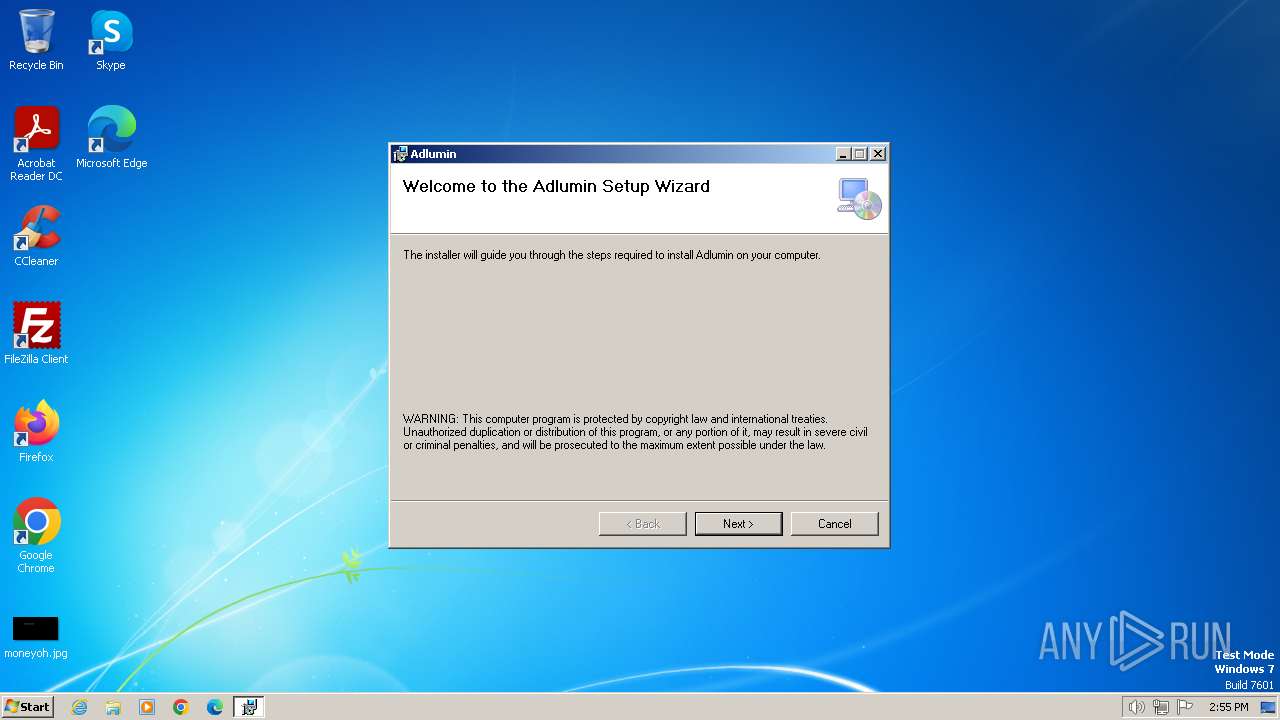
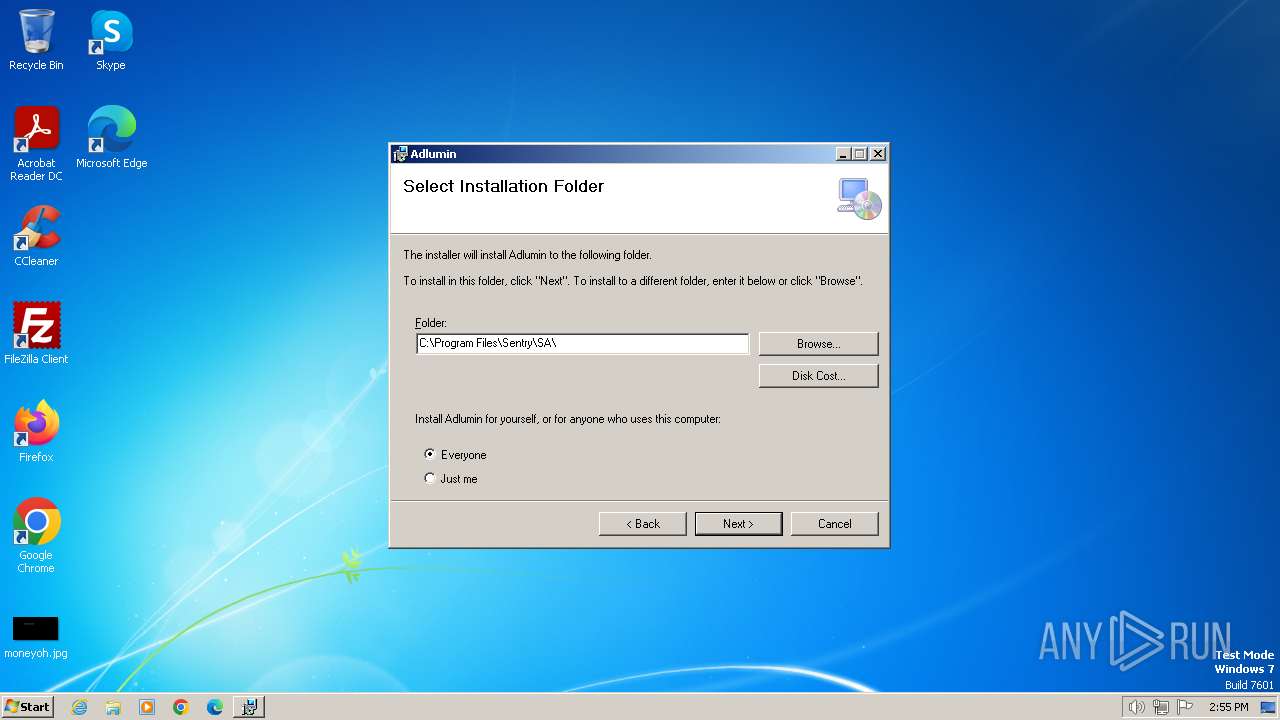
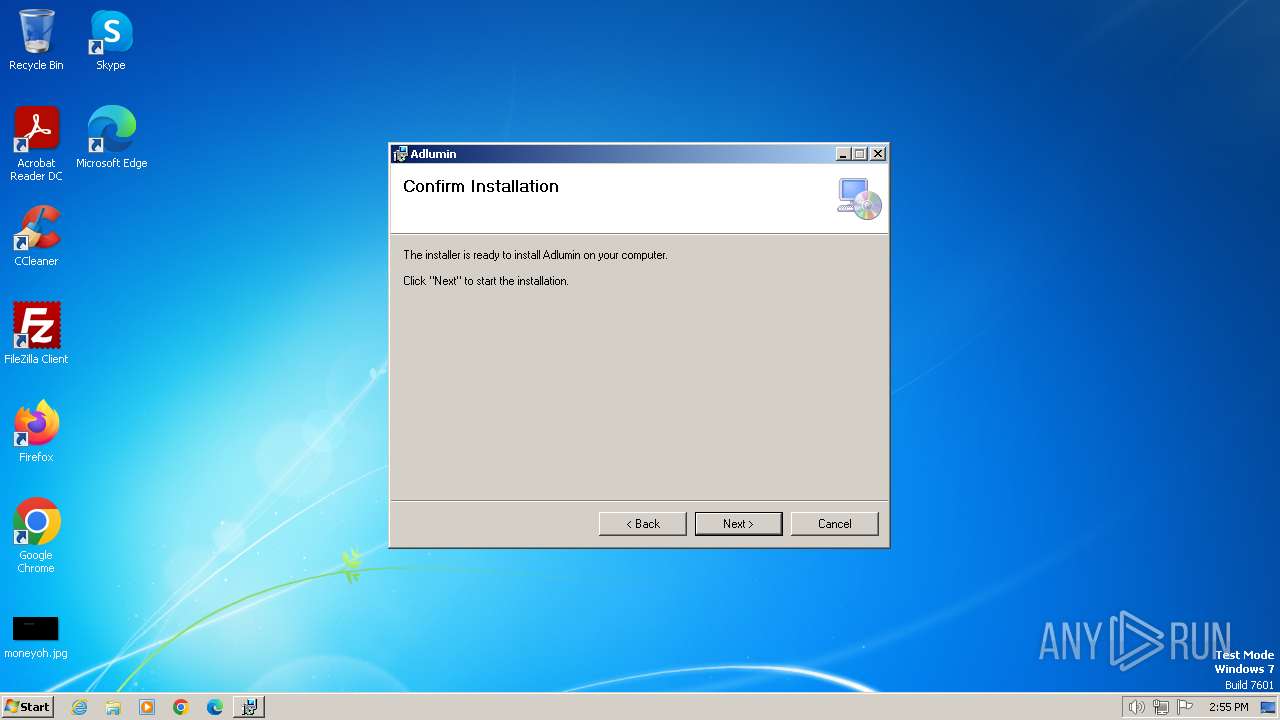
| File name: | AdluminInstaller.msi |
| Full analysis: | https://app.any.run/tasks/c2d2b7cf-e102-45ae-a7a1-804e2b5de5e7 |
| Verdict: | Malicious activity |
| Analysis date: | July 05, 2024, 13:55:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Create Time/Date: Mon Jun 21 07:00:00 1999, Name of Creating Application: Windows Installer, Security: 1, Code page: 1252, Template: Intel;1033, Number of Pages: 200, Revision Number: {42ABFE88-767C-40F1-A093-C641BCD06347}, Title: Adlumin, Author: Adlumin, Inc, Comments: Adlumin messaging service, Number of Words: 2, Last Saved Time/Date: Tue Apr 30 07:31:17 2024, Last Printed: Tue Apr 30 07:31:17 2024 |
| MD5: | 4DF0568D6AF367F6600C50F04DB9524C |
| SHA1: | 44FC39A857AE35F801B3D2A651E482EBEAE37CD6 |
| SHA256: | 59BBC6D93AFD16A5AF3792BE9A95A667ECFDCEEC5E55EC11AB4579C51EF21AC4 |
| SSDEEP: | 98304:8giRM4v1dHhKqgpW4pUT0votoe80PTAD8z0xlVWH3DenYeKjOF6RKQBwFEUrrwck:4KAuAiwB1V |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 3432)
- Sysmon.exe (PID: 1620)
Application was injected by another process
- sppsvc.exe (PID: 3032)
- WmiPrvSE.exe (PID: 3956)
- spoolsv.exe (PID: 1220)
- svchost.exe (PID: 816)
- svchost.exe (PID: 1372)
- svchost.exe (PID: 1060)
- svchost.exe (PID: 844)
- svchost.exe (PID: 752)
- lsass.exe (PID: 480)
Runs injected code in another process
- Sysmon.exe (PID: 2328)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 3788)
- cmd.exe (PID: 3448)
- cmd.exe (PID: 3620)
Creates a writable file in the system directory
- sentryagent.exe (PID: 2544)
SUSPICIOUS
Process drops legitimate windows executable
- msiexec.exe (PID: 3380)
- msiexec.exe (PID: 3432)
Executes as Windows Service
- VSSVC.exe (PID: 2748)
- sentryagent.exe (PID: 2544)
- Sysmon.exe (PID: 2328)
Checks Windows Trust Settings
- msiexec.exe (PID: 3432)
- sentryagent.exe (PID: 2544)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 3432)
- sentryagent.exe (PID: 2544)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 3432)
- Sysmon.exe (PID: 1620)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 524)
- sentryagent.exe (PID: 2544)
Creates file in the systems drive root
- sentryagent.exe (PID: 2544)
Executable content was dropped or overwritten
- Sysmon.exe (PID: 1620)
Starts SC.EXE for service management
- sentryagent.exe (PID: 2544)
- cmd.exe (PID: 2332)
Starts itself from another location
- Sysmon.exe (PID: 1620)
Uses WEVTUTIL.EXE to remove publishers and event logs from the manifest
- Sysmon.exe (PID: 1072)
Uses WEVTUTIL.EXE to install publishers and event logs from the manifest
- Sysmon.exe (PID: 1072)
Creates or modifies Windows services
- sentryagent.exe (PID: 2544)
Process uses IPCONFIG to discover network configuration
- sentryagent.exe (PID: 2544)
Starts CMD.EXE for commands execution
- sentryagent.exe (PID: 2544)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 3836)
Adds/modifies Windows certificates
- sentryagent.exe (PID: 2544)
INFO
Reads the software policy settings
- msiexec.exe (PID: 3380)
- msiexec.exe (PID: 3432)
- lsass.exe (PID: 480)
- sentryagent.exe (PID: 2544)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 3380)
Reads the machine GUID from the registry
- msiexec.exe (PID: 3432)
- msiexec.exe (PID: 3172)
- msiexec.exe (PID: 3976)
- msiexec.exe (PID: 524)
- sentryagent.exe (PID: 2544)
- Sysmon.exe (PID: 1620)
- Sysmon.exe (PID: 1072)
- Sysmon.exe (PID: 2328)
Reads the computer name
- msiexec.exe (PID: 3432)
- msiexec.exe (PID: 3172)
- msiexec.exe (PID: 3976)
- msiexec.exe (PID: 524)
- sentryagent.exe (PID: 2544)
- Sysmon.exe (PID: 1620)
- Sysmon.exe (PID: 1072)
- Sysmon.exe (PID: 2328)
Checks supported languages
- msiexec.exe (PID: 3432)
- msiexec.exe (PID: 3172)
- msiexec.exe (PID: 3976)
- sentryagent.exe (PID: 2544)
- msiexec.exe (PID: 524)
- Sysmon.exe (PID: 1072)
- Sysmon.exe (PID: 1620)
- Sysmon.exe (PID: 2328)
Create files in a temporary directory
- msiexec.exe (PID: 3172)
- msiexec.exe (PID: 3976)
- msiexec.exe (PID: 3432)
Drops the executable file immediately after the start
- msiexec.exe (PID: 3380)
Application launched itself
- msiexec.exe (PID: 3432)
Executable content was dropped or overwritten
- msiexec.exe (PID: 3380)
- msiexec.exe (PID: 3432)
Creates files in the program directory
- svchost.exe (PID: 1372)
- sentryagent.exe (PID: 2544)
Reads the time zone
- svchost.exe (PID: 752)
- WmiPrvSE.exe (PID: 3956)
- Sysmon.exe (PID: 2328)
Creates a software uninstall entry
- msiexec.exe (PID: 3432)
Reads Environment values
- sentryagent.exe (PID: 2544)
Creates a writable file in the system directory
- svchost.exe (PID: 752)
- svchost.exe (PID: 844)
- lsass.exe (PID: 480)
Reads CPU info
- Sysmon.exe (PID: 2328)
- sentryagent.exe (PID: 2544)
Reads Windows Product ID
- WmiPrvSE.exe (PID: 3956)
Disables trace logs
- sentryagent.exe (PID: 2544)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (90.2) |
|---|---|---|
| .msp | | | Windows Installer Patch (8.4) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CreateDate: | 1999:06:21 07:00:00 |
|---|---|
| Software: | Windows Installer |
| Security: | Password protected |
| CodePage: | Windows Latin 1 (Western European) |
| Template: | Intel;1033 |
| Pages: | 200 |
| RevisionNumber: | {42ABFE88-767C-40F1-A093-C641BCD06347} |
| Title: | Adlumin |
| Subject: | - |
| Author: | Adlumin, Inc |
| Keywords: | - |
| Comments: | Adlumin messaging service |
| Words: | 2 |
| ModifyDate: | 2024:05:31 07:31:17 |
| LastPrinted: | 2024:05:31 07:31:17 |
Total processes
90
Monitored processes
48
Malicious processes
5
Suspicious processes
9
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 324 | "C:\Windows\system32\wevtutil.exe" im "C:\Windows\TEMP\MAN523F.tmp" | C:\Windows\System32\wevtutil.exe | — | Sysmon.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Eventing Command Line Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 480 | C:\Windows\system32\lsass.exe | C:\Windows\System32\lsass.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Local Security Authority Process Version: 6.1.7601.24545 (win7sp1_ldr_escrow.200102-1707) Modules
| |||||||||||||||
| 524 | C:\Windows\system32\MsiExec.exe -Embedding 20495C5E4A2BCF0EF54EB1D02246A8A3 E Global\MSI0000 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 724 | reg add "HKLM\Software\Wow6432Node\Policies\Microsoft\Microsoft Antimalware" /v ThreatFileHashLogging /t REG_DWORD /d 1 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 752 | C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestricted | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 816 | C:\Windows\system32\svchost.exe -k LocalService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 844 | C:\Windows\system32\svchost.exe -k netsvcs | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 952 | "sc" qc Sysmon | C:\Windows\System32\sc.exe | — | sentryagent.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 972 | auditpol /set /subcategory:"Other Account Logon Events" /success:enable /failure:enable | C:\Windows\System32\auditpol.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Audit Policy Program Exit code: 0 Version: 6.1.7601.24545 (win7sp1_ldr_escrow.200102-1707) Modules
| |||||||||||||||
| 1060 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
38 704
Read events
38 055
Write events
590
Delete events
59
Modification events
| (PID) Process: | (3380) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3432) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000F8B85D0DE3CEDA01680D0000C00A0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3432) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000F8B85D0DE3CEDA01680D0000C00A0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3432) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 75 | |||
| (PID) Process: | (3432) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4000000000000000BE121A0EE3CEDA01680D0000C00A0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3432) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000018751C0EE3CEDA01680D0000840B0000E8030000010000000000000000000000E9A079145E72B8409F054EAC578C4CEF0000000000000000 | |||
| (PID) Process: | (844) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\WMI Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000080FE250EE3CEDA014C030000B0040000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1060) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\System Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000080FE250EE3CEDA0124040000F0050000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2748) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000080FE250EE3CEDA01BC0A0000780B0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2748) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000080FE250EE3CEDA01BC0A00005C0C0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
28
Suspicious files
36
Text files
16
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3432 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 1060 | svchost.exe | C:\Windows\system32\CatRoot2\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\catdb | — | |
MD5:— | SHA256:— | |||
| 3432 | msiexec.exe | C:\Windows\Installer\53eb6.msi | — | |
MD5:— | SHA256:— | |||
| 3380 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIEABB.tmp | executable | |
MD5:B77A2A2768B9CC78A71BBFFB9812B978 | SHA256:F74C97B1A53541B059D3BFAFE41A79005CE5065F8210D7DE9F1B600DC4E28AA0 | |||
| 1060 | svchost.exe | C:\Windows\SERVIC~2\NETWOR~1\AppData\Local\Temp\Cab296B.tmp | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3380 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIEA5C.tmp | executable | |
MD5:B77A2A2768B9CC78A71BBFFB9812B978 | SHA256:F74C97B1A53541B059D3BFAFE41A79005CE5065F8210D7DE9F1B600DC4E28AA0 | |||
| 1372 | svchost.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:3A77A559E3B07BBD7A93662DB0D76EBC | SHA256:A595B430358B4737810D83B5284678B122473364F60DC45234D4FD632341F7CE | |||
| 1372 | svchost.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:DA719408F612ADD100833AADED818178 | SHA256:7EE16D568447D0581553F1D8883BD9703D906C7705433A698CDE2FF4F18727DA | |||
| 1060 | svchost.exe | C:\Windows\SERVIC~2\NETWOR~1\AppData\Local\Temp\Tar296C.tmp | cat | |
MD5:78785956AB4E54D6116D673C3491EDFF | SHA256:C514DBDBB13632CBB378C59086C1EBB0BC9B25FFB0A349F2B052B065C0D913E6 | |||
| 1372 | svchost.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\21253908F3CB05D51B1C2DA8B681A785 | der | |
MD5:979F91388D4DF2F2D68497400C9830DD | SHA256:A9F27E26AA818BC97449D30D5707254EDCA571D21D36B4576C7CD9A56FB18BC5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
25
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
2544 | sentryagent.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d279bd661a9ff8ae | unknown | — | — | unknown |
2544 | sentryagent.exe | GET | — | 104.18.38.233:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSdE3gf41WAic8Uh9lF92%2BIJqh5qwQUMuuSmv81lkgvKEBCcCA2kVwXheYCEGIdbQxSAZ47kHkVIIkhHAo%3D | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?bc7dc717ba1916bd | unknown | — | — | unknown |
2544 | sentryagent.exe | GET | 200 | 104.18.38.233:80 | http://crl.sectigo.com/SectigoPublicCodeSigningRootR46.crl | unknown | — | — | unknown |
2544 | sentryagent.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEEj8k7RgVZSNNqfJionWlBY%3D | unknown | — | — | unknown |
2544 | sentryagent.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQVD%2BnGf79Hpedv3mhy6uKMVZkPCQQUDyrLIIcouOxvSK4rVKYpqhekzQwCEFRu%2BQqDf5E3Ia%2BuOtsz8VA%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 239.255.255.250:3702 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1372 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1372 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1372 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
1372 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
master-ingest-4.securityeco.com |
| malicious |
master-ingest-1.securityeco.com |
| malicious |
255.100.168.192.in-addr.arpa |
| unknown |
2.100.168.192.in-addr.arpa |
| unknown |
186.240.85.35.in-addr.arpa |
| unknown |
39.108.212.34.in-addr.arpa |
| unknown |
Threats
Process | Message |
|---|---|
svchost.exe | base\diagnosis\diagtrack\include\SettingsDownloader.h(237)\diagtrack.dll!7168FFE8: (caller: 7168B65A) ReturnHr[PreRelease](20) tid(604) 80072EE2 |
svchost.exe | base\diagnosis\diagtrack\matchengine\asimovuploader.cpp(1592)\diagtrack.dll!716A7440: (caller: 716A76F0) ReturnHr[PreRelease](21) tid(604) 80070510 The requested file operation failed because the storage policy blocks that type of file. For more information, contact your system administrator.
|
svchost.exe | base\diagnosis\diagtrack\engine\settingsmanager.cpp(843)\diagtrack.dll!7168B77D: (caller: 71689D61) ReturnHr[PreRelease](22) tid(604) 80072EE2 |
svchost.exe | base\diagnosis\diagtrack\engine\settingsmanager.cpp(127)\diagtrack.dll!71689D76: (caller: 7167C7FD) LogHr(9) tid(604) 80072EE2 |
svchost.exe | base\diagnosis\diagtrack\matchengine\asimovuploader.cpp(1592)\diagtrack.dll!716A7440: (caller: 716A76F0) ReturnHr[PreRelease](23) tid(604) 80070510 The requested file operation failed because the storage policy blocks that type of file. For more information, contact your system administrator.
|
svchost.exe | base\diagnosis\diagtrack\engine\settingsmanager.cpp(588)\diagtrack.dll!7168AD66: (caller: 7168A8E9) ReturnHr[PreRelease](24) tid(604) 80070002 The system cannot find the file specified.
|
svchost.exe | base\diagnosis\diagtrack\engine\settingsmanager.cpp(506)\diagtrack.dll!7168A900: (caller: 7168A0B2) LogHr(10) tid(604) 80070002 The system cannot find the file specified.
|
svchost.exe | base\diagnosis\diagtrack\include\Utils.h(2581)\diagtrack.dll!71676EF3: (caller: 7167DC9B) ReturnHr[PreRelease](25) tid(604) 800401F3 Invalid class string
|
svchost.exe | base\diagnosis\diagtrack\include\Utils.h(2581)\diagtrack.dll!71676EF3: (caller: 7167DC9B) ReturnHr[PreRelease](26) tid(604) 800401F3 Invalid class string
|
svchost.exe | base\diagnosis\diagtrack\include\Utils.h(2581)\diagtrack.dll!71676EF3: (caller: 7167DC9B) ReturnHr[PreRelease](27) tid(604) 800401F3 Invalid class string
|