| File name: | Office2024VolumeLicensePack_x64.exe |
| Full analysis: | https://app.any.run/tasks/a75a25ce-b6c7-49ef-83e4-db8b13e0d3e4 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 10:12:21 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 650C3A652962E3A0DF8B81CEC440CFB6 |
| SHA1: | 09ABDF0F9E9F2858D9D474CCF4E0184D895F4754 |
| SHA256: | 59DD32C1E81E829DACFFC74E4B2EF59DD504778BDE8EB9AE692BEB1AD773F0D9 |
| SSDEEP: | 12288:B4xxcymHvgBO69xbR9DlWZESvl1aVVVVVVVVVVOmOZEkRrV:B4xxcNvgU69xbJslRmOiqV |
MALICIOUS
Accesses environment variables (SCRIPT)
- cscript.exe (PID: 8000)
Gets %windir% folder path (SCRIPT)
- cscript.exe (PID: 8000)
Checks whether a specified folder exists (SCRIPT)
- cscript.exe (PID: 8000)
SUSPICIOUS
Process drops legitimate windows executable
- Office2024VolumeLicensePack_x64.exe (PID: 7644)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 8000)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- cscript.exe (PID: 8000)
Checks whether a specific file exists (SCRIPT)
- cscript.exe (PID: 8000)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 8000)
Sets XML DOM element text (SCRIPT)
- cscript.exe (PID: 8000)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 8000)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- cscript.exe (PID: 8000)
Reads data from a file (SCRIPT)
- cscript.exe (PID: 8000)
Runs shell command (SCRIPT)
- cscript.exe (PID: 8000)
Executable content was dropped or overwritten
- Dism.exe (PID: 6668)
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 904)
Accesses system date via WMI (SCRIPT)
- cscript.exe (PID: 8000)
Reads security settings of Internet Explorer
- Office2024VolumeLicensePack_x64.exe (PID: 7644)
The process checks if it is being run in the virtual environment
- cscript.exe (PID: 8000)
Changes charset (SCRIPT)
- cscript.exe (PID: 8000)
The process creates files with name similar to system file names
- Dism.exe (PID: 6668)
The process executes VB scripts
- Office2024VolumeLicensePack_x64.exe (PID: 7644)
INFO
Reads the software policy settings
- cscript.exe (PID: 8000)
Reads security settings of Internet Explorer
- cscript.exe (PID: 8000)
Checks proxy server information
- cscript.exe (PID: 8000)
Creates files or folders in the user directory
- cscript.exe (PID: 8000)
Checks supported languages
- Office2024VolumeLicensePack_x64.exe (PID: 7644)
- DismHost.exe (PID: 904)
Create files in a temporary directory
- Dism.exe (PID: 6668)
- Office2024VolumeLicensePack_x64.exe (PID: 7644)
The sample compiled with english language support
- Dism.exe (PID: 6668)
Reads the computer name
- DismHost.exe (PID: 904)
- Office2024VolumeLicensePack_x64.exe (PID: 7644)
Reads Environment values
- DismHost.exe (PID: 904)
Creates files in the program directory
- Office2024VolumeLicensePack_x64.exe (PID: 7644)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:07:02 00:20:33+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.38 |
| CodeSize: | 232960 |
| InitializedDataSize: | 132096 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x20c63 |
| OSVersion: | 6.1 |
| ImageVersion: | - |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 16.0.17830.20004 |
| ProductVersionNumber: | 16.0.17830.20004 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Microsoft Corporation |
| FileVersion: | 16.0.17830.20004 |
| LegalTrademarks1: | Microsoft® is a registered trademark of Microsoft Corporation. |
| LegalTrademarks2: | Windows® is a registered trademark of Microsoft Corporation. |
| ProductVersion: | 16.0.17830.20004 |
Total processes
138
Monitored processes
9
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 904 | C:\Users\admin\AppData\Local\Temp\F041D996-9A91-402B-AC02-AB66EE175F1D\dismhost.exe {8CFCCFEB-7C67-44DD-B52D-CBA00255CF42} | C:\Users\admin\AppData\Local\Temp\F041D996-9A91-402B-AC02-AB66EE175F1D\DismHost.exe | — | Dism.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Dism Host Servicing Process Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6668 | C:\WINDOWS\SysNative\Dism.exe /online /get-featureinfo /featurename:volumeactivation-full-role /NoRestart | C:\Windows\System32\Dism.exe | cscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Dism Image Servicing Utility Exit code: 2148468748 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6872 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7548 | "C:\Users\admin\Downloads\Office2024VolumeLicensePack_x64.exe" | C:\Users\admin\Downloads\Office2024VolumeLicensePack_x64.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 3221226540 Version: 16.0.17830.20004 Modules
| |||||||||||||||
| 7644 | "C:\Users\admin\Downloads\Office2024VolumeLicensePack_x64.exe" | C:\Users\admin\Downloads\Office2024VolumeLicensePack_x64.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 16.0.17830.20004 Modules
| |||||||||||||||
| 7680 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7712 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8000 | cscript //Nologo kms_host24.vbs | C:\Windows\SysWOW64\cscript.exe | Office2024VolumeLicensePack_x64.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 8008 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 470
Read events
5 468
Write events
2
Delete events
0
Modification events
| (PID) Process: | (6872) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdHigh |
Value: 31176943 | |||
| (PID) Process: | (6872) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdLow |
Value: | |||
Executable files
50
Suspicious files
5
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
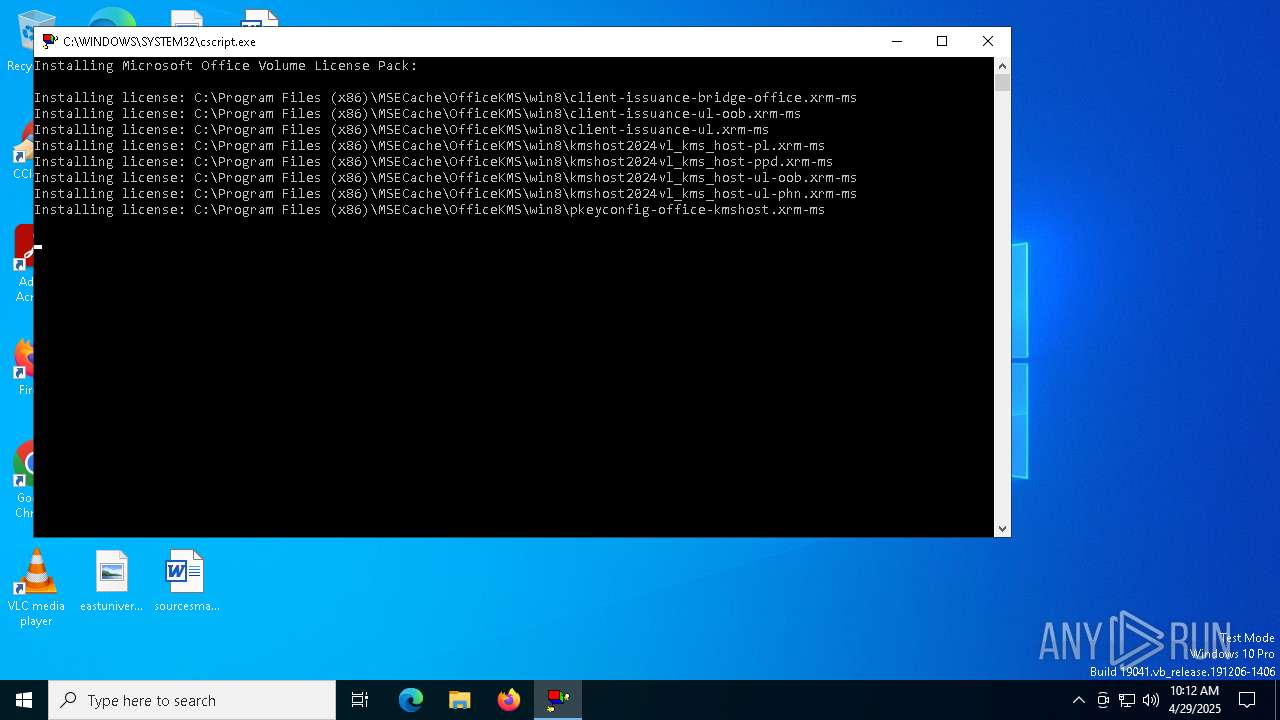
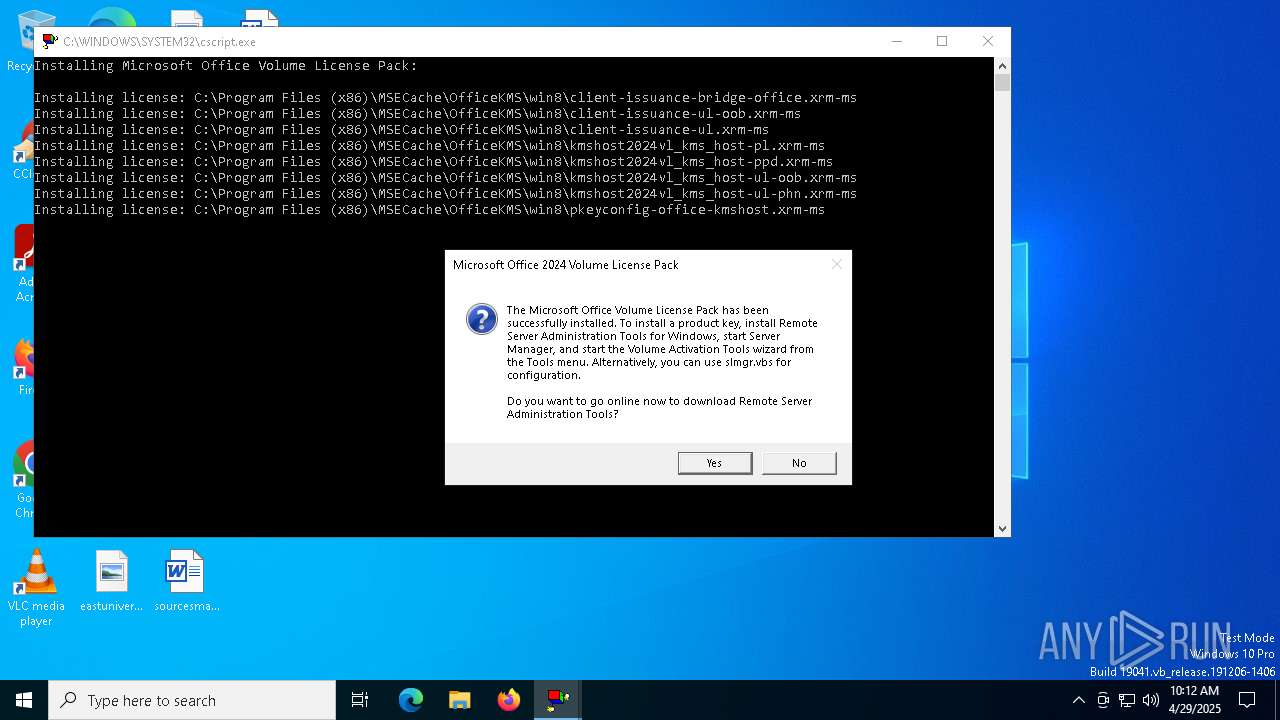
| 7644 | Office2024VolumeLicensePack_x64.exe | C:\Program Files (x86)\MSECache\OfficeKMS\kms_host.xml | text | |
MD5:195B335E6F9C7D65416C973F2F084762 | SHA256:9F5BA492B3D09551F04F13F95372ED245F51EE3CA761C337F904665E9F1037EE | |||
| 7644 | Office2024VolumeLicensePack_x64.exe | C:\Program Files (x86)\MSECache\OfficeKMS\win8\client-issuance-bridge-office.xrm-ms | xml | |
MD5:33C1695D278F5917F28067D27B4868EE | SHA256:65BCCC008F5B44D2DBD880C0C33AFCFFF27C07DD24DC0CC7DDA2B3BFA7E9AE74 | |||
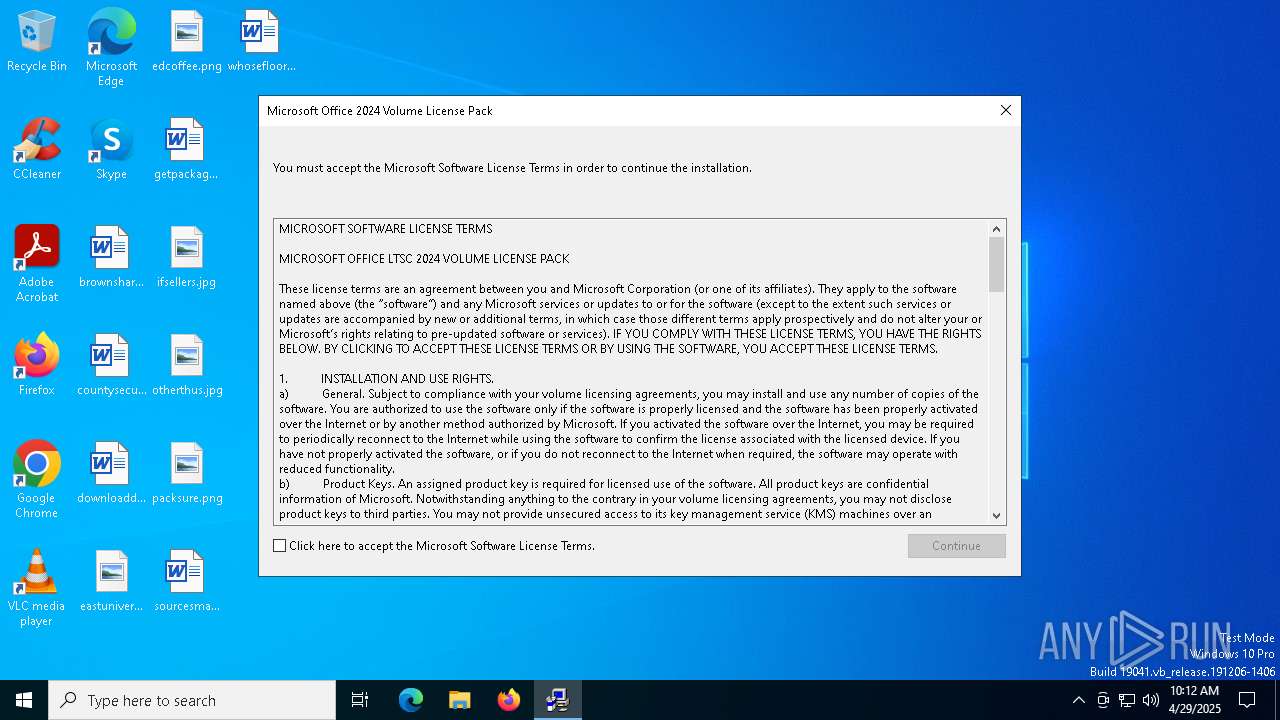
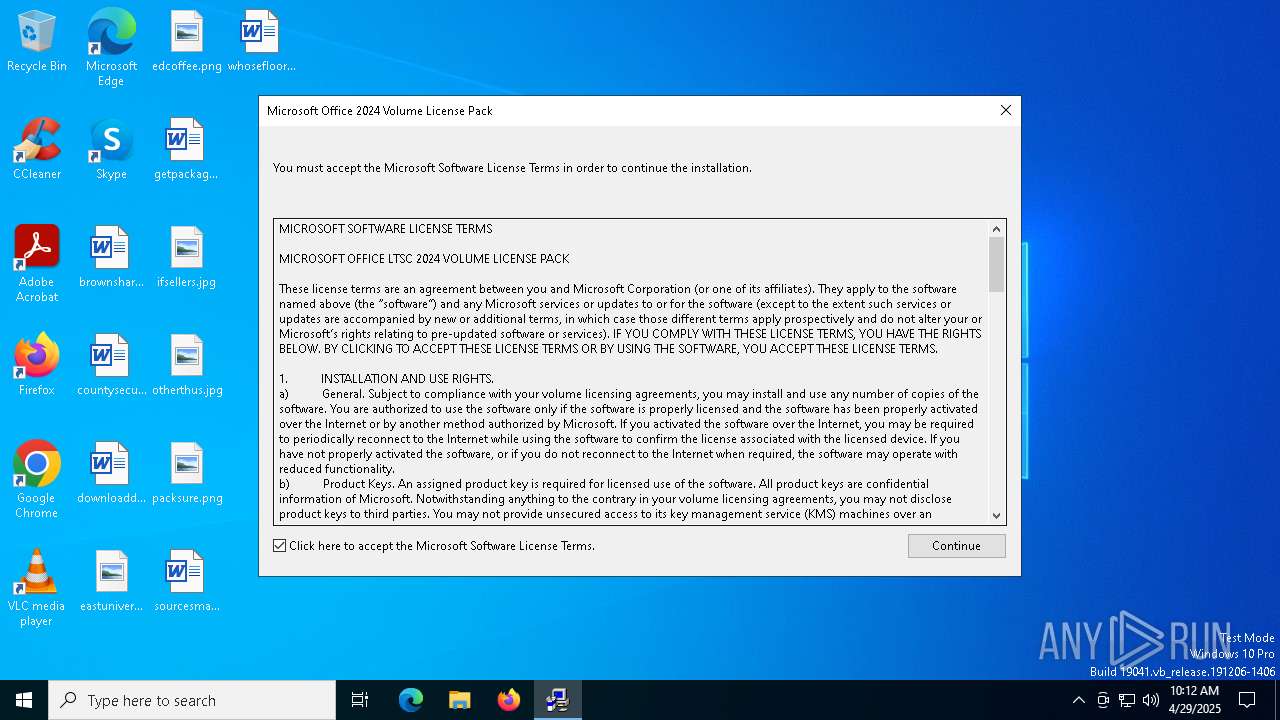
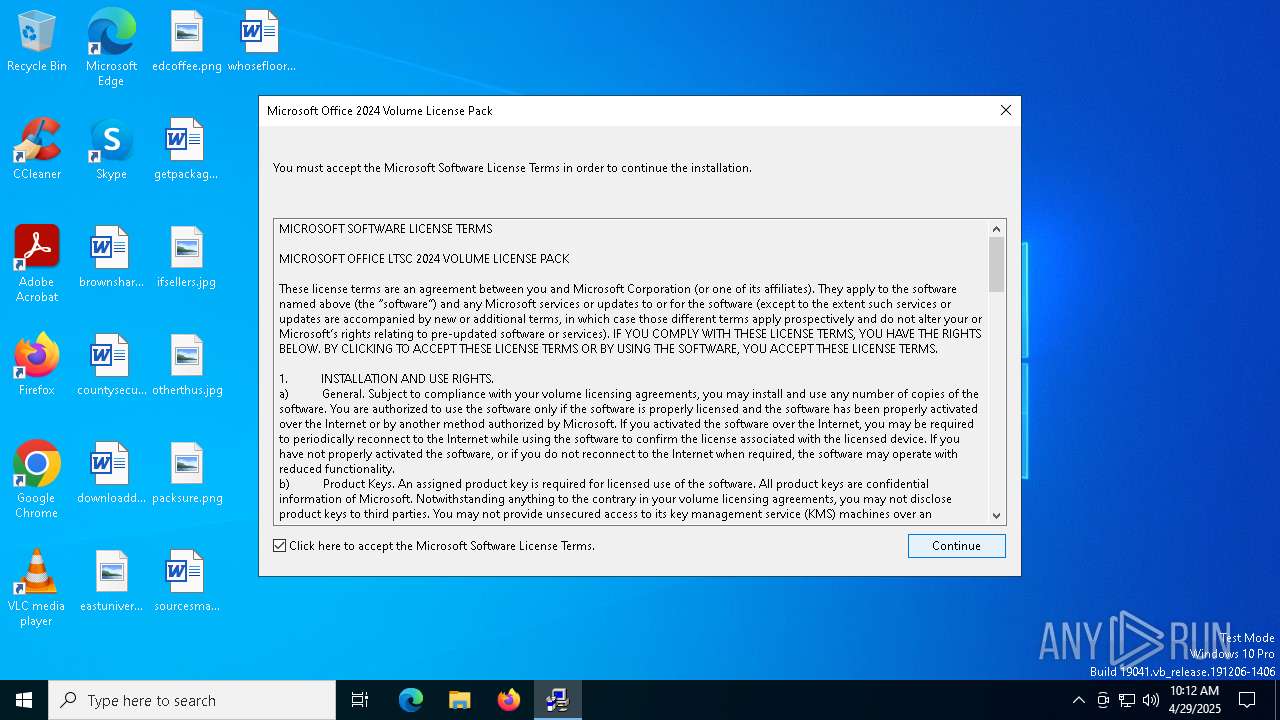
| 7644 | Office2024VolumeLicensePack_x64.exe | C:\Users\admin\AppData\Local\Temp\OWPBAC6.tmp\eula.txt | text | |
MD5:FF5A780583F82C2ACCA1B28C0EB9E8E6 | SHA256:FBF3D437B420C67A41463CB89C3430C41360A00018B5AB454F9BA96C895ACDEE | |||
| 7644 | Office2024VolumeLicensePack_x64.exe | C:\Program Files (x86)\MSECache\OfficeKMS\Catalog\files.cat | binary | |
MD5:5F4FAA48EEA210D7BC199B81071606EB | SHA256:629CB19F93BD400A897E232CCAFDC2BE84633636DE383EBA140E6D69704AEC7B | |||
| 7644 | Office2024VolumeLicensePack_x64.exe | C:\Program Files (x86)\MSECache\OfficeKMS\kms_host24.vbs | text | |
MD5:813ADD22B015607FF475258A66784E9A | SHA256:FA97ECF609FF15BD7034BF6A29F8F3EFC886C7C2A2476D6D305F7365EEE23985 | |||
| 7644 | Office2024VolumeLicensePack_x64.exe | C:\Program Files (x86)\MSECache\OfficeKMS\win8\kmshost2024vl_kms_host-ppd.xrm-ms | xml | |
MD5:D177603B32CE4C79E108FC18BE52D7AF | SHA256:4B9EFC3A13CD259336AD60FA6384C60307978FF55E0ACC75187CC84ADD10F1A8 | |||
| 7644 | Office2024VolumeLicensePack_x64.exe | C:\Program Files (x86)\MSECache\OfficeKMS\win8\client-issuance-ul-oob.xrm-ms | xml | |
MD5:9B4DD4D831E23302D5ED965A3F2ABF9C | SHA256:786D03827D0E39745F05EEA04642F67575B5749B076F2402FA92CA8973514616 | |||
| 7644 | Office2024VolumeLicensePack_x64.exe | C:\Program Files (x86)\MSECache\OfficeKMS\win8\kmshost2024vl_kms_host-pl.xrm-ms | xml | |
MD5:2B9635E8596E20DB2E603A4C974E55DA | SHA256:22352180C0AF915EA5F0C9AE186DD274FB5D4E60C854C32ACD911644C0129482 | |||
| 7644 | Office2024VolumeLicensePack_x64.exe | C:\Program Files (x86)\MSECache\OfficeKMS\win8\kmshost2024vl_kms_host-ul-oob.xrm-ms | xml | |
MD5:916DC7D6F671D1FB41AD3F8849172D63 | SHA256:635D233C9C3151A04178C42CA958B2EB52360EFCB6914CD8AB04A5B13A74E753 | |||
| 7644 | Office2024VolumeLicensePack_x64.exe | C:\Program Files (x86)\MSECache\OfficeKMS\win8\client-issuance-ul.xrm-ms | xml | |
MD5:5B39AE306BDCF1AB7432EF34668E7840 | SHA256:387BBEDCE2F48B2AE3EAFD83BC0BD8383EC23C9031221DD4F9E0D2CC78150C7B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
20
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
8000 | cscript.exe | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
8000 | cscript.exe | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_2010-07-06.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7636 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7636 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.16.164.114:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
8000 | cscript.exe | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
6544 | svchost.exe | 20.190.159.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |