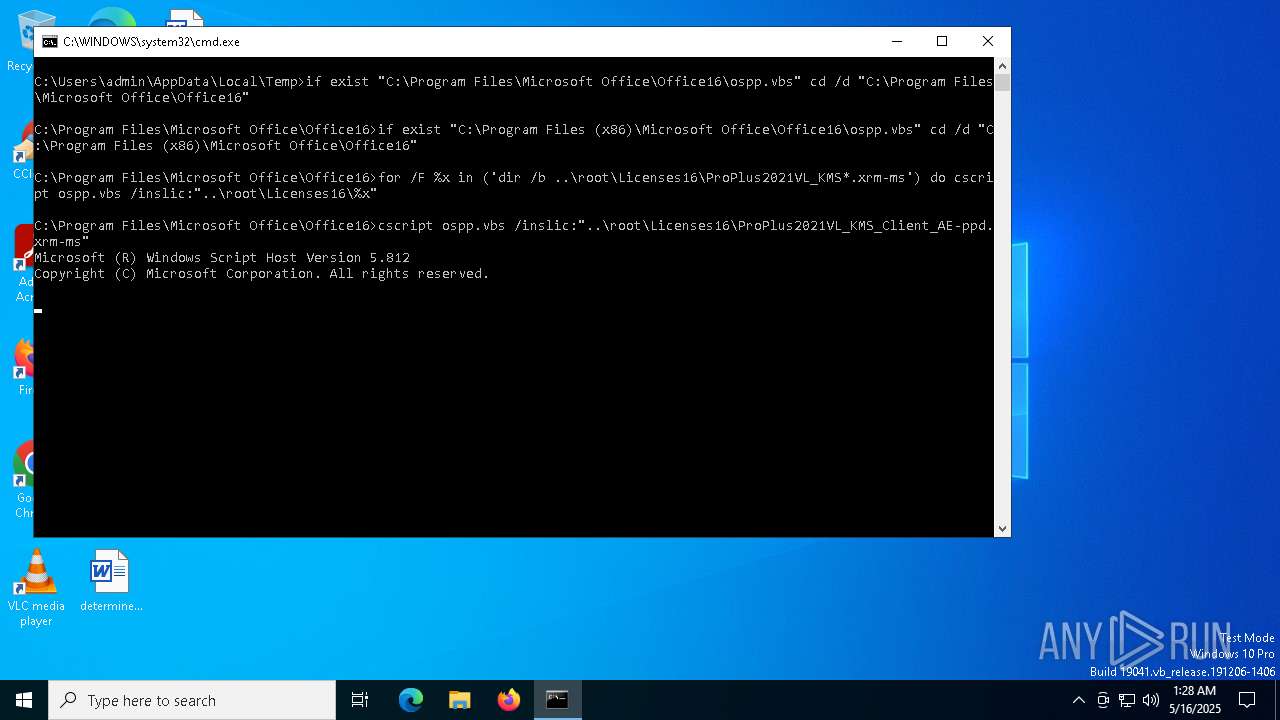
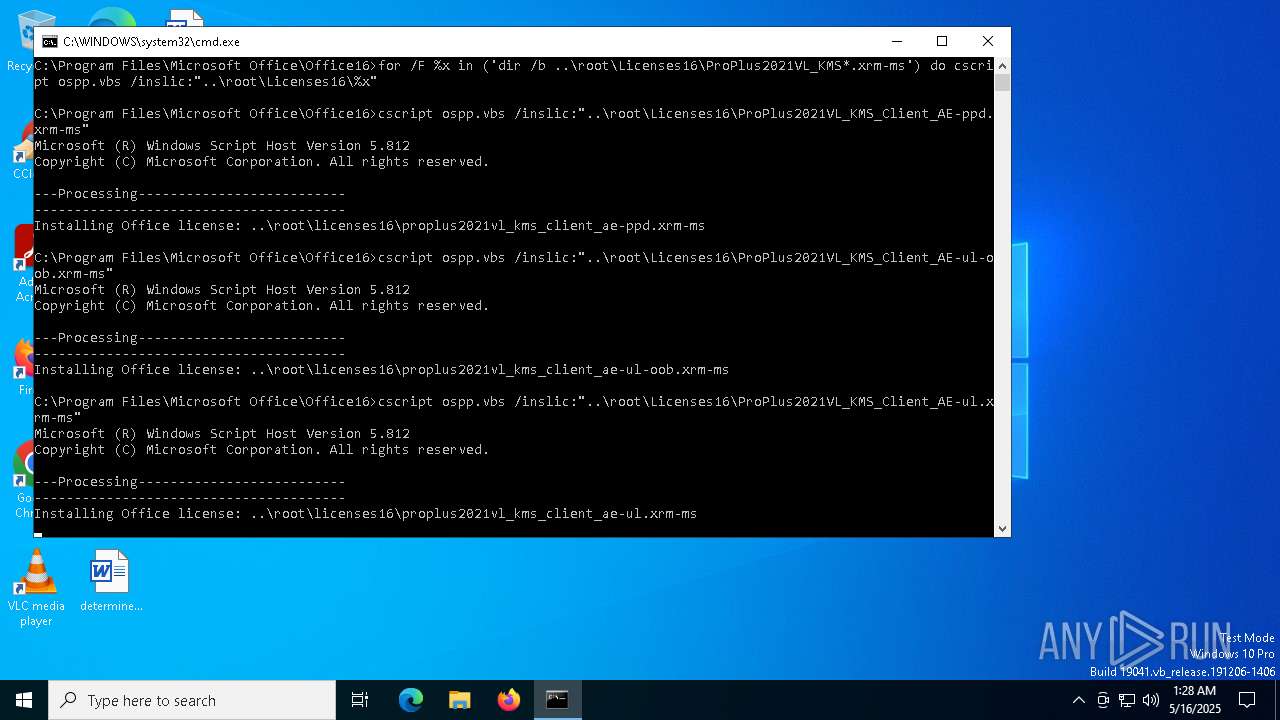
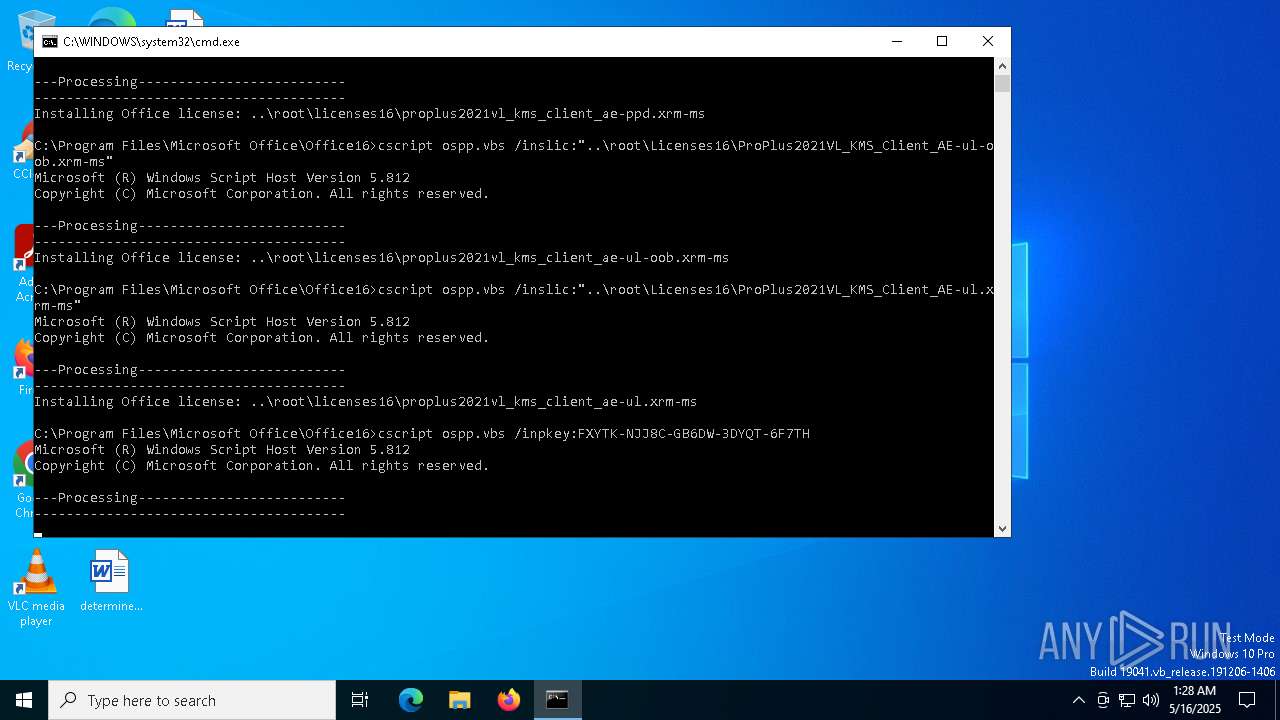
| 3176 | cscript ospp.vbs /inpkey:FXYTK-NJJ8C-GB6DW-3DYQT-6F7TH | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 4776 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\oppsrearm.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4880 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5892 | cscript ospp.vbs /act | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6700 | cscript ospp.vbs /sethst:kms.msgang.com | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 7220 | C:\WINDOWS\system32\cmd.exe /c dir /b ..\root\Licenses16\ProPlus2021VL_KMS*.xrm-ms | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7244 | cscript ospp.vbs /inslic:"..\root\Licenses16\ProPlus2021VL_KMS_Client_AE-ppd.xrm-ms" | C:\Windows\System32\cscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 3221225477 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 7320 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7356 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7624 | C:\WINDOWS\system32\WerFault.exe -u -p 7244 -s 1680 | C:\Windows\System32\WerFault.exe | — | cscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
25 251
Read events
25 251
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
13
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7624 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_cscript.exe_62b6f5ddb4f9b32f9faaaa562a56d6d8f11b6a_d25c8a3a_945c82eb-86bf-4340-b998-9cebbb95f1b1\Report.wer | — | |
MD5:— | SHA256:— | |||
| 7984 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_cscript.exe_62b6f5ddb4f9b32f9faaaa562a56d6d8f11b6a_d25c8a3a_e6e42e9d-8e5d-46d8-8bd7-ad7288dc4f66\Report.wer | — | |
MD5:— | SHA256:— | |||
| 8108 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_cscript.exe_62b6f5ddb4f9b32f9faaaa562a56d6d8f11b6a_d25c8a3a_dad87844-24ea-4069-87e6-e4f6f71ca0a9\Report.wer | — | |
MD5:— | SHA256:— | |||
| 7244 | cscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A583E2A51BFBDC1E492A57B7C8325850 | binary | |
MD5:54C3285B2A0ACDCFB6EAC75CC3100632 | SHA256:F3F8638B8E77B38A53F4761B9AE823FB83A34EA9B776909FB4D97DA05820CB5D | |||
| 7984 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERCCB9.tmp.WERInternalMetadata.xml | binary | |
MD5:EEC7A9F0303E0206235C3E8FD691CD1A | SHA256:E84179B39F73CE8C8B54402E93CCD1E25DE8397A92CEF2F9DE6B769E8D8819C6 | |||
| 7624 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERC20C.tmp.xml | xml | |
MD5:B98F6D24BB7C6777C5CF7C1E4AFA7748 | SHA256:580E95E4668F44E9D6A32855A06AEBD8E0694D9FC5278D6E1532A30ED1245A41 | |||
| 7984 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERCC1C.tmp.dmp | binary | |
MD5:62653423EFA29A84331D1CD98CA9B182 | SHA256:E48D9F2D5EEE8DF95EA21710AF2EF8E86B45D36683586A54C54FCAF9338F5281 | |||
| 7984 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\cscript.exe.7768.dmp | binary | |
MD5:1019B9553DC50345DB393ACFAF838C36 | SHA256:2DCBD49FB9F0B0C5900DA1B4F04BB80CBA51DFF99D19687C0BE200C138630C1F | |||
| 7984 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERCCE9.tmp.xml | xml | |
MD5:5960C42F0A5B9C08F7113AA8335B6E50 | SHA256:D217073423530561F19E7F58783C44946BE9D15868152E1441CD015881020844 | |||
| 8108 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERD1FA.tmp.xml | xml | |
MD5:D33B04DB162B777A2A854A6C4619AF73 | SHA256:D3C6F049540B67959DC6BE420420E6421CB24619158B0568AB3936E3556B253A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
21
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7244 | cscript.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
7244 | cscript.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_2010-07-06.crl | unknown | — | — | whitelisted |
6040 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6040 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
976 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
7244 | cscript.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2112 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
activation.sls.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |