| File name: | 59a3f7c8511f22a6e48ec6a8f058fefaa3c881c0577bde3cf3ba34ef5688990b.msi |
| Full analysis: | https://app.any.run/tasks/d5be0005-2f79-4c73-8b2c-cdb54b14ef85 |
| Verdict: | Malicious activity |
| Analysis date: | January 14, 2022, 19:22:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Last Printed: Fri Dec 11 11:47:44 2009, Create Time/Date: Fri Dec 11 11:47:44 2009, Last Saved Time/Date: Fri Sep 18 15:06:51 2020, Security: 0, Code page: 1252, Revision Number: {F4F1A063-F85C-44FB-889E-0A184A11BD00}, Number of Words: 10, Subject: Carregando.., Author: FDSDRFGSEWRR, Name of Creating Application: Advanced Installer 18.1 build 4fb1edbd, Template: ;1046, Comments: A base dados do instalador contm a lgica e os dados necessrios para instalar o Carregando..., Title: Installation Database, Keywords: Installer, MSI, Database, Number of Pages: 200 |
| MD5: | C86C9CC460DA0B7D5A09C8096500C4AD |
| SHA1: | 6414D036E3963F0844311329FA921D58A9E7BEDF |
| SHA256: | 59A3F7C8511F22A6E48EC6A8F058FEFAA3C881C0577BDE3CF3BA34EF5688990B |
| SSDEEP: | 12288:zW1xfYBowv43bqKlRH1Vq9iyX9AQ4NqlASvGD7lASvGDw:zW1JYBowvitjVqoA9AOuTD7uTDw |
MALICIOUS
Drops executable file immediately after starts
- msiexec.exe (PID: 3304)
Application was dropped or rewritten from another process
- DGWWP�GEC�U3E4U��D�H.exe (PID: 2072)
SUSPICIOUS
Executable content was dropped or overwritten
- MsiExec.exe (PID: 3796)
- msiexec.exe (PID: 3304)
Drops a file with a compile date too recent
- MsiExec.exe (PID: 3796)
Reads the Windows organization settings
- msiexec.exe (PID: 3024)
- msiexec.exe (PID: 3304)
Executed as Windows Service
- msiexec.exe (PID: 3304)
Reads Windows owner or organization settings
- msiexec.exe (PID: 3024)
- msiexec.exe (PID: 3304)
Drops a file that was compiled in debug mode
- MsiExec.exe (PID: 3796)
- msiexec.exe (PID: 3304)
Checks for external IP
- DGWWP�GEC�U3E4U��D�H.exe (PID: 2072)
Reads the computer name
- DGWWP�GEC�U3E4U��D�H.exe (PID: 2072)
Checks supported languages
- DGWWP�GEC�U3E4U��D�H.exe (PID: 2072)
Creates files in the program directory
- DGWWP�GEC�U3E4U��D�H.exe (PID: 2072)
Application launched itself
- msiexec.exe (PID: 3304)
INFO
Reads the computer name
- msiexec.exe (PID: 3024)
- msiexec.exe (PID: 3304)
- MsiExec.exe (PID: 3796)
Checks Windows Trust Settings
- MsiExec.exe (PID: 3796)
Reads settings of System Certificates
- MsiExec.exe (PID: 3796)
- DGWWP�GEC�U3E4U��D�H.exe (PID: 2072)
Checks supported languages
- msiexec.exe (PID: 3024)
- msiexec.exe (PID: 3304)
- MsiExec.exe (PID: 3796)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (88.6) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (10) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| Pages: | 200 |
|---|---|
| Keywords: | Installer, MSI, Database |
| Title: | Installation Database |
| Comments: | A base dados do instalador contêm a lógica e os dados necessários para instalar o Carregando... |
| Template: | ;1046 |
| Software: | Advanced Installer 18.1 build 4fb1edbd |
| LastModifiedBy: | - |
| Author: | FDSDRFGSEWRR |
| Subject: | Carregando.. |
| Words: | 10 |
| RevisionNumber: | {F4F1A063-F85C-44FB-889E-0A184A11BD00} |
| CodePage: | Windows Latin 1 (Western European) |
| Security: | None |
| ModifyDate: | 2020:09:18 14:06:51 |
| CreateDate: | 2009:12:11 11:47:44 |
| LastPrinted: | 2009:12:11 11:47:44 |
Total processes
40
Monitored processes
4
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
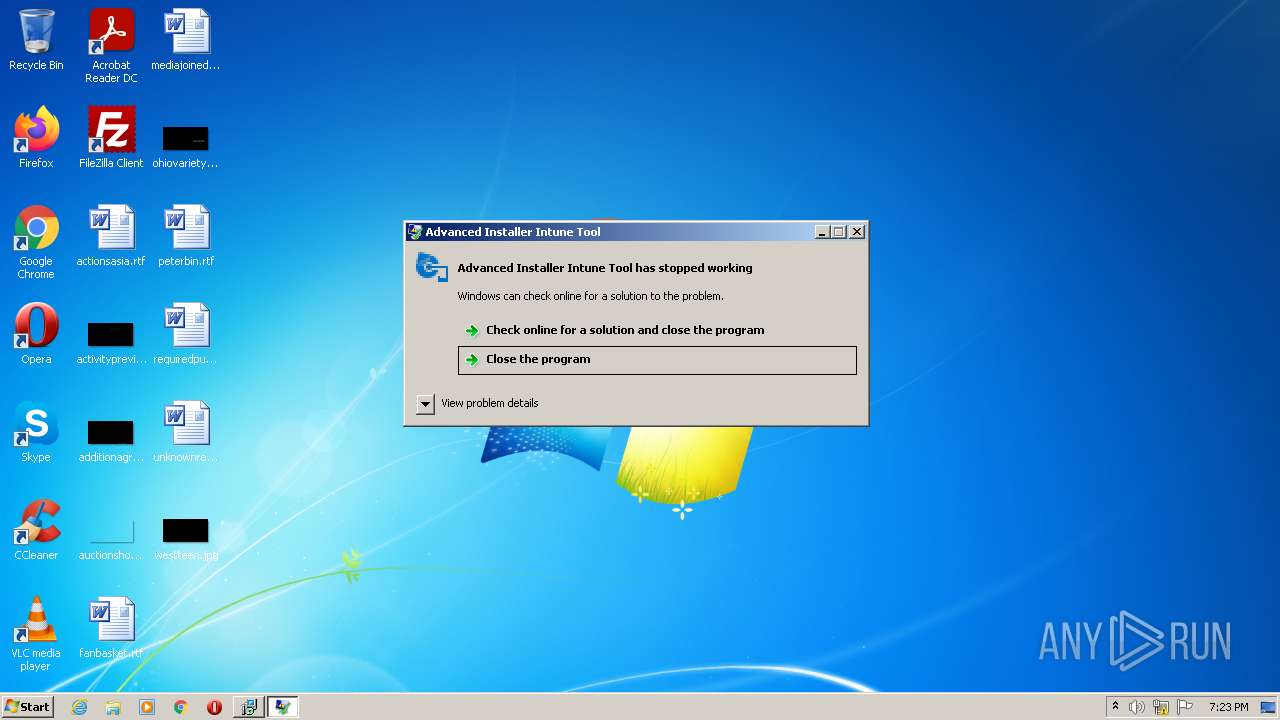
| 2072 | C:\Users\Public\Documents\DGWWP�GEC�U3E4U��D�H.exe | C:\Users\Public\Documents\DGWWP�GEC�U3E4U��D�H.exe | MsiExec.exe | ||||||||||||
User: admin Company: Caphyon LTD Integrity Level: MEDIUM Description: Advanced Installer Intune Tool Exit code: 0 Version: 18.1.0.0 Modules
| |||||||||||||||
| 3024 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\59a3f7c8511f22a6e48ec6a8f058fefaa3c881c0577bde3cf3ba34ef5688990b.msi" | C:\Windows\System32\msiexec.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows� installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3304 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows� installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3796 | C:\Windows\system32\MsiExec.exe -Embedding D0A15CF2120076324D5154CE5781A8A7 | C:\Windows\system32\MsiExec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows� installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
9 508
Read events
9 445
Write events
63
Delete events
0
Modification events
| (PID) Process: | (3304) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: E80C00002002110E7C09D801 | |||
| (PID) Process: | (3304) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 5958448E0EB8240715FDBD5D03A508EF9AD93B04EAD20F9CA87EE8A0C66EB74E | |||
| (PID) Process: | (3304) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (3304) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\InProgress |
| Operation: | write | Name: | (default) |
Value: C:\Windows\Installer\193570.ipi | |||
| (PID) Process: | (3796) MsiExec.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3796) MsiExec.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3796) MsiExec.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3796) MsiExec.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3796) MsiExec.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3796) MsiExec.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000003B010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A80164000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
8
Suspicious files
6
Text files
1
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3304 | msiexec.exe | C:\Windows\Installer\193570.ipi | binary | |
MD5:— | SHA256:— | |||
| 3304 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF8089EA92D82A8DB8.TMP | gmc | |
MD5:— | SHA256:— | |||
| 3796 | MsiExec.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\TRYRETFDGFHGDSF[1].png | executable | |
MD5:— | SHA256:— | |||
| 3796 | MsiExec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\0255CEC2C51D081EFF40366512890989_76C19BA11C72361998CF4C34B60D39D2 | binary | |
MD5:— | SHA256:— | |||
| 3796 | MsiExec.exe | C:\Users\Public\Documents\zlibai.dll | executable | |
MD5:— | SHA256:— | |||
| 3796 | MsiExec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3796 | MsiExec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\5080DC7A65DB6A5960ECD874088F3328_862BA1770B2FEE013603D2FF9ABEAFDA | der | |
MD5:— | SHA256:— | |||
| 3796 | MsiExec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_2DBE917624E9880FE0C7C5570D56E691 | binary | |
MD5:— | SHA256:— | |||
| 3796 | MsiExec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\0255CEC2C51D081EFF40366512890989_76C19BA11C72361998CF4C34B60D39D2 | der | |
MD5:— | SHA256:— | |||
| 3796 | MsiExec.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\FGREWAGTRETWRE[1].png | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
7
DNS requests
5
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2072 | DGWWP�GEC�U3E4U��D�H.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | binary | 272 b | malicious |
3796 | MsiExec.exe | GET | 200 | 104.18.30.182:80 | http://ocsp.comodoca.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBReAhtobFzTvhaRmVeJ38QUchY9AwQUu69%2BAj36pvE8hI6t7jiY7NkyMtQCEQDwHUvue3yjezwFZqwFlyRY | US | der | 728 b | whitelisted |
3796 | MsiExec.exe | GET | 200 | 104.18.30.182:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEGfe9D7xe9riT%2FWUBgbSwIQ%3D | US | der | 471 b | whitelisted |
3796 | MsiExec.exe | GET | 200 | 104.18.30.182:80 | http://ocsp.comodoca.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSTufqHinruS%2FP9Wi1XSjRRzoTLfAQUfgNaZUFrp34K4bidCOodjh1qx2UCEQDJ99nHmXsm6UCfPUeS28Zn | US | der | 472 b | whitelisted |
2072 | DGWWP�GEC�U3E4U��D�H.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | binary | 272 b | malicious |
3796 | MsiExec.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5b7785a346fb93ee | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3796 | MsiExec.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
3796 | MsiExec.exe | 5.9.147.237:443 | 3dgq1431.simple.az | Hetzner Online GmbH | DE | unknown |
3796 | MsiExec.exe | 104.18.30.182:80 | ocsp.comodoca.com | Cloudflare Inc | US | suspicious |
2072 | DGWWP�GEC�U3E4U��D�H.exe | 104.23.98.190:443 | pastebin.com | Cloudflare Inc | US | malicious |
2072 | DGWWP�GEC�U3E4U��D�H.exe | 208.95.112.1:80 | ip-api.com | IBURST | — | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
3dgq1431.simple.az |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
pastebin.com |
| malicious |
ip-api.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2072 | DGWWP�GEC�U3E4U��D�H.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
2072 | DGWWP�GEC�U3E4U��D�H.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
2072 | DGWWP�GEC�U3E4U��D�H.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
2072 | DGWWP�GEC�U3E4U��D�H.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |