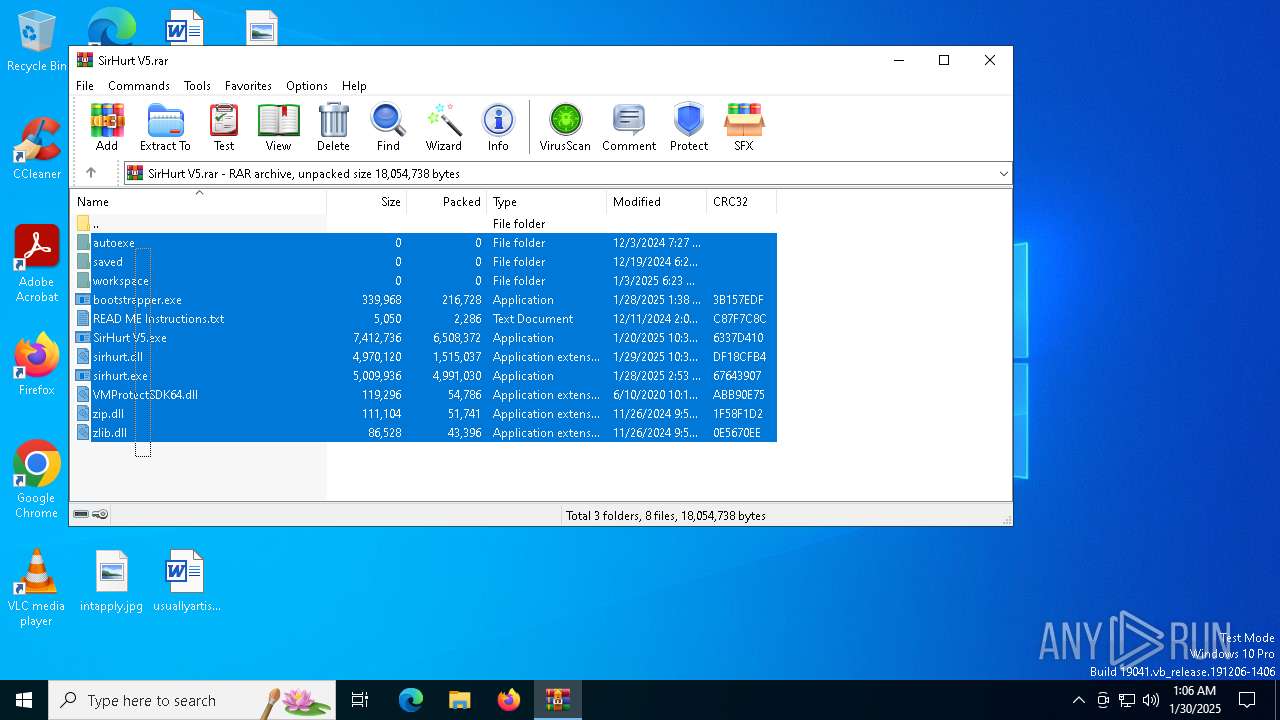
| File name: | SirHurt V5.rar |
| Full analysis: | https://app.any.run/tasks/70a6c58d-b6d2-46a3-9cfd-e75e4e889802 |
| Verdict: | Malicious activity |
| Analysis date: | January 30, 2025, 01:06:04 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 5E5C8624B24808787BF0CDA399AFC608 |
| SHA1: | C73C48D40C7BD2349CE72B3A99C6D697DD2078E7 |
| SHA256: | 59D4C0C86AB83476AAAFFAB20C1CC684394BE3B09424885A65B33DFF57346A30 |
| SSDEEP: | 98304:XVAFfjiC3NwIlu6SJyRLNdafiW86KgB0VfDqfJgL1M6lVrj0PvLGlftjiP9xykFF:3KuoIS69mLpAtqB+0EutGYcwBkT |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4724)
SUSPICIOUS
Reads the BIOS version
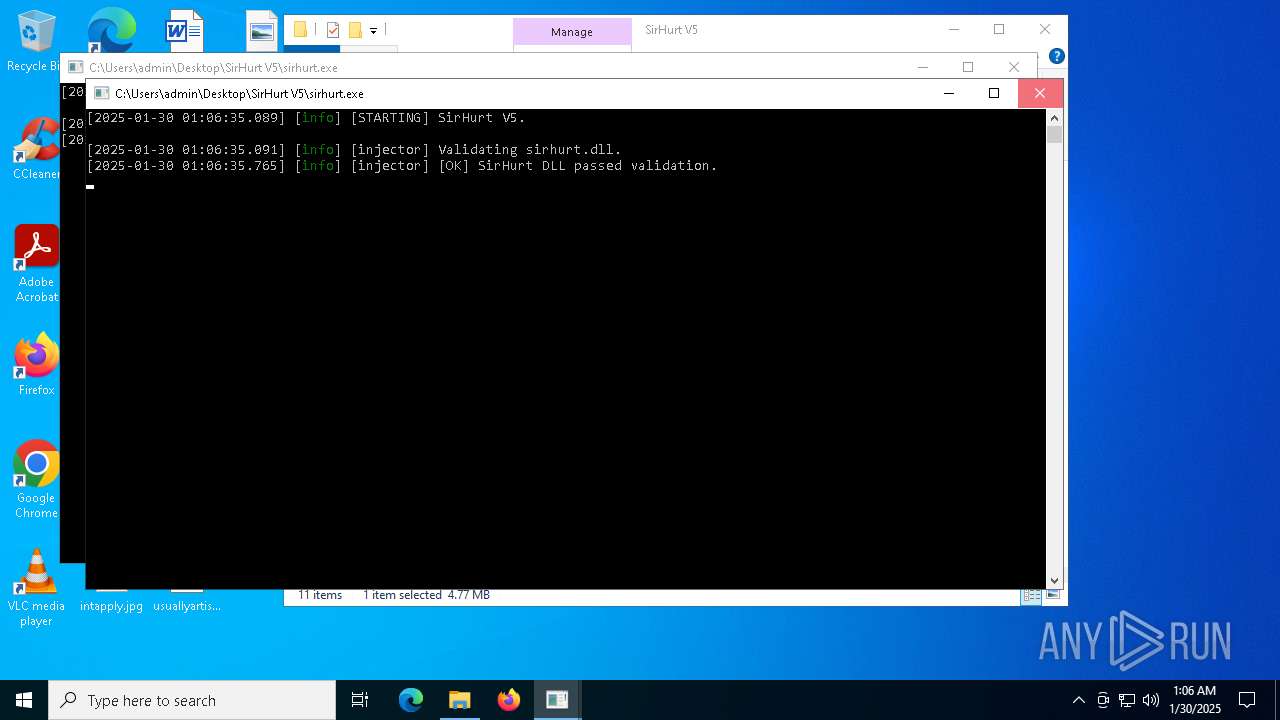
- sirhurt.exe (PID: 1580)
- sirhurt.exe (PID: 2940)
- sirhurt.exe (PID: 4308)
Executable content was dropped or overwritten
- sirhurt.exe (PID: 1580)
Process drops legitimate windows executable
- sirhurt.exe (PID: 1580)
Hides command output
- cmd.exe (PID: 2940)
- cmd.exe (PID: 2512)
- cmd.exe (PID: 6196)
Executing commands from a ".bat" file
- sirhurt.exe (PID: 1580)
- sirhurt.exe (PID: 2940)
- sirhurt.exe (PID: 4308)
Starts CMD.EXE for commands execution
- sirhurt.exe (PID: 1580)
- sirhurt.exe (PID: 2940)
- sirhurt.exe (PID: 4308)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2940)
- sirhurt.exe (PID: 1580)
- cmd.exe (PID: 2512)
- cmd.exe (PID: 6196)
- sirhurt.exe (PID: 2940)
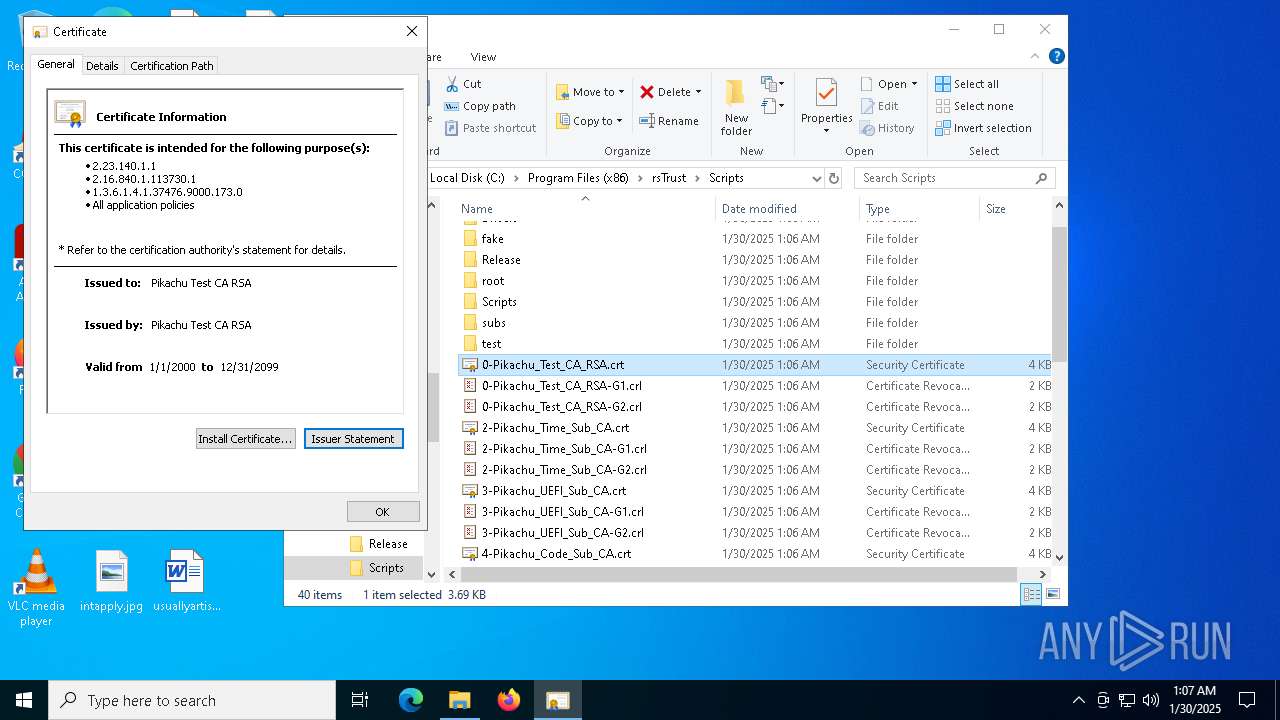
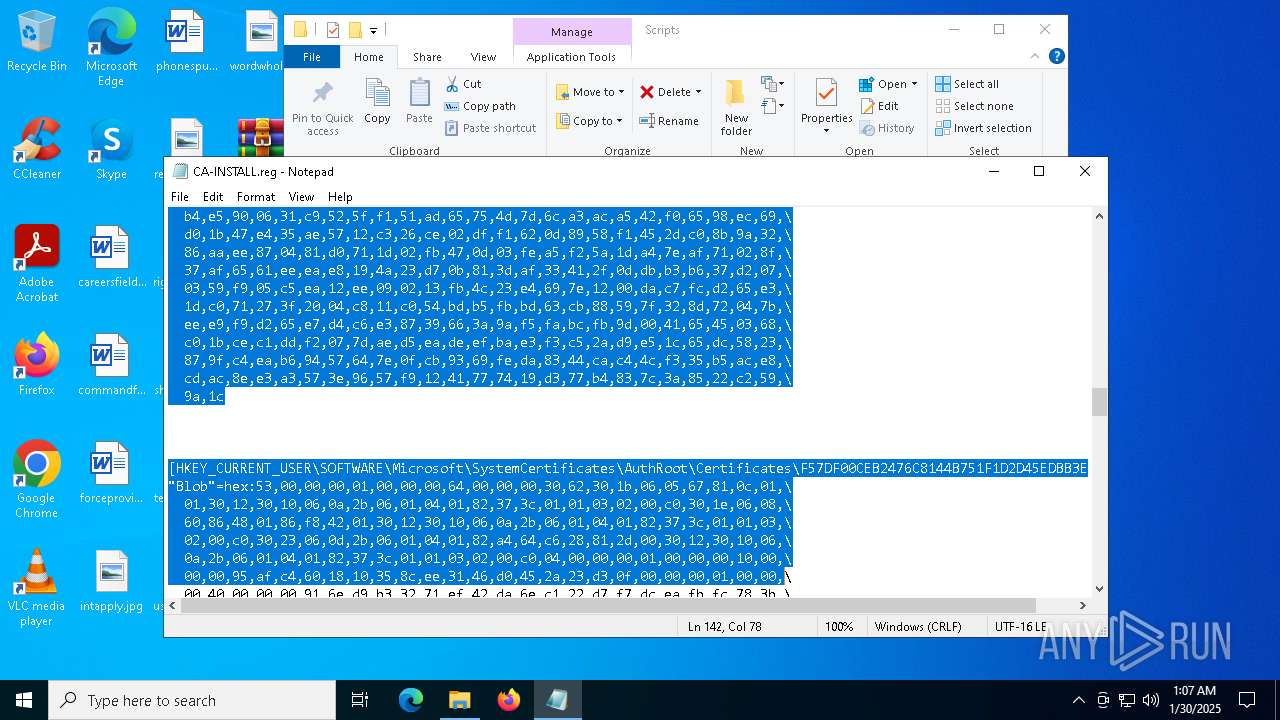
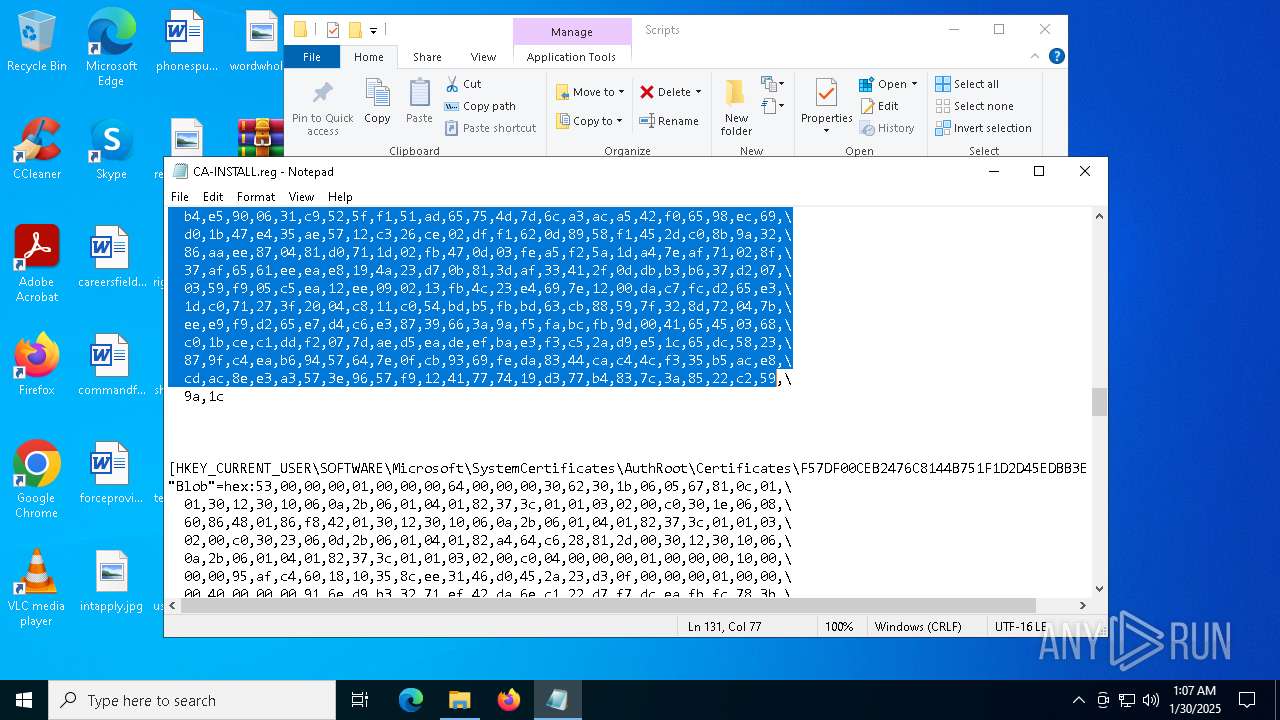
Adds/modifies Windows certificates
- regedit.exe (PID: 556)
- regedit.exe (PID: 6304)
Changes settings of the software policy
- regedit.exe (PID: 556)
- regedit.exe (PID: 6304)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 3664)
INFO
Manual execution by a user
- sirhurt.exe (PID: 5300)
- sirhurt.exe (PID: 1580)
- sirhurt.exe (PID: 2572)
- sirhurt.exe (PID: 3260)
- sirhurt.exe (PID: 2940)
- sirhurt.exe (PID: 4308)
- rundll32.exe (PID: 6592)
- Certmgr.exe (PID: 6648)
- notepad.exe (PID: 6772)
- firefox.exe (PID: 6876)
The sample compiled with english language support
- WinRAR.exe (PID: 4724)
- sirhurt.exe (PID: 1580)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4724)
Process checks whether UAC notifications are on
- sirhurt.exe (PID: 1580)
- sirhurt.exe (PID: 2940)
- sirhurt.exe (PID: 4308)
Checks supported languages
- sirhurt.exe (PID: 1580)
- mode.com (PID: 3988)
- sirhurt.exe (PID: 4308)
- sirhurt.exe (PID: 2940)
- mode.com (PID: 6148)
- mode.com (PID: 6248)
- Certmgr.exe (PID: 6648)
- ShellExperienceHost.exe (PID: 3664)
Reads the machine GUID from the registry
- sirhurt.exe (PID: 1580)
- sirhurt.exe (PID: 4308)
- sirhurt.exe (PID: 2940)
Reads the computer name
- sirhurt.exe (PID: 1580)
- sirhurt.exe (PID: 2940)
- sirhurt.exe (PID: 4308)
- Certmgr.exe (PID: 6648)
- ShellExperienceHost.exe (PID: 3664)
Create files in a temporary directory
- sirhurt.exe (PID: 1580)
Creates files in the program directory
- sirhurt.exe (PID: 1580)
- dllhost.exe (PID: 5560)
Starts MODE.COM to configure console settings
- mode.com (PID: 3988)
- mode.com (PID: 6148)
- mode.com (PID: 6248)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 6592)
- notepad.exe (PID: 6772)
- dllhost.exe (PID: 5560)
- dllhost.exe (PID: 5828)
Reads the software policy settings
- rundll32.exe (PID: 6592)
Application launched itself
- firefox.exe (PID: 6896)
- firefox.exe (PID: 6876)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 1515037 |
| UncompressedSize: | 4970120 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | sirhurt.dll |
Total processes
168
Monitored processes
44
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 420 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sirhurt.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
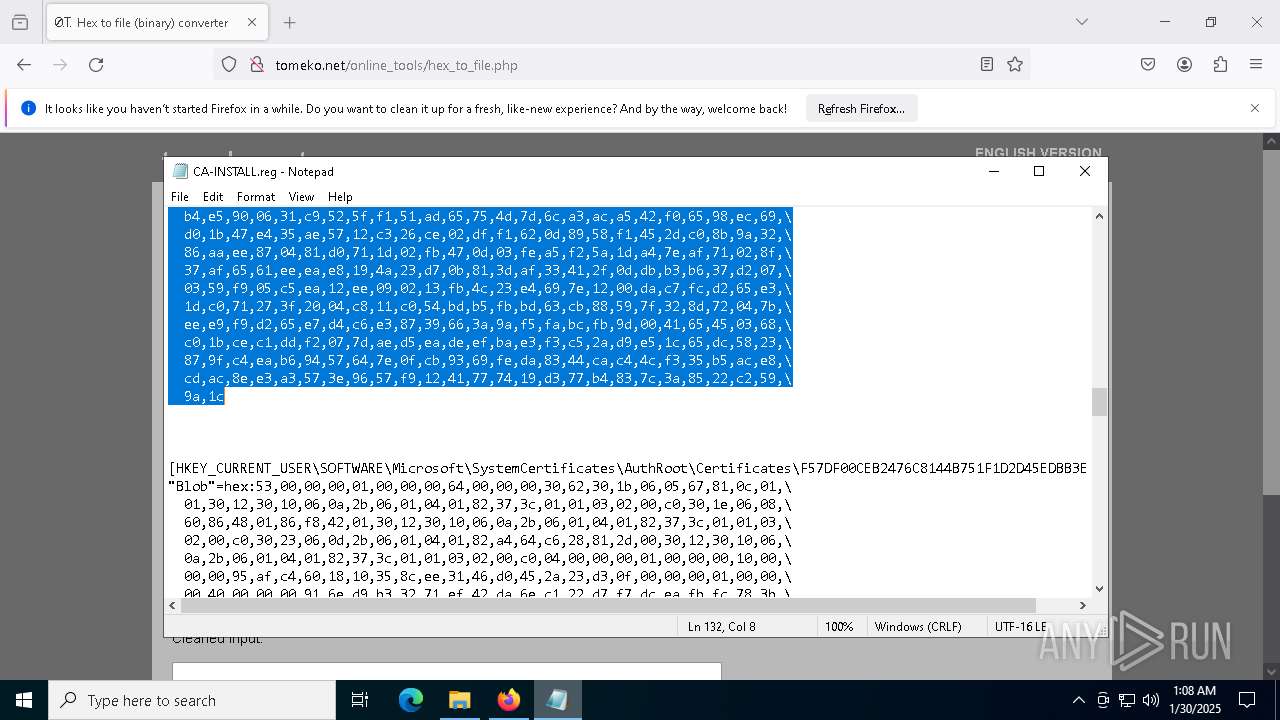
| 556 | regedit.exe /s "C:\Program Files (x86)\rsTrust\Scripts\CA-INSTALL.reg" | C:\Windows\regedit.exe | — | sirhurt.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1580 | "C:\Users\admin\Desktop\SirHurt V5\sirhurt.exe" | C:\Users\admin\Desktop\SirHurt V5\sirhurt.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2424 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sirhurt.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2512 | cmd.exe /C "C:\Program Files (x86)\rsTrust\Scripts\CA-INSTALL.bat" >nul 2>&1 | C:\Windows\System32\cmd.exe | — | sirhurt.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2572 | "C:\Users\admin\Desktop\SirHurt V5\sirhurt.exe" | C:\Users\admin\Desktop\SirHurt V5\sirhurt.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2940 | cmd.exe /C "C:\Program Files (x86)\rsTrust\Scripts\CA-INSTALL.bat" >nul 2>&1 | C:\Windows\System32\cmd.exe | — | sirhurt.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2940 | "C:\Users\admin\Desktop\SirHurt V5\sirhurt.exe" | C:\Users\admin\Desktop\SirHurt V5\sirhurt.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225786 Modules
| |||||||||||||||
| 2976 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4864 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 4944 -prefMapHandle 4860 -prefsLen 36588 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {c27ccda4-64b4-4819-b1a3-d7d184ddac8c} 6896 "\\.\pipe\gecko-crash-server-pipe.6896" 2b39636b510 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 1 Version: 123.0 Modules
| |||||||||||||||
| 3260 | "C:\Users\admin\Desktop\SirHurt V5\sirhurt.exe" | C:\Users\admin\Desktop\SirHurt V5\sirhurt.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
22 415
Read events
22 363
Write events
39
Delete events
13
Modification events
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\SirHurt V5.rar | |||
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
9
Suspicious files
211
Text files
74
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
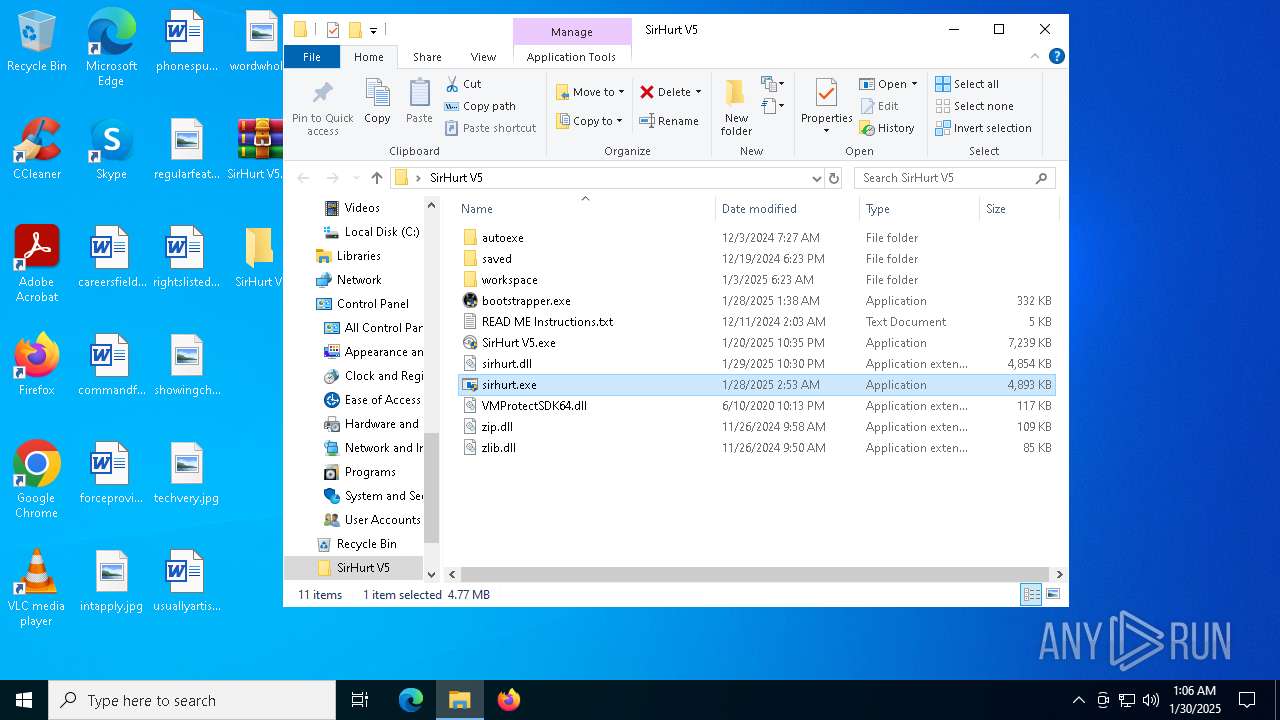
| 4724 | WinRAR.exe | C:\Users\admin\Desktop\SirHurt V5\sirhurt.dll | executable | |
MD5:4640394983E2F1E5555A687665D25BC1 | SHA256:016CDE43A2FEF967B7E14BBB346A2AF3ADBDC06C972F869B36D037A61470772C | |||
| 4724 | WinRAR.exe | C:\Users\admin\Desktop\SirHurt V5\bootstrapper.exe | executable | |
MD5:36080AE944ECC9AC301C128E8CB696A4 | SHA256:F8C112998BAE986FDF5DD33CB8FB819F963B50C0F5A3F406F5333B242124793A | |||
| 4724 | WinRAR.exe | C:\Users\admin\Desktop\SirHurt V5\sirhurt.exe | executable | |
MD5:FD2EFF183BF443715AED9E08F67B367A | SHA256:397E1422413B38E64BAD8E150A57C923FD49F37B1F6F5A3E4BB1878DCD5F35E2 | |||
| 1580 | sirhurt.exe | C:\Users\admin\AppData\Local\Temp\rstrust_temp.zip | compressed | |
MD5:E10D9C8A96EC507F2CE6BF74AF9D4D4D | SHA256:3ACF202A25C28FEC3001A3A0E3345121DA75C6D92C4F287B0B0634610FE883F2 | |||
| 1580 | sirhurt.exe | C:\Program Files (x86)\rsTrust\Scripts\0-Pikachu_Test_CA_RSA.crt | text | |
MD5:C6B82192E9F8FCF65608A1A5640F706B | SHA256:D49701E4F6B57229FE7623A7355EA1B2AC14AD3D5A387D30387A3A82E403553E | |||
| 4724 | WinRAR.exe | C:\Users\admin\Desktop\SirHurt V5\VMProtectSDK64.dll | executable | |
MD5:8952450F3D98016016682A6B0B716518 | SHA256:A56239B26392A8EC49A47D27B0632B65A3F98A2735BF60DCE66139A71FF804FC | |||
| 4724 | WinRAR.exe | C:\Users\admin\Desktop\SirHurt V5\zip.dll | executable | |
MD5:D18F84C69C2931986B3284AC0E0BEE00 | SHA256:A7EC733AF1BA0172ED54F9A714C5DC4E6901CC1FD7DC8D3B17D195FACA69C22F | |||
| 4724 | WinRAR.exe | C:\Users\admin\Desktop\SirHurt V5\SirHurt V5.exe | executable | |
MD5:6A06AF324DAF89CE137F3959A4C4DA20 | SHA256:BA9B5EE8F7DFDEF785D87A9884BED1AB10AEE870E415ED9263454143A227C557 | |||
| 1580 | sirhurt.exe | C:\Program Files (x86)\rsTrust\Scripts\2-Pikachu_Time_Sub_CA-G2.crl | text | |
MD5:AEE260B1675E4E2C28EAA9D5BA8DAA53 | SHA256:7373E065047C75F671FA75BAC5A65E78FAD71ECB59FF2CC7E1DE89D4C7207884 | |||
| 1580 | sirhurt.exe | C:\Program Files (x86)\rsTrust\Scripts\0-Pikachu_Test_CA_RSA-G1.crl | text | |
MD5:51F968C58DCD358393EA98DE5B0D340E | SHA256:1C83C4B49A985BA87BA0CD1BD0D65DB972F1F3FF5C4772744C16A093F7824EC5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
45
TCP/UDP connections
107
DNS requests
135
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6896 | firefox.exe | POST | 200 | 2.19.120.159:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
6896 | firefox.exe | POST | 200 | 172.217.16.195:80 | http://o.pki.goog/wr2 | unknown | — | — | whitelisted |
6896 | firefox.exe | POST | 200 | 172.217.16.195:80 | http://o.pki.goog/wr2 | unknown | — | — | whitelisted |
6896 | firefox.exe | POST | 200 | 172.217.16.195:80 | http://o.pki.goog/wr2 | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.78.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3416 | svchost.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6364 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.78.42:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
3416 | svchost.exe | 95.101.78.42:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.209.214.100:80 | www.microsoft.com | PT. Telekomunikasi Selular | ID | whitelisted |
3416 | svchost.exe | 23.209.214.100:80 | www.microsoft.com | PT. Telekomunikasi Selular | ID | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.21.65.132:443 | www.bing.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.sirhurt.net |
| unknown |
sirhurt.net |
| unknown |
Threats
Process | Message |
|---|---|
regedit.exe | REGEDIT: CreateFile failed, GetLastError() = 2
|
regedit.exe | REGEDIT: CreateFile failed, GetLastError() = 2
|
regedit.exe | REGEDIT: CreateFile failed, GetLastError() = 2
|