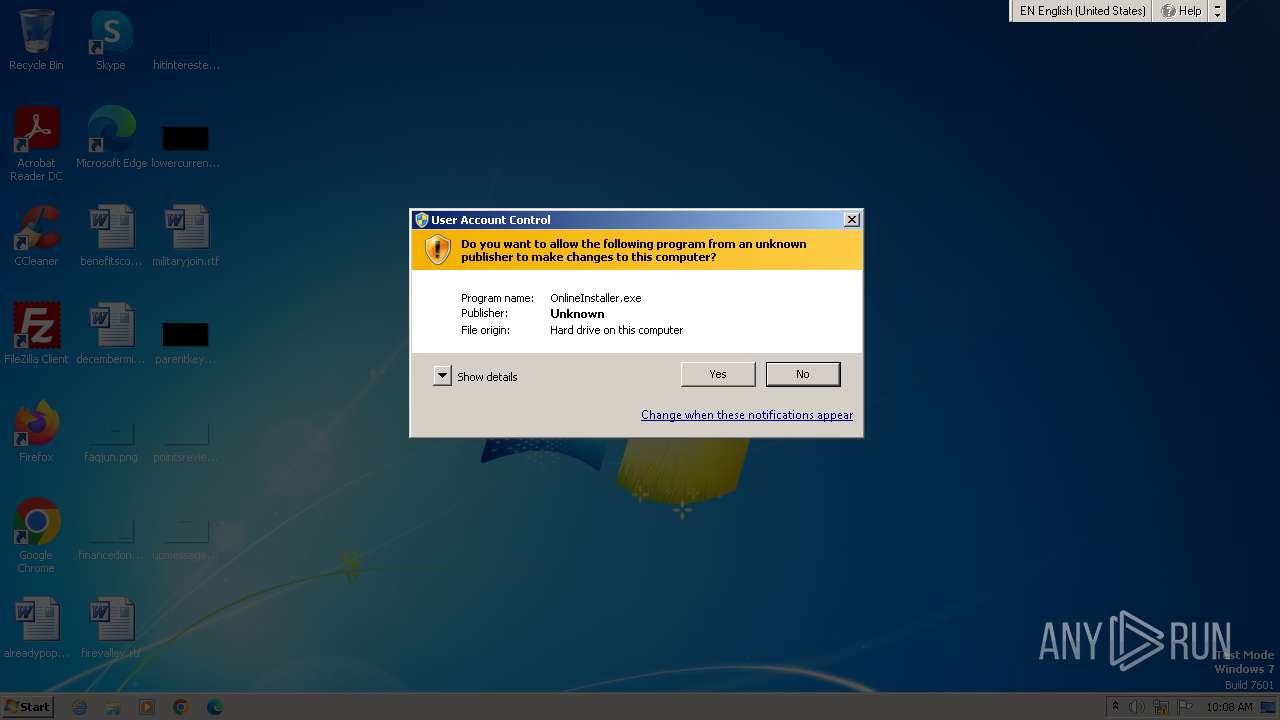
| File name: | OnlineInstaller.exe |
| Full analysis: | https://app.any.run/tasks/055e3b2c-5051-4afb-9146-b8b4ddf155b1 |
| Verdict: | Malicious activity |
| Threats: | A rootkit is a type of malicious software designed to provide unauthorized administrative-level access to a computer or network while concealing its presence. Rootkits are tools used by cybercriminals to hide their activities, including keyloggers, spyware, and other malware, often enabling long-term system exploitation. |
| Analysis date: | December 14, 2024, 10:08:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 4B042BFD9C11AB6A3FB78FA5C34F55D0 |
| SHA1: | B0F506640C205D3FBCFE90BDE81E49934B870EAB |
| SHA256: | 59C662A5207C6806046205348B22EE45DA3F685FE022556716DBBD6643E61834 |
| SSDEEP: | 98304:ghXqJiXwwhwvxR7FI6wYroMUQrYeoFj6bjsKzZx7T7:ghXqsX3hs79bxiEbgKX7 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts itself from another location
- OnlineInstaller.exe (PID: 2832)
Executable content was dropped or overwritten
- OnlineInstaller.exe (PID: 2832)
- OnlineInstaller.tmp (PID: 2052)
Starts application with an unusual extension
- OnlineInstaller.exe (PID: 2832)
Drops a system driver (possible attempt to evade defenses)
- OnlineInstaller.tmp (PID: 2052)
Creates files in the driver directory
- OnlineInstaller.tmp (PID: 2052)
Reads the Internet Settings
- OnlineInstaller.exe (PID: 2832)
Reads security settings of Internet Explorer
- OnlineInstaller.exe (PID: 2832)
INFO
Reads the computer name
- OnlineInstaller.exe (PID: 2832)
- OnlineInstaller.tmp (PID: 2052)
- wmpnscfg.exe (PID: 2648)
Create files in a temporary directory
- OnlineInstaller.exe (PID: 2832)
Checks supported languages
- OnlineInstaller.tmp (PID: 2052)
- OnlineInstaller.exe (PID: 2832)
- wmpnscfg.exe (PID: 2648)
The sample compiled with english language support
- OnlineInstaller.tmp (PID: 2052)
Checks proxy server information
- OnlineInstaller.exe (PID: 2832)
Reads the machine GUID from the registry
- OnlineInstaller.exe (PID: 2832)
Creates files or folders in the user directory
- OnlineInstaller.exe (PID: 2832)
Manual execution by a user
- wmpnscfg.exe (PID: 2648)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:03:21 12:57:55+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 423424 |
| InitializedDataSize: | 3337216 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x534e1 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
41
Monitored processes
4
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1016 | "C:\Users\admin\Desktop\OnlineInstaller.exe" | C:\Users\admin\Desktop\OnlineInstaller.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2052 | C:\Users\admin\AppData\Local\Temp\OnlineInstaller.tmp -install | C:\Users\admin\AppData\Local\Temp\OnlineInstaller.tmp | OnlineInstaller.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2648 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2832 | "C:\Users\admin\Desktop\OnlineInstaller.exe" | C:\Users\admin\Desktop\OnlineInstaller.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
481
Read events
454
Write events
21
Delete events
6
Modification events
| (PID) Process: | (2832) OnlineInstaller.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2832) OnlineInstaller.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2832) OnlineInstaller.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2052) OnlineInstaller.tmp | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\CrashControl |
| Operation: | write | Name: | DumpFilters |
Value: dumpfve.sys | |||
| (PID) Process: | (2832) OnlineInstaller.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2832) OnlineInstaller.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyServer |
Value: | |||
| (PID) Process: | (2832) OnlineInstaller.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyOverride |
Value: | |||
| (PID) Process: | (2832) OnlineInstaller.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoConfigURL |
Value: | |||
| (PID) Process: | (2832) OnlineInstaller.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoDetect |
Value: | |||
| (PID) Process: | (2832) OnlineInstaller.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005F010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
5
Suspicious files
3
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2832 | OnlineInstaller.exe | C:\Users\admin\AppData\Local\Temp\OnlineInstaller.tmp | executable | |
MD5:4B042BFD9C11AB6A3FB78FA5C34F55D0 | SHA256:59C662A5207C6806046205348B22EE45DA3F685FE022556716DBBD6643E61834 | |||
| 2052 | OnlineInstaller.tmp | C:\Windows\System32\KeyHook32.dll | executable | |
MD5:B67D42DD62B273A1266A62EC87950E33 | SHA256:C038A6738563680CB3AB9653D6D24959C084B2ACF4BADFB8E0233DD52EDF332B | |||
| 2052 | OnlineInstaller.tmp | C:\Windows\System32\spoolsr.exe | executable | |
MD5:4F63269D5E1C9C40E74973E2E2380FF2 | SHA256:DF62657C3955A7C1D942B2BDC2712B45731697FE08C9F35F0AC763805698832A | |||
| 2052 | OnlineInstaller.tmp | C:\Windows\System32\usp20.dll | executable | |
MD5:F55888F0327532F7E6867DD70C8502F3 | SHA256:238A1A558D41CE8CDE8E8E6D6C10E39E89CA688434A52CB2327C9DDD5499414C | |||
| 2052 | OnlineInstaller.tmp | C:\Windows\System32\KH.dat | binary | |
MD5:0E12D17BCA64049853F35A35925E410D | SHA256:1C25850A193A8F7C0A7022592EC7F51210A106291AB5538D999421F92B7108DB | |||
| 2832 | OnlineInstaller.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\XJTQ7C6D.txt | text | |
MD5:EF3B0DF31FE07C0562FCEBCCEDEA1767 | SHA256:8C5A77B648A78ED3EE4C6D6AC3F813FD90393BEEF8DF06B1E2489B3092949E03 | |||
| 2832 | OnlineInstaller.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\BRZQDM7V.txt | text | |
MD5:5CD8C53DB8388BD25F7081692A98B41A | SHA256:2BBFA9D74DD9666CF197FCD0CFB7AFE7DC8B6DCB6B2F60E247115528FB7CD15F | |||
| 2052 | OnlineInstaller.tmp | C:\Windows\System32\drivers\iaStorE.sys | executable | |
MD5:6A421F96BE2CA0518C693B24E23CC636 | SHA256:0B7DF102204E60711048FAACB41E6323B5F429B1298EC8FA0A919B1F5CDDD34A | |||
| 2052 | OnlineInstaller.tmp | C:\Windows\System32\UP.dat | binary | |
MD5:398D8B564C8C034D3943764D2617AD01 | SHA256:F3DDEDCEE0F043D859F702674B7A169B9FFA9F23B9583D5B17EA4A01F79B9D08 | |||
| 2052 | OnlineInstaller.tmp | C:\Windows\System32\MS.dat | binary | |
MD5:4AF0CC26DEA802706A30A3C73F370FDA | SHA256:B213DC28EF8791B4D4491634783FC33CB0CF59DF642A1C3004FDD4A564743FBC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
6
DNS requests
2
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2832 | OnlineInstaller.exe | POST | 200 | 35.164.78.200:80 | http://iostream.system.band/dump/io/time.php | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1108 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
2832 | OnlineInstaller.exe | 35.164.78.200:80 | iostream.system.band | AMAZON-02 | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
iostream.system.band |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2832 | OnlineInstaller.exe | A Network Trojan was detected | ET MALWARE Possible Compromised Host AnubisNetworks Sinkhole Cookie Value Snkz |