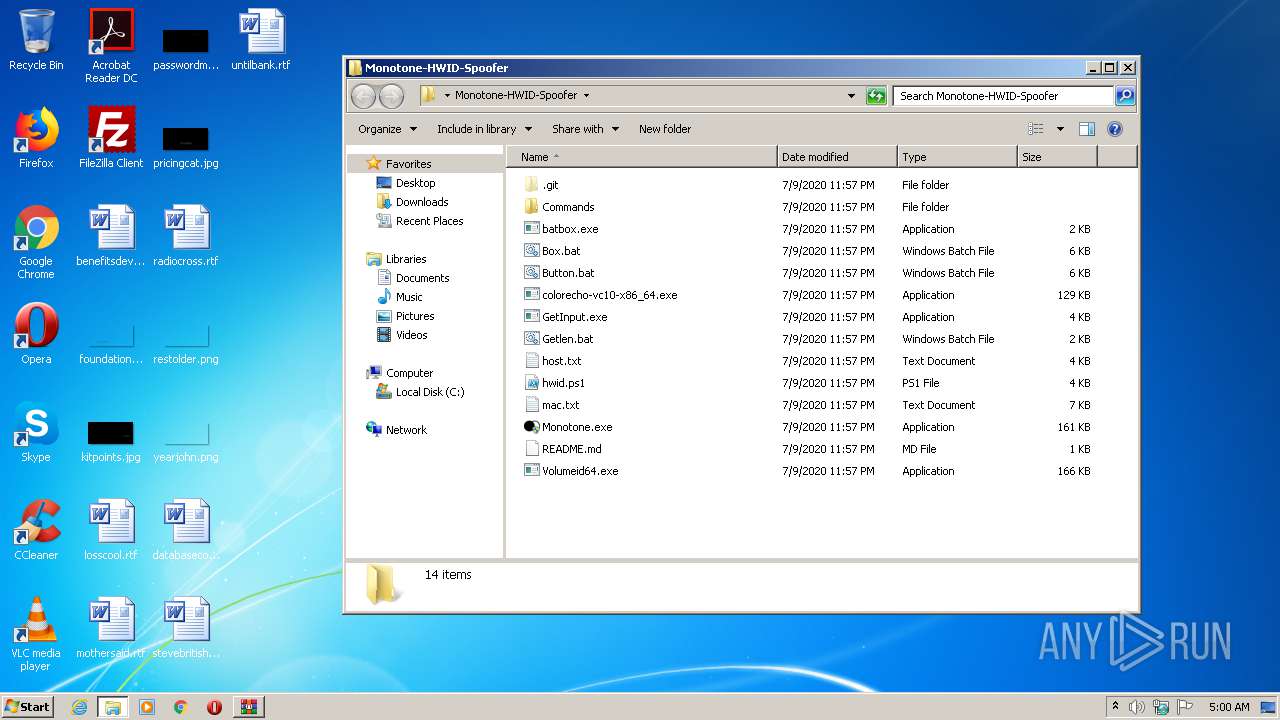
| File name: | Monotone-HWID-Spoofer.zip |
| Full analysis: | https://app.any.run/tasks/e37be01a-6b57-42d8-aa6d-80a81b8a21e7 |
| Verdict: | Malicious activity |
| Analysis date: | July 10, 2020, 03:59:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 991EB28F2A69E3005B35ED24D66F8412 |
| SHA1: | AD2EE312FFC0D8ACBFAEBA8D7EE416DE1CB05AB4 |
| SHA256: | 59DE0781B884DC65532693E485B1AC50178585957CC3F7B673114846119912B0 |
| SSDEEP: | 24576:t2Y/OLZgrhGnD6Yr9AbzVBF9+X/GqrsYK0kqGvm6QQvUUAv7quZnozLmMBXLA:t8Z2rrtBF9lbE5GO6JvhW7TZno396 |
MALICIOUS
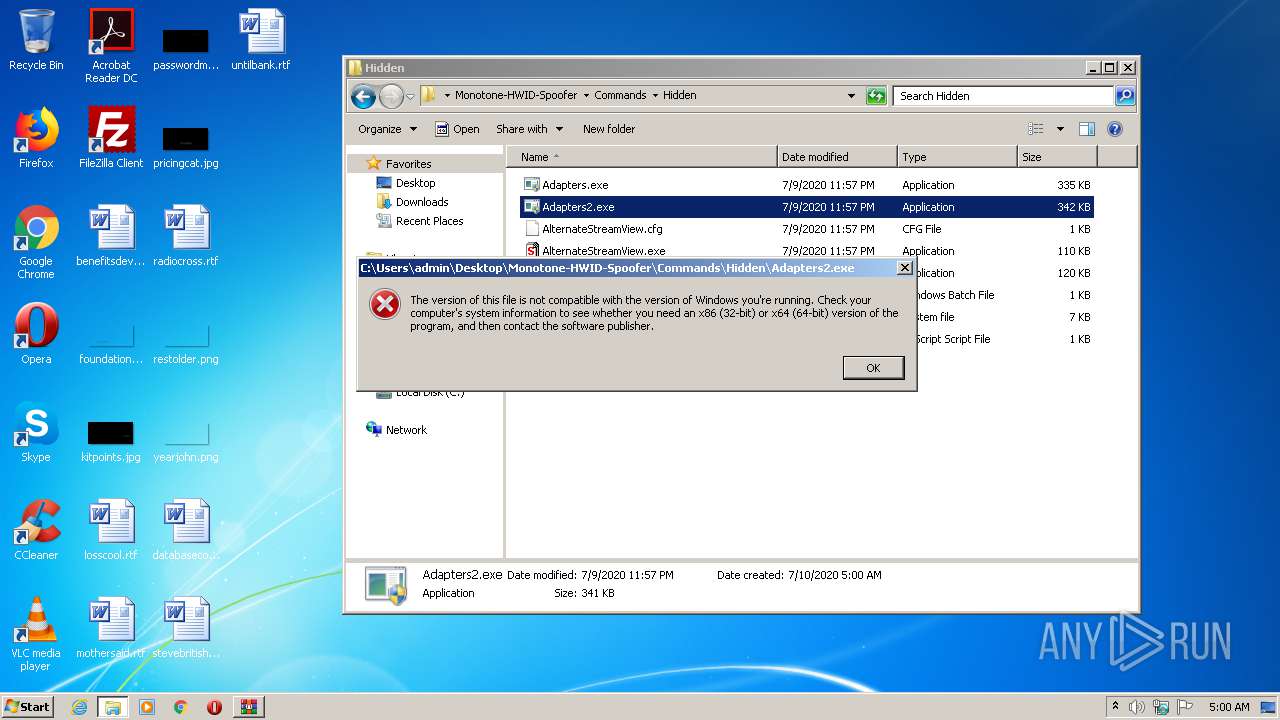
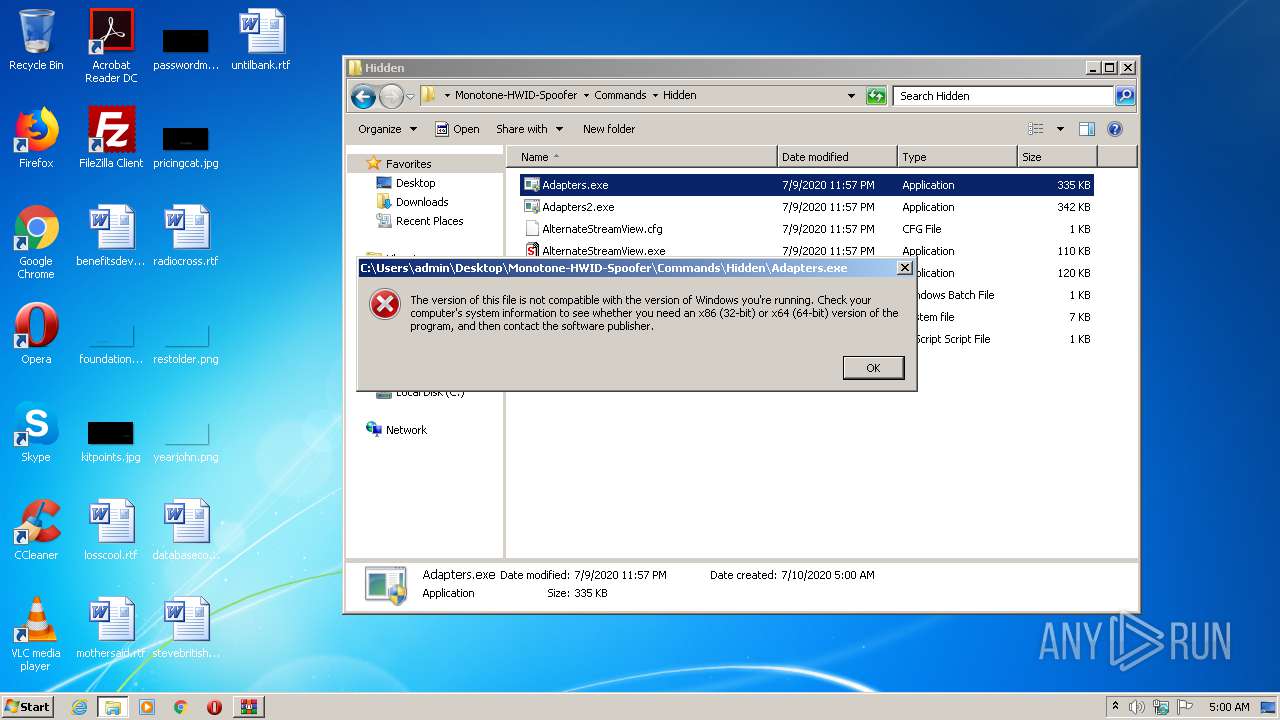
Application was dropped or rewritten from another process
- GetInput.exe (PID: 3652)
- batbox.exe (PID: 3360)
SUSPICIOUS
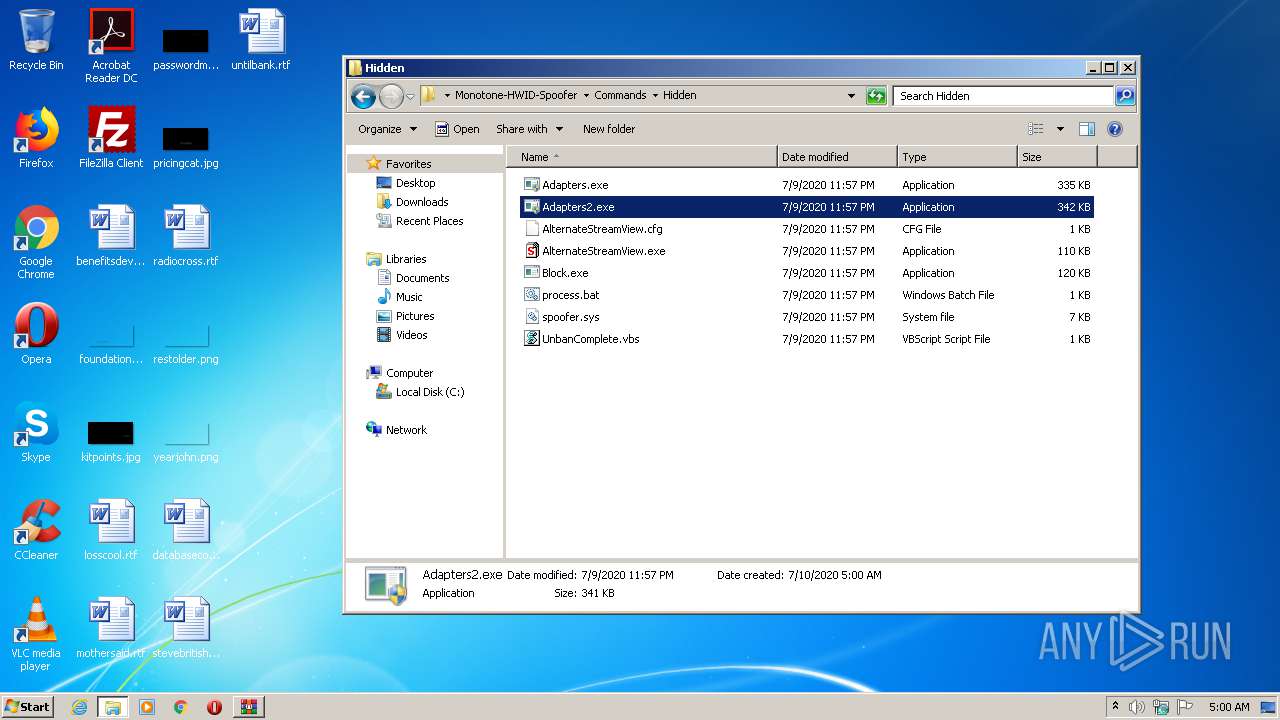
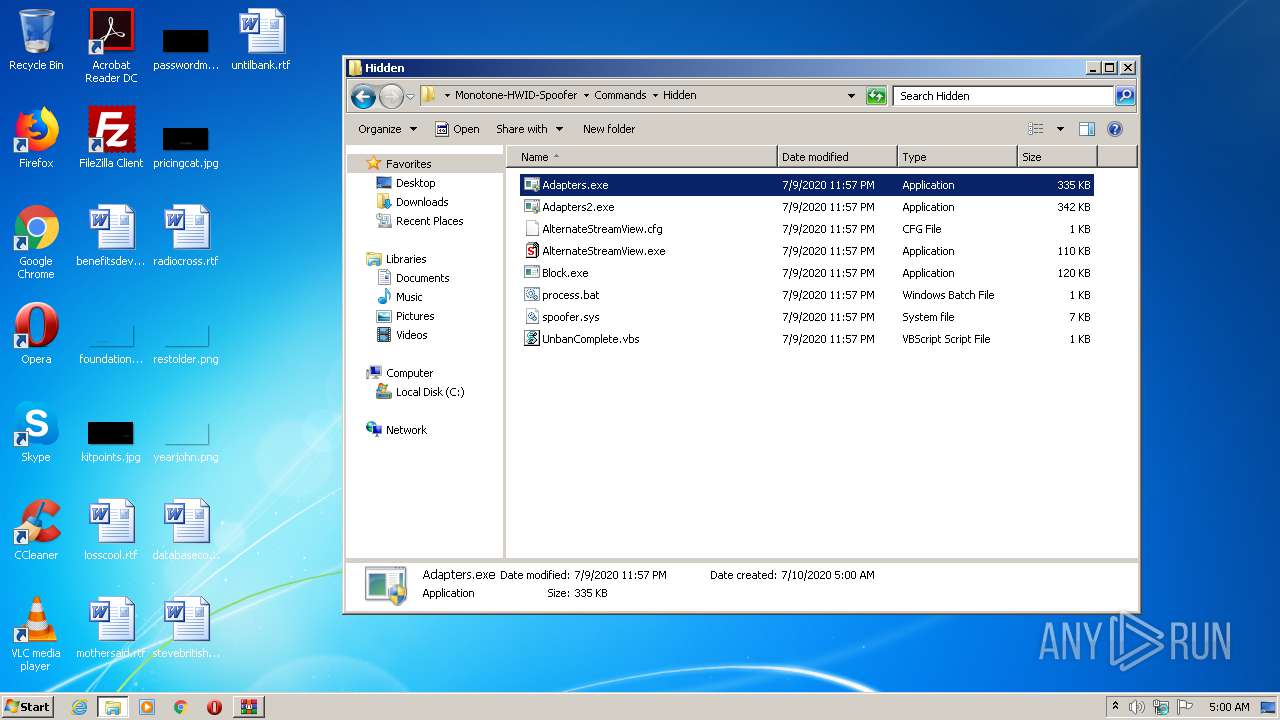
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2088)
Uses TASKLIST.EXE to query information about running processes
- cmd.exe (PID: 572)
INFO
Manual execution by user
- GetInput.exe (PID: 3652)
- cmd.exe (PID: 572)
- cmd.exe (PID: 236)
- cmd.exe (PID: 1764)
- batbox.exe (PID: 3360)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:07:09 23:57:07 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Monotone-HWID-Spoofer/.git/ |
Total processes
54
Monitored processes
9
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | cmd /c ""C:\Users\admin\Desktop\Monotone-HWID-Spoofer\Box.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
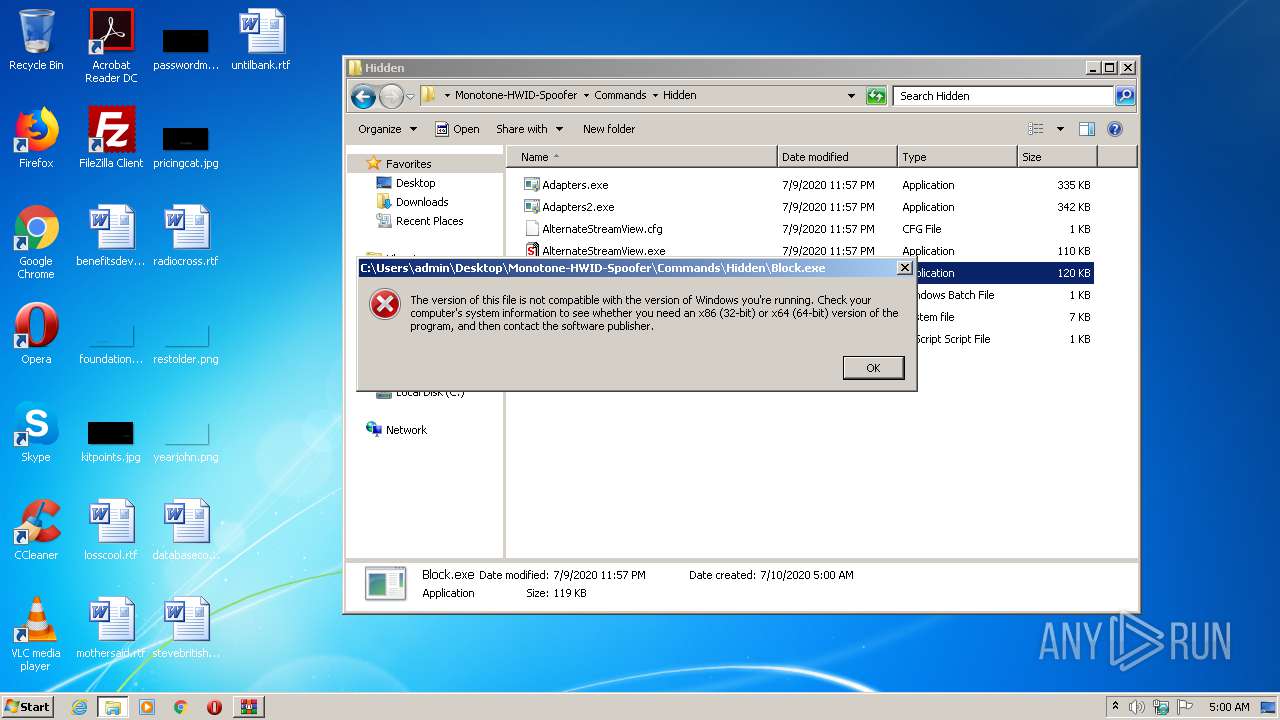
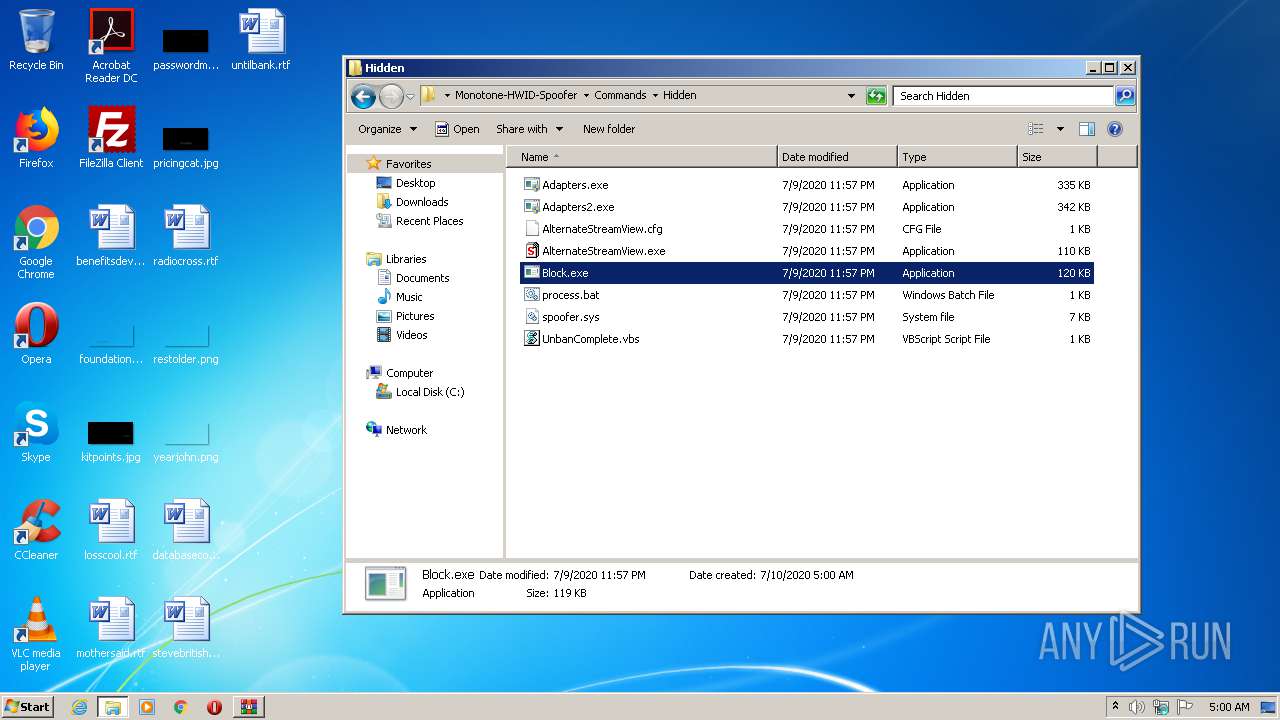
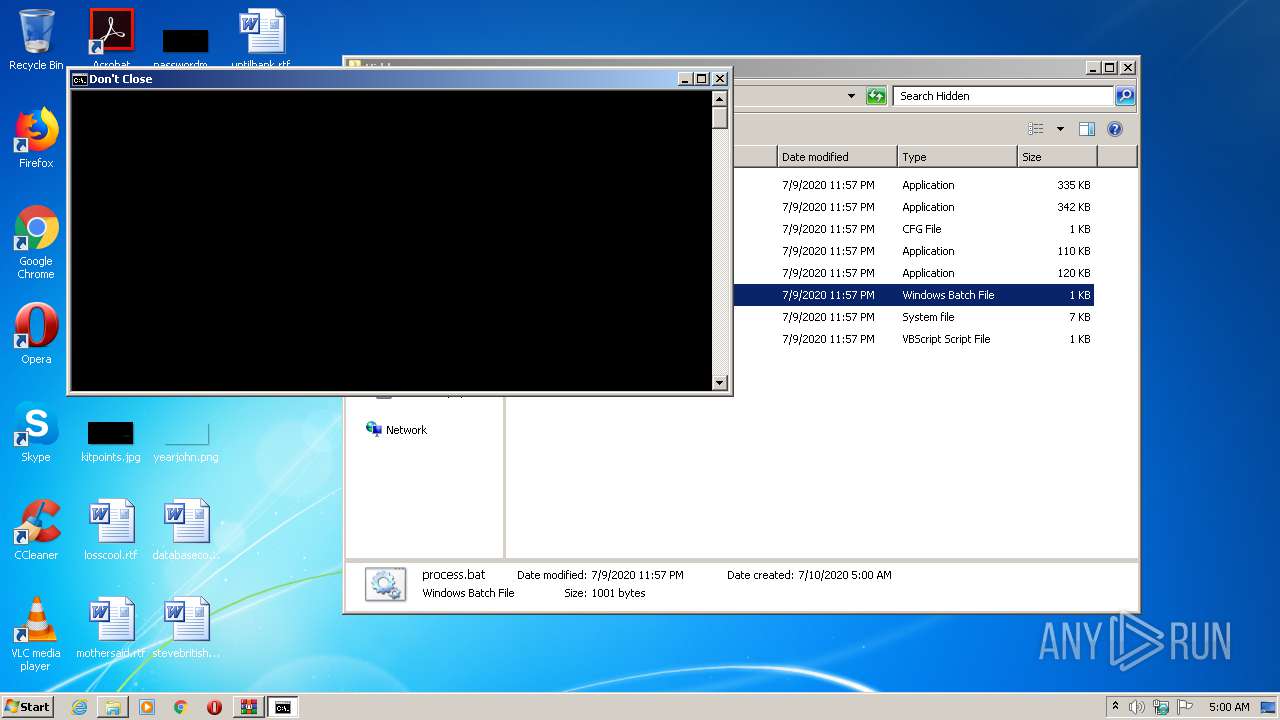
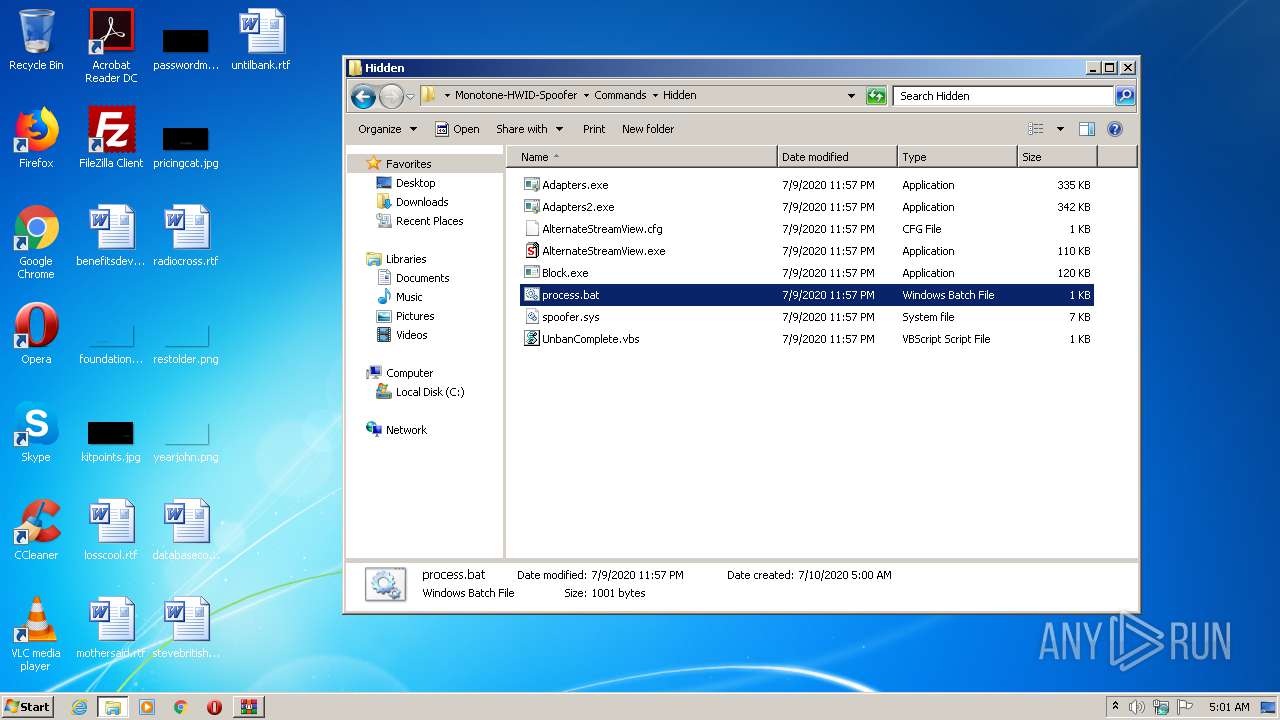
| 572 | cmd /c ""C:\Users\admin\Desktop\Monotone-HWID-Spoofer\Commands\Hidden\process.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1764 | cmd /c ""C:\Users\admin\Desktop\Monotone-HWID-Spoofer\Button.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2088 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Monotone-HWID-Spoofer.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2732 | ping localhost | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3360 | "C:\Users\admin\Desktop\Monotone-HWID-Spoofer\batbox.exe" | C:\Users\admin\Desktop\Monotone-HWID-Spoofer\batbox.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
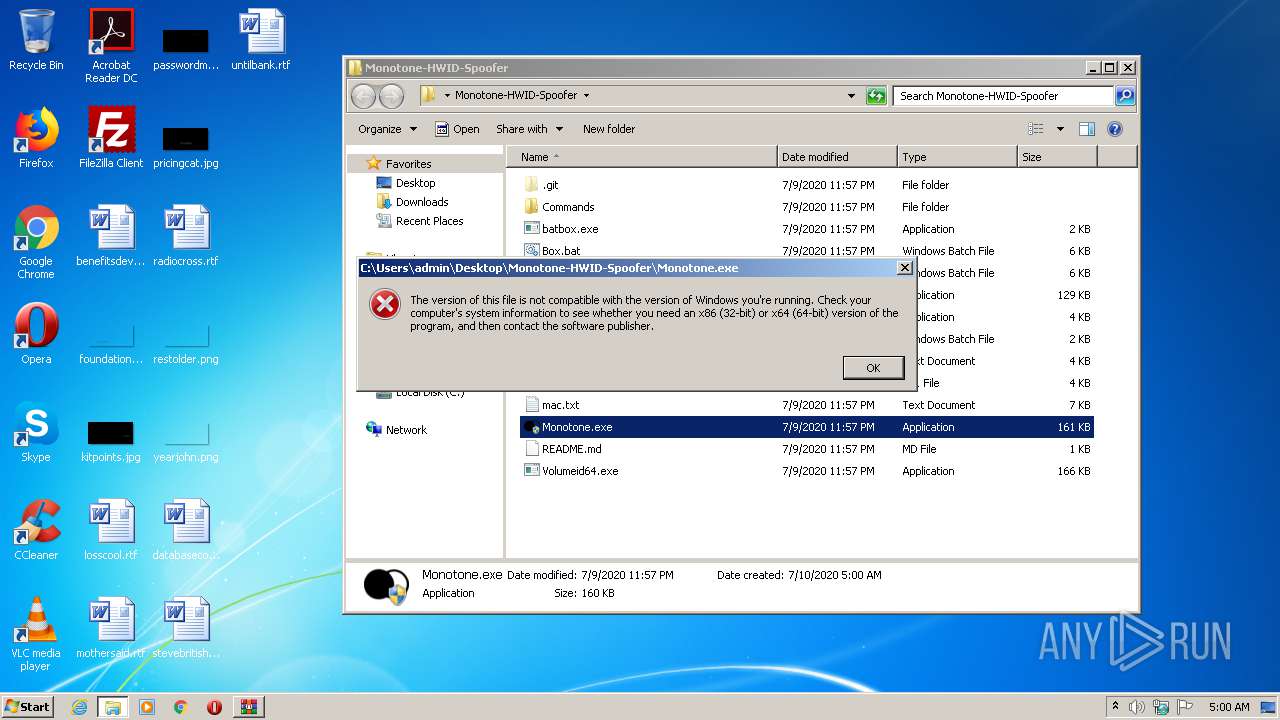
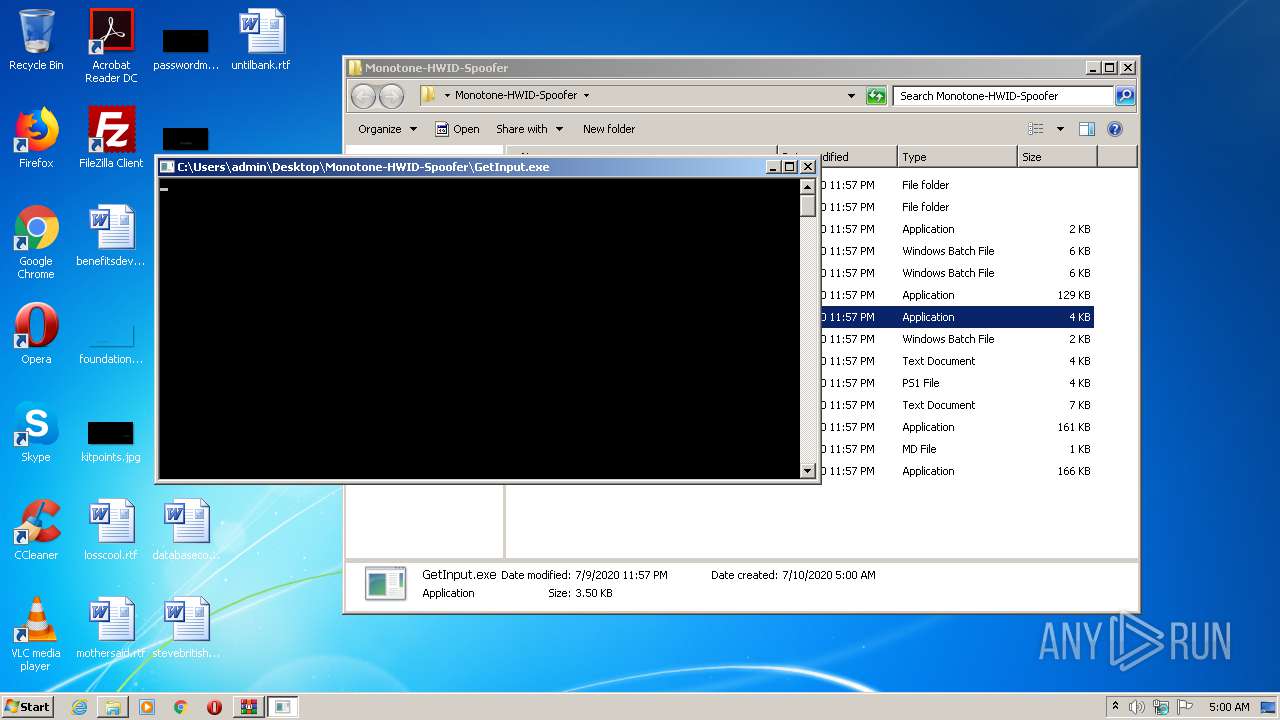
| 3652 | "C:\Users\admin\Desktop\Monotone-HWID-Spoofer\GetInput.exe" | C:\Users\admin\Desktop\Monotone-HWID-Spoofer\GetInput.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 97 Modules
| |||||||||||||||
| 3920 | tasklist /NH /FI "imagename eq Monotone.exe" | C:\Windows\system32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4016 | find /i "Monotone.exe" | C:\Windows\system32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
459
Read events
450
Write events
9
Delete events
0
Modification events
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Monotone-HWID-Spoofer.zip | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
10
Suspicious files
72
Text files
32
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2088 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2088.44368\Monotone-HWID-Spoofer\.git\config | text | |
MD5:— | SHA256:— | |||
| 2088 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2088.44368\Monotone-HWID-Spoofer\.git\hooks\applypatch-msg.sample | text | |
MD5:CE562E08D8098926A3862FC6E7905199 | SHA256:0223497A0B8B033AA58A3A521B8629869386CF7AB0E2F101963D328AA62193F7 | |||
| 2088 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2088.44368\Monotone-HWID-Spoofer\.git\hooks\commit-msg.sample | text | |
MD5:579A3C1E12A1E74A98169175FB913012 | SHA256:1F74D5E9292979B573EBD59741D46CB93FF391ACDD083D340B94370753D92437 | |||
| 2088 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2088.44368\Monotone-HWID-Spoofer\.git\HEAD | text | |
MD5:4CF2D64E44205FE628DDD534E1151B58 | SHA256:F6F2B945F6C411B02BA3DA9C7ACE88DCF71B6AF65BA2E0D89AA82900042B5A10 | |||
| 2088 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2088.44368\Monotone-HWID-Spoofer\.git\hooks\pre-applypatch.sample | text | |
MD5:054F9FFB8BFE04A599751CC757226DDA | SHA256:E15C5B469EA3E0A695BEA6F2C82BCF8E62821074939DDD85B77E0007FF165475 | |||
| 2088 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2088.44368\Monotone-HWID-Spoofer\.git\index | binary | |
MD5:— | SHA256:— | |||
| 2088 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2088.44368\Monotone-HWID-Spoofer\.git\hooks\post-update.sample | text | |
MD5:2B7EA5CEE3C49FF53D41E00785EB974C | SHA256:81765AF2DAEF323061DCBC5E61FC16481CB74B3BAC9AD8A174B186523586F6C5 | |||
| 2088 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2088.44368\Monotone-HWID-Spoofer\.git\hooks\fsmonitor-watchman.sample | text | |
MD5:EA587B0FAE70333BCE92257152996E70 | SHA256:F3C0228D8E827F1C5260AC59FDD92C3D425C46E54711EF713C5A54AE0A4DB2B4 | |||
| 2088 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2088.44368\Monotone-HWID-Spoofer\.git\hooks\pre-merge-commit.sample | text | |
MD5:39CB268E2A85D436B9EB6F47614C3CBC | SHA256:D3825A70337940EBBD0A5C072984E13245920CDF8898BD225C8D27A6DFC9CB53 | |||
| 2088 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2088.44368\Monotone-HWID-Spoofer\.git\hooks\pre-receive.sample | text | |
MD5:2AD18EC82C20AF7B5926ED9CEA6AEEDD | SHA256:A4C3D2B9C7BB3FD8D1441C31BD4EE71A595D66B44FCF49DDB310252320169989 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report